University ICTNWK410: Hardware Installation and Network Project
VerifiedAdded on 2023/05/30
|20
|3587
|421
Project
AI Summary
This document presents a comprehensive solution for the ICTNWK410 Install Hardware to a Network assignment. It begins by outlining the main functions and technical specifications of network hardware, specifically routers and switches, detailing their authentication methods, encryption algorithms, and functionalities. The project then discusses the necessary configurations for optimizing hardware within a network system, including the use of IPSec protocol for VPN connections. It also covers alternative hardware components, licensing requirements, and potential security and compatibility issues. Furthermore, the assignment explores workplace IT contracting procedures, including purchasing policies, contractor responsibilities, and information security measures. A brief analysis of suitable network structures, such as LAN, WAN, and wireless networks, is provided, along with their limitations. The document also includes observations on hardware installation, covering the installation of RAM, wireless interfaces, graphics cards, and mice. Finally, it outlines gateway functions, FTP transfer modes, ICMP, UDP, and various network protocols like BOOT and AARP, along with Ethernet categories and network monitoring program applications.

Running head: ICTNWK410 INSTALL HARDWARE TO A NETWORK
ICTNWK410 Install Hardware to a Network
Name of the Student
Name of the University
Author’s Note
ICTNWK410 Install Hardware to a Network
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
ICTNWK410 INSTALL HARDWARE TO A NETWORK
Table of Contents
Assessment 1 (Project)...............................................................................................................2
Assessment 2 (Observation).......................................................................................................7
Assessment 3 (Observation).....................................................................................................10
Bibliography.............................................................................................................................18
ICTNWK410 INSTALL HARDWARE TO A NETWORK
Table of Contents
Assessment 1 (Project)...............................................................................................................2
Assessment 2 (Observation).......................................................................................................7
Assessment 3 (Observation).....................................................................................................10
Bibliography.............................................................................................................................18

2
ICTNWK410 INSTALL HARDWARE TO A NETWORK
Assessment 1 (Project)
What are the main functions of the hardware?
The hardware is used for the performing different calculation and interacting with the
other hardware connected in the network. Here the main hardware used for setting up the
network are the router and switches that manages the transmission of data packets from
source and destination in the network.
Outline the technical specifications of the hardware?
Technical specification of the router
Authentication Method - Secure Shell v.2 (SSH2)
Status Indicators - Power, link/activity
Encryption Algorithm - DES, Triple DES, SSL 3.0, 128-bit AES, 192-bit AES, 256-
bit AES
Manufacturer – Cisco
Form Factor - desktop
Type - Router
Connectivity Technology -wired
Data Link Protocol -Ethernet, Fast Ethernet
Network / Transport Protocol - IPSec
Features - MPLS support, Quality of Service (QoS), VPN support, firewall protection,
hardware encryption, modular design, wall mountable
Compliant Standards - IEEE 802.1x, IEEE 802.3af
ICTNWK410 INSTALL HARDWARE TO A NETWORK
Assessment 1 (Project)
What are the main functions of the hardware?
The hardware is used for the performing different calculation and interacting with the
other hardware connected in the network. Here the main hardware used for setting up the
network are the router and switches that manages the transmission of data packets from
source and destination in the network.
Outline the technical specifications of the hardware?
Technical specification of the router
Authentication Method - Secure Shell v.2 (SSH2)
Status Indicators - Power, link/activity
Encryption Algorithm - DES, Triple DES, SSL 3.0, 128-bit AES, 192-bit AES, 256-
bit AES
Manufacturer – Cisco
Form Factor - desktop
Type - Router
Connectivity Technology -wired
Data Link Protocol -Ethernet, Fast Ethernet
Network / Transport Protocol - IPSec
Features - MPLS support, Quality of Service (QoS), VPN support, firewall protection,
hardware encryption, modular design, wall mountable
Compliant Standards - IEEE 802.1x, IEEE 802.3af
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
ICTNWK410 INSTALL HARDWARE TO A NETWORK
Remote Management Protocol - SNMP 3
Functionality – It is used for routing the data and information from the source to the
destination address in the network. It maintains the route and helps in management of the
communication between the user connected in the network.
Technical specification of switch
Subtype - Fast Ethernet
Ports - 24 x 10/100 + 2 x 10/100/1000
Performance - Switching capacity: 32 Gbps
Forwarding performance (64-byte packet size): 6.5 Mpps
Authentication Method - RADIUS, Secure Shell (SSH), TACACS+
RAM - 64 MB
MAC Address Table Size - 8K entries
Authentication Method - Secure Shell (SSH), RADIUS, TACACS+
Status Indicators - Port transmission speed, port duplex mode, power, link OK,
system, link/activity
Encryption Algorithm - SSL
Manufacturer – Cisco
Functionality – It mainly manages the distribution of the network and connecting the
multiple hosts in the network for enabling them sending and receiving data in the network.
For increasing the security the switch can be configured with VLAN and isolating them from
the other departments.
ICTNWK410 INSTALL HARDWARE TO A NETWORK
Remote Management Protocol - SNMP 3
Functionality – It is used for routing the data and information from the source to the
destination address in the network. It maintains the route and helps in management of the
communication between the user connected in the network.
Technical specification of switch
Subtype - Fast Ethernet
Ports - 24 x 10/100 + 2 x 10/100/1000
Performance - Switching capacity: 32 Gbps
Forwarding performance (64-byte packet size): 6.5 Mpps
Authentication Method - RADIUS, Secure Shell (SSH), TACACS+
RAM - 64 MB
MAC Address Table Size - 8K entries
Authentication Method - Secure Shell (SSH), RADIUS, TACACS+
Status Indicators - Port transmission speed, port duplex mode, power, link OK,
system, link/activity
Encryption Algorithm - SSL
Manufacturer – Cisco
Functionality – It mainly manages the distribution of the network and connecting the
multiple hosts in the network for enabling them sending and receiving data in the network.
For increasing the security the switch can be configured with VLAN and isolating them from
the other departments.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
ICTNWK410 INSTALL HARDWARE TO A NETWORK
Discuss what configurations are required to adapt / optimise the hardware to the network
system
For optimizing the hardware with the network system the router is needed to be
configured with IPSec protocol such that a vpn connection is established between the head
office and the branch office of the organization.
List any other hardware components that could perform the same functions as the
hardware chosen
The other hardware component that can provide same function is the cisco catalyst 3560 layer
3 switch.
List any licensing requirements of the hardware
The licensing requirement is needed such that the quality standard of the network is
maintained and cisco certification is used for ensuring that the device is compatible with the
standards and protocols developed by cisco.
Include any known security or compatibility issues with the hardware
It does not have support for 1000BASE-T ethernet and also not have physical support
for the wireless network and separate wireless router is needed to be installed in the network
for distribution of the wireless network.
List the required drivers / programs required to be installed to adequately utilise hardware
The followings are the list of required drivers needed to be installed for using the router:
Balanced drivers
Client PC installed with cmd terminal
Outline of the workplace information technology contracting procedures
ICTNWK410 INSTALL HARDWARE TO A NETWORK
Discuss what configurations are required to adapt / optimise the hardware to the network
system
For optimizing the hardware with the network system the router is needed to be
configured with IPSec protocol such that a vpn connection is established between the head
office and the branch office of the organization.
List any other hardware components that could perform the same functions as the
hardware chosen
The other hardware component that can provide same function is the cisco catalyst 3560 layer
3 switch.
List any licensing requirements of the hardware
The licensing requirement is needed such that the quality standard of the network is
maintained and cisco certification is used for ensuring that the device is compatible with the
standards and protocols developed by cisco.
Include any known security or compatibility issues with the hardware
It does not have support for 1000BASE-T ethernet and also not have physical support
for the wireless network and separate wireless router is needed to be installed in the network
for distribution of the wireless network.
List the required drivers / programs required to be installed to adequately utilise hardware
The followings are the list of required drivers needed to be installed for using the router:
Balanced drivers
Client PC installed with cmd terminal
Outline of the workplace information technology contracting procedures

5
ICTNWK410 INSTALL HARDWARE TO A NETWORK
Policy Number: P15483245
Policy Date: 09th December 2018
Purpose: To maintain service level agreement for maintenance of the network
Procedure:
Purchase of hardware
Purchase of computer
Purchase of server
Purchase of computer peripheral
Additional policies for purchasing hardware
Responsibilities of the IT contractor for the workplace
The IT contractor is responsible to analyse the standards and the compatibility of the
device used for the development of the network framework. The data and information assets
should be protected from unauthorised incidents and disclosures. The integrity of the
information assets and the data should also be managed such that it is protected from
accidental modifications.
Outline of the information security procedures at the workplace
For the management of the information security the network is created with
configuring the router with a DMZ zone and the servers should be configured with access
control policy. It should be ensured that the device used meets the relevant legislation and the
device installed complies with the security policy of the organization.
Brief analysis of the network structures suitable for the business / work structure
ICTNWK410 INSTALL HARDWARE TO A NETWORK
Policy Number: P15483245
Policy Date: 09th December 2018
Purpose: To maintain service level agreement for maintenance of the network
Procedure:
Purchase of hardware
Purchase of computer
Purchase of server
Purchase of computer peripheral
Additional policies for purchasing hardware
Responsibilities of the IT contractor for the workplace
The IT contractor is responsible to analyse the standards and the compatibility of the
device used for the development of the network framework. The data and information assets
should be protected from unauthorised incidents and disclosures. The integrity of the
information assets and the data should also be managed such that it is protected from
accidental modifications.
Outline of the information security procedures at the workplace
For the management of the information security the network is created with
configuring the router with a DMZ zone and the servers should be configured with access
control policy. It should be ensured that the device used meets the relevant legislation and the
device installed complies with the security policy of the organization.
Brief analysis of the network structures suitable for the business / work structure
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
ICTNWK410 INSTALL HARDWARE TO A NETWORK
The network structure should be used for the management of the distributed
environment and reducing the complexity of the framework. For the development of then
network a firewall is used at the entry and exit point of the network. Separate VLAN should
be used for the department for subnetting the network into smaller parts and reduce the
congestion. The router should also be configured with access control list such that the
unknown data packets can be dropped to reach the internal network of the organization.
Limitation of the following types of network regarding to the business structure:
Local area network – There is data security threat in the local area network because
unauthorised users can have access of the network and get important data if the data
in the central server is not secured. It also have a limited area of coverage and cannot
be used for covering large geographical area.
Wide area network – The maintenance of the wide area network requires more
supervisors and since different people have the access of the network the security of
the network can be compromised. More cost can be included for protecting the
network from hackers and viruses
Wireless network – The transfer speed of the files are slower and the network
bandwidth can get stolen if the access points are not secured with password
protection.
Mobile Equipment – it needs new technology and costly devices for setting up the
new network and there is a need of ongoing maintenance. There is a potential for
disruption in the business and productivity with the increase in the number of device.
ICTNWK410 INSTALL HARDWARE TO A NETWORK
The network structure should be used for the management of the distributed
environment and reducing the complexity of the framework. For the development of then
network a firewall is used at the entry and exit point of the network. Separate VLAN should
be used for the department for subnetting the network into smaller parts and reduce the
congestion. The router should also be configured with access control list such that the
unknown data packets can be dropped to reach the internal network of the organization.
Limitation of the following types of network regarding to the business structure:
Local area network – There is data security threat in the local area network because
unauthorised users can have access of the network and get important data if the data
in the central server is not secured. It also have a limited area of coverage and cannot
be used for covering large geographical area.
Wide area network – The maintenance of the wide area network requires more
supervisors and since different people have the access of the network the security of
the network can be compromised. More cost can be included for protecting the
network from hackers and viruses
Wireless network – The transfer speed of the files are slower and the network
bandwidth can get stolen if the access points are not secured with password
protection.
Mobile Equipment – it needs new technology and costly devices for setting up the
new network and there is a need of ongoing maintenance. There is a potential for
disruption in the business and productivity with the increase in the number of device.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
ICTNWK410 INSTALL HARDWARE TO A NETWORK
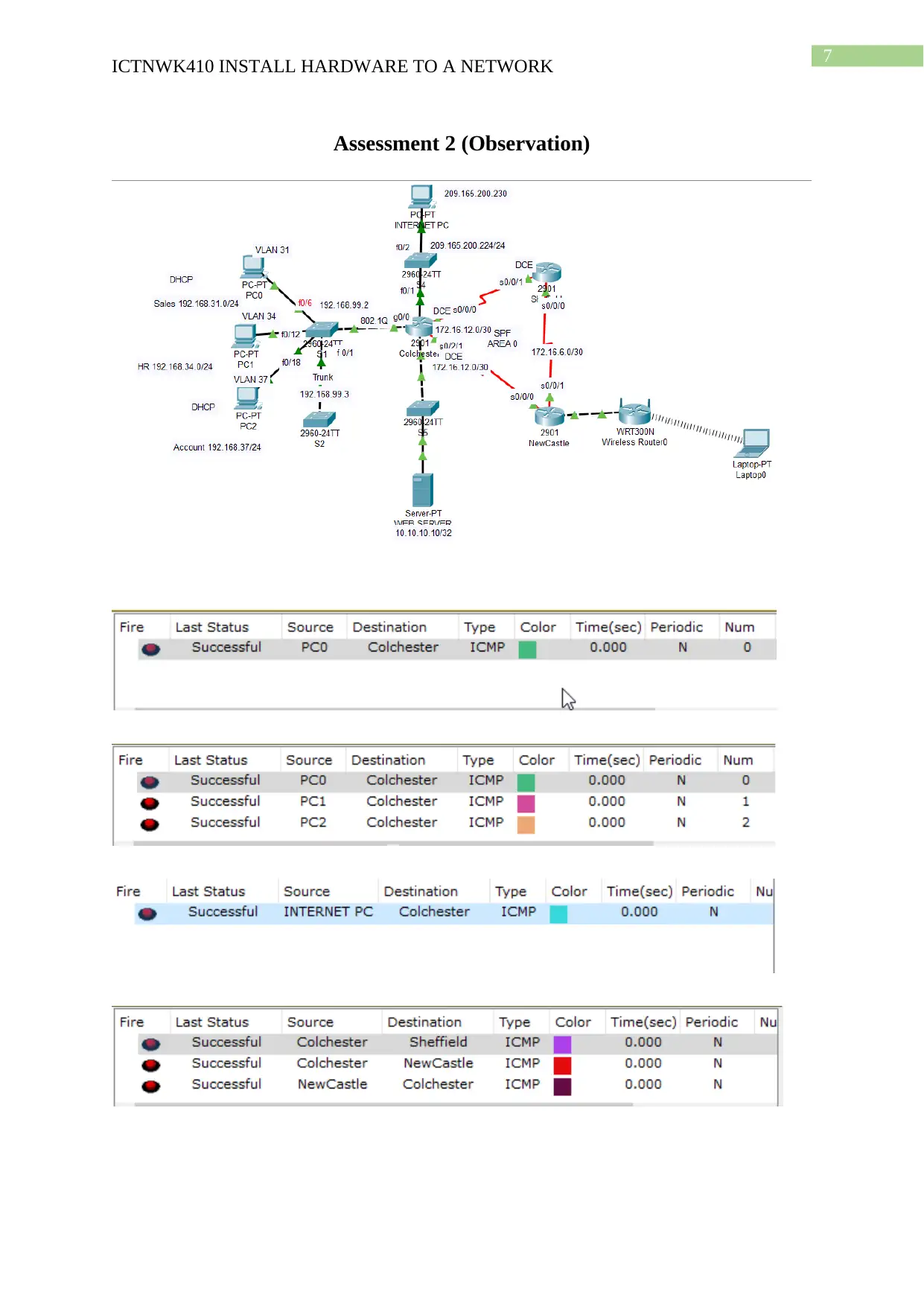
Assessment 2 (Observation)
ICTNWK410 INSTALL HARDWARE TO A NETWORK
Assessment 2 (Observation)
8
ICTNWK410 INSTALL HARDWARE TO A NETWORK
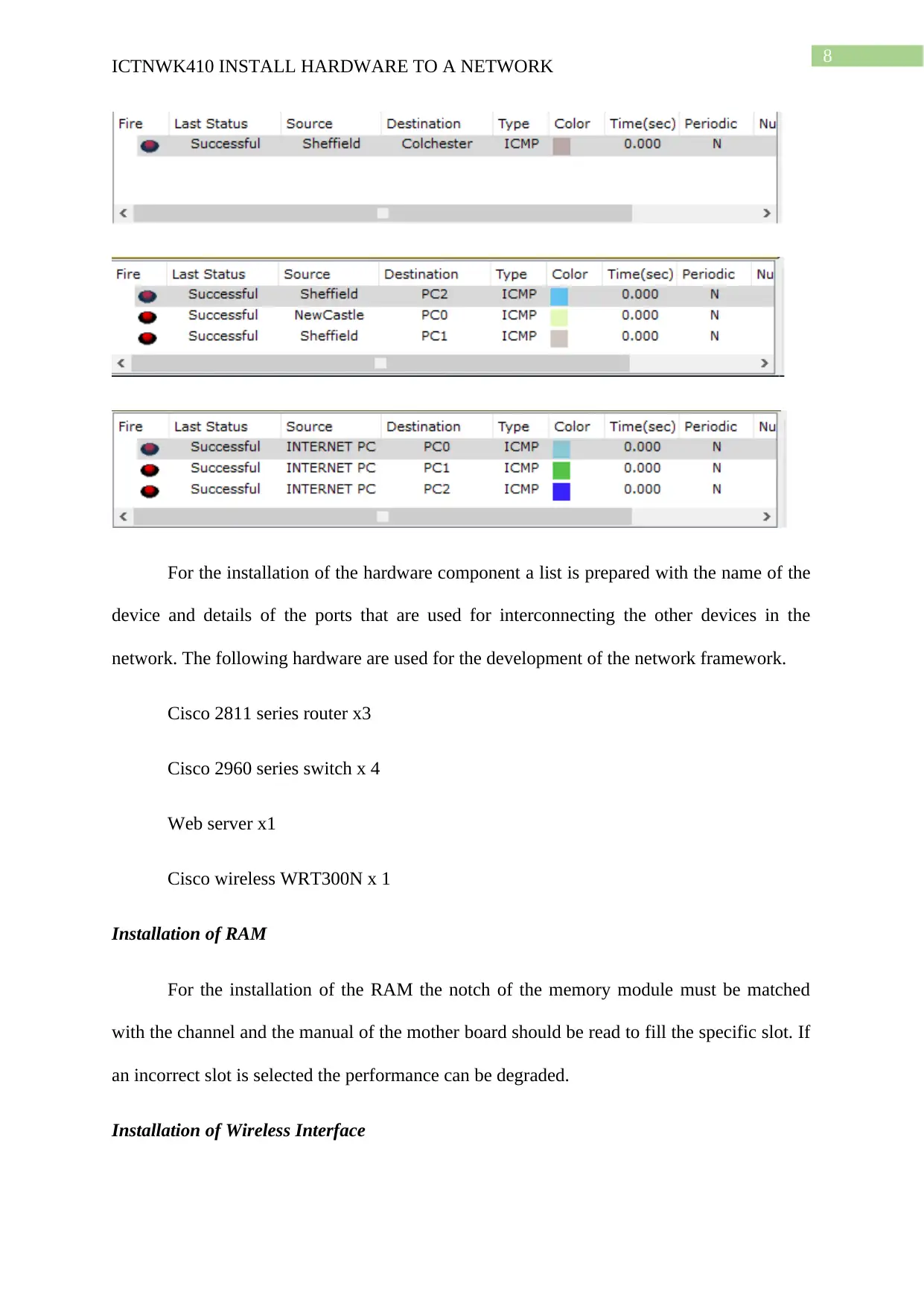
For the installation of the hardware component a list is prepared with the name of the
device and details of the ports that are used for interconnecting the other devices in the
network. The following hardware are used for the development of the network framework.
Cisco 2811 series router x3
Cisco 2960 series switch x 4
Web server x1
Cisco wireless WRT300N x 1
Installation of RAM
For the installation of the RAM the notch of the memory module must be matched
with the channel and the manual of the mother board should be read to fill the specific slot. If
an incorrect slot is selected the performance can be degraded.
Installation of Wireless Interface
ICTNWK410 INSTALL HARDWARE TO A NETWORK
For the installation of the hardware component a list is prepared with the name of the
device and details of the ports that are used for interconnecting the other devices in the
network. The following hardware are used for the development of the network framework.
Cisco 2811 series router x3
Cisco 2960 series switch x 4
Web server x1
Cisco wireless WRT300N x 1
Installation of RAM
For the installation of the RAM the notch of the memory module must be matched
with the channel and the manual of the mother board should be read to fill the specific slot. If
an incorrect slot is selected the performance can be degraded.
Installation of Wireless Interface
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
ICTNWK410 INSTALL HARDWARE TO A NETWORK
The computer should be powered off and the case should be opened for the
identification of the empty slot. The wireless networking card should be aligned with the
PCIE slot in the motherboard and pushed in for installation. The card should be screwed with
the case and the yellow caps should be removed from the antennas and installed with the card
using the supplied screws.
Installation of Graphics Card
The older driver of graphics card should be uninstalled and the PC should be powered
off before starting the installation. The Second PCIE clot should be used for this installation
and it follows the same procedure as the installation of the wireless interface card. New driver
for the GPU is needed to be downloaded for maintaining effective communication of
Windows with the card.
Installation of Mouse
The mouse can works with simple plug and play option using the PS/2 port. The pins
of the mouse should be matched and the green port should be used for the installation. After
successful connection the driver gets automatically installed and it can function normally.
ICTNWK410 INSTALL HARDWARE TO A NETWORK
The computer should be powered off and the case should be opened for the
identification of the empty slot. The wireless networking card should be aligned with the
PCIE slot in the motherboard and pushed in for installation. The card should be screwed with
the case and the yellow caps should be removed from the antennas and installed with the card
using the supplied screws.
Installation of Graphics Card
The older driver of graphics card should be uninstalled and the PC should be powered
off before starting the installation. The Second PCIE clot should be used for this installation
and it follows the same procedure as the installation of the wireless interface card. New driver
for the GPU is needed to be downloaded for maintaining effective communication of
Windows with the card.
Installation of Mouse
The mouse can works with simple plug and play option using the PS/2 port. The pins
of the mouse should be matched and the green port should be used for the installation. After
successful connection the driver gets automatically installed and it can function normally.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
ICTNWK410 INSTALL HARDWARE TO A NETWORK
Assessment 3 (Observation)
For the installation of the hardware the compatibility of the hardware with the other
networking devices should be identified and the protocols that should be used for the
configuration of the router should be documented. The services required by the user should
be analysed for the configuration of the network solution. The development of the training
plan for using the network would help the user to utilize the network resources efficiently and
maintain high functionality of the network.
What is a gateway? What function does it performs?
The gateway is a network node that is used for connecting two networks. It is used for
The gateway allows the network host to communicate with the remote host or the
remote network.
What are the 3 FTP transfer modes? Briefly describe each?
Stream mode – In this mode the files are transferred continuously as a stream of TCP
bytes and the TCP maintains its responsibility to divide the data into multiple segments.
Block Mode – It is used for delivering data from FTP to TCP blocks and a 3 bytes of
header is added to each of the block. The first block represents the descriptor and the 2nd and
the 3rd is used for defining the block size in bytes.
Compressed Mode – In this mode the data are compressed and Run-length encoding
is used for the compression. For example in the text file the space are eliminated and in case
of the binary files the null characters are compressed.
What is Internet Control Message (ICMP)? What are the functions of this?
ICTNWK410 INSTALL HARDWARE TO A NETWORK
Assessment 3 (Observation)
For the installation of the hardware the compatibility of the hardware with the other
networking devices should be identified and the protocols that should be used for the
configuration of the router should be documented. The services required by the user should
be analysed for the configuration of the network solution. The development of the training
plan for using the network would help the user to utilize the network resources efficiently and
maintain high functionality of the network.
What is a gateway? What function does it performs?
The gateway is a network node that is used for connecting two networks. It is used for
The gateway allows the network host to communicate with the remote host or the
remote network.
What are the 3 FTP transfer modes? Briefly describe each?
Stream mode – In this mode the files are transferred continuously as a stream of TCP
bytes and the TCP maintains its responsibility to divide the data into multiple segments.
Block Mode – It is used for delivering data from FTP to TCP blocks and a 3 bytes of
header is added to each of the block. The first block represents the descriptor and the 2nd and
the 3rd is used for defining the block size in bytes.
Compressed Mode – In this mode the data are compressed and Run-length encoding
is used for the compression. For example in the text file the space are eliminated and in case
of the binary files the null characters are compressed.
What is Internet Control Message (ICMP)? What are the functions of this?

11
ICTNWK410 INSTALL HARDWARE TO A NETWORK
It is a protocol used for error reporting and utilized for generating error message when
the delivery of data packet to the destination address is prevented.
It is used by the network administrator for pinging and troubleshooting the
connectivity between the devices connected in the network.
What is ‘User Datagram Protocol’ used for?
It is used for sending short messages known as datagrams and it is a part of the
internet protocol suite. It is used by the programs on the computer nodes for communicating
with the nodes connected in the network.
Outline the functions of the following protocols:
BOOT Protocol –
Used for obtaining the IP address from the server and used as a replacement of the
reverse address resolution protocol.
It is used by the computer to find the necessary thing that is needed to be performed
after booting up.
AARP –
It is used for mapping the IP address with the MAC address of the computer.
What are the 3 principle categories of Ethernet?
IEEE 802.3 – it operates on 10 Mbps using coaxial cable
100 Mbps Ethernet – Known as fast ethernet operating 100 Mbps using twisted pair
cable
1000 Mbps Ethernet – Known as Gigabit ethernet operating at 1 Gbps using fiber
optic or twisted pair cable.
ICTNWK410 INSTALL HARDWARE TO A NETWORK
It is a protocol used for error reporting and utilized for generating error message when
the delivery of data packet to the destination address is prevented.
It is used by the network administrator for pinging and troubleshooting the
connectivity between the devices connected in the network.
What is ‘User Datagram Protocol’ used for?
It is used for sending short messages known as datagrams and it is a part of the
internet protocol suite. It is used by the programs on the computer nodes for communicating
with the nodes connected in the network.
Outline the functions of the following protocols:
BOOT Protocol –
Used for obtaining the IP address from the server and used as a replacement of the
reverse address resolution protocol.
It is used by the computer to find the necessary thing that is needed to be performed
after booting up.
AARP –
It is used for mapping the IP address with the MAC address of the computer.
What are the 3 principle categories of Ethernet?
IEEE 802.3 – it operates on 10 Mbps using coaxial cable
100 Mbps Ethernet – Known as fast ethernet operating 100 Mbps using twisted pair
cable
1000 Mbps Ethernet – Known as Gigabit ethernet operating at 1 Gbps using fiber
optic or twisted pair cable.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





