ICTNWK503: Enterprise Security Plan & Authentication Methods
VerifiedAdded on 2023/06/12
|8
|2461
|253
Case Study
AI Summary
This case study provides a security plan for NetSecurity Pty Ltd., focusing on secure authentication and authorization methods for EducationalFirst Pty Ltd. The plan addresses unauthorized access and virus threats, proposing a VPN service for secure remote access. It identifies enterprise security requirements, including authentication via login credentials and authorization for access privileges. Various authentication methods, such as passwords and biometrics, are discussed, with EAP (Extensible Authentication Protocol) selected as the suitable method. User attributes, permissions, and responsibilities within the authentication system are detailed, along with secure storage solutions like cloud storage. The report also includes an ongoing monitoring plan and incident management procedures to ensure the system's effectiveness and security. This document is available on Desklib, where students can find a wealth of solved assignments and past papers to aid their studies.

Running head: INFORMATION TECHNOLOGY
INFORMATION TECHNOLOGY
[Name of the Student]
[Name of the University]
[Author note]
INFORMATION TECHNOLOGY
[Name of the Student]
[Name of the University]
[Author note]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION TECHNOLOGY
1. Introduction
NetSecurity Pty Ltd. is an organization which is specialized in providing outsourced
security and is associated with working with multiple number of companies in order to
provide secure authentication services and deploy certain Security policies for the
Companies whit whom they are working. A client named EducationalFirst Pty Ltd.
has recently approached the NetSecurity Pty Ltd. in order to save itself from various
virus or security related threats. The main aim of this report is to provide a secure
authentication method to the computers and the online modules of the client so as
make sure that the client is secure from any type of virus or security related threats.
The report also aims at providing the essential requirements so as to create a VPN
service for the employees of EducationalFirst Pty Ltd. in order to help them work
secure from their homes.
2. Describe the enterprise security plan.
The main scope of this report is to create an authentication process so as to save the
materials from any type of unauthenticated access of the materials which are online
and are stored. There should exist a secure authentic model for the computers of
EducationFirst as well as for the online modules. It is also to be made sure that there
is no virus or security threats in the systems of the client. The main security issue
that is to be addressed is that there is no unauthorised access and the system is free
of virus. The VPN that is to be created would be associated with providing all the
employees a secure access to the private network. This VPN would act like a firewall
in the computer and the only difference is that this protection would be provided
online.
Page 1
1. Introduction
NetSecurity Pty Ltd. is an organization which is specialized in providing outsourced
security and is associated with working with multiple number of companies in order to
provide secure authentication services and deploy certain Security policies for the
Companies whit whom they are working. A client named EducationalFirst Pty Ltd.
has recently approached the NetSecurity Pty Ltd. in order to save itself from various
virus or security related threats. The main aim of this report is to provide a secure
authentication method to the computers and the online modules of the client so as
make sure that the client is secure from any type of virus or security related threats.
The report also aims at providing the essential requirements so as to create a VPN
service for the employees of EducationalFirst Pty Ltd. in order to help them work
secure from their homes.
2. Describe the enterprise security plan.
The main scope of this report is to create an authentication process so as to save the
materials from any type of unauthenticated access of the materials which are online
and are stored. There should exist a secure authentic model for the computers of
EducationFirst as well as for the online modules. It is also to be made sure that there
is no virus or security threats in the systems of the client. The main security issue
that is to be addressed is that there is no unauthorised access and the system is free
of virus. The VPN that is to be created would be associated with providing all the
employees a secure access to the private network. This VPN would act like a firewall
in the computer and the only difference is that this protection would be provided
online.
Page 1
2INFORMATION TECHNOLOGY
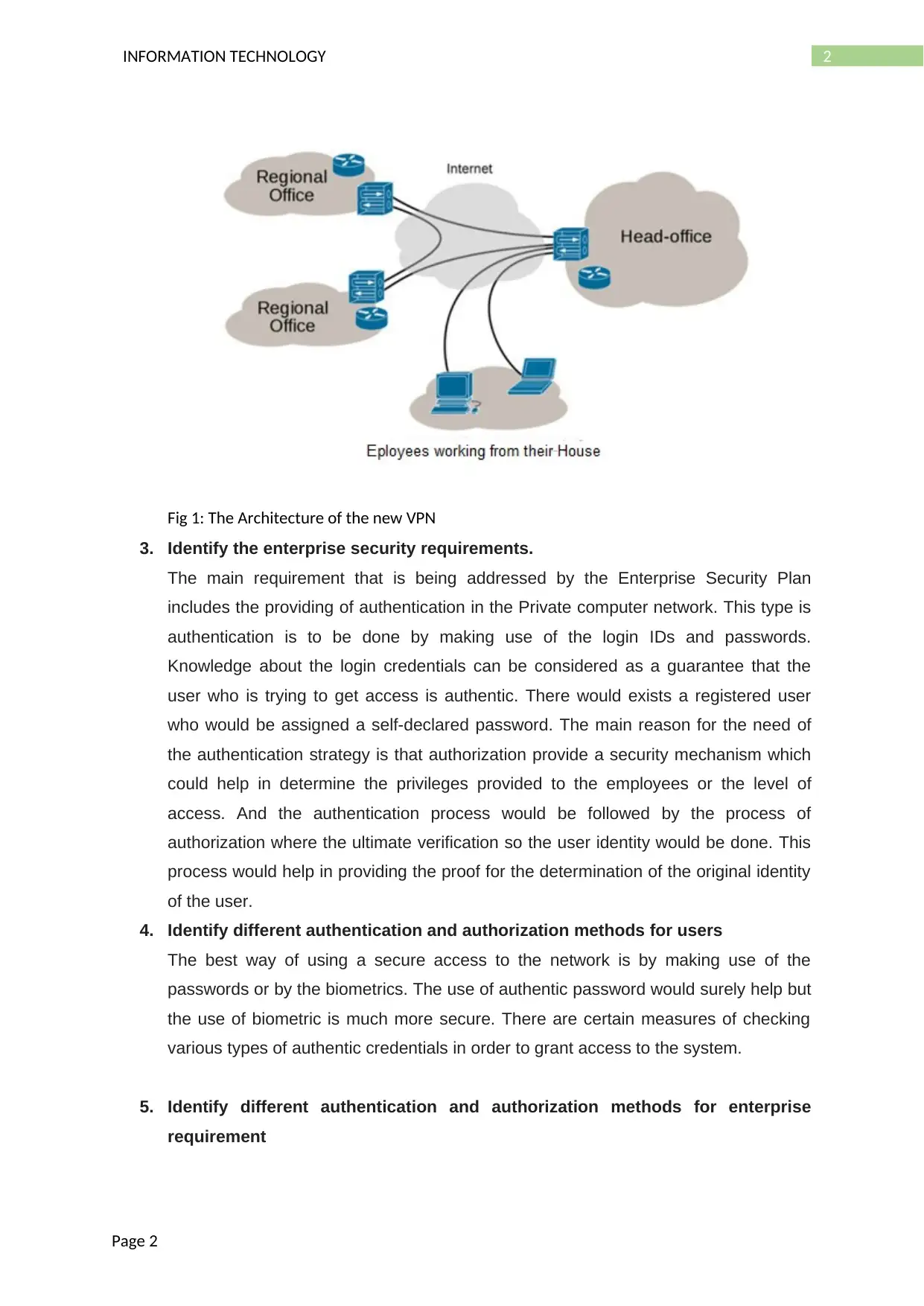
Fig 1: The Architecture of the new VPN
3. Identify the enterprise security requirements.
The main requirement that is being addressed by the Enterprise Security Plan
includes the providing of authentication in the Private computer network. This type is
authentication is to be done by making use of the login IDs and passwords.
Knowledge about the login credentials can be considered as a guarantee that the
user who is trying to get access is authentic. There would exists a registered user
who would be assigned a self-declared password. The main reason for the need of
the authentication strategy is that authorization provide a security mechanism which
could help in determine the privileges provided to the employees or the level of
access. And the authentication process would be followed by the process of
authorization where the ultimate verification so the user identity would be done. This
process would help in providing the proof for the determination of the original identity
of the user.
4. Identify different authentication and authorization methods for users
The best way of using a secure access to the network is by making use of the
passwords or by the biometrics. The use of authentic password would surely help but
the use of biometric is much more secure. There are certain measures of checking
various types of authentic credentials in order to grant access to the system.
5. Identify different authentication and authorization methods for enterprise
requirement
Page 2
Fig 1: The Architecture of the new VPN
3. Identify the enterprise security requirements.
The main requirement that is being addressed by the Enterprise Security Plan
includes the providing of authentication in the Private computer network. This type is
authentication is to be done by making use of the login IDs and passwords.
Knowledge about the login credentials can be considered as a guarantee that the
user who is trying to get access is authentic. There would exists a registered user
who would be assigned a self-declared password. The main reason for the need of
the authentication strategy is that authorization provide a security mechanism which
could help in determine the privileges provided to the employees or the level of
access. And the authentication process would be followed by the process of
authorization where the ultimate verification so the user identity would be done. This
process would help in providing the proof for the determination of the original identity
of the user.
4. Identify different authentication and authorization methods for users
The best way of using a secure access to the network is by making use of the
passwords or by the biometrics. The use of authentic password would surely help but
the use of biometric is much more secure. There are certain measures of checking
various types of authentic credentials in order to grant access to the system.
5. Identify different authentication and authorization methods for enterprise
requirement
Page 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION TECHNOLOGY
The authentication process generally consists of two goals and this mainly includes
the keeping away of the unauthorized persons from getting access to the resources
which are private. The authentication process is also associated with providing the
authorized persons with an easy access to the various types of resources that are
needed. There is a need of number of components in order to accomplish this goals.
One of the way involves the assigning the permission of access to the resources in
order to specify the users who would be capable or not capable of accessing the
resources and under what circumstances this happens. And authorization of the user
would only occur when the authentication is completed. Whenever an employee
would try to log in into the VPN he/she would be provide with an access token which
would be consisting of all the information about the security of EducationFirst Pyt Ltd.
after this whenever the employee would try to access the resources in the network
then Access Control List or the ACL which is associated with the resources would be
checking all the aspects against the access token. Once the ACL sees that the
person is having the permission to access the resources and also the token shows
that the person is the employee of EducationFirst then the access would be granted.
The authentication that is to be used by the client is EAP or Extensible Authentication
protocol or the EAP authentication method.
6. Select and explain the suitable authentication and authorization method.
The best method is the EAP authentication method which would be mainly
associated with providing authentication to the remote access connections, in this
method the VPN client and the authenticator would be associated with deciding if to
start an authentication mechanism or not.
7. Describe the user attributes and user attributes setup.
There would be different types of user present the new system and this might include
the administrators, security administrators, standard users and many more. This
users are associated with supporting the secure system in different ways. The main
users of the system includes the admin staffs and the teachers. The security
administrators would mainly be management and distribution of the various system
related information to its different employees. The administrator would be associated
with coordinating of various types of work. The security administrator would be
responsible for dictating all the security related problems and helping the other
employees in understanding the various types of benefits and the issues that might
arise due to the introduction of the new system. The employees or the teachers
associated with the organization would be responsible for using the system in a valid
way without leaving any kind of vulnerabilities. They must make it sure that they are
Page 3
The authentication process generally consists of two goals and this mainly includes
the keeping away of the unauthorized persons from getting access to the resources
which are private. The authentication process is also associated with providing the
authorized persons with an easy access to the various types of resources that are
needed. There is a need of number of components in order to accomplish this goals.
One of the way involves the assigning the permission of access to the resources in
order to specify the users who would be capable or not capable of accessing the
resources and under what circumstances this happens. And authorization of the user
would only occur when the authentication is completed. Whenever an employee
would try to log in into the VPN he/she would be provide with an access token which
would be consisting of all the information about the security of EducationFirst Pyt Ltd.
after this whenever the employee would try to access the resources in the network
then Access Control List or the ACL which is associated with the resources would be
checking all the aspects against the access token. Once the ACL sees that the
person is having the permission to access the resources and also the token shows
that the person is the employee of EducationFirst then the access would be granted.
The authentication that is to be used by the client is EAP or Extensible Authentication
protocol or the EAP authentication method.
6. Select and explain the suitable authentication and authorization method.
The best method is the EAP authentication method which would be mainly
associated with providing authentication to the remote access connections, in this
method the VPN client and the authenticator would be associated with deciding if to
start an authentication mechanism or not.
7. Describe the user attributes and user attributes setup.
There would be different types of user present the new system and this might include
the administrators, security administrators, standard users and many more. This
users are associated with supporting the secure system in different ways. The main
users of the system includes the admin staffs and the teachers. The security
administrators would mainly be management and distribution of the various system
related information to its different employees. The administrator would be associated
with coordinating of various types of work. The security administrator would be
responsible for dictating all the security related problems and helping the other
employees in understanding the various types of benefits and the issues that might
arise due to the introduction of the new system. The employees or the teachers
associated with the organization would be responsible for using the system in a valid
way without leaving any kind of vulnerabilities. They must make it sure that they are
Page 3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION TECHNOLOGY
aware of all the security aspects and does not disclose their authentication criteria’s
to others.
8. Briefly describe the user permission and responsibilities on the authentication
system.
The users would be mainly be associated with various types of various kinds of
responsibilities. Their responsibilities mainly includes the maintenance of the
security of the system. The users should be also make it sure that any of the
authenticating credentials are not disclosed to anyone. And if in case if it is disclosed
then they should be sure that it is informed to the authority so as to help them in
changing the authentication criteria’s like password or the username. Along with this
it is their responsibility to use strong and complicated passwords. The administration
should make it sure that the system which they are operating is kept up to dated and
it should be made sure that trusted anti-virus are installed so as to protect the
information from any type of virus attacks. The employees should also make it sure
that they are not using the public computers or networks so as to access their
accounts. They should also look into the matter that their passwords are not getting
auto saved and should not share their password with anyone. Trainings should be
provided by the security administrators to every employee about the system should
be used.
9. Describe the Secure location to store the permission and configuration
information.
The best place to store the permissions and the configurations is on the clouds
where it can be accessed by every authentic users. The data can be recovered from
the cloud if the authentic users have access to the clouds. The cloud system is one
of the secure storage system which the organization can use to store the information
and configure the process of accessing the information. The authenticated users
would be provided the process of getting access to this information and this would
initially help them getting access to the required information even if the administrator
of the system is not present.
10. Review the authentication system.
The proposed system is much better than the system which is existing right now in
EducationFirst Pty Ltd. The current system is designed for the small group of user
but with increasing number of students the handling of the various activities would
become difficult. But the new system would greatly help in handling a large number
Page 4
aware of all the security aspects and does not disclose their authentication criteria’s
to others.
8. Briefly describe the user permission and responsibilities on the authentication
system.
The users would be mainly be associated with various types of various kinds of
responsibilities. Their responsibilities mainly includes the maintenance of the
security of the system. The users should be also make it sure that any of the
authenticating credentials are not disclosed to anyone. And if in case if it is disclosed
then they should be sure that it is informed to the authority so as to help them in
changing the authentication criteria’s like password or the username. Along with this
it is their responsibility to use strong and complicated passwords. The administration
should make it sure that the system which they are operating is kept up to dated and
it should be made sure that trusted anti-virus are installed so as to protect the
information from any type of virus attacks. The employees should also make it sure
that they are not using the public computers or networks so as to access their
accounts. They should also look into the matter that their passwords are not getting
auto saved and should not share their password with anyone. Trainings should be
provided by the security administrators to every employee about the system should
be used.
9. Describe the Secure location to store the permission and configuration
information.
The best place to store the permissions and the configurations is on the clouds
where it can be accessed by every authentic users. The data can be recovered from
the cloud if the authentic users have access to the clouds. The cloud system is one
of the secure storage system which the organization can use to store the information
and configure the process of accessing the information. The authenticated users
would be provided the process of getting access to this information and this would
initially help them getting access to the required information even if the administrator
of the system is not present.
10. Review the authentication system.
The proposed system is much better than the system which is existing right now in
EducationFirst Pty Ltd. The current system is designed for the small group of user
but with increasing number of students the handling of the various activities would
become difficult. But the new system would greatly help in handling a large number
Page 4

5INFORMATION TECHNOLOGY
of users and the users mainly include the teachers and the admin staffs which would
increase with the increased number of students. The new system also resistant to the
various types of security threats which are increasing day by day.
11. Prepare the ongoing monitoring plan
The new security system that is to be deployed needs to be monitored effectively.
Monitoring is to be done in order to see if there is any of deficiency in the security
system. The main thing that is to be monitored is the way in which a user is getting
authenticated and to see if there is any kind of problem during the authentication
process.
12. Prepare incident management and reporting document.
In case if it is seen that there is any type of problem in getting access to the secured
network then the problem must be critically analysed. The critical analysis is to be
done in order to check the actual reason which is responsible for the problem. After
the detection of the problem is done and the main reason. In case whenever a failed
login happens then checking should be done regarding the input of the correct
password. The failed login might also occur if an unauthorized person gets access to
the account and changes the password. So it must be checked if any kind of breach
has occurred or not.
Page 5
of users and the users mainly include the teachers and the admin staffs which would
increase with the increased number of students. The new system also resistant to the
various types of security threats which are increasing day by day.
11. Prepare the ongoing monitoring plan
The new security system that is to be deployed needs to be monitored effectively.
Monitoring is to be done in order to see if there is any of deficiency in the security
system. The main thing that is to be monitored is the way in which a user is getting
authenticated and to see if there is any kind of problem during the authentication
process.
12. Prepare incident management and reporting document.
In case if it is seen that there is any type of problem in getting access to the secured
network then the problem must be critically analysed. The critical analysis is to be
done in order to check the actual reason which is responsible for the problem. After
the detection of the problem is done and the main reason. In case whenever a failed
login happens then checking should be done regarding the input of the correct
password. The failed login might also occur if an unauthorized person gets access to
the account and changes the password. So it must be checked if any kind of breach
has occurred or not.
Page 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION TECHNOLOGY
References:
Akella, A. V., & Xiong, K. (2014, August). Quality of service (QoS)-guaranteed
network resource allocation via software defined networking (SDN).
In Dependable, Autonomic and Secure Computing (DASC), 2014 IEEE 12th
International Conference on (pp. 7-13). IEEE.
An, F. T., Hsueh, Y. L., Kim, K. S., White, I. M., & Kazovsky, L. G. (2014). A new
dynamic bandwidth allocation protocol with quality of service in ethernet-
based passive optical networks. arXiv preprint arXiv:1404.2413.
Bhargavan, K., Lavaud, A. D., Fournet, C., Pironti, A., & Strub, P. Y. (2014, May).
Triple handshakes and cookie cutters: Breaking and fixing authentication over
TLS. In Security and Privacy (SP), 2014 IEEE Symposium on (pp. 98-113).
IEEE.
De Marsico, M., Nappi, M., Riccio, D., & Wechsler, H. (2015). Mobile Iris Challenge
Evaluation (MICHE)-I, biometric iris dataset and protocols. Pattern
Recognition Letters, 57, 17-23.
DeKok, A., & Lior, A. (2013). Remote Authentication Dial In User Service (RADIUS)
Protocol Extensions (No. RFC 6929).
Fournaris, A. P., & Keramidas, G. (2014). From hardware security tokens to trusted
computing and trusted systems. In System-Level Design Methodologies for
Telecommunication(pp. 99-117). Springer, Cham.
He, D., Zhao, W., & Wu, S. (2013). Security Analysis of a Dynamic ID-based
Authentication Scheme for Multi-server Environment Using Smart Cards. IJ
Network Security, 15(5), 350-356.
Krishna, P. V., Misra, S., Joshi, D., Gupta, A., & Obaidat, M. S. (2014). Secure
socket layer certificate verification: a learning automata approach. Security
and Communication Networks, 7(11), 1712-1718.
Lee, C. C., Liu, C. H., & Hwang, M. S. (2013). Guessing Attacks on Strong-Password
Authentication Protocol. IJ Network Security, 15(1), 64-67.
Page 6
References:
Akella, A. V., & Xiong, K. (2014, August). Quality of service (QoS)-guaranteed
network resource allocation via software defined networking (SDN).
In Dependable, Autonomic and Secure Computing (DASC), 2014 IEEE 12th
International Conference on (pp. 7-13). IEEE.
An, F. T., Hsueh, Y. L., Kim, K. S., White, I. M., & Kazovsky, L. G. (2014). A new
dynamic bandwidth allocation protocol with quality of service in ethernet-
based passive optical networks. arXiv preprint arXiv:1404.2413.
Bhargavan, K., Lavaud, A. D., Fournet, C., Pironti, A., & Strub, P. Y. (2014, May).
Triple handshakes and cookie cutters: Breaking and fixing authentication over
TLS. In Security and Privacy (SP), 2014 IEEE Symposium on (pp. 98-113).
IEEE.
De Marsico, M., Nappi, M., Riccio, D., & Wechsler, H. (2015). Mobile Iris Challenge
Evaluation (MICHE)-I, biometric iris dataset and protocols. Pattern
Recognition Letters, 57, 17-23.
DeKok, A., & Lior, A. (2013). Remote Authentication Dial In User Service (RADIUS)
Protocol Extensions (No. RFC 6929).
Fournaris, A. P., & Keramidas, G. (2014). From hardware security tokens to trusted
computing and trusted systems. In System-Level Design Methodologies for
Telecommunication(pp. 99-117). Springer, Cham.
He, D., Zhao, W., & Wu, S. (2013). Security Analysis of a Dynamic ID-based
Authentication Scheme for Multi-server Environment Using Smart Cards. IJ
Network Security, 15(5), 350-356.
Krishna, P. V., Misra, S., Joshi, D., Gupta, A., & Obaidat, M. S. (2014). Secure
socket layer certificate verification: a learning automata approach. Security
and Communication Networks, 7(11), 1712-1718.
Lee, C. C., Liu, C. H., & Hwang, M. S. (2013). Guessing Attacks on Strong-Password
Authentication Protocol. IJ Network Security, 15(1), 64-67.
Page 6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION TECHNOLOGY
Lopez-Fernandez, L., Gallego, M., García, B., Fernández-López, D., & López, F. J.
(2014). Authentication, authorization, and accounting in webrtc paas
infrastructures: The case of kurento. IEEE Internet Computing, 18(6), 34-40.
Manjusha, R., & Ramachandran, R. (2015). Secure authentication and access
system for cloud computing auditing services using associated digital
certificate. Indian Journal of Science and Technology, 8, 220.
Marquet, B., Rossi, A., & Cosquer, F. J. (2013). SECURITY THROUGH
INTEGRATION. Certification and Security in E-Services: From E-Government
to E-Business, 127, 183.
Nobori, D., & Shinjo, Y. (2014, April). VPN Gate: A Volunteer-Organized Public VPN
Relay System with Blocking Resistance for Bypassing Government
Censorship Firewalls. In NSDI (pp. 229-241).
Percival, C., & Josefsson, S. (2016). The scrypt password-based key derivation
function (No. RFC 7914).
Rhodes-Ousley, M. (2013). Information security: the complete reference. McGraw Hill
Education.
Santesson, S., Myers, M., Ankney, R., Malpani, A., Galperin, S., & Adams, C.
(2013). X. 509 Internet public key infrastructure online certificate status
protocol-OCSP (No. RFC 6960).
Zhu, L., Hartman, S., Leach, P., & Emery, S. (2017). Anonymity support for Kerberos.
Page 7
Lopez-Fernandez, L., Gallego, M., García, B., Fernández-López, D., & López, F. J.
(2014). Authentication, authorization, and accounting in webrtc paas
infrastructures: The case of kurento. IEEE Internet Computing, 18(6), 34-40.
Manjusha, R., & Ramachandran, R. (2015). Secure authentication and access
system for cloud computing auditing services using associated digital
certificate. Indian Journal of Science and Technology, 8, 220.
Marquet, B., Rossi, A., & Cosquer, F. J. (2013). SECURITY THROUGH
INTEGRATION. Certification and Security in E-Services: From E-Government
to E-Business, 127, 183.
Nobori, D., & Shinjo, Y. (2014, April). VPN Gate: A Volunteer-Organized Public VPN
Relay System with Blocking Resistance for Bypassing Government
Censorship Firewalls. In NSDI (pp. 229-241).
Percival, C., & Josefsson, S. (2016). The scrypt password-based key derivation
function (No. RFC 7914).
Rhodes-Ousley, M. (2013). Information security: the complete reference. McGraw Hill
Education.
Santesson, S., Myers, M., Ankney, R., Malpani, A., Galperin, S., & Adams, C.
(2013). X. 509 Internet public key infrastructure online certificate status
protocol-OCSP (No. RFC 6960).
Zhu, L., Hartman, S., Leach, P., & Emery, S. (2017). Anonymity support for Kerberos.
Page 7
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




