ICTNWK509 - Design and Implementation of SolutionTech Network Security
VerifiedAdded on 2022/08/17
|12
|877
|15
Practical Assignment
AI Summary
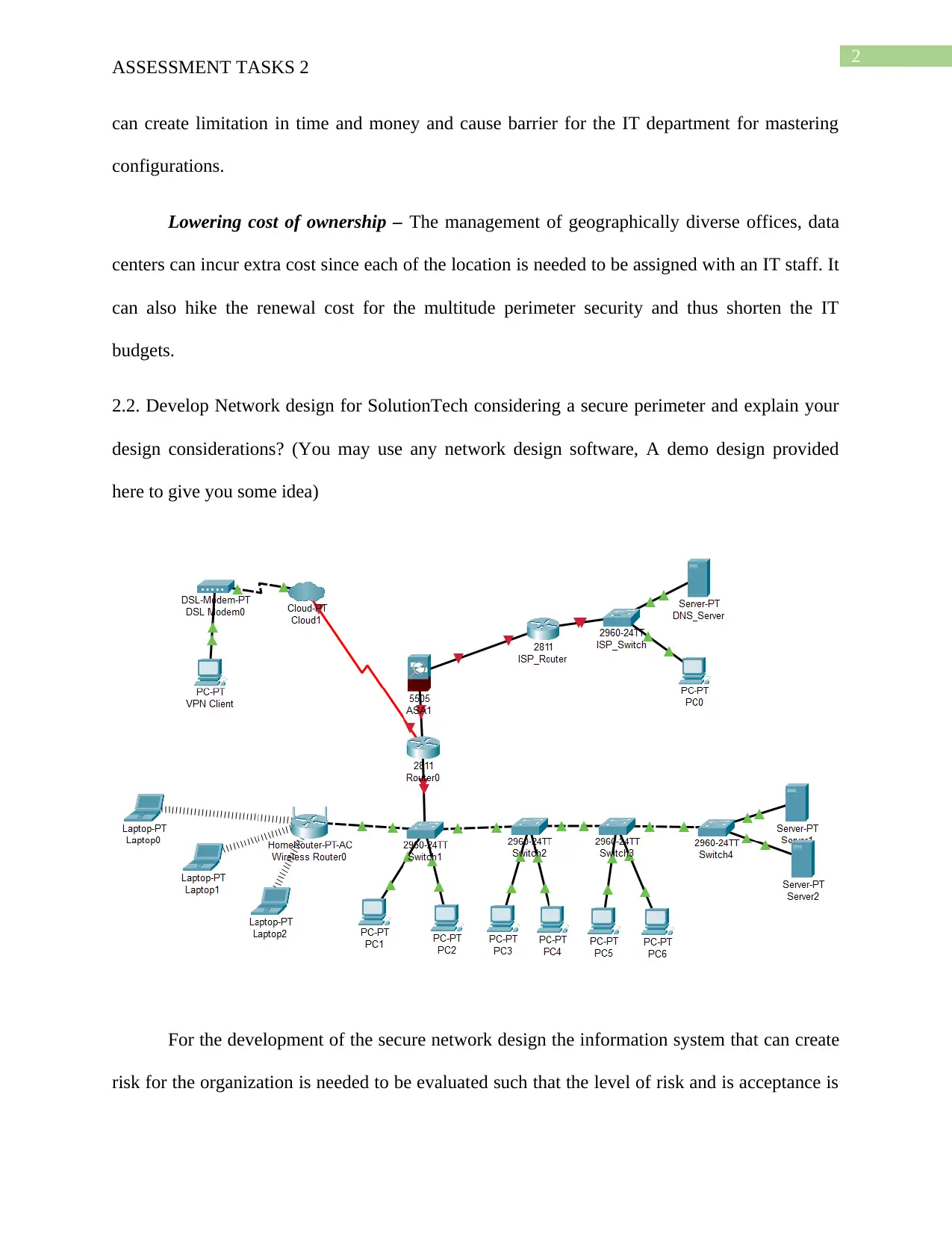
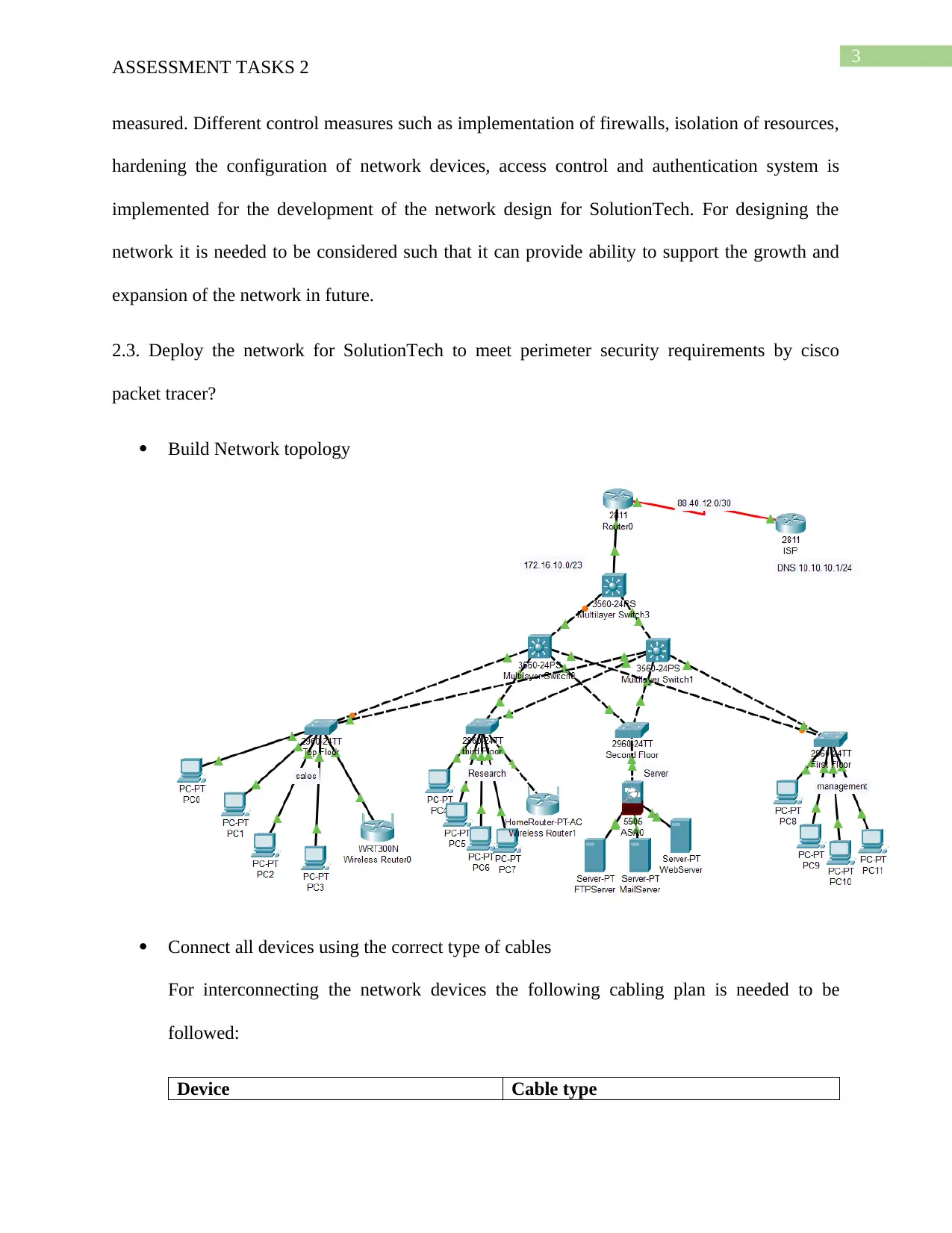
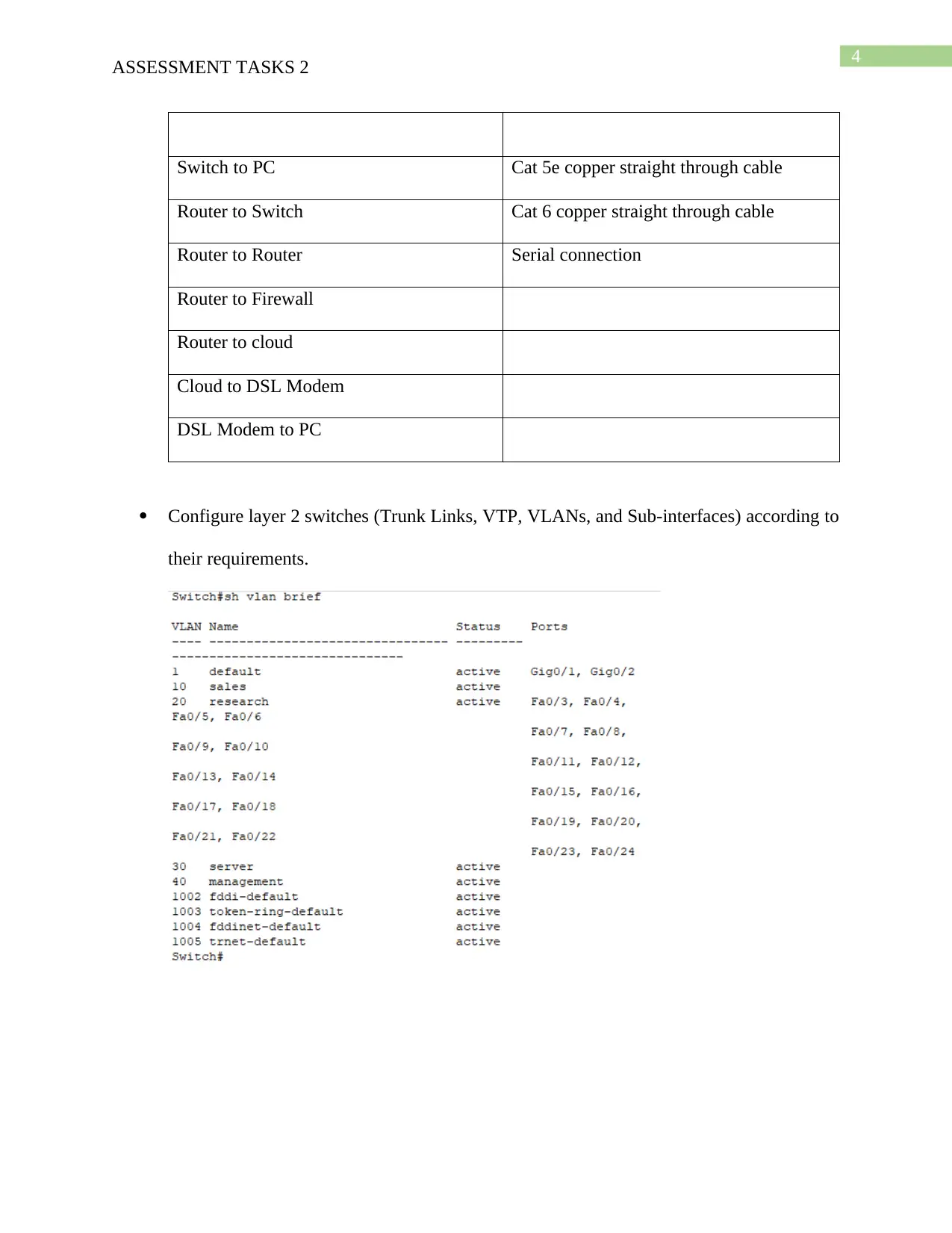
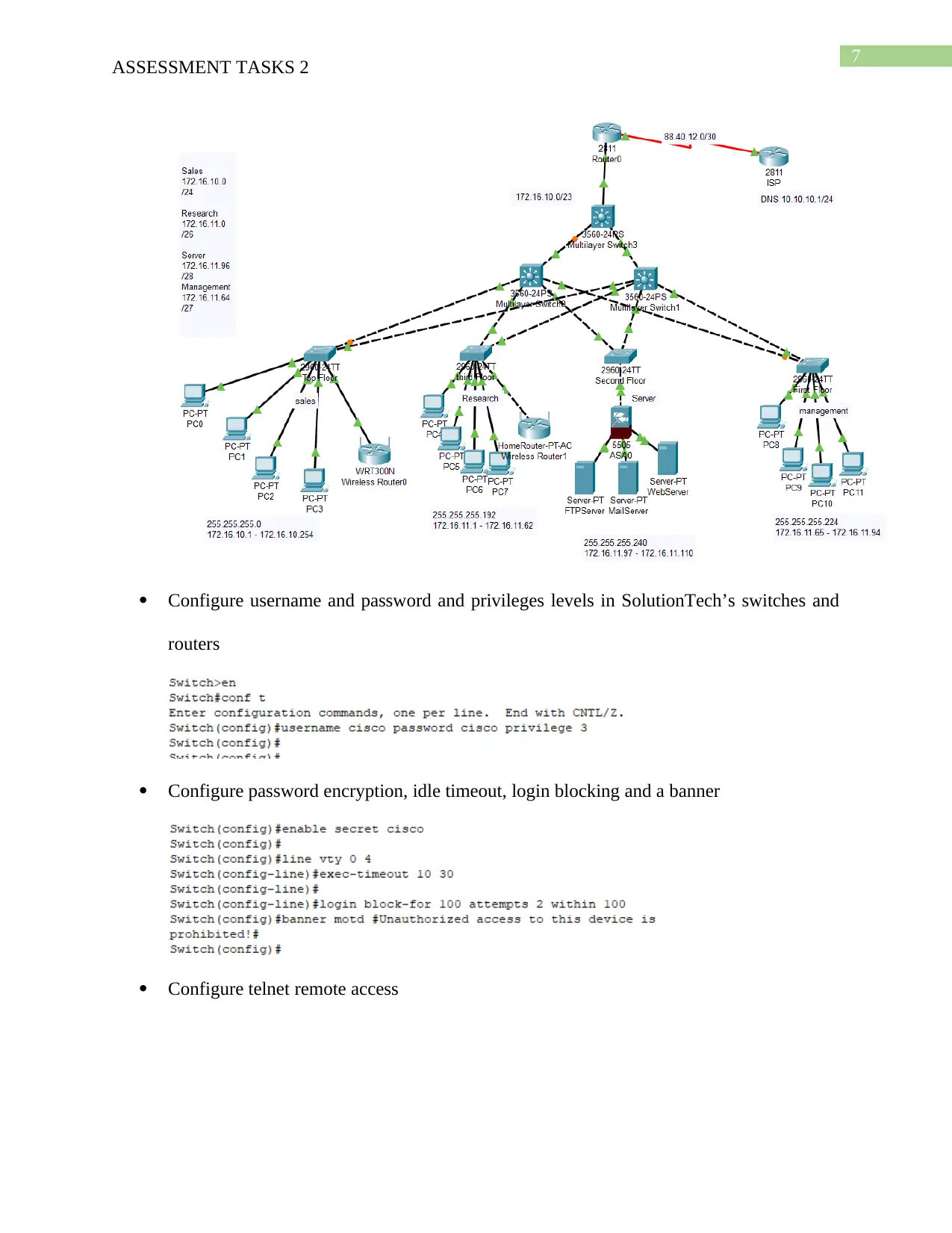
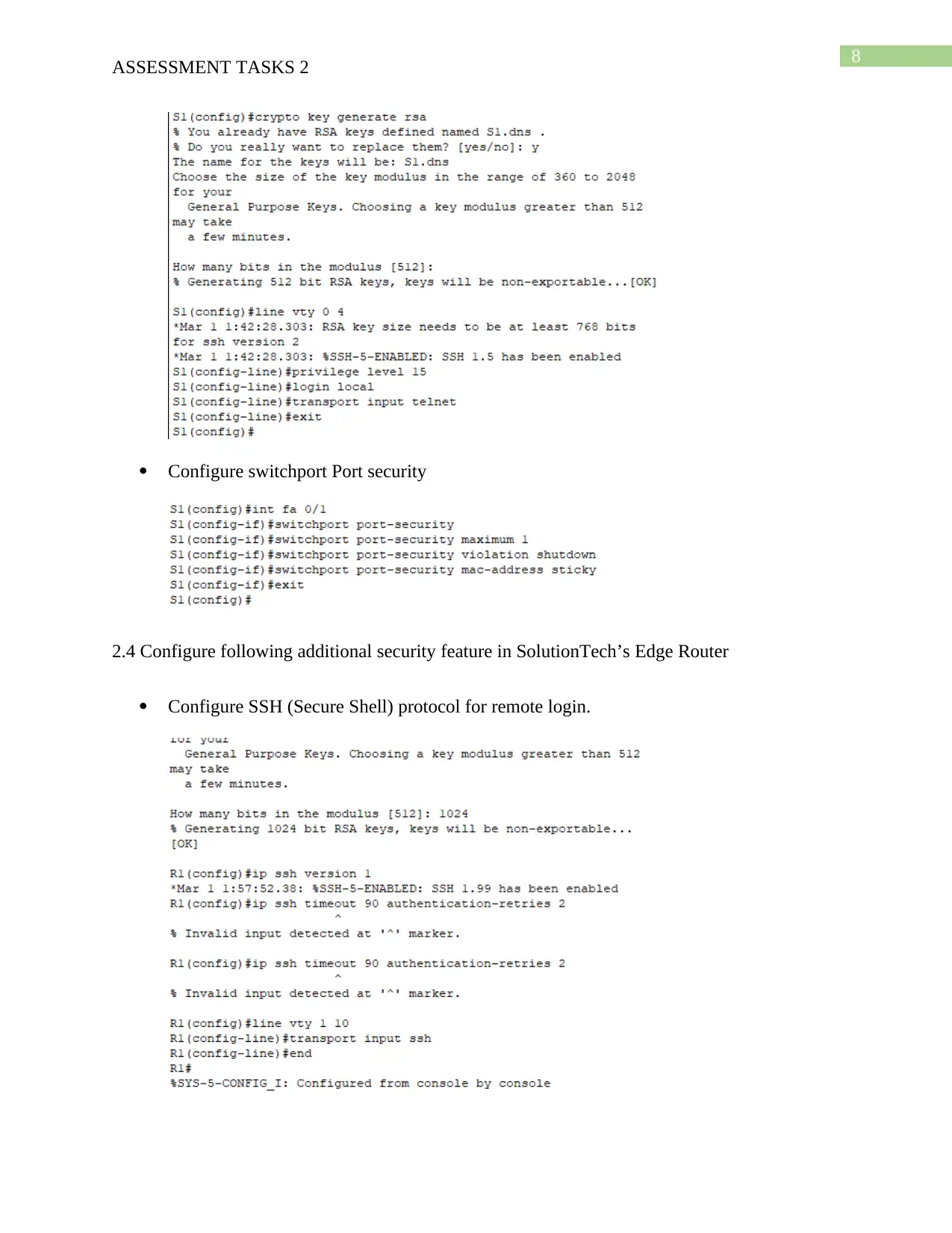
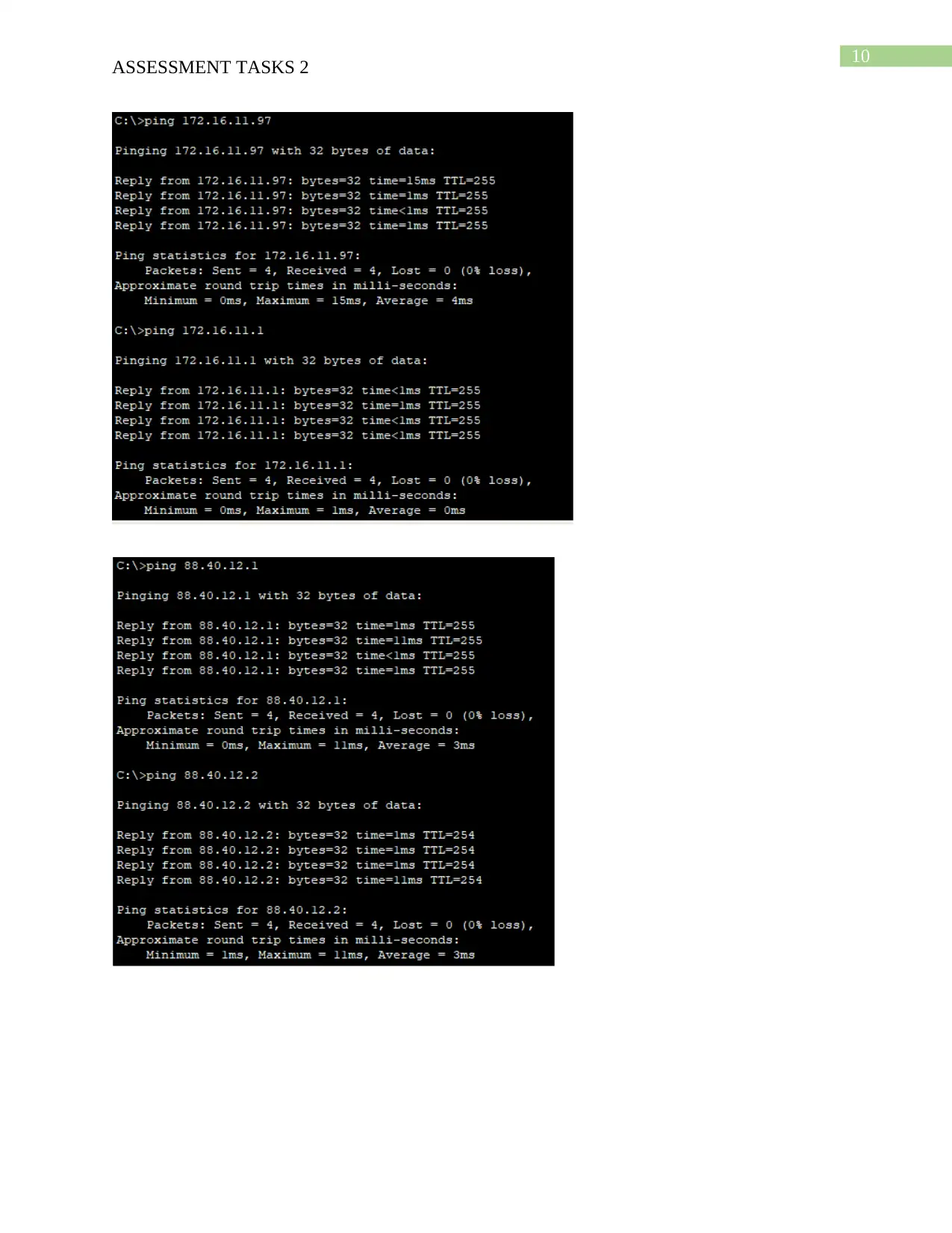
This assignment addresses the design and implementation of a secure network perimeter for SolutionTech, focusing on the ICTNWK509 module. The student identifies potential threats to SolutionTech's network security, such as hacking, malware, and misconfigurations. A network design is developed, considering future scalability and incorporating security measures like firewalls, access control, and authentication. The network is then deployed using Cisco Packet Tracer, including cabling, switch configurations (VLANs, VTP, trunk links), IP address allocation (static and DHCP), routing, and wireless access point setup. The configuration of username/password, encryption, remote access via Telnet, and port security are also covered. Furthermore, the solution includes configuring SSH for secure remote login and access control lists to restrict network access. Finally, a remote access VPN is configured to enable secure access to the SolutionTech network from external locations, with testing and screenshots provided for validation. The assignment is supported by a bibliography of relevant research papers.
1 out of 12













![[object Object]](/_next/static/media/star-bottom.7253800d.svg)