University Server Virtualization Implementation Assessment
VerifiedAdded on 2022/12/03
|23
|5038
|305
Homework Assignment
AI Summary
This document presents a comprehensive solution to an assignment focused on the implementation of server virtualization for an ICT system. The assignment covers a range of topics including the definition of key terms like business domain, business function, and organization, and explores the compatibility of guest operating systems with Microsoft Hyper-V. It delves into the configuration of IP-related parameters on a Windows server, lists industry-used server virtualization software, and examines the documentation of server information. The solution addresses project phases like planning, build, and manage processes, as well as the use of system diagnostic tools. It further discusses considerations for configuring power supplies, memory (RAM), and processors in server design, along with network architecture factors such as network cards (NICs) and bandwidth. The assignment also explains how to determine hardware compatibility for Hyper-V installations, describes the three types of virtual switches supported, and the purpose of check pointing in Hyper-V. This detailed solution provides valuable insights into server virtualization principles and practical implementation strategies.

IMPLEMENTATION OF SERVER VIRTUALIZATION
ASSESSMENT-1
IMPLEMENTATION OF SERVER VIRTUALIZATION FOR ICT SYSTEM
Name of the Student
Name of the University
Author Note
ASSESSMENT-1
IMPLEMENTATION OF SERVER VIRTUALIZATION FOR ICT SYSTEM
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IMPLEMENTATION OF SERVER VIRTUALIZATION
1. Briefly explain what is meant by the following terms:
Answer –Business Domain: In object-oriented programming, this can be stated as the
collection of classes which highlight the objects in the given business model for
implementation. Business domains are completely distinguishable from the business model
just because of their understanding. It comes up with an explanation for information and
behavior in the problem domain. It is generally implemented for the given model in the
specific program.
Business Function: It can be defined as a set of activities that are being performed by the
department, which is initiated by a set of activities carried out by various department. This
is merely initiated by an event, materials and procedure encountered at the output. This
merely comprises of cash management, tracking customer response.
Organization: This can be stated as an entity which comprises of various people like
association and institution. It merely comes up with goals that are completely linked to
external environment. It comes up legal kind of organization like government, political,
armed, political organization, armed forces, partnership, co-operative and educational
institutes.
2. Summaries how I determine if a guest operating system, say Windows 2008 Server is
compatible with Microsoft Hyper V. If an operating system is not compatible with Microsoft
Hyper V, what, if anything, can I do to resolve the situation?
Answer – Hyper-V aims to provide support to various version of windows and Linux
distribution for running on virtual machine like guest operating system. In this, some of the
operating systems comes up with inbuilt features. There are many others which require to
install and upgrade the integration services. This is considered an operating system provided
1. Briefly explain what is meant by the following terms:
Answer –Business Domain: In object-oriented programming, this can be stated as the
collection of classes which highlight the objects in the given business model for
implementation. Business domains are completely distinguishable from the business model
just because of their understanding. It comes up with an explanation for information and
behavior in the problem domain. It is generally implemented for the given model in the
specific program.
Business Function: It can be defined as a set of activities that are being performed by the
department, which is initiated by a set of activities carried out by various department. This
is merely initiated by an event, materials and procedure encountered at the output. This
merely comprises of cash management, tracking customer response.
Organization: This can be stated as an entity which comprises of various people like
association and institution. It merely comes up with goals that are completely linked to
external environment. It comes up legal kind of organization like government, political,
armed, political organization, armed forces, partnership, co-operative and educational
institutes.
2. Summaries how I determine if a guest operating system, say Windows 2008 Server is
compatible with Microsoft Hyper V. If an operating system is not compatible with Microsoft
Hyper V, what, if anything, can I do to resolve the situation?
Answer – Hyper-V aims to provide support to various version of windows and Linux
distribution for running on virtual machine like guest operating system. In this, some of the
operating systems comes up with inbuilt features. There are many others which require to
install and upgrade the integration services. This is considered an operating system provided

IMPLEMENTATION OF SERVER VIRTUALIZATION
in the virtual machine. This particular issue can be resolved by installation of host computer
where Hyper-V virtual machines are located. User can have this from the Microsoft Download
center.
3.Describe how I would configure the following IP-related parameters on a Windows server:
IP address, subnet mask, and default gateway.
Answer-
User needs to login on the windows server and analyze the network internet access icon.
User needs to click on it for open and sharing network.
After that, click on adapter settings.
Click on the Ethernet and go to the setting of properties. User needs to select internet
version 4, followed by clicking on properties.
User needs to enter the IP address, gateway and subnet mask.
User needs to click ok and close to the save option.
2. List two software products that are currently used in industry to provide server
virtualization.
Answer-
VMWare ESX.
XenConvert.
Microsoft Hyper-V
in the virtual machine. This particular issue can be resolved by installation of host computer
where Hyper-V virtual machines are located. User can have this from the Microsoft Download
center.
3.Describe how I would configure the following IP-related parameters on a Windows server:
IP address, subnet mask, and default gateway.
Answer-
User needs to login on the windows server and analyze the network internet access icon.
User needs to click on it for open and sharing network.
After that, click on adapter settings.
Click on the Ethernet and go to the setting of properties. User needs to select internet
version 4, followed by clicking on properties.
User needs to enter the IP address, gateway and subnet mask.
User needs to click ok and close to the save option.
2. List two software products that are currently used in industry to provide server
virtualization.
Answer-
VMWare ESX.
XenConvert.
Microsoft Hyper-V
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IMPLEMENTATION OF SERVER VIRTUALIZATION
5. Give two examples of information about a server running virtualization software you would
document as part of a technical specification for that server. For each example of information,
describe how you would gather the information.
Answer- VMware Vcentre: Vcenter server comes up with a data management server based
application completely developed by VMware Inc. It is mainly needed for monitoring in the
virtual environment. VCentre server aims to provide centralized operation and management
along with these performance evaluation of virtual machine. This merely tends to reside on the
distributed data centres. VCentre server of VMware has been mainly designed for VSphere.
VMware platform is needed for building the virtualized cloud environment. Earlier VMware
centre was known as VMware Virtual centre. VMware aims to provide a collection of reports
that are completely based on API. It is merely needed for making custom arrangement so that
data can be accumulated for virtualization. This is needed by system programs and associated
physical server.
6. In a project implementing a virtualization solution, it is typical to have a planning process, a
build process and a manage process. Give an example of how the outputs from one phase in
the project, such as the planning process, can become an input into the next phase of the
project, such as the build process.
Answer- In actual arrangement of virtualization, output of one given stage is put into the
other. All the required components are needed to be introduced for the building process.
This is mainly caught on the arrangement of any given component and programs as per
the necessity.
7. List two system diagnostic tools I could use to gather information about servers that I
5. Give two examples of information about a server running virtualization software you would
document as part of a technical specification for that server. For each example of information,
describe how you would gather the information.
Answer- VMware Vcentre: Vcenter server comes up with a data management server based
application completely developed by VMware Inc. It is mainly needed for monitoring in the
virtual environment. VCentre server aims to provide centralized operation and management
along with these performance evaluation of virtual machine. This merely tends to reside on the
distributed data centres. VCentre server of VMware has been mainly designed for VSphere.
VMware platform is needed for building the virtualized cloud environment. Earlier VMware
centre was known as VMware Virtual centre. VMware aims to provide a collection of reports
that are completely based on API. It is merely needed for making custom arrangement so that
data can be accumulated for virtualization. This is needed by system programs and associated
physical server.
6. In a project implementing a virtualization solution, it is typical to have a planning process, a
build process and a manage process. Give an example of how the outputs from one phase in
the project, such as the planning process, can become an input into the next phase of the
project, such as the build process.
Answer- In actual arrangement of virtualization, output of one given stage is put into the
other. All the required components are needed to be introduced for the building process.
This is mainly caught on the arrangement of any given component and programs as per
the necessity.
7. List two system diagnostic tools I could use to gather information about servers that I
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IMPLEMENTATION OF SERVER VIRTUALIZATION
am considering for virtualization. Briefly describe how I would use the tools.
Answer- RV Tools: It is known to be VMware utility that makes use of VISDK for
getting all the required information about the virtual environment. It mainly aims to
establish connection of vCenter server for collecting all the required information. This
is merely a tool which has been developed Rob de Veij which works well for both
VMware sphere and V13 computing. PowerShell: Microsoft has designed this so that
they can automate every task like batch processing. It is needed for building system
management tools which are seen in the implemented process. It can be considered to
be similar to Perl. It is completely built on the .NET framework, which is needed for
offering automated task.
With cmdlets, it can be considered to be much similar like .NET classes which
appear like system commands.
8.When I am planning my server design for virtualization, briefly summaries the
considerations that would apply to configuring power supplies and power management on
a server running virtualization software.
Answer- The quantity of power and cooling which is required for the information center can be
decreased up to a certain level by implementation of server union. The basic things like control
settings, some of which can be said as show, framework rest settings can result in controlling of
reserve funds. By this the needs of the controls can be diminished. The ancient upgrading
equipment helps to accomplish the excess decrease. For reducing the value of power and cooling
of information centre, server union is required. Control server funds will result in some basic
am considering for virtualization. Briefly describe how I would use the tools.
Answer- RV Tools: It is known to be VMware utility that makes use of VISDK for
getting all the required information about the virtual environment. It mainly aims to
establish connection of vCenter server for collecting all the required information. This
is merely a tool which has been developed Rob de Veij which works well for both
VMware sphere and V13 computing. PowerShell: Microsoft has designed this so that
they can automate every task like batch processing. It is needed for building system
management tools which are seen in the implemented process. It can be considered to
be similar to Perl. It is completely built on the .NET framework, which is needed for
offering automated task.
With cmdlets, it can be considered to be much similar like .NET classes which
appear like system commands.
8.When I am planning my server design for virtualization, briefly summaries the
considerations that would apply to configuring power supplies and power management on
a server running virtualization software.
Answer- The quantity of power and cooling which is required for the information center can be
decreased up to a certain level by implementation of server union. The basic things like control
settings, some of which can be said as show, framework rest settings can result in controlling of
reserve funds. By this the needs of the controls can be diminished. The ancient upgrading
equipment helps to accomplish the excess decrease. For reducing the value of power and cooling
of information centre, server union is required. Control server funds will result in some basic

IMPLEMENTATION OF SERVER VIRTUALIZATION
things like control setting like show framework in the whole organization for reducing the needs.
Any kind of extra decrease can come into picture by upgradation of ancient equipment’s.
9.When I am planning my server design for virtualization, briefly describe at least two
factors that determine how much memory (RAM) is needed on a server running
virtualization software, such as Microsoft Hyper-V.
Answer-
RAM which is required for the server system is generally more than the RAM used
in personal computer. This factor depends upon the application, usage and
configuration of the server. It is more appreciable to plan before setting a server
system so that the system can have the option of up gradation in future. The
limitation of physical memory or RAM in the server should also be considered
before implementation.
This factor is also dependent on the number of systems connected to the server.
The minimum requirement of RAM in a system is 4GB and it can be upgraded in
future.
10.When I am planning my server design for virtualization, briefly describe at least two
factors that determine how many processors are needed on a server running virtualization
software, such as Microsoft Hyper-V.
Answer- Hyper V is only compatible with 64-bit hardware processors. The other two elements
which are required by the Hyper-V other than the hardware processors are as follows
Hardware-assisted virtualization: An additional privilege mode in Hardware assisted
virtualization which is above Ring-0 (also known as Ring-1) is supported by the processors.
things like control setting like show framework in the whole organization for reducing the needs.
Any kind of extra decrease can come into picture by upgradation of ancient equipment’s.
9.When I am planning my server design for virtualization, briefly describe at least two
factors that determine how much memory (RAM) is needed on a server running
virtualization software, such as Microsoft Hyper-V.
Answer-
RAM which is required for the server system is generally more than the RAM used
in personal computer. This factor depends upon the application, usage and
configuration of the server. It is more appreciable to plan before setting a server
system so that the system can have the option of up gradation in future. The
limitation of physical memory or RAM in the server should also be considered
before implementation.
This factor is also dependent on the number of systems connected to the server.
The minimum requirement of RAM in a system is 4GB and it can be upgraded in
future.
10.When I am planning my server design for virtualization, briefly describe at least two
factors that determine how many processors are needed on a server running virtualization
software, such as Microsoft Hyper-V.
Answer- Hyper V is only compatible with 64-bit hardware processors. The other two elements
which are required by the Hyper-V other than the hardware processors are as follows
Hardware-assisted virtualization: An additional privilege mode in Hardware assisted
virtualization which is above Ring-0 (also known as Ring-1) is supported by the processors.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IMPLEMENTATION OF SERVER VIRTUALIZATION
Hyper-V can operate by leaving the Ring-0 for running the guest operating system. There are
specific names for each processor and the names are marked on each and every hardware-
assisted virtualization platform of the processors. The term used for the processors of Intel and
AMD are VT and AMD-V respectively.
Hardware-based Data Execution Prevention: Data Executive Prevention is the second
requirement of Hyper-V. The Hardware-based Data Execution Prevention helps to mark the
required sections as non-executable. This feature is exclusively available for Intel XD and AMD
NX processors.
The user can run 3 or 4 basic virtual machines on the system of host that has a minimum RAM of
4GB. Although the criteria to virtualize a machine depends on the resources. Large virtual
machines which have 512 MB RAM and 32 Bit hardware can also be created by using same
hardware.
11.When I am planning my network architecture for virtualization, briefly describe at least
two factors that determine how many network cards (NICs) and what bandwidth are
needed on a server running virtualization software, such as Microsoft Hyper-V.
Answer-The ideal networking system for Hyper-V have same kind of recommendations for the
storage. Multiple NICs are made available for the Hyper V-Host.
In this case an example can be seen in which a server named HY-SVR-001 has one NIC card
having a speed of 1Gbps installed in the system. After the installation, NIC can be selected for
creating an external virtual network by the manager of network system.
More bandwidth and better networking plan helps to increase the number of virtual
machines. The administrator of the system found out that the main reason for increase in number
Hyper-V can operate by leaving the Ring-0 for running the guest operating system. There are
specific names for each processor and the names are marked on each and every hardware-
assisted virtualization platform of the processors. The term used for the processors of Intel and
AMD are VT and AMD-V respectively.
Hardware-based Data Execution Prevention: Data Executive Prevention is the second
requirement of Hyper-V. The Hardware-based Data Execution Prevention helps to mark the
required sections as non-executable. This feature is exclusively available for Intel XD and AMD
NX processors.
The user can run 3 or 4 basic virtual machines on the system of host that has a minimum RAM of
4GB. Although the criteria to virtualize a machine depends on the resources. Large virtual
machines which have 512 MB RAM and 32 Bit hardware can also be created by using same
hardware.
11.When I am planning my network architecture for virtualization, briefly describe at least
two factors that determine how many network cards (NICs) and what bandwidth are
needed on a server running virtualization software, such as Microsoft Hyper-V.
Answer-The ideal networking system for Hyper-V have same kind of recommendations for the
storage. Multiple NICs are made available for the Hyper V-Host.
In this case an example can be seen in which a server named HY-SVR-001 has one NIC card
having a speed of 1Gbps installed in the system. After the installation, NIC can be selected for
creating an external virtual network by the manager of network system.
More bandwidth and better networking plan helps to increase the number of virtual
machines. The administrator of the system found out that the main reason for increase in number
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IMPLEMENTATION OF SERVER VIRTUALIZATION
of virtual machines is the usage of NIC. The backup of all virtual machine servers is configured
according to the same physical NIC.
Bandwidth is the term to measure the rate of data and the traffic flowing through a
channel between the user and the sites through internet. The general meaning of bandwidth can
be said as the data transfer but in reality these two things are different.
The amount of bandwidth offered by the various company sites can be identified as a
good indication of the host capacity by the site owners. The generalized term which can be said
for this case is greater the bandwidth is the higher will be the internet speed and connectivity.
12.When setting up and installing Microsoft Hyper V, how do I determine what server
hardware is compatible with the software I want to install, i.e. what vendor resource would
I consult to answer this question?
Answer- The necessary items for the Hyper-V compatible hardware are as follows
Combination of 64-bit hardware processor and the Second Level Address Translation
(SLAT)
VM Monitor Mode Extension supported by the CPU (The VT used in the CPU of Intel)
A least memory of 4 GB. This memory is required by the Hyper-V host for providing
maximum amount of memory which is essential for managing the virtual workload.
The items which are required to enable the BIOS system are
Virtualization Technology having various other levels which is dependent upon the
manufacturer of motherboard.
Hardware Enforced Data Execution Prevention
The steps for verifying compatibility of hardware includes the process of opening
of virtual machines is the usage of NIC. The backup of all virtual machine servers is configured
according to the same physical NIC.
Bandwidth is the term to measure the rate of data and the traffic flowing through a
channel between the user and the sites through internet. The general meaning of bandwidth can
be said as the data transfer but in reality these two things are different.
The amount of bandwidth offered by the various company sites can be identified as a
good indication of the host capacity by the site owners. The generalized term which can be said
for this case is greater the bandwidth is the higher will be the internet speed and connectivity.
12.When setting up and installing Microsoft Hyper V, how do I determine what server
hardware is compatible with the software I want to install, i.e. what vendor resource would
I consult to answer this question?
Answer- The necessary items for the Hyper-V compatible hardware are as follows
Combination of 64-bit hardware processor and the Second Level Address Translation
(SLAT)
VM Monitor Mode Extension supported by the CPU (The VT used in the CPU of Intel)
A least memory of 4 GB. This memory is required by the Hyper-V host for providing
maximum amount of memory which is essential for managing the virtual workload.
The items which are required to enable the BIOS system are
Virtualization Technology having various other levels which is dependent upon the
manufacturer of motherboard.
Hardware Enforced Data Execution Prevention
The steps for verifying compatibility of hardware includes the process of opening

IMPLEMENTATION OF SERVER VIRTUALIZATION
a Command prompt or a Power Shell and then typing the system information. After
this step if the Hyper-V requirement value shows ‘Yes’ then the computer can run
Hyper V-role but if it shows ‘No’ then the requirements should be checked and
adjustment should be made to make the system compatible.
13. Briefly describe the three types of virtual switches supported in Microsoft Hyper V.
Answer- The three switches supported in the Microsoft Hyper V are
Internal Switch: This switch is not usually supposed to be bound to any sort of
physical network card, this tends to allow the traffic among the host and the VM
External Switch: This switch is usually supposed to be bound to cards of physical
network, this cards are situated within the host. They have the ability to share the
management traffic along with the VM traffic in the same switch.
Private Switch: This sort of switches is supposed to be utilized for numerous virtual
machines in order to maintain a communication channel between each other. It could
be used for certain types like cluster networks.
14. Briefly describe the purpose of check pointing in Microsoft Hyper V.
Answer-
One of the benefits that are provided by the virtualization include the ability of saving the present
state of a specific VM. IN caser of Hyper-V this could be carried out with the usage of virtual
machine checkpoints. The user might require creating a virtual machine checkpoint initially in
order to make changes the software configuration, applying a certain update in the software,
installation of a new software and many more
Standard Checkpoints: It takes a snapshot of provided virtual machine along with the memory
state of the virtual machine when the checkpoints are initiated. Snapshots cannot be defined as a
a Command prompt or a Power Shell and then typing the system information. After
this step if the Hyper-V requirement value shows ‘Yes’ then the computer can run
Hyper V-role but if it shows ‘No’ then the requirements should be checked and
adjustment should be made to make the system compatible.
13. Briefly describe the three types of virtual switches supported in Microsoft Hyper V.
Answer- The three switches supported in the Microsoft Hyper V are
Internal Switch: This switch is not usually supposed to be bound to any sort of
physical network card, this tends to allow the traffic among the host and the VM
External Switch: This switch is usually supposed to be bound to cards of physical
network, this cards are situated within the host. They have the ability to share the
management traffic along with the VM traffic in the same switch.
Private Switch: This sort of switches is supposed to be utilized for numerous virtual
machines in order to maintain a communication channel between each other. It could
be used for certain types like cluster networks.
14. Briefly describe the purpose of check pointing in Microsoft Hyper V.
Answer-
One of the benefits that are provided by the virtualization include the ability of saving the present
state of a specific VM. IN caser of Hyper-V this could be carried out with the usage of virtual
machine checkpoints. The user might require creating a virtual machine checkpoint initially in
order to make changes the software configuration, applying a certain update in the software,
installation of a new software and many more
Standard Checkpoints: It takes a snapshot of provided virtual machine along with the memory
state of the virtual machine when the checkpoints are initiated. Snapshots cannot be defined as a
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IMPLEMENTATION OF SERVER VIRTUALIZATION
complete backup; it has the chances to cause issues regarding data consistency with the systems
which are responsible for replicating information among numerous nodes
Production Checkpoints: These checkpoints male use of Volume Shadow Copy Service along
with File System Freeze in a particular Linux Virtual Machine, this is done for the purpose of
creating data consistent backup on the VM. Snapshot of memory state of the VM is also
recorded. This checkpoint is usually chosen by default whereas it could be changed with the use
of PowerShell or Hyper-V manager.
15.Briefly describe the following features as they apply to server CPUs.
Answer-
The features in single processor are
Sharing of same type of resources
Complex power management
High speed data transmission between the cores due to the presence of short
buses
Compressed in term of space occupied
Non redundant system
The features in multi-processor are
Loss of speed during the transmission of data between the processors due to
uni directional system
Presence of dedicated resources in every core of the processor.
Not compressed thus takes a lot of space
Redundancy in the system which helps various processors to work
simultaneously.
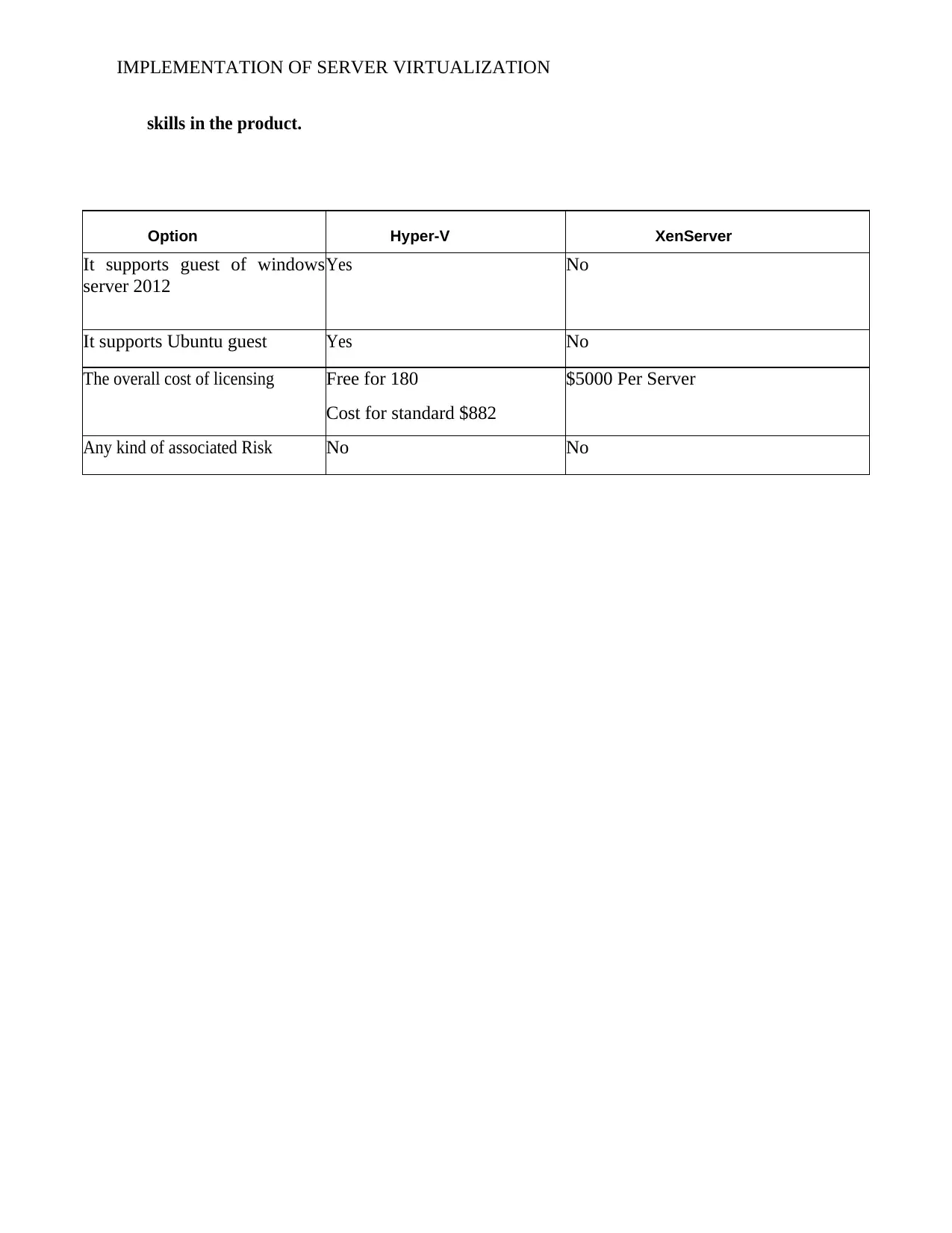
16. You have been asked to research and analyses alternative virtualizations scenarios for
a company called DEF Corporation. The company wants to virtualize its existing servers,
which are currently running operating systems such as Windows 2012 and Ubuntu Linux.
Complete the table below for comparing the virtualization alternatives of Microsoft Hyper-
V with Citrix XenServer 6.2. You should also note any risks associated with running either
of the alternative virtualization solutions, such as support arrangements, and finding
complete backup; it has the chances to cause issues regarding data consistency with the systems
which are responsible for replicating information among numerous nodes
Production Checkpoints: These checkpoints male use of Volume Shadow Copy Service along
with File System Freeze in a particular Linux Virtual Machine, this is done for the purpose of
creating data consistent backup on the VM. Snapshot of memory state of the VM is also
recorded. This checkpoint is usually chosen by default whereas it could be changed with the use
of PowerShell or Hyper-V manager.
15.Briefly describe the following features as they apply to server CPUs.
Answer-
The features in single processor are
Sharing of same type of resources
Complex power management
High speed data transmission between the cores due to the presence of short
buses
Compressed in term of space occupied
Non redundant system
The features in multi-processor are
Loss of speed during the transmission of data between the processors due to
uni directional system
Presence of dedicated resources in every core of the processor.
Not compressed thus takes a lot of space
Redundancy in the system which helps various processors to work
simultaneously.
16. You have been asked to research and analyses alternative virtualizations scenarios for
a company called DEF Corporation. The company wants to virtualize its existing servers,
which are currently running operating systems such as Windows 2012 and Ubuntu Linux.
Complete the table below for comparing the virtualization alternatives of Microsoft Hyper-
V with Citrix XenServer 6.2. You should also note any risks associated with running either
of the alternative virtualization solutions, such as support arrangements, and finding
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IMPLEMENTATION OF SERVER VIRTUALIZATION
skills in the product.
Option Hyper-V XenServer
It supports guest of windows
server 2012
Yes No
It supports Ubuntu guest Yes No
The overall cost of licensing Free for 180
Cost for standard $882
$5000 Per Server
Any kind of associated Risk No No
skills in the product.
Option Hyper-V XenServer
It supports guest of windows
server 2012
Yes No
It supports Ubuntu guest Yes No
The overall cost of licensing Free for 180
Cost for standard $882
$5000 Per Server
Any kind of associated Risk No No

Running head: IMPLEMENTATION OF SERVER VIRTUALIZATION
ASSESSMENT-2
IMPLEMENTATION OF SERVER VIRTUALIZATION FOR ICT SYSTEM
Name of the Student
Name of the University
Author Note
ASSESSMENT-2
IMPLEMENTATION OF SERVER VIRTUALIZATION FOR ICT SYSTEM
Name of the Student
Name of the University
Author Note
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





