IFN511 Security Management - Semester 1 2019: BYOD Risk Report ABC
VerifiedAdded on 2023/01/19
|5
|948
|84
Report
AI Summary
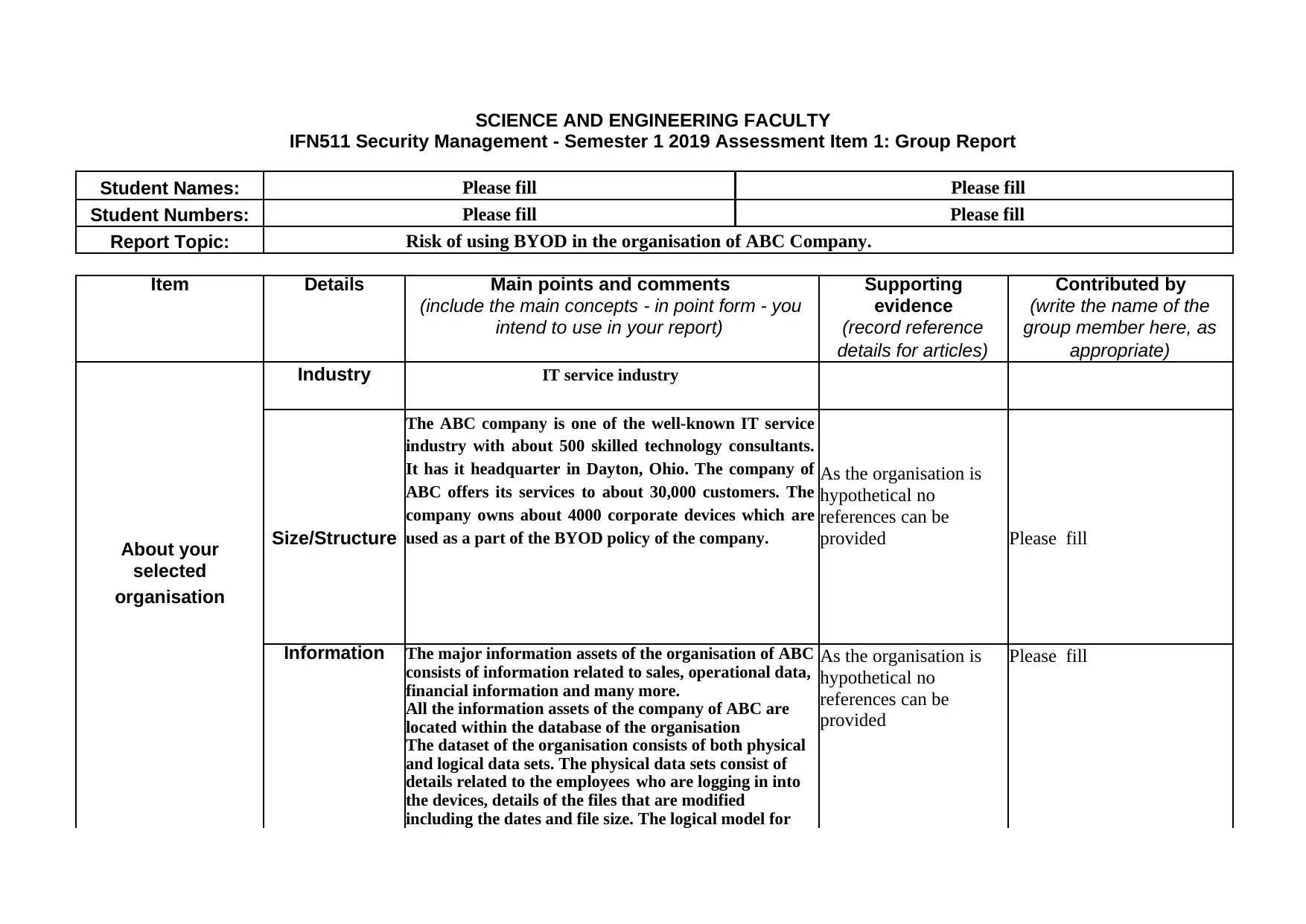
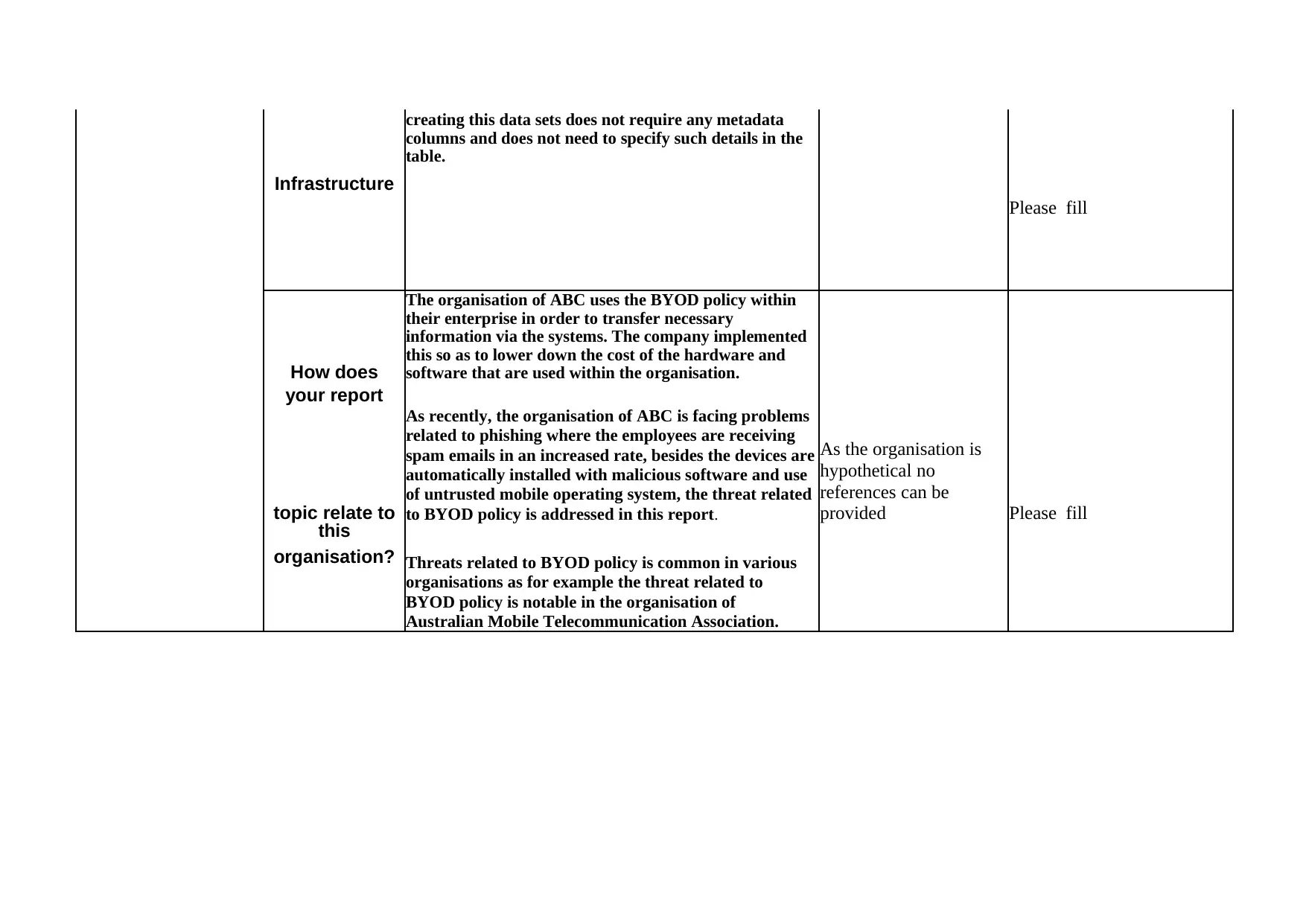
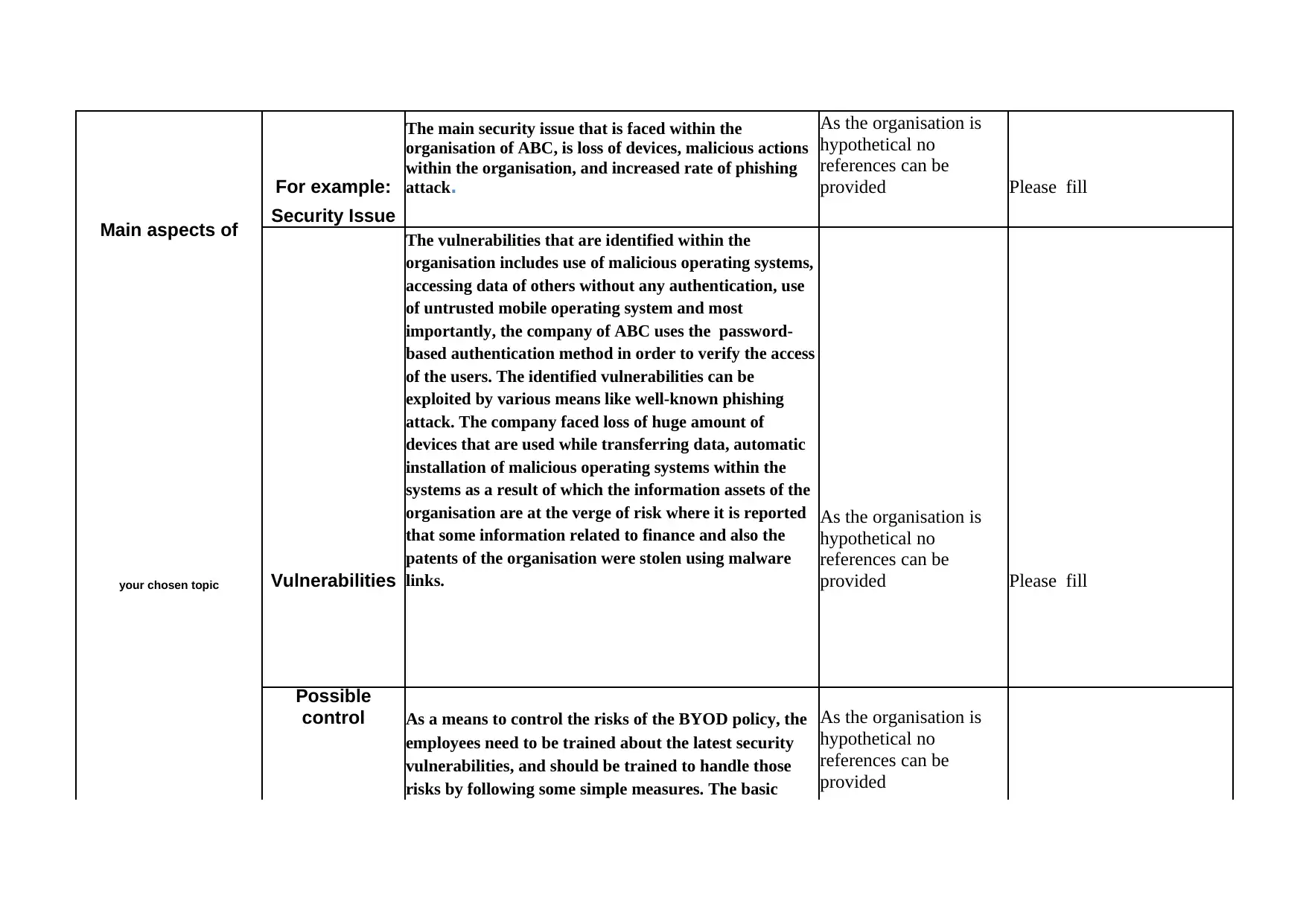
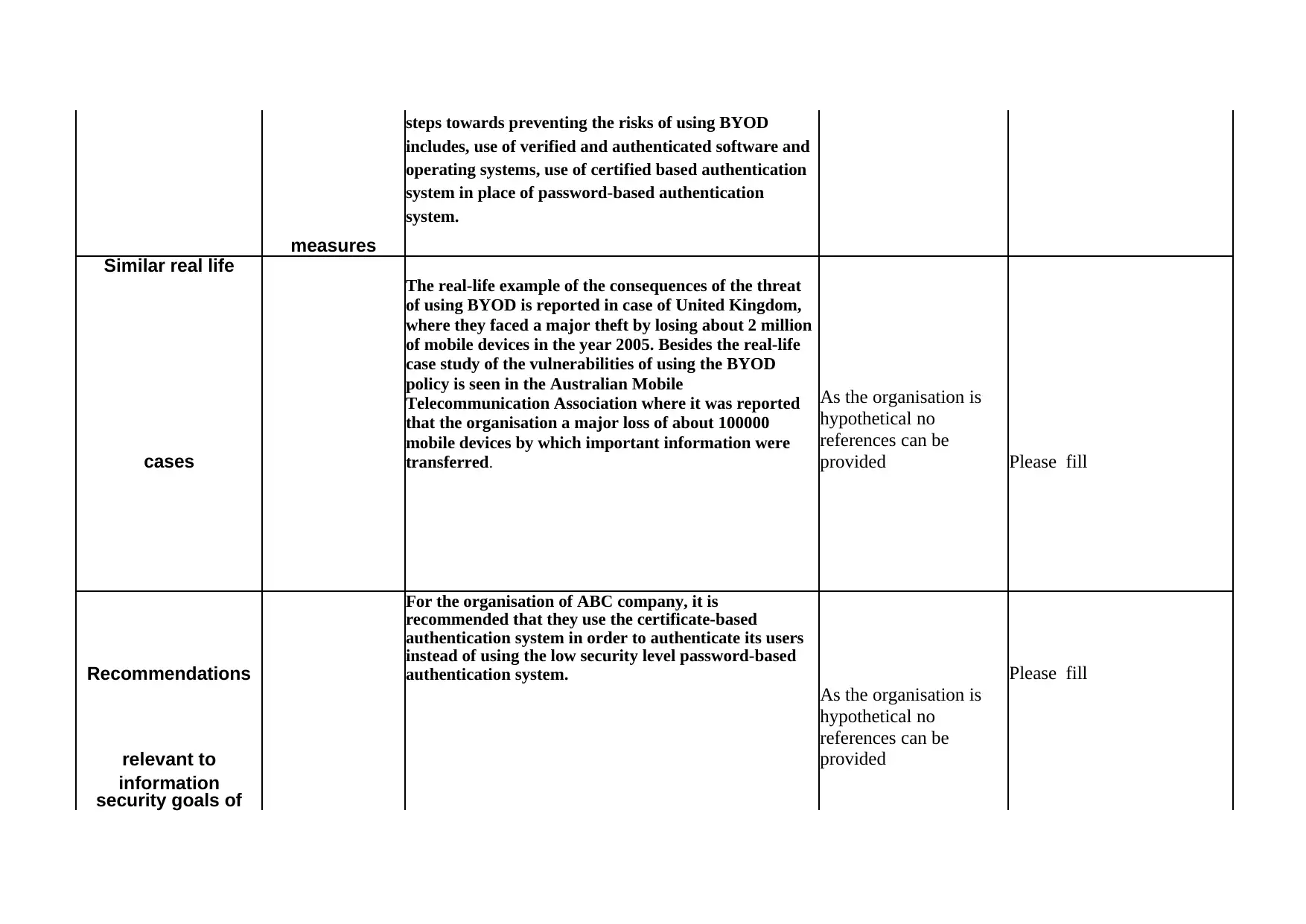
This report, prepared for the IFN511 Security Management course, examines the risks associated with the Bring Your Own Device (BYOD) policy implemented by the ABC Company, an IT service provider. The report identifies the company's industry, size, and information assets, highlighting the significance of information security. It details the infrastructure and the specific threats related to BYOD, such as loss of devices, malicious actions, and phishing attacks. The vulnerabilities are discussed, including the use of malicious and untrusted operating systems, and the password-based authentication method. To mitigate these risks, the report recommends training employees on security vulnerabilities, implementing verified software, and adopting certificate-based authentication. The report references real-life cases of security breaches and provides recommendations tailored to the ABC Company to enhance its security posture. This report is a comprehensive analysis of BYOD security risks, providing insights into vulnerabilities, threats, and mitigation strategies.
1 out of 5







![[object Object]](/_next/static/media/star-bottom.7253800d.svg)