IFSM 370 - Telecommunication and Information Security Final Assessment
VerifiedAdded on 2022/08/18
|15
|3211
|14
Homework Assignment
AI Summary
This assignment delves into the core concepts of telecommunication and information security, covering a range of topics essential for understanding modern network infrastructure and security. The student begins by differentiating between various network devices: hubs, bridges, switches, routers, and firewalls, detailing their functions, applications, and positions within the OSI model. The assignment then explores Virtual Private Networks (VPNs), distinguishing between hardware and software VPNs, explaining their functionalities and applications, and discussing their advantages and disadvantages. Further, the paper describes four wireless technologies/standards, including 802.11a, 802.11b, 802.15.1, and 802.16, detailing their operational mechanisms, differences, and use cases. The assignment also examines cloud computing, defining it and exploring the three cloud computing models (SaaS, PaaS, and IaaS), along with their respective utilization scenarios. Finally, the assignment provides a comprehensive overview of the Internet of Things (IoT), addressing its definition, associated issues, and the potential impact on the internet. Each question is supported by a minimum of two references in APA format.

Running head: TELECOMMUNICATION AND INFORMATION SECURITY
TELECOMMUNICATION AND INFORMATION SECURITY
Name of the Student:
Name of the University:
Author’s Note:
TELECOMMUNICATION AND INFORMATION SECURITY
Name of the Student:
Name of the University:
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1TELECOMMUNICATION AND INFORMATION SECURITY
Question 1:-
Explain the differences between the following network devices: hub, bridge, switch, router, and a
firewall. Where would you utilize each device and why? Where does each device reside within
the OSI model?
Answer:-
Hub:-
It is mainly a multiport repeater. This links with several wires coming from several
branches. Hubs cannot filter information, so data packets are directing to all attached devices
(Gil et al., 2014). They do not have the logical expression to search the most exceptional
technique for data packets which leads to ineffectiveness and excess.
Bridge:-
It mainly works at the data link layer. It is also a repeater. A bridge is the layer-2 devices,
working on the frames. The bridge is also applying for interrelating two LANs working on the
equivalent protocol. It has a particular input and distinct output port, thus constructing it a two-
port device. The two types of the bridge are source routing and transparent bridges.
Switch:-
It is a multiport connection with a buffer and a construct that can improve its
effectiveness and performance. There is a data link layer device. The switch can execute fault
checking before promoting data that creates (Jovcic & Lin, 2014). It was handy as it does not
forward packets that have technical mistakes and forward proper packets selectively to accurate
port only.
Question 1:-
Explain the differences between the following network devices: hub, bridge, switch, router, and a
firewall. Where would you utilize each device and why? Where does each device reside within
the OSI model?
Answer:-
Hub:-
It is mainly a multiport repeater. This links with several wires coming from several
branches. Hubs cannot filter information, so data packets are directing to all attached devices
(Gil et al., 2014). They do not have the logical expression to search the most exceptional
technique for data packets which leads to ineffectiveness and excess.
Bridge:-
It mainly works at the data link layer. It is also a repeater. A bridge is the layer-2 devices,
working on the frames. The bridge is also applying for interrelating two LANs working on the
equivalent protocol. It has a particular input and distinct output port, thus constructing it a two-
port device. The two types of the bridge are source routing and transparent bridges.
Switch:-
It is a multiport connection with a buffer and a construct that can improve its
effectiveness and performance. There is a data link layer device. The switch can execute fault
checking before promoting data that creates (Jovcic & Lin, 2014). It was handy as it does not
forward packets that have technical mistakes and forward proper packets selectively to accurate
port only.

2TELECOMMUNICATION AND INFORMATION SECURITY
Router:-
It mainly routes data packets built on their IP addresses. This network Layer device
connects with WANs and LANs together. The router has dynamically informing routing
benchmark based on which they make choices on routing the data packets. Routers execute the
traffic pointing functions on the Internet. The information sent over the internet, like as an email
or webpage, is in the procedure of data packets.
Firewall:-
It is a network safety structure that controls and displays departing and external network
traffic constructed on scheduled security directions. A firewall generally obstructs a reliable
internal network and untrusted outside network, like as the Internet. Its objective is to create an
obstacle between the core network and inbound traffic from external resources in order to block
malicious traffic like hackers and viruses (Hassanin et al., 2018). The three types of firewall are
Circuit-level gateway, Packet filtering firewall and Stateful inspection firewall.
Purposes:-
Hub:-
The people mainly use the hub to fix a network of individual computers together. People
can just link the Hub to the standing network jack and then the Hub tool. Furthermore, it is also
taking to run cabling from the Switch to the cubicle.
Bridge:-
Collision is very much tricky terms in network engineering. With the help of a bridge, the
user system designer can avoid network collision effectively. The principal aim for segmenting
Router:-
It mainly routes data packets built on their IP addresses. This network Layer device
connects with WANs and LANs together. The router has dynamically informing routing
benchmark based on which they make choices on routing the data packets. Routers execute the
traffic pointing functions on the Internet. The information sent over the internet, like as an email
or webpage, is in the procedure of data packets.
Firewall:-
It is a network safety structure that controls and displays departing and external network
traffic constructed on scheduled security directions. A firewall generally obstructs a reliable
internal network and untrusted outside network, like as the Internet. Its objective is to create an
obstacle between the core network and inbound traffic from external resources in order to block
malicious traffic like hackers and viruses (Hassanin et al., 2018). The three types of firewall are
Circuit-level gateway, Packet filtering firewall and Stateful inspection firewall.
Purposes:-
Hub:-
The people mainly use the hub to fix a network of individual computers together. People
can just link the Hub to the standing network jack and then the Hub tool. Furthermore, it is also
taking to run cabling from the Switch to the cubicle.
Bridge:-
Collision is very much tricky terms in network engineering. With the help of a bridge, the
user system designer can avoid network collision effectively. The principal aim for segmenting
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3TELECOMMUNICATION AND INFORMATION SECURITY
networks is to decrease the number of devices linked to the equivalent wire and thus decrease the
waiting period for the transmission. Bridge also helpful to install any network device. With the
help of Bridge, the device takes a data packet where the destination and source addresses are on
the equivalent segment, and it overlooks it.
Switch:-
These are generally used in LAN to send every incoming communication frame by
considering at the physical device location, known as the MAC address. Usually, a switch
delivers a massive number of ports for cable networks, allowing for star topology routing. It is
generally using to link several computers to the network (Ragupathi, Sekar & Susitra, 2014).
These also distributes a LAN into several collision domains with free broadband, thus
importantly rising the LAN bandwidth.
Router:-
It mainly links several networks and forward packets intended either for its particular
networks or other networks. It is also measured a layer-3 device for its prime forwarding
selection is based on the evidence in the layer-3 IP packet, exactly the terminal of protocol
location.
Firewall:-
With the help of a firewall, the user can avoid illegal internet operators from retrieving
isolated networks linked to the internet, particularly intranets. It is also working to block these
illegal requests, passing over only selected traffic. The user can also construct a firewall to
prohibit access to specific facilities to prevent workers from retrieving non-work sources while
on the timepiece.
networks is to decrease the number of devices linked to the equivalent wire and thus decrease the
waiting period for the transmission. Bridge also helpful to install any network device. With the
help of Bridge, the device takes a data packet where the destination and source addresses are on
the equivalent segment, and it overlooks it.
Switch:-
These are generally used in LAN to send every incoming communication frame by
considering at the physical device location, known as the MAC address. Usually, a switch
delivers a massive number of ports for cable networks, allowing for star topology routing. It is
generally using to link several computers to the network (Ragupathi, Sekar & Susitra, 2014).
These also distributes a LAN into several collision domains with free broadband, thus
importantly rising the LAN bandwidth.
Router:-
It mainly links several networks and forward packets intended either for its particular
networks or other networks. It is also measured a layer-3 device for its prime forwarding
selection is based on the evidence in the layer-3 IP packet, exactly the terminal of protocol
location.
Firewall:-
With the help of a firewall, the user can avoid illegal internet operators from retrieving
isolated networks linked to the internet, particularly intranets. It is also working to block these
illegal requests, passing over only selected traffic. The user can also construct a firewall to
prohibit access to specific facilities to prevent workers from retrieving non-work sources while
on the timepiece.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4TELECOMMUNICATION AND INFORMATION SECURITY
OSI Layers:-
Device Name OSI Layer
Hub Physical Layer
Bridge Data Link layer
Switch Data Link
Router Network Layer
Firewall Network Layer and Transport Layer
Question 2:-
Define what VPNs are and used for. Distinguish hardware VPN devices and appliances from
software devices. Give examples of both. How do VPNs work? Why would one use a VPN?
What are the downsides of using VPNs?
Answer:-
VPN:-
It spreads a private network through a public network. It permits users to receive and send
information across public or shared networks as if their computing devices were openly linking
to the private network (Nziko & Scheiner, 2015). The VPN facilities establish protected and
encrypted networks to deliver better discretion than even a protected Wi-Fi hotspot.
VPN can be used for different purposes such as
Bypass physical restrictions on sites or streaming video and audio.
Protect the network from interfering on unreliable Wi-Fi hotspots.
OSI Layers:-
Device Name OSI Layer
Hub Physical Layer
Bridge Data Link layer
Switch Data Link
Router Network Layer
Firewall Network Layer and Transport Layer
Question 2:-
Define what VPNs are and used for. Distinguish hardware VPN devices and appliances from
software devices. Give examples of both. How do VPNs work? Why would one use a VPN?
What are the downsides of using VPNs?
Answer:-
VPN:-
It spreads a private network through a public network. It permits users to receive and send
information across public or shared networks as if their computing devices were openly linking
to the private network (Nziko & Scheiner, 2015). The VPN facilities establish protected and
encrypted networks to deliver better discretion than even a protected Wi-Fi hotspot.
VPN can be used for different purposes such as
Bypass physical restrictions on sites or streaming video and audio.
Protect the network from interfering on unreliable Wi-Fi hotspots.

5TELECOMMUNICATION AND INFORMATION SECURITY
Increase at least some secrecy online by beating the correct network location.
Hardware VPN vs Software VPN:-
Hardware VPNs are tools that deliver VPN characteristics such as decryption,
authentication and encryption. It also has a dedicated system structure (Pradeep et al., 2014).
Moreover, they also tend to propose a hardware firewall functionalities to protect the device.
These are stand-alone and also switch every VPN actions.
Example:-
Cisco ASA Series, Cisco VPN 3000 Concentrator.
The Software VPNs can execute any user’s devices. On the supplier’s end, software VPN
is both the consumer they improve and what they install on the available VPN servers.
Example:-
Windows, Mobile operating systems, MAC.
Working principle:-
It works by routing user device's internet linking through user selected VPN's private
server rather than user ISP. When the user information is transmitted to the internet, it originates
from the VPN rather than the user computer. It works as an intermediate of sorts as user link to
the internet, in that way they were hiding user IP location (Draper-Gil et al., 2016). Moreover, if
the user information is someway disturbed, it will be unreadable until it spreads its final
terminus.
Increase at least some secrecy online by beating the correct network location.
Hardware VPN vs Software VPN:-
Hardware VPNs are tools that deliver VPN characteristics such as decryption,
authentication and encryption. It also has a dedicated system structure (Pradeep et al., 2014).
Moreover, they also tend to propose a hardware firewall functionalities to protect the device.
These are stand-alone and also switch every VPN actions.
Example:-
Cisco ASA Series, Cisco VPN 3000 Concentrator.
The Software VPNs can execute any user’s devices. On the supplier’s end, software VPN
is both the consumer they improve and what they install on the available VPN servers.
Example:-
Windows, Mobile operating systems, MAC.
Working principle:-
It works by routing user device's internet linking through user selected VPN's private
server rather than user ISP. When the user information is transmitted to the internet, it originates
from the VPN rather than the user computer. It works as an intermediate of sorts as user link to
the internet, in that way they were hiding user IP location (Draper-Gil et al., 2016). Moreover, if
the user information is someway disturbed, it will be unreadable until it spreads its final
terminus.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6TELECOMMUNICATION AND INFORMATION SECURITY
Why:-
VPN would have restricted use. If the user is trying to avoid government guidelines and
access social media sites such as Twitter, Instagram or Facebook, a VPN might be beneficial.
Even then, the user would have to be somewhat dependent on the government’s willingness to
express the other technique. Any user is trying to continue private from interfering eyes or avoid
NSA-style bulk information collection as a matter of code. A trustworthy VPN will perhaps be
decent enough.
Downsides:-
There are some drawbacks of VPN as follows-
1. Low internet connection
2. Definite barriers to VPN facilities
3. Unlawful use of VPNs
4. The logging and possible reselling of user internet practices to third parties
5. Connection disruptions
6. An unnecessary sense of online exemption
Question 3:
Describe four wireless technologies/standards. Describe what each one does and briefly how it
works? How is each one different from the other standards? Why would you use one over the
other?
Answer:-
Standard:-
Why:-
VPN would have restricted use. If the user is trying to avoid government guidelines and
access social media sites such as Twitter, Instagram or Facebook, a VPN might be beneficial.
Even then, the user would have to be somewhat dependent on the government’s willingness to
express the other technique. Any user is trying to continue private from interfering eyes or avoid
NSA-style bulk information collection as a matter of code. A trustworthy VPN will perhaps be
decent enough.
Downsides:-
There are some drawbacks of VPN as follows-
1. Low internet connection
2. Definite barriers to VPN facilities
3. Unlawful use of VPNs
4. The logging and possible reselling of user internet practices to third parties
5. Connection disruptions
6. An unnecessary sense of online exemption
Question 3:
Describe four wireless technologies/standards. Describe what each one does and briefly how it
works? How is each one different from the other standards? Why would you use one over the
other?
Answer:-
Standard:-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7TELECOMMUNICATION AND INFORMATION SECURITY
802.11a:-
It is an extension to 802.11 that executes to wireless LANs and delivers up to 50 to 55-
Mbps in the 5.2 GHz band. It also applies an orthogonal "frequency division multiplexing
encoding structure" relatively than DSS or FHSS. This standard permits for more synchronized
users, and it has the quickest transmission speed.
802.11b:-
It is the most common wireless variant applied. With communication speeds of just
10.56Mbits/sec, it is too the slowest. 802.11b also applied the 40bit WEP security protocol,
which was established to have a number of insufficiencies.
802.15.1:-
It is more usually known as Bluetooth, is a low-power wireless low-data-ratio,
networking standard designed at exchanging cables between trivial devices (Burg,
Chattopadhyay & Lam, 2017). The Bluetooth stack describes many apparatus above the MAC
and PHY layers, some of which are non-compulsory.
802.16:-
This wireless technology permits data to be moved at a proportion of 30-40 Mb/sec. The
word refers exactly to interoperable applications of the IEEE 802.16 wireless structure. The
technology was formerly used by some portable carriers, notably Sprint, to carry wireless
information to its clients.
Differences:-
Specification 802.11a 802.11b 802.15.1 802.16
802.11a:-
It is an extension to 802.11 that executes to wireless LANs and delivers up to 50 to 55-
Mbps in the 5.2 GHz band. It also applies an orthogonal "frequency division multiplexing
encoding structure" relatively than DSS or FHSS. This standard permits for more synchronized
users, and it has the quickest transmission speed.
802.11b:-
It is the most common wireless variant applied. With communication speeds of just
10.56Mbits/sec, it is too the slowest. 802.11b also applied the 40bit WEP security protocol,
which was established to have a number of insufficiencies.
802.15.1:-
It is more usually known as Bluetooth, is a low-power wireless low-data-ratio,
networking standard designed at exchanging cables between trivial devices (Burg,
Chattopadhyay & Lam, 2017). The Bluetooth stack describes many apparatus above the MAC
and PHY layers, some of which are non-compulsory.
802.16:-
This wireless technology permits data to be moved at a proportion of 30-40 Mb/sec. The
word refers exactly to interoperable applications of the IEEE 802.16 wireless structure. The
technology was formerly used by some portable carriers, notably Sprint, to carry wireless
information to its clients.
Differences:-
Specification 802.11a 802.11b 802.15.1 802.16
8TELECOMMUNICATION AND INFORMATION SECURITY
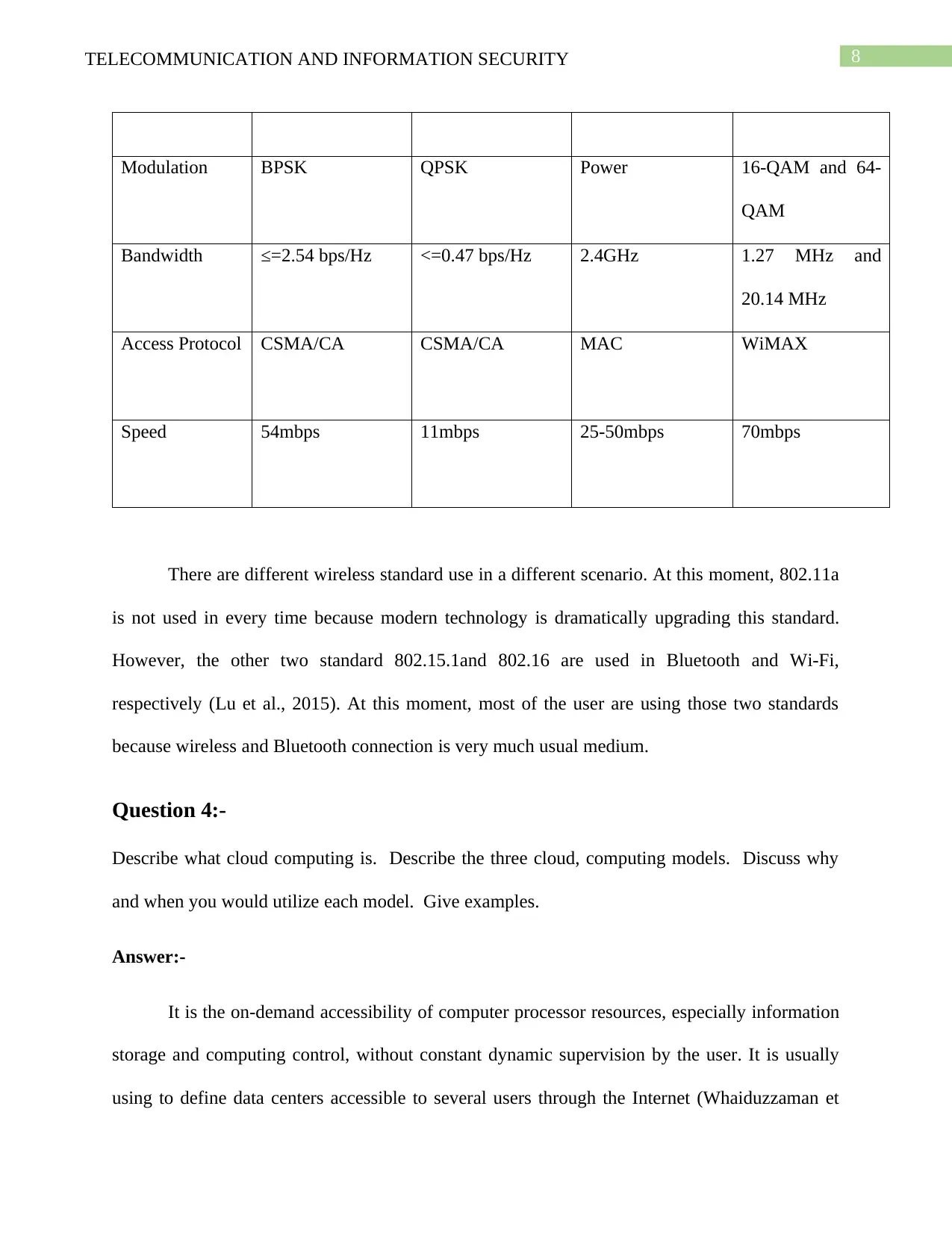
Modulation BPSK QPSK Power 16-QAM and 64-
QAM
Bandwidth ≤=2.54 bps/Hz <=0.47 bps/Hz 2.4GHz 1.27 MHz and
20.14 MHz
Access Protocol CSMA/CA CSMA/CA MAC WiMAX
Speed 54mbps 11mbps 25-50mbps 70mbps
There are different wireless standard use in a different scenario. At this moment, 802.11a
is not used in every time because modern technology is dramatically upgrading this standard.
However, the other two standard 802.15.1and 802.16 are used in Bluetooth and Wi-Fi,
respectively (Lu et al., 2015). At this moment, most of the user are using those two standards
because wireless and Bluetooth connection is very much usual medium.
Question 4:-
Describe what cloud computing is. Describe the three cloud, computing models. Discuss why
and when you would utilize each model. Give examples.
Answer:-
It is the on-demand accessibility of computer processor resources, especially information
storage and computing control, without constant dynamic supervision by the user. It is usually
using to define data centers accessible to several users through the Internet (Whaiduzzaman et
Modulation BPSK QPSK Power 16-QAM and 64-
QAM
Bandwidth ≤=2.54 bps/Hz <=0.47 bps/Hz 2.4GHz 1.27 MHz and
20.14 MHz
Access Protocol CSMA/CA CSMA/CA MAC WiMAX
Speed 54mbps 11mbps 25-50mbps 70mbps
There are different wireless standard use in a different scenario. At this moment, 802.11a
is not used in every time because modern technology is dramatically upgrading this standard.
However, the other two standard 802.15.1and 802.16 are used in Bluetooth and Wi-Fi,
respectively (Lu et al., 2015). At this moment, most of the user are using those two standards
because wireless and Bluetooth connection is very much usual medium.
Question 4:-
Describe what cloud computing is. Describe the three cloud, computing models. Discuss why
and when you would utilize each model. Give examples.
Answer:-
It is the on-demand accessibility of computer processor resources, especially information
storage and computing control, without constant dynamic supervision by the user. It is usually
using to define data centers accessible to several users through the Internet (Whaiduzzaman et
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9TELECOMMUNICATION AND INFORMATION SECURITY
al., 2014). It has become the perfect technique to distribute enterprise applications and the
desired explanation for businesses spreading their arrangement or launching new inventions.
Models:-
The three cloud computing model is as follows,
SaaS:-
It is a software authorizing and distribution model in which software is certified on a donation
basis and is centrally introduced. It is usually mentioned to as "on-demand software", and was
earlier stated to as "software plus services" by Microsoft (Ali, Khan & Vasilakos, 2015). The
Important benefits of SaaS contain compatibility, accessibility, and effective management.
PaaS:-
Platform as a service is a category of cloud computing contributing process. This facility
provider delivers a stage to clients and permitting them to improve, run, and cope with
professional applications without the necessity to construct. It keeps the infrastructure like
software development procedures typically want.
IaaS:-
It is also the part of cloud computing which delivers high-level APIs. It is applied to dereference
several low-level facts of fundamental network arrangement like location, physical computing
resources, data separating, security, scaling, backup. Conversely, with the beginning of
innovative technologies, like serverless and containers, and the linked rise of the microservices
application design, IaaS remains introductory but is in a packed field always.
al., 2014). It has become the perfect technique to distribute enterprise applications and the
desired explanation for businesses spreading their arrangement or launching new inventions.
Models:-
The three cloud computing model is as follows,
SaaS:-
It is a software authorizing and distribution model in which software is certified on a donation
basis and is centrally introduced. It is usually mentioned to as "on-demand software", and was
earlier stated to as "software plus services" by Microsoft (Ali, Khan & Vasilakos, 2015). The
Important benefits of SaaS contain compatibility, accessibility, and effective management.
PaaS:-
Platform as a service is a category of cloud computing contributing process. This facility
provider delivers a stage to clients and permitting them to improve, run, and cope with
professional applications without the necessity to construct. It keeps the infrastructure like
software development procedures typically want.
IaaS:-
It is also the part of cloud computing which delivers high-level APIs. It is applied to dereference
several low-level facts of fundamental network arrangement like location, physical computing
resources, data separating, security, scaling, backup. Conversely, with the beginning of
innovative technologies, like serverless and containers, and the linked rise of the microservices
application design, IaaS remains introductory but is in a packed field always.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10TELECOMMUNICATION AND INFORMATION SECURITY
The three different categories are using for different purposes. SaaS permits quicker and
easier integration with other stands without the necessity to get costly infrastructure.
Conceivably one of the most vital explanations for watching at PaaS is the potential industrial
benefits they can deliver. PaaS allows businesses to be very responsive and receptive to concerns
or demand (Almorsy, Grundy & Müller, 2016). IaaS is beneficial for conduct irregular demand
and progressively rising storage requirements. It can also simplify scheduling and supervision of
backup and repossession systems.
Question 5:-
Describe in detail what the Internet of Things (IoT) is. What are the issues with IoT? Do you
believe IoT is the wave of the future (yes or no, and why)? How will IoT impact the overall
internet?
Answer:-
The IoT is a structure of consistent computing tools, digital and mechanical technologies
delivered with exceptional identifiers and the capability to handover information over a network
without demanding human computer interaction (Zhang et al., 2014). The governments in a
diversity of businesses are using IoT to function more proficiently, better understand clients to
provide enhanced client facility, improve decision-making and increase the business value.
Issues:-
Several issues are suffering from the IoT. The issues are as follows
Cloud Attacks
Security Vulnerabilities
The three different categories are using for different purposes. SaaS permits quicker and
easier integration with other stands without the necessity to get costly infrastructure.
Conceivably one of the most vital explanations for watching at PaaS is the potential industrial
benefits they can deliver. PaaS allows businesses to be very responsive and receptive to concerns
or demand (Almorsy, Grundy & Müller, 2016). IaaS is beneficial for conduct irregular demand
and progressively rising storage requirements. It can also simplify scheduling and supervision of
backup and repossession systems.
Question 5:-
Describe in detail what the Internet of Things (IoT) is. What are the issues with IoT? Do you
believe IoT is the wave of the future (yes or no, and why)? How will IoT impact the overall
internet?
Answer:-
The IoT is a structure of consistent computing tools, digital and mechanical technologies
delivered with exceptional identifiers and the capability to handover information over a network
without demanding human computer interaction (Zhang et al., 2014). The governments in a
diversity of businesses are using IoT to function more proficiently, better understand clients to
provide enhanced client facility, improve decision-making and increase the business value.
Issues:-
Several issues are suffering from the IoT. The issues are as follows
Cloud Attacks
Security Vulnerabilities

11TELECOMMUNICATION AND INFORMATION SECURITY
Deficiency of confidence
Internet firewalls
Privacy
Future:-
IoT is very much essential for modern society. The society can get a good advantage for
these techniques. In future, this IoT technology can make the smart universe. People can use a
different type of smart apparatus for this reason. People can get a smart city and smart learning
concept for the IoT. So the conclusion is that IoT is the wave for the upcoming world.
Impact:-
The Internet attaches persons via commercial and social communication or with
structures via professional transaction like as e-commerce and internet banking. Additionally, the
developing IoT is all about concerning machines and structures together via actuators and
sensors. So that demonstrative evidence from these structures can be collected, and activities are
taken to develop human efficiency and effectiveness (Alaba et al., 2017). IoT-enabled tools are
supporting us to decrease air pollution in some of the human world's biggest metropolises. It is
also improve farming and human food source, and even sense and cover lethal viruses. The
conclusion is that IoT can create a significant impact on the internet as well as a modern society.
Deficiency of confidence
Internet firewalls
Privacy
Future:-
IoT is very much essential for modern society. The society can get a good advantage for
these techniques. In future, this IoT technology can make the smart universe. People can use a
different type of smart apparatus for this reason. People can get a smart city and smart learning
concept for the IoT. So the conclusion is that IoT is the wave for the upcoming world.
Impact:-
The Internet attaches persons via commercial and social communication or with
structures via professional transaction like as e-commerce and internet banking. Additionally, the
developing IoT is all about concerning machines and structures together via actuators and
sensors. So that demonstrative evidence from these structures can be collected, and activities are
taken to develop human efficiency and effectiveness (Alaba et al., 2017). IoT-enabled tools are
supporting us to decrease air pollution in some of the human world's biggest metropolises. It is
also improve farming and human food source, and even sense and cover lethal viruses. The
conclusion is that IoT can create a significant impact on the internet as well as a modern society.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





