IIL Location Intelligence for Policy Assessment (LIPPA) Project Report
VerifiedAdded on 2020/05/04
|14
|2912
|55
Project
AI Summary
This project report addresses the implementation of a Risk Analysis Product (RAP) for Inshore Insurance Limited (IIL), an Australian financial institution. The project aims to analyze risks associated with insurance claims, accidents, and cyber threats. The report details the solution scope, overview, constraints, and design, including system object models, object collaboration, and non-functional requirements. Key components include a cloud-based architecture, data solutions utilizing big data technologies, and a focus on data security and user access control. The project's budget is estimated at $1.35 million, with a target completion date in Q4 2016. The solution involves an in-house RAP application, integrating with the cloud platform to detect vulnerabilities, manage large data volumes, and provide recommendations for IT solutions. The project considers constraints like external dependencies, data breaches, and cyber threats, while excluding external factors like CEO responsibilities. The report also provides use cases, system diagrams, and interface models to illustrate the project's functionality and architecture. The data solution leverages cloud and big data technologies, with an estimated database size of 10TB, growing by 50-70% annually. The project emphasizes the importance of secure access control and data security.

Running head: IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
IIL Location Intelligence for Policy Assessment (LIPPA) Project
Name of the Student:
Name of the University:
Author Note
IIL Location Intelligence for Policy Assessment (LIPPA) Project
Name of the Student:
Name of the University:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
IIL Location Intelligence for Policy Assessment (LIPPA) Project
Table of Contents
1.0 Introduction...........................................................................................................................................3
1.1 Introduction.......................................................................................................................................3
1.1 Solution Scope...................................................................................................................................3
1.2 Solution Overview.............................................................................................................................3
1.3 Constraints.........................................................................................................................................4
1.4 Exclusions..........................................................................................................................................4
2.0 Glossary.................................................................................................................................................4
3.0 Use Cases...............................................................................................................................................5
3.1 Actors................................................................................................................................................5
3.2 Use Case Diagrams............................................................................................................................5
4.0 Design Overview....................................................................................................................................6
4.1 Solution Architecture.........................................................................................................................6
4.2.1 Project Governance Process...........................................................................................................6
4.2.2 IT Infrastructure Solution................................................................................................................7
4.2.3 Infrastructure Security....................................................................................................................7
4.2.4 Application Solution........................................................................................................................7
4.3 Data Solution.....................................................................................................................................7
4.4 Capacity Requirements......................................................................................................................7
4.6 Constraints and Assumptions............................................................................................................8
5.0 System Object Model............................................................................................................................8
5.1 Sub Systems.......................................................................................................................................8
5.2 Subsystem Interfaces.........................................................................................................................9
6.0 Object Collaboration..............................................................................................................................9
6.1 Collaboration Diagrams.....................................................................................................................9
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
IIL Location Intelligence for Policy Assessment (LIPPA) Project
Table of Contents
1.0 Introduction...........................................................................................................................................3
1.1 Introduction.......................................................................................................................................3
1.1 Solution Scope...................................................................................................................................3
1.2 Solution Overview.............................................................................................................................3
1.3 Constraints.........................................................................................................................................4
1.4 Exclusions..........................................................................................................................................4
2.0 Glossary.................................................................................................................................................4
3.0 Use Cases...............................................................................................................................................5
3.1 Actors................................................................................................................................................5
3.2 Use Case Diagrams............................................................................................................................5
4.0 Design Overview....................................................................................................................................6
4.1 Solution Architecture.........................................................................................................................6
4.2.1 Project Governance Process...........................................................................................................6
4.2.2 IT Infrastructure Solution................................................................................................................7
4.2.3 Infrastructure Security....................................................................................................................7
4.2.4 Application Solution........................................................................................................................7
4.3 Data Solution.....................................................................................................................................7
4.4 Capacity Requirements......................................................................................................................7
4.6 Constraints and Assumptions............................................................................................................8
5.0 System Object Model............................................................................................................................8
5.1 Sub Systems.......................................................................................................................................8
5.2 Subsystem Interfaces.........................................................................................................................9
6.0 Object Collaboration..............................................................................................................................9
6.1 Collaboration Diagrams.....................................................................................................................9

2
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
6.2 Access Model...................................................................................................................................10
7.0 Non Functional Requirements.............................................................................................................10
7.1 Performance Considerations...........................................................................................................10
7.2 Design Constraints...........................................................................................................................11
7.3 Test Criteria.....................................................................................................................................11
7.4 Proof of Compliance........................................................................................................................11
8.0 Bibliography.........................................................................................................................................12
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
6.2 Access Model...................................................................................................................................10
7.0 Non Functional Requirements.............................................................................................................10
7.1 Performance Considerations...........................................................................................................10
7.2 Design Constraints...........................................................................................................................11
7.3 Test Criteria.....................................................................................................................................11
7.4 Proof of Compliance........................................................................................................................11
8.0 Bibliography.........................................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
1.0 Introduction
1.1 Introduction
The paper is concerned with the Inshore Insurance Limited organization located in Australia. It is
a regulated financial institution that is concerned with the assets that are in an excess of $1 Billion. The
head office for the company is locate in Sydney. The IT services for the managed in-house and the main
data center for the company are present in the head offices. They also make use of the cloud services
for various type of other activities that are to be performed for the business of the company. According
to the provided information the crimes and accidents that results in the insurance claims by the people
directly. The frequency and the cost of the company is being hampered due to this, and hence the
company is looking to implement some IT solutions for the company that would be helping the company
in overcome the threats that are being possessed towards the company.
The paper provides the detailed threat analysis for the company and also the discussions about
the solutions to the threats.
The solution scope, solution overview, constrains for the solutions and the design overview for
the solutions have been included in this paper. In addition to this, the system object model, the object
collaboration model and the Non-functional requirements for the models have also been provided in
this paper.
1.1 Solution Scope
The board of the company wants a high level analysis and effective recommendations for the IT
solutions for the company. The company is looking to implement an RAP or Risk analysis product for the
analysis of the risks for the company. The solution would be able to detect the vulnerabilities within the
company and also the ones that are included in the business procedures of the company. The solution
should also be able to define a single platform that would be able to support huge amounts of data that
are generated from the in-house software and also from the cloud platforms of the company.
1.2 Solution Overview
The company is looking to implement a solution that would help in the analysis of the risks for
the company. The Risk Analysis Product or the RAP application would be helpful for the company to
detect the threats that are prevalent within the organization and also the application would provide
assistance to the company in the process of threat resolution. The in-house platform has been chosen by
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
1.0 Introduction
1.1 Introduction
The paper is concerned with the Inshore Insurance Limited organization located in Australia. It is
a regulated financial institution that is concerned with the assets that are in an excess of $1 Billion. The
head office for the company is locate in Sydney. The IT services for the managed in-house and the main
data center for the company are present in the head offices. They also make use of the cloud services
for various type of other activities that are to be performed for the business of the company. According
to the provided information the crimes and accidents that results in the insurance claims by the people
directly. The frequency and the cost of the company is being hampered due to this, and hence the
company is looking to implement some IT solutions for the company that would be helping the company
in overcome the threats that are being possessed towards the company.
The paper provides the detailed threat analysis for the company and also the discussions about
the solutions to the threats.
The solution scope, solution overview, constrains for the solutions and the design overview for
the solutions have been included in this paper. In addition to this, the system object model, the object
collaboration model and the Non-functional requirements for the models have also been provided in
this paper.
1.1 Solution Scope
The board of the company wants a high level analysis and effective recommendations for the IT
solutions for the company. The company is looking to implement an RAP or Risk analysis product for the
analysis of the risks for the company. The solution would be able to detect the vulnerabilities within the
company and also the ones that are included in the business procedures of the company. The solution
should also be able to define a single platform that would be able to support huge amounts of data that
are generated from the in-house software and also from the cloud platforms of the company.
1.2 Solution Overview
The company is looking to implement a solution that would help in the analysis of the risks for
the company. The Risk Analysis Product or the RAP application would be helpful for the company to
detect the threats that are prevalent within the organization and also the application would provide
assistance to the company in the process of threat resolution. The in-house platform has been chosen by
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
the organization for this implementation and the purchase of any software from an external vendor. In
addition to this, the integration with the cloud platform is also chosen by the company. The company
has estimated a budget of around $1.35 million and solution for the company is due in the fourth
quarter of the year 2016.
1.3 Constraints
The main constrains of the company that are to be considered during the implementation of the
RAP application. There are two type of threats that the application may be subjected to. The external
dependencies on which the threat model for the application depends basically includes the
management of claims, archives and the cloud services. The verification of the accounts of the users and
the management of the large volume of data by the company also possess a considerable probability of
threats for the company. Hence, the developed solution is required to address all these issues that are
prevalent in the organization.
In addition to this, there are various high potential threats that lies within the organization, such
as data breaches that can take place due to the access control features in the system. The organization
would also have to share a large amount of data on the cloud, and hence, there is potential treat of the
data of the company being exposed to the outside world. Additional threats may also occur in case of a
dispute over the claims by the clients. Threat from the cyber attackers also exists for the information
system that is in place for the company.
1.4 Exclusions
The application would be helpful for the company in the mitigation of the risk that are prevalent
in the company and the internal factors of the businesses of the company can be handled efficiently by
the application but the external factors that would be affecting the business of the company cannot be
handled by the application. Various criteria such as the responsibilities of the CEO of the company and
the executive operations of the company cannot be handled by the application and also the process of
reducing the threats involved in these operations of the company.
2.0 Glossary
RAP Application, Information system, Cloud Architecture, Cloud Services, Cloud Solutions, IT
Solutions, Big Data, Use Cases, Project Budget, Database, Data Centers, Severs, Insurance, Claims,
Clients, Agents, Broker.
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
the organization for this implementation and the purchase of any software from an external vendor. In
addition to this, the integration with the cloud platform is also chosen by the company. The company
has estimated a budget of around $1.35 million and solution for the company is due in the fourth
quarter of the year 2016.
1.3 Constraints
The main constrains of the company that are to be considered during the implementation of the
RAP application. There are two type of threats that the application may be subjected to. The external
dependencies on which the threat model for the application depends basically includes the
management of claims, archives and the cloud services. The verification of the accounts of the users and
the management of the large volume of data by the company also possess a considerable probability of
threats for the company. Hence, the developed solution is required to address all these issues that are
prevalent in the organization.
In addition to this, there are various high potential threats that lies within the organization, such
as data breaches that can take place due to the access control features in the system. The organization
would also have to share a large amount of data on the cloud, and hence, there is potential treat of the
data of the company being exposed to the outside world. Additional threats may also occur in case of a
dispute over the claims by the clients. Threat from the cyber attackers also exists for the information
system that is in place for the company.
1.4 Exclusions
The application would be helpful for the company in the mitigation of the risk that are prevalent
in the company and the internal factors of the businesses of the company can be handled efficiently by
the application but the external factors that would be affecting the business of the company cannot be
handled by the application. Various criteria such as the responsibilities of the CEO of the company and
the executive operations of the company cannot be handled by the application and also the process of
reducing the threats involved in these operations of the company.
2.0 Glossary
RAP Application, Information system, Cloud Architecture, Cloud Services, Cloud Solutions, IT
Solutions, Big Data, Use Cases, Project Budget, Database, Data Centers, Severs, Insurance, Claims,
Clients, Agents, Broker.
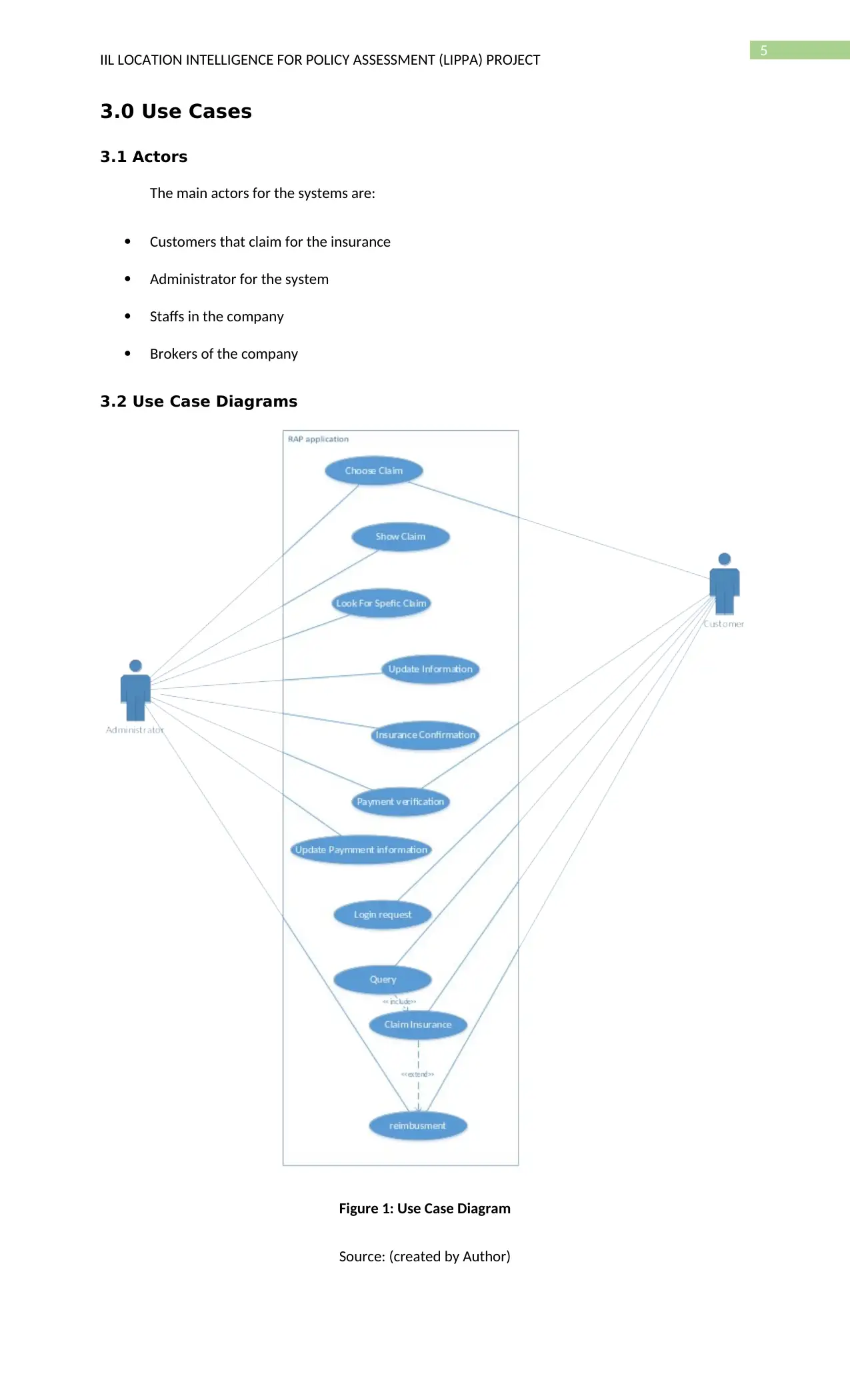
5
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
3.0 Use Cases
3.1 Actors
The main actors for the systems are:
Customers that claim for the insurance
Administrator for the system
Staffs in the company
Brokers of the company
3.2 Use Case Diagrams
Figure 1: Use Case Diagram
Source: (created by Author)
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
3.0 Use Cases
3.1 Actors
The main actors for the systems are:
Customers that claim for the insurance
Administrator for the system
Staffs in the company
Brokers of the company
3.2 Use Case Diagrams
Figure 1: Use Case Diagram
Source: (created by Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
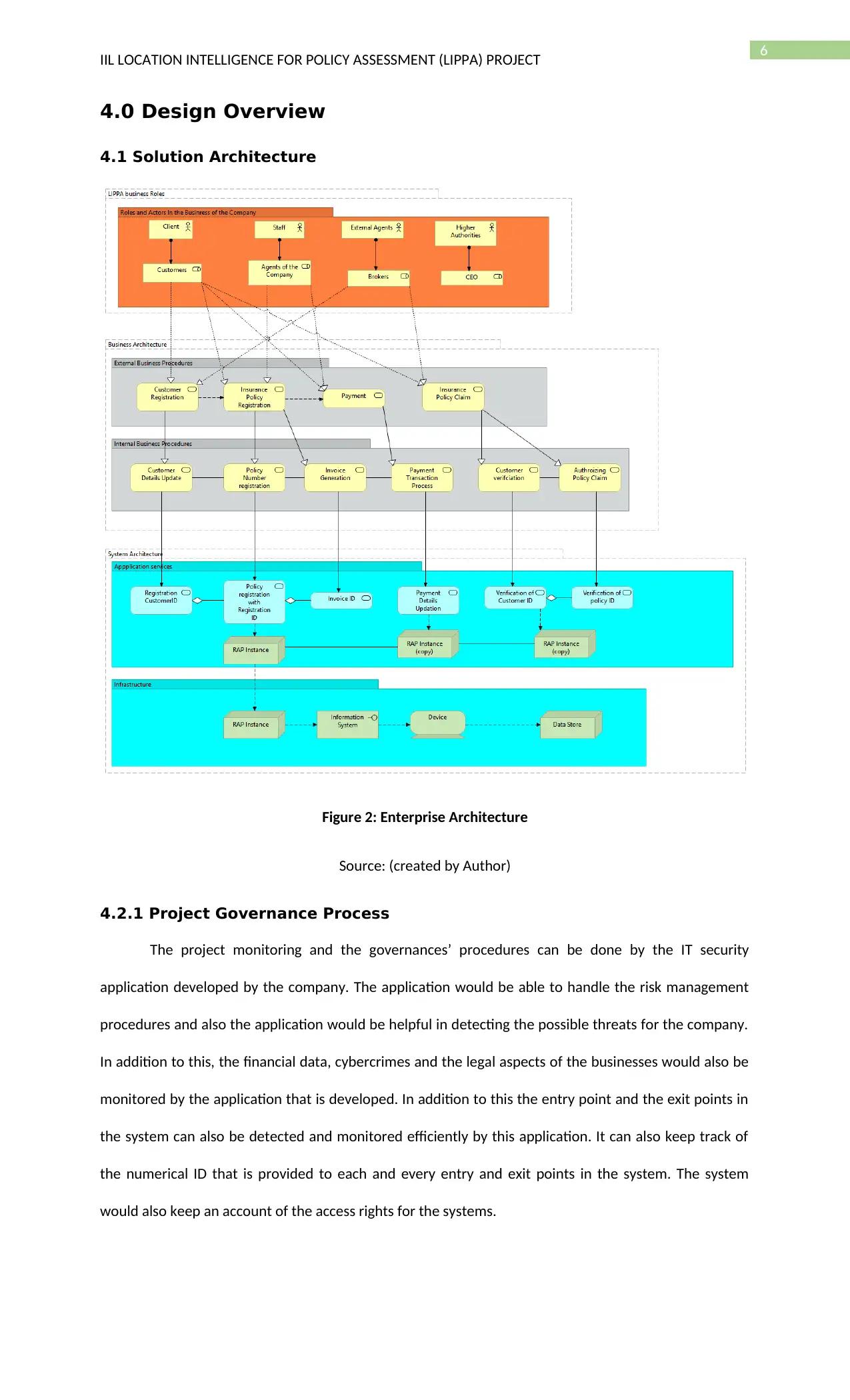
6
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
4.0 Design Overview
4.1 Solution Architecture
Figure 2: Enterprise Architecture
Source: (created by Author)
4.2.1 Project Governance Process
The project monitoring and the governances’ procedures can be done by the IT security
application developed by the company. The application would be able to handle the risk management
procedures and also the application would be helpful in detecting the possible threats for the company.
In addition to this, the financial data, cybercrimes and the legal aspects of the businesses would also be
monitored by the application that is developed. In addition to this the entry point and the exit points in
the system can also be detected and monitored efficiently by this application. It can also keep track of
the numerical ID that is provided to each and every entry and exit points in the system. The system
would also keep an account of the access rights for the systems.
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
4.0 Design Overview
4.1 Solution Architecture
Figure 2: Enterprise Architecture
Source: (created by Author)
4.2.1 Project Governance Process
The project monitoring and the governances’ procedures can be done by the IT security
application developed by the company. The application would be able to handle the risk management
procedures and also the application would be helpful in detecting the possible threats for the company.
In addition to this, the financial data, cybercrimes and the legal aspects of the businesses would also be
monitored by the application that is developed. In addition to this the entry point and the exit points in
the system can also be detected and monitored efficiently by this application. It can also keep track of
the numerical ID that is provided to each and every entry and exit points in the system. The system
would also keep an account of the access rights for the systems.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
4.2.2 IT Infrastructure Solution
The company would maintain a portal for the customers and the different level of users that are
associated with the company and the different type of processes that are followed by the company. The
system would also maintain a data store in the cloud and would be able to fetch and upload the data in
the cloud. The cloud architecture would also help in the distribution of the system and help the
company to reach out to their clients. The brokers for the company would be able to register the
customers in to the systems and handle the insurance claims for the customers. The staffs of the
company would be able to process the insurances procedures for the customers.
4.2.3 Infrastructure Security
The RAP is required to secure the IT solutions for the company. They are responsible for the
security of the Information system as well. The application would be able to monitor the entry points
and the exit points in the systems. The points are also given some numerical values that would help in
the references of the security systems. Proper Authentication and the authorization features are also
being deployed by the application that is in place for the company.
4.2.4 Application Solution
The RAP application can be used in various other procedures of the company in the future. The
application might be able to handle various aspects of financial background for the company. The
application would able to restrict the access to the internal systems of the company. This performance
expectations of the application would also be increased to a great extent for the company. They would
be able to fill the gaps where the company needs to compromise and increase the overall efficiency of
the company as a result.
4.3 Data Solution
The data the stored in the systems of the company would be in the form of virtual data that
would be uploaded on the cloud. The Big Data technologies can also be integrated with the systems.
This technology is very efficient for the cloud based solutions. This would help the company in
maintaining a cloud based solution and also they would be able to access the database that can be set
up in the remote severs with the help of the cloud based solutions that are integrated with the Big Data
Technologies.
4.4 Capacity Requirements
For the development of the systems and the management of the data that is generated from
the system, a database system is to be maintained. The estimated size of the database for the system is
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
4.2.2 IT Infrastructure Solution
The company would maintain a portal for the customers and the different level of users that are
associated with the company and the different type of processes that are followed by the company. The
system would also maintain a data store in the cloud and would be able to fetch and upload the data in
the cloud. The cloud architecture would also help in the distribution of the system and help the
company to reach out to their clients. The brokers for the company would be able to register the
customers in to the systems and handle the insurance claims for the customers. The staffs of the
company would be able to process the insurances procedures for the customers.
4.2.3 Infrastructure Security
The RAP is required to secure the IT solutions for the company. They are responsible for the
security of the Information system as well. The application would be able to monitor the entry points
and the exit points in the systems. The points are also given some numerical values that would help in
the references of the security systems. Proper Authentication and the authorization features are also
being deployed by the application that is in place for the company.
4.2.4 Application Solution
The RAP application can be used in various other procedures of the company in the future. The
application might be able to handle various aspects of financial background for the company. The
application would able to restrict the access to the internal systems of the company. This performance
expectations of the application would also be increased to a great extent for the company. They would
be able to fill the gaps where the company needs to compromise and increase the overall efficiency of
the company as a result.
4.3 Data Solution
The data the stored in the systems of the company would be in the form of virtual data that
would be uploaded on the cloud. The Big Data technologies can also be integrated with the systems.
This technology is very efficient for the cloud based solutions. This would help the company in
maintaining a cloud based solution and also they would be able to access the database that can be set
up in the remote severs with the help of the cloud based solutions that are integrated with the Big Data
Technologies.
4.4 Capacity Requirements
For the development of the systems and the management of the data that is generated from
the system, a database system is to be maintained. The estimated size of the database for the system is

8
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
10TB and there is scope for the database size to grow to about 50 to 70 percent per anum in the future.
In addition to this the location Intelligence initiatives taken by the company would result in the size of
the datasets growing by about 10TB in the future.
4.5 System Interfaces
The user would be able to communicate with the system of the company with the help of RAP
application designed by the company that is in-house maintained. The Staffs in the company would be
able to update the systems and also perform an analysis of the current system provided they have the
proper authentication for the systems. The staffs would also be able to generate the report from the
application after the analysis of the systems of the company has been completed.
4.6 Constraints and Assumptions
The main constrains provided for the system are that there should only be 10 users that would
be able to use the desktops in the Head Quarters. The application developed should also possess an API
and also the access and the distribution will be logged securely in the system. It is assumed that the RAP
application would be interfaced with the cloud technology and the information system for the company.
5.0 System Object Model
5.1 Sub Systems
The system is divided into two levels:
The logical level: The logical level consists of further two tiers and the those are the
business architecture and the system architecture. The business architecture is
concerned with the process that takes place manually. They can be sub divided into the
internal procedures and the external procedures. The system architecture consists of
the application services and the infrastructure of the system.
The Physical level: the physical level is concerned with the main actors and the business
roles for the system.
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
10TB and there is scope for the database size to grow to about 50 to 70 percent per anum in the future.
In addition to this the location Intelligence initiatives taken by the company would result in the size of
the datasets growing by about 10TB in the future.
4.5 System Interfaces
The user would be able to communicate with the system of the company with the help of RAP
application designed by the company that is in-house maintained. The Staffs in the company would be
able to update the systems and also perform an analysis of the current system provided they have the
proper authentication for the systems. The staffs would also be able to generate the report from the
application after the analysis of the systems of the company has been completed.
4.6 Constraints and Assumptions
The main constrains provided for the system are that there should only be 10 users that would
be able to use the desktops in the Head Quarters. The application developed should also possess an API
and also the access and the distribution will be logged securely in the system. It is assumed that the RAP
application would be interfaced with the cloud technology and the information system for the company.
5.0 System Object Model
5.1 Sub Systems
The system is divided into two levels:
The logical level: The logical level consists of further two tiers and the those are the
business architecture and the system architecture. The business architecture is
concerned with the process that takes place manually. They can be sub divided into the
internal procedures and the external procedures. The system architecture consists of
the application services and the infrastructure of the system.
The Physical level: the physical level is concerned with the main actors and the business
roles for the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
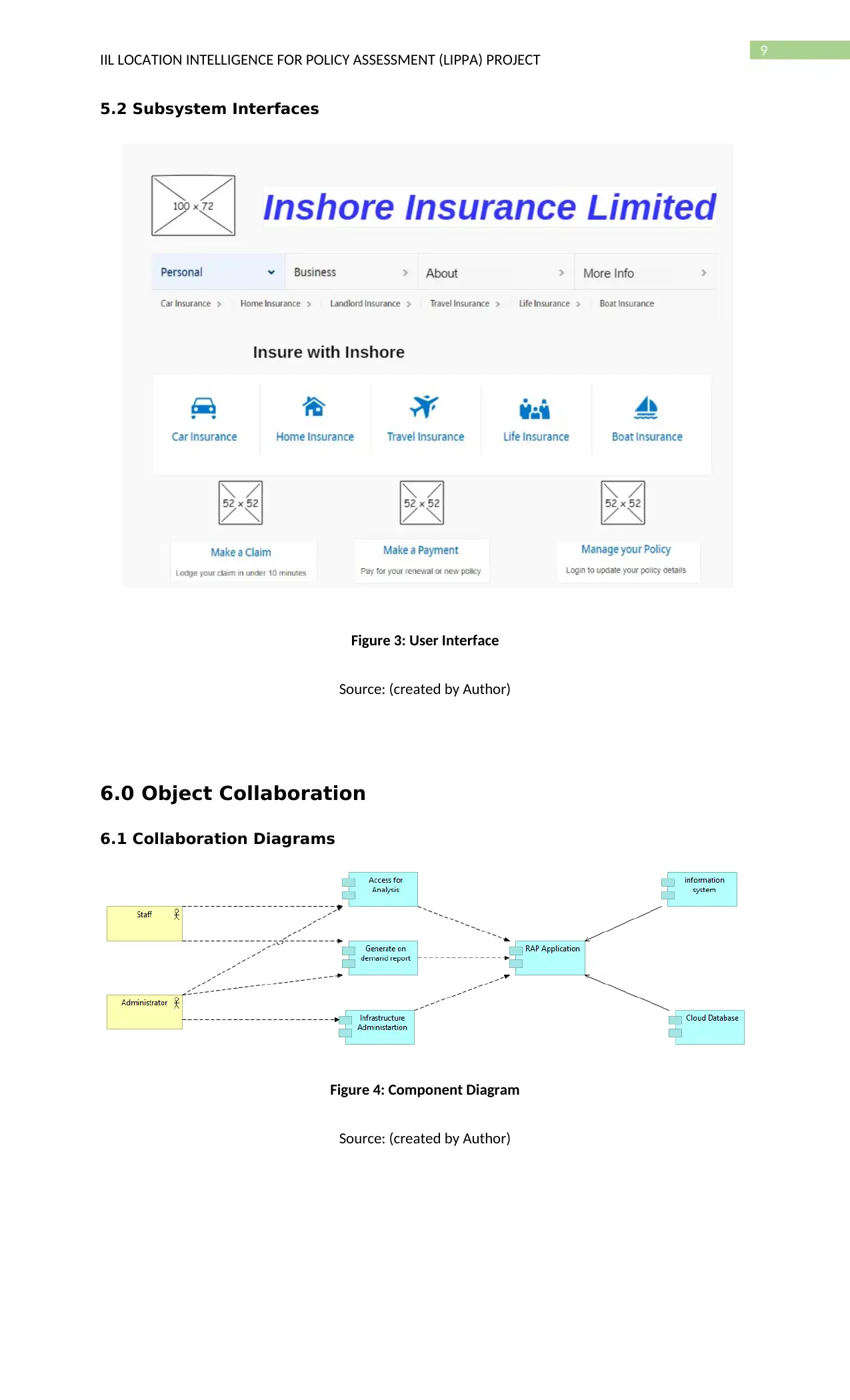
9
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
5.2 Subsystem Interfaces
Figure 3: User Interface
Source: (created by Author)
6.0 Object Collaboration
6.1 Collaboration Diagrams
Figure 4: Component Diagram
Source: (created by Author)
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
5.2 Subsystem Interfaces
Figure 3: User Interface
Source: (created by Author)
6.0 Object Collaboration
6.1 Collaboration Diagrams
Figure 4: Component Diagram
Source: (created by Author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
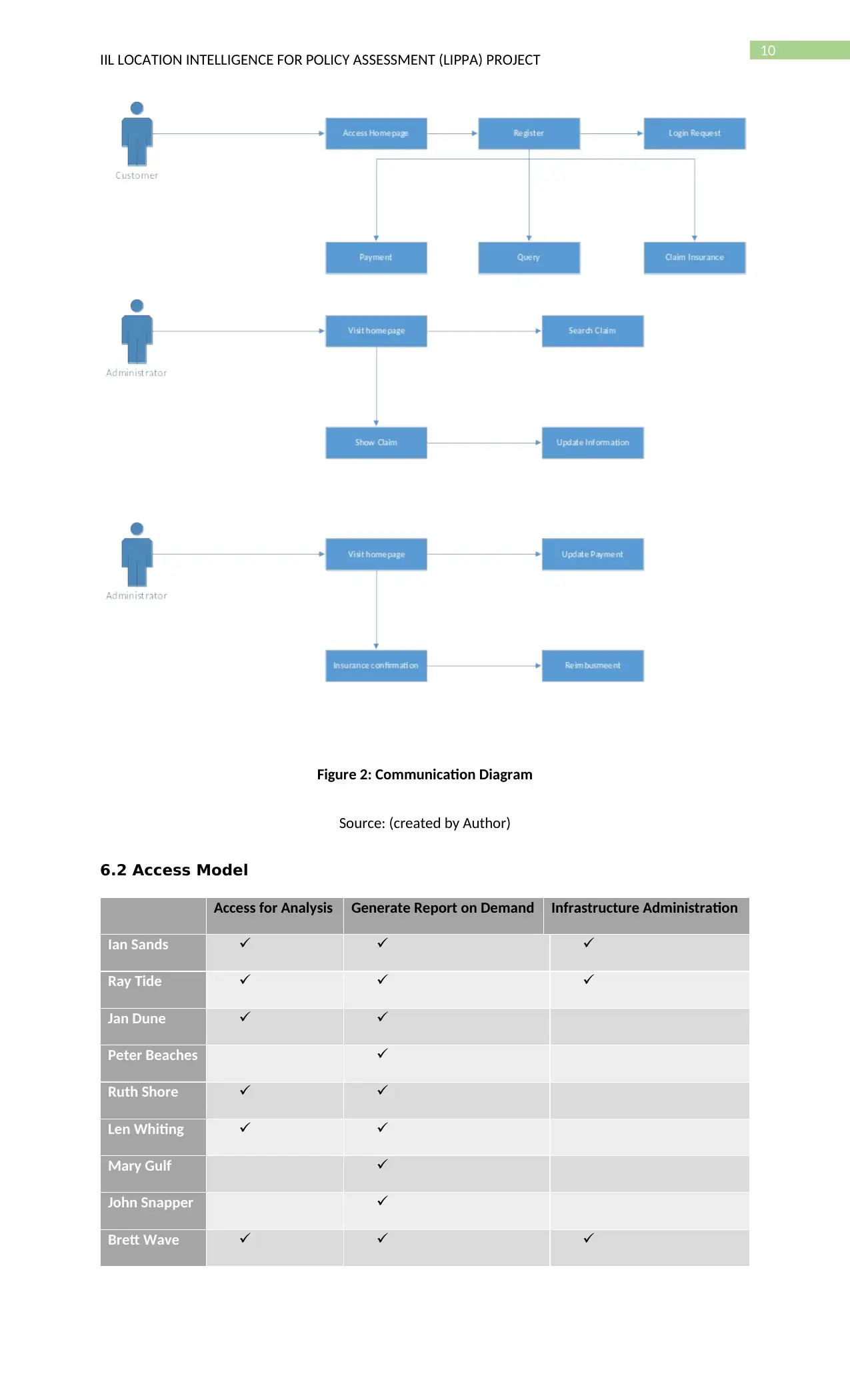
10
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
Figure 2: Communication Diagram
Source: (created by Author)
6.2 Access Model
Access for Analysis Generate Report on Demand Infrastructure Administration
Ian Sands
Ray Tide
Jan Dune
Peter Beaches
Ruth Shore
Len Whiting
Mary Gulf
John Snapper
Brett Wave
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
Figure 2: Communication Diagram
Source: (created by Author)
6.2 Access Model
Access for Analysis Generate Report on Demand Infrastructure Administration
Ian Sands
Ray Tide
Jan Dune
Peter Beaches
Ruth Shore
Len Whiting
Mary Gulf
John Snapper
Brett Wave

11
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
7.0 Non Functional Requirements
7.1 Performance Considerations
For the system various types of functional constrains can be considered. Firstly, the security if
the system is concern and hence the system should have proper firewall in place and efficient access
control for the users in the system. There are addition requirements for the data of the system. The
system The estimated size of the database for the system is 10TB and there is scope for the database
size to grow to about 50 to 70 percent per anum in the future. In addition to this, the company has
estimated a budget of around $1.35 million and system for the company is to be implemented within
the fourth quarter of the year 2016.
7.2 Design Constraints
The designing of the application should be done in such a way so that the system is very easily
navigable by the users and also efficient access control should be maintained by the system. The
authorization and the authentication process should also be efficiently handled by the system.
7.3 Test Criteria
The implemented solution for the company should be tried and tested and hence the solution
should go through some mock hacking techniques where the hackers would try to get through the
different access points in the system and also try and crack the security of the system. The hackers
would also be encouraged to try and look for the different entry points in the system and try to exploit
them.
7.4 Proof of Compliance
The system would prove sustainable if the hackers are unable to enter via the entry points into
the systems and also they are unable to exploit the drawbacks that exists within the system. In addition
to this the hackers would also be expected to point out the areas that are easy for the mal practitioners
to get through. This would help in the efficiency of the security of the system.
IIL LOCATION INTELLIGENCE FOR POLICY ASSESSMENT (LIPPA) PROJECT
7.0 Non Functional Requirements
7.1 Performance Considerations
For the system various types of functional constrains can be considered. Firstly, the security if
the system is concern and hence the system should have proper firewall in place and efficient access
control for the users in the system. There are addition requirements for the data of the system. The
system The estimated size of the database for the system is 10TB and there is scope for the database
size to grow to about 50 to 70 percent per anum in the future. In addition to this, the company has
estimated a budget of around $1.35 million and system for the company is to be implemented within
the fourth quarter of the year 2016.
7.2 Design Constraints
The designing of the application should be done in such a way so that the system is very easily
navigable by the users and also efficient access control should be maintained by the system. The
authorization and the authentication process should also be efficiently handled by the system.
7.3 Test Criteria
The implemented solution for the company should be tried and tested and hence the solution
should go through some mock hacking techniques where the hackers would try to get through the
different access points in the system and also try and crack the security of the system. The hackers
would also be encouraged to try and look for the different entry points in the system and try to exploit
them.
7.4 Proof of Compliance
The system would prove sustainable if the hackers are unable to enter via the entry points into
the systems and also they are unable to exploit the drawbacks that exists within the system. In addition
to this the hackers would also be expected to point out the areas that are easy for the mal practitioners
to get through. This would help in the efficiency of the security of the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





