Threat Model for Inshore Insurance Ltd (IIL): ISYS631 Project B Report
VerifiedAdded on 2023/06/03
|14
|2096
|185
Report
AI Summary
This report presents a comprehensive threat model for Inshore Insurance Ltd (IIL), addressing critical data security concerns within the context of ISYS631 Project B at Australia Catholic University. The report begins with an introduction to the company and the project's objectives, focusing on the challenges of data insecurity and poor database management. It details the scope of the solution, which involves constructing a database model and schemas using MySQL. The report includes a glossary, data diagrams illustrating actors and data flows, and a design overview encompassing solution architecture, project governance, and infrastructure solutions. A system object model and object collaboration diagrams further elaborate on the system's structure and interactions. Non-functional requirements, including performance considerations and design constraints, are also discussed. The document highlights the roles and responsibilities of each team member and references relevant academic sources to support the analysis and proposed solutions. The project aims to upgrade the manual data storage system to improve operational efficiency and client services, addressing the company's need for enhanced data security and automation. The document includes a detailed project management plan, and a threat model for the LIPPA project.

THREAT MODEL
FOR
INSHORE INSURANCE LTD (IIL)
Assignment 1 of ISYS631 Project B
Master of Information Technology
Australia Catholic University (ACU)
Group Members:
Ngoc Quoc Minh HOANG (S00219699)
Shaffali Garg (S00236014)
Lecturer:
Dr. Nitya Karmakar
1
FOR
INSHORE INSURANCE LTD (IIL)
Assignment 1 of ISYS631 Project B
Master of Information Technology
Australia Catholic University (ACU)
Group Members:
Ngoc Quoc Minh HOANG (S00219699)
Shaffali Garg (S00236014)
Lecturer:
Dr. Nitya Karmakar
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
INTRODUCTION.......................................................................................................................3
1.1 Introduction............................................................................................................................3
1.2 Scope of solution....................................................................................................................3
1.3 Overview of solution..............................................................................................................3
1.4 Constraints of the project.......................................................................................................3
1.5 Exclusions..............................................................................................................................4
2.0 GLOSSARY...........................................................................................................................5
2.1 Integration of information......................................................................................................5
2.2 Security of data......................................................................................................................6
2.3 Performance Increment..........................................................................................................7
DATA DIAGRAMS....................................................................................................................8
3.1 Actors.....................................................................................................................................8
3.2 Data flow diagrams (DFDs)...................................................................................................9
4.0 Design overview..................................................................................................................10
4.1 Solution architecture............................................................................................................10
4.1.1 Project governance process...........................................................................................10
4.1.2 Infrastructure solution...................................................................................................11
SYSTEM OBJECT MODEL.....................................................................................................13
5.1 Sub-systems.........................................................................................................................13
5.2 Sub-system interfaces..........................................................................................................13
OBJECT COLLABORATION..................................................................................................14
6.1 Collaboration Diagram.........................................................................................................14
6.2 Access model.......................................................................................................................15
NON-FUNCTIONAL REQUIREMENTS................................................................................16
7.1 Performance considerations.................................................................................................16
7.2 Constraints of design............................................................................................................16
References:.................................................................................................................................17
2
INTRODUCTION.......................................................................................................................3
1.1 Introduction............................................................................................................................3
1.2 Scope of solution....................................................................................................................3
1.3 Overview of solution..............................................................................................................3
1.4 Constraints of the project.......................................................................................................3
1.5 Exclusions..............................................................................................................................4
2.0 GLOSSARY...........................................................................................................................5
2.1 Integration of information......................................................................................................5
2.2 Security of data......................................................................................................................6
2.3 Performance Increment..........................................................................................................7
DATA DIAGRAMS....................................................................................................................8
3.1 Actors.....................................................................................................................................8
3.2 Data flow diagrams (DFDs)...................................................................................................9
4.0 Design overview..................................................................................................................10
4.1 Solution architecture............................................................................................................10
4.1.1 Project governance process...........................................................................................10
4.1.2 Infrastructure solution...................................................................................................11
SYSTEM OBJECT MODEL.....................................................................................................13
5.1 Sub-systems.........................................................................................................................13
5.2 Sub-system interfaces..........................................................................................................13
OBJECT COLLABORATION..................................................................................................14
6.1 Collaboration Diagram.........................................................................................................14
6.2 Access model.......................................................................................................................15
NON-FUNCTIONAL REQUIREMENTS................................................................................16
7.1 Performance considerations.................................................................................................16
7.2 Constraints of design............................................................................................................16
References:.................................................................................................................................17
2

INTRODUCTION
1.1 Introduction
The inshore insurance limited (IIL) is an international insurance body that focuses the IT services
and the security of workmanship. According to a preliminary statement of work in first
assessment, the case study of Inshore Insurance Ltd (IIL), the major problem was stated and that
was a poor database management. Since the IT services which is in housed in the head office
located in the capital Sydney, there is a high risk of data insecurity. Additionally, the company is
paying extra for an Australian 3rd party data center in the purpose of the disaster recovery and
archiving document which is an additional expense for the company. Henceforth, to research
deeply inside the main factors of the Inshore Insurance Ltd (IIL), the CEO of the company was
interviewed by our team and addresses many more information about the conflictions and their
requirements.
1.2 Scope of solution
The solution scope is set to address the challenge of data insecurity by the construction of a
database model and schemas to simulate the full processes. MySQL database will be used to
design the databases.
1.3 Overview of solution
Consequently, the requirements of the stakeholders are to upgrade a new system with a lot of
automation in terms of high volumes of data transformation, storage and its security.
1.4 Constraints of the project
The compatibility between the data operations and the client’s services is required for enhancing
the company. Likewise, the stakeholder CEO advised to give security for highly sensitive
competitive and personal private data. As the budget of upgrading system of the company, CEO
estimated approximately 5 million which can be -/+ 10%. Lastly, the CEO told us the reason
why these modifications has to occur in the future is to make the company more competitive
(Binder, 2016)
3
1.1 Introduction
The inshore insurance limited (IIL) is an international insurance body that focuses the IT services
and the security of workmanship. According to a preliminary statement of work in first
assessment, the case study of Inshore Insurance Ltd (IIL), the major problem was stated and that
was a poor database management. Since the IT services which is in housed in the head office
located in the capital Sydney, there is a high risk of data insecurity. Additionally, the company is
paying extra for an Australian 3rd party data center in the purpose of the disaster recovery and
archiving document which is an additional expense for the company. Henceforth, to research
deeply inside the main factors of the Inshore Insurance Ltd (IIL), the CEO of the company was
interviewed by our team and addresses many more information about the conflictions and their
requirements.
1.2 Scope of solution
The solution scope is set to address the challenge of data insecurity by the construction of a
database model and schemas to simulate the full processes. MySQL database will be used to
design the databases.
1.3 Overview of solution
Consequently, the requirements of the stakeholders are to upgrade a new system with a lot of
automation in terms of high volumes of data transformation, storage and its security.
1.4 Constraints of the project
The compatibility between the data operations and the client’s services is required for enhancing
the company. Likewise, the stakeholder CEO advised to give security for highly sensitive
competitive and personal private data. As the budget of upgrading system of the company, CEO
estimated approximately 5 million which can be -/+ 10%. Lastly, the CEO told us the reason
why these modifications has to occur in the future is to make the company more competitive
(Binder, 2016)
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1.5 Exclusions
This results as an absence of compatibility between the operations under the system of the
company and slow services to the clients as it takes a lot of time to provide the information they
want. Thus, the main problem of the company was a storage as per stated by the CEO while
interviewing and the company relying in the manual system of data management.
4
This results as an absence of compatibility between the operations under the system of the
company and slow services to the clients as it takes a lot of time to provide the information they
want. Thus, the main problem of the company was a storage as per stated by the CEO while
interviewing and the company relying in the manual system of data management.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
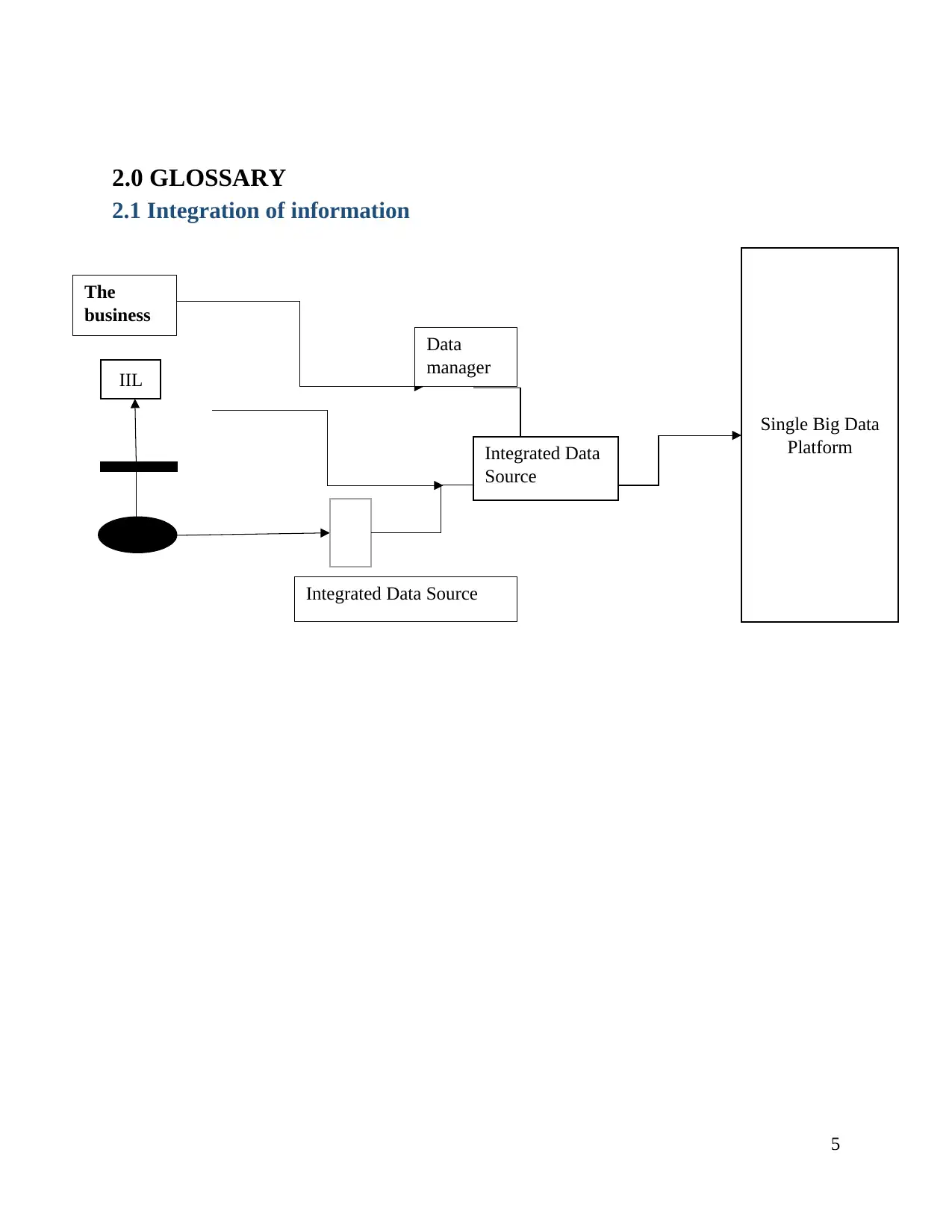
2.0 GLOSSARY
2.1 Integration of information
5
IIL
Single Big Data
Platform
The
business
case
Integrated Data
Source
Data
manager
Integrated Data Source
2.1 Integration of information
5
IIL
Single Big Data
Platform
The
business
case
Integrated Data
Source
Data
manager
Integrated Data Source
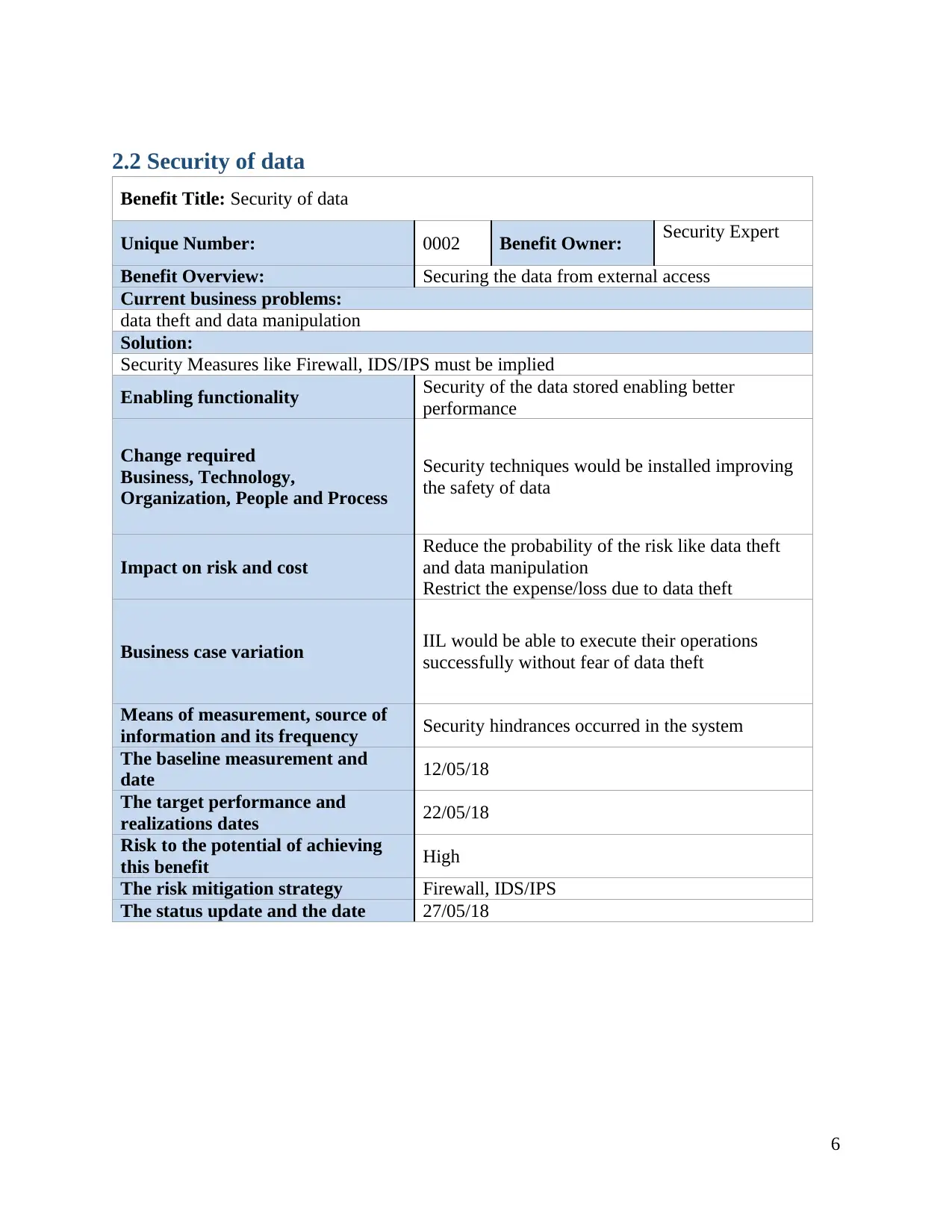
2.2 Security of data
Benefit Title: Security of data
Unique Number: 0002 Benefit Owner: Security Expert
Benefit Overview: Securing the data from external access
Current business problems:
data theft and data manipulation
Solution:
Security Measures like Firewall, IDS/IPS must be implied
Enabling functionality Security of the data stored enabling better
performance
Change required
Business, Technology,
Organization, People and Process
Security techniques would be installed improving
the safety of data
Impact on risk and cost
Reduce the probability of the risk like data theft
and data manipulation
Restrict the expense/loss due to data theft
Business case variation IIL would be able to execute their operations
successfully without fear of data theft
Means of measurement, source of
information and its frequency Security hindrances occurred in the system
The baseline measurement and
date 12/05/18
The target performance and
realizations dates 22/05/18
Risk to the potential of achieving
this benefit High
The risk mitigation strategy Firewall, IDS/IPS
The status update and the date 27/05/18
6
Benefit Title: Security of data
Unique Number: 0002 Benefit Owner: Security Expert
Benefit Overview: Securing the data from external access
Current business problems:
data theft and data manipulation
Solution:
Security Measures like Firewall, IDS/IPS must be implied
Enabling functionality Security of the data stored enabling better
performance
Change required
Business, Technology,
Organization, People and Process
Security techniques would be installed improving
the safety of data
Impact on risk and cost
Reduce the probability of the risk like data theft
and data manipulation
Restrict the expense/loss due to data theft
Business case variation IIL would be able to execute their operations
successfully without fear of data theft
Means of measurement, source of
information and its frequency Security hindrances occurred in the system
The baseline measurement and
date 12/05/18
The target performance and
realizations dates 22/05/18
Risk to the potential of achieving
this benefit High
The risk mitigation strategy Firewall, IDS/IPS
The status update and the date 27/05/18
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
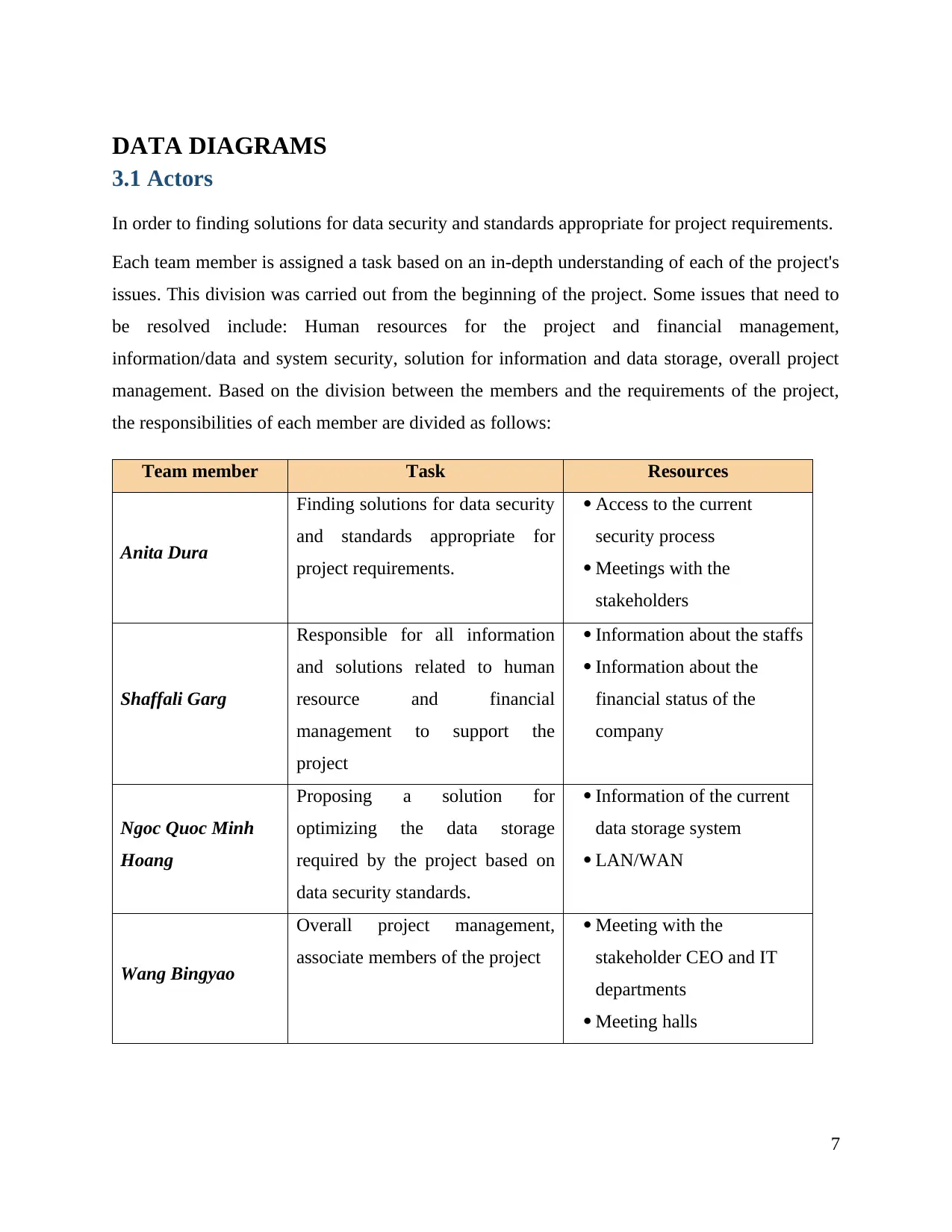
DATA DIAGRAMS
3.1 Actors
In order to finding solutions for data security and standards appropriate for project requirements.
Each team member is assigned a task based on an in-depth understanding of each of the project's
issues. This division was carried out from the beginning of the project. Some issues that need to
be resolved include: Human resources for the project and financial management,
information/data and system security, solution for information and data storage, overall project
management. Based on the division between the members and the requirements of the project,
the responsibilities of each member are divided as follows:
Team member Task Resources
Anita Dura
Finding solutions for data security
and standards appropriate for
project requirements.
Access to the current
security process
Meetings with the
stakeholders
Shaffali Garg
Responsible for all information
and solutions related to human
resource and financial
management to support the
project
Information about the staffs
Information about the
financial status of the
company
Ngoc Quoc Minh
Hoang
Proposing a solution for
optimizing the data storage
required by the project based on
data security standards.
Information of the current
data storage system
LAN/WAN
Wang Bingyao
Overall project management,
associate members of the project
Meeting with the
stakeholder CEO and IT
departments
Meeting halls
7
3.1 Actors
In order to finding solutions for data security and standards appropriate for project requirements.
Each team member is assigned a task based on an in-depth understanding of each of the project's
issues. This division was carried out from the beginning of the project. Some issues that need to
be resolved include: Human resources for the project and financial management,
information/data and system security, solution for information and data storage, overall project
management. Based on the division between the members and the requirements of the project,
the responsibilities of each member are divided as follows:
Team member Task Resources
Anita Dura
Finding solutions for data security
and standards appropriate for
project requirements.
Access to the current
security process
Meetings with the
stakeholders
Shaffali Garg
Responsible for all information
and solutions related to human
resource and financial
management to support the
project
Information about the staffs
Information about the
financial status of the
company
Ngoc Quoc Minh
Hoang
Proposing a solution for
optimizing the data storage
required by the project based on
data security standards.
Information of the current
data storage system
LAN/WAN
Wang Bingyao
Overall project management,
associate members of the project
Meeting with the
stakeholder CEO and IT
departments
Meeting halls
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
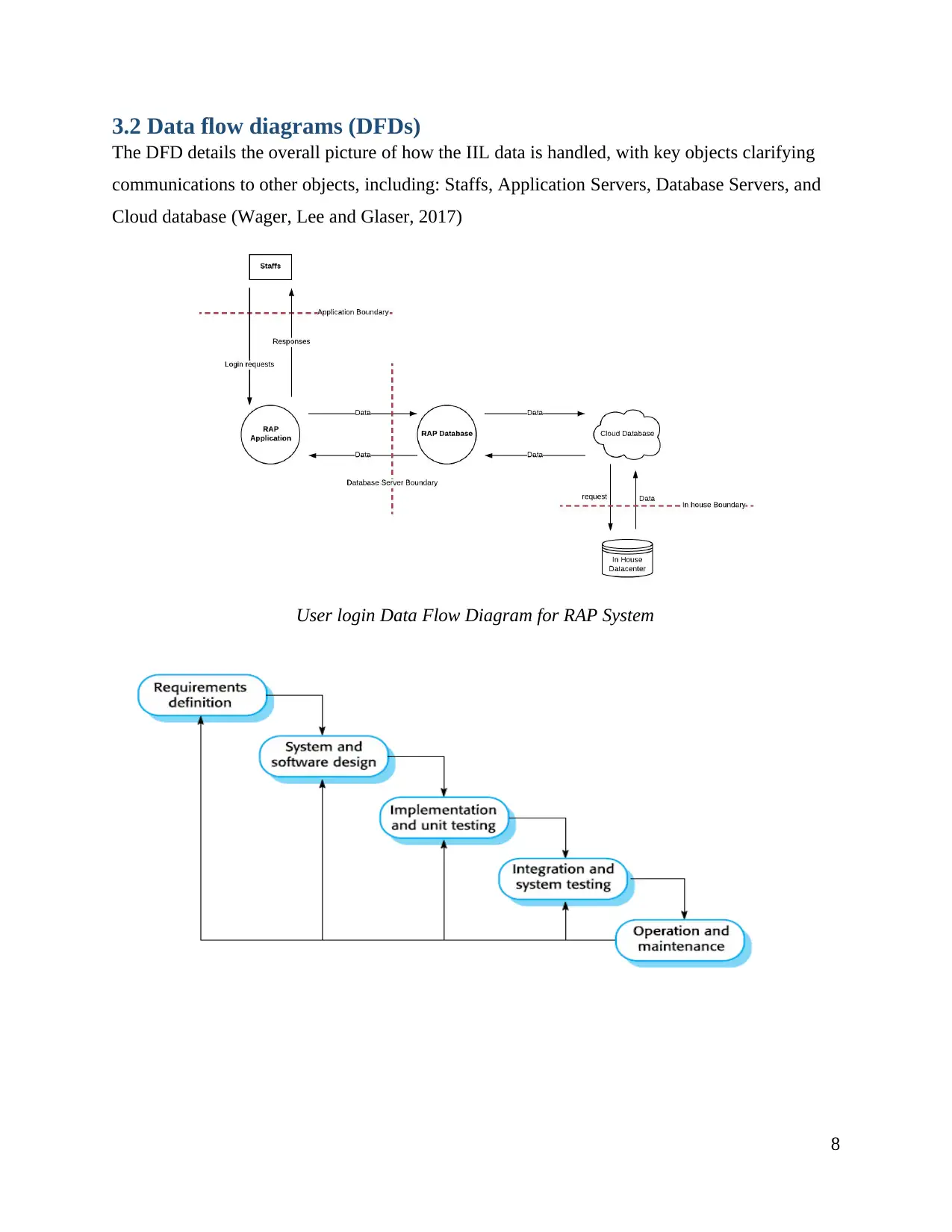
3.2 Data flow diagrams (DFDs)
The DFD details the overall picture of how the IIL data is handled, with key objects clarifying
communications to other objects, including: Staffs, Application Servers, Database Servers, and
Cloud database (Wager, Lee and Glaser, 2017)
User login Data Flow Diagram for RAP System
8
The DFD details the overall picture of how the IIL data is handled, with key objects clarifying
communications to other objects, including: Staffs, Application Servers, Database Servers, and
Cloud database (Wager, Lee and Glaser, 2017)
User login Data Flow Diagram for RAP System
8

4.0 Design overview
4.1 Solution architecture
The main project objective is to upgrade the manual data storage system of IIL with an
automation in order to improve and fasten the company’s operations and provide services to the
clients efficiently and conveniently (Marchewka, 2014)
4.1.1 Project governance process
9
4.1 Solution architecture
The main project objective is to upgrade the manual data storage system of IIL with an
automation in order to improve and fasten the company’s operations and provide services to the
clients efficiently and conveniently (Marchewka, 2014)
4.1.1 Project governance process
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
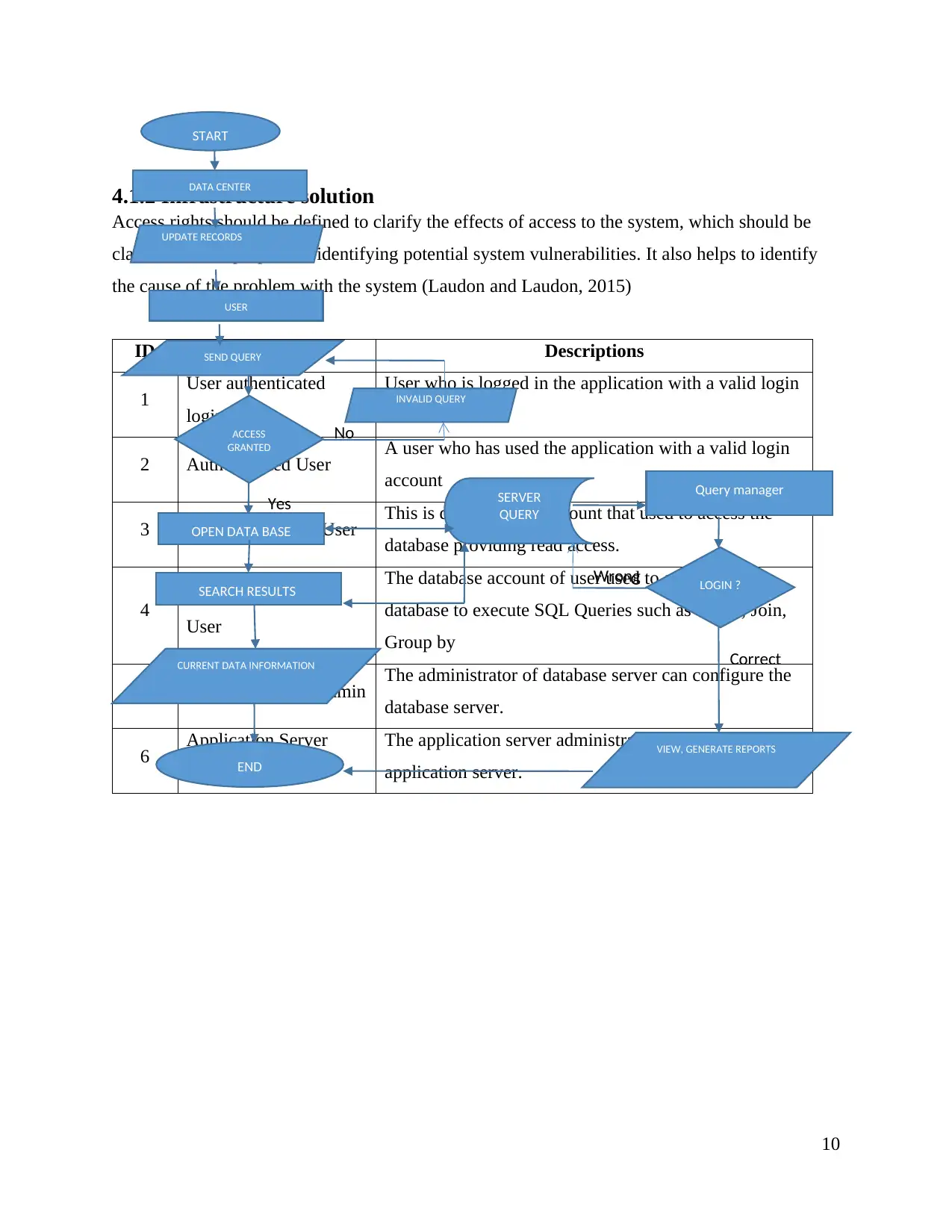
4.1.2 Infrastructure solution
Access rights should be defined to clarify the effects of access to the system, which should be
clarified for the purpose of identifying potential system vulnerabilities. It also helps to identify
the cause of the problem with the system (Laudon and Laudon, 2015)
ID Name Descriptions
1 User authenticated
login
User who is logged in the application with a valid login
account
2 Authenticated User A user who has used the application with a valid login
account
3 Database to Read User This is database user account that used to access the
database providing read access.
4 Database Execution
User
The database account of user used to access the
database to execute SQL Queries such as Select, Join,
Group by
5 Database-Server Admin The administrator of database server can configure the
database server.
6 Application Server
Administrator
The application server administrator can configure the
application server.
10
Yes
No
Wrong
Correct
START
OPEN DATA BASE
END
ACCESS
GRANTED
SERVER
QUERY
SEARCH RESULTS
SEND QUERY
CURRENT DATA INFORMATION
INVALID QUERY
UPDATE RECORDS
DATA CENTER
Query manager
USER
LOGIN ?
VIEW, GENERATE REPORTS
Access rights should be defined to clarify the effects of access to the system, which should be
clarified for the purpose of identifying potential system vulnerabilities. It also helps to identify
the cause of the problem with the system (Laudon and Laudon, 2015)
ID Name Descriptions
1 User authenticated
login
User who is logged in the application with a valid login
account
2 Authenticated User A user who has used the application with a valid login
account
3 Database to Read User This is database user account that used to access the
database providing read access.
4 Database Execution
User
The database account of user used to access the
database to execute SQL Queries such as Select, Join,
Group by
5 Database-Server Admin The administrator of database server can configure the
database server.
6 Application Server
Administrator
The application server administrator can configure the
application server.
10
Yes
No
Wrong
Correct
START
OPEN DATA BASE
END
ACCESS
GRANTED
SERVER
QUERY
SEARCH RESULTS
SEND QUERY
CURRENT DATA INFORMATION
INVALID QUERY
UPDATE RECORDS
DATA CENTER
Query manager
USER
LOGIN ?
VIEW, GENERATE REPORTS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SYSTEM OBJECT MODEL
5.1 Sub-systems
The main project objective is to upgrade the manual data storage system of IIL with an
automation in order to improve and fasten the company’s operations and provide services to the
clients efficiently and conveniently.
5.2 Sub-system interfaces
Due to the manual system of IIL, the storage operation has been causing a problem as per the
increasing number of clients since then the operations and services to the clients has been slow.
To overcome all these causing factors a lot of automation in this current system is required.
Thus, a cloud system is the main solutions in which the research is going to be done in order to
meet the company’s need and customer’s requirement. The budget limitations of this project is
approximately or -/+ 5 millions AUD and the duration to complete the project is 2- 3 months
(Kerzner and Kerzner, 2017)
Fig: Gantt chart of IIL upgrading storage system
11
5.1 Sub-systems
The main project objective is to upgrade the manual data storage system of IIL with an
automation in order to improve and fasten the company’s operations and provide services to the
clients efficiently and conveniently.
5.2 Sub-system interfaces
Due to the manual system of IIL, the storage operation has been causing a problem as per the
increasing number of clients since then the operations and services to the clients has been slow.
To overcome all these causing factors a lot of automation in this current system is required.
Thus, a cloud system is the main solutions in which the research is going to be done in order to
meet the company’s need and customer’s requirement. The budget limitations of this project is
approximately or -/+ 5 millions AUD and the duration to complete the project is 2- 3 months
(Kerzner and Kerzner, 2017)
Fig: Gantt chart of IIL upgrading storage system
11
OBJECT COLLABORATION
6.1 Collaboration Diagram
Team member Task Resources
Anita Dura
Finding solutions for data security
and standards appropriate for
project requirements.
Access to the current
security process
Meetings with the
stakeholders
Shaffali Garg
Responsible for all information
and solutions related to human
resource and financial
management to support the
project
Information about the staffs
Information about the
financial status of the
company
Ngoc Quoc Minh
Hoang
Proposing a solution for
optimizing the data storage
required by the project based on
data security standards.
Information of the current
data storage system
LAN/WAN
Wang Bingyao
Overall project management,
associate members of the project
Meeting with the
stakeholder CEO and IT
departments
Meeting halls
12
6.1 Collaboration Diagram
Team member Task Resources
Anita Dura
Finding solutions for data security
and standards appropriate for
project requirements.
Access to the current
security process
Meetings with the
stakeholders
Shaffali Garg
Responsible for all information
and solutions related to human
resource and financial
management to support the
project
Information about the staffs
Information about the
financial status of the
company
Ngoc Quoc Minh
Hoang
Proposing a solution for
optimizing the data storage
required by the project based on
data security standards.
Information of the current
data storage system
LAN/WAN
Wang Bingyao
Overall project management,
associate members of the project
Meeting with the
stakeholder CEO and IT
departments
Meeting halls
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





