Implementation of Hospital Data Storage System: A Detailed Report
VerifiedAdded on 2020/02/24
|14
|4621
|110
Report
AI Summary
This report provides a comprehensive analysis of implementing a new in-patient data storage system within a hospital setting. It begins with an introduction to the utilization of Information and Communication Technologies (ICTs) in healthcare, emphasizing the benefits of Patient Health Information Systems (PHIS) for improved patient care and operational efficiency. The report delves into the complexities of adopting such systems, including the transition from paper-based records to digital formats, and discusses different levels of maturity in technology adoption, referencing the Capability Maturity Model (CMM) and HIMSS EMR Adoption Model. It highlights the advantages of Electronic Health Records (EHRs), such as enhanced data collection, improved productivity, and reduced errors, while also acknowledging potential drawbacks like data access issues. The report then focuses on Risk Management Planning, outlining the essential steps involved in identifying, assessing, and mitigating risks associated with the implementation of a new data storage system. It covers risk identification techniques, assessment methods, and the development of a comprehensive risk management plan, including mitigation strategies and contingency planning. The report emphasizes the importance of proactive risk management to ensure a successful and beneficial implementation of the new in-patient data storage system, leading to improved healthcare services and patient outcomes.

Implementation of a new in-Patient data storing system for hospitals
[Name]
[Name]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Implementation of a new in-Patient data storing system for hospitals
Contents
Introduction................................................................................................................................1
Patient Health Information System............................................................................................2
Risk Management Planning.......................................................................................................4
Project System boundaries.........................................................................................................5
Risk Management Alternatives..................................................................................................6
Risk management plan...............................................................................................................8
Conclusions..............................................................................................................................10
References................................................................................................................................11
2
Contents
Introduction................................................................................................................................1
Patient Health Information System............................................................................................2
Risk Management Planning.......................................................................................................4
Project System boundaries.........................................................................................................5
Risk Management Alternatives..................................................................................................6
Risk management plan...............................................................................................................8
Conclusions..............................................................................................................................10
References................................................................................................................................11
2

Implementation of a new in-Patient data storing system for hospitals
Introduction
Information and communication technologies (ICTs) are used for enhancing health
information system such that quality of health services can be improved. Patient information
systems can be used for tracking health issues of patients which can act as inputs for
diagnostic tools that bring insights for patients helping them in identifying treatment to
improve their health conditions. This information system can be very useful for treating
chronic and acute health illnesses.
In the past few years, there have been many technological advances happening in the health
space that are bringing better healthcare services and benefits for patients. Electronic medical
records were introduced in health systems across countries initially at a low level as they
needed significant investments to be made for implementations as well needed a large
number of resources including working labour, finance, and technology. Thus, developing
countries or low income countries like India and China were unable to adapt to these
practices until International Organization for Standardization (ISO) came u with health
architecture that brought a level of maturity in the health system component to reduce gaps in
requirements and capacities. With this, many organizations stared to adopt health storage
technologies using computers for recording data and making electronic transmissions of the
health records. The health architecture provides standards for data interoperability,
messaging, data management and vocabulary that are very important blocks in a health care
system (Spohr, 2012).
The storage systems allow hospital management to access the aggregated data of the patients
in addition to the individual patient health information that brings them opportunities to
enhance services in general for most patients thereby improving their healthcare services in
response to getting the insights from the health records.
This report is going to explore the case of a hospital that is planning to adopt a new in-patient
data storage system as a part of their healthcare management systems. While the system
would bring many benefits for the hospital management as well as patients as already
discovered, there are also some likely risks that can affect the development, implementation,
and operations of the new healthcare storage system considering that is going to be a huge
ICT project for the hospital organization. It is essential to identify the kinds of risks that the
hospital management or systems can face in case of the storage system project so that
appropriate solutions can be determined that can help either avoid the situation of risk or
mitigate its impacts to minimize the possible losses occurring because of these risks.
Patient Health Information System
A survey conducted on hospitals by WHO on the use of ICT in the healthcare system found
that a huge amount of the information that is valuable for the healthcare organizations come
from patient encounters with the health professionals and this data is collected from the
patient over the time of his or her interaction with the hospital and healthcare professionals.
This data obtained from patients can be aggregated based on which decisions can be taken by
3
Introduction
Information and communication technologies (ICTs) are used for enhancing health
information system such that quality of health services can be improved. Patient information
systems can be used for tracking health issues of patients which can act as inputs for
diagnostic tools that bring insights for patients helping them in identifying treatment to
improve their health conditions. This information system can be very useful for treating
chronic and acute health illnesses.
In the past few years, there have been many technological advances happening in the health
space that are bringing better healthcare services and benefits for patients. Electronic medical
records were introduced in health systems across countries initially at a low level as they
needed significant investments to be made for implementations as well needed a large
number of resources including working labour, finance, and technology. Thus, developing
countries or low income countries like India and China were unable to adapt to these
practices until International Organization for Standardization (ISO) came u with health
architecture that brought a level of maturity in the health system component to reduce gaps in
requirements and capacities. With this, many organizations stared to adopt health storage
technologies using computers for recording data and making electronic transmissions of the
health records. The health architecture provides standards for data interoperability,
messaging, data management and vocabulary that are very important blocks in a health care
system (Spohr, 2012).
The storage systems allow hospital management to access the aggregated data of the patients
in addition to the individual patient health information that brings them opportunities to
enhance services in general for most patients thereby improving their healthcare services in
response to getting the insights from the health records.
This report is going to explore the case of a hospital that is planning to adopt a new in-patient
data storage system as a part of their healthcare management systems. While the system
would bring many benefits for the hospital management as well as patients as already
discovered, there are also some likely risks that can affect the development, implementation,
and operations of the new healthcare storage system considering that is going to be a huge
ICT project for the hospital organization. It is essential to identify the kinds of risks that the
hospital management or systems can face in case of the storage system project so that
appropriate solutions can be determined that can help either avoid the situation of risk or
mitigate its impacts to minimize the possible losses occurring because of these risks.
Patient Health Information System
A survey conducted on hospitals by WHO on the use of ICT in the healthcare system found
that a huge amount of the information that is valuable for the healthcare organizations come
from patient encounters with the health professionals and this data is collected from the
patient over the time of his or her interaction with the hospital and healthcare professionals.
This data obtained from patients can be aggregated based on which decisions can be taken by
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Implementation of a new in-Patient data storing system for hospitals
a hospital authority or the healthcare professional on general patient healthcare or on
individual cases of patients’ This needs resource management, monitoring, evaluation,
surveillance, and operational research.
The data collected by healthcare professionals during the interaction with patients can be
recorded in the storage systems such that it can be accessed, analysed and shared to give the
personalized attention and care to the patient at a higher level.
Electronic patient information systems can help hospitals improve their quality of services as
well as reduce their costs with improved patient information. However, when a new
organization is adopting health information or storage system, it needs them to convert their
paper records to digital records which can be very challenging. The adoption of the
technology in a hospital can happen at different levels of maturity as defined in the Capability
Maturity Model (CMM) and these include
initial level where individuals take initiative for adoption, at this level of early
awareness some basic storage systems may be used by the hospital management,
repeatable in which processes can be repeated with repeated outcomes received,
defined in which the hospital has a standard process defined for adoption, the hospital
would have standard set of guidelines adopted for managing data, services and
business processes,
managed in which the hospital not just has a standard process for adoption but also
metrics for measurement of the performance of the output, the hospital would have
some definite interoperability goals such as adoption of specific standards and shared
understanding of the internal processes or data services,
measured in which organization would have the established processes for
measurement of the interoperability in the health organization, and
Lastly, optimized that involves deliberate processes implemented for optimization or
improvement which is facilitated by monitoring and feedback processes (Đurković &
Raković, 2009).
There are also some other technology adoption models that have been identified in the
healthcare space such as HIMSS EMR Adoption Model which focuses on the management of
the information of the hospital patient. It has levels from 0 to 7 beginning with some level of
4
a hospital authority or the healthcare professional on general patient healthcare or on
individual cases of patients’ This needs resource management, monitoring, evaluation,
surveillance, and operational research.
The data collected by healthcare professionals during the interaction with patients can be
recorded in the storage systems such that it can be accessed, analysed and shared to give the
personalized attention and care to the patient at a higher level.
Electronic patient information systems can help hospitals improve their quality of services as
well as reduce their costs with improved patient information. However, when a new
organization is adopting health information or storage system, it needs them to convert their
paper records to digital records which can be very challenging. The adoption of the
technology in a hospital can happen at different levels of maturity as defined in the Capability
Maturity Model (CMM) and these include
initial level where individuals take initiative for adoption, at this level of early
awareness some basic storage systems may be used by the hospital management,
repeatable in which processes can be repeated with repeated outcomes received,
defined in which the hospital has a standard process defined for adoption, the hospital
would have standard set of guidelines adopted for managing data, services and
business processes,
managed in which the hospital not just has a standard process for adoption but also
metrics for measurement of the performance of the output, the hospital would have
some definite interoperability goals such as adoption of specific standards and shared
understanding of the internal processes or data services,
measured in which organization would have the established processes for
measurement of the interoperability in the health organization, and
Lastly, optimized that involves deliberate processes implemented for optimization or
improvement which is facilitated by monitoring and feedback processes (Đurković &
Raković, 2009).
There are also some other technology adoption models that have been identified in the
healthcare space such as HIMSS EMR Adoption Model which focuses on the management of
the information of the hospital patient. It has levels from 0 to 7 beginning with some level of
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Implementation of a new in-Patient data storing system for hospitals
clinical automation, and is followed by establishing of a laboratory or a pharmacy, clinical
document repository, clinical documentations like flow sheets and vital signs, decision
support capacities that have evidence based protocols for medicine prescriptions, closed loop
administrative environment providing patient service area, full documentation and charting of
patient data, and implementation of a paperless EMR environment in which electronic
records can be maintained as well as shared. There are a very few hospitals that have reached
the stage seven of complete paperless environment.
There are several benefits of having electronic health records in a hospital such as improved
patient data collection, enhanced productivity of the hospital, better and real time access to
data, reduced human errors, efficient usage of time, increased satisfaction in hospital visitors,
improved communication within and with patients, and increased rate of immunization. HRs
have been observed to bring improvements in diabetes care, preventive care service such as
vaccination and occult blood testing, and establishing a culture of improvement in the
organization for services. However, when observing the implementations happened in various
hospitals, there were some disadvantages observed with this adoption such as slow access to
the data, more time consuming data entry process and reduction in the quality of interaction
between the patient and the doctor.
Mobile based healthcare system is another growing area of development in the healthcare
system that makes the patient information portal which is very useful considering the fact that
a patient may not have only a single touch point with the hospital and thus, data may be
collected from patients using a distributed healthcare network with mHealth systems. This
would improve data collection capability of the hospital as well as would improve the quality
of healthcare, safety and effectiveness of the system.
Risk Management Planning
Risk management is not a new practice and there are many tools as well as techniques that
are available for identifying and managing risks in the information system development. With
respect to information system, a risk can be considered as anything that can potentially cause
harm in the future because of certain actions happening in the present. Risk management is
about understanding as well as responding to the factors that can lead to the failure of security
aspects such as integrity, confidentiality, and availability or any other harm happening to the
organization that is using an information system.
Risk management plans are developed for identification of risks and for planning the
response to those risks. The risk management process in any system development project
would go through a series of processes including establishing of context, identification of
risks, assessment of risks, identification of risk treatments or responses, creation of a risk
management plan, implementation of the risk management plan and its evaluation.
Establishing context: In the initial stage of risk management, potentials risks on projects are
identified and documented. This stage involves determination of the social scope of risk,
objectives of the project stakeholders, availability of resources that could help mitigate the
5
clinical automation, and is followed by establishing of a laboratory or a pharmacy, clinical
document repository, clinical documentations like flow sheets and vital signs, decision
support capacities that have evidence based protocols for medicine prescriptions, closed loop
administrative environment providing patient service area, full documentation and charting of
patient data, and implementation of a paperless EMR environment in which electronic
records can be maintained as well as shared. There are a very few hospitals that have reached
the stage seven of complete paperless environment.
There are several benefits of having electronic health records in a hospital such as improved
patient data collection, enhanced productivity of the hospital, better and real time access to
data, reduced human errors, efficient usage of time, increased satisfaction in hospital visitors,
improved communication within and with patients, and increased rate of immunization. HRs
have been observed to bring improvements in diabetes care, preventive care service such as
vaccination and occult blood testing, and establishing a culture of improvement in the
organization for services. However, when observing the implementations happened in various
hospitals, there were some disadvantages observed with this adoption such as slow access to
the data, more time consuming data entry process and reduction in the quality of interaction
between the patient and the doctor.
Mobile based healthcare system is another growing area of development in the healthcare
system that makes the patient information portal which is very useful considering the fact that
a patient may not have only a single touch point with the hospital and thus, data may be
collected from patients using a distributed healthcare network with mHealth systems. This
would improve data collection capability of the hospital as well as would improve the quality
of healthcare, safety and effectiveness of the system.
Risk Management Planning
Risk management is not a new practice and there are many tools as well as techniques that
are available for identifying and managing risks in the information system development. With
respect to information system, a risk can be considered as anything that can potentially cause
harm in the future because of certain actions happening in the present. Risk management is
about understanding as well as responding to the factors that can lead to the failure of security
aspects such as integrity, confidentiality, and availability or any other harm happening to the
organization that is using an information system.
Risk management plans are developed for identification of risks and for planning the
response to those risks. The risk management process in any system development project
would go through a series of processes including establishing of context, identification of
risks, assessment of risks, identification of risk treatments or responses, creation of a risk
management plan, implementation of the risk management plan and its evaluation.
Establishing context: In the initial stage of risk management, potentials risks on projects are
identified and documented. This stage involves determination of the social scope of risk,
objectives of the project stakeholders, availability of resources that could help mitigate the
5

Implementation of a new in-Patient data storing system for hospitals
risk impacts, and the existing structures in the organization or the hospital that can be used
for risk management.
Risk Identification: Problems arising from risks can be effectively addressed if their causes
are known at a granular level. A range of threats can arise from risks such as loss of money,
loss of staff, loss of data, loss of property, and so on. These risks can be classified in several
ways such as based on impact factors into operational, personnel, property related, program
related, and so on. Risks can be identified using major risk impact areas such as use of
unproven technologies, system requirements, software architecture, system performance and
organizational areas of development (Boban, et al., 2003).
Risk Assessment: At this stage, risks are assessed using a grading system in which the
probability of occurrence of risk and the level of the severity of the impacts caused by risks
are calculated such that results would help in prioritizing risks (Trahan, et al., 2012).
Risk response: A risk can be responded to by avoiding it, reducing its impacts through
mitigation, transferring the resulting loss to the partner, or retaining the risks when the losses
are not very significant. A choice can be made based on the assessment of risk and the
situation. The response is also affected by the level of tolerance of the risk which can be high
in which case, the risk cannot be retained and has to be avoided but if low then it can be.
Risk Management Plan: Once the risk response is identified, appropriate control or
countermeasures are selected and risk management plan is developed. This plan usually
involves creation of a risk management table containing details of risks, their likelihood of
occurrence, level of severity of impact, risk assessment ranking, current status of risk,
response action to be taken, who would be responsible for action, and the cost it would incur.
Once the plan is developed and approved, it is implemented in an organization post which the
outcomes are evaluated and reviewed to bring continuous improvement (John Snow, Inc.,
2010).
The two most important parts of the risk management planning are the identification of risks
and mitigation strategies as they would determine what needs to be done while implementing
the plan such that risks can be reduced. Risks can be known or unknown and the risk
management plan can identify the known risks for proactive management through preventive
actions while unknown risks can be handled by contingency planning. There are a variety of
risk identification techniques available such as Delphi technique, Flowcharting, root cause
analysis, Brainstorming, SWOT analysis, Cause and Effective analysis, Influence
diagramming, and interviewing.
There can be two types of mitigation strategies that include preventive actions that are
intended to reduce the likelihood of the occurrence of the risk and contingency which deals
with the actions that would reduce the severity of the impact of the risk (Tasmania
Government, 2008).
Risk response is largely dependent on the risk assessment results as they help in classifying
and prioritising risks. The assessment involves analysis of the identified risks which can be
6
risk impacts, and the existing structures in the organization or the hospital that can be used
for risk management.
Risk Identification: Problems arising from risks can be effectively addressed if their causes
are known at a granular level. A range of threats can arise from risks such as loss of money,
loss of staff, loss of data, loss of property, and so on. These risks can be classified in several
ways such as based on impact factors into operational, personnel, property related, program
related, and so on. Risks can be identified using major risk impact areas such as use of
unproven technologies, system requirements, software architecture, system performance and
organizational areas of development (Boban, et al., 2003).
Risk Assessment: At this stage, risks are assessed using a grading system in which the
probability of occurrence of risk and the level of the severity of the impacts caused by risks
are calculated such that results would help in prioritizing risks (Trahan, et al., 2012).
Risk response: A risk can be responded to by avoiding it, reducing its impacts through
mitigation, transferring the resulting loss to the partner, or retaining the risks when the losses
are not very significant. A choice can be made based on the assessment of risk and the
situation. The response is also affected by the level of tolerance of the risk which can be high
in which case, the risk cannot be retained and has to be avoided but if low then it can be.
Risk Management Plan: Once the risk response is identified, appropriate control or
countermeasures are selected and risk management plan is developed. This plan usually
involves creation of a risk management table containing details of risks, their likelihood of
occurrence, level of severity of impact, risk assessment ranking, current status of risk,
response action to be taken, who would be responsible for action, and the cost it would incur.
Once the plan is developed and approved, it is implemented in an organization post which the
outcomes are evaluated and reviewed to bring continuous improvement (John Snow, Inc.,
2010).
The two most important parts of the risk management planning are the identification of risks
and mitigation strategies as they would determine what needs to be done while implementing
the plan such that risks can be reduced. Risks can be known or unknown and the risk
management plan can identify the known risks for proactive management through preventive
actions while unknown risks can be handled by contingency planning. There are a variety of
risk identification techniques available such as Delphi technique, Flowcharting, root cause
analysis, Brainstorming, SWOT analysis, Cause and Effective analysis, Influence
diagramming, and interviewing.
There can be two types of mitigation strategies that include preventive actions that are
intended to reduce the likelihood of the occurrence of the risk and contingency which deals
with the actions that would reduce the severity of the impact of the risk (Tasmania
Government, 2008).
Risk response is largely dependent on the risk assessment results as they help in classifying
and prioritising risks. The assessment involves analysis of the identified risks which can be
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Implementation of a new in-Patient data storing system for hospitals
either qualitative or quantitative. Qualitative analysis involved development of priorities
based on several factors like probability of occurrence of the risk, corresponding impact, and
other factors like risk tolerance of the project, time frame, project cost, schedule, quality
requirements and project scope. There are several techniques available to be used for this
analysis such as process assessment, probability distribution, impact analysis, sensitivity
analysis, modelling, and simulation and decision tree analysis (Farahmand, 2004).
A risk management plan documents the entire risk management process as it would be
followed. The risk management plan mainly addresses following:
Risk Management Procedures: The plan includes a summary of how risk management
processes would be performed by explaining steps involved, approaches that would be used
for identification of risk such as technical, managerial, and political, approaches that would
be used for risk assessment including qualitative and quantitative risk analyses, response to
each identified risk including mitigation and contingency measures, and approaches to risk
monitoring, control, and reporting.
Risk Management Tools: If there are any tools that would be used for recording the risk
logs such as risk register then the same also has to be explained in the risk management plan.
Project System boundaries
The objective of this project is to develop a risk management plan for the implementation of
an in-patient data storage system. The project activities include:
Identification of trends in the use of ICT for hospitals and healthcare
Understanding of how risk management works in hospital
Exploring components of risk management including risk identification, risk
assessment, and risk response planning
Identifying risks that can occur on the project and analyse them qualitatively and
quantitatively.
Develop a risk management plan that includes risks, their ratings, and response plans
The project does not include:
Implementation plan for the in-patient data storage system that is proposed
Implementation of the risk management plan in practice
Risk Management Alternatives
After the risks are evaluated along with their probability of occurrence and the possible level
of severity of the corresponding loss, a risk management matrix can be prepared for specific
level of the risk exposure such that the frequencies or probabilities of risks occurrences are
7
either qualitative or quantitative. Qualitative analysis involved development of priorities
based on several factors like probability of occurrence of the risk, corresponding impact, and
other factors like risk tolerance of the project, time frame, project cost, schedule, quality
requirements and project scope. There are several techniques available to be used for this
analysis such as process assessment, probability distribution, impact analysis, sensitivity
analysis, modelling, and simulation and decision tree analysis (Farahmand, 2004).
A risk management plan documents the entire risk management process as it would be
followed. The risk management plan mainly addresses following:
Risk Management Procedures: The plan includes a summary of how risk management
processes would be performed by explaining steps involved, approaches that would be used
for identification of risk such as technical, managerial, and political, approaches that would
be used for risk assessment including qualitative and quantitative risk analyses, response to
each identified risk including mitigation and contingency measures, and approaches to risk
monitoring, control, and reporting.
Risk Management Tools: If there are any tools that would be used for recording the risk
logs such as risk register then the same also has to be explained in the risk management plan.
Project System boundaries
The objective of this project is to develop a risk management plan for the implementation of
an in-patient data storage system. The project activities include:
Identification of trends in the use of ICT for hospitals and healthcare
Understanding of how risk management works in hospital
Exploring components of risk management including risk identification, risk
assessment, and risk response planning
Identifying risks that can occur on the project and analyse them qualitatively and
quantitatively.
Develop a risk management plan that includes risks, their ratings, and response plans
The project does not include:
Implementation plan for the in-patient data storage system that is proposed
Implementation of the risk management plan in practice
Risk Management Alternatives
After the risks are evaluated along with their probability of occurrence and the possible level
of severity of the corresponding loss, a risk management matrix can be prepared for specific
level of the risk exposure such that the frequencies or probabilities of risks occurrences are
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
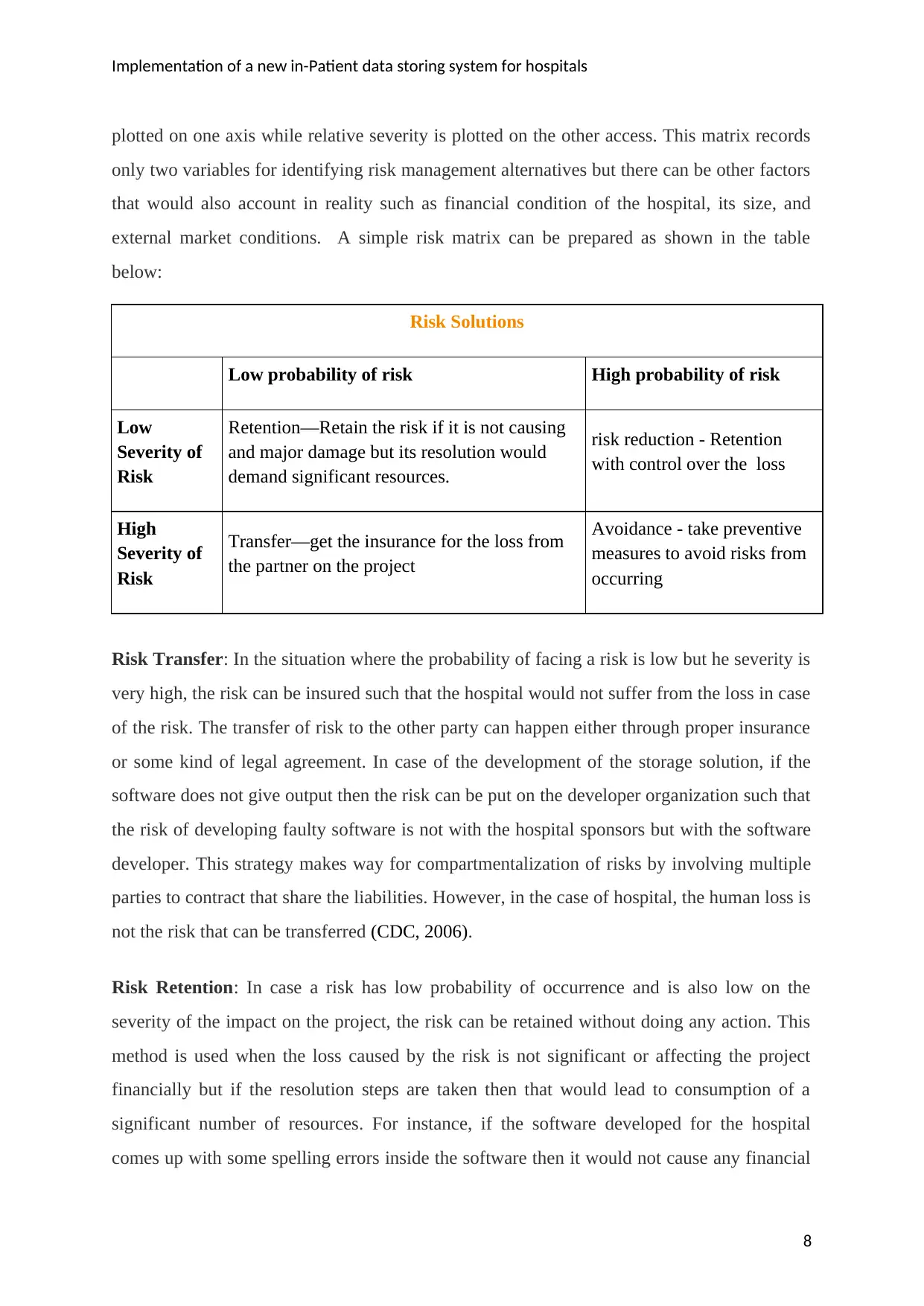
Implementation of a new in-Patient data storing system for hospitals
plotted on one axis while relative severity is plotted on the other access. This matrix records
only two variables for identifying risk management alternatives but there can be other factors
that would also account in reality such as financial condition of the hospital, its size, and
external market conditions. A simple risk matrix can be prepared as shown in the table
below:
Risk Solutions
Low probability of risk High probability of risk
Low
Severity of
Risk
Retention—Retain the risk if it is not causing
and major damage but its resolution would
demand significant resources.
risk reduction - Retention
with control over the loss
High
Severity of
Risk
Transfer—get the insurance for the loss from
the partner on the project
Avoidance - take preventive
measures to avoid risks from
occurring
Risk Transfer: In the situation where the probability of facing a risk is low but he severity is
very high, the risk can be insured such that the hospital would not suffer from the loss in case
of the risk. The transfer of risk to the other party can happen either through proper insurance
or some kind of legal agreement. In case of the development of the storage solution, if the
software does not give output then the risk can be put on the developer organization such that
the risk of developing faulty software is not with the hospital sponsors but with the software
developer. This strategy makes way for compartmentalization of risks by involving multiple
parties to contract that share the liabilities. However, in the case of hospital, the human loss is
not the risk that can be transferred (CDC, 2006).
Risk Retention: In case a risk has low probability of occurrence and is also low on the
severity of the impact on the project, the risk can be retained without doing any action. This
method is used when the loss caused by the risk is not significant or affecting the project
financially but if the resolution steps are taken then that would lead to consumption of a
significant number of resources. For instance, if the software developed for the hospital
comes up with some spelling errors inside the software then it would not cause any financial
8
plotted on one axis while relative severity is plotted on the other access. This matrix records
only two variables for identifying risk management alternatives but there can be other factors
that would also account in reality such as financial condition of the hospital, its size, and
external market conditions. A simple risk matrix can be prepared as shown in the table
below:
Risk Solutions
Low probability of risk High probability of risk
Low
Severity of
Risk
Retention—Retain the risk if it is not causing
and major damage but its resolution would
demand significant resources.
risk reduction - Retention
with control over the loss
High
Severity of
Risk
Transfer—get the insurance for the loss from
the partner on the project
Avoidance - take preventive
measures to avoid risks from
occurring
Risk Transfer: In the situation where the probability of facing a risk is low but he severity is
very high, the risk can be insured such that the hospital would not suffer from the loss in case
of the risk. The transfer of risk to the other party can happen either through proper insurance
or some kind of legal agreement. In case of the development of the storage solution, if the
software does not give output then the risk can be put on the developer organization such that
the risk of developing faulty software is not with the hospital sponsors but with the software
developer. This strategy makes way for compartmentalization of risks by involving multiple
parties to contract that share the liabilities. However, in the case of hospital, the human loss is
not the risk that can be transferred (CDC, 2006).
Risk Retention: In case a risk has low probability of occurrence and is also low on the
severity of the impact on the project, the risk can be retained without doing any action. This
method is used when the loss caused by the risk is not significant or affecting the project
financially but if the resolution steps are taken then that would lead to consumption of a
significant number of resources. For instance, if the software developed for the hospital
comes up with some spelling errors inside the software then it would not cause any financial
8

Implementation of a new in-Patient data storing system for hospitals
damage but if the same has to be corrected, the developers have to be deployed again for the
correction. Risks are also retained in the cases where the company has losses but very less
such that the risk can be tolerated. Whether the risk should be retained or not would be
determined by the tolerability of the risk such that if it is high then risk may be retained but if
it is low then either risk reduction is needed or an alternative response has to be considered
(Elky, 2007)
.
Risk reduction: When the likelihood of the occurrence of the risk is high but the severity of
its impact is low then the risks are retained but with measures taken for reduction of the risk
as it can occur more frequently causing damages to the organization in the long run. For
instance, any hospital equipment that may be used for recording the patient information or for
diagnostics can wear and tear causing losses, in such a situation, the equipment can be
maintained to ensure that the wear and tear is reduced. In this strategy, the objective of the
risk response is to reduce the probability of the occurrence of the loss. However, this
reduction cannot be used for the long run as the risk impacts can get pronounced in which
case, preventive or other measures can be taken.
Risk Avoidance: In situations where the probability of the occurrence of the risk is high as
well as the severity of the impacts is high, the risks are usually avoided by taking preventive
actions. In the case of the implementation of the patient data storage system in the hospital,
certain risks can cause major harm and the probability of their occurrence may also be high
such as incompatibility of the software with the systems used in the hospital and
incompetence of the staff to use the developed system after implementation. In both the
cases, the resolution is to avoid such risks as they can cause major damage to the project. The
issue of incompatibility can be taken care of by testing or identifying system requirements at
the time of development such that required systems are acquired before the solution is
implemented. The problem of staff competence can be avoided by providing them sufficient
training on the new system that is developed for the hospital so that they can use the same
after it is implemented and is made to go live.
9
damage but if the same has to be corrected, the developers have to be deployed again for the
correction. Risks are also retained in the cases where the company has losses but very less
such that the risk can be tolerated. Whether the risk should be retained or not would be
determined by the tolerability of the risk such that if it is high then risk may be retained but if
it is low then either risk reduction is needed or an alternative response has to be considered
(Elky, 2007)
.
Risk reduction: When the likelihood of the occurrence of the risk is high but the severity of
its impact is low then the risks are retained but with measures taken for reduction of the risk
as it can occur more frequently causing damages to the organization in the long run. For
instance, any hospital equipment that may be used for recording the patient information or for
diagnostics can wear and tear causing losses, in such a situation, the equipment can be
maintained to ensure that the wear and tear is reduced. In this strategy, the objective of the
risk response is to reduce the probability of the occurrence of the loss. However, this
reduction cannot be used for the long run as the risk impacts can get pronounced in which
case, preventive or other measures can be taken.
Risk Avoidance: In situations where the probability of the occurrence of the risk is high as
well as the severity of the impacts is high, the risks are usually avoided by taking preventive
actions. In the case of the implementation of the patient data storage system in the hospital,
certain risks can cause major harm and the probability of their occurrence may also be high
such as incompatibility of the software with the systems used in the hospital and
incompetence of the staff to use the developed system after implementation. In both the
cases, the resolution is to avoid such risks as they can cause major damage to the project. The
issue of incompatibility can be taken care of by testing or identifying system requirements at
the time of development such that required systems are acquired before the solution is
implemented. The problem of staff competence can be avoided by providing them sufficient
training on the new system that is developed for the hospital so that they can use the same
after it is implemented and is made to go live.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
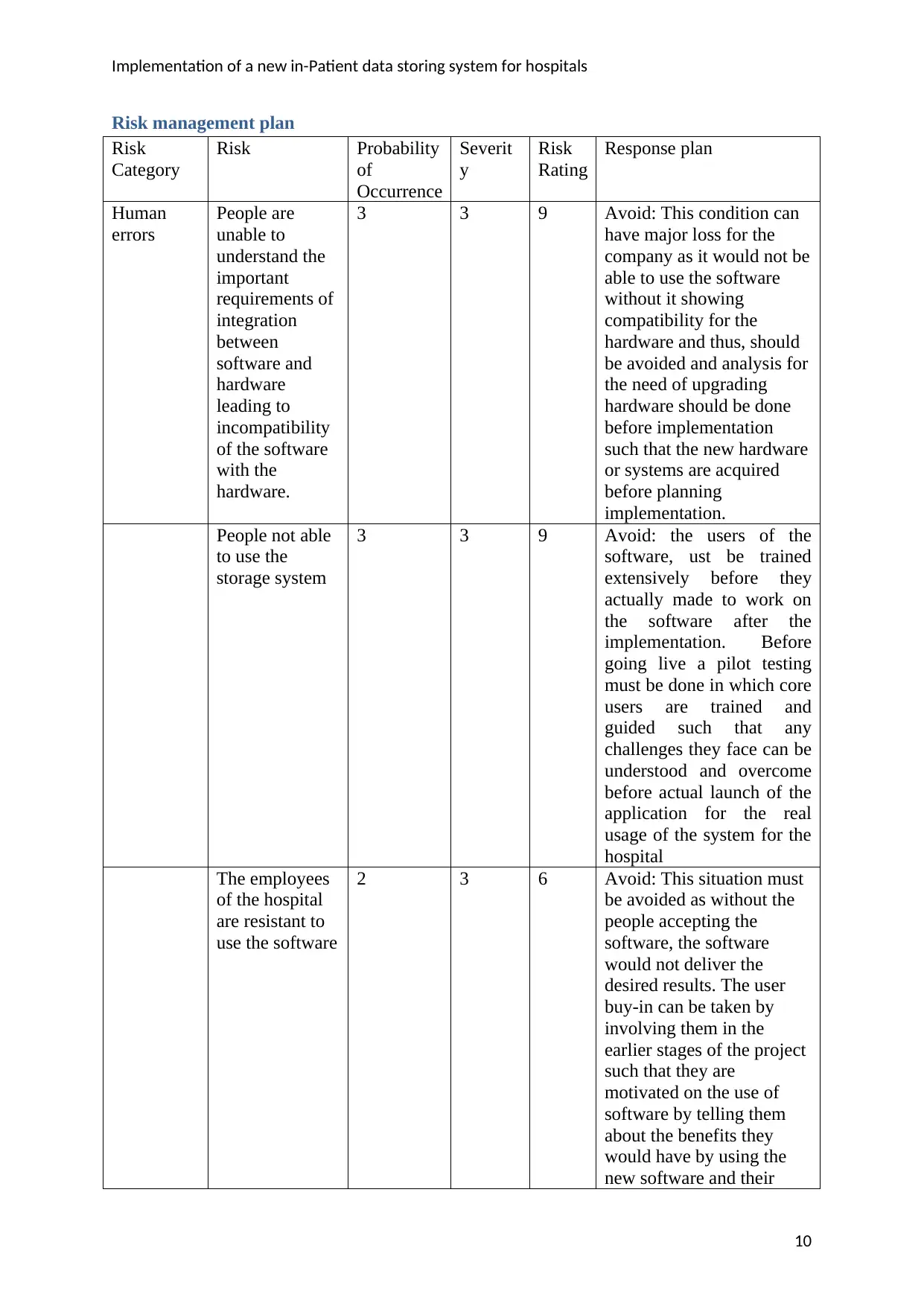
Implementation of a new in-Patient data storing system for hospitals
Risk management plan
Risk
Category
Risk Probability
of
Occurrence
Severit
y
Risk
Rating
Response plan
Human
errors
People are
unable to
understand the
important
requirements of
integration
between
software and
hardware
leading to
incompatibility
of the software
with the
hardware.
3 3 9 Avoid: This condition can
have major loss for the
company as it would not be
able to use the software
without it showing
compatibility for the
hardware and thus, should
be avoided and analysis for
the need of upgrading
hardware should be done
before implementation
such that the new hardware
or systems are acquired
before planning
implementation.
People not able
to use the
storage system
3 3 9 Avoid: the users of the
software, ust be trained
extensively before they
actually made to work on
the software after the
implementation. Before
going live a pilot testing
must be done in which core
users are trained and
guided such that any
challenges they face can be
understood and overcome
before actual launch of the
application for the real
usage of the system for the
hospital
The employees
of the hospital
are resistant to
use the software
2 3 6 Avoid: This situation must
be avoided as without the
people accepting the
software, the software
would not deliver the
desired results. The user
buy-in can be taken by
involving them in the
earlier stages of the project
such that they are
motivated on the use of
software by telling them
about the benefits they
would have by using the
new software and their
10
Risk management plan
Risk
Category
Risk Probability
of
Occurrence
Severit
y
Risk
Rating
Response plan
Human
errors
People are
unable to
understand the
important
requirements of
integration
between
software and
hardware
leading to
incompatibility
of the software
with the
hardware.
3 3 9 Avoid: This condition can
have major loss for the
company as it would not be
able to use the software
without it showing
compatibility for the
hardware and thus, should
be avoided and analysis for
the need of upgrading
hardware should be done
before implementation
such that the new hardware
or systems are acquired
before planning
implementation.
People not able
to use the
storage system
3 3 9 Avoid: the users of the
software, ust be trained
extensively before they
actually made to work on
the software after the
implementation. Before
going live a pilot testing
must be done in which core
users are trained and
guided such that any
challenges they face can be
understood and overcome
before actual launch of the
application for the real
usage of the system for the
hospital
The employees
of the hospital
are resistant to
use the software
2 3 6 Avoid: This situation must
be avoided as without the
people accepting the
software, the software
would not deliver the
desired results. The user
buy-in can be taken by
involving them in the
earlier stages of the project
such that they are
motivated on the use of
software by telling them
about the benefits they
would have by using the
new software and their
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
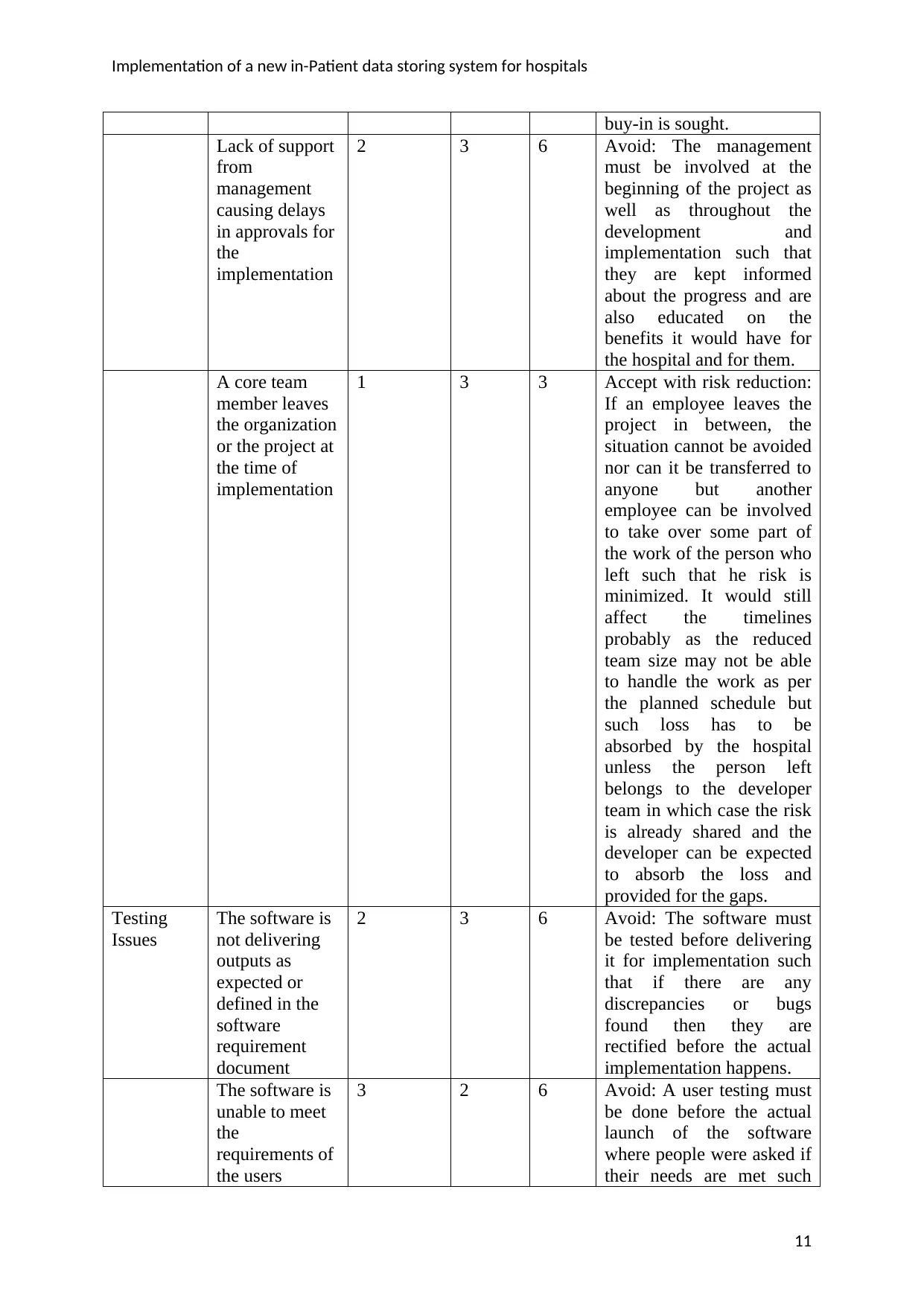
Implementation of a new in-Patient data storing system for hospitals
buy-in is sought.
Lack of support
from
management
causing delays
in approvals for
the
implementation
2 3 6 Avoid: The management
must be involved at the
beginning of the project as
well as throughout the
development and
implementation such that
they are kept informed
about the progress and are
also educated on the
benefits it would have for
the hospital and for them.
A core team
member leaves
the organization
or the project at
the time of
implementation
1 3 3 Accept with risk reduction:
If an employee leaves the
project in between, the
situation cannot be avoided
nor can it be transferred to
anyone but another
employee can be involved
to take over some part of
the work of the person who
left such that he risk is
minimized. It would still
affect the timelines
probably as the reduced
team size may not be able
to handle the work as per
the planned schedule but
such loss has to be
absorbed by the hospital
unless the person left
belongs to the developer
team in which case the risk
is already shared and the
developer can be expected
to absorb the loss and
provided for the gaps.
Testing
Issues
The software is
not delivering
outputs as
expected or
defined in the
software
requirement
document
2 3 6 Avoid: The software must
be tested before delivering
it for implementation such
that if there are any
discrepancies or bugs
found then they are
rectified before the actual
implementation happens.
The software is
unable to meet
the
requirements of
the users
3 2 6 Avoid: A user testing must
be done before the actual
launch of the software
where people were asked if
their needs are met such
11
buy-in is sought.
Lack of support
from
management
causing delays
in approvals for
the
implementation
2 3 6 Avoid: The management
must be involved at the
beginning of the project as
well as throughout the
development and
implementation such that
they are kept informed
about the progress and are
also educated on the
benefits it would have for
the hospital and for them.
A core team
member leaves
the organization
or the project at
the time of
implementation
1 3 3 Accept with risk reduction:
If an employee leaves the
project in between, the
situation cannot be avoided
nor can it be transferred to
anyone but another
employee can be involved
to take over some part of
the work of the person who
left such that he risk is
minimized. It would still
affect the timelines
probably as the reduced
team size may not be able
to handle the work as per
the planned schedule but
such loss has to be
absorbed by the hospital
unless the person left
belongs to the developer
team in which case the risk
is already shared and the
developer can be expected
to absorb the loss and
provided for the gaps.
Testing
Issues
The software is
not delivering
outputs as
expected or
defined in the
software
requirement
document
2 3 6 Avoid: The software must
be tested before delivering
it for implementation such
that if there are any
discrepancies or bugs
found then they are
rectified before the actual
implementation happens.
The software is
unable to meet
the
requirements of
the users
3 2 6 Avoid: A user testing must
be done before the actual
launch of the software
where people were asked if
their needs are met such
11
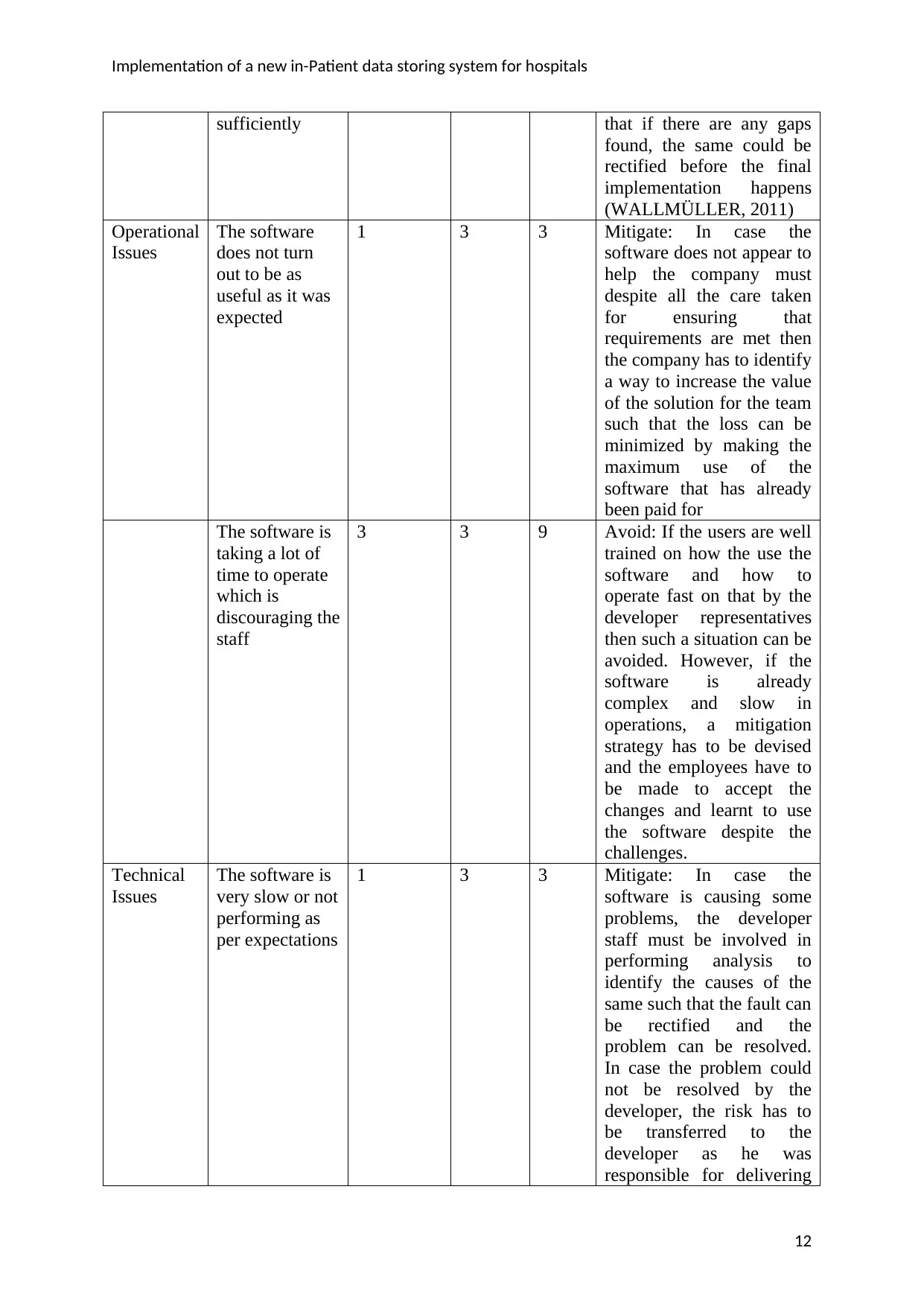
Implementation of a new in-Patient data storing system for hospitals
sufficiently that if there are any gaps
found, the same could be
rectified before the final
implementation happens
(WALLMÜLLER, 2011)
Operational
Issues
The software
does not turn
out to be as
useful as it was
expected
1 3 3 Mitigate: In case the
software does not appear to
help the company must
despite all the care taken
for ensuring that
requirements are met then
the company has to identify
a way to increase the value
of the solution for the team
such that the loss can be
minimized by making the
maximum use of the
software that has already
been paid for
The software is
taking a lot of
time to operate
which is
discouraging the
staff
3 3 9 Avoid: If the users are well
trained on how the use the
software and how to
operate fast on that by the
developer representatives
then such a situation can be
avoided. However, if the
software is already
complex and slow in
operations, a mitigation
strategy has to be devised
and the employees have to
be made to accept the
changes and learnt to use
the software despite the
challenges.
Technical
Issues
The software is
very slow or not
performing as
per expectations
1 3 3 Mitigate: In case the
software is causing some
problems, the developer
staff must be involved in
performing analysis to
identify the causes of the
same such that the fault can
be rectified and the
problem can be resolved.
In case the problem could
not be resolved by the
developer, the risk has to
be transferred to the
developer as he was
responsible for delivering
12
sufficiently that if there are any gaps
found, the same could be
rectified before the final
implementation happens
(WALLMÜLLER, 2011)
Operational
Issues
The software
does not turn
out to be as
useful as it was
expected
1 3 3 Mitigate: In case the
software does not appear to
help the company must
despite all the care taken
for ensuring that
requirements are met then
the company has to identify
a way to increase the value
of the solution for the team
such that the loss can be
minimized by making the
maximum use of the
software that has already
been paid for
The software is
taking a lot of
time to operate
which is
discouraging the
staff
3 3 9 Avoid: If the users are well
trained on how the use the
software and how to
operate fast on that by the
developer representatives
then such a situation can be
avoided. However, if the
software is already
complex and slow in
operations, a mitigation
strategy has to be devised
and the employees have to
be made to accept the
changes and learnt to use
the software despite the
challenges.
Technical
Issues
The software is
very slow or not
performing as
per expectations
1 3 3 Mitigate: In case the
software is causing some
problems, the developer
staff must be involved in
performing analysis to
identify the causes of the
same such that the fault can
be rectified and the
problem can be resolved.
In case the problem could
not be resolved by the
developer, the risk has to
be transferred to the
developer as he was
responsible for delivering
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





