MN623 T1 2020: Implementation and Evaluation of Pen Testing Tools
VerifiedAdded on 2022/09/15
|7
|969
|40
Homework Assignment
AI Summary
This assignment focuses on the implementation and evaluation of penetration testing tools within the context of cyber security and analytics. Specifically, the student explores the use of Kali Linux to build a software testing platform for password cracking tools. The assignment details the implementation and evaluation of two key tools: THC Hydra, an online cracking tool for dictionary and brute-force attacks, and John the Ripper, an open-source password cracking tool. The student emphasizes the importance of penetration testing in identifying system vulnerabilities and outlines the different phases involved, including data gathering, scanning, access gaining, maintaining access, and covering tracks. Furthermore, the assignment highlights the attributes of a good penetration testing tool, such as visibility, configurability, license flexibility, extensibility, and documentation. The student also provides references to relevant research papers and online resources.

Running head: CYBER SECURITY AND ANALYTICS
Implementation and evaluation of penetration testing tools
Name of the Student
Name of the University
Author’s Note
Implementation and evaluation of penetration testing tools
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CYBER SECURITY AND ANALYTICS
Assignment 1a: Implementation and evaluation of
5 password cracking tools in Kali Linux
Demonstration of building software testing platform for
evaluation of 2 password cracking tool
For the development of software testing platform Kali Linux is used and a research is made on the
different password cracking tool that can be used for penetration testing. The following are the two
tools that are implemented and evaluated for cracking password.
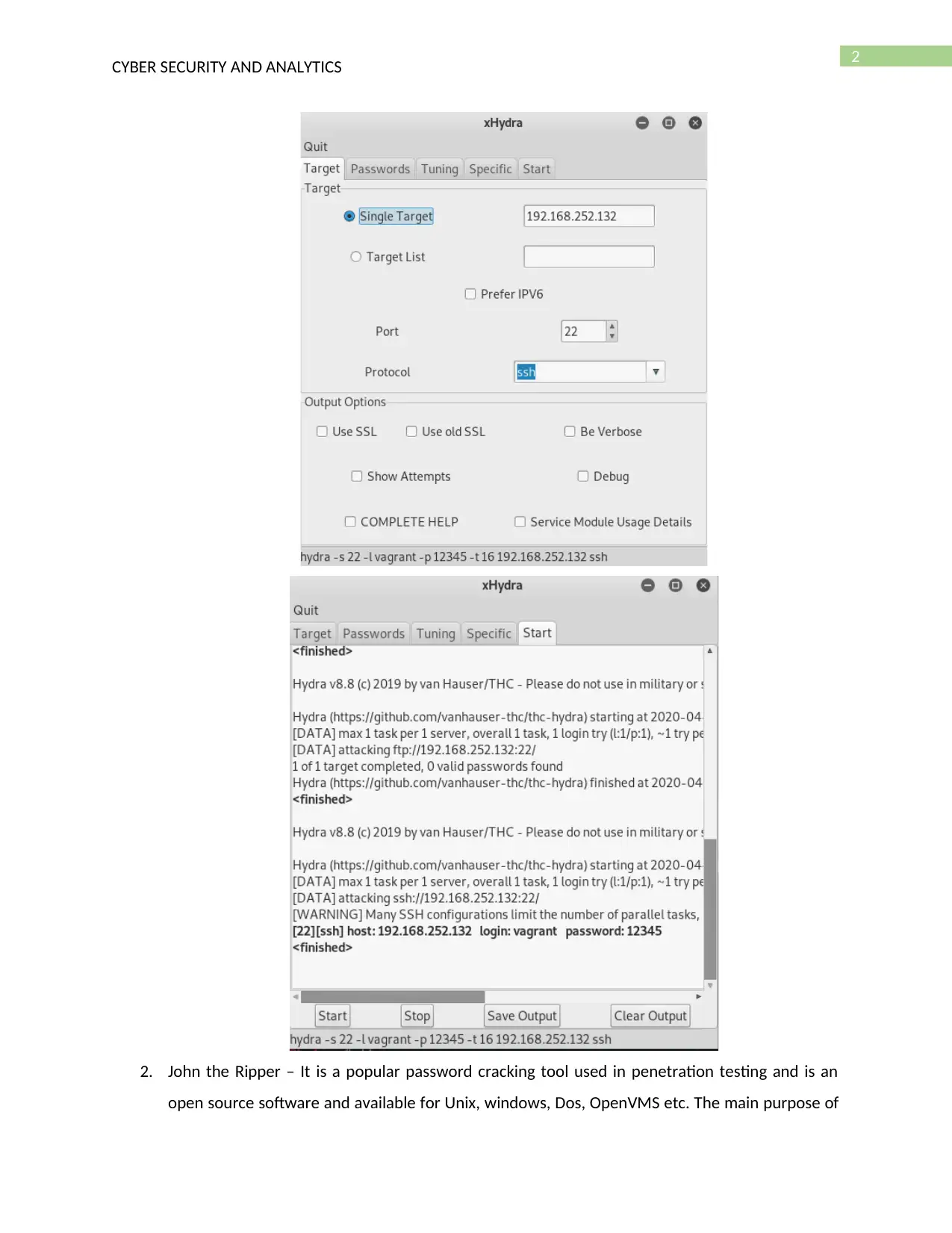
1. THC Hydra – Hydra is an online cracking tool and it is used for performing dictionary attack
rapidly against more than 50 protocols such as SSH, FTP, TELNET, HTTPS, SMB, etc. that can be
used for cracking password of database and user accounts [1]. It can be used for performing
brute force attack against a remote system and gain unauthroised access. The different areas of
security are focused such that the captured packets are exported to a text file such that it can be
processed using third party tools. For performing the attack, it uses replay attack, packet
injection or DE authentication. The IP address of the targeted host is needed to be inputted and
there is also option to attack on multiple target by inputting a list of target. The open ports is
selected that can be obtained from NMAP scan and settings are made to fetch user name from
list and password from list and crack the username and password of the targeted system in
order to gain access.
CYBER SECURITY AND ANALYTICS
Assignment 1a: Implementation and evaluation of
5 password cracking tools in Kali Linux
Demonstration of building software testing platform for
evaluation of 2 password cracking tool
For the development of software testing platform Kali Linux is used and a research is made on the
different password cracking tool that can be used for penetration testing. The following are the two
tools that are implemented and evaluated for cracking password.
1. THC Hydra – Hydra is an online cracking tool and it is used for performing dictionary attack
rapidly against more than 50 protocols such as SSH, FTP, TELNET, HTTPS, SMB, etc. that can be
used for cracking password of database and user accounts [1]. It can be used for performing
brute force attack against a remote system and gain unauthroised access. The different areas of
security are focused such that the captured packets are exported to a text file such that it can be
processed using third party tools. For performing the attack, it uses replay attack, packet
injection or DE authentication. The IP address of the targeted host is needed to be inputted and
there is also option to attack on multiple target by inputting a list of target. The open ports is
selected that can be obtained from NMAP scan and settings are made to fetch user name from
list and password from list and crack the username and password of the targeted system in
order to gain access.
2
CYBER SECURITY AND ANALYTICS
2. John the Ripper – It is a popular password cracking tool used in penetration testing and is an
open source software and available for Unix, windows, Dos, OpenVMS etc. The main purpose of
CYBER SECURITY AND ANALYTICS
2. John the Ripper – It is a popular password cracking tool used in penetration testing and is an
open source software and available for Unix, windows, Dos, OpenVMS etc. The main purpose of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
CYBER SECURITY AND ANALYTICS
the software is to detect a weak password by detecting the password hash type and inclusion of
customizable cracker. It has the ability to run against different format of encrypted password
that are based on MD5, DES and Bowfish. There are different additional modules that can be
combined to extend its ability for cracking MD4 based hashed used in MYSQL and LDAP.
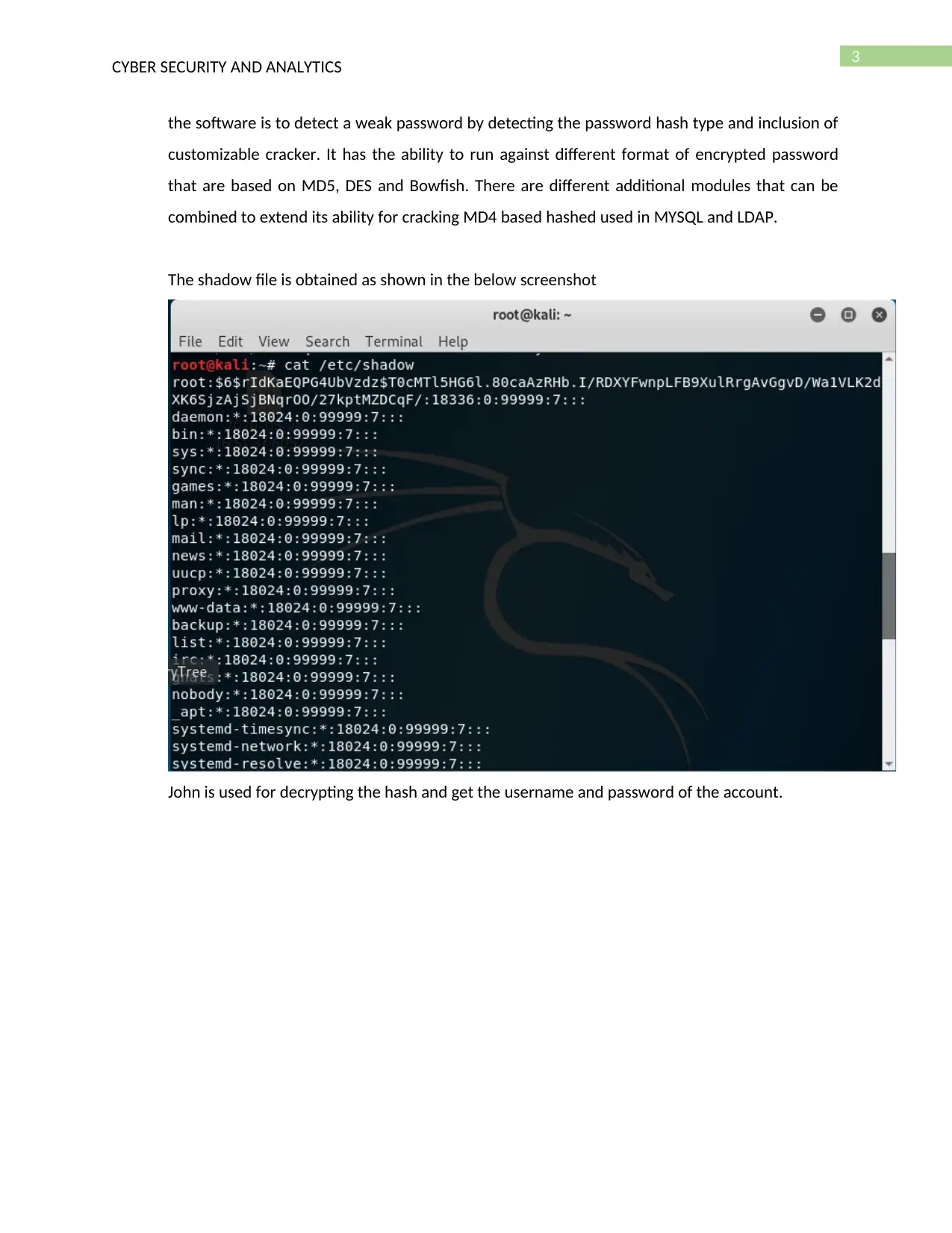
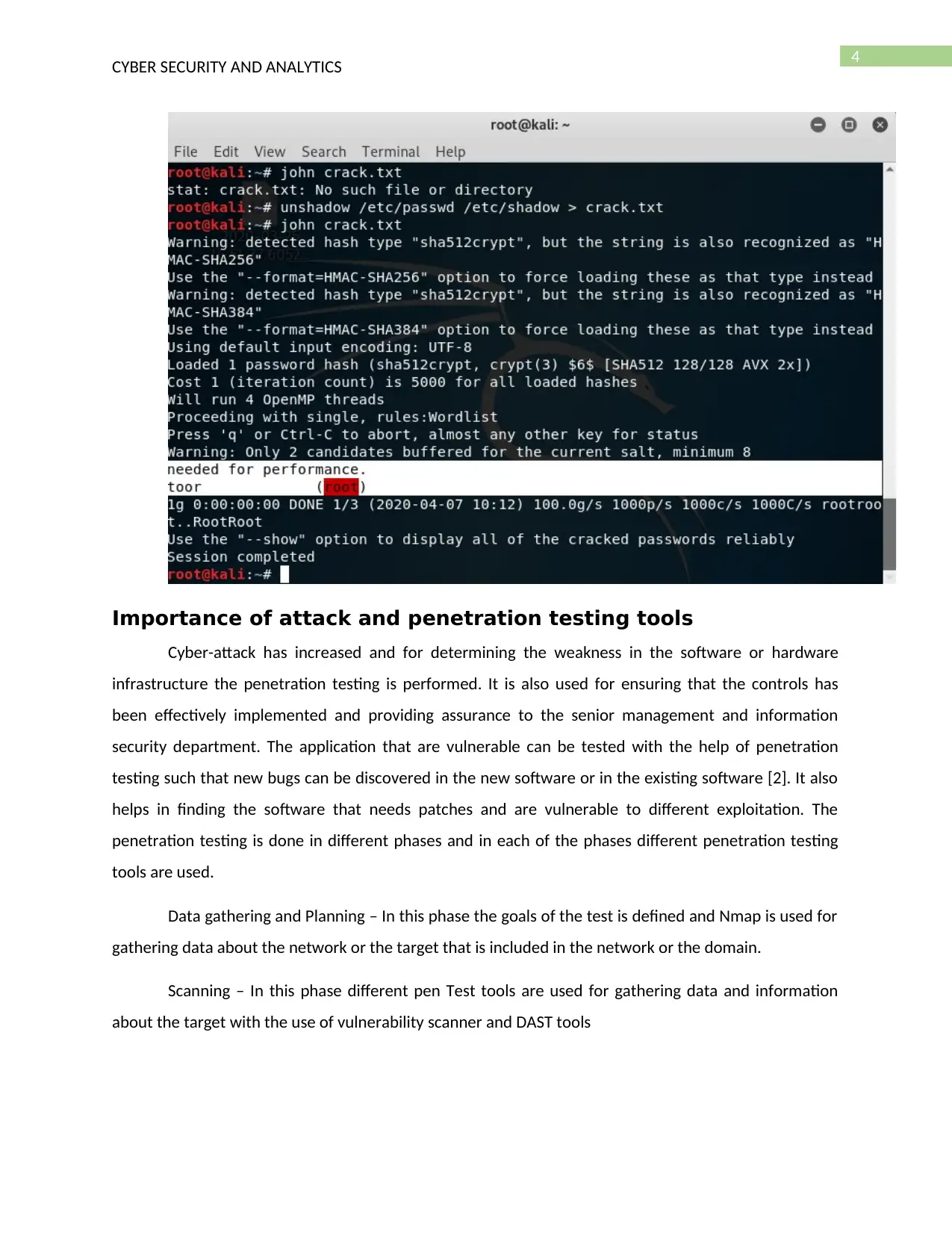
The shadow file is obtained as shown in the below screenshot
John is used for decrypting the hash and get the username and password of the account.
CYBER SECURITY AND ANALYTICS
the software is to detect a weak password by detecting the password hash type and inclusion of
customizable cracker. It has the ability to run against different format of encrypted password
that are based on MD5, DES and Bowfish. There are different additional modules that can be
combined to extend its ability for cracking MD4 based hashed used in MYSQL and LDAP.
The shadow file is obtained as shown in the below screenshot
John is used for decrypting the hash and get the username and password of the account.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
CYBER SECURITY AND ANALYTICS
Importance of attack and penetration testing tools
Cyber-attack has increased and for determining the weakness in the software or hardware
infrastructure the penetration testing is performed. It is also used for ensuring that the controls has
been effectively implemented and providing assurance to the senior management and information
security department. The application that are vulnerable can be tested with the help of penetration
testing such that new bugs can be discovered in the new software or in the existing software [2]. It also
helps in finding the software that needs patches and are vulnerable to different exploitation. The
penetration testing is done in different phases and in each of the phases different penetration testing
tools are used.
Data gathering and Planning – In this phase the goals of the test is defined and Nmap is used for
gathering data about the network or the target that is included in the network or the domain.
Scanning – In this phase different pen Test tools are used for gathering data and information
about the target with the use of vulnerability scanner and DAST tools
CYBER SECURITY AND ANALYTICS
Importance of attack and penetration testing tools
Cyber-attack has increased and for determining the weakness in the software or hardware
infrastructure the penetration testing is performed. It is also used for ensuring that the controls has
been effectively implemented and providing assurance to the senior management and information
security department. The application that are vulnerable can be tested with the help of penetration
testing such that new bugs can be discovered in the new software or in the existing software [2]. It also
helps in finding the software that needs patches and are vulnerable to different exploitation. The
penetration testing is done in different phases and in each of the phases different penetration testing
tools are used.
Data gathering and Planning – In this phase the goals of the test is defined and Nmap is used for
gathering data about the network or the target that is included in the network or the domain.
Scanning – In this phase different pen Test tools are used for gathering data and information
about the target with the use of vulnerability scanner and DAST tools

5
CYBER SECURITY AND ANALYTICS
Access Gaining – Cross site scripting and SQL injection is used for performing WEB application
attack and exposing the vulnerability of the system. Data are stolen and permissions are increased for
exposing the vulnerability.
Maintaining Access – after gaining access of the system sensitive data is accessed for causing
harm and a backdoor is created for continuing access to the system.
Covering Tracks – For remaining undetected configuration changes are made for returning to a
previous stage such that the red flag is not raised.
Attributes of good assessment tool for Penetration Test
For performing the penetration testing right penetration testing tool is needed to be selected
and the following are the attributes that is found most useful in a pen test tool among the available
ones:
Visibility – The test and the outcome is needed to be completely visible and the commercial
tools that covering as proprietary is needed to be avoided [1]. Open source tools are needed to be
selected that provided the scan result completely visible to the pen testing team.
Configurability – The testing tool is needed to be configurable depending on the test that is
performed.
License Flexibility – The tools that are available commercially can lock down some of the feature
for licensing purpose and this tools or its features are avoided.
Extensibility – The customization option present in the tool i.e. capability of use of plug ins and
scripting language for the construction of customizable probes.
Documentation – It is needed for maximizing the usefulness such that the probes are explained
and well documented.
CYBER SECURITY AND ANALYTICS
Access Gaining – Cross site scripting and SQL injection is used for performing WEB application
attack and exposing the vulnerability of the system. Data are stolen and permissions are increased for
exposing the vulnerability.
Maintaining Access – after gaining access of the system sensitive data is accessed for causing
harm and a backdoor is created for continuing access to the system.
Covering Tracks – For remaining undetected configuration changes are made for returning to a
previous stage such that the red flag is not raised.
Attributes of good assessment tool for Penetration Test
For performing the penetration testing right penetration testing tool is needed to be selected
and the following are the attributes that is found most useful in a pen test tool among the available
ones:
Visibility – The test and the outcome is needed to be completely visible and the commercial
tools that covering as proprietary is needed to be avoided [1]. Open source tools are needed to be
selected that provided the scan result completely visible to the pen testing team.
Configurability – The testing tool is needed to be configurable depending on the test that is
performed.
License Flexibility – The tools that are available commercially can lock down some of the feature
for licensing purpose and this tools or its features are avoided.
Extensibility – The customization option present in the tool i.e. capability of use of plug ins and
scripting language for the construction of customizable probes.
Documentation – It is needed for maximizing the usefulness such that the probes are explained
and well documented.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CYBER SECURITY AND ANALYTICS
References
[1]"VULNERABILITY ASSESSMENT & PENETRATION TESTING (VAPT)", International Journal of Recent
Trends in Engineering and Research, vol. 4, no. 3, pp. 326-330, 2018. Available:
10.23883/ijrter.2018.4135.tru9k.
[2]"13 Powerful Penetration Testing Tools The Pros Use", PhoenixNAP Global IT Services, 2020. [Online].
Available: https://phoenixnap.com/blog/best-penetration-testing-tools. [Accessed: 07- Apr- 2020].
CYBER SECURITY AND ANALYTICS
References
[1]"VULNERABILITY ASSESSMENT & PENETRATION TESTING (VAPT)", International Journal of Recent
Trends in Engineering and Research, vol. 4, no. 3, pp. 326-330, 2018. Available:
10.23883/ijrter.2018.4135.tru9k.
[2]"13 Powerful Penetration Testing Tools The Pros Use", PhoenixNAP Global IT Services, 2020. [Online].
Available: https://phoenixnap.com/blog/best-penetration-testing-tools. [Accessed: 07- Apr- 2020].
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




