7COM1066: Incident Response to Online Credit Card Fraud
VerifiedAdded on 2022/09/10
|13
|1270
|28
Project
AI Summary
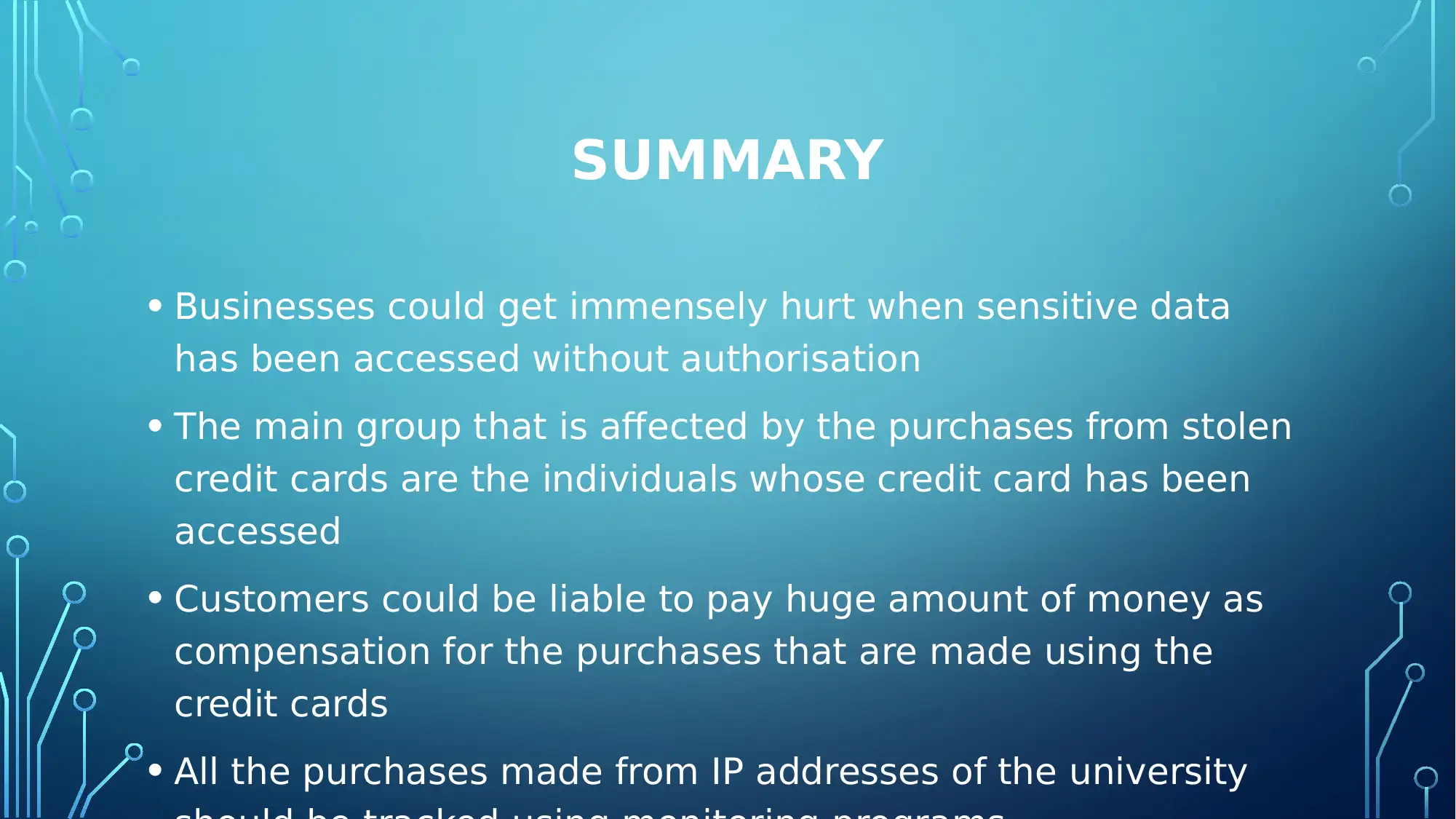
This project addresses a critical data breach scenario where online purchases are made using stolen credit cards originating from a university's IP address. The assignment explores the severity of the situation, identifying affected parties such as credit card holders, the university, and potential perpetrators. It outlines methods for containing the breach, including blocking the compromised IP address, centralizing transaction monitoring, and blocking suspicious websites. Recovery strategies involve restricting credit card usage from the university's IP, implementing robust firewalls, and tracing fraudulent transactions. The project also details preventive measures, such as limiting purchase numbers, installing antivirus software, and monitoring all transactions. Enhanced detection methods include installing detection programs, blocking suspicious credit cards, and hiring expert IT professionals. The project provides references to support the recommendations.
1 out of 13


















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)