Data Breach Incident Response Plan: University of Hertfordshire
VerifiedAdded on 2023/04/21
|18
|971
|230
Report
AI Summary
This report details an incident response plan designed to address a data breach within the Department of Computer Science at the University of Hertfordshire. The plan emphasizes a coordinated, strategic, and multidisciplinary approach to manage the incident effectively. It identifies potential data breach targets, including personal information, intellectual property, and financial data, and outlines the associated threats and consequences. The report highlights the importance of a well-defined incident response plan in determining the scope of the breach, identifying affected systems, and guiding the investigation. It includes details on the roles of key personnel like the CISO, the composition of the incident response team, and the actions to be taken in response to the breach, such as assessment, legal advice, evidence preservation, and security audits. The report also provides recommendations for improving security, including incorporating cybersecurity into discussions, implementing mechanisms to counter breaches, and auditing existing security controls. Furthermore, it suggests strategies for leveraging data and analytics to improve business solutions using the Six Sigma methodology.
1 out of 18








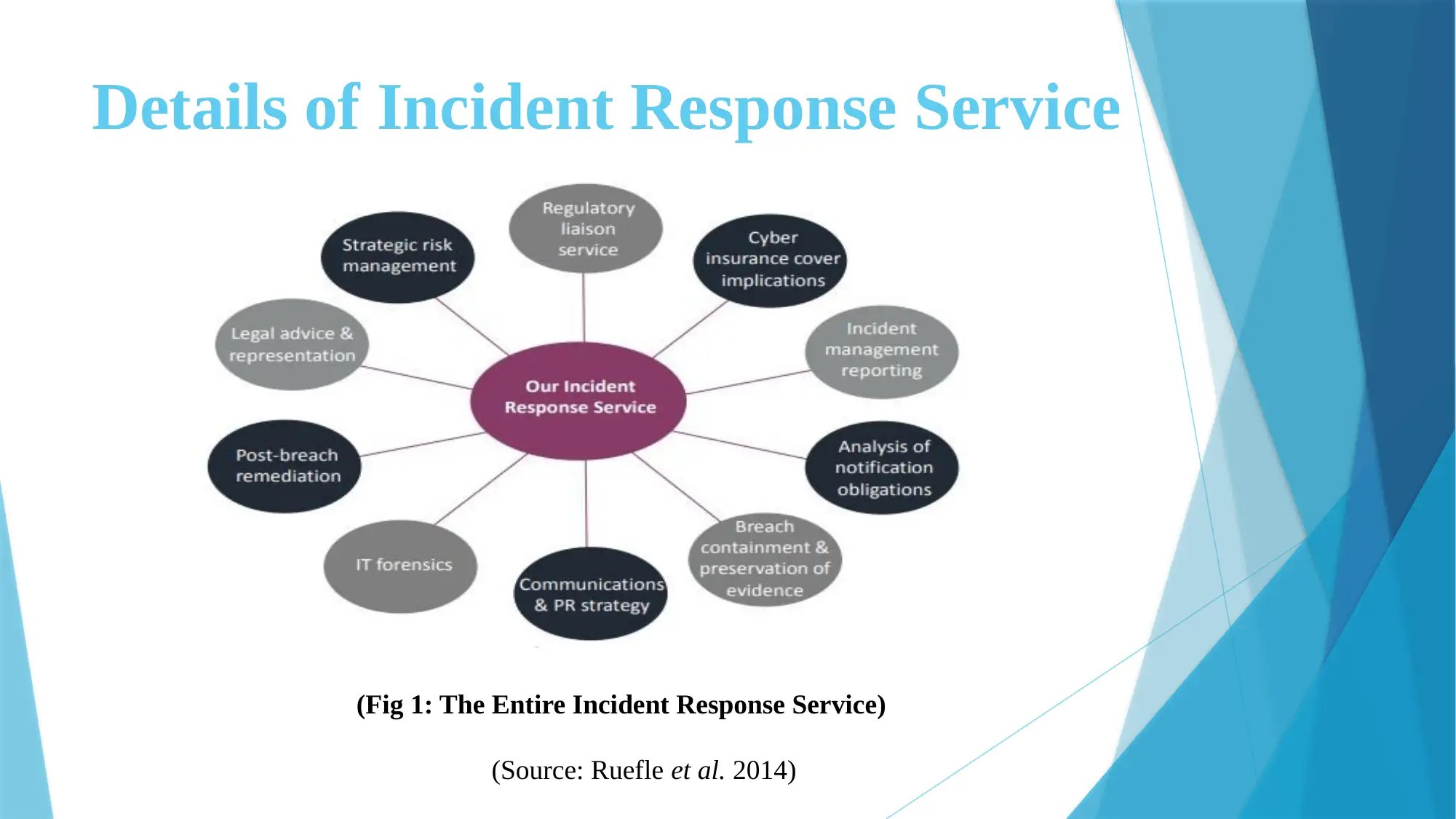

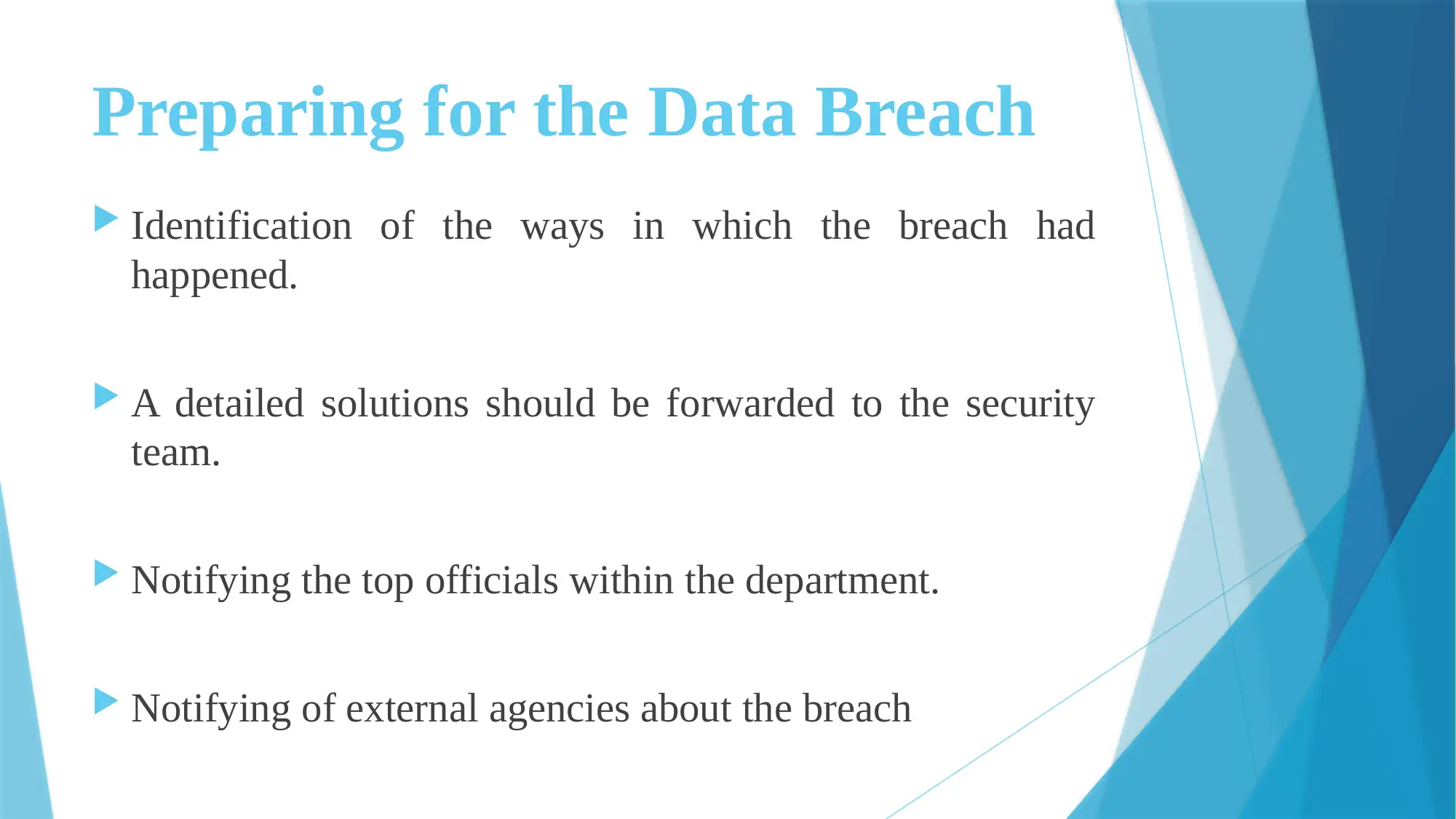

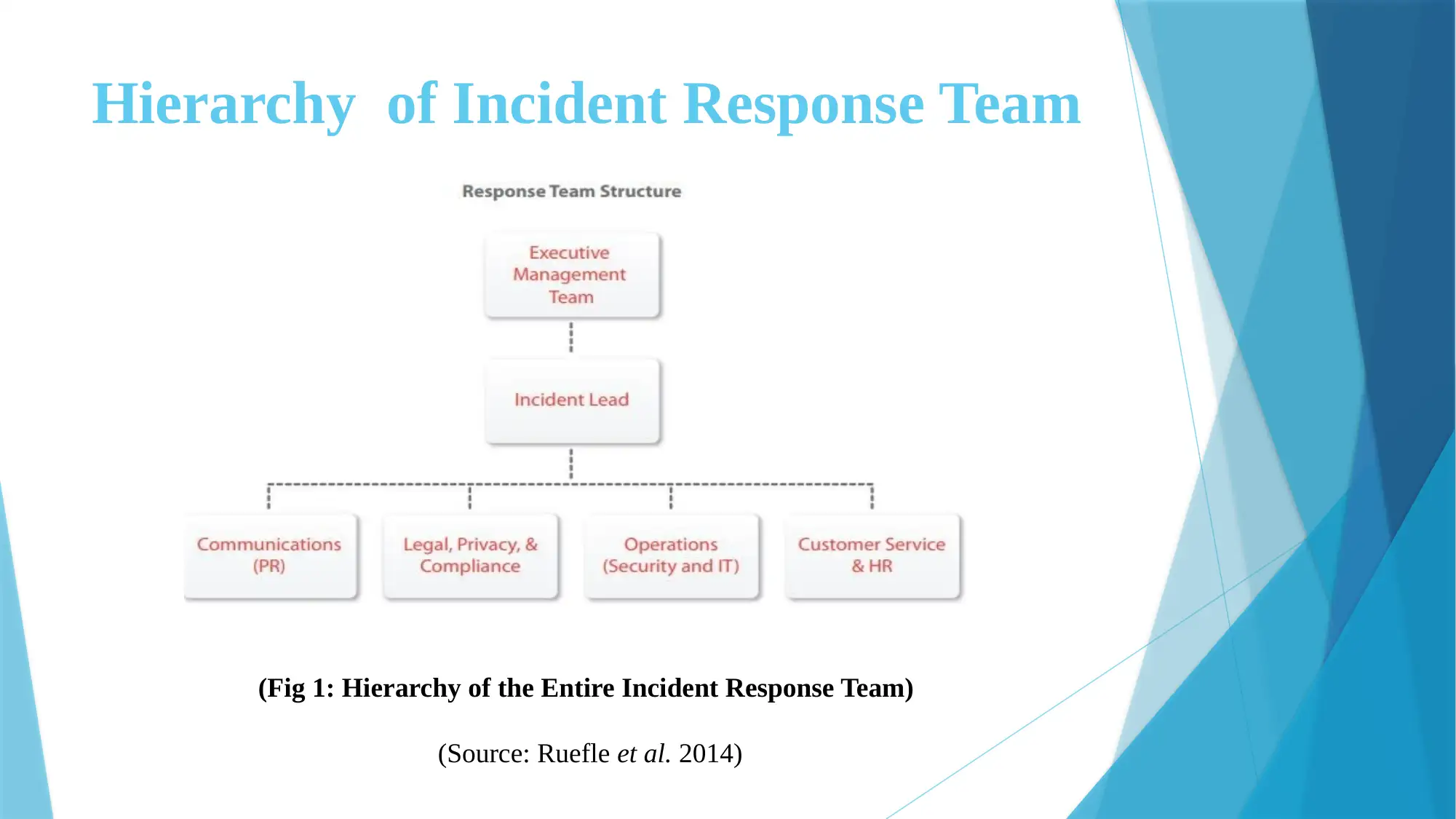






![[object Object]](/_next/static/media/star-bottom.7253800d.svg)