Incident Response Plan and Security Risk Assessment for the SSA
VerifiedAdded on 2020/04/21
|13
|2593
|121
Report
AI Summary
This report provides an incident response plan designed for the Social Security Administration (SSA) in the United States, addressing the aftermath of cyber disasters and focusing on risk management. The report analyzes security risks, particularly Denial of Service (DoS) attacks, and outlines a four-step incident response strategy: preparation, detection and analysis, containment and recovery, and post-incident activity. It references the SSA's 2015 audit report and discusses the roles of distributed, central, and coordinating teams in handling threats. The report details procedures for preparation, detection using tools like Wireshark and Netflow, containment via ACL and rate limiting, and eradication/recovery. It also includes a risk assessment table, identifying threats, impacts, and recommended corrective actions, along with recommendations for enhancing the organization's security framework. The report concludes by emphasizing the need for ongoing security upgrades and compliance with the Federal Information Security Modernization Act of 2014 (FISMA).

Running head: INCIDENT RESPONSE
Incident response
Name of the student
Name of the university
Author Note
Incident response
Name of the student
Name of the university
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INCIDENT RESPONSE
Executive summary
The following report discusses about an incident response plan that is to be integrated in the
Social Security Administration. The chosen country is the United States. The report further
discusses about a security risk assessment that is to be done for the identified threats in the
chosen organization.
Executive summary
The following report discusses about an incident response plan that is to be integrated in the
Social Security Administration. The chosen country is the United States. The report further
discusses about a security risk assessment that is to be done for the identified threats in the
chosen organization.

2INCIDENT RESPONSE
Table of Contents
Introduction:....................................................................................................................................3
Discussion:.......................................................................................................................................3
Incident response:........................................................................................................................3
Recommendations:..........................................................................................................................9
Conclusion:....................................................................................................................................10
References:....................................................................................................................................11
Table of Contents
Introduction:....................................................................................................................................3
Discussion:.......................................................................................................................................3
Incident response:........................................................................................................................3
Recommendations:..........................................................................................................................9
Conclusion:....................................................................................................................................10
References:....................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INCIDENT RESPONSE
Introduction:
An incident response is supposed to be a strategic approach which is used for addressing
the after effects of a cyber disaster. This cyber disaster is also known as a computer incident or
IT incident or a security related incident. The main objective of such strategic steps is the
reduction of damages cost by the cyber disasters and the recovery of cost and time.
This report mainly discusses about the risk management plan which will be addressed by
the Social Security Administration (SSA) of United States. The report also includes a discussion
about the incident response to be followed.
Discussion:
This section of the report discusses about the main incident response and the security
assessment for SSA.
Incident response:
An event is termed as those types of incidents that have a direct relation to an outcome.
This may include the connection of a secondary hard drive in the computer or accessing the
server of a company. However, a computer security related incident is one which is used to
unethically get access to a system (Von Solms & Van Niekerk, 2013). Examples of such
incidents are the use of an automated tool used for sending enormous traffic to a website causing
its server to lose control eventually leading to crashes.
A successful incident response involves the creation of a strategy for making 4 different
steps. The first step involves taking necessary precautions. These precautions are for
safeguarding against network or cyber related attacks. The second step involves application of
Introduction:
An incident response is supposed to be a strategic approach which is used for addressing
the after effects of a cyber disaster. This cyber disaster is also known as a computer incident or
IT incident or a security related incident. The main objective of such strategic steps is the
reduction of damages cost by the cyber disasters and the recovery of cost and time.
This report mainly discusses about the risk management plan which will be addressed by
the Social Security Administration (SSA) of United States. The report also includes a discussion
about the incident response to be followed.
Discussion:
This section of the report discusses about the main incident response and the security
assessment for SSA.
Incident response:
An event is termed as those types of incidents that have a direct relation to an outcome.
This may include the connection of a secondary hard drive in the computer or accessing the
server of a company. However, a computer security related incident is one which is used to
unethically get access to a system (Von Solms & Van Niekerk, 2013). Examples of such
incidents are the use of an automated tool used for sending enormous traffic to a website causing
its server to lose control eventually leading to crashes.
A successful incident response involves the creation of a strategy for making 4 different
steps. The first step involves taking necessary precautions. These precautions are for
safeguarding against network or cyber related attacks. The second step involves application of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INCIDENT RESPONSE
detection and analysis methods which will be able to detect the presence of any vulnerabilities or
threats before their occurrence (Peltier, 2016). The third step is the addressing of any such
occurred problems. This involves the disaster recovery protocols that are to be applied to the
system. The fourth step involves is the learning and recommendations process which is done to
stop such types of attacks in the future.
Overview:
According to the audit report for the fiscal year 2015 for the SSA, the main objective was
to determine the effectiveness of the information and security policies so that it would be
complied with the Federal Information Security Modernization Act of 2014 (FISMA).
Denial of Service (DoS):
Although there are various security related risks, for this incident response plan, the
Denial of Service (DoS) risks are discussed. Denial of Service attacks affects a system by
making it unusable to its intended users. This is basically done by flooding the system with
unusual amount of traffic which the device becomes unable to handle. This crashes the servers if
present and denies access. In addition, for personal computers their uses are done to remove user
access from the system.
Roles:
For any detected vulnerability or threats, a response team will be present who are solely
responsible for addressing the requirements. This team comprises of employees of the SSA who
specializes in the risk management methods. There are three types of teams which will be
comprised of various personnel responsible for a specific task. These teams are the distributed,
detection and analysis methods which will be able to detect the presence of any vulnerabilities or
threats before their occurrence (Peltier, 2016). The third step is the addressing of any such
occurred problems. This involves the disaster recovery protocols that are to be applied to the
system. The fourth step involves is the learning and recommendations process which is done to
stop such types of attacks in the future.
Overview:
According to the audit report for the fiscal year 2015 for the SSA, the main objective was
to determine the effectiveness of the information and security policies so that it would be
complied with the Federal Information Security Modernization Act of 2014 (FISMA).
Denial of Service (DoS):
Although there are various security related risks, for this incident response plan, the
Denial of Service (DoS) risks are discussed. Denial of Service attacks affects a system by
making it unusable to its intended users. This is basically done by flooding the system with
unusual amount of traffic which the device becomes unable to handle. This crashes the servers if
present and denies access. In addition, for personal computers their uses are done to remove user
access from the system.
Roles:
For any detected vulnerability or threats, a response team will be present who are solely
responsible for addressing the requirements. This team comprises of employees of the SSA who
specializes in the risk management methods. There are three types of teams which will be
comprised of various personnel responsible for a specific task. These teams are the distributed,

5INCIDENT RESPONSE
central and the coordinating team (Computer Security Incident Handling Guide, 2017).
Additionally, the personnel are either employees or contractual workers. These workers together
will be responsible for addressing to any threats like the intrusions or breaches in the system. In
addition, they will also be responsible for handling requests of other employees in case when
they see any such changes in the system.
Testing:
The adopted cloud based technologies have not been tested according to the audit report.
In addition, the various cloud based processes have not been integrated with the existing
processes. For testing the presence of any vulnerabilities, effective monitoring is used which
analyzes the whole network for any detected vulnerability or threat.
Incident Notification:
The personnel discussed in the above section have the sole responsibility to detect any
presence of threats or vulnerabilities in the system. This will be used to safeguard the system and
make it more resistant to such attacks. To do this in a more efficient way, the need for
notification or a red flag system is present. The red flag system is responsible for detecting any
such threats by analyzing the behavior of the system (The Social Security Administration’s
Compliance with the Federal Information Security Modernization Act of 2014 for Fiscal Year
2015, 2015). If the user behavior seems odd in comparison to the older data, it is possible that a
breach is likely to occur. This sends a red flag to the system and alerts the personnel right away.
This notification regarding the problems in the network is to be sent to the teams responsible for
the process. The team to be notified is the employees of the SSA who are responsible for the
central and the coordinating team (Computer Security Incident Handling Guide, 2017).
Additionally, the personnel are either employees or contractual workers. These workers together
will be responsible for addressing to any threats like the intrusions or breaches in the system. In
addition, they will also be responsible for handling requests of other employees in case when
they see any such changes in the system.
Testing:
The adopted cloud based technologies have not been tested according to the audit report.
In addition, the various cloud based processes have not been integrated with the existing
processes. For testing the presence of any vulnerabilities, effective monitoring is used which
analyzes the whole network for any detected vulnerability or threat.
Incident Notification:
The personnel discussed in the above section have the sole responsibility to detect any
presence of threats or vulnerabilities in the system. This will be used to safeguard the system and
make it more resistant to such attacks. To do this in a more efficient way, the need for
notification or a red flag system is present. The red flag system is responsible for detecting any
such threats by analyzing the behavior of the system (The Social Security Administration’s
Compliance with the Federal Information Security Modernization Act of 2014 for Fiscal Year
2015, 2015). If the user behavior seems odd in comparison to the older data, it is possible that a
breach is likely to occur. This sends a red flag to the system and alerts the personnel right away.
This notification regarding the problems in the network is to be sent to the teams responsible for
the process. The team to be notified is the employees of the SSA who are responsible for the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INCIDENT RESPONSE
risks management processes. In such cases, the proper steps will be taken to safeguard the
system.
Risks present:
The various risks present in the system are the DoS attacks. In addition, the identity and
access threat are another risks that requires addressing by the organizational head.
Procedure:
1. Preparation: The main system of the SSA includes the presence of a logical access
control and a monitoring system for analyzing the applications. However, in the audit report,
there is a clear mentioning of the fact that there are various vulnerabilities and threats in their
system. There are various methods by which preparation for a DoS attack can be done
(Computer Security Incident Handling Guide, 2017). The first method is the recognition of the
attack. This method involves detecting the presence of any such vulnerabilities and threats in the
system by which DoS attacks can be possible. A critical thing in every infrastructure is the
presence of additional redundant systems for business needs. This can also be targeted by
attackers to get access to the system and hence the need for cloud features is necessary. Another
method is includes contacting the ISP. If an organization feels the likelihood of a DoS attack, the
ISP can re-route their traffic so that the network cannot be detected further. The last method
involves dumping the log files. This reduces the space on the server and makes it less likely to
affect from a DoS attack.
2. Detection: The detection phase involves detecting the presence of any Trojans or
malwares or viruses which can affect the working of the system. There are several ways through
which attacks can occur. The use of various analytical tools can help to mitigate the risks
risks management processes. In such cases, the proper steps will be taken to safeguard the
system.
Risks present:
The various risks present in the system are the DoS attacks. In addition, the identity and
access threat are another risks that requires addressing by the organizational head.
Procedure:
1. Preparation: The main system of the SSA includes the presence of a logical access
control and a monitoring system for analyzing the applications. However, in the audit report,
there is a clear mentioning of the fact that there are various vulnerabilities and threats in their
system. There are various methods by which preparation for a DoS attack can be done
(Computer Security Incident Handling Guide, 2017). The first method is the recognition of the
attack. This method involves detecting the presence of any such vulnerabilities and threats in the
system by which DoS attacks can be possible. A critical thing in every infrastructure is the
presence of additional redundant systems for business needs. This can also be targeted by
attackers to get access to the system and hence the need for cloud features is necessary. Another
method is includes contacting the ISP. If an organization feels the likelihood of a DoS attack, the
ISP can re-route their traffic so that the network cannot be detected further. The last method
involves dumping the log files. This reduces the space on the server and makes it less likely to
affect from a DoS attack.
2. Detection: The detection phase involves detecting the presence of any Trojans or
malwares or viruses which can affect the working of the system. There are several ways through
which attacks can occur. The use of various analytical tools can help to mitigate the risks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INCIDENT RESPONSE
involved. The first tools that can be used are the Wireshark which are mainly used for capturing
the traffic related to the system. This is also known as a tool used for packet monitoring. In
addition, the traffic from the UDP packets and the ICMP packets can also be effectively
monitored. Moreover, the Wireshark tool can also be used for capturing the TCP SYN packets
thereby making it a best to have in all network systems. Another tool which can be used is the
Netflow software which can detect the end and the start time of a DoS attack.
3. Containment: The containment process is usually in place to address any detected
anomalies. This is done to check the threat to spread any further. To address the requirement of a
containment strategy, there are various strategies that are to be followed. For mitigating the DoS
attacks, the use of the ACL and the rate limiting procedure is used. The ACL (Access Control
Lists) includes a list of rules that can be applied to a router for analyzing the traffic. If the set of
IPs does not match the set criteria by the ACL, they are rejected. In addition, the rate limiting is
another technique which can be used for mitigating DoS attacks. This is a technique which limits
the rate of traffic in a server which can be handled. This reduces the excess traffic to the system
and secures the system accordingly.
4. Eradication and recovery steps: This section is concerned with the removal of the treats
from the concerned organization. If a threat can be removed by small steps like the use of
antivirus programs, the eradications are done right away (Computer Security Incident Handling
Guide, 2017). The recovery processes involves the re-establishment of the BGP connections
which implies the connections among the peer partners. The next method involves the re-
establishment of the firewalls and other network software that will help to secure the system for
any further attack. Moreover an ISP will not provide any connection to their customers involved
with a DoS attack. The organization need to contact them and convince them about doing
involved. The first tools that can be used are the Wireshark which are mainly used for capturing
the traffic related to the system. This is also known as a tool used for packet monitoring. In
addition, the traffic from the UDP packets and the ICMP packets can also be effectively
monitored. Moreover, the Wireshark tool can also be used for capturing the TCP SYN packets
thereby making it a best to have in all network systems. Another tool which can be used is the
Netflow software which can detect the end and the start time of a DoS attack.
3. Containment: The containment process is usually in place to address any detected
anomalies. This is done to check the threat to spread any further. To address the requirement of a
containment strategy, there are various strategies that are to be followed. For mitigating the DoS
attacks, the use of the ACL and the rate limiting procedure is used. The ACL (Access Control
Lists) includes a list of rules that can be applied to a router for analyzing the traffic. If the set of
IPs does not match the set criteria by the ACL, they are rejected. In addition, the rate limiting is
another technique which can be used for mitigating DoS attacks. This is a technique which limits
the rate of traffic in a server which can be handled. This reduces the excess traffic to the system
and secures the system accordingly.
4. Eradication and recovery steps: This section is concerned with the removal of the treats
from the concerned organization. If a threat can be removed by small steps like the use of
antivirus programs, the eradications are done right away (Computer Security Incident Handling
Guide, 2017). The recovery processes involves the re-establishment of the BGP connections
which implies the connections among the peer partners. The next method involves the re-
establishment of the firewalls and other network software that will help to secure the system for
any further attack. Moreover an ISP will not provide any connection to their customers involved
with a DoS attack. The organization need to contact them and convince them about doing
8INCIDENT RESPONSE
business again. Lastly, application recovery needs to be done so that the business gets back on
track.
5. Post-incident activity: For the weaknesses described in SSA for DoS attacks, there are
various steps that have been taken to ensure the smooth functioning of the system. This includes
the enhancement of risks mitigation procedures and other procedures. In addition, to completely
address such issues, the higher risks were being targeted first (The Social Security
Administration’s Compliance with the Federal Information Security Modernization Act of 2014
for Fiscal Year 2015, 2015). In addition, the development of such methods was also supposed to
be under good governance.
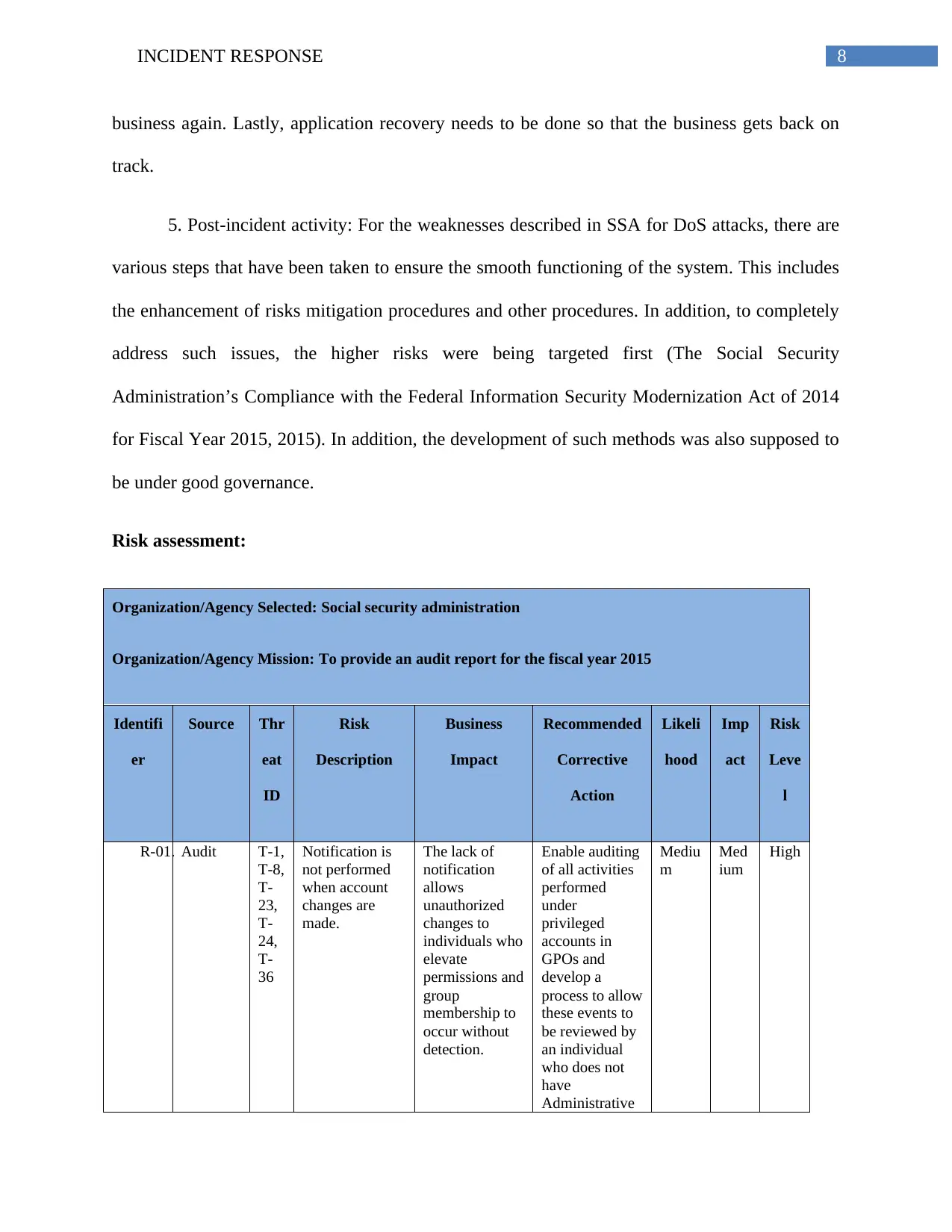
Risk assessment:
Organization/Agency Selected: Social security administration
Organization/Agency Mission: To provide an audit report for the fiscal year 2015
Identifi
er
Source Thr
eat
ID
Risk
Description
Business
Impact
Recommended
Corrective
Action
Likeli
hood
Imp
act
Risk
Leve
l
R-01. Audit T-1,
T-8,
T-
23,
T-
24,
T-
36
Notification is
not performed
when account
changes are
made.
The lack of
notification
allows
unauthorized
changes to
individuals who
elevate
permissions and
group
membership to
occur without
detection.
Enable auditing
of all activities
performed
under
privileged
accounts in
GPOs and
develop a
process to allow
these events to
be reviewed by
an individual
who does not
have
Administrative
Mediu
m
Med
ium
High
business again. Lastly, application recovery needs to be done so that the business gets back on
track.
5. Post-incident activity: For the weaknesses described in SSA for DoS attacks, there are
various steps that have been taken to ensure the smooth functioning of the system. This includes
the enhancement of risks mitigation procedures and other procedures. In addition, to completely
address such issues, the higher risks were being targeted first (The Social Security
Administration’s Compliance with the Federal Information Security Modernization Act of 2014
for Fiscal Year 2015, 2015). In addition, the development of such methods was also supposed to
be under good governance.
Risk assessment:
Organization/Agency Selected: Social security administration
Organization/Agency Mission: To provide an audit report for the fiscal year 2015
Identifi
er
Source Thr
eat
ID
Risk
Description
Business
Impact
Recommended
Corrective
Action
Likeli
hood
Imp
act
Risk
Leve
l
R-01. Audit T-1,
T-8,
T-
23,
T-
24,
T-
36
Notification is
not performed
when account
changes are
made.
The lack of
notification
allows
unauthorized
changes to
individuals who
elevate
permissions and
group
membership to
occur without
detection.
Enable auditing
of all activities
performed
under
privileged
accounts in
GPOs and
develop a
process to allow
these events to
be reviewed by
an individual
who does not
have
Administrative
Mediu
m
Med
ium
High
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9INCIDENT RESPONSE
Organization/Agency Selected: Social security administration
Organization/Agency Mission: To provide an audit report for the fiscal year 2015
Identifi
er
Source Thr
eat
ID
Risk
Description
Business
Impact
Recommended
Corrective
Action
Likeli
hood
Imp
act
Risk
Leve
l
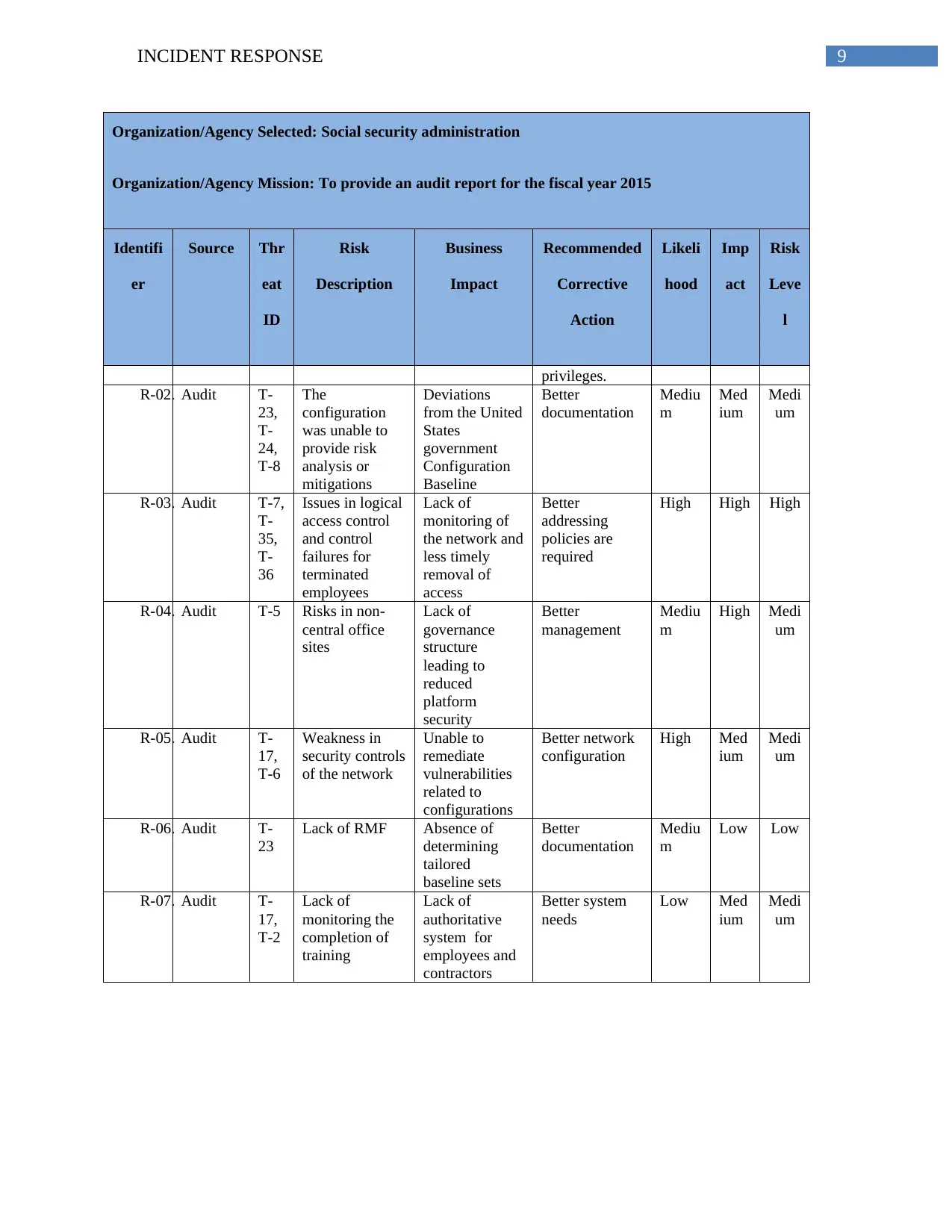
privileges.
R-02. Audit T-
23,
T-
24,
T-8
The
configuration
was unable to
provide risk
analysis or
mitigations
Deviations
from the United
States
government
Configuration
Baseline
Better
documentation
Mediu
m
Med
ium
Medi
um
R-03. Audit T-7,
T-
35,
T-
36
Issues in logical
access control
and control
failures for
terminated
employees
Lack of
monitoring of
the network and
less timely
removal of
access
Better
addressing
policies are
required
High High High
R-04. Audit T-5 Risks in non-
central office
sites
Lack of
governance
structure
leading to
reduced
platform
security
Better
management
Mediu
m
High Medi
um
R-05. Audit T-
17,
T-6
Weakness in
security controls
of the network
Unable to
remediate
vulnerabilities
related to
configurations
Better network
configuration
High Med
ium
Medi
um
R-06. Audit T-
23
Lack of RMF Absence of
determining
tailored
baseline sets
Better
documentation
Mediu
m
Low Low
R-07. Audit T-
17,
T-2
Lack of
monitoring the
completion of
training
Lack of
authoritative
system for
employees and
contractors
Better system
needs
Low Med
ium
Medi
um
Organization/Agency Selected: Social security administration
Organization/Agency Mission: To provide an audit report for the fiscal year 2015
Identifi
er
Source Thr
eat
ID
Risk
Description
Business
Impact
Recommended
Corrective
Action
Likeli
hood
Imp
act
Risk
Leve
l
privileges.
R-02. Audit T-
23,
T-
24,
T-8
The
configuration
was unable to
provide risk
analysis or
mitigations
Deviations
from the United
States
government
Configuration
Baseline
Better
documentation
Mediu
m
Med
ium
Medi
um
R-03. Audit T-7,
T-
35,
T-
36
Issues in logical
access control
and control
failures for
terminated
employees
Lack of
monitoring of
the network and
less timely
removal of
access
Better
addressing
policies are
required
High High High
R-04. Audit T-5 Risks in non-
central office
sites
Lack of
governance
structure
leading to
reduced
platform
security
Better
management
Mediu
m
High Medi
um
R-05. Audit T-
17,
T-6
Weakness in
security controls
of the network
Unable to
remediate
vulnerabilities
related to
configurations
Better network
configuration
High Med
ium
Medi
um
R-06. Audit T-
23
Lack of RMF Absence of
determining
tailored
baseline sets
Better
documentation
Mediu
m
Low Low
R-07. Audit T-
17,
T-2
Lack of
monitoring the
completion of
training
Lack of
authoritative
system for
employees and
contractors
Better system
needs
Low Med
ium
Medi
um
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INCIDENT RESPONSE
Recommendations:
The need for protecting the assets of the organization is a requirement that is
recommended in this report. The data that is being gathered everyday may be subjected to risks
which might lead to grave threats. The need for enhancing the security framework and
technologies are needed.
Conclusion:
Thus, it can be concluded that the presence of various security related upgrades for
addressing the requirements of the processes is not able to completely address the security issues.
This report includes various deficiencies in the normal processing which can account for the
weakness of the Social security administration. But, the audit report can state that the compliance
policy of SSA is at par with the FISMA policy. The weaknesses that have been identified in this
report can lead to various threats and vulnerabilities causing to failure of the organization in
aspect of information security.
Recommendations:
The need for protecting the assets of the organization is a requirement that is
recommended in this report. The data that is being gathered everyday may be subjected to risks
which might lead to grave threats. The need for enhancing the security framework and
technologies are needed.
Conclusion:
Thus, it can be concluded that the presence of various security related upgrades for
addressing the requirements of the processes is not able to completely address the security issues.
This report includes various deficiencies in the normal processing which can account for the
weakness of the Social security administration. But, the audit report can state that the compliance
policy of SSA is at par with the FISMA policy. The weaknesses that have been identified in this
report can lead to various threats and vulnerabilities causing to failure of the organization in
aspect of information security.

11INCIDENT RESPONSE
References:
Agrawal, M., Campoe, A., & Pierce, E. (2014). Information security and IT risk management.
Wiley Publishing.
Computer Security Incident Handling Guide. (2017) (2nd ed.). Retrieved from
http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
Crossler, R. E., Johnston, A. C., Lowry, P. B., Hu, Q., Warkentin, M., & Baskerville, R. (2013).
Future directions for behavioral information security research. computers & security, 32, 90-101.
Hu, Q., Dinev, T., Hart, P., & Cooke, D. (2012). Managing employee compliance with
information security policies: The critical role of top management and organizational
culture. Decision Sciences, 43(4), 615-660.
Ifinedo, P. (2012). Understanding information systems security policy compliance: An
integration of the theory of planned behavior and the protection motivation theory. Computers &
Security, 31(1), 83-95.
Klipper, S. (2011). Information Security Risk Management. Verlag Vieweg+ Teubner.
Wiesbaden.
Peltier, T. R. (2013). Information security fundamentals. CRC Press.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
References:
Agrawal, M., Campoe, A., & Pierce, E. (2014). Information security and IT risk management.
Wiley Publishing.
Computer Security Incident Handling Guide. (2017) (2nd ed.). Retrieved from
http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
Crossler, R. E., Johnston, A. C., Lowry, P. B., Hu, Q., Warkentin, M., & Baskerville, R. (2013).
Future directions for behavioral information security research. computers & security, 32, 90-101.
Hu, Q., Dinev, T., Hart, P., & Cooke, D. (2012). Managing employee compliance with
information security policies: The critical role of top management and organizational
culture. Decision Sciences, 43(4), 615-660.
Ifinedo, P. (2012). Understanding information systems security policy compliance: An
integration of the theory of planned behavior and the protection motivation theory. Computers &
Security, 31(1), 83-95.
Klipper, S. (2011). Information Security Risk Management. Verlag Vieweg+ Teubner.
Wiesbaden.
Peltier, T. R. (2013). Information security fundamentals. CRC Press.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




