Analysis of Factors Contributing to Increased Cybersecurity Demand
VerifiedAdded on 2022/11/30
|7
|1041
|316
Report
AI Summary
This report delves into the escalating demand for cybersecurity professionals in the contemporary digital landscape. It explores the multifaceted reasons behind this surge, including the proliferation of internet usage, the increasing sophistication of cyber threats, and the growing reliance on interconnected devices and services. The report analyzes the impact of data breaches, the need for robust data protection, and the importance of a skilled cybersecurity workforce to combat cybercrime and industrial espionage. It also examines the role of education and training in developing a 'cyber-literate' workforce capable of defending against evolving cyber attacks, highlighting the critical need for professionals in the Information and Communications Technology (ICT) sector. The study investigates the independent variables such as increased internet usage, availability of internet-connected devices, and the availability of personal data online. The dependent variable is the heightened risk of cybersecurity threats and attacks, which, in turn, increases the demand for cybersecurity professionals. The research concludes that the demand for cybersecurity professionals is rising due to the increased threat landscape and need for skilled personnel to protect critical information and systems.

Running head: REASONS FOR RECENT INCREASE IN DEMAND FOR CYBER SECURITY PROFESSIONALS
REASONS FOR RECENT INCREASE IN DEMAND FOR CYBER SECURITY
PROFESSIONALS
Name of the Student
Name of the University
Author note
REASONS FOR RECENT INCREASE IN DEMAND FOR CYBER SECURITY
PROFESSIONALS
Name of the Student
Name of the University
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1REASONS FOR RECENT INCREASE IN DEMAND FOR CYBER SECURITY PROFESSIONALS
Table of Contents
Introduction..................................................................................................................................2
Overview......................................................................................................................................2
Problem statement.......................................................................................................................3
Research aim................................................................................................................................3
Research hypothesis.....................................................................................................................4
Variables......................................................................................................................................4
Conclusion...................................................................................................................................5
References....................................................................................................................................6
Table of Contents
Introduction..................................................................................................................................2
Overview......................................................................................................................................2
Problem statement.......................................................................................................................3
Research aim................................................................................................................................3
Research hypothesis.....................................................................................................................4
Variables......................................................................................................................................4
Conclusion...................................................................................................................................5
References....................................................................................................................................6

2REASONS FOR RECENT INCREASE IN DEMAND FOR CYBER SECURITY PROFESSIONALS
Introduction
“The technology is ubiquitous and increasingly integral to almost every facet of modern society.”
(Fishcer, 2016).
As technology is beginning to evolve day by day, so do the opportunities and challenges
that come along with it. Human beings are now at a crossroads as the society is moving into an
era where all aspects of life is intertwined with the internet in the age of Big Data, automation
and Internet of Things or IoT. But with the great benefits that the internet brings along with it,
the number of threats is high as well. The very nature of the internet today is a hub for
cybercrime, cyber attacks and industrial espionage. Therefore, protection from such attacks
becomes the predominant priority to any individual ("Cybersecurity – Threats Challenges
Opportunities", 2016).
Overview
According to Fischer (2016), the act of protecting systems of the Information And
Communications Technology or ICT is defined as cybersecurity. This is sometimes used as an
umbrella term for explaining privacy breach, sharing information, gathering intelligence and
surveillance. But cybersecurity somewhat does deal with privacy protection and prevention
against unauthorized surveillance. Information sharing and intelligence gathering are some
methods which could be used as effective tools to enhance cybersecurity (Fischer, 2016).
Some of the threats which constitute the vast domain of cybersecurity concerns are attack
vectors like botnets, ransomware; threats such as data manipulation, identity theft and
cyberwarfare; and other tangential issues ("Cybersecurity – Threats Challenges Opportunities",
2016).
Introduction
“The technology is ubiquitous and increasingly integral to almost every facet of modern society.”
(Fishcer, 2016).
As technology is beginning to evolve day by day, so do the opportunities and challenges
that come along with it. Human beings are now at a crossroads as the society is moving into an
era where all aspects of life is intertwined with the internet in the age of Big Data, automation
and Internet of Things or IoT. But with the great benefits that the internet brings along with it,
the number of threats is high as well. The very nature of the internet today is a hub for
cybercrime, cyber attacks and industrial espionage. Therefore, protection from such attacks
becomes the predominant priority to any individual ("Cybersecurity – Threats Challenges
Opportunities", 2016).
Overview
According to Fischer (2016), the act of protecting systems of the Information And
Communications Technology or ICT is defined as cybersecurity. This is sometimes used as an
umbrella term for explaining privacy breach, sharing information, gathering intelligence and
surveillance. But cybersecurity somewhat does deal with privacy protection and prevention
against unauthorized surveillance. Information sharing and intelligence gathering are some
methods which could be used as effective tools to enhance cybersecurity (Fischer, 2016).
Some of the threats which constitute the vast domain of cybersecurity concerns are attack
vectors like botnets, ransomware; threats such as data manipulation, identity theft and
cyberwarfare; and other tangential issues ("Cybersecurity – Threats Challenges Opportunities",
2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3REASONS FOR RECENT INCREASE IN DEMAND FOR CYBER SECURITY PROFESSIONALS
According to Dawson and Thompson (2018), the existing study of what constitutes the
cyber domain and what are the skills that are necessary to build a functional cyber workforce is
still incomplete. Therefore, the development of more innovative and effective defense
mechanisms against malware is a crucial requirement in the cybersecurity industry (Jang-Jaccard
& Nepal, 2014). New research has shown that cybersecurity workers are in high demand even
through slim number of openings in the US market across all industries (Huergo, 2018).
The ability of a nation to produce professionals who have the capability to defend against
successful cyber attacks would only arise from a skilled ‘cyber-literate’ workforce and therefore,
there is a need for the educational system to develop such skills in individuals (Catota, Morgan
& Sicker, 2019)
Therefore, this study emphasizes the reasons why the need for cybersecurity
professionals is increasing in the present age of the internet.
Problem statement
Due to the rise of internet use, the threats that come along with it are on the rise as well.
These malwares and cyber attacks could reach into a regular individual’s home system or a big
MNC’s central server, depending on its type, and could disrupt or even shutdown entire systems.
Therefore, the need for cybersecurity personnel, who specialize in dealing with such problems, is
on the rise.
Research aim
The aim of this research is to investigate the reasons which might encourage the
employment of more cybersecurity professionals in the ICT industry.
According to Dawson and Thompson (2018), the existing study of what constitutes the
cyber domain and what are the skills that are necessary to build a functional cyber workforce is
still incomplete. Therefore, the development of more innovative and effective defense
mechanisms against malware is a crucial requirement in the cybersecurity industry (Jang-Jaccard
& Nepal, 2014). New research has shown that cybersecurity workers are in high demand even
through slim number of openings in the US market across all industries (Huergo, 2018).
The ability of a nation to produce professionals who have the capability to defend against
successful cyber attacks would only arise from a skilled ‘cyber-literate’ workforce and therefore,
there is a need for the educational system to develop such skills in individuals (Catota, Morgan
& Sicker, 2019)
Therefore, this study emphasizes the reasons why the need for cybersecurity
professionals is increasing in the present age of the internet.
Problem statement
Due to the rise of internet use, the threats that come along with it are on the rise as well.
These malwares and cyber attacks could reach into a regular individual’s home system or a big
MNC’s central server, depending on its type, and could disrupt or even shutdown entire systems.
Therefore, the need for cybersecurity personnel, who specialize in dealing with such problems, is
on the rise.
Research aim
The aim of this research is to investigate the reasons which might encourage the
employment of more cybersecurity professionals in the ICT industry.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4REASONS FOR RECENT INCREASE IN DEMAND FOR CYBER SECURITY PROFESSIONALS
Research hypothesis
The research hypotheses are
H0 - There is no demand for cybersecurity professionals.
H1- There is a rising demand for cybersecurity professionals.
Variables
The independent variables or the causal variables in this research are
1. The increased use of internet based services.
2. The increased availability of devices that have internet connectivity on them.
3. The increased availability of personal data, such as bank details, birth dates, and more on
websites.
4. Ignorance of internet users who take such services for granted.
5. Multiple illegal access points to the internet that are not registered and could be used for
malpractices.
The dependent variable here is the high risk of cybersecurity threats and attacks.
Research hypothesis
The research hypotheses are
H0 - There is no demand for cybersecurity professionals.
H1- There is a rising demand for cybersecurity professionals.
Variables
The independent variables or the causal variables in this research are
1. The increased use of internet based services.
2. The increased availability of devices that have internet connectivity on them.
3. The increased availability of personal data, such as bank details, birth dates, and more on
websites.
4. Ignorance of internet users who take such services for granted.
5. Multiple illegal access points to the internet that are not registered and could be used for
malpractices.
The dependent variable here is the high risk of cybersecurity threats and attacks.
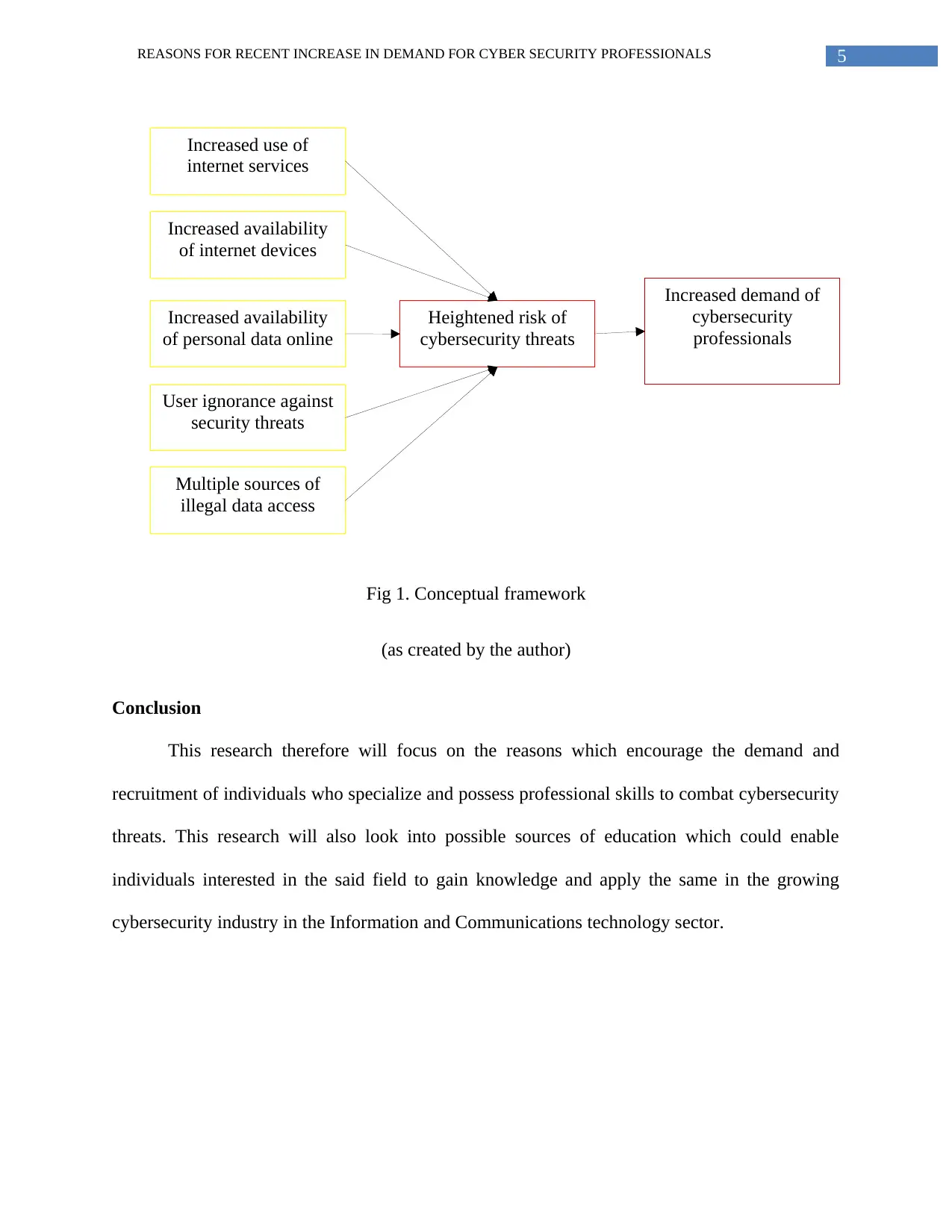
5REASONS FOR RECENT INCREASE IN DEMAND FOR CYBER SECURITY PROFESSIONALS
Increased availability
of internet devices
Increased use of
internet services
Increased availability
of personal data online
User ignorance against
security threats
Multiple sources of
illegal data access
Heightened risk of
cybersecurity threats
Increased demand of
cybersecurity
professionals
Fig 1. Conceptual framework
(as created by the author)
Conclusion
This research therefore will focus on the reasons which encourage the demand and
recruitment of individuals who specialize and possess professional skills to combat cybersecurity
threats. This research will also look into possible sources of education which could enable
individuals interested in the said field to gain knowledge and apply the same in the growing
cybersecurity industry in the Information and Communications technology sector.
Increased availability
of internet devices
Increased use of
internet services
Increased availability
of personal data online
User ignorance against
security threats
Multiple sources of
illegal data access
Heightened risk of
cybersecurity threats
Increased demand of
cybersecurity
professionals
Fig 1. Conceptual framework
(as created by the author)
Conclusion
This research therefore will focus on the reasons which encourage the demand and
recruitment of individuals who specialize and possess professional skills to combat cybersecurity
threats. This research will also look into possible sources of education which could enable
individuals interested in the said field to gain knowledge and apply the same in the growing
cybersecurity industry in the Information and Communications technology sector.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6REASONS FOR RECENT INCREASE IN DEMAND FOR CYBER SECURITY PROFESSIONALS
References
Catota, F., Morgan, M., & Sicker, D. (2019). Cybersecurity education in a developing nation: the
Ecuadorian environment. Journal Of Cybersecurity, 5(1). doi: 10.1093/cybsec/tyz001
Cybersecurity – Threats Challenges Opportunities. (2016). Retrieved from
https://www.acs.org.au/content/dam/acs/acs-publications/ACS_Cybersecurity_Guide.pdf
Dawson, J., & Thomson, R. (2018). The Future Cybersecurity Workforce: Going Beyond
Technical Skills for Successful Cyber Performance. Frontiers In Psychology. doi: doi:
10.3389/fpsyg.2018.00744
Fischer, E. (2016). Cybersecurity Issues and Challenges: In Brief. Congressional Research
Service, 7(5700). doi: R43831
Huergo, J. (2018). New Data Show Demand for Cybersecurity Professionals Accelerating.
Retrieved from https://www.nist.gov/news-events/news/2018/11/new-data-show-
demand-cybersecurity-professionals-accelerating
Jang-Jaccard, J., & Nepal, S. (2014). A survey of emerging threats in cybersecurity. Journal Of
Computer And System Sciences, 80, 973-993. doi:
http://dx.doi.org/10.1016/j.jcss.2014.02.005
References
Catota, F., Morgan, M., & Sicker, D. (2019). Cybersecurity education in a developing nation: the
Ecuadorian environment. Journal Of Cybersecurity, 5(1). doi: 10.1093/cybsec/tyz001
Cybersecurity – Threats Challenges Opportunities. (2016). Retrieved from
https://www.acs.org.au/content/dam/acs/acs-publications/ACS_Cybersecurity_Guide.pdf
Dawson, J., & Thomson, R. (2018). The Future Cybersecurity Workforce: Going Beyond
Technical Skills for Successful Cyber Performance. Frontiers In Psychology. doi: doi:
10.3389/fpsyg.2018.00744
Fischer, E. (2016). Cybersecurity Issues and Challenges: In Brief. Congressional Research
Service, 7(5700). doi: R43831
Huergo, J. (2018). New Data Show Demand for Cybersecurity Professionals Accelerating.
Retrieved from https://www.nist.gov/news-events/news/2018/11/new-data-show-
demand-cybersecurity-professionals-accelerating
Jang-Jaccard, J., & Nepal, S. (2014). A survey of emerging threats in cybersecurity. Journal Of
Computer And System Sciences, 80, 973-993. doi:
http://dx.doi.org/10.1016/j.jcss.2014.02.005
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



