Industrial Control System (ICS) / SCADA System Analysis Report
VerifiedAdded on 2023/04/21
|4
|1048
|381
Report
AI Summary
This report provides an analysis of an ICS/SCADA system, specifically focusing on iX HMI software. It begins with an abstract, followed by an introduction to industrial control systems and SCADA systems, emphasizing their role in power networks. The report details the components of iX HMI software, including Controller Data Exchange, Multi-Controller, Component Library, and others. A network diagram illustrates the system's architecture. Furthermore, the report identifies potential future challenges and examines the system's vulnerabilities and risks, such as anonymity, unknown perimeter, unknown path, system complexity, and sharing of files. The report concludes by summarizing the key findings and includes a bibliography of cited sources.

Abstract
In this report we will study and analyze the ICS/SCADA system. We will study and
analyze the design, behavior and components of such system. The risks and vulnerabilities of
these system also take in discussion briefly. We will also check and analyze the matters which
causes of security issues and how to overcome and get rid of these security issues.
Introduction
Industrial control system are control and command systems and networks that are
designed to support the processes of the industries. Supervisory Control and Data Acquisition
systems are the largest sub groups of the industrial control system (ICS). SCADA in power
network will be sketched out on the grounds that the power dissemination application that is
regularly bolstered the PC code bundle. The electrical appropriation framework comprises of
numerous substations; these substations can have various quantities of controllers, sensors and
administrator interface focuses.
When all is said in done, for overwhelming and watching a station progressively (PLCs)
Programmable Logic Controllers, Circuit breakers and Power screens are utilized. Information is
transmitted from the PLCs and distinctive gadgets to a PC based-SCADA hub arranged at each
station. One or extra PCs are arranged at totally unique brought together administration and
watching focuses.
The name of the organization that hold the software is Beijer Electronics. This
organization is the large organization and has the different branches in different locations of the
world. The main head quarter of this organization is in the SWEDEN. This organization has
different market sites in different countries like United Kingdom, Germany, Denmark, USA,
France, China, Turkey and Norway.
Components of iX HMI Software
The components of iX HMI software are as follows:
Controller Data Exchange
Multi-Controller
Component Library
Import third part component
Web Server
OPC UA Server
FTP Server
SQL Connectivity
Controller Data Exchange
Controller Data Exchange enables controller to exchange the real time data between
different controllers. This helps a lot in transferring the data from one component to other
component. This can be treated as the Gateway.
In this report we will study and analyze the ICS/SCADA system. We will study and
analyze the design, behavior and components of such system. The risks and vulnerabilities of
these system also take in discussion briefly. We will also check and analyze the matters which
causes of security issues and how to overcome and get rid of these security issues.
Introduction
Industrial control system are control and command systems and networks that are
designed to support the processes of the industries. Supervisory Control and Data Acquisition
systems are the largest sub groups of the industrial control system (ICS). SCADA in power
network will be sketched out on the grounds that the power dissemination application that is
regularly bolstered the PC code bundle. The electrical appropriation framework comprises of
numerous substations; these substations can have various quantities of controllers, sensors and
administrator interface focuses.
When all is said in done, for overwhelming and watching a station progressively (PLCs)
Programmable Logic Controllers, Circuit breakers and Power screens are utilized. Information is
transmitted from the PLCs and distinctive gadgets to a PC based-SCADA hub arranged at each
station. One or extra PCs are arranged at totally unique brought together administration and
watching focuses.
The name of the organization that hold the software is Beijer Electronics. This
organization is the large organization and has the different branches in different locations of the
world. The main head quarter of this organization is in the SWEDEN. This organization has
different market sites in different countries like United Kingdom, Germany, Denmark, USA,
France, China, Turkey and Norway.
Components of iX HMI Software
The components of iX HMI software are as follows:
Controller Data Exchange
Multi-Controller
Component Library
Import third part component
Web Server
OPC UA Server
FTP Server
SQL Connectivity
Controller Data Exchange
Controller Data Exchange enables controller to exchange the real time data between
different controllers. This helps a lot in transferring the data from one component to other
component. This can be treated as the Gateway.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Multi-Controller
One tag can be associated with a few controllers, which permits the equivalent HMI
application to keep running against various PLC's. Multi-controller can help in these situations.
Component Library
Secure a steady plan by sharing your segment library, or parts of it, with partners or sub
providers. Component Library can help to adjust different components for specific task.
Import Third Party Component
Importing the third party component defines the extensibility of the system. It is also
advantage from altered predefined segments, or request instant segments from a third party
supplier. iX enables you to import .NET gatherings, or capacity squares, and broaden the extent
of usefulness further.
Web Server
Web Server is an online portal which analyze the whole system. It also utilizing the board
web server you can plan a site page and access the board data from a remote area
OPC-UA Server
Boards can be server or customers, in this way they can convey by means of board
systems or between manufacturing plant floor and business framework.
FTP Server
File transfer protocol is an online server that is responsible for the transfer of file in the
network. It is conceivable to up and download documents to the administrator board from a
remote PC
SQL Connectivity
SQL connectivity is responsible for the management tasks. All the database activities
done through this connectivity.
One tag can be associated with a few controllers, which permits the equivalent HMI
application to keep running against various PLC's. Multi-controller can help in these situations.
Component Library
Secure a steady plan by sharing your segment library, or parts of it, with partners or sub
providers. Component Library can help to adjust different components for specific task.
Import Third Party Component
Importing the third party component defines the extensibility of the system. It is also
advantage from altered predefined segments, or request instant segments from a third party
supplier. iX enables you to import .NET gatherings, or capacity squares, and broaden the extent
of usefulness further.
Web Server
Web Server is an online portal which analyze the whole system. It also utilizing the board
web server you can plan a site page and access the board data from a remote area
OPC-UA Server
Boards can be server or customers, in this way they can convey by means of board
systems or between manufacturing plant floor and business framework.
FTP Server
File transfer protocol is an online server that is responsible for the transfer of file in the
network. It is conceivable to up and download documents to the administrator board from a
remote PC
SQL Connectivity
SQL connectivity is responsible for the management tasks. All the database activities
done through this connectivity.
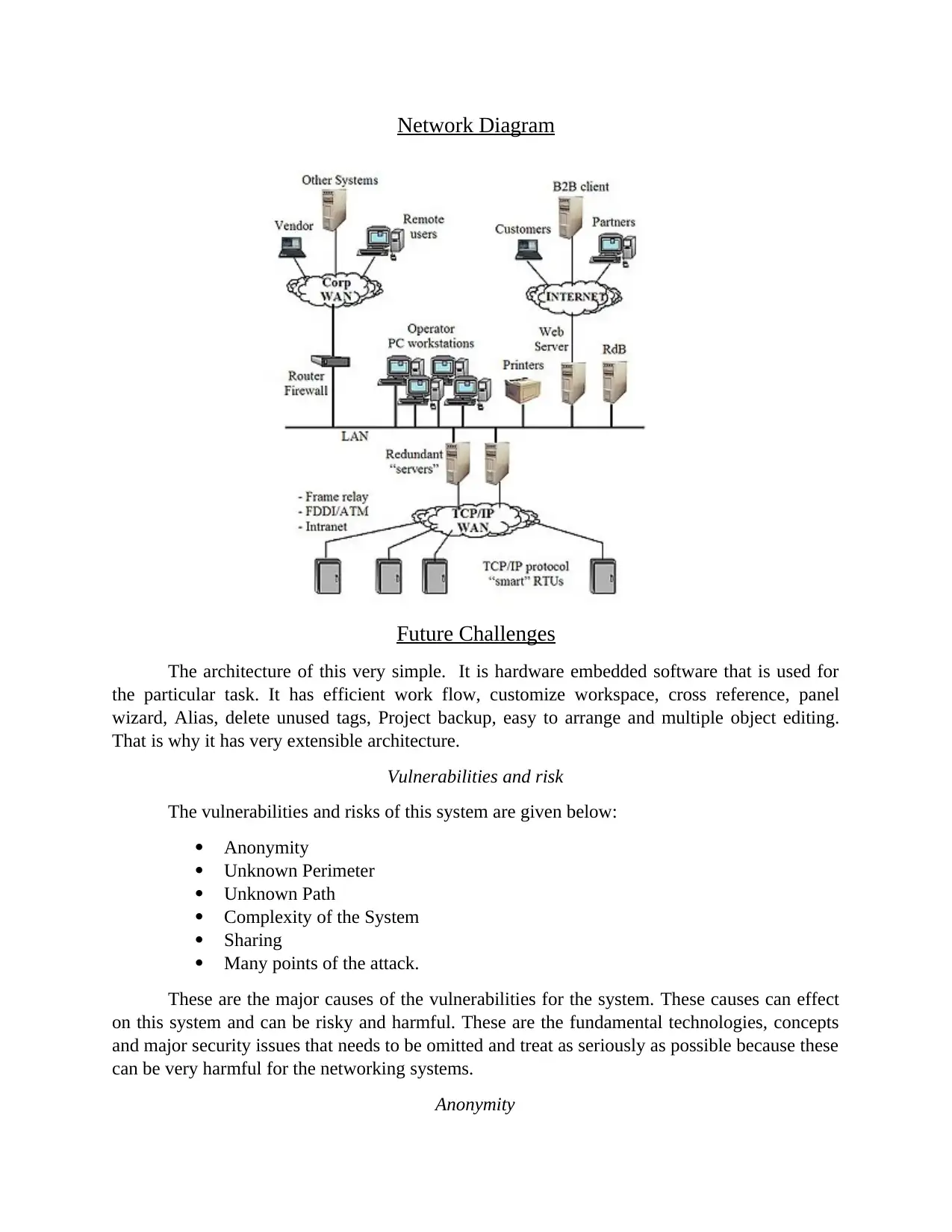
Network Diagram
Future Challenges
The architecture of this very simple. It is hardware embedded software that is used for
the particular task. It has efficient work flow, customize workspace, cross reference, panel
wizard, Alias, delete unused tags, Project backup, easy to arrange and multiple object editing.
That is why it has very extensible architecture.
Vulnerabilities and risk
The vulnerabilities and risks of this system are given below:
Anonymity
Unknown Perimeter
Unknown Path
Complexity of the System
Sharing
Many points of the attack.
These are the major causes of the vulnerabilities for the system. These causes can effect
on this system and can be risky and harmful. These are the fundamental technologies, concepts
and major security issues that needs to be omitted and treat as seriously as possible because these
can be very harmful for the networking systems.
Anonymity
Future Challenges
The architecture of this very simple. It is hardware embedded software that is used for
the particular task. It has efficient work flow, customize workspace, cross reference, panel
wizard, Alias, delete unused tags, Project backup, easy to arrange and multiple object editing.
That is why it has very extensible architecture.
Vulnerabilities and risk
The vulnerabilities and risks of this system are given below:
Anonymity
Unknown Perimeter
Unknown Path
Complexity of the System
Sharing
Many points of the attack.
These are the major causes of the vulnerabilities for the system. These causes can effect
on this system and can be risky and harmful. These are the fundamental technologies, concepts
and major security issues that needs to be omitted and treat as seriously as possible because these
can be very harmful for the networking systems.
Anonymity
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

An attack that can be mounted by the attacker from thousands of miles and never come
into direct system, administrator, or user is anonymity.
Unknown Perimeter
Unknown or uncontrolled group of possibly malicious users is a security disadvantage. These are
due to the accessibility of the network at different nodes.
Unknown Path
As the system can be access from the different host. And an attack can be came from unknown
host that contain unknown path.
Complexity of the System
If the system is complex than the operating system than it is also the cause of the network
vulnerability.
Sharing
Sharing a virus affected file in the network can also cause for the network vulnerability. This can
also steal the major information regarding this network.
Attack from multiple access
When a file is stored in a network host remote from the user, the data or the file itself may pass
through many hosts to get to the user.
Conclusion
In this report, we studied the real time example of ICS/SCADA system in the shape of iX
HMI software. We studied the functionality, architecture and components of this system. We
also mentioned the vulnerabilities and security issues which this system can have.
Bibliography
business-it-security-vulnerabilities. (n.d.). Retrieved from https://www.dobson.net:
https://www.dobson.net/7-business-it-security-vulnerabilities/
cyber-security-essentials. (n.d.). Retrieved from https://www.sans.org: https://www.sans.org/course/ics-
scada-cyber-security-essentials
Watts, S. (2017, June 21). security-vulnerability-vs-threat-vs-risk-whats-difference. Retrieved from
https://www.bmc.com/blogs: https://www.bmc.com/blogs/security-vulnerability-vs-threat-vs-
risk-whats-difference/
into direct system, administrator, or user is anonymity.
Unknown Perimeter
Unknown or uncontrolled group of possibly malicious users is a security disadvantage. These are
due to the accessibility of the network at different nodes.
Unknown Path
As the system can be access from the different host. And an attack can be came from unknown
host that contain unknown path.
Complexity of the System
If the system is complex than the operating system than it is also the cause of the network
vulnerability.
Sharing
Sharing a virus affected file in the network can also cause for the network vulnerability. This can
also steal the major information regarding this network.
Attack from multiple access
When a file is stored in a network host remote from the user, the data or the file itself may pass
through many hosts to get to the user.
Conclusion
In this report, we studied the real time example of ICS/SCADA system in the shape of iX
HMI software. We studied the functionality, architecture and components of this system. We
also mentioned the vulnerabilities and security issues which this system can have.
Bibliography
business-it-security-vulnerabilities. (n.d.). Retrieved from https://www.dobson.net:
https://www.dobson.net/7-business-it-security-vulnerabilities/
cyber-security-essentials. (n.d.). Retrieved from https://www.sans.org: https://www.sans.org/course/ics-
scada-cyber-security-essentials
Watts, S. (2017, June 21). security-vulnerability-vs-threat-vs-risk-whats-difference. Retrieved from
https://www.bmc.com/blogs: https://www.bmc.com/blogs/security-vulnerability-vs-threat-vs-
risk-whats-difference/
1 out of 4
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.