Enterprise-Wide Risk Management Framework: INF80043 Report
VerifiedAdded on 2023/03/20
|3
|840
|79
Report
AI Summary
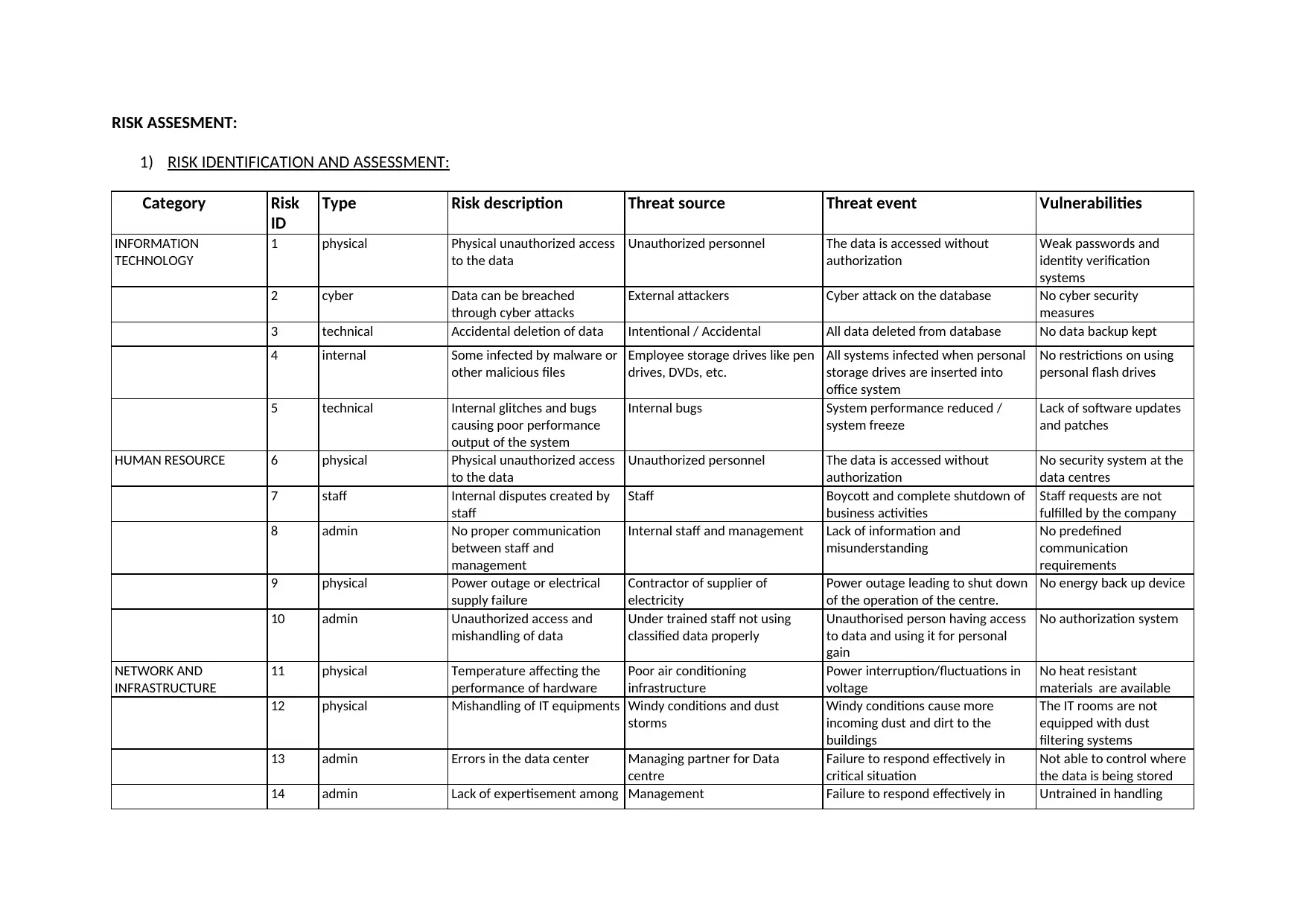
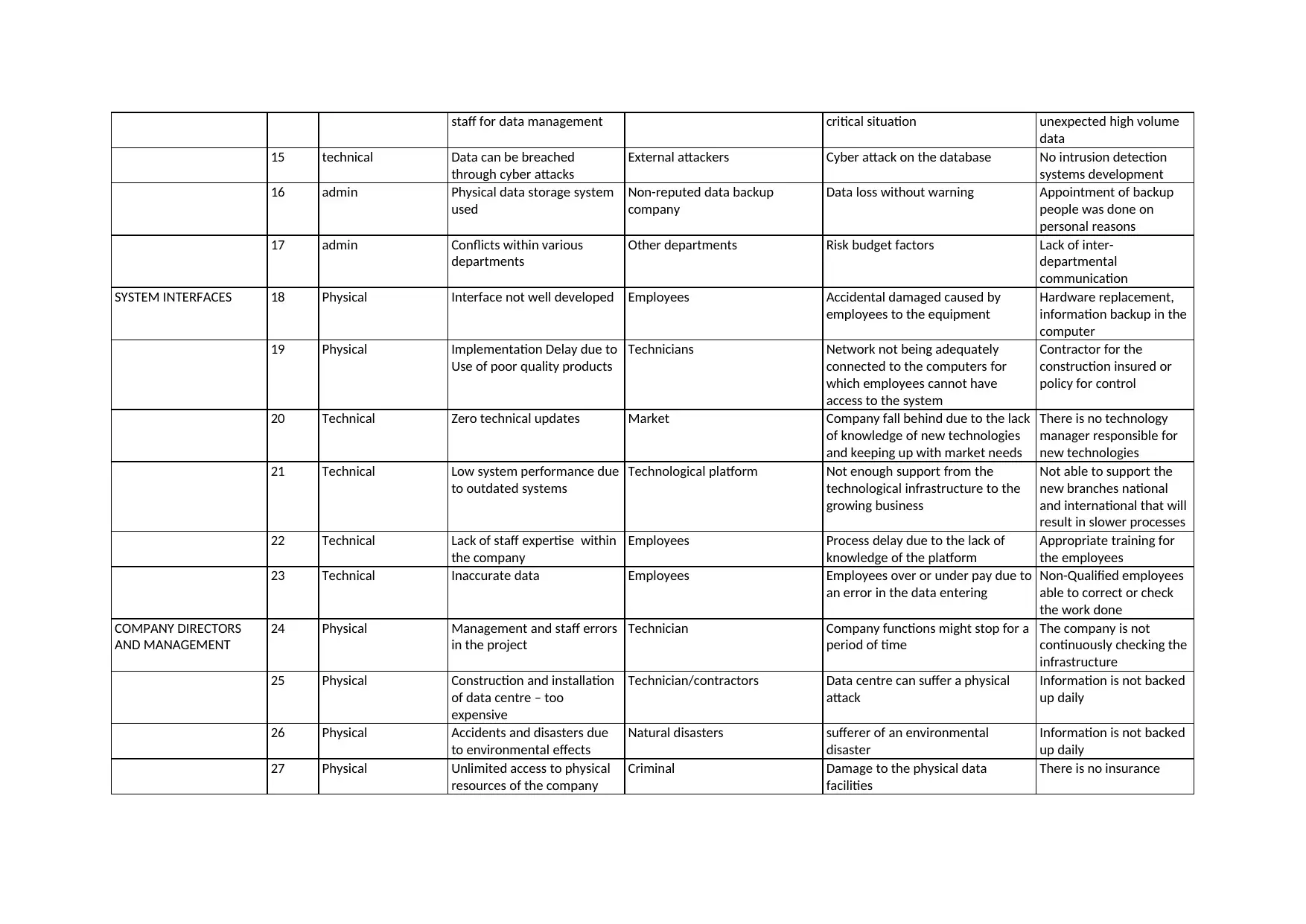
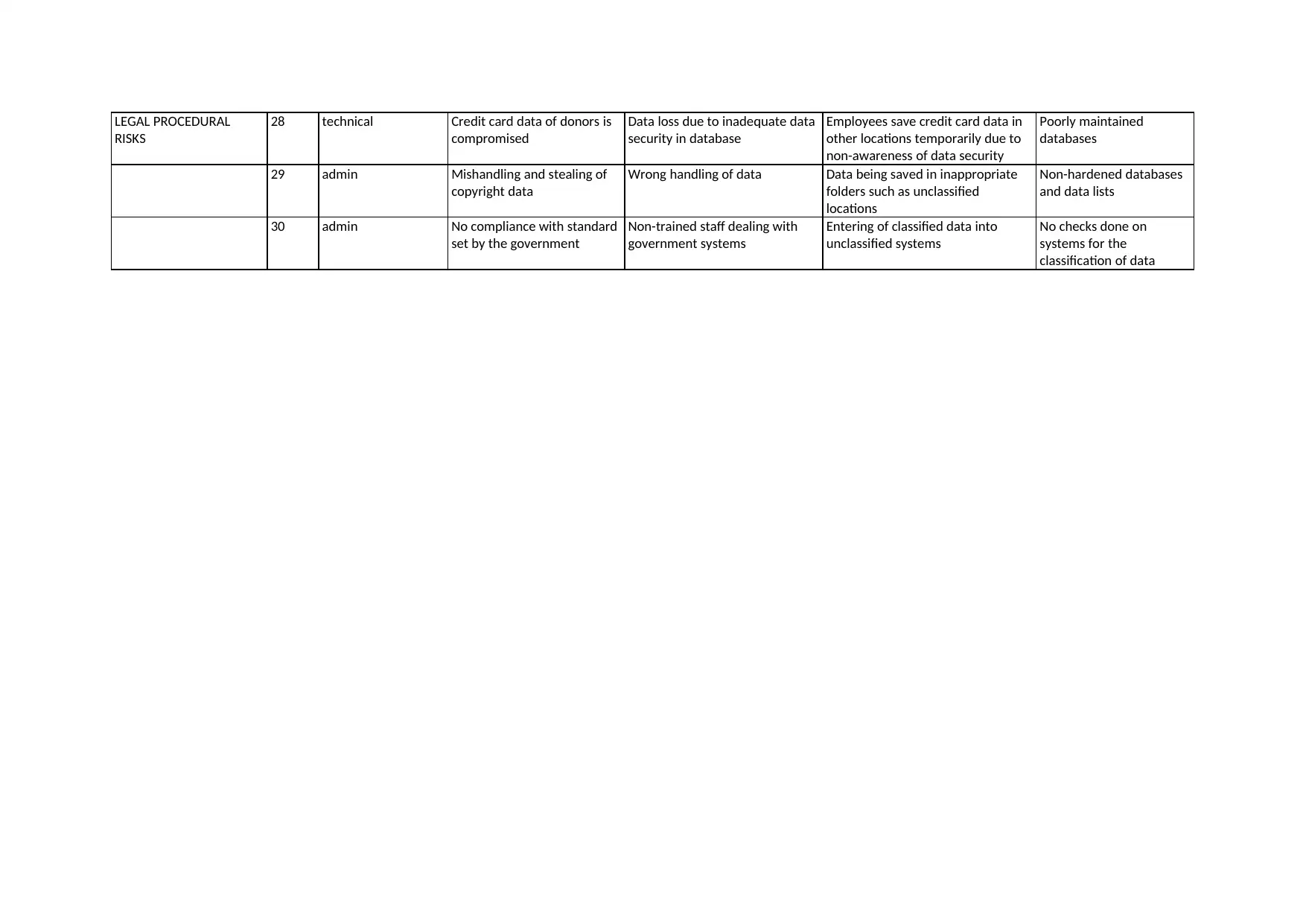
This report presents a comprehensive risk assessment, covering various categories such as information technology, human resources, network and infrastructure, and legal/procedural risks. It identifies numerous potential threats, vulnerabilities, and risk events, detailing their sources and impacts on organizational functions. The assessment includes a detailed analysis of the scenario involving a data breach and outlines the roles and responsibilities of IT managers, CIOs, and CEOs in addressing such incidents. Furthermore, the report explores the importance of risk management processes, including risk identification, control, and mitigation, while emphasizing the need for a systematic approach. It also addresses the concepts of due care, due diligence, and vicarious liability in information security, alongside the significance of contingency planning and incident response. The report provides insights into the impacts of information asset exploitation, the importance of information security, and the roles of management in ensuring IS/IT asset security. The report draws upon the course INF80043, emphasizing the need for proactive measures to prepare for worst-case scenarios and the integration of IS/IT risk management into business strategy and governance.
1 out of 3




![[object Object]](/_next/static/media/star-bottom.7253800d.svg)