Information Security Countermeasures and Solutions Report - Analysis
VerifiedAdded on 2020/07/23
|14
|4978
|51
Report
AI Summary
This report provides an in-depth analysis of information security challenges faced by Australia, focusing on vulnerabilities, threats, risks, and effective countermeasures. It explores various cybercrime incidents, including malware attacks, data breaches, and hacking attempts, highlighting the impact on businesses, government, and critical infrastructure. The report identifies the involvement of foreign entities in cyberattacks and discusses the financial and national security implications. It examines specific cases, such as the CODAN Ltd. incident and the impact of ransomware, and evaluates the effectiveness of existing security measures. The report also offers recommendations for strengthening cybersecurity, including software upgrades, anti-malware software, and government initiatives to protect against cyber warfare. Furthermore, the report emphasizes the need for proactive measures to safeguard personal and professional data and protect against the increasing sophistication of cyber threats. The report highlights the increasing number of cybercrime reports and the government's efforts to address these threats, including financial investments and the implementation of offensive cyber-warfare operations. The report concludes by emphasizing the importance of protecting the country's critical infrastructure and national security against cyberattacks.

Report on information
security counter measures
and solutions
security counter measures
and solutions
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION..........................................................................................................................1
Identify and explain all the potential vulnerabilities.............................................................1
Appropriate threats, impacts and risks..................................................................................5
Cyber crime and security countermeasures demonstrated:...................................................7
Timeline mapping..................................................................................................................8
Recommendations.................................................................................................................9
REFERENCES.............................................................................................................................11
INTRODUCTION..........................................................................................................................1
Identify and explain all the potential vulnerabilities.............................................................1
Appropriate threats, impacts and risks..................................................................................5
Cyber crime and security countermeasures demonstrated:...................................................7
Timeline mapping..................................................................................................................8
Recommendations.................................................................................................................9
REFERENCES.............................................................................................................................11

INTRODUCTION
In the modern world there are various beneficial changes that can be seen through the
technology. There are immense development in the Engineering field that can be seen within last
decade. It has profited to almost every sector and segment in the market. Similarly, advancement
can be seen in the information technology which is ubiquitous recognized by people. Cloud
computing, artificial intelligence and many more applications are developed that support to
human life and their working (Duncan, Zhao, and Whittington, 2017). However, there are people
that uses these technologies in negative way popularly known as cybercrime. There are people
like corporate raiders, hackers, spies, terrorists, professional criminals and vandals that can bring
the cyber warfare. Using network system they can bring vulnerabilities to the system and nation's
security. There are various communities and cyber-security agencies that are identifying convicts
but there are no specific evidence that can prove it. Current reports is about the information
security counter experienced by Australia and effective measures and solution that can aid them
from such issues.
Identify and explain all the potential vulnerabilities.
Arthur, (2011) have stated hackers requires only little time and inquiring mind in order to
hack the professional and personal information. Millions of people are using the Microsoft's
Windows where hackers have identified many security holes. Moreover, they are not-updated
which leaves the holes unpatched. There are no boundaries for hacking, and many countries
including Australia, Germany, Britain, US and India are affected due to such cases. China is
among the most suspicion and has produced dangerously effective hackers. Such activities are
also identified by the Australian Cyber Corporation department, Australian Security Intelligence
Organisation (Ng, 2016). Hackers from that country gather private or secret information of other
countries, companies and government and use them as per their benefits. Such issues are
experienced by the Australian industries, government in recent months and were facing higher
conflicts. Even modern computer systems are vulnerable hacking. There are more than 1000
cases that happened in recent years in Australia.
One of the such case is of CODAN Ltd. which they experienced 2 years ago. They faced
issues when they sold their metal detector to the customers which was returned due to improper
working. China produced the fake products and was selling it using the company's brand name
(the control copy was of Australia but electronics and other things were made in China).
1
In the modern world there are various beneficial changes that can be seen through the
technology. There are immense development in the Engineering field that can be seen within last
decade. It has profited to almost every sector and segment in the market. Similarly, advancement
can be seen in the information technology which is ubiquitous recognized by people. Cloud
computing, artificial intelligence and many more applications are developed that support to
human life and their working (Duncan, Zhao, and Whittington, 2017). However, there are people
that uses these technologies in negative way popularly known as cybercrime. There are people
like corporate raiders, hackers, spies, terrorists, professional criminals and vandals that can bring
the cyber warfare. Using network system they can bring vulnerabilities to the system and nation's
security. There are various communities and cyber-security agencies that are identifying convicts
but there are no specific evidence that can prove it. Current reports is about the information
security counter experienced by Australia and effective measures and solution that can aid them
from such issues.
Identify and explain all the potential vulnerabilities.
Arthur, (2011) have stated hackers requires only little time and inquiring mind in order to
hack the professional and personal information. Millions of people are using the Microsoft's
Windows where hackers have identified many security holes. Moreover, they are not-updated
which leaves the holes unpatched. There are no boundaries for hacking, and many countries
including Australia, Germany, Britain, US and India are affected due to such cases. China is
among the most suspicion and has produced dangerously effective hackers. Such activities are
also identified by the Australian Cyber Corporation department, Australian Security Intelligence
Organisation (Ng, 2016). Hackers from that country gather private or secret information of other
countries, companies and government and use them as per their benefits. Such issues are
experienced by the Australian industries, government in recent months and were facing higher
conflicts. Even modern computer systems are vulnerable hacking. There are more than 1000
cases that happened in recent years in Australia.
One of the such case is of CODAN Ltd. which they experienced 2 years ago. They faced
issues when they sold their metal detector to the customers which was returned due to improper
working. China produced the fake products and was selling it using the company's brand name
(the control copy was of Australia but electronics and other things were made in China).
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CODAN was victim of industrial-avalanche. Moreover, the issues was identified by the dealers
as their system was hacked by China. The possible ways are by entering the malware, spyware or
virus to the system. The main reason behind it was the executive which visited China for office
purpose and accessed Hotel's Wi-Fi. Within fraction of seconds the malicious software was
installed to system and all the private company details were available to the hackers. Ngo, and
Jaishankar, (2017) have identified that malware attacks such as spam are increasing. Malware are
the malicious software developed by the hackers to gain authorized access, disrupt or damage
user's computer. However, spyware are also similar to that but they gather personal information
and internet activities. All the private information of the company was with others. It has
affected their brand image, values, private data, and technology. Moreover, it could help the
competitor to provide the same materials at cheaper rates. Further, the software was transferred
to the other system of CODAN (Alazab and Broadhurst, 2017).
Not only the Australian companies, impact can also be seen on IT companies such as
Yahoo where more than 3bn user data was hacked by hackers. There are several other companies
that have experienced threats from the hackers however, due to impact on company brand name
these issues are not specifically identified. CONDAN was also developing the decoding devices
which helps to decode the data and was selling it to US, UK and Australian government. This
has increases the level of consequence that the company was going to face. However, they made
changes in their security system and protected their data. John Blackburn, National Security
Consultant said that from such hacking companies can never get protected however, some of the
security measure can be taken to protect the privacy of the company. China has been identified
by many other countries for spying and hacking the system. There are certain companies that
have good relationship with China. They provide them raw material and minerals as-well-as
other construction materials (Hui, Kim and Wang, 2017). One such companies from Australia is
Blue Scope Steel that has plants in Beijing, Suzhou and Shanghai. Similar companies are helping
the Chinese hackers to access the data of Australia.
Gary Waters, AIF strategic consultants, said that government and industries must protect
their system with software up-gradation and other anti-malware software so that these activities
can be prevented. There are billions of dollars that Australian government has to spent in order to
prevent the cyber warfare. The issues are increasing as the technologies are integrating with the
other system. Now airlines, railways, communication and other devices can becoming the
2
as their system was hacked by China. The possible ways are by entering the malware, spyware or
virus to the system. The main reason behind it was the executive which visited China for office
purpose and accessed Hotel's Wi-Fi. Within fraction of seconds the malicious software was
installed to system and all the private company details were available to the hackers. Ngo, and
Jaishankar, (2017) have identified that malware attacks such as spam are increasing. Malware are
the malicious software developed by the hackers to gain authorized access, disrupt or damage
user's computer. However, spyware are also similar to that but they gather personal information
and internet activities. All the private information of the company was with others. It has
affected their brand image, values, private data, and technology. Moreover, it could help the
competitor to provide the same materials at cheaper rates. Further, the software was transferred
to the other system of CODAN (Alazab and Broadhurst, 2017).
Not only the Australian companies, impact can also be seen on IT companies such as
Yahoo where more than 3bn user data was hacked by hackers. There are several other companies
that have experienced threats from the hackers however, due to impact on company brand name
these issues are not specifically identified. CONDAN was also developing the decoding devices
which helps to decode the data and was selling it to US, UK and Australian government. This
has increases the level of consequence that the company was going to face. However, they made
changes in their security system and protected their data. John Blackburn, National Security
Consultant said that from such hacking companies can never get protected however, some of the
security measure can be taken to protect the privacy of the company. China has been identified
by many other countries for spying and hacking the system. There are certain companies that
have good relationship with China. They provide them raw material and minerals as-well-as
other construction materials (Hui, Kim and Wang, 2017). One such companies from Australia is
Blue Scope Steel that has plants in Beijing, Suzhou and Shanghai. Similar companies are helping
the Chinese hackers to access the data of Australia.
Gary Waters, AIF strategic consultants, said that government and industries must protect
their system with software up-gradation and other anti-malware software so that these activities
can be prevented. There are billions of dollars that Australian government has to spent in order to
prevent the cyber warfare. The issues are increasing as the technologies are integrating with the
other system. Now airlines, railways, communication and other devices can becoming the
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

electronic controlled. These devices can be easily controlled using Wi-Fi or other networks and
performance can be hampered. The country is considered as vulnerable in terms of the cyber
attacks and need possible solution to protect themselves. There are other software such as
ransomware and WannaCry attack, that has affected the Australian government, companies and
people(Arthur, 2011). These are similar to above viruses where personal and private data are
accessed by the hackers. Victims were asked to pay Bitcoins in order to get their details and
private account back. After the virus attack every company were warned about the security patch
that user must start in order to protect the system.
As per the Durkin (2017), in terms of the cybercrime there were more than 114,000
reports after 2014. The reports were recorded by the Australian Cybercrime Online Reporting
Network (ACORN). Moreover, the attacks also affected the security system of the Australia.
Prime Minister Malcolm Turnbull have to command the offensive military cyber-warfare
operations in order to get protected from such attacks. Foreign criminal networks have somehow
started to access the private data of the Australian government. Though, companies were facing
the issues of cyber security breach but now government have to spend more than $630 million in
order to protect the national security against cyber crime (Ngo and Jaishankar, 2017). It was
accounted that country has to pat more than $1 billion each year in order to protect their private
data. Sphere phishing emails are other sources where these malware and other software can be
installed. These are send by the hackers to know their personal details like account passwords,
financial information and other bank details. Other than this, Australian government has
identified Petya ransomware which access the user system and demands for the $300 to be paid
in Bitcoin. It was started in Ukrainian and part of European counties. However, has reached to
the global level and is affecting the people.
Chinese Ambassador, Chen Yuming has denied that there is no such activities conducted
in China and they too are getting affected to this situations. He mentioned that in China also due
to oversea there were more than 1000 cases registered (Durkin, 2017). The active report of the
other country details stated that these cyber attacks were from the China. There is greater threat
to Australia as the China is more economical power in terms of military and technologies. They
are using the Sphere phishing virus to access the military data and other governmental
information (Smith and Ingram, 2017). Moreover, they have simple performing, the virus
activates itself after single click. After that, whenever the system is connected to the internet it
3
performance can be hampered. The country is considered as vulnerable in terms of the cyber
attacks and need possible solution to protect themselves. There are other software such as
ransomware and WannaCry attack, that has affected the Australian government, companies and
people(Arthur, 2011). These are similar to above viruses where personal and private data are
accessed by the hackers. Victims were asked to pay Bitcoins in order to get their details and
private account back. After the virus attack every company were warned about the security patch
that user must start in order to protect the system.
As per the Durkin (2017), in terms of the cybercrime there were more than 114,000
reports after 2014. The reports were recorded by the Australian Cybercrime Online Reporting
Network (ACORN). Moreover, the attacks also affected the security system of the Australia.
Prime Minister Malcolm Turnbull have to command the offensive military cyber-warfare
operations in order to get protected from such attacks. Foreign criminal networks have somehow
started to access the private data of the Australian government. Though, companies were facing
the issues of cyber security breach but now government have to spend more than $630 million in
order to protect the national security against cyber crime (Ngo and Jaishankar, 2017). It was
accounted that country has to pat more than $1 billion each year in order to protect their private
data. Sphere phishing emails are other sources where these malware and other software can be
installed. These are send by the hackers to know their personal details like account passwords,
financial information and other bank details. Other than this, Australian government has
identified Petya ransomware which access the user system and demands for the $300 to be paid
in Bitcoin. It was started in Ukrainian and part of European counties. However, has reached to
the global level and is affecting the people.
Chinese Ambassador, Chen Yuming has denied that there is no such activities conducted
in China and they too are getting affected to this situations. He mentioned that in China also due
to oversea there were more than 1000 cases registered (Durkin, 2017). The active report of the
other country details stated that these cyber attacks were from the China. There is greater threat
to Australia as the China is more economical power in terms of military and technologies. They
are using the Sphere phishing virus to access the military data and other governmental
information (Smith and Ingram, 2017). Moreover, they have simple performing, the virus
activates itself after single click. After that, whenever the system is connected to the internet it
3

starts sending the private details of the users to the hackers. Other than this, western countries are
unable to compete them due to their tactics. As per the professor Des Ball, Strategic and Defence
Study Centre have acknowledged that most the attacks will be experienced by the electronic
privacy activities. Various other countries have identified that China has been sources of hackers
and they were trying to access the personal data (Meekin, 2016). Many researchers from the
Australia and people associated with Cyber security were facing the serious consequence as they
knew that China was getting their personal details/ information but they were unaware about the
methods they were going to use those data. Along with this they have to identify what possible
impact will Australia have from such activities. Security warning are provided by the
government to the local companies and households to protect their data and private information
whenever they identify such cases.
Mr. Clark chief executive of US-based Symantec has warned Australia as the cyber
attacks were increasing rapidly, the country has been ranked 11th at the international level and
3rd for ransomware attacks (Global cyberattack: Australia considers calling in the military,
2017). Moreover, there is rise in the cases of such activities to 50%. Chinese hackers have
somehow got the access to the defence of the country. Along with this, the attack reached to the
Department of Prime Ministers Cabinet, Parliamentary house where attackers were able to
overlook the private details (Shafqat and Masood, 2016). All this process was started from the
Tourism portal, information was hacked and complete system data was accessed by them. At
Department of Foreign Affairs and Trade, the private and confidential details of the country was
there that was accessed by these people. It was identified that some of the greedy business person
of Australia were also involved in these system. They help these hackers so that their personal
motives can be carried out. There was another issue that was highlighted by the government
where blue print of the company was taken. There were protective wire shielding and other full
protection for the Australian Police, however all the things were ineffective. There were issues in
installing the communication system, lighting and other security system as the blueprint has
exposed all the details to hackers. There was only one thing identified that the contractor was
involved in the leak but there was no proof of that thing. Other than this there are various other
cases where Australian government departments had to face issues due to hackers (Saran, 2016).
Such cases are increasing rapidly and there is need to identify proper solution to these things.
4
unable to compete them due to their tactics. As per the professor Des Ball, Strategic and Defence
Study Centre have acknowledged that most the attacks will be experienced by the electronic
privacy activities. Various other countries have identified that China has been sources of hackers
and they were trying to access the personal data (Meekin, 2016). Many researchers from the
Australia and people associated with Cyber security were facing the serious consequence as they
knew that China was getting their personal details/ information but they were unaware about the
methods they were going to use those data. Along with this they have to identify what possible
impact will Australia have from such activities. Security warning are provided by the
government to the local companies and households to protect their data and private information
whenever they identify such cases.
Mr. Clark chief executive of US-based Symantec has warned Australia as the cyber
attacks were increasing rapidly, the country has been ranked 11th at the international level and
3rd for ransomware attacks (Global cyberattack: Australia considers calling in the military,
2017). Moreover, there is rise in the cases of such activities to 50%. Chinese hackers have
somehow got the access to the defence of the country. Along with this, the attack reached to the
Department of Prime Ministers Cabinet, Parliamentary house where attackers were able to
overlook the private details (Shafqat and Masood, 2016). All this process was started from the
Tourism portal, information was hacked and complete system data was accessed by them. At
Department of Foreign Affairs and Trade, the private and confidential details of the country was
there that was accessed by these people. It was identified that some of the greedy business person
of Australia were also involved in these system. They help these hackers so that their personal
motives can be carried out. There was another issue that was highlighted by the government
where blue print of the company was taken. There were protective wire shielding and other full
protection for the Australian Police, however all the things were ineffective. There were issues in
installing the communication system, lighting and other security system as the blueprint has
exposed all the details to hackers. There was only one thing identified that the contractor was
involved in the leak but there was no proof of that thing. Other than this there are various other
cases where Australian government departments had to face issues due to hackers (Saran, 2016).
Such cases are increasing rapidly and there is need to identify proper solution to these things.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Appropriate threats, impacts and risks
There is great threats to the personal and professional details of the company. Other than
this, economical and financial data are most affected due to the cybercrime. It could cause more
than billions of loss as the country has to protect from such cases and the investment made to
reduce such cases. Along with this there are issues to the national security and critical
infrastructure of the country. In the coming years as the technological advancement will be there
so defects in such cases can increase the faults and create more threats to the country. There will
be higher incidents of massive data breaches (Gupta, Agrawal and Yamaguchi, 2016). In the
country, all the electronic, digital as-well-as communication devices will get disintegrate. In total
there will be potentially enormous physical losses as well as liabilities. Every year, cyber
incidents, attacks and cases are increasing. Many counties have identified that China was
involved in such cases, however, there are no proof that can be approve it that are using it for
their personal benefits. There will be great impact to the banking, financial, governmental,
educational, healthcare and business. Among the mentioned field, higher impact can be seen in
the medical and healthcare sector that is mostly going to get affected. Other than this, there are
large impacts which Australian business have faced due to cyber-attacks and there are chances
that high data breaching can be experienced in the business and industrial sectors (Govt.
confirms Australia hit in cyber attack, 2017).
Not only government and business entrepreneurs also have to sort out these issues as they
too have to invest billions to protect the private data and other information. It can completely
ruin the firm image and hackers may provide these information to their competitor so that they
can better growth. Most of the cyber crimes were seen from the China however, no possible steps
can be taken from there(Štitilis, Pakutinskas and Malinauskaitė-van de Castel, 2016). Threats
such as loss of intellectual property, price of countermeasures, mitigation strategies, insurance
and recovery from cyber attacks. Along with this, there can be distortion of trade or even it c an
be loss of trade and competitiveness as seen in the case study.
There will less opportunities and higher costs for the data protection which will including
service and employment disruptions. For the companies that has faced the cyber threats will have
damage brand image and reputation. Symantec ltd. has mentioned that there are 250,000 web
attacks that are daily blocked by the site, they also mentioned that most of internet websites were
infected and around 1.6 million of new malware are identified everyday (Vogel, 2016).
5
There is great threats to the personal and professional details of the company. Other than
this, economical and financial data are most affected due to the cybercrime. It could cause more
than billions of loss as the country has to protect from such cases and the investment made to
reduce such cases. Along with this there are issues to the national security and critical
infrastructure of the country. In the coming years as the technological advancement will be there
so defects in such cases can increase the faults and create more threats to the country. There will
be higher incidents of massive data breaches (Gupta, Agrawal and Yamaguchi, 2016). In the
country, all the electronic, digital as-well-as communication devices will get disintegrate. In total
there will be potentially enormous physical losses as well as liabilities. Every year, cyber
incidents, attacks and cases are increasing. Many counties have identified that China was
involved in such cases, however, there are no proof that can be approve it that are using it for
their personal benefits. There will be great impact to the banking, financial, governmental,
educational, healthcare and business. Among the mentioned field, higher impact can be seen in
the medical and healthcare sector that is mostly going to get affected. Other than this, there are
large impacts which Australian business have faced due to cyber-attacks and there are chances
that high data breaching can be experienced in the business and industrial sectors (Govt.
confirms Australia hit in cyber attack, 2017).
Not only government and business entrepreneurs also have to sort out these issues as they
too have to invest billions to protect the private data and other information. It can completely
ruin the firm image and hackers may provide these information to their competitor so that they
can better growth. Most of the cyber crimes were seen from the China however, no possible steps
can be taken from there(Štitilis, Pakutinskas and Malinauskaitė-van de Castel, 2016). Threats
such as loss of intellectual property, price of countermeasures, mitigation strategies, insurance
and recovery from cyber attacks. Along with this, there can be distortion of trade or even it c an
be loss of trade and competitiveness as seen in the case study.
There will less opportunities and higher costs for the data protection which will including
service and employment disruptions. For the companies that has faced the cyber threats will have
damage brand image and reputation. Symantec ltd. has mentioned that there are 250,000 web
attacks that are daily blocked by the site, they also mentioned that most of internet websites were
infected and around 1.6 million of new malware are identified everyday (Vogel, 2016).
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Moreover, in Australia, the cases are increasing regarding the attack activities, malware,
vulnerabilities and phishing. Malware are more spread from the social media sites, mobile
applications. Higher the employees in the companies and their growth, greater they are affected
from such cases. Impact to the business and technologies will be more as these hackers earn
higher from these industries.
For the government and companies, eliminating risk is impossible and it impedes agility.
They have to define their risk appetite and have to become Cyber Resilient of their own
(Hashim, Masrek and Yunos, 2016). The cyber security can be achieved by the company using
the cyber resilience methods. It is based on the cyber-resilience framework where three factors
are considered, human, technology and process. They have to know (find, categorize and
aggregate), prevent (define, build and maintain), detect (monitor, analyse and alert), respond
(block, remediate and restore) control (audits) so that they remain protected from the system.
However, there are some of the legal developments that can be seen in this area such as
Data Breach Liability
Class Action Lawsuits
Data Breach Insurance Coverage
Companies that have affected from the cyber attacks may get protection using the insurance
(Chang, 2016). Types of cyber risk coverage include:
Loss/Corruption of Data
Business Interruption
Liabilities
D&O/Management Liability
Cyber Extortion
Criminal Rewards
Crisis Management
Data Breach and theft
Social Media/Networking and cloud computing.
These are the areas where protection can be seen and large data can be protected. Further,
government should help these companies to protect their data and should support them. They
should notify other companies that they could tell were targeted by the same attackers. Such
6
vulnerabilities and phishing. Malware are more spread from the social media sites, mobile
applications. Higher the employees in the companies and their growth, greater they are affected
from such cases. Impact to the business and technologies will be more as these hackers earn
higher from these industries.
For the government and companies, eliminating risk is impossible and it impedes agility.
They have to define their risk appetite and have to become Cyber Resilient of their own
(Hashim, Masrek and Yunos, 2016). The cyber security can be achieved by the company using
the cyber resilience methods. It is based on the cyber-resilience framework where three factors
are considered, human, technology and process. They have to know (find, categorize and
aggregate), prevent (define, build and maintain), detect (monitor, analyse and alert), respond
(block, remediate and restore) control (audits) so that they remain protected from the system.
However, there are some of the legal developments that can be seen in this area such as
Data Breach Liability
Class Action Lawsuits
Data Breach Insurance Coverage
Companies that have affected from the cyber attacks may get protection using the insurance
(Chang, 2016). Types of cyber risk coverage include:
Loss/Corruption of Data
Business Interruption
Liabilities
D&O/Management Liability
Cyber Extortion
Criminal Rewards
Crisis Management
Data Breach and theft
Social Media/Networking and cloud computing.
These are the areas where protection can be seen and large data can be protected. Further,
government should help these companies to protect their data and should support them. They
should notify other companies that they could tell were targeted by the same attackers. Such
6

notification and can protect users who had been targeted. They learned from their mistakes and
took strong measures to protect themselves from similar attacks in the future.
Cyber crime and security countermeasures demonstrated:
Any crime that involves a computer and a network is considered as a cybercrime. These
crimes are for the purpose of stealing money, personal information, credit card details, etc. In the
present technological era, all the function from intelligence, security of nation, economical
procedures that are being performed with the assistance of internet are having severe future
threats. There are different types of cybercrime, some of them are as follows:
Hacking: It is the most popular way to attempt the crime. In this, unauthorised access to the
computers and networks is performed by the external elements.
Trojan: These are the programmes which perform the different tasks then the one which they
were meant to execute.
Viruses: It is an external source that when entered to the network, infects the other files, data and
programmes by modifying.
Ransomware: It is a malicious software that threatens to publish the data. In present context, the
threat of ransomware is major. It is a malware virus that attacks on the users' system and prevents
them to access the same by locking the system's screens.
These cyber-attacks results in the theft or breach of confidential information that may
cause various challenges. In the present case, the Chinese hacker may have used any of these
methods to steal the software design. Hence, the government of Australia is required to develop
security countermeasures buy considering all these factors in the planning. The countermeasures
can be defined as the action, system, process or technology that can be used to eliminate the
affects of cyber attack on the computers, networks or serves. There are various cyber security
tools present for counter-measuring the attacks. Some of them involves Wireshark, Metasploit,
Nessus, Aircrack and Snort.
In order to avoid such cases in future, the organisation can use the Patching application in
the systems and devices that are used in the software designing. This technique covers the
fixation of security vulnerabilities and bugs. This tool is installed with the help of Microsoft
Windows Installer. The list of major functions that a Patch can play is below:
In addressing new security vulnerabilities.
It fixes the software bug.
7
took strong measures to protect themselves from similar attacks in the future.
Cyber crime and security countermeasures demonstrated:
Any crime that involves a computer and a network is considered as a cybercrime. These
crimes are for the purpose of stealing money, personal information, credit card details, etc. In the
present technological era, all the function from intelligence, security of nation, economical
procedures that are being performed with the assistance of internet are having severe future
threats. There are different types of cybercrime, some of them are as follows:
Hacking: It is the most popular way to attempt the crime. In this, unauthorised access to the
computers and networks is performed by the external elements.
Trojan: These are the programmes which perform the different tasks then the one which they
were meant to execute.
Viruses: It is an external source that when entered to the network, infects the other files, data and
programmes by modifying.
Ransomware: It is a malicious software that threatens to publish the data. In present context, the
threat of ransomware is major. It is a malware virus that attacks on the users' system and prevents
them to access the same by locking the system's screens.
These cyber-attacks results in the theft or breach of confidential information that may
cause various challenges. In the present case, the Chinese hacker may have used any of these
methods to steal the software design. Hence, the government of Australia is required to develop
security countermeasures buy considering all these factors in the planning. The countermeasures
can be defined as the action, system, process or technology that can be used to eliminate the
affects of cyber attack on the computers, networks or serves. There are various cyber security
tools present for counter-measuring the attacks. Some of them involves Wireshark, Metasploit,
Nessus, Aircrack and Snort.
In order to avoid such cases in future, the organisation can use the Patching application in
the systems and devices that are used in the software designing. This technique covers the
fixation of security vulnerabilities and bugs. This tool is installed with the help of Microsoft
Windows Installer. The list of major functions that a Patch can play is below:
In addressing new security vulnerabilities.
It fixes the software bug.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
In installing the new drivers.
Patch addresses the software stability issues.
For upgrading the software.
It is mainly installed into the existing program. This app can further upgraded by
reinstalling it. It is a self-contained package encompassing the updates to the application. It is
helpful in determining the app version which can receive a patch. They are the piece of software
prepared to update a computer program. With the help of this tool, the program can be updated
consistently by eliminating the access of the other party. A patch basically performs the function
of "door closing" for the external threats that may harm the software.
In addition to this, Australian agencies have implemented a strong cyber security strategy
having five key priorities, which are a national cyber partnership, strong cyber defences, global
responsibility & influence, growth and innovation and a cyber smart nation. Further, the country
is encouraging basic training on cybercrime and digital evidence. In addition to this, the states
and the commonwealth unit are required to intensify the process to set up national cyber crime
fighting unit.
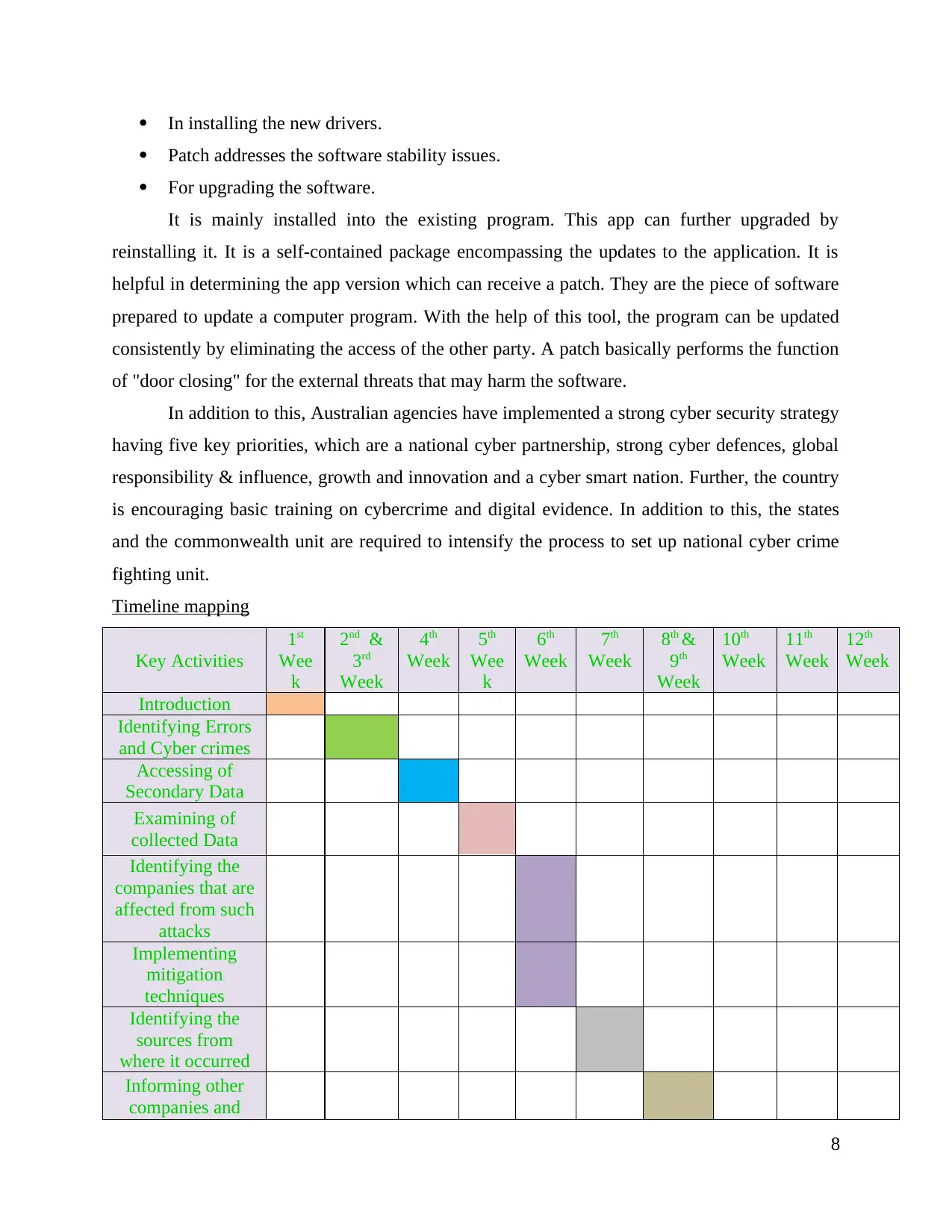
Timeline mapping
Key Activities
1st
Wee
k
2nd &
3rd
Week
4th
Week
5th
Wee
k
6th
Week
7th
Week
8th &
9th
Week
10th
Week
11th
Week
12th
Week
Introduction
Identifying Errors
and Cyber crimes
Accessing of
Secondary Data
Examining of
collected Data
Identifying the
companies that are
affected from such
attacks
Implementing
mitigation
techniques
Identifying the
sources from
where it occurred
Informing other
companies and
8
Patch addresses the software stability issues.
For upgrading the software.
It is mainly installed into the existing program. This app can further upgraded by
reinstalling it. It is a self-contained package encompassing the updates to the application. It is
helpful in determining the app version which can receive a patch. They are the piece of software
prepared to update a computer program. With the help of this tool, the program can be updated
consistently by eliminating the access of the other party. A patch basically performs the function
of "door closing" for the external threats that may harm the software.
In addition to this, Australian agencies have implemented a strong cyber security strategy
having five key priorities, which are a national cyber partnership, strong cyber defences, global
responsibility & influence, growth and innovation and a cyber smart nation. Further, the country
is encouraging basic training on cybercrime and digital evidence. In addition to this, the states
and the commonwealth unit are required to intensify the process to set up national cyber crime
fighting unit.
Timeline mapping
Key Activities
1st
Wee
k
2nd &
3rd
Week
4th
Week
5th
Wee
k
6th
Week
7th
Week
8th &
9th
Week
10th
Week
11th
Week
12th
Week
Introduction
Identifying Errors
and Cyber crimes
Accessing of
Secondary Data
Examining of
collected Data
Identifying the
companies that are
affected from such
attacks
Implementing
mitigation
techniques
Identifying the
sources from
where it occurred
Informing other
companies and
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

government about
the issues
Enhancing the
security of system
Analysing the
errors
Final Submission
to government
Recommendations
There are no measures that can prevent companies and government authorities to protect
their data however adopting the strategies made by Australian Signals Directorate (ASD)
regarding mitigation of targeted Cyber Intrusions. All these instructions were made based on
current visibility and for protecting from cyber-threat environment. They have made certain
changes in Australian Government Protective Security Policy Framework and in Information
security manual. It is considered that this will mitigate around 85% of the issues which
companies are experiencing. However, it is for the Windows operating system. Under the 4
mitigation strategies mentioned by them are:
1. In order to prevent the computing environment, application whitelisting can be used
which maintains consistency, security and stability. App-locker is the similar application
that is provided by Microsoft to protect the data using the restriction methods by the
Organizational Unit. Its generation mechanism helps organization to utilize the Standard
Operating Environment (SOE).
2. Patch Application which helps in protecting the data by fixing security vulnerabilities,
bugfix and improving performance of system. Organization must update their software
and applications, along with this they must implement more effective protection against
the malicious activities in the system. Its better if the patching is completely autonomous
as using the method, system can detect, obtain and install patches for themselves.
Moreover, there are other security consideration that must be considered by the
companies such as administrative privileges, user-interaction and assurance. Under
assurance, companies must be aware about the patch level, as if they miss it then they
will not be able to protect the environment. It will increase threats and reduce risk-
assessments for the security issues.
9
the issues
Enhancing the
security of system
Analysing the
errors
Final Submission
to government
Recommendations
There are no measures that can prevent companies and government authorities to protect
their data however adopting the strategies made by Australian Signals Directorate (ASD)
regarding mitigation of targeted Cyber Intrusions. All these instructions were made based on
current visibility and for protecting from cyber-threat environment. They have made certain
changes in Australian Government Protective Security Policy Framework and in Information
security manual. It is considered that this will mitigate around 85% of the issues which
companies are experiencing. However, it is for the Windows operating system. Under the 4
mitigation strategies mentioned by them are:
1. In order to prevent the computing environment, application whitelisting can be used
which maintains consistency, security and stability. App-locker is the similar application
that is provided by Microsoft to protect the data using the restriction methods by the
Organizational Unit. Its generation mechanism helps organization to utilize the Standard
Operating Environment (SOE).
2. Patch Application which helps in protecting the data by fixing security vulnerabilities,
bugfix and improving performance of system. Organization must update their software
and applications, along with this they must implement more effective protection against
the malicious activities in the system. Its better if the patching is completely autonomous
as using the method, system can detect, obtain and install patches for themselves.
Moreover, there are other security consideration that must be considered by the
companies such as administrative privileges, user-interaction and assurance. Under
assurance, companies must be aware about the patch level, as if they miss it then they
will not be able to protect the environment. It will increase threats and reduce risk-
assessments for the security issues.
9

3. Patch the operating system: There are various difficulties in securing the entire
computing environment but its main core that is operating system can be secured. So if
significant changes are made in the operating parts then systems can be protected. Some
steps that can be taken are:
There should be different patch devices with various configuration in organizations.
Assurance, emergency patches must be there.
External devices and other unknown devices must be reported.
4. Minimize administrate privileges: System should be least modified by the users if they
are unaware about the system configurations as such activities can increase the risk.
Moreover, user might damage the reliability and security of system. Further, target for
malicious intruders, separate the privileges accounts from the general accounts. User
must have privileges in system administration, software installation, compatibility and to
remote access.
However, security breaching is still possible so if such cases are observed then
transparency between companies and government should be there so that mitigation or other
action can be taken. Further, organizations must have information and resources so that they can
be protected from the computer security threats. They can adopt these simple steps to avoid such
issues:
There should be accuracy in the personal accounts.
Limit any personal or professional details access from other's servers.
Unknown and suspected mails, links and websites must be avoided or there should be
firewall option that can prevent such issues.
System must have updated antivirus, anti-spyware, anti-malware and firewall software so
that protection can be provided.
10
computing environment but its main core that is operating system can be secured. So if
significant changes are made in the operating parts then systems can be protected. Some
steps that can be taken are:
There should be different patch devices with various configuration in organizations.
Assurance, emergency patches must be there.
External devices and other unknown devices must be reported.
4. Minimize administrate privileges: System should be least modified by the users if they
are unaware about the system configurations as such activities can increase the risk.
Moreover, user might damage the reliability and security of system. Further, target for
malicious intruders, separate the privileges accounts from the general accounts. User
must have privileges in system administration, software installation, compatibility and to
remote access.
However, security breaching is still possible so if such cases are observed then
transparency between companies and government should be there so that mitigation or other
action can be taken. Further, organizations must have information and resources so that they can
be protected from the computer security threats. They can adopt these simple steps to avoid such
issues:
There should be accuracy in the personal accounts.
Limit any personal or professional details access from other's servers.
Unknown and suspected mails, links and websites must be avoided or there should be
firewall option that can prevent such issues.
System must have updated antivirus, anti-spyware, anti-malware and firewall software so
that protection can be provided.
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





