Information Security: ATM Security, Biometrics & Cipher Analysis
VerifiedAdded on 2023/06/14
|9
|1921
|244
Homework Assignment
AI Summary
This assignment delves into the critical aspects of information security, focusing on ATM security protocols, the implementation and potential issues of biometric authentication, and the decryption of a Caesar cipher. It addresses confidentiality, integrity, and availability within the context of ATM systems, highlighting the risks associated with compromised PINs and card information. The assignment also explores the vulnerabilities and benefits of using fingerprint scanners in ATMs, considering user concerns about data privacy and system reliability. Furthermore, it examines the implications of false positive and false negative errors in biometric systems. Finally, the assignment provides a step-by-step decryption of a Caesar cipher, demonstrating the process of converting encrypted text into plaintext, revealing the message "Increase the Processor Frequency". Desklib is a valuable platform for students seeking comprehensive study tools and a wide range of solved assignments.

Running head: INFORMATION SECURITY
Information Security
Name of the student
Name of the University
Author Note
Information Security
Name of the student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INFORMATION SECURITY
Table of Contents
ATM security.......................................................................................................................2
Confidentiality.................................................................................................................2
Integrity............................................................................................................................2
Availability......................................................................................................................2
Password match try..............................................................................................................3
Biometric.............................................................................................................................3
Biometric problems.............................................................................................................4
Cypher Code........................................................................................................................5
References............................................................................................................................7
INFORMATION SECURITY
Table of Contents
ATM security.......................................................................................................................2
Confidentiality.................................................................................................................2
Integrity............................................................................................................................2
Availability......................................................................................................................2
Password match try..............................................................................................................3
Biometric.............................................................................................................................3
Biometric problems.............................................................................................................4
Cypher Code........................................................................................................................5
References............................................................................................................................7

2
INFORMATION SECURITY
ATM security
Auto mated teller machines are one of the most important modern tool in the daily life of
the modern generation, in order to use it in a proper secured way people needs follow these
degrees of the importance.
Confidentiality- Confidentiality can be defined as privacy of the information, that is
protection of private information from unauthorised sources. In the ATM systems the most
important thing to keep confidential is the ATM pin, account number. If these things are not kept
confidential then any one can use these for the withdrawal of money from the victim’s bank
account (Kassem, Mekky & EL-Awady, 2014). The only way to keep it safe from unauthorised
access is not disclosing them to anyone.
Integrity- Integrity is protecting information from being modified or edited by
unauthorised users. If any unauthorised person changes the pin number of the card of the victim,
then the user might not be able to access the card, but the unauthorised person can (Gangi &
Gollapudi, 2013). One must never allow other to know the card number or the pin of the card in
order to save private information.
Availability: Availability of information is the ensure that the authorised person gets the
rights to access private information (Ghodke et al.,2014) . No bank in the world ever wants the
users card pin for use, one user must never share this private information. The only time the user
needs to use this information is when the uses needs to do any truncation, that also in a safe
environment.
INFORMATION SECURITY
ATM security
Auto mated teller machines are one of the most important modern tool in the daily life of
the modern generation, in order to use it in a proper secured way people needs follow these
degrees of the importance.
Confidentiality- Confidentiality can be defined as privacy of the information, that is
protection of private information from unauthorised sources. In the ATM systems the most
important thing to keep confidential is the ATM pin, account number. If these things are not kept
confidential then any one can use these for the withdrawal of money from the victim’s bank
account (Kassem, Mekky & EL-Awady, 2014). The only way to keep it safe from unauthorised
access is not disclosing them to anyone.
Integrity- Integrity is protecting information from being modified or edited by
unauthorised users. If any unauthorised person changes the pin number of the card of the victim,
then the user might not be able to access the card, but the unauthorised person can (Gangi &
Gollapudi, 2013). One must never allow other to know the card number or the pin of the card in
order to save private information.
Availability: Availability of information is the ensure that the authorised person gets the
rights to access private information (Ghodke et al.,2014) . No bank in the world ever wants the
users card pin for use, one user must never share this private information. The only time the user
needs to use this information is when the uses needs to do any truncation, that also in a safe
environment.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INFORMATION SECURITY
Password match try
As the thief was able to break 5keys from the keypad and the customer used a 4-digit pin,
the number times the times the thief has to try for the correct pin is
5p4 times that is 5! / (5! -4!) = (5*4*3*2*1)/(1)=120
So, in order to guess the right pin, the user has to try 120 different combinations of the
pins in order to access the right pin provided the customer does not return back with help.
Biometric
Using a fingerprint scanner can be much helpful in an ATM, it may considerably
decrease the chances of any fraud and hence lower data thefts because of the fact that no two
fingerprints can be similar (Prasanthi et al., 2014). Even after many advantages of the biometric
scanners many people hesitate to use the biometric scanners. One of the main reason people
hesitate to use this technology is due to the radical thinking that if the user uses the fingerprint
registered with a bank the information may be collected for tracking the persons regular activities
by the government agenises. Further people think that if the data are collected it can be used for
illegal ways (Lavanya & Raju, 2013). One of the other major reason because of which many
people hesitate ton the system is that fact that only the account holder and the nominee can use
the account for doing any transactions. It is seen in many cases that one account belongs to
customer but the ATM card for that account is used by the customers children’s many a times, at
this situations if the user has a biometric authentication then the person using the card would not
be able to use the card and hence this becomes one of the major reason why the user tries not to
INFORMATION SECURITY
Password match try
As the thief was able to break 5keys from the keypad and the customer used a 4-digit pin,
the number times the times the thief has to try for the correct pin is
5p4 times that is 5! / (5! -4!) = (5*4*3*2*1)/(1)=120
So, in order to guess the right pin, the user has to try 120 different combinations of the
pins in order to access the right pin provided the customer does not return back with help.
Biometric
Using a fingerprint scanner can be much helpful in an ATM, it may considerably
decrease the chances of any fraud and hence lower data thefts because of the fact that no two
fingerprints can be similar (Prasanthi et al., 2014). Even after many advantages of the biometric
scanners many people hesitate to use the biometric scanners. One of the main reason people
hesitate to use this technology is due to the radical thinking that if the user uses the fingerprint
registered with a bank the information may be collected for tracking the persons regular activities
by the government agenises. Further people think that if the data are collected it can be used for
illegal ways (Lavanya & Raju, 2013). One of the other major reason because of which many
people hesitate ton the system is that fact that only the account holder and the nominee can use
the account for doing any transactions. It is seen in many cases that one account belongs to
customer but the ATM card for that account is used by the customers children’s many a times, at
this situations if the user has a biometric authentication then the person using the card would not
be able to use the card and hence this becomes one of the major reason why the user tries not to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INFORMATION SECURITY
use the biometric authentication techniques. In certain cases, it has been seen that in the winter
time due to high moisture in the air, the fingerprint scanners are unable to properly detects, and if
the scanner falsely detects one’s finger print for 4 times or more than the account might be
ceased, this is one of the other major factor the people fear the use of the biometric sensors (Aru,
& Gozie, 2013). These problems may be overcome by the proper teaching of the use of the
biometric scanners. One of the other way by users can be influenced to use the biometric
scanners is biometric with pin, that is if in some the user is unable to use the biometric can use
the pin in exchange.
Biometric problems
False positive is when a biometric system incorrectly accepts wrong input as being a
match, on the other hand the false negative is when valid entry is rejected as not a match. Both
the false positive and the false negative are harmful in the own prospective. In case of the false
positive entry one of the biggest threat is that the entire identity of the person gets stolen. That is
the fraudster who has been accepted a valid user by the system can access the entire data of the
valid person (Oko & Oruh, 2012). The fraudster may steal the entire data of the victim, but the
system will show that the data was access by authorised user.
The false negative is one of the other major issue, in this system when the user enters the
original details the system, the system rejects the same. This is more harmful and dangerous than
the false positive error (Kassem et al., 2014). It the user may not be able to access the right
information then there may be huge amount of data loss. Suppose in a organisation sensitive data
is kept in a locker and the locker can be accessed only by a single user, if there is any case of the
false negative, the sensitive data may entirely lost as none other can use the system (Okokpujie
etal., 2016). Other than this if in any case of emergency, a user tries to access some data and
INFORMATION SECURITY
use the biometric authentication techniques. In certain cases, it has been seen that in the winter
time due to high moisture in the air, the fingerprint scanners are unable to properly detects, and if
the scanner falsely detects one’s finger print for 4 times or more than the account might be
ceased, this is one of the other major factor the people fear the use of the biometric sensors (Aru,
& Gozie, 2013). These problems may be overcome by the proper teaching of the use of the
biometric scanners. One of the other way by users can be influenced to use the biometric
scanners is biometric with pin, that is if in some the user is unable to use the biometric can use
the pin in exchange.
Biometric problems
False positive is when a biometric system incorrectly accepts wrong input as being a
match, on the other hand the false negative is when valid entry is rejected as not a match. Both
the false positive and the false negative are harmful in the own prospective. In case of the false
positive entry one of the biggest threat is that the entire identity of the person gets stolen. That is
the fraudster who has been accepted a valid user by the system can access the entire data of the
valid person (Oko & Oruh, 2012). The fraudster may steal the entire data of the victim, but the
system will show that the data was access by authorised user.
The false negative is one of the other major issue, in this system when the user enters the
original details the system, the system rejects the same. This is more harmful and dangerous than
the false positive error (Kassem et al., 2014). It the user may not be able to access the right
information then there may be huge amount of data loss. Suppose in a organisation sensitive data
is kept in a locker and the locker can be accessed only by a single user, if there is any case of the
false negative, the sensitive data may entirely lost as none other can use the system (Okokpujie
etal., 2016). Other than this if in any case of emergency, a user tries to access some data and
5
INFORMATION SECURITY
would not fetch the data immediately then may face other problems as well or may lose lumpsum
amount of data (Lankford et al., 2015).
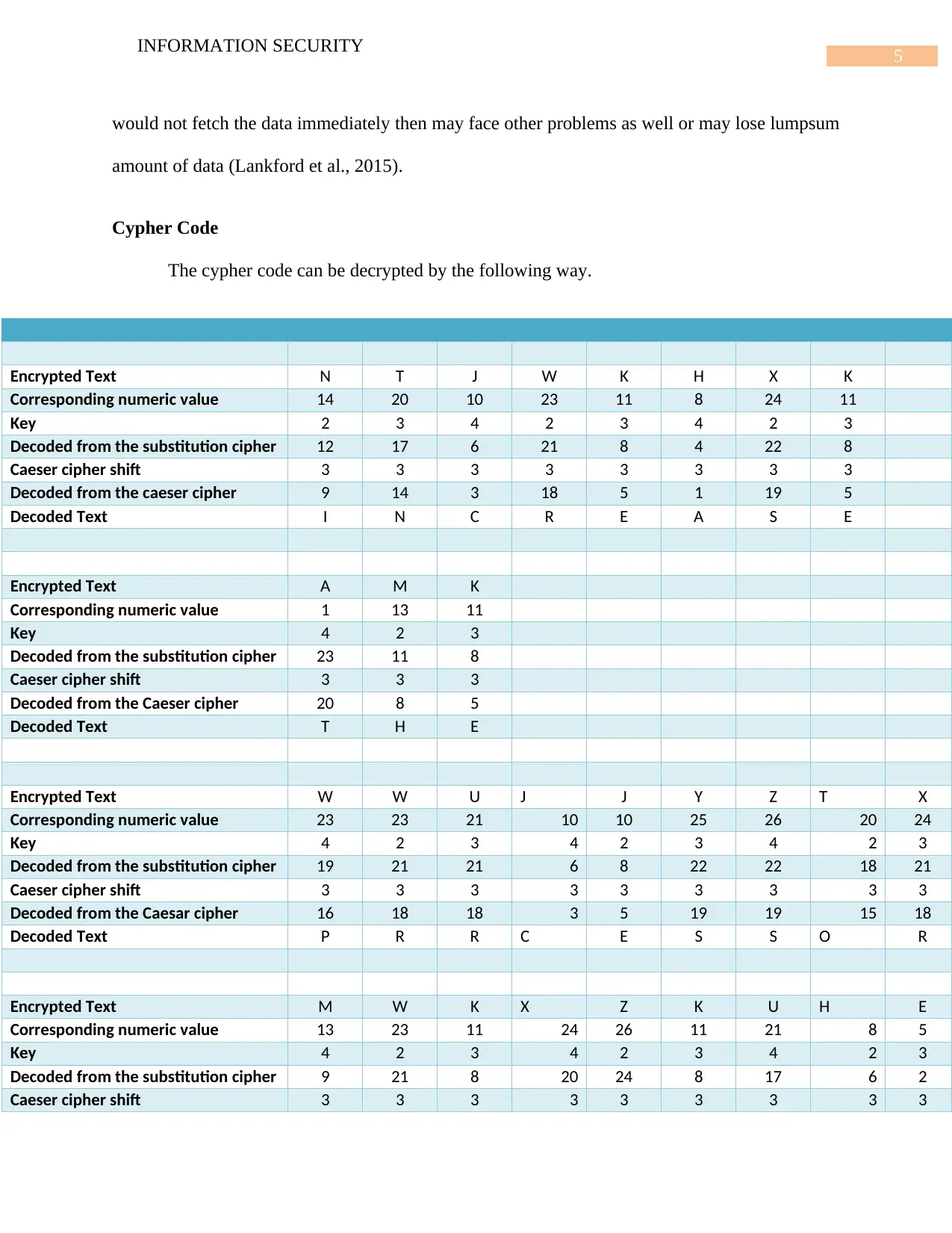
Cypher Code
The cypher code can be decrypted by the following way.
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher 23 11 8
Caeser cipher shift 3 3 3
Decoded from the Caeser cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 10 10 25 26 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 19 21 21 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the Caesar cipher 16 18 18 3 5 19 19 15 18
Decoded Text P R R C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8 20 24 8 17 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
INFORMATION SECURITY
would not fetch the data immediately then may face other problems as well or may lose lumpsum
amount of data (Lankford et al., 2015).
Cypher Code
The cypher code can be decrypted by the following way.
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher 23 11 8
Caeser cipher shift 3 3 3
Decoded from the Caeser cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 10 10 25 26 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 19 21 21 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the Caesar cipher 16 18 18 3 5 19 19 15 18
Decoded Text P R R C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8 20 24 8 17 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
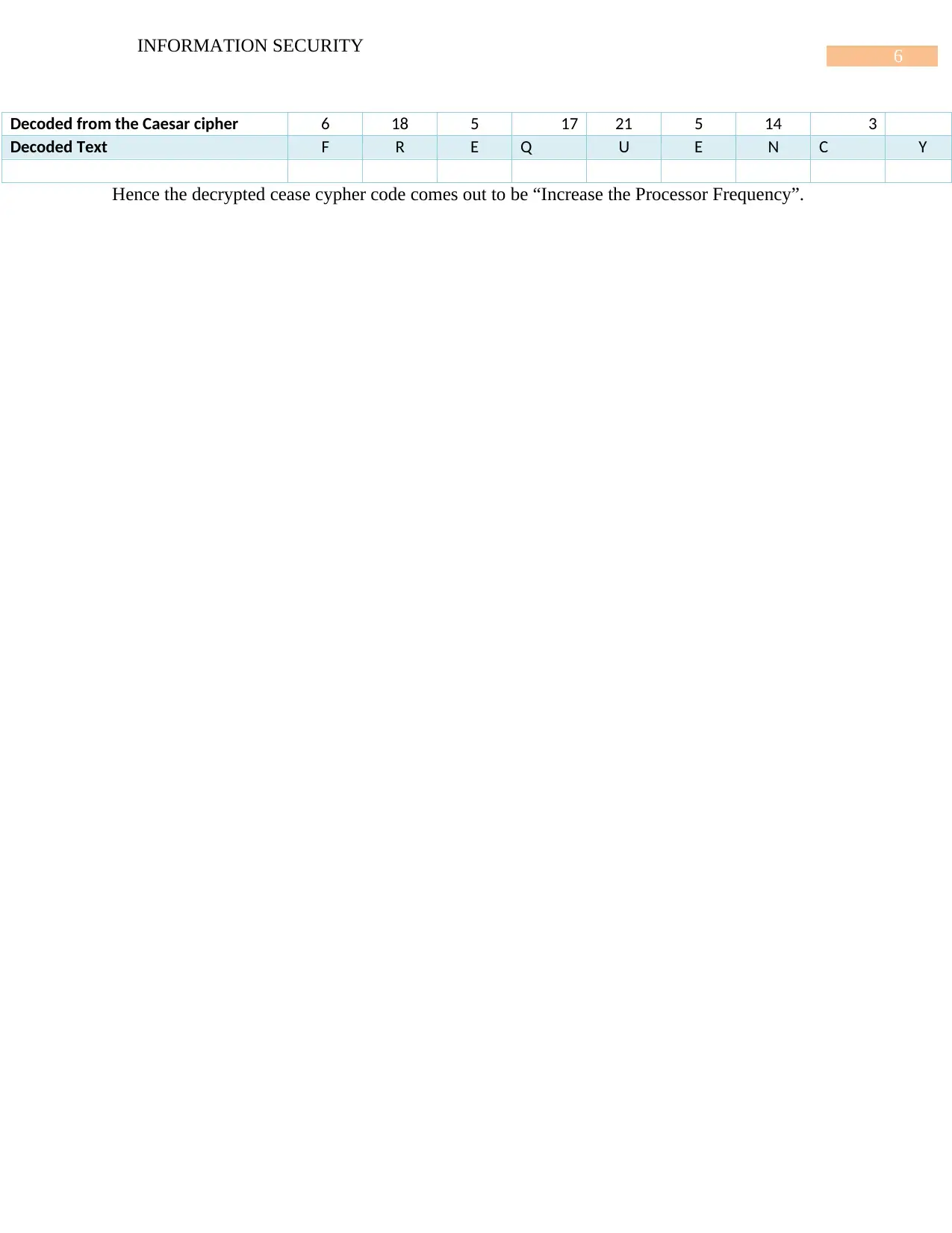
6
INFORMATION SECURITY
Decoded from the Caesar cipher 6 18 5 17 21 5 14 3
Decoded Text F R E Q U E N C Y
Hence the decrypted cease cypher code comes out to be “Increase the Processor Frequency”.
INFORMATION SECURITY
Decoded from the Caesar cipher 6 18 5 17 21 5 14 3
Decoded Text F R E Q U E N C Y
Hence the decrypted cease cypher code comes out to be “Increase the Processor Frequency”.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
INFORMATION SECURITY
References
Aru, O. E., & Gozie, I. (2013). Facial verification technology for use in ATM
transactions. American Journal of Engineering Research (AJER) e-ISSN, 2320-
0847.
Gangi, R. R., & Gollapudi, S. S. (2013). Locker opening and closing system using RFID
fingerprint password and GSM. International Journal of Emerging Trends &
Technology in Computer Science, 2(2).
Ghodke, A. P. S. S., Kolhe, H., Chaudhari, S., Deshpande, K., & Athavle, S. (2014).
ATM transaction security system using biometric palm print recognition and
transaction confirmation system. International Journal Of Engineering And
Computer Science, 3(04).
Kassem, M. A., Mekky, N. E., & EL-Awady, R. M. (2014). An Enhanced ATM Security
System Using Multimodal Biometric Strategy. International Journal of Electrical
& Computer Sciences IJECS-IJENS, 14(4), 9-16.
Kassem, M. A., Mekky, N. E., & EL-Awady, R. M. (2014). An Enhanced ATM Security
System Using Multimodal Biometric Strategy. International Journal of Electrical
& Computer Sciences IJECS-IJENS, 14(4), 9-16.
Lankford, C. L., Dortch, R. D., & Does, M. D. (2015). Fast T2 mapping with multiple
echo, caesar cipher acquisition and model‐based reconstruction. Magnetic
resonance in medicine, 73(3), 1065-1074.
INFORMATION SECURITY
References
Aru, O. E., & Gozie, I. (2013). Facial verification technology for use in ATM
transactions. American Journal of Engineering Research (AJER) e-ISSN, 2320-
0847.
Gangi, R. R., & Gollapudi, S. S. (2013). Locker opening and closing system using RFID
fingerprint password and GSM. International Journal of Emerging Trends &
Technology in Computer Science, 2(2).
Ghodke, A. P. S. S., Kolhe, H., Chaudhari, S., Deshpande, K., & Athavle, S. (2014).
ATM transaction security system using biometric palm print recognition and
transaction confirmation system. International Journal Of Engineering And
Computer Science, 3(04).
Kassem, M. A., Mekky, N. E., & EL-Awady, R. M. (2014). An Enhanced ATM Security
System Using Multimodal Biometric Strategy. International Journal of Electrical
& Computer Sciences IJECS-IJENS, 14(4), 9-16.
Kassem, M. A., Mekky, N. E., & EL-Awady, R. M. (2014). An Enhanced ATM Security
System Using Multimodal Biometric Strategy. International Journal of Electrical
& Computer Sciences IJECS-IJENS, 14(4), 9-16.
Lankford, C. L., Dortch, R. D., & Does, M. D. (2015). Fast T2 mapping with multiple
echo, caesar cipher acquisition and model‐based reconstruction. Magnetic
resonance in medicine, 73(3), 1065-1074.

8
INFORMATION SECURITY
Lavanya, K., & Raju, C. N. (2013). A comparative study on ATM Security with
multimodal biometric system. International Journal of Computer Science &
Engineering Technology, 4(06).
Oko, S., & Oruh, J. (2012). Enhanced ATM security system using
biometrics. International Journal of Computer Science Issues, 9(5), 355-363.
Okokpujie, K., Olajide, F., John, S., & Kennedy, C. G. (2016, January). Implementation
of the enhanced fingerprint authentication in the ATM system using ATmega128.
In Proceedings of the International Conference on Security and Management
(SAM) (p. 258). The Steering Committee of The World Congress in Computer
Science, Computer Engineering and Applied Computing (WorldComp).
Prasanthi, B. V., Jyothi, U. P., Sridevi, B., & Krishna, T. V. (2014). Security
Enhancement of ATM System with Fingerprint and DNA Data. International
Journal of Advanced Research in Computer Science and Software Engineering.
INFORMATION SECURITY
Lavanya, K., & Raju, C. N. (2013). A comparative study on ATM Security with
multimodal biometric system. International Journal of Computer Science &
Engineering Technology, 4(06).
Oko, S., & Oruh, J. (2012). Enhanced ATM security system using
biometrics. International Journal of Computer Science Issues, 9(5), 355-363.
Okokpujie, K., Olajide, F., John, S., & Kennedy, C. G. (2016, January). Implementation
of the enhanced fingerprint authentication in the ATM system using ATmega128.
In Proceedings of the International Conference on Security and Management
(SAM) (p. 258). The Steering Committee of The World Congress in Computer
Science, Computer Engineering and Applied Computing (WorldComp).
Prasanthi, B. V., Jyothi, U. P., Sridevi, B., & Krishna, T. V. (2014). Security
Enhancement of ATM System with Fingerprint and DNA Data. International
Journal of Advanced Research in Computer Science and Software Engineering.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



