A Report on Information Governance and Cyber Security at PFJ Bank
VerifiedAdded on 2019/09/21
|17
|5005
|116
Report
AI Summary
This report provides a comprehensive overview of information governance and cyber security within the context of PFJ Bank, a European retail and investment bank. It emphasizes the critical role of information governance in safeguarding sensitive customer data and maintaining stakeholder trust. The report outlines the importance of establishing robust policies and procedures to manage and secure information, including the implementation of an Information Governance Framework (IGF). This framework addresses various aspects of data management, from accessibility and compliance to security and privacy, and includes a discussion of cyber security policies to protect against cyber threats such as data breaches and phishing attacks. The report highlights best practices for e-banking security, including two-factor authentication, virus protection, and customer education. It also justifies the implementation of information governance, emphasizing the need for executive sponsorship, thorough analysis of current state, and the establishment of checkpoints to ensure effective data management and risk mitigation within the bank. The report underscores the significance of information governance in maintaining the bank's reputation, creditability, and financial stability.

Table of Contents
Information Governance and Cyber Security............................................................................................- 2 -
Introduction............................................................................................................................................- 2 -
Information Governance & Cyber Security Policy................................................................................- 2 -
Information Governance Policy.........................................................................................................- 2 -
Cyber Security Policy........................................................................................................................- 3 -
Importance of Information Governance & Cyber Security in PFJ Bank...............................................- 6 -
Justification for Implementing Information Governance....................................................................- 10 -
Personal Responsibility & Initiatives...................................................................................................- 13 -
Conclusion...........................................................................................................................................- 14 -
References............................................................................................................................................- 15 -
Appendix..............................................................................................................................................- 17 -
1 | P a g e
Information Governance and Cyber Security............................................................................................- 2 -
Introduction............................................................................................................................................- 2 -
Information Governance & Cyber Security Policy................................................................................- 2 -
Information Governance Policy.........................................................................................................- 2 -
Cyber Security Policy........................................................................................................................- 3 -
Importance of Information Governance & Cyber Security in PFJ Bank...............................................- 6 -
Justification for Implementing Information Governance....................................................................- 10 -
Personal Responsibility & Initiatives...................................................................................................- 13 -
Conclusion...........................................................................................................................................- 14 -
References............................................................................................................................................- 15 -
Appendix..............................................................................................................................................- 17 -
1 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Information Governance and Cyber Security
Introduction
Information is crucial in terms of banking in managing the customer information and the effective
management of services. This Paper discusses about the implementation of Information Governance
policy in PFJ bank which is one of the European retails and investment bank operating across Europe. PFJ
bank holds the trust with the all its established client bases and all relevant stakeholders with its stability
and security towards their data. The board of directors of PFJ bank trust that strong information
governance is essential in safeguarding their most sensitive and private information.This paper justifies
that the information governance policy meets thePFJ organization’s business needs andalso ensures that
all the information is dealt legally, securely and effectively with minimized risks.Governance refers to
control, accountability, responsibility of any issues inside the Organization. With this policy implemented
the organization can establish a strong logical framework to handle theirsecured information.
Information Governance & Cyber Security Policy
Information Governance Policy
Information is considered as a most vital asset in terms of all types of organization and Institutions. Hence
it is therefore necessary in providing appropriate policies and procedures in managing and securing them.
Information governanceis the management of information within an organization securely. It also provides
legal compliance, transparency in its operation and reducing costs.To protect the bank’s information from
either internal or external threats, information governance policy can be implemented which provides
quality and provides strategic decision making. Collectively information management refers to efficient
coordination and control of information from external and internal sources.
Information Governance Framework (IGF): The Information Governance Framework is a framework
which provides a format of capturing the data and information of the bank customers in all formats that
can be used from archives.It provides a logical framework in which the employees can handle their data
and information through information governance policies. It outlines the approach of how to handle the
Electronically Stored Information (ESI) by the Employees with Compliance, risk management,
accountability and security. This framework also constitutes some factors which are related directly or
indirectly to information in bank.
2 | P a g e
Introduction
Information is crucial in terms of banking in managing the customer information and the effective
management of services. This Paper discusses about the implementation of Information Governance
policy in PFJ bank which is one of the European retails and investment bank operating across Europe. PFJ
bank holds the trust with the all its established client bases and all relevant stakeholders with its stability
and security towards their data. The board of directors of PFJ bank trust that strong information
governance is essential in safeguarding their most sensitive and private information.This paper justifies
that the information governance policy meets thePFJ organization’s business needs andalso ensures that
all the information is dealt legally, securely and effectively with minimized risks.Governance refers to
control, accountability, responsibility of any issues inside the Organization. With this policy implemented
the organization can establish a strong logical framework to handle theirsecured information.
Information Governance & Cyber Security Policy
Information Governance Policy
Information is considered as a most vital asset in terms of all types of organization and Institutions. Hence
it is therefore necessary in providing appropriate policies and procedures in managing and securing them.
Information governanceis the management of information within an organization securely. It also provides
legal compliance, transparency in its operation and reducing costs.To protect the bank’s information from
either internal or external threats, information governance policy can be implemented which provides
quality and provides strategic decision making. Collectively information management refers to efficient
coordination and control of information from external and internal sources.
Information Governance Framework (IGF): The Information Governance Framework is a framework
which provides a format of capturing the data and information of the bank customers in all formats that
can be used from archives.It provides a logical framework in which the employees can handle their data
and information through information governance policies. It outlines the approach of how to handle the
Electronically Stored Information (ESI) by the Employees with Compliance, risk management,
accountability and security. This framework also constitutes some factors which are related directly or
indirectly to information in bank.
2 | P a g e

Fig 1: Information Governance Framework
There are some factors that should be considered by banks in an information governance framework. They
are:
a. Information serves great value to banks nowadays and it is essential for why they need and what an
information that must handle with it.
b. Banks may implement information governance through IGFafter verified by the selected group of bank
executives.
c. To deal with the dynamic banking industry, information governance framework should consider
multiple aspects of the information and governance that are able to deal the issues inside the bank.
d. Information governance framework in banks includes several factors and some of them are
accessibility, Compliance, Consummation, ethics, monitoring, privacy, security, mobility, transparency
and value.
e. Some IGF deals consists of Dimensions and Factors. Dimensions are the first level of framework and
they are the grouping of interconnected information. Factors are second level and they identify the
issues that the bank must address to implement the IGF.(Tamara Tebaldi Lajara)
Cyber Security Policy
The Internet banking or E-bankinghas become one of the fastest and convenient way of banking
nowadays and cyber threats are also at an increasing rate in banking and e-commerce industries. Banks
have migrated their operations widely to Internet banking because of its high rate of customer experience
at reduced cost. It also led to huge number of security threats to the customers. So, it is responsibility of a
bank to deploy more security policies and safeguard internet banking experience.
3 | P a g e
There are some factors that should be considered by banks in an information governance framework. They
are:
a. Information serves great value to banks nowadays and it is essential for why they need and what an
information that must handle with it.
b. Banks may implement information governance through IGFafter verified by the selected group of bank
executives.
c. To deal with the dynamic banking industry, information governance framework should consider
multiple aspects of the information and governance that are able to deal the issues inside the bank.
d. Information governance framework in banks includes several factors and some of them are
accessibility, Compliance, Consummation, ethics, monitoring, privacy, security, mobility, transparency
and value.
e. Some IGF deals consists of Dimensions and Factors. Dimensions are the first level of framework and
they are the grouping of interconnected information. Factors are second level and they identify the
issues that the bank must address to implement the IGF.(Tamara Tebaldi Lajara)
Cyber Security Policy
The Internet banking or E-bankinghas become one of the fastest and convenient way of banking
nowadays and cyber threats are also at an increasing rate in banking and e-commerce industries. Banks
have migrated their operations widely to Internet banking because of its high rate of customer experience
at reduced cost. It also led to huge number of security threats to the customers. So, it is responsibility of a
bank to deploy more security policies and safeguard internet banking experience.
3 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

An attack via cyber space to disrupt, disable or destroy a computer infrastructure maliciously and collapse
the data or stealing the secured information are called cyberAttack. CyberSecurity is the ability to
protect the system from these cyber attackers. Example could be, when a user signs in a webpage with
someone’s credentials from another device, an automated notification must be sent to the customer’s
registered mobile number.(Jaafar M. Alghazo and Zafar Kazmi)
Some of the practices the PFJ bank can implement to have a safe e-banking are
Operating System must to be up to date to protect from the malware and when a software is downloaded
from a 3rd party site, it also downloads some malicious codes which can be hidden inside the software.
Installing an Antivirus detects any suspicious virus that is residing on the system and delete them.
Browsers are the most probable medium for the cyber attackers. If the browsers are not frequently
updated, then there is a chance of sharing that customer’s data with someone.
Managingpasswords is essential criteria. Passwords must be more unique to recognize which prevents
the unauthorized access. Changing the passwords once in every 6 months is a good practice and limiting
the number of attempts to try also provide good security.
Understanding Banking agreement: A recent survey had a report that the users do not read and
understood the complete online banking agreement which highlights some of the security policies and the
areas which the bank want to educate their customers on sensitive nature of internet banking. The bank
believes that the customers has clearly understood the terms and conditions for online banking when
he/she signs the contract.(Munirul Ula)
Taxonomy of Cyber-attacks:
Cyber-attacks cause potential impact to the information in a bank and they are classified mainly into
Syntactic and Semantic Attacks. Syntactic attacks deal with viruses and trojans and Semantic attacks are
those which interfere with the bank server and network and distract them. To facilitate more deeper
understanding in the cyber-attacks, we should describe the different types of cyber-attacks. These attacks
may be from the inside organization or external. This classification will provide an outline of the range of
harms and the impacts that creates within the bank’s security structure. (Marinela Vrîncianu)
Data Breaches: Data breaches is one of the commontypes of cyber event in which the personal
information such as usernames & passwords, credit card numbers and other personal information either in
a printed or digital information. Most Commonly this occurs from the theft laptop or computers containing
personal information to steal the financial information of a person.
4 | P a g e
the data or stealing the secured information are called cyberAttack. CyberSecurity is the ability to
protect the system from these cyber attackers. Example could be, when a user signs in a webpage with
someone’s credentials from another device, an automated notification must be sent to the customer’s
registered mobile number.(Jaafar M. Alghazo and Zafar Kazmi)
Some of the practices the PFJ bank can implement to have a safe e-banking are
Operating System must to be up to date to protect from the malware and when a software is downloaded
from a 3rd party site, it also downloads some malicious codes which can be hidden inside the software.
Installing an Antivirus detects any suspicious virus that is residing on the system and delete them.
Browsers are the most probable medium for the cyber attackers. If the browsers are not frequently
updated, then there is a chance of sharing that customer’s data with someone.
Managingpasswords is essential criteria. Passwords must be more unique to recognize which prevents
the unauthorized access. Changing the passwords once in every 6 months is a good practice and limiting
the number of attempts to try also provide good security.
Understanding Banking agreement: A recent survey had a report that the users do not read and
understood the complete online banking agreement which highlights some of the security policies and the
areas which the bank want to educate their customers on sensitive nature of internet banking. The bank
believes that the customers has clearly understood the terms and conditions for online banking when
he/she signs the contract.(Munirul Ula)
Taxonomy of Cyber-attacks:
Cyber-attacks cause potential impact to the information in a bank and they are classified mainly into
Syntactic and Semantic Attacks. Syntactic attacks deal with viruses and trojans and Semantic attacks are
those which interfere with the bank server and network and distract them. To facilitate more deeper
understanding in the cyber-attacks, we should describe the different types of cyber-attacks. These attacks
may be from the inside organization or external. This classification will provide an outline of the range of
harms and the impacts that creates within the bank’s security structure. (Marinela Vrîncianu)
Data Breaches: Data breaches is one of the commontypes of cyber event in which the personal
information such as usernames & passwords, credit card numbers and other personal information either in
a printed or digital information. Most Commonly this occurs from the theft laptop or computers containing
personal information to steal the financial information of a person.
4 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
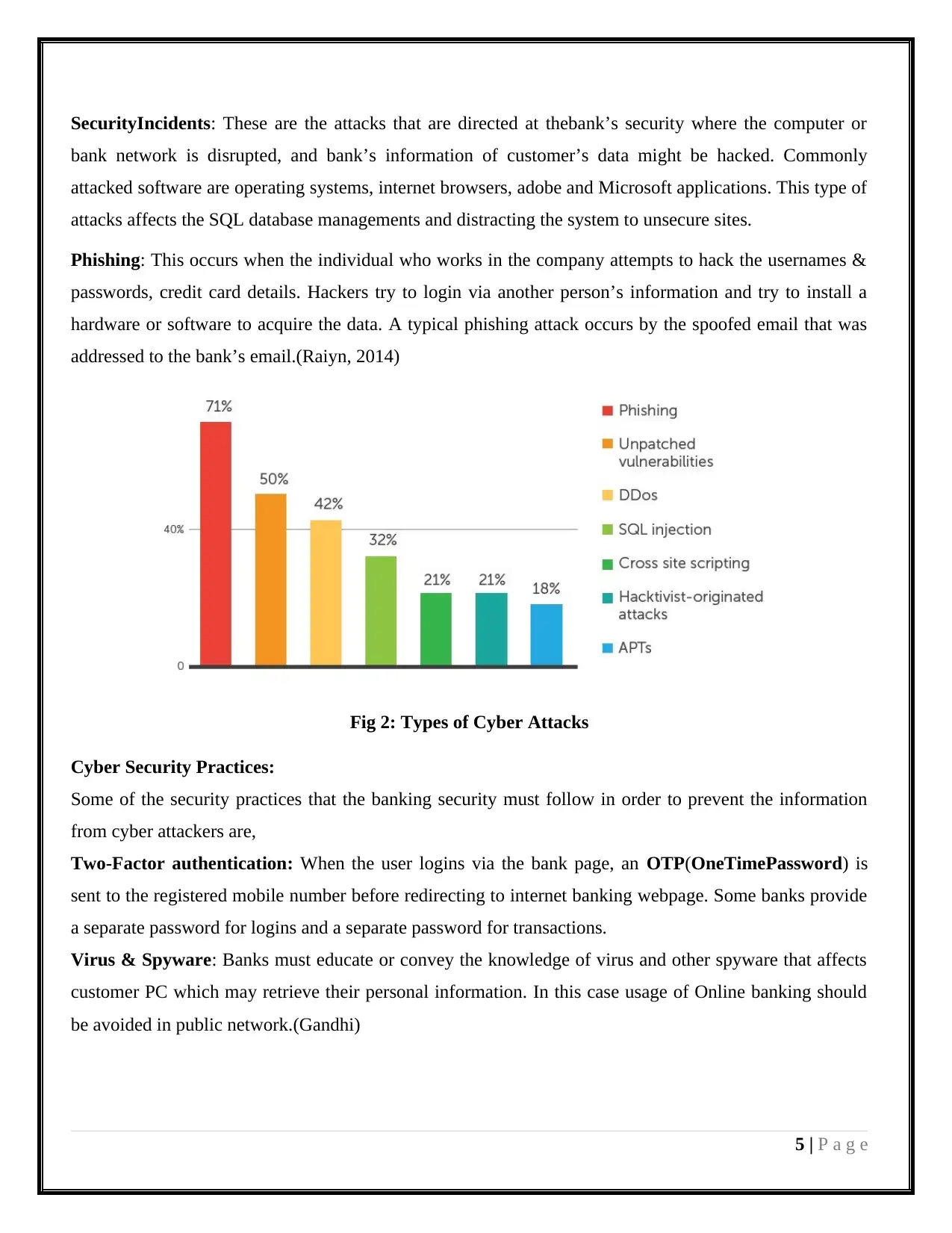
SecurityIncidents: These are the attacks that are directed at thebank’s security where the computer or
bank network is disrupted, and bank’s information of customer’s data might be hacked. Commonly
attacked software are operating systems, internet browsers, adobe and Microsoft applications. This type of
attacks affects the SQL database managements and distracting the system to unsecure sites.
Phishing: This occurs when the individual who works in the company attempts to hack the usernames &
passwords, credit card details. Hackers try to login via another person’s information and try to install a
hardware or software to acquire the data. A typical phishing attack occurs by the spoofed email that was
addressed to the bank’s email.(Raiyn, 2014)
Fig 2: Types of Cyber Attacks
Cyber Security Practices:
Some of the security practices that the banking security must follow in order to prevent the information
from cyber attackers are,
Two-Factor authentication: When the user logins via the bank page, an OTP(OneTimePassword) is
sent to the registered mobile number before redirecting to internet banking webpage. Some banks provide
a separate password for logins and a separate password for transactions.
Virus & Spyware: Banks must educate or convey the knowledge of virus and other spyware that affects
customer PC which may retrieve their personal information. In this case usage of Online banking should
be avoided in public network.(Gandhi)
5 | P a g e
bank network is disrupted, and bank’s information of customer’s data might be hacked. Commonly
attacked software are operating systems, internet browsers, adobe and Microsoft applications. This type of
attacks affects the SQL database managements and distracting the system to unsecure sites.
Phishing: This occurs when the individual who works in the company attempts to hack the usernames &
passwords, credit card details. Hackers try to login via another person’s information and try to install a
hardware or software to acquire the data. A typical phishing attack occurs by the spoofed email that was
addressed to the bank’s email.(Raiyn, 2014)
Fig 2: Types of Cyber Attacks
Cyber Security Practices:
Some of the security practices that the banking security must follow in order to prevent the information
from cyber attackers are,
Two-Factor authentication: When the user logins via the bank page, an OTP(OneTimePassword) is
sent to the registered mobile number before redirecting to internet banking webpage. Some banks provide
a separate password for logins and a separate password for transactions.
Virus & Spyware: Banks must educate or convey the knowledge of virus and other spyware that affects
customer PC which may retrieve their personal information. In this case usage of Online banking should
be avoided in public network.(Gandhi)
5 | P a g e

Online Fraud Call: Banks must educate the customers regarding the online fraudulent calls by requesting
their secured information like ATM pin, passwords etc. And the customers are advised not to share their
personal banking information to anyone.
Login Pages: The Login pages must be designed in such a way that all the information related to access
has to be provided in first page itself.So that the filter occurs at the first page and prevents the malicious
accounts to get logged into the summary page.(Robin)
Importance of Information Governance& Cyber Security in PFJ Bank
The rapid changes and innovations in the Information and technology has led to major changes in many
organizations and banking sectors. PFJ is one such bank which holds large amount of information and
protecting them has become a greater challenge for them. Information governance has become an
important part nowadays in the information management system since the huge amount of information,
policies, standards are managed efficiently by the organizations. Below is the detailed description of the
importance of information governance in the PFJ bank. It also explains the factors that must be considered
before arriving at their implementation.(Patrick Mikalef)
PFJ Bank operate in afinancial environment where the changes in system occur constantly over a period
very rapidly. Also, the bankinvests large amount of money in the IT industry for maintaining database and
is responsible for any changes that are happening. These changes must be monitored and archived by a
team or group of executives which an information governance can do it. Sometimes banks are at a
confused to deal with the structured and unstructured data which refers to type in which they are grouped.
Some of the factors that must be considered before implementing IG are,(M.N.Kooper)
a. Before implementing information governance in the PFJ bank, there must be a pre-requisite study like
why the bank needs an information governance and what are all the information that must be secured.
b. IG can be implemented through anInformation Governance Framework (IGF) and the bank
executives should check for the factors and dimensions in the framework proposed by them.
c. A research must made by the bank to check whether the dynamic banking works fine with the factors
and dimensions proposed by the information governance framework.(Noursilawati A. Halim, 2018)
PFJ Bank can create a structure to deal with the information management and their governance. By
linking it with auditing team, it becomes a criterion for obtaining a license for the banking software.
Without proper governance, bank information will be used for improper activities and that will damage
6 | P a g e
their secured information like ATM pin, passwords etc. And the customers are advised not to share their
personal banking information to anyone.
Login Pages: The Login pages must be designed in such a way that all the information related to access
has to be provided in first page itself.So that the filter occurs at the first page and prevents the malicious
accounts to get logged into the summary page.(Robin)
Importance of Information Governance& Cyber Security in PFJ Bank
The rapid changes and innovations in the Information and technology has led to major changes in many
organizations and banking sectors. PFJ is one such bank which holds large amount of information and
protecting them has become a greater challenge for them. Information governance has become an
important part nowadays in the information management system since the huge amount of information,
policies, standards are managed efficiently by the organizations. Below is the detailed description of the
importance of information governance in the PFJ bank. It also explains the factors that must be considered
before arriving at their implementation.(Patrick Mikalef)
PFJ Bank operate in afinancial environment where the changes in system occur constantly over a period
very rapidly. Also, the bankinvests large amount of money in the IT industry for maintaining database and
is responsible for any changes that are happening. These changes must be monitored and archived by a
team or group of executives which an information governance can do it. Sometimes banks are at a
confused to deal with the structured and unstructured data which refers to type in which they are grouped.
Some of the factors that must be considered before implementing IG are,(M.N.Kooper)
a. Before implementing information governance in the PFJ bank, there must be a pre-requisite study like
why the bank needs an information governance and what are all the information that must be secured.
b. IG can be implemented through anInformation Governance Framework (IGF) and the bank
executives should check for the factors and dimensions in the framework proposed by them.
c. A research must made by the bank to check whether the dynamic banking works fine with the factors
and dimensions proposed by the information governance framework.(Noursilawati A. Halim, 2018)
PFJ Bank can create a structure to deal with the information management and their governance. By
linking it with auditing team, it becomes a criterion for obtaining a license for the banking software.
Without proper governance, bank information will be used for improper activities and that will damage
6 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the bank’s reputation, creditability, revenue and other legal litigations. These all will lead to the loss of
high returns from the shareholders and other business revenues.
Fig 3: Risk Assessments
The Information governance can be implemented in PFJ bank via information governance framework
which creates an awareness among the bank executives about the allocation of resources in managing
them. Due to huge run of data, it leads to out spacing and creates a confusion of what need to be stored
and secured and the period it must be managed. Information Governance Framework provides solution for
all these issues and at a lower cost and risks. Hence banks try to implement information governance
through an information governance framework.(Fernando de Abreu Faria, Jan 2013)
Some of the key requirements that must be addressed before implementing the policy in PFJ bank are as
follows.
Sponsorship: The information governance within the PFJ bank may be highly dependent upon executive
sponsorships. There are many source and type of information which creates confusion of which one must
be highly prioritized. This higher level of sponsorships will make the information handled by the PFJ bank
to remain in high priorities irrespective of other tasks.
Comprehend current State: Before implementing the information governance, the PFJ bank must
analyze the starting point or place from where the process must be started. Starting point here refers to the
file or folder which holds specific type of information.
Checkpoints: Specific milestones and check points must be created along with the open discussions with
the PFJ bank executives at periodic intervals. To avoid the huge collapse that occurs after an issue is
identified, it is necessary keep some check points. This provides a solution for the issues that arise amidst
of bank functioning and provides long term viability and sustainability.(Jorja Wright)
7 | P a g e
high returns from the shareholders and other business revenues.
Fig 3: Risk Assessments
The Information governance can be implemented in PFJ bank via information governance framework
which creates an awareness among the bank executives about the allocation of resources in managing
them. Due to huge run of data, it leads to out spacing and creates a confusion of what need to be stored
and secured and the period it must be managed. Information Governance Framework provides solution for
all these issues and at a lower cost and risks. Hence banks try to implement information governance
through an information governance framework.(Fernando de Abreu Faria, Jan 2013)
Some of the key requirements that must be addressed before implementing the policy in PFJ bank are as
follows.
Sponsorship: The information governance within the PFJ bank may be highly dependent upon executive
sponsorships. There are many source and type of information which creates confusion of which one must
be highly prioritized. This higher level of sponsorships will make the information handled by the PFJ bank
to remain in high priorities irrespective of other tasks.
Comprehend current State: Before implementing the information governance, the PFJ bank must
analyze the starting point or place from where the process must be started. Starting point here refers to the
file or folder which holds specific type of information.
Checkpoints: Specific milestones and check points must be created along with the open discussions with
the PFJ bank executives at periodic intervals. To avoid the huge collapse that occurs after an issue is
identified, it is necessary keep some check points. This provides a solution for the issues that arise amidst
of bank functioning and provides long term viability and sustainability.(Jorja Wright)
7 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cross functional teams: The information governance will create a fundamental shift in the bank and it is
necessary to build a cross functional team within bank. This team involves PFJ bank’s stakeholders,
customers who must be involved and disseminating the information.
Fig 4: Risk Management
IdentifyStakeholders: The Stakeholders in the PFJ bank must be an effective leader who can be trusted
and empowered and lead an initiative. Stakeholders must be engaged to identify the issues in the areas of
higher risk and noting them. When the critical area is identified, it must be addressed one by one starting
from the bigger issue, rather than addressing all at a time.(Erkka Niemi)
Database Management: A research from Compliance, Governance, and Oversight Council in 2012
shows that database of the 69% of leading banks contains no legal or business value. From this it is
evident that huge number of space and cost is spent on data that is no longer useful and not to be retained.
Hence it is necessary to group the secure and non-secure data and information that is available in the PFJ
bank’s database separately for easy management.
Data Classification/modelling: A complete classification of data and information that is available in PFJ
databasemust be prepared so that the amount of priority that must be given to the particular type will be
identified. Else all the data will be given equal priority leading to huge cost and increase the opportunities
for malicious attacks. Based on the type of data, security measures can be applied accordingly.
CyberSecurity will address the threats that are posing on the bank’s security systems. Addressing all
these will reduce the threats that arise in the banking. When there is an increase in the data breach or some
other threats, it means that proper security measures are incorporated inside the bank and hence the
8 | P a g e
necessary to build a cross functional team within bank. This team involves PFJ bank’s stakeholders,
customers who must be involved and disseminating the information.
Fig 4: Risk Management
IdentifyStakeholders: The Stakeholders in the PFJ bank must be an effective leader who can be trusted
and empowered and lead an initiative. Stakeholders must be engaged to identify the issues in the areas of
higher risk and noting them. When the critical area is identified, it must be addressed one by one starting
from the bigger issue, rather than addressing all at a time.(Erkka Niemi)
Database Management: A research from Compliance, Governance, and Oversight Council in 2012
shows that database of the 69% of leading banks contains no legal or business value. From this it is
evident that huge number of space and cost is spent on data that is no longer useful and not to be retained.
Hence it is necessary to group the secure and non-secure data and information that is available in the PFJ
bank’s database separately for easy management.
Data Classification/modelling: A complete classification of data and information that is available in PFJ
databasemust be prepared so that the amount of priority that must be given to the particular type will be
identified. Else all the data will be given equal priority leading to huge cost and increase the opportunities
for malicious attacks. Based on the type of data, security measures can be applied accordingly.
CyberSecurity will address the threats that are posing on the bank’s security systems. Addressing all
these will reduce the threats that arise in the banking. When there is an increase in the data breach or some
other threats, it means that proper security measures are incorporated inside the bank and hence the
8 | P a g e

damage. PFJbank should adopt a highly secured cyber environment than any other organizations since
they deal with the most confidential and secured information of any individual or an organization. (Daniel
Schatz)
Web servers and application configurations are major cause of cyber-attacks and in the failure of proper
maintenance leads to a vast security breach which are flaws in security patch of server, unauthorized
permissions to a file or directory, misconfigured SSL certifications and encryption settings, Improper
authentication with external systems. Computers and networks within the PFJ bank’s server must be
configured in such a way that it can access only the trusted servers, install programs intended for their use
alone.(Drabwell)
Cyber-attacks cause potential impact to the information in a bank and they are classified mainly into
Syntactic and Semantic Attacks. Syntactic attacks deal with viruses and trojans and Semantic attacks are
those which interfere with the bank server and network and distract them.
Fig 5: Cyber-attacks Security measures
The frequency of security measures must be assessed and updated as per the National Institute of
Standards and Technology and continuous monitoring and guidelines can be prepared. Also, the
protection measure must be extended or updated as per the latest cyber-attack surface which includes
moving the security beyond the network layers, applications, databases, cloud environments and Internet
of Things.(Ahmed AlKalbani)
9 | P a g e
they deal with the most confidential and secured information of any individual or an organization. (Daniel
Schatz)
Web servers and application configurations are major cause of cyber-attacks and in the failure of proper
maintenance leads to a vast security breach which are flaws in security patch of server, unauthorized
permissions to a file or directory, misconfigured SSL certifications and encryption settings, Improper
authentication with external systems. Computers and networks within the PFJ bank’s server must be
configured in such a way that it can access only the trusted servers, install programs intended for their use
alone.(Drabwell)
Cyber-attacks cause potential impact to the information in a bank and they are classified mainly into
Syntactic and Semantic Attacks. Syntactic attacks deal with viruses and trojans and Semantic attacks are
those which interfere with the bank server and network and distract them.
Fig 5: Cyber-attacks Security measures
The frequency of security measures must be assessed and updated as per the National Institute of
Standards and Technology and continuous monitoring and guidelines can be prepared. Also, the
protection measure must be extended or updated as per the latest cyber-attack surface which includes
moving the security beyond the network layers, applications, databases, cloud environments and Internet
of Things.(Ahmed AlKalbani)
9 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Justification forImplementingInformation Governance
Information governance policy seems to be most valuable solution for data security and managing them.
They have some set of data management procedures and programs and which are proactive, strategic
approaches.So, when the PFJ bank takes information governance policy in hand, they have a precise
control over managing them.The purpose of strategy is to create an approach in providing a robust
information governance framework for the management of information in compliance with legislation,
standards and best practice.There are two key components in information governance strategy and they
are: The trust in Information governance Policy which outlines the objectives that are included in the
policy and the annual action plan that arise form the initial level of assessment on the data and
information.
Information Management:The data and information of the PFJ bank includes both Structured and
unstructured. Data can be stored in house bank’s database or either in the Cloud for ease access and
security purposes. Information governance falls into process of managing this information from databases
and governing them.
Low Affordability: The cyber-attacks and data breaches are more common nowadays in electronic
banking and the process of rediscover and securing them are at higher cost. Information governance
provides cost-effective program of protecting them and, they avoid legal, reputational risks with under
managed data.
10 | P a g e
Information governance policy seems to be most valuable solution for data security and managing them.
They have some set of data management procedures and programs and which are proactive, strategic
approaches.So, when the PFJ bank takes information governance policy in hand, they have a precise
control over managing them.The purpose of strategy is to create an approach in providing a robust
information governance framework for the management of information in compliance with legislation,
standards and best practice.There are two key components in information governance strategy and they
are: The trust in Information governance Policy which outlines the objectives that are included in the
policy and the annual action plan that arise form the initial level of assessment on the data and
information.
Information Management:The data and information of the PFJ bank includes both Structured and
unstructured. Data can be stored in house bank’s database or either in the Cloud for ease access and
security purposes. Information governance falls into process of managing this information from databases
and governing them.
Low Affordability: The cyber-attacks and data breaches are more common nowadays in electronic
banking and the process of rediscover and securing them are at higher cost. Information governance
provides cost-effective program of protecting them and, they avoid legal, reputational risks with under
managed data.
10 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Fig 6: Information security cycle
Following are some of the action plans that can be implementing the policy in the PFJ bank.
1. Information must be protected from the unauthorized access and the confidentiality and integrity of the
information must be maintained.
2. If in case of hacked data, regulatory and legislative measures must take in identifying the fraudulent
and necessary precautions must be taken to avoid in future.
3. It is mandatory to train the staffs on mandatory information governance policy and all the breaches
must be reported to the respective governance team in conjunction with the Data Protection Officer.
4. The accountable officer should have overall responsibility of maintaining an effective Document
management system and who checks and ensures whether all the valuable information and their assets
are recorded in Information Management Systems.
5. The Head of the Information technology and Cyber Security should develop a necessary protocol to
ensure whether the systems and the infrastructure remain complaint with Data Protection Act 2018.
(Aloul)
Information Governance Strategy: The scope of the information governance strategy covers structures,
authorities, regulations of the PFJ bank and its management process. These all will form information
governance framework. For any information governance framework developed, there are certain goals
which should satisfy both the PFJ bank and its customers. They should promote cost effective, scalable ad
11 | P a g e
Following are some of the action plans that can be implementing the policy in the PFJ bank.
1. Information must be protected from the unauthorized access and the confidentiality and integrity of the
information must be maintained.
2. If in case of hacked data, regulatory and legislative measures must take in identifying the fraudulent
and necessary precautions must be taken to avoid in future.
3. It is mandatory to train the staffs on mandatory information governance policy and all the breaches
must be reported to the respective governance team in conjunction with the Data Protection Officer.
4. The accountable officer should have overall responsibility of maintaining an effective Document
management system and who checks and ensures whether all the valuable information and their assets
are recorded in Information Management Systems.
5. The Head of the Information technology and Cyber Security should develop a necessary protocol to
ensure whether the systems and the infrastructure remain complaint with Data Protection Act 2018.
(Aloul)
Information Governance Strategy: The scope of the information governance strategy covers structures,
authorities, regulations of the PFJ bank and its management process. These all will form information
governance framework. For any information governance framework developed, there are certain goals
which should satisfy both the PFJ bank and its customers. They should promote cost effective, scalable ad
11 | P a g e

usable information systems.It should manage accountability, ethical standards and logical errors. It should
build partnership between consumers, clients and the bank.
Information Strategy has been formulated to facilitate the needs of the bank and not for the needs of the
Customer. So, a healthy strategy must be built to overcome the issues that arise from the recent
technology development. Some of the emerging issues with the modern technology advancements are:
Smart Cards: Smart cards holds personal data of the individual like a person’s digital certificates which
are linked to prove the user’s identity for authentication purposes. Despite the advantages it also leads to
the leakage of information when it is stolen or hacked.So, this is one of the emerging issues in recent
times.
Smart Image recognition could lead to matching of similar faces identity in a crowded region or
underground railway.So, this is not a good approach of handling the secured information.
Mobile numbers registered with house address or any other address proofs might lead to dangerous
security threat.(Singh)
The main purpose of this strategy is to create an approach that must be taken with the PFJ bank to provide
a robust information governance framework for the current and future functioning of the bank which will
ensure that it is in compliance with all ethical, legislation and logical standards.(John)
Benefits of Information Governance:
Information Governance provides platform for control over e-discovery of information, disposition and
compliance which provides great value to the bank. On implementing Information Governance policy in
the PFJ bank, following are some of the benefits,
Safer & Secure Information: For implementing an information governance policy inside the PFJ bank, it
requires a set of rules, standards, responsibilities and regulations to secure the data. So, the data in PFJ
bank can provide assurance of information to its customers.
Accesstodata: With this information governance policy implemented, data are classified separately
according to their types and the bank employees have an easier and quicker way of accessing them.
LifecycleEfficiency: When the data of the bank customers are organized better, the normal functioning of
the bank becomes easier and reduces the repetition of work. This enhances the lifecycle of the operations.
Improved Customer Service: Since the data are hold and governed separately according to their nature
and type, it becomes easier for the customers to get information from the bank quickly and efficiently.
This will give an improved customer service to the Bank.(Hagmann)
12 | P a g e
build partnership between consumers, clients and the bank.
Information Strategy has been formulated to facilitate the needs of the bank and not for the needs of the
Customer. So, a healthy strategy must be built to overcome the issues that arise from the recent
technology development. Some of the emerging issues with the modern technology advancements are:
Smart Cards: Smart cards holds personal data of the individual like a person’s digital certificates which
are linked to prove the user’s identity for authentication purposes. Despite the advantages it also leads to
the leakage of information when it is stolen or hacked.So, this is one of the emerging issues in recent
times.
Smart Image recognition could lead to matching of similar faces identity in a crowded region or
underground railway.So, this is not a good approach of handling the secured information.
Mobile numbers registered with house address or any other address proofs might lead to dangerous
security threat.(Singh)
The main purpose of this strategy is to create an approach that must be taken with the PFJ bank to provide
a robust information governance framework for the current and future functioning of the bank which will
ensure that it is in compliance with all ethical, legislation and logical standards.(John)
Benefits of Information Governance:
Information Governance provides platform for control over e-discovery of information, disposition and
compliance which provides great value to the bank. On implementing Information Governance policy in
the PFJ bank, following are some of the benefits,
Safer & Secure Information: For implementing an information governance policy inside the PFJ bank, it
requires a set of rules, standards, responsibilities and regulations to secure the data. So, the data in PFJ
bank can provide assurance of information to its customers.
Accesstodata: With this information governance policy implemented, data are classified separately
according to their types and the bank employees have an easier and quicker way of accessing them.
LifecycleEfficiency: When the data of the bank customers are organized better, the normal functioning of
the bank becomes easier and reduces the repetition of work. This enhances the lifecycle of the operations.
Improved Customer Service: Since the data are hold and governed separately according to their nature
and type, it becomes easier for the customers to get information from the bank quickly and efficiently.
This will give an improved customer service to the Bank.(Hagmann)
12 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





