Information Governance and Cyber Security: A PFJ Bank Perspective
VerifiedAdded on 2020/11/23
|16
|5097
|158
Report
AI Summary
This report provides a comprehensive analysis of information governance and cyber security within the context of PFJ Bank, a European retail and investment bank operating under UK and EU law. It begins by highlighting the increasing threat of cyberattacks in the financial sector, referencing specific incidents like the 2016 US postal service breach and the 2014 JP Morgan Chase data compromise. The report defines key concepts such as cyber security and information governance, emphasizing the importance of data protection, confidentiality, availability, and integrity. It then explores information governance frameworks relevant to the financial sector, including the Financial Conduct Authority (FCA), COBIT 5, and ISO/IEC 27001, outlining their benefits and weaknesses. The report also discusses key principles of information governance like accountability, integrity, protection, and transparency. Finally, the report culminates in a discussion of policies suitable for PFJ Bank and proposes a maturity model to guide the implementation of effective information governance and cyber security measures. The report emphasizes the need for banks to protect their data and maintain customer trust in the face of evolving cyber threats.

Information
Governance and Cyber
Security
Governance and Cyber
Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................2
Recent cyber security attacks.......................................................................................................2
Background Scope and Objectives..............................................................................................3
Cyber security definition.............................................................................................................3
Information Governance Definition............................................................................................3
Information Governance frameworks in the financial sector......................................................5
Critical Analysis and suitability for PFJ BANK..........................................................................8
IG implementation guide.............................................................................................................8
A maturity model.........................................................................................................................9
The Policy of PFJ BANK..........................................................................................................10
CONCLUSION..............................................................................................................................10
REFERENCES..............................................................................................................................12
INTRODUCTION...........................................................................................................................2
Recent cyber security attacks.......................................................................................................2
Background Scope and Objectives..............................................................................................3
Cyber security definition.............................................................................................................3
Information Governance Definition............................................................................................3
Information Governance frameworks in the financial sector......................................................5
Critical Analysis and suitability for PFJ BANK..........................................................................8
IG implementation guide.............................................................................................................8
A maturity model.........................................................................................................................9
The Policy of PFJ BANK..........................................................................................................10
CONCLUSION..............................................................................................................................10
REFERENCES..............................................................................................................................12

EXECUTIVE SUMMARY
This report has described about information governance and cyber security issues due to
which companies have to protect their data. It has been discussed about recent cyber attacks that
occurred in financial sector. Besides this, key principles of information governance in financial
sector has been described. Also, ISO standards and controls are been discussed. Apart from this,
many other IS frameworks in financial sector like COBIT 5, ISO/IEC27001, FSMA, NIST, etc.
is been discussed and what guidelines or policies in each one is followed is shown. Moreover,
benefits and weakness of each framework is explained. In last section it has been described that
what policy should be followed by PFJ BANK and maturity model is developed. . It is also
discussed that what policies has been formed by bank in order to organize and manage
information.
1
This report has described about information governance and cyber security issues due to
which companies have to protect their data. It has been discussed about recent cyber attacks that
occurred in financial sector. Besides this, key principles of information governance in financial
sector has been described. Also, ISO standards and controls are been discussed. Apart from this,
many other IS frameworks in financial sector like COBIT 5, ISO/IEC27001, FSMA, NIST, etc.
is been discussed and what guidelines or policies in each one is followed is shown. Moreover,
benefits and weakness of each framework is explained. In last section it has been described that
what policy should be followed by PFJ BANK and maturity model is developed. . It is also
discussed that what policies has been formed by bank in order to organize and manage
information.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
In present time, it is very essential for companies engaged in financial sector to protect their
information. This is because of rise in cyber crimes and attacks that is resulting in huge losses.
Information governance is a practice of preventing unauthorized access, use, disruption, etc. of
information. Thus, businesses are focusing on maintaining information so that its integrity and
confidentiality is maintained (von Solms and von Solms, 2018). However, there are several
policies which are used in managing information. Moreover, the government is responsible to
formulate laws and regulations related to data privacy. It provides a framework through which
data and information is protected. For every business it is essential to secure information so that
it can not be misused. However, by analysing this it becomes easy to retain customers. PFJ Bank
is a European retail and investment bank headquartered in the UK with operations across Europe. It is
governed by all UK and EU law. This report will describe about information governance and its
principles in financial sector. Besides this, it will discuss about framework of information
governance and how they are applied in PFJ bank. Also, capital analysis and suitability of bank
is discussed. At last maturity model is described along with policy of PFJ bank.
Main Body
Recent cyber security attacks
Cyber crime is a world that is emerging to a great extent. It has majorly impacted on
financial sector. The rate at which attacks are increasing is very high. So, this has been a major
concern for banks and investment companies to focus on it. Due to emerging advance
technologies it has become easy for hacker to steal data. Despite protocols and high quality
protected network and system, data breach is easily possible. Currently there have been a lot of
cyber attacks that has occurred. It has led to data breach and its misuse. Due to cyber attacks,
companies have lost their customer base and trust as well (Data breach in 21st century. 2016).
The rise in cyber attacks is main reason due to which it has become necessary in financial sector
to maintain information. The cyber attack are as below:-
A cyber attack was occurred in 2016 on US postal services. It was due to data breach,
theft of data, etc. due to this there was a huge loss of data of about 1 million people (Liu, Huang
and Lucas, 2016). Moreover, it was observed that US financial stability was impacted to a great
extent to frequent cyber attacks and loss of data. It was a major issue for postal services and
banks. Therefore, laws and policies were developed through which cyber attacks were managed.
2
In present time, it is very essential for companies engaged in financial sector to protect their
information. This is because of rise in cyber crimes and attacks that is resulting in huge losses.
Information governance is a practice of preventing unauthorized access, use, disruption, etc. of
information. Thus, businesses are focusing on maintaining information so that its integrity and
confidentiality is maintained (von Solms and von Solms, 2018). However, there are several
policies which are used in managing information. Moreover, the government is responsible to
formulate laws and regulations related to data privacy. It provides a framework through which
data and information is protected. For every business it is essential to secure information so that
it can not be misused. However, by analysing this it becomes easy to retain customers. PFJ Bank
is a European retail and investment bank headquartered in the UK with operations across Europe. It is
governed by all UK and EU law. This report will describe about information governance and its
principles in financial sector. Besides this, it will discuss about framework of information
governance and how they are applied in PFJ bank. Also, capital analysis and suitability of bank
is discussed. At last maturity model is described along with policy of PFJ bank.
Main Body
Recent cyber security attacks
Cyber crime is a world that is emerging to a great extent. It has majorly impacted on
financial sector. The rate at which attacks are increasing is very high. So, this has been a major
concern for banks and investment companies to focus on it. Due to emerging advance
technologies it has become easy for hacker to steal data. Despite protocols and high quality
protected network and system, data breach is easily possible. Currently there have been a lot of
cyber attacks that has occurred. It has led to data breach and its misuse. Due to cyber attacks,
companies have lost their customer base and trust as well (Data breach in 21st century. 2016).
The rise in cyber attacks is main reason due to which it has become necessary in financial sector
to maintain information. The cyber attack are as below:-
A cyber attack was occurred in 2016 on US postal services. It was due to data breach,
theft of data, etc. due to this there was a huge loss of data of about 1 million people (Liu, Huang
and Lucas, 2016). Moreover, it was observed that US financial stability was impacted to a great
extent to frequent cyber attacks and loss of data. It was a major issue for postal services and
banks. Therefore, laws and policies were developed through which cyber attacks were managed.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Another example of attack can be taken in which JP Morgan Chase in 2014 suffered a
crucial blow. It was almost half of that is 76 million US household and 7 million small
businesses data and information was hacked. The data included name, address, contact no. etc.
But only information related to customers were stolen. There was no financial loss. Besides this,
customer account no, password, etc. were lost. In this case hacker was no able to steal main bank
server. Thus, it saved millions of money of both customers and businesses. Later it was found
that data breach was done by 4 people who gained access in unauthorized way. From this, JP
Morgan spends about $250 million each year on information governance and cyber security of
data.
Therefore, these attacks highly impacted on overall financial sector. It was due to
ineffective security measures and ineffective management of data (Webb and Hume, 2018) .
However, it creates awareness among banks and companies to protect their data and information.
Background Scope and Objectives
Data and information are two crucial elements which enabled a business to retain
customers and gain their trust. Through this, they are able to show how much customer
information values to them. Earlier there was no such guidelines or policies which has to be
followed in information security. So, it was difficult to maintain integrity and reliability of data.
With help of information governance, it is easy to manage and organise data in effective way.
Moreover, their main objective is to store data or information in such a way so that it is easily
accessed. The overall regulation is in hands of government which restricts banks to share info
with others. In addition to it, another objective is to formulate guidelines and policies that
enables in regulating data.
Cyber security definition
Cyber security refers to protecting internet bases systems including hardware, software,
etc. and information transmitted via it. Also, it means to protect network from external threats
and unauthorized access. In recent time, cyber security does not only mean to protect network
but also to secure data and information (De Bruin and Von Solms, 2016). There are many
activities involved in this such as integrity, confidentiality, reliability of network and computer
systems.
3
crucial blow. It was almost half of that is 76 million US household and 7 million small
businesses data and information was hacked. The data included name, address, contact no. etc.
But only information related to customers were stolen. There was no financial loss. Besides this,
customer account no, password, etc. were lost. In this case hacker was no able to steal main bank
server. Thus, it saved millions of money of both customers and businesses. Later it was found
that data breach was done by 4 people who gained access in unauthorized way. From this, JP
Morgan spends about $250 million each year on information governance and cyber security of
data.
Therefore, these attacks highly impacted on overall financial sector. It was due to
ineffective security measures and ineffective management of data (Webb and Hume, 2018) .
However, it creates awareness among banks and companies to protect their data and information.
Background Scope and Objectives
Data and information are two crucial elements which enabled a business to retain
customers and gain their trust. Through this, they are able to show how much customer
information values to them. Earlier there was no such guidelines or policies which has to be
followed in information security. So, it was difficult to maintain integrity and reliability of data.
With help of information governance, it is easy to manage and organise data in effective way.
Moreover, their main objective is to store data or information in such a way so that it is easily
accessed. The overall regulation is in hands of government which restricts banks to share info
with others. In addition to it, another objective is to formulate guidelines and policies that
enables in regulating data.
Cyber security definition
Cyber security refers to protecting internet bases systems including hardware, software,
etc. and information transmitted via it. Also, it means to protect network from external threats
and unauthorized access. In recent time, cyber security does not only mean to protect network
but also to secure data and information (De Bruin and Von Solms, 2016). There are many
activities involved in this such as integrity, confidentiality, reliability of network and computer
systems.
3

Information Governance Definition
It is very essential to maintain security of information so that customer trust is retained.
Also, if information is misused, it can impact on organizational growth to a great extent. A
business contains a lot of data and info relate to customers, products, services, etc. So, they have
to manage, organize and store it in proper manner. But securing of information is priority. This
concept is known as information security. It is a practice of preventing unauthorized access, use,
disruption, etc. of information. It is followed from encryption to decryption of data from one
source to another. In present time, three concepts have evolved in information security. They are
confidentiality, reliability and integrity. They are commonly used in information security. Each
of them is having a different framework which helps in securing data.
Confidentiality – It refers to protecting information so that there is no unauthorized
access of data. Moreover, it refers to securing data in database or server. Keeping
confidentiality of data enables in securing it from cyber attack.
Availability – It means to maintain reliability of data. Here, information kept should be
authentic, consistent and reliable.
Integrity – It is combination of both reliability and accountability. It means that data
privacy must be maintained along with its reliability. However, if integrity is maintained
it is easy to store and protect data.
The information security led to rise in emerging of information governance. It allowed
businesses to organize their data in systematic and effective manner (Liu, Huang and Lucas,
2017). Information governance is process of managing and organising crucial information in a
company. It is done by following legal policies and regulations, maintaining transparency, etc.
By developing a framework, policies and regulations are properly followed.
Key principles of information Governance
There are several principles of information governance which is followed by company. It
helps in managing information in systematic way (Principles of information governance. 2014).
For every sector, principles varies but they are usually common. In financial sector principles are
as follows :-
Principle of accountability – It refers to responsibility that, in any case a specific person or
member in an organization is responsible for information governance. It is useful in storing and
4
It is very essential to maintain security of information so that customer trust is retained.
Also, if information is misused, it can impact on organizational growth to a great extent. A
business contains a lot of data and info relate to customers, products, services, etc. So, they have
to manage, organize and store it in proper manner. But securing of information is priority. This
concept is known as information security. It is a practice of preventing unauthorized access, use,
disruption, etc. of information. It is followed from encryption to decryption of data from one
source to another. In present time, three concepts have evolved in information security. They are
confidentiality, reliability and integrity. They are commonly used in information security. Each
of them is having a different framework which helps in securing data.
Confidentiality – It refers to protecting information so that there is no unauthorized
access of data. Moreover, it refers to securing data in database or server. Keeping
confidentiality of data enables in securing it from cyber attack.
Availability – It means to maintain reliability of data. Here, information kept should be
authentic, consistent and reliable.
Integrity – It is combination of both reliability and accountability. It means that data
privacy must be maintained along with its reliability. However, if integrity is maintained
it is easy to store and protect data.
The information security led to rise in emerging of information governance. It allowed
businesses to organize their data in systematic and effective manner (Liu, Huang and Lucas,
2017). Information governance is process of managing and organising crucial information in a
company. It is done by following legal policies and regulations, maintaining transparency, etc.
By developing a framework, policies and regulations are properly followed.
Key principles of information Governance
There are several principles of information governance which is followed by company. It
helps in managing information in systematic way (Principles of information governance. 2014).
For every sector, principles varies but they are usually common. In financial sector principles are
as follows :-
Principle of accountability – It refers to responsibility that, in any case a specific person or
member in an organization is responsible for information governance. It is useful in storing and
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

managing information. When a person is given responsibility then it becomes his or her duty to
protect data and organize information.
Principle of integrity – This principle state that management of organization will maintain
reliability of data. This means that it will not be misused or modified. Apart from it, there will be
no changes made and its originality will be maintained.
Principle of protection – This is the most important principle as it defines that data will be kept
secured and protected. It will not be shared with third parties and any other person or businesses.
The data will be kept secured in database or servers.
Principle of transparency – It shows that the overall process of data and information transfer
will be transparent. This means that data will be verified at each stage (Schneider, Sedenberg
and Mulligan, 2016).
There is another principle that exists that is data management. Here, it refers to data
protection and minimization. Alongside it, isolation of data and information is done to reduce
attack and risk of data loss.
Critical evaluation of Information Governance frameworks in the financial sector.
There is a separate framework in financial sector as it includes more policies and
regulation that needs to be followed. The framework is formulated by international agencies and
organizations. Alongside this, it gives an overview about how and what guidelines have to be
followed. Also, it is essential for financial companies to implement this. The framework is
described below :-
FCA (financial conduct authority)- It is a regulatory body in UK that operate
independently and govern overall financial services. It regulates firms and maintains integrity of
consumer data. Besides this, it focused on how retail and finance company’s trade. Moreover,
FCA possesses power to set standards of providing services to consumers. They can also ban
certain product or service.
Benefits –
It entirely regulates financial services within UK. Also, it provides guidelines related to
services, their benefits, etc.
Regulation helps in controlling of services and what procedure is to be followed.
Weakness –
5
protect data and organize information.
Principle of integrity – This principle state that management of organization will maintain
reliability of data. This means that it will not be misused or modified. Apart from it, there will be
no changes made and its originality will be maintained.
Principle of protection – This is the most important principle as it defines that data will be kept
secured and protected. It will not be shared with third parties and any other person or businesses.
The data will be kept secured in database or servers.
Principle of transparency – It shows that the overall process of data and information transfer
will be transparent. This means that data will be verified at each stage (Schneider, Sedenberg
and Mulligan, 2016).
There is another principle that exists that is data management. Here, it refers to data
protection and minimization. Alongside it, isolation of data and information is done to reduce
attack and risk of data loss.
Critical evaluation of Information Governance frameworks in the financial sector.
There is a separate framework in financial sector as it includes more policies and
regulation that needs to be followed. The framework is formulated by international agencies and
organizations. Alongside this, it gives an overview about how and what guidelines have to be
followed. Also, it is essential for financial companies to implement this. The framework is
described below :-
FCA (financial conduct authority)- It is a regulatory body in UK that operate
independently and govern overall financial services. It regulates firms and maintains integrity of
consumer data. Besides this, it focused on how retail and finance company’s trade. Moreover,
FCA possesses power to set standards of providing services to consumers. They can also ban
certain product or service.
Benefits –
It entirely regulates financial services within UK. Also, it provides guidelines related to
services, their benefits, etc.
Regulation helps in controlling of services and what procedure is to be followed.
Weakness –
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

There are no laws and regulations formulated by FCA that restricts them to take any legal
action.
There are no guidelines and policies formed by them so companies operate freely without
any restrictions (Popescu, 2017).
COBIT 5 (Control Objectives for Information and Related Technologies) – This
framework includes latest technology, practices and analytical tools which helps in managing
information systems. It was developed by ISACA. It is also useful in maintaining value of
intellectual property, reducing IT risks, etc. (COBIT 5 2019) besides this, it is useful for banks in
optimizing use of IT services and technology. The framework is used in managing relevant
information and its reliability. Moreover, in this it is clearly defined about difference between
information management and governance.
Benefits
It provides tools on how to maintain information system. This makes it easy in applying
those practices and implementing tools.
It helps in controlling of information by using different types of technology
Weakness
It only helps in managing information through practices.
There are no guidelines or policies included in this as it is only a framework.
ISO/IEC27001 (International organization for standardization) - It is the best method
to manage important information. It helps an organization to keep their asset, employee details
and information, etc. through third parties. Also, it includes requirements that are needed for
information security management system (ISMS) (Webb and Hume, 2018).
Benefits
Every business either it is small, large or medium follows ISO standards which enable
them to maintain standards of product and services quality.
Weakness
Any change in one standard makes it difficult for small business to apply it.
FSMA (Financial services and market authority)- It is an organization that regulate
and govern entire financial activities information of banks and investment companies. The main
objective is to have transparency in operations of financial markets. Besides this, it provides
6
action.
There are no guidelines and policies formed by them so companies operate freely without
any restrictions (Popescu, 2017).
COBIT 5 (Control Objectives for Information and Related Technologies) – This
framework includes latest technology, practices and analytical tools which helps in managing
information systems. It was developed by ISACA. It is also useful in maintaining value of
intellectual property, reducing IT risks, etc. (COBIT 5 2019) besides this, it is useful for banks in
optimizing use of IT services and technology. The framework is used in managing relevant
information and its reliability. Moreover, in this it is clearly defined about difference between
information management and governance.
Benefits
It provides tools on how to maintain information system. This makes it easy in applying
those practices and implementing tools.
It helps in controlling of information by using different types of technology
Weakness
It only helps in managing information through practices.
There are no guidelines or policies included in this as it is only a framework.
ISO/IEC27001 (International organization for standardization) - It is the best method
to manage important information. It helps an organization to keep their asset, employee details
and information, etc. through third parties. Also, it includes requirements that are needed for
information security management system (ISMS) (Webb and Hume, 2018).
Benefits
Every business either it is small, large or medium follows ISO standards which enable
them to maintain standards of product and services quality.
Weakness
Any change in one standard makes it difficult for small business to apply it.
FSMA (Financial services and market authority)- It is an organization that regulate
and govern entire financial activities information of banks and investment companies. The main
objective is to have transparency in operations of financial markets. Besides this, it provides
6
provision of how companies will apply rule of conduct. They supervise products and services
offered and verify it.
Benefits
It supports in maintaining transparency in financial transactions.
Weakness
There are no proper guideline or standards mentioned in it.
NIST (National institute of standards and technology)- It is a framework that consists
of guidelines practices, standards, etc. which are followed in order to manage information and
cyber security risk (Almuhammadi and Alsaleh, 2017). Moreover, it helps in promoting
protection related to national and economic security (NIST. 2016). In this, there are five
procedures followed that are identify, protect, detect, respond and recover. Here, it is described
that how data should be protected, what measures has to be taken to resolve cyber threats, etc.
Benefits
The practices and standards mentioned are easy to follow as it helps in reducing risk
related to information security.
Its five procedures help in eliminating risks in effective manner.
Weakness
Usually, the standards are applied by large companies as they possess advance
technology.
COMPARING FRAMEWORKS
COBIT 5 ISO/IEC27001 FSMA NIST
It includes latest
technology, practices
and analytical tools
which helps in
managing information
systems.
Here, it is described
about overall
standards that have to
be followed in
services and products.
It regulates and
govern entire financial
activities information
of banks and
investment companies
A framework that
consists of guidelines
practices, standards,
etc. which are
followed in order to
manage information
and cyber security
risk.
7
offered and verify it.
Benefits
It supports in maintaining transparency in financial transactions.
Weakness
There are no proper guideline or standards mentioned in it.
NIST (National institute of standards and technology)- It is a framework that consists
of guidelines practices, standards, etc. which are followed in order to manage information and
cyber security risk (Almuhammadi and Alsaleh, 2017). Moreover, it helps in promoting
protection related to national and economic security (NIST. 2016). In this, there are five
procedures followed that are identify, protect, detect, respond and recover. Here, it is described
that how data should be protected, what measures has to be taken to resolve cyber threats, etc.
Benefits
The practices and standards mentioned are easy to follow as it helps in reducing risk
related to information security.
Its five procedures help in eliminating risks in effective manner.
Weakness
Usually, the standards are applied by large companies as they possess advance
technology.
COMPARING FRAMEWORKS
COBIT 5 ISO/IEC27001 FSMA NIST
It includes latest
technology, practices
and analytical tools
which helps in
managing information
systems.
Here, it is described
about overall
standards that have to
be followed in
services and products.
It regulates and
govern entire financial
activities information
of banks and
investment companies
A framework that
consists of guidelines
practices, standards,
etc. which are
followed in order to
manage information
and cyber security
risk.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CHOOSING A FRAMEWORK :
It is necessary for PFJ BANK to choose a framework that is best suitable. This is because
it will give an insight that how to secure their information asset such as financial information,
employee details, etc. Moreover, each framework differs from each other and allows in
managing information. But it depends on company that what framework is chosen and how it
will help in proper regulation.
In PFJ BANK, ISO/IEC 27000 framework should be selected so that it will help in
securing their asset. Also, it will allow them to maintain trust on third parties that are involved in
completion of transactions (Kohnke and Shoemaker, 2015). Furthermore, through this, PFJ
BANK will protect their process of storing records, IT systems, etc.
Risk -The risk associated with ISO/IEC 27000 is it only helps in securing asset but not
information. Thus, there are high chances of unauthorized access and stealing of data.
Benefits- Its benefit is it through securing of asset information can be automatically protected.
Here, overall asset are easily managed and organized in proper way.
ISO STANDARDS THAT APPLY TO PFJ BANK
There are certain ISO standards that are applied in PFJ bank. They are described below :-
ISO 2700 information security – It enables bank to organize customer data and
information in effective way. Also, they need to protect their data in server or database so
that it is not misused. For example- customer credit or debit card details should be stored
in database.
ISO 31000 Risk management- The bank needs to mitigate risk of cyber security so that
integrity of data is maintained. For example – to ensure security of financial transactions
between customers and bank.
ISO 27400 Information security implementation- The bank need to define how overall
network will work and what systems will be used in offering services. For example-
using authentic mobile applications and website.
ISO STANDARDS AND CONTROL
ISO 9001 certification – It state that there organization should belong to ISO standard training
and certification. So, PFJ bank must include systems that are ISO approved. For example –
Computer system and devices used must be approved by ISO.
8
It is necessary for PFJ BANK to choose a framework that is best suitable. This is because
it will give an insight that how to secure their information asset such as financial information,
employee details, etc. Moreover, each framework differs from each other and allows in
managing information. But it depends on company that what framework is chosen and how it
will help in proper regulation.
In PFJ BANK, ISO/IEC 27000 framework should be selected so that it will help in
securing their asset. Also, it will allow them to maintain trust on third parties that are involved in
completion of transactions (Kohnke and Shoemaker, 2015). Furthermore, through this, PFJ
BANK will protect their process of storing records, IT systems, etc.
Risk -The risk associated with ISO/IEC 27000 is it only helps in securing asset but not
information. Thus, there are high chances of unauthorized access and stealing of data.
Benefits- Its benefit is it through securing of asset information can be automatically protected.
Here, overall asset are easily managed and organized in proper way.
ISO STANDARDS THAT APPLY TO PFJ BANK
There are certain ISO standards that are applied in PFJ bank. They are described below :-
ISO 2700 information security – It enables bank to organize customer data and
information in effective way. Also, they need to protect their data in server or database so
that it is not misused. For example- customer credit or debit card details should be stored
in database.
ISO 31000 Risk management- The bank needs to mitigate risk of cyber security so that
integrity of data is maintained. For example – to ensure security of financial transactions
between customers and bank.
ISO 27400 Information security implementation- The bank need to define how overall
network will work and what systems will be used in offering services. For example-
using authentic mobile applications and website.
ISO STANDARDS AND CONTROL
ISO 9001 certification – It state that there organization should belong to ISO standard training
and certification. So, PFJ bank must include systems that are ISO approved. For example –
Computer system and devices used must be approved by ISO.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Critical Analysis and suitability for PFJ BANK
It can be evaluated that there are different IM frameworks in financial sector which are
been followed. Each one contains some guidelines and practices which assist in managing
information. There are some practices as well that is applied in securing data and info. As PFJ
BANK is investment bank it should follow ISO/IEC27000 standards. This is because it will
support in optimum utilization of resources. However, after developing framework PFJ BANK
can make changes in it according to standards mentioned in ISO/IEC27000.
In this way they will be able to offer financial services to customers. Also, large data sets
and information can be kept secured and protected. Furthermore, with help of government bank
will be able to control and regulate financial services (Katina and et.al., 2017). Through this, data
integrity and confidentiality is maintained.
IG implementation guide
ISO 2700 Information security – This gives principles and standards which are to be set
while providing services. Also, it shows how information can be protected. Here, PFJ
BANK will get an overview on how to protect information and what standards or
guidelines are to be followed in doing this. For example – guidelines used in opening
accounts. After opening of account verification will be sent to customer e mail id.
ISO 3300/15489 Record management – By this, PFJ BANK will be able to manage
records in a structural format. It provides a process through which records are
maintained. It gives clarity on how to store data, metadata, etc. controlling records,
capturing it, etc. PFJ BANK will be able to form a process through which records are
stored and managed. In this way, records can be stored in segregated and structured way.
For example – Each branch will store their customer data in systematic way.
ISO 38500 Corporate governance for IT- In this, it includes guidelines and principles
related to use of info and data for management of organization that are owners, partners,
etc. (von Solms and von Solms, 2018). Here, PFJ BANK will be able to utilize
technology in proper way. Also, managers and employees will be responsible for using
IT tools. For example – employees of bank will access and use computer systems by Id
and password provided by bank.
ISO 31000 Risk management- It provides guidelines and procedure to reduce and
manage risk. By this, PFJ BANK can develop specific procedure to reduce risk. They
9
It can be evaluated that there are different IM frameworks in financial sector which are
been followed. Each one contains some guidelines and practices which assist in managing
information. There are some practices as well that is applied in securing data and info. As PFJ
BANK is investment bank it should follow ISO/IEC27000 standards. This is because it will
support in optimum utilization of resources. However, after developing framework PFJ BANK
can make changes in it according to standards mentioned in ISO/IEC27000.
In this way they will be able to offer financial services to customers. Also, large data sets
and information can be kept secured and protected. Furthermore, with help of government bank
will be able to control and regulate financial services (Katina and et.al., 2017). Through this, data
integrity and confidentiality is maintained.
IG implementation guide
ISO 2700 Information security – This gives principles and standards which are to be set
while providing services. Also, it shows how information can be protected. Here, PFJ
BANK will get an overview on how to protect information and what standards or
guidelines are to be followed in doing this. For example – guidelines used in opening
accounts. After opening of account verification will be sent to customer e mail id.
ISO 3300/15489 Record management – By this, PFJ BANK will be able to manage
records in a structural format. It provides a process through which records are
maintained. It gives clarity on how to store data, metadata, etc. controlling records,
capturing it, etc. PFJ BANK will be able to form a process through which records are
stored and managed. In this way, records can be stored in segregated and structured way.
For example – Each branch will store their customer data in systematic way.
ISO 38500 Corporate governance for IT- In this, it includes guidelines and principles
related to use of info and data for management of organization that are owners, partners,
etc. (von Solms and von Solms, 2018). Here, PFJ BANK will be able to utilize
technology in proper way. Also, managers and employees will be responsible for using
IT tools. For example – employees of bank will access and use computer systems by Id
and password provided by bank.
ISO 31000 Risk management- It provides guidelines and procedure to reduce and
manage risk. By this, PFJ BANK can develop specific procedure to reduce risk. They
9
will be able to secure and protect data in effective way. Hence, risk of data breach is
mitigated by taking proper measures. For example- firewall can be installed in network to
protect unauthorized access. This will help in mitigating risk of cyber attack as well.
CALCULATION PLANS. POSSIBLY WITH DIAGRAMS
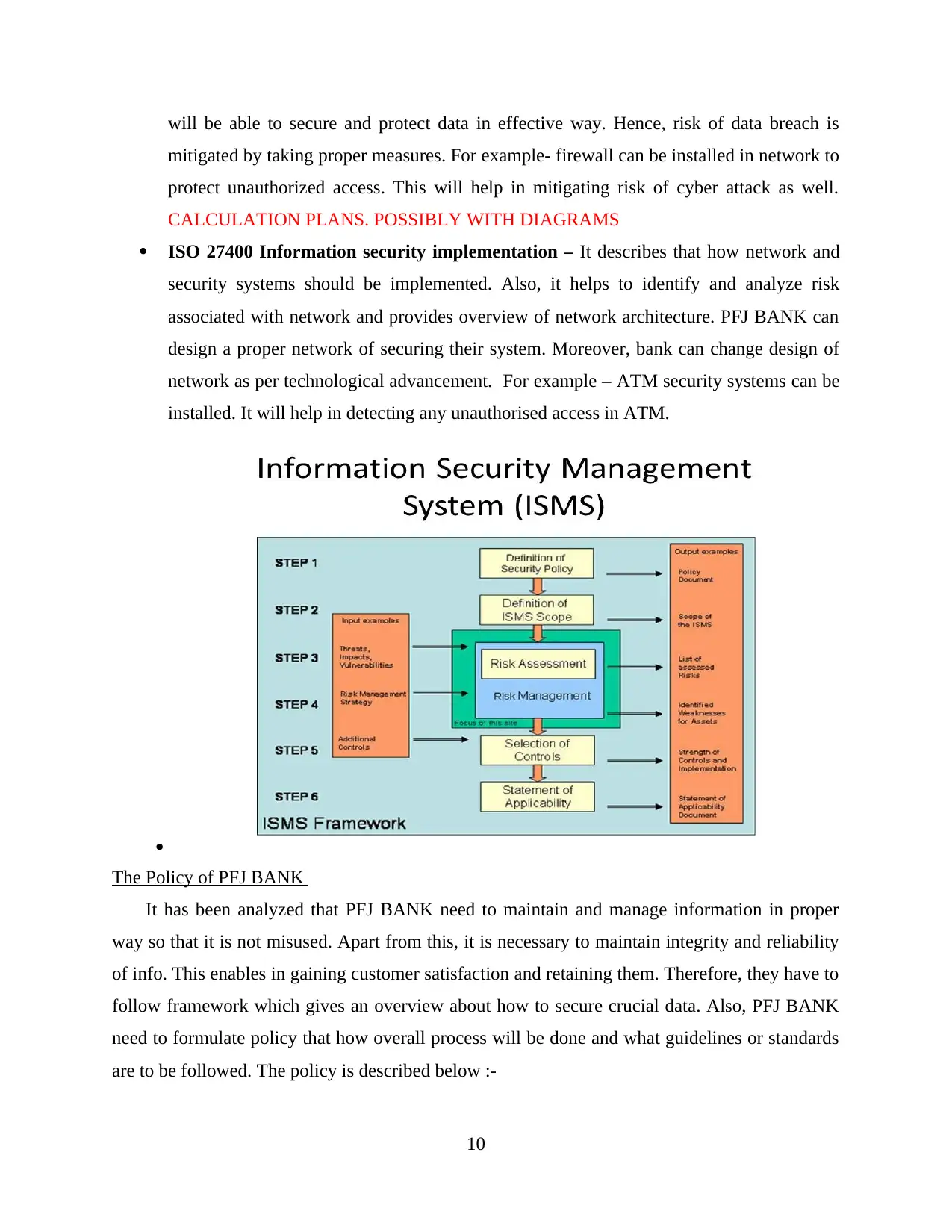
ISO 27400 Information security implementation – It describes that how network and
security systems should be implemented. Also, it helps to identify and analyze risk
associated with network and provides overview of network architecture. PFJ BANK can
design a proper network of securing their system. Moreover, bank can change design of
network as per technological advancement. For example – ATM security systems can be
installed. It will help in detecting any unauthorised access in ATM.
The Policy of PFJ BANK
It has been analyzed that PFJ BANK need to maintain and manage information in proper
way so that it is not misused. Apart from this, it is necessary to maintain integrity and reliability
of info. This enables in gaining customer satisfaction and retaining them. Therefore, they have to
follow framework which gives an overview about how to secure crucial data. Also, PFJ BANK
need to formulate policy that how overall process will be done and what guidelines or standards
are to be followed. The policy is described below :-
10
mitigated by taking proper measures. For example- firewall can be installed in network to
protect unauthorized access. This will help in mitigating risk of cyber attack as well.
CALCULATION PLANS. POSSIBLY WITH DIAGRAMS
ISO 27400 Information security implementation – It describes that how network and
security systems should be implemented. Also, it helps to identify and analyze risk
associated with network and provides overview of network architecture. PFJ BANK can
design a proper network of securing their system. Moreover, bank can change design of
network as per technological advancement. For example – ATM security systems can be
installed. It will help in detecting any unauthorised access in ATM.
The Policy of PFJ BANK
It has been analyzed that PFJ BANK need to maintain and manage information in proper
way so that it is not misused. Apart from this, it is necessary to maintain integrity and reliability
of info. This enables in gaining customer satisfaction and retaining them. Therefore, they have to
follow framework which gives an overview about how to secure crucial data. Also, PFJ BANK
need to formulate policy that how overall process will be done and what guidelines or standards
are to be followed. The policy is described below :-
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





