CIS3005-N Information Governance Portfolio: Risk Management & Training
VerifiedAdded on 2022/11/28
|23
|5882
|443
Portfolio
AI Summary
This portfolio examines information governance for a national dating agency, Private Match, focusing on risk management and staff training. The report begins with an introduction to information governance and its importance for data security, emphasizing confidentiality, integrity, and availability. It proposes a risk management plan to enhance operational and environmental security, including risk identification, assessment, and control. The portfolio identifies information assets such as strategies, intellectual properties, and customer data, and assesses potential threats and vulnerabilities. It also provides strategies for risk control, including defense, transferral, mitigation, acceptance, and termination. Furthermore, the portfolio discusses staff training and security considerations, covering ethical, legal, and regulatory compliance, including the Data Protection Act and GDPR, and outlines a framework for preventing data breaches. Finally, the portfolio concludes by summarizing the key findings and recommendations for effective information governance.

Running head: INFORMATION GOVERNANCE
Information Governance
Name of the Student
Name of the University
Author’s Note:
Information Governance
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INFORMATION GOVERNANCE
Table of Contents
1. Introduction............................................................................................................................2
2. Proposal of Risk Management to enhance Operational and Environmental Security of the
Company....................................................................................................................................2
2.1 Objective of the Risk Management..................................................................................2
2.2 Identification of Information Assets................................................................................4
2.3 Risk Assessment...............................................................................................................6
2.4 Risk Control.....................................................................................................................8
2.5 Business Continuity Planning........................................................................................10
3. Staff Training and Security Considerations.........................................................................12
3.1 Ethical, Legal and Regulatory Compliance...................................................................12
3.2 Data Protection Act........................................................................................................14
3.3 Data Breach Incidents....................................................................................................14
3.4 Suitable Framework for ensuring Prevention of Data Breaches....................................15
3.5 Ensuring Policy in place with Quarterly Review...........................................................15
3.6 Process of Company complying GDPR or Reporting to any Suspected Fraud Activity
..............................................................................................................................................16
4. Conclusion............................................................................................................................17
References................................................................................................................................18
INFORMATION GOVERNANCE
Table of Contents
1. Introduction............................................................................................................................2
2. Proposal of Risk Management to enhance Operational and Environmental Security of the
Company....................................................................................................................................2
2.1 Objective of the Risk Management..................................................................................2
2.2 Identification of Information Assets................................................................................4
2.3 Risk Assessment...............................................................................................................6
2.4 Risk Control.....................................................................................................................8
2.5 Business Continuity Planning........................................................................................10
3. Staff Training and Security Considerations.........................................................................12
3.1 Ethical, Legal and Regulatory Compliance...................................................................12
3.2 Data Protection Act........................................................................................................14
3.3 Data Breach Incidents....................................................................................................14
3.4 Suitable Framework for ensuring Prevention of Data Breaches....................................15
3.5 Ensuring Policy in place with Quarterly Review...........................................................15
3.6 Process of Company complying GDPR or Reporting to any Suspected Fraud Activity
..............................................................................................................................................16
4. Conclusion............................................................................................................................17
References................................................................................................................................18

2
INFORMATION GOVERNANCE
1. Introduction
Information governance (IG) can be referred to as the proper management of
information within any particular company. Information governance focuses on CIA or
confidentiality, integrity and availability of the confidential data under every circumstance
and hence providing proper guidance over data security (Tallon, Ramirez and Short 2013).
The report highlights a proper discussion on information governance program for a popular
national dating agency, known as PM or Private Match. This particular website matches
people, who are looking for a partner with similar personalities and interests. Around 6
offices are present of this company and they have been expanding their business majorly.
They had IT support teams for every office and current they are using their own server
equipment for storing the data. The administrator of Private Match uses algorithms of
artificial intelligence that automatically notify the client as soon as match is being found. The
user can accept, reject and even mark as tentative for later reviewing. With the help of AI, it
is being observed that matching is done in a better manner. Since, customers are providing
personal data, it is quite important to include information governance. It would help them in
securing CIA or confidentiality, integrity and availability of data. This report will be
providing details regarding two most important segment of risk management and staff
training as well as security consideration.
2. Proposal of Risk Management to enhance Operational and Environmental Security
of the Company
2.1 Objective of the Risk Management
Private Match requires risk management in their business for enhancing their
operational and environmental security of the organization (Smallwood 2014). The main
objective of this risk management is identifying the potential issues even before they occur so
INFORMATION GOVERNANCE
1. Introduction
Information governance (IG) can be referred to as the proper management of
information within any particular company. Information governance focuses on CIA or
confidentiality, integrity and availability of the confidential data under every circumstance
and hence providing proper guidance over data security (Tallon, Ramirez and Short 2013).
The report highlights a proper discussion on information governance program for a popular
national dating agency, known as PM or Private Match. This particular website matches
people, who are looking for a partner with similar personalities and interests. Around 6
offices are present of this company and they have been expanding their business majorly.
They had IT support teams for every office and current they are using their own server
equipment for storing the data. The administrator of Private Match uses algorithms of
artificial intelligence that automatically notify the client as soon as match is being found. The
user can accept, reject and even mark as tentative for later reviewing. With the help of AI, it
is being observed that matching is done in a better manner. Since, customers are providing
personal data, it is quite important to include information governance. It would help them in
securing CIA or confidentiality, integrity and availability of data. This report will be
providing details regarding two most important segment of risk management and staff
training as well as security consideration.
2. Proposal of Risk Management to enhance Operational and Environmental Security
of the Company
2.1 Objective of the Risk Management
Private Match requires risk management in their business for enhancing their
operational and environmental security of the organization (Smallwood 2014). The main
objective of this risk management is identifying the potential issues even before they occur so
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INFORMATION GOVERNANCE
that the risk handling activities might be planned as well as invoked for mitigating the
adverse effects over achievement of the objectives. The administrator of PM would be able to
detect, analyse and even manage the threats. Successful detection of the threats mainly
includes identification of the vulnerabilities and threats that could be affecting the respective
assets of the company. An effective risk management involves a proper risk identification
through better involvement and collaboration of all stakeholders. A strong leadership with
every stakeholder is required for establishment of the environment for open discussion and
disclosure of risks (Van Grembergen and De Haes 2018). There are three components of risk
management, which are as follows:
i) Risk Identification: The first component is risk identification, in which the
inventory assets are identified and prioritized. Finally, the threats and risks are identified and
prioritized. For Private Match, the main assets include IT infrastructure, servers, database,
software applications and software packages. Since, they are dealing with customers’ data, it
is evident that they would require high level of risk management, so that there exists no
option of data loss under any circumstance.
ii) Risk Assessment: The second component of risk management is risk assessment,
by which the vulnerabilities within threats and assets could be identified and the asset
exposure is identified as well as quantified (Caldicott 2013). The risk factors could be easily
identified so that risk evaluation is possible in PM without much complexity.
iii) Risk Control: The final component of risk management is risk control. It is the
collection of methodologies, through which the organizations are able to evaluate the
potential losses before taking any action for successful reduction or elimination of the threats.
It is required to manage or control the risks effectively so that PM does not face any type of
complexity.
INFORMATION GOVERNANCE
that the risk handling activities might be planned as well as invoked for mitigating the
adverse effects over achievement of the objectives. The administrator of PM would be able to
detect, analyse and even manage the threats. Successful detection of the threats mainly
includes identification of the vulnerabilities and threats that could be affecting the respective
assets of the company. An effective risk management involves a proper risk identification
through better involvement and collaboration of all stakeholders. A strong leadership with
every stakeholder is required for establishment of the environment for open discussion and
disclosure of risks (Van Grembergen and De Haes 2018). There are three components of risk
management, which are as follows:
i) Risk Identification: The first component is risk identification, in which the
inventory assets are identified and prioritized. Finally, the threats and risks are identified and
prioritized. For Private Match, the main assets include IT infrastructure, servers, database,
software applications and software packages. Since, they are dealing with customers’ data, it
is evident that they would require high level of risk management, so that there exists no
option of data loss under any circumstance.
ii) Risk Assessment: The second component of risk management is risk assessment,
by which the vulnerabilities within threats and assets could be identified and the asset
exposure is identified as well as quantified (Caldicott 2013). The risk factors could be easily
identified so that risk evaluation is possible in PM without much complexity.
iii) Risk Control: The final component of risk management is risk control. It is the
collection of methodologies, through which the organizations are able to evaluate the
potential losses before taking any action for successful reduction or elimination of the threats.
It is required to manage or control the risks effectively so that PM does not face any type of
complexity.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INFORMATION GOVERNANCE
2.2 Identification of Information Assets
Risk can be defined as the possibility to lose anything of value such as assets,
resources for any company. Information asset like a body of knowledge, which is eventually
organized as well as managed as one single entity (Hagmann 2013). For any specific
corporate asset, the information assets of the company comprise of financial values. This
particular value increments in the direct relationship to those people, who have the core
ability of making use of the information. Since, any information comprises of a shorter life
cycle, it has the tendency of depreciating over time like several other corporate assets. Speed
at which information value is being lost mainly is dependent on the type of information the
asset could represent and level of accuracy the information is remaining on time. In
maximum companies, this information could not be utilized as a liability. The information
asset could be sub divided as per criteria for not only the frequency of use or relative
importance (Silic and Back 2013). The information assets of PM are extremely important and
significant for the success of the company and even for improving future revenue or
reduction of future expenses. The major information assets of PM are as follows:
i) Strategies: The first information asset of PM is their business strategies. They have
made unique business strategies for gaining competitive advantages. These strategies,
objectives, goals and plans are required for improving the current position of the company
within the existing market.
ii) Intellectual Properties: These are the second important and significant information
assets for Private Match. Intellectual properties are valuable copyrights, patents, trademarks
or any other information, which is substantially granted legal protections like trade dress
(Wu, Straub and Liang 2015). The developed software with AI algorithms is also included as
IP.
INFORMATION GOVERNANCE
2.2 Identification of Information Assets
Risk can be defined as the possibility to lose anything of value such as assets,
resources for any company. Information asset like a body of knowledge, which is eventually
organized as well as managed as one single entity (Hagmann 2013). For any specific
corporate asset, the information assets of the company comprise of financial values. This
particular value increments in the direct relationship to those people, who have the core
ability of making use of the information. Since, any information comprises of a shorter life
cycle, it has the tendency of depreciating over time like several other corporate assets. Speed
at which information value is being lost mainly is dependent on the type of information the
asset could represent and level of accuracy the information is remaining on time. In
maximum companies, this information could not be utilized as a liability. The information
asset could be sub divided as per criteria for not only the frequency of use or relative
importance (Silic and Back 2013). The information assets of PM are extremely important and
significant for the success of the company and even for improving future revenue or
reduction of future expenses. The major information assets of PM are as follows:
i) Strategies: The first information asset of PM is their business strategies. They have
made unique business strategies for gaining competitive advantages. These strategies,
objectives, goals and plans are required for improving the current position of the company
within the existing market.
ii) Intellectual Properties: These are the second important and significant information
assets for Private Match. Intellectual properties are valuable copyrights, patents, trademarks
or any other information, which is substantially granted legal protections like trade dress
(Wu, Straub and Liang 2015). The developed software with AI algorithms is also included as
IP.
5
INFORMATION GOVERNANCE
iii) Trade Secrets: The trade secrets are inclusive of methods, processes, formulas,
designs, techniques and procedures together are termed as other important information asset
for PM and are used for competitive advantages.
iv) Decision Support Tools: Another vital and distinctive information asset for PM is
decision support tool. These are information tools as well as confidential data, which are
being utilized for improving business decisions.
v) Customer Data Documentation: This is yet another vital information asset for PM
(Von Solms and Van Niekerk 2013). Since they have to deal with customers’ data, it is highly
required for them to document customer data and preserve them for avoiding any kind of data
loss.
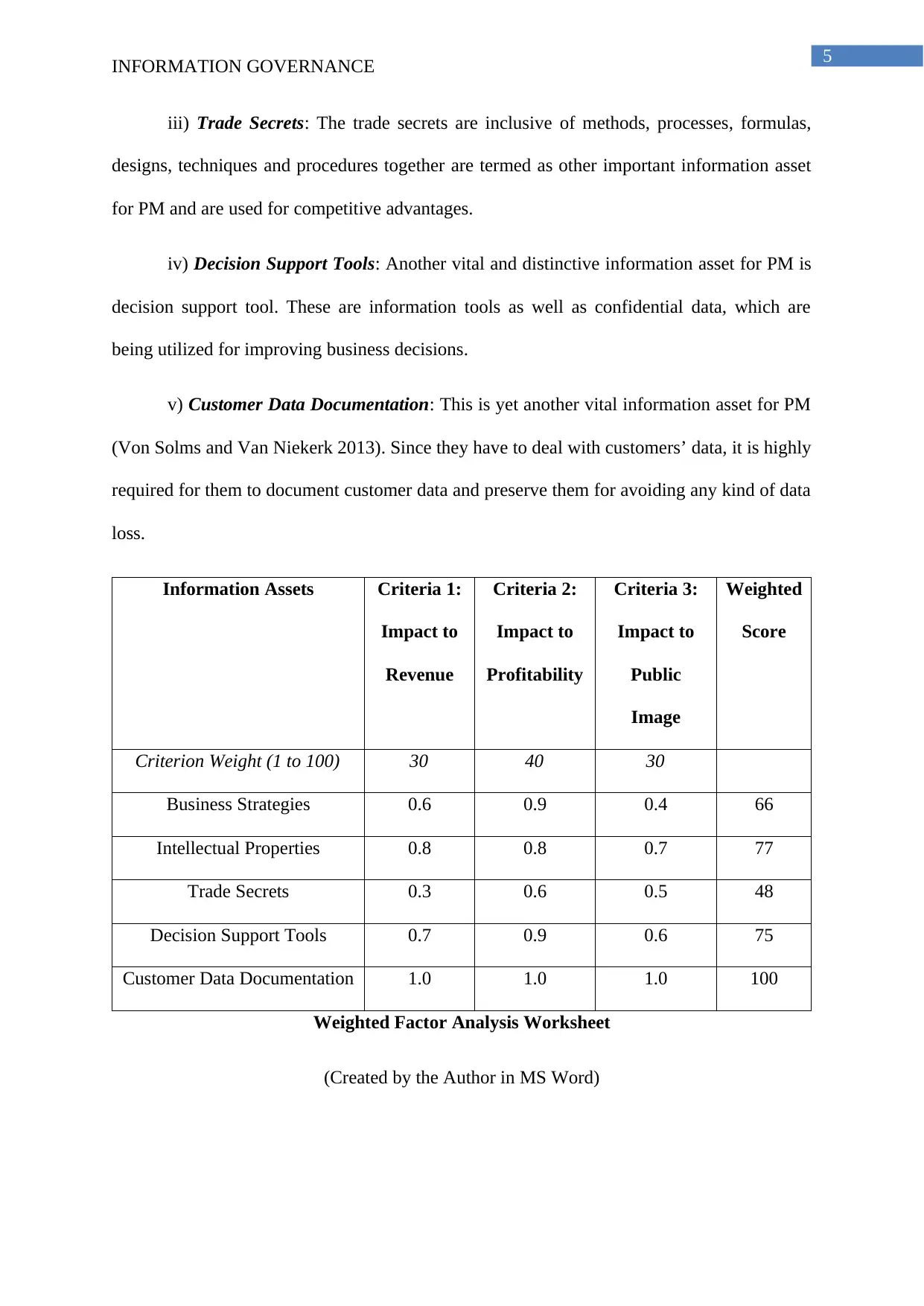
Information Assets Criteria 1:
Impact to
Revenue
Criteria 2:
Impact to
Profitability
Criteria 3:
Impact to
Public
Image
Weighted
Score
Criterion Weight (1 to 100) 30 40 30
Business Strategies 0.6 0.9 0.4 66
Intellectual Properties 0.8 0.8 0.7 77
Trade Secrets 0.3 0.6 0.5 48
Decision Support Tools 0.7 0.9 0.6 75
Customer Data Documentation 1.0 1.0 1.0 100
Weighted Factor Analysis Worksheet
(Created by the Author in MS Word)
INFORMATION GOVERNANCE
iii) Trade Secrets: The trade secrets are inclusive of methods, processes, formulas,
designs, techniques and procedures together are termed as other important information asset
for PM and are used for competitive advantages.
iv) Decision Support Tools: Another vital and distinctive information asset for PM is
decision support tool. These are information tools as well as confidential data, which are
being utilized for improving business decisions.
v) Customer Data Documentation: This is yet another vital information asset for PM
(Von Solms and Van Niekerk 2013). Since they have to deal with customers’ data, it is highly
required for them to document customer data and preserve them for avoiding any kind of data
loss.
Information Assets Criteria 1:
Impact to
Revenue
Criteria 2:
Impact to
Profitability
Criteria 3:
Impact to
Public
Image
Weighted
Score
Criterion Weight (1 to 100) 30 40 30
Business Strategies 0.6 0.9 0.4 66
Intellectual Properties 0.8 0.8 0.7 77
Trade Secrets 0.3 0.6 0.5 48
Decision Support Tools 0.7 0.9 0.6 75
Customer Data Documentation 1.0 1.0 1.0 100
Weighted Factor Analysis Worksheet
(Created by the Author in MS Word)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
INFORMATION GOVERNANCE
2.3 Risk Assessment
Risk assessment in Private Match is completed in five distinctive steps, which are
given:
i) Identification of Hazards: The first step in this particular risk assessment is
identification of hazards. PM would be able to look for the major of threats and
vulnerabilities related to the respective organizational assets (Crossler et al. 2013). This is
required for their successful implementation of risk management plan.
ii) Decision of getting harmed: The second step of risk assessment that should be
considered by Private Match is that they should check the vulnerabilities are affecting which
particular asset of the company.
iii) Evaluation of the Risks: The risks identified are required to be evaluated in the
next step, for understanding the level of vulnerability. This particular step is vital as PM has
to deal with customers’ personal data and data loss which might result in loss of reputation as
well as failure of the business.
iv) Recording of Findings: In the fourth step, it is needed to record the findings of
risk evaluation and analyse them in an effective manner.
v) Reviewing of Assessment: The final step of this risk assessment process is to
review the entire assessment (Peltier 2013). It helps in understanding what steps should be
undertaken for successful elimination or eradication of the risks identified.
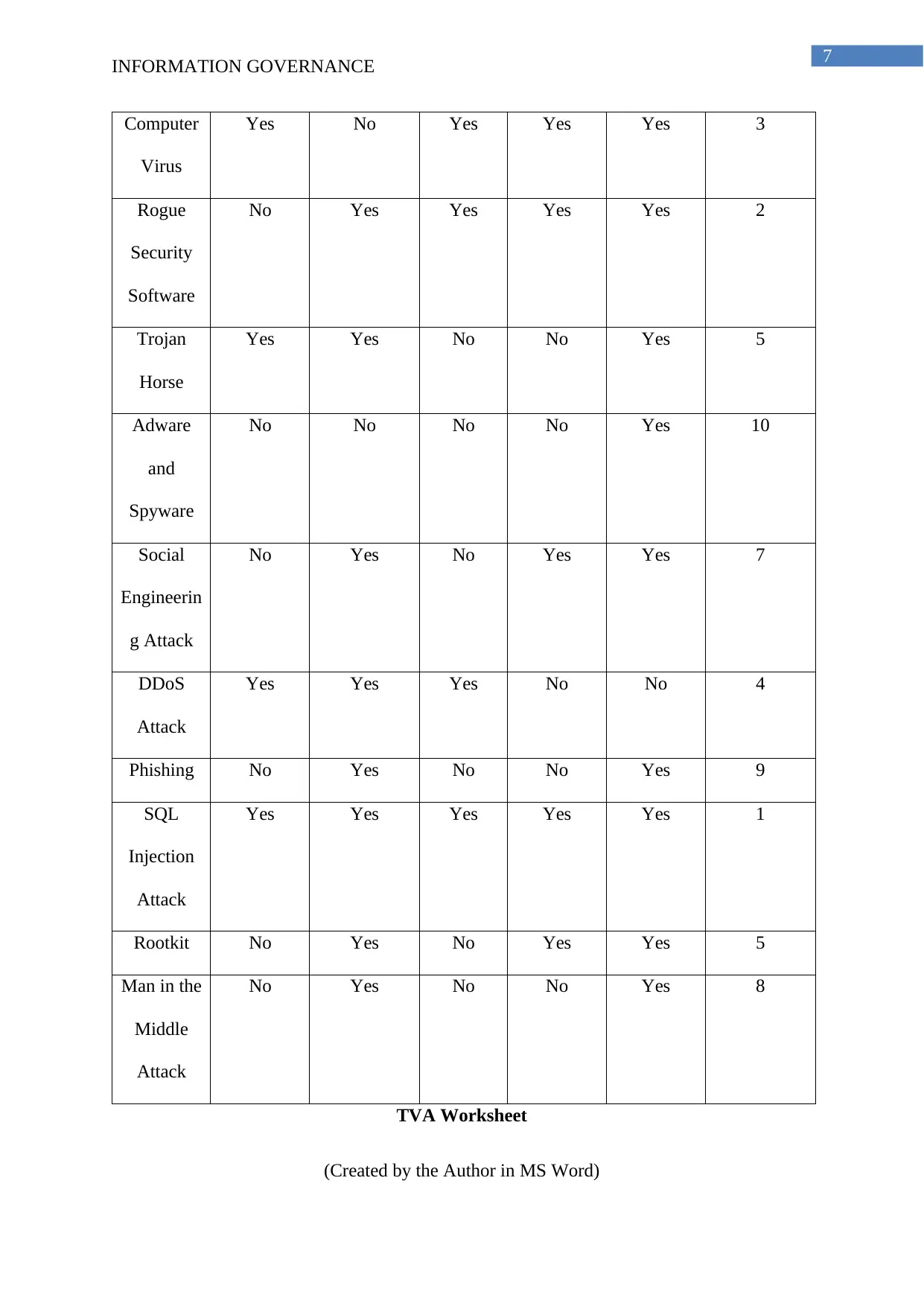
2.3.1 Threats Vulnerabilities Assets Worksheet or TVA
Threats IT
Infrastruc
ture
Servers Databas
e
Artificial
Intelligen
ce
Software
Applicati
ons
Priority of
Controls (1
to 10)
INFORMATION GOVERNANCE
2.3 Risk Assessment
Risk assessment in Private Match is completed in five distinctive steps, which are
given:
i) Identification of Hazards: The first step in this particular risk assessment is
identification of hazards. PM would be able to look for the major of threats and
vulnerabilities related to the respective organizational assets (Crossler et al. 2013). This is
required for their successful implementation of risk management plan.
ii) Decision of getting harmed: The second step of risk assessment that should be
considered by Private Match is that they should check the vulnerabilities are affecting which
particular asset of the company.
iii) Evaluation of the Risks: The risks identified are required to be evaluated in the
next step, for understanding the level of vulnerability. This particular step is vital as PM has
to deal with customers’ personal data and data loss which might result in loss of reputation as
well as failure of the business.
iv) Recording of Findings: In the fourth step, it is needed to record the findings of
risk evaluation and analyse them in an effective manner.
v) Reviewing of Assessment: The final step of this risk assessment process is to
review the entire assessment (Peltier 2013). It helps in understanding what steps should be
undertaken for successful elimination or eradication of the risks identified.
2.3.1 Threats Vulnerabilities Assets Worksheet or TVA
Threats IT
Infrastruc
ture
Servers Databas
e
Artificial
Intelligen
ce
Software
Applicati
ons
Priority of
Controls (1
to 10)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
INFORMATION GOVERNANCE
Computer
Virus
Yes No Yes Yes Yes 3
Rogue
Security
Software
No Yes Yes Yes Yes 2
Trojan
Horse
Yes Yes No No Yes 5
Adware
and
Spyware
No No No No Yes 10
Social
Engineerin
g Attack
No Yes No Yes Yes 7
DDoS
Attack
Yes Yes Yes No No 4
Phishing No Yes No No Yes 9
SQL
Injection
Attack
Yes Yes Yes Yes Yes 1
Rootkit No Yes No Yes Yes 5
Man in the
Middle
Attack
No Yes No No Yes 8
TVA Worksheet
(Created by the Author in MS Word)
INFORMATION GOVERNANCE
Computer
Virus
Yes No Yes Yes Yes 3
Rogue
Security
Software
No Yes Yes Yes Yes 2
Trojan
Horse
Yes Yes No No Yes 5
Adware
and
Spyware
No No No No Yes 10
Social
Engineerin
g Attack
No Yes No Yes Yes 7
DDoS
Attack
Yes Yes Yes No No 4
Phishing No Yes No No Yes 9
SQL
Injection
Attack
Yes Yes Yes Yes Yes 1
Rootkit No Yes No Yes Yes 5
Man in the
Middle
Attack
No Yes No No Yes 8
TVA Worksheet
(Created by the Author in MS Word)

8
INFORMATION GOVERNANCE
2.4 Risk Control
Risk control is a set of methods, through which any specific firm can evaluate or
assess the potential losses and then undertake relevant actions for reduction or elimination of
the threats. Risk control is the most effective technique, which uses findings from risk
assessment that include identification of potential risk factor and providing level of
vulnerability (Siponen, Mahmood and Pahnila 2014). It implements proactive changes for
reduction of risks and hence limiting to the lost assets and income as well. There is a
diversified collection of potential dangers, competitors and obstacles and helps in
identification, assessment as well as preparation for any kind of dangers, disaster potentials
and hazards. It is a plan based strategy, which has core aims for identification and assessment
of the business strategies. The figurative and physical potentials might interfere with the
operations and objectives of the company. For the agency of Private Match, they should
consider to be major and the most important strategy for risk control. (Peltier 2016) The ten
identified risks for PM are system virus, rogue security software, Trojan horse, adware and
spyware, social engineering attack, DDoS attacks, phishing, rootkit, SQL injection attacks
and man in the middle attack.
2.4.1 Strategies for Risk Control
The five strategies of risk control include defence, transferral, mitigation, acceptance
and termination. These five above mentioned strategies are required for controlling the ten
identified risk for PM. The details are provided below:
i) Defence: The first and the foremost strategy for risk control is defence. The
application of safe guards, which eradicate or decrease the remaining controlled risks. This
particular strategy is for those risks, which need defence to lower the overall effect (Safa,
INFORMATION GOVERNANCE
2.4 Risk Control
Risk control is a set of methods, through which any specific firm can evaluate or
assess the potential losses and then undertake relevant actions for reduction or elimination of
the threats. Risk control is the most effective technique, which uses findings from risk
assessment that include identification of potential risk factor and providing level of
vulnerability (Siponen, Mahmood and Pahnila 2014). It implements proactive changes for
reduction of risks and hence limiting to the lost assets and income as well. There is a
diversified collection of potential dangers, competitors and obstacles and helps in
identification, assessment as well as preparation for any kind of dangers, disaster potentials
and hazards. It is a plan based strategy, which has core aims for identification and assessment
of the business strategies. The figurative and physical potentials might interfere with the
operations and objectives of the company. For the agency of Private Match, they should
consider to be major and the most important strategy for risk control. (Peltier 2016) The ten
identified risks for PM are system virus, rogue security software, Trojan horse, adware and
spyware, social engineering attack, DDoS attacks, phishing, rootkit, SQL injection attacks
and man in the middle attack.
2.4.1 Strategies for Risk Control
The five strategies of risk control include defence, transferral, mitigation, acceptance
and termination. These five above mentioned strategies are required for controlling the ten
identified risk for PM. The details are provided below:
i) Defence: The first and the foremost strategy for risk control is defence. The
application of safe guards, which eradicate or decrease the remaining controlled risks. This
particular strategy is for those risks, which need defence to lower the overall effect (Safa,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
INFORMATION GOVERNANCE
Von Solms and Furnell 2016). The DDoS attacks and social engineering attacks in PM could
be controlled with this strategy.
ii) Transferral: The second strategy for risk control is transferral that shifts the risks
to any other area or the outside entity. The risks of rogue security software and adware and
spyware can be controlled with this specific strategy.
iii) Mitigation: The next strategy for control of risks is mitigation. The reduction of
impact of the information assets regarding exploitation of vulnerability is possible with
mitigation of the risks (Xu et al. 2014). The risks of man in the middle attack and phishing
can be controlled with this specific strategy.
iv) Acceptance: Another distinctive strategy for risk control is acceptance. Proper
understanding of consequences of selecting to leave any risk uncontrolled and then properly
acknowledging these risks, which remain without any attempt for control. The computer virus
and rootkit can be controlled with this specific risk control strategy.
v) Termination: The next strategy of risk control is termination. The removal or
discontinuation of the information assets from the operating environment of the company
(Yang, Shieh and Tzeng 2013). The Trojan horse and SQL injection attack can be controlled
with this specific risk control strategy.
2.4.2 Justification of Risk Control
The risk control strategies in PM are required for reducing or eliminating the issues
and threats faced by the organization in their systems. The first strategy of defence works for
deterring an exploitation of vulnerability, which needs major protection. These defence
methods could apply to the physical and logical methods for providing subsequent protection
of a defence strategy. This application of the several layers of defensive measures could be
known as defence in depth. The second distinctive strategy of risk control for PM is
INFORMATION GOVERNANCE
Von Solms and Furnell 2016). The DDoS attacks and social engineering attacks in PM could
be controlled with this strategy.
ii) Transferral: The second strategy for risk control is transferral that shifts the risks
to any other area or the outside entity. The risks of rogue security software and adware and
spyware can be controlled with this specific strategy.
iii) Mitigation: The next strategy for control of risks is mitigation. The reduction of
impact of the information assets regarding exploitation of vulnerability is possible with
mitigation of the risks (Xu et al. 2014). The risks of man in the middle attack and phishing
can be controlled with this specific strategy.
iv) Acceptance: Another distinctive strategy for risk control is acceptance. Proper
understanding of consequences of selecting to leave any risk uncontrolled and then properly
acknowledging these risks, which remain without any attempt for control. The computer virus
and rootkit can be controlled with this specific risk control strategy.
v) Termination: The next strategy of risk control is termination. The removal or
discontinuation of the information assets from the operating environment of the company
(Yang, Shieh and Tzeng 2013). The Trojan horse and SQL injection attack can be controlled
with this specific risk control strategy.
2.4.2 Justification of Risk Control
The risk control strategies in PM are required for reducing or eliminating the issues
and threats faced by the organization in their systems. The first strategy of defence works for
deterring an exploitation of vulnerability, which needs major protection. These defence
methods could apply to the physical and logical methods for providing subsequent protection
of a defence strategy. This application of the several layers of defensive measures could be
known as defence in depth. The second distinctive strategy of risk control for PM is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
INFORMATION GOVERNANCE
transferral. It is the successful sharing of the responsibilities of risks within any specific third
party (Singh 2013). It is needed for not permanently removing the risks, however providing a
shield to the company assets. Another important strategy for Private Match is mitigation. This
particular strategy ensures completion removal or mitigation of the risks by implementing
measures and restricting a successful attack. The fourth strategy for PM regarding risk control
is acceptance. It accepts the identified threat, however deploys no defence strategy. Few risks
are effective for the business. Finally, the fifth strategy is termination. Instead of utilizing a
safeguard for protection of the asset and deployment of 0 safeguards, this particular strategy
eventually removes asset from environment with risk (Soomro, Shah and Ahmed 2016). It is
highly recommended for PM to implement these five above mentioned strategies for
successful eradication of the ten risks identified.
2.5 Business Continuity Planning
Business continuity planning or BCP can be referred to as the procedure that is being
included to create a specific system for prevention as well as recovery from any potential
threats to an organization. The main objectives of BCP is to enable each and every ongoing
operation before or even at the time of execution of the disaster recovery. It is the core
capability for making the changes within organizational environment. It helps in enabling the
companies to endure these changes or even to adapt a new method to work in the manner that
is effective for the business (D'Arcy, Herath and Shoss 2014). BCP would be extremely
effective for PM for few distinctive advantages, which are as follows:
i) Minimization of Effect of Disruption: The disruption effects are highly reduced
with successful implementation of BCP in PM and they would be able to run the business
smoothly.
INFORMATION GOVERNANCE
transferral. It is the successful sharing of the responsibilities of risks within any specific third
party (Singh 2013). It is needed for not permanently removing the risks, however providing a
shield to the company assets. Another important strategy for Private Match is mitigation. This
particular strategy ensures completion removal or mitigation of the risks by implementing
measures and restricting a successful attack. The fourth strategy for PM regarding risk control
is acceptance. It accepts the identified threat, however deploys no defence strategy. Few risks
are effective for the business. Finally, the fifth strategy is termination. Instead of utilizing a
safeguard for protection of the asset and deployment of 0 safeguards, this particular strategy
eventually removes asset from environment with risk (Soomro, Shah and Ahmed 2016). It is
highly recommended for PM to implement these five above mentioned strategies for
successful eradication of the ten risks identified.
2.5 Business Continuity Planning
Business continuity planning or BCP can be referred to as the procedure that is being
included to create a specific system for prevention as well as recovery from any potential
threats to an organization. The main objectives of BCP is to enable each and every ongoing
operation before or even at the time of execution of the disaster recovery. It is the core
capability for making the changes within organizational environment. It helps in enabling the
companies to endure these changes or even to adapt a new method to work in the manner that
is effective for the business (D'Arcy, Herath and Shoss 2014). BCP would be extremely
effective for PM for few distinctive advantages, which are as follows:
i) Minimization of Effect of Disruption: The disruption effects are highly reduced
with successful implementation of BCP in PM and they would be able to run the business
smoothly.

11
INFORMATION GOVERNANCE
ii) Reduction of Physical Asset Risk: The risks to physical assets are the most
common risks for PM and this could be reduced with an effective BCP (Andress 2014).
iii) Recovery of Critical System: The critical system could be easily recovered in a
specific time frame and this would be easily analysed without any complexity.
iv) Measuring of Level of Compliance: The level of compliance could be measured
with the help of BCP in PM (Cárdenas, Manadhata and Rajan 2013).
2.5.1 Disaster Recovery
Disaster recovery planning is the structured approach with basic instructions to
respond towards any type of incident (Ahmad, Maynard and Park 2014). It is a sequential
plan that comprises of the subsequent precautions for successful minimization of effects of a
disaster so that the company could continue in operation or quickly resuming of the mission
critical functionalities. The disaster recovery planning includes a better analysis of the
business processes or needs of continuity. Before generation of a detailed planning, PM can
easily perform an analysis of the business impact as well as risk analysis, so that they are able
to establish the recovery time objective. As PM has to deal with customers’ personal data, the
disaster recovery planning would be extremely effective for the business (Posey et al. 2014).
The main issues such as data, suppliers, resources, technology and budget are required to be
analysed and it is possible with the successful implementation of DR plan.
2.5.2 Incident Response Plan
The incident response (IR) planning is a documented as well as systematic
methodology towards approaching or managing the situations that result from the incidents or
breaches of IT security (Chen, Ramamurthy and Wen 2015). The IR plan in PM could be
used in the enterprise IT facilities and environments for limiting, identifying and responding
INFORMATION GOVERNANCE
ii) Reduction of Physical Asset Risk: The risks to physical assets are the most
common risks for PM and this could be reduced with an effective BCP (Andress 2014).
iii) Recovery of Critical System: The critical system could be easily recovered in a
specific time frame and this would be easily analysed without any complexity.
iv) Measuring of Level of Compliance: The level of compliance could be measured
with the help of BCP in PM (Cárdenas, Manadhata and Rajan 2013).
2.5.1 Disaster Recovery
Disaster recovery planning is the structured approach with basic instructions to
respond towards any type of incident (Ahmad, Maynard and Park 2014). It is a sequential
plan that comprises of the subsequent precautions for successful minimization of effects of a
disaster so that the company could continue in operation or quickly resuming of the mission
critical functionalities. The disaster recovery planning includes a better analysis of the
business processes or needs of continuity. Before generation of a detailed planning, PM can
easily perform an analysis of the business impact as well as risk analysis, so that they are able
to establish the recovery time objective. As PM has to deal with customers’ personal data, the
disaster recovery planning would be extremely effective for the business (Posey et al. 2014).
The main issues such as data, suppliers, resources, technology and budget are required to be
analysed and it is possible with the successful implementation of DR plan.
2.5.2 Incident Response Plan
The incident response (IR) planning is a documented as well as systematic
methodology towards approaching or managing the situations that result from the incidents or
breaches of IT security (Chen, Ramamurthy and Wen 2015). The IR plan in PM could be
used in the enterprise IT facilities and environments for limiting, identifying and responding
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





