Report: Information and Network Security Solutions Analysis
VerifiedAdded on 2020/06/06
|8
|2010
|67
Report
AI Summary
This report provides an overview of information and network security solutions, emphasizing the importance of data protection in the modern digital landscape. It explores various applications and strategies, including the triple R framework and white-box cryptography, to combat cyber attacks and ensure data confidentiality. The report also discusses the role of an ICT manager in assessing client databases and delivering customized security and network solutions. Furthermore, it highlights the significance of adapting to evolving threats and adopting measures to safeguard data from unauthorized access and misuse. The report concludes that while delivering security services, it is important to keep the data of the client safe and take corrective measures that will help in providing the customized software based on the demand of the client.

PARTICIPATION
ACTIVITIES
ACTIVITIES
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
Information and network security solutions................................................................................1
Applications to expand in next five years...................................................................................2
CONCLUSION................................................................................................................................2
INTRODUCTION...........................................................................................................................1
Information and network security solutions................................................................................1
Applications to expand in next five years...................................................................................2
CONCLUSION................................................................................................................................2

INTRODUCTION
Information and communication technology is a growing field these days where majority
of people are involved in using internet. It is important to keep the data safe and secure and use
proper antivirus and safety security to perform it. The report discusses different types of
applications used in the industry. Further, several measures are discussed that can be adopted by
the entity (Liu and et.al., 2012).
Information and network security solutions
Network security is the process of taking physical and software preventative measures to
protect the underlying networking infrastructure from unauthorised access, misuse, malfunction,
modification thereby creating a secure platform for the computer users and programmers to
perform their tasks. Information system is the study of complementary networks of handwork
and software that people and organisation used to collect, filter and process the data (O’Connell,
2012).
The advantages of information and securities with triple R framework are the communication
through messaging, emails, voice and video should be relevant. The availability of information
has made it possible for the business to gather reliable information from the sources. The cost
effectiveness and the productivity promotes more efficient operation of the company and also
improves the supply of information. Globalization and cultural gap can bring down the linguistic
and geographical relationship between countries which creates a good reputation of the
company.
Disadvantages of information and security with triple R framework
The irrelevant or insufficient knowledge creates unemployment and lack of job securities.
The dominant culture may create or give the unhealthy environment and will lead to break down
of reputation. Security issues like hacking, getting access to confidential files should be stopped
to increase the reliability of the company.
The entity is planning to indulge in cyber security model where it will provide security to
the data of the clients. It is important to assess the malware available in the society and then plan
to take corrective actions (Pfleeger and Caputo, 2012). Information, communication and
technology is an important factor while providing these types of services to the client. The
company has to take care of economic, social and environmental factors while analysing client's
database and keep the data confidential.
1
Information and communication technology is a growing field these days where majority
of people are involved in using internet. It is important to keep the data safe and secure and use
proper antivirus and safety security to perform it. The report discusses different types of
applications used in the industry. Further, several measures are discussed that can be adopted by
the entity (Liu and et.al., 2012).
Information and network security solutions
Network security is the process of taking physical and software preventative measures to
protect the underlying networking infrastructure from unauthorised access, misuse, malfunction,
modification thereby creating a secure platform for the computer users and programmers to
perform their tasks. Information system is the study of complementary networks of handwork
and software that people and organisation used to collect, filter and process the data (O’Connell,
2012).
The advantages of information and securities with triple R framework are the communication
through messaging, emails, voice and video should be relevant. The availability of information
has made it possible for the business to gather reliable information from the sources. The cost
effectiveness and the productivity promotes more efficient operation of the company and also
improves the supply of information. Globalization and cultural gap can bring down the linguistic
and geographical relationship between countries which creates a good reputation of the
company.
Disadvantages of information and security with triple R framework
The irrelevant or insufficient knowledge creates unemployment and lack of job securities.
The dominant culture may create or give the unhealthy environment and will lead to break down
of reputation. Security issues like hacking, getting access to confidential files should be stopped
to increase the reliability of the company.
The entity is planning to indulge in cyber security model where it will provide security to
the data of the clients. It is important to assess the malware available in the society and then plan
to take corrective actions (Pfleeger and Caputo, 2012). Information, communication and
technology is an important factor while providing these types of services to the client. The
company has to take care of economic, social and environmental factors while analysing client's
database and keep the data confidential.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Applications to expand in next five years
As an ICT manager, it is important to assess the database of the client in right manner and
deliver what is required by them. Providing not only security solution but also network solutions
to them. It is also important to deliver right amount of security to their data in order to make
them loyal. The company can focus on customizing the software as per the clients demand and
also keep some software handy that can directly be provided to the customers (Von Solms and
Van Niekerk, 2013).
These practices will help the company to build its business and keep a track on the clients
demand as well. Emails, voice, video and messaging are the other components that will keep the
client and the entity in touch (Yan and et.al., 2012).
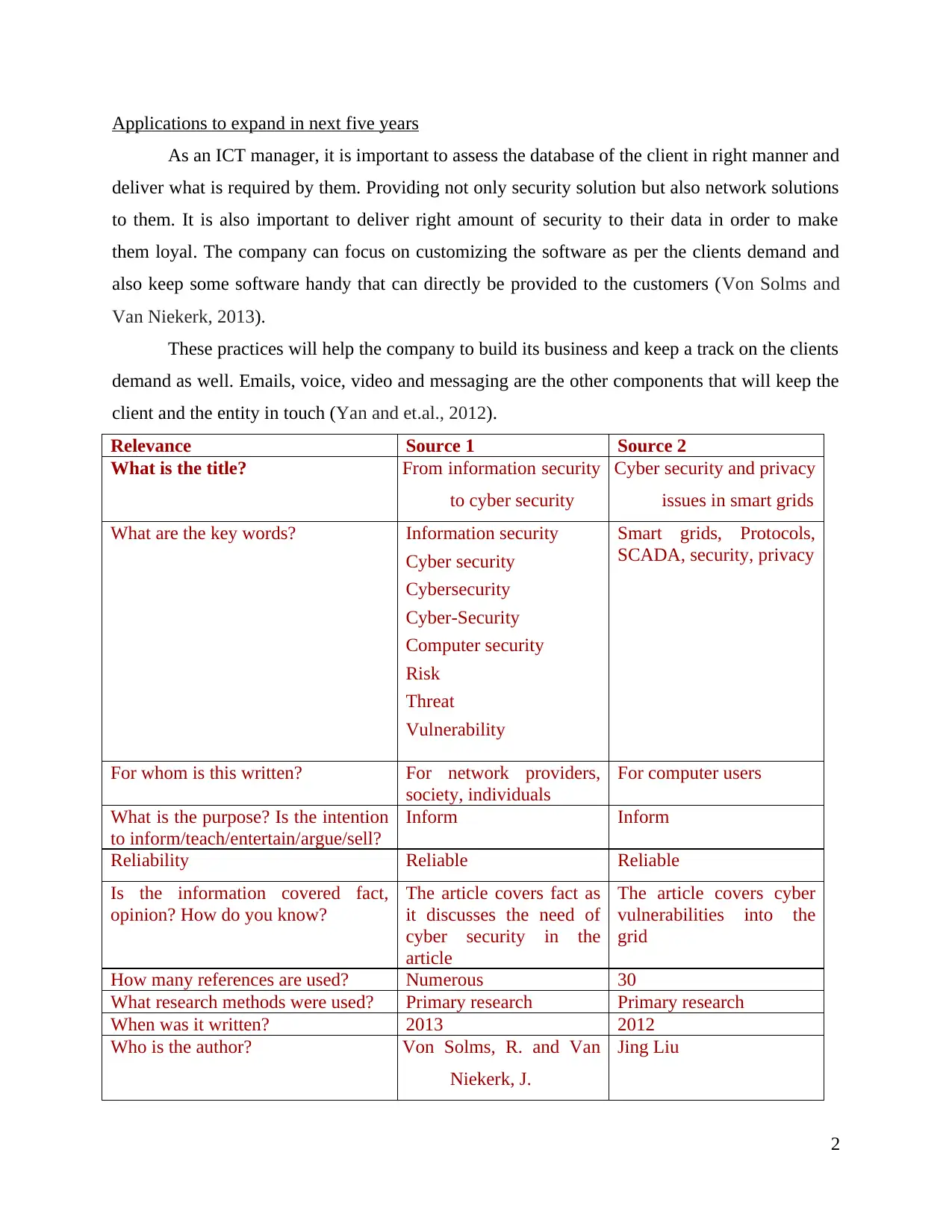
Relevance Source 1 Source 2
What is the title? From information security
to cyber security
Cyber security and privacy
issues in smart grids
What are the key words? Information security
Cyber security
Cybersecurity
Cyber-Security
Computer security
Risk
Threat
Vulnerability
Smart grids, Protocols,
SCADA, security, privacy
For whom is this written? For network providers,
society, individuals
For computer users
What is the purpose? Is the intention
to inform/teach/entertain/argue/sell?
Inform Inform
Reliability Reliable Reliable
Is the information covered fact,
opinion? How do you know?
The article covers fact as
it discusses the need of
cyber security in the
article
The article covers cyber
vulnerabilities into the
grid
How many references are used? Numerous 30
What research methods were used? Primary research Primary research
When was it written? 2013 2012
Who is the author? Von Solms, R. and Van
Niekerk, J.
Jing Liu
2
As an ICT manager, it is important to assess the database of the client in right manner and
deliver what is required by them. Providing not only security solution but also network solutions
to them. It is also important to deliver right amount of security to their data in order to make
them loyal. The company can focus on customizing the software as per the clients demand and
also keep some software handy that can directly be provided to the customers (Von Solms and
Van Niekerk, 2013).
These practices will help the company to build its business and keep a track on the clients
demand as well. Emails, voice, video and messaging are the other components that will keep the
client and the entity in touch (Yan and et.al., 2012).
Relevance Source 1 Source 2
What is the title? From information security
to cyber security
Cyber security and privacy
issues in smart grids
What are the key words? Information security
Cyber security
Cybersecurity
Cyber-Security
Computer security
Risk
Threat
Vulnerability
Smart grids, Protocols,
SCADA, security, privacy
For whom is this written? For network providers,
society, individuals
For computer users
What is the purpose? Is the intention
to inform/teach/entertain/argue/sell?
Inform Inform
Reliability Reliable Reliable
Is the information covered fact,
opinion? How do you know?
The article covers fact as
it discusses the need of
cyber security in the
article
The article covers cyber
vulnerabilities into the
grid
How many references are used? Numerous 30
What research methods were used? Primary research Primary research
When was it written? 2013 2012
Who is the author? Von Solms, R. and Van
Niekerk, J.
Jing Liu
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
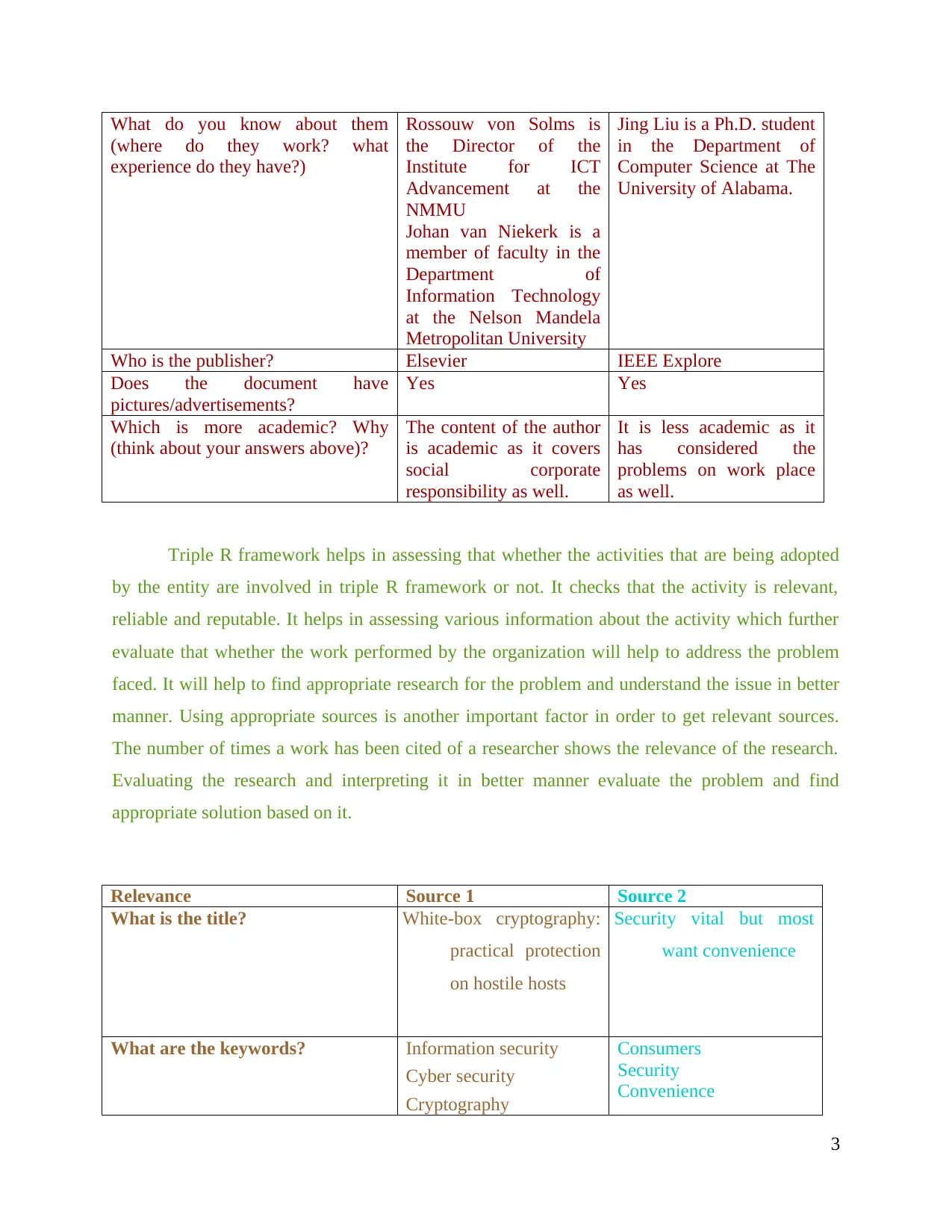
What do you know about them
(where do they work? what
experience do they have?)
Rossouw von Solms is
the Director of the
Institute for ICT
Advancement at the
NMMU
Johan van Niekerk is a
member of faculty in the
Department of
Information Technology
at the Nelson Mandela
Metropolitan University
Jing Liu is a Ph.D. student
in the Department of
Computer Science at The
University of Alabama.
Who is the publisher? Elsevier IEEE Explore
Does the document have
pictures/advertisements?
Yes Yes
Which is more academic? Why
(think about your answers above)?
The content of the author
is academic as it covers
social corporate
responsibility as well.
It is less academic as it
has considered the
problems on work place
as well.
Triple R framework helps in assessing that whether the activities that are being adopted
by the entity are involved in triple R framework or not. It checks that the activity is relevant,
reliable and reputable. It helps in assessing various information about the activity which further
evaluate that whether the work performed by the organization will help to address the problem
faced. It will help to find appropriate research for the problem and understand the issue in better
manner. Using appropriate sources is another important factor in order to get relevant sources.
The number of times a work has been cited of a researcher shows the relevance of the research.
Evaluating the research and interpreting it in better manner evaluate the problem and find
appropriate solution based on it.
Relevance Source 1 Source 2
What is the title? White-box cryptography:
practical protection
on hostile hosts
Security vital but most
want convenience
What are the keywords? Information security
Cyber security
Cryptography
Consumers
Security
Convenience
3
(where do they work? what
experience do they have?)
Rossouw von Solms is
the Director of the
Institute for ICT
Advancement at the
NMMU
Johan van Niekerk is a
member of faculty in the
Department of
Information Technology
at the Nelson Mandela
Metropolitan University
Jing Liu is a Ph.D. student
in the Department of
Computer Science at The
University of Alabama.
Who is the publisher? Elsevier IEEE Explore
Does the document have
pictures/advertisements?
Yes Yes
Which is more academic? Why
(think about your answers above)?
The content of the author
is academic as it covers
social corporate
responsibility as well.
It is less academic as it
has considered the
problems on work place
as well.
Triple R framework helps in assessing that whether the activities that are being adopted
by the entity are involved in triple R framework or not. It checks that the activity is relevant,
reliable and reputable. It helps in assessing various information about the activity which further
evaluate that whether the work performed by the organization will help to address the problem
faced. It will help to find appropriate research for the problem and understand the issue in better
manner. Using appropriate sources is another important factor in order to get relevant sources.
The number of times a work has been cited of a researcher shows the relevance of the research.
Evaluating the research and interpreting it in better manner evaluate the problem and find
appropriate solution based on it.
Relevance Source 1 Source 2
What is the title? White-box cryptography:
practical protection
on hostile hosts
Security vital but most
want convenience
What are the keywords? Information security
Cyber security
Cryptography
Consumers
Security
Convenience
3
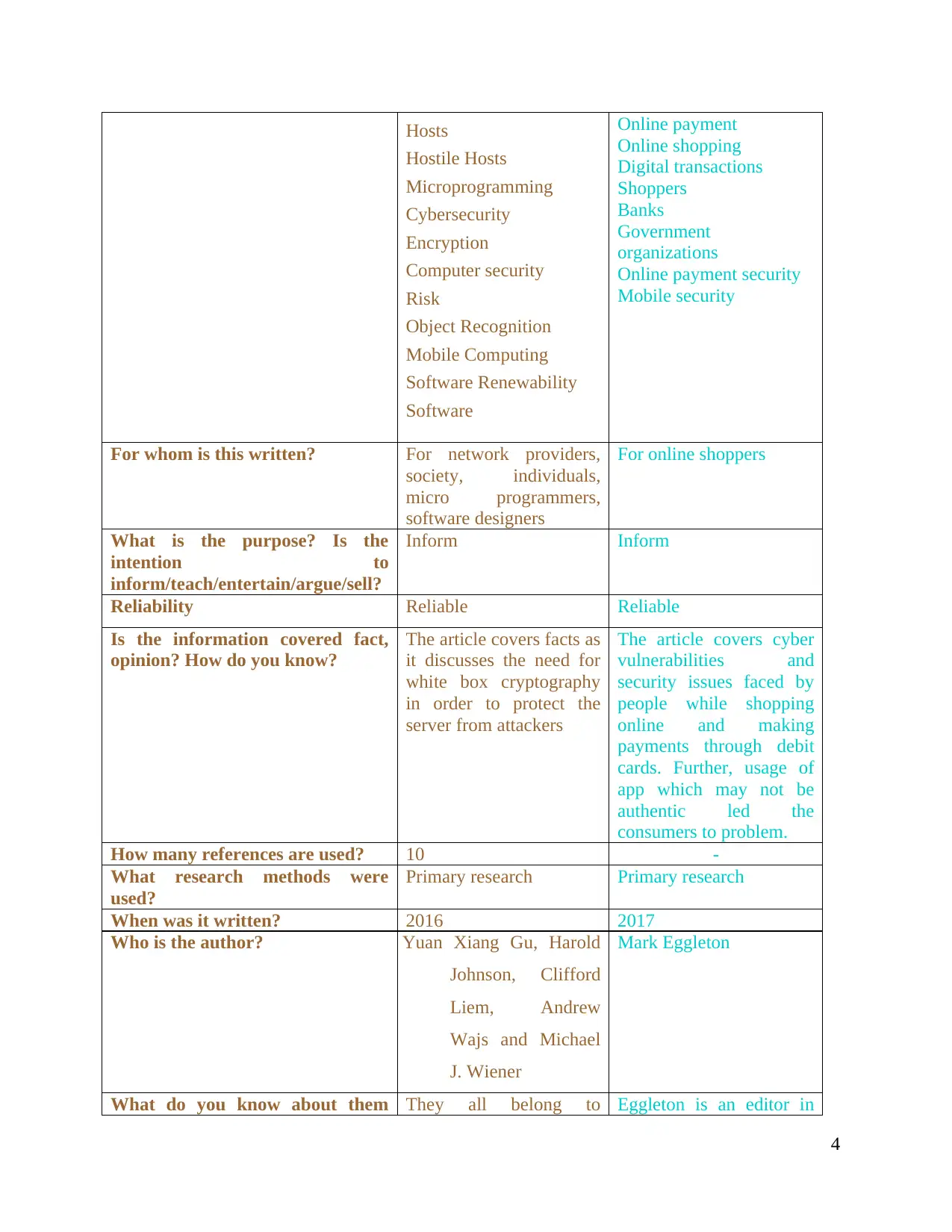
Hosts
Hostile Hosts
Microprogramming
Cybersecurity
Encryption
Computer security
Risk
Object Recognition
Mobile Computing
Software Renewability
Software
Online payment
Online shopping
Digital transactions
Shoppers
Banks
Government
organizations
Online payment security
Mobile security
For whom is this written? For network providers,
society, individuals,
micro programmers,
software designers
For online shoppers
What is the purpose? Is the
intention to
inform/teach/entertain/argue/sell?
Inform Inform
Reliability Reliable Reliable
Is the information covered fact,
opinion? How do you know?
The article covers facts as
it discusses the need for
white box cryptography
in order to protect the
server from attackers
The article covers cyber
vulnerabilities and
security issues faced by
people while shopping
online and making
payments through debit
cards. Further, usage of
app which may not be
authentic led the
consumers to problem.
How many references are used? 10 -
What research methods were
used?
Primary research Primary research
When was it written? 2016 2017
Who is the author? Yuan Xiang Gu, Harold
Johnson, Clifford
Liem, Andrew
Wajs and Michael
J. Wiener
Mark Eggleton
What do you know about them They all belong to Eggleton is an editor in
4
Hostile Hosts
Microprogramming
Cybersecurity
Encryption
Computer security
Risk
Object Recognition
Mobile Computing
Software Renewability
Software
Online payment
Online shopping
Digital transactions
Shoppers
Banks
Government
organizations
Online payment security
Mobile security
For whom is this written? For network providers,
society, individuals,
micro programmers,
software designers
For online shoppers
What is the purpose? Is the
intention to
inform/teach/entertain/argue/sell?
Inform Inform
Reliability Reliable Reliable
Is the information covered fact,
opinion? How do you know?
The article covers facts as
it discusses the need for
white box cryptography
in order to protect the
server from attackers
The article covers cyber
vulnerabilities and
security issues faced by
people while shopping
online and making
payments through debit
cards. Further, usage of
app which may not be
authentic led the
consumers to problem.
How many references are used? 10 -
What research methods were
used?
Primary research Primary research
When was it written? 2016 2017
Who is the author? Yuan Xiang Gu, Harold
Johnson, Clifford
Liem, Andrew
Wajs and Michael
J. Wiener
Mark Eggleton
What do you know about them They all belong to Eggleton is an editor in
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
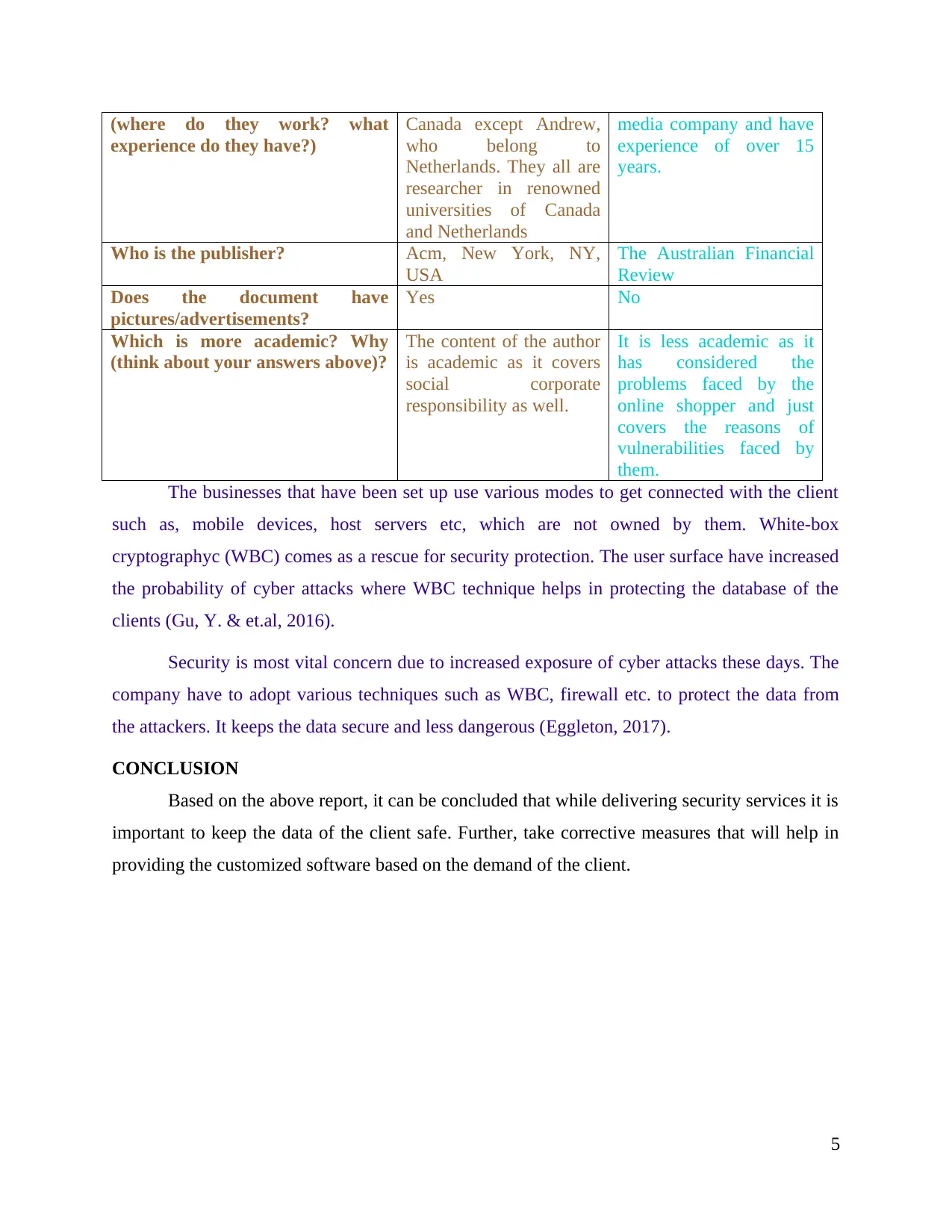
(where do they work? what
experience do they have?)
Canada except Andrew,
who belong to
Netherlands. They all are
researcher in renowned
universities of Canada
and Netherlands
media company and have
experience of over 15
years.
Who is the publisher? Acm, New York, NY,
USA
The Australian Financial
Review
Does the document have
pictures/advertisements?
Yes No
Which is more academic? Why
(think about your answers above)?
The content of the author
is academic as it covers
social corporate
responsibility as well.
It is less academic as it
has considered the
problems faced by the
online shopper and just
covers the reasons of
vulnerabilities faced by
them.
The businesses that have been set up use various modes to get connected with the client
such as, mobile devices, host servers etc, which are not owned by them. White-box
cryptographyc (WBC) comes as a rescue for security protection. The user surface have increased
the probability of cyber attacks where WBC technique helps in protecting the database of the
clients (Gu, Y. & et.al, 2016).
Security is most vital concern due to increased exposure of cyber attacks these days. The
company have to adopt various techniques such as WBC, firewall etc. to protect the data from
the attackers. It keeps the data secure and less dangerous (Eggleton, 2017).
CONCLUSION
Based on the above report, it can be concluded that while delivering security services it is
important to keep the data of the client safe. Further, take corrective measures that will help in
providing the customized software based on the demand of the client.
5
experience do they have?)
Canada except Andrew,
who belong to
Netherlands. They all are
researcher in renowned
universities of Canada
and Netherlands
media company and have
experience of over 15
years.
Who is the publisher? Acm, New York, NY,
USA
The Australian Financial
Review
Does the document have
pictures/advertisements?
Yes No
Which is more academic? Why
(think about your answers above)?
The content of the author
is academic as it covers
social corporate
responsibility as well.
It is less academic as it
has considered the
problems faced by the
online shopper and just
covers the reasons of
vulnerabilities faced by
them.
The businesses that have been set up use various modes to get connected with the client
such as, mobile devices, host servers etc, which are not owned by them. White-box
cryptographyc (WBC) comes as a rescue for security protection. The user surface have increased
the probability of cyber attacks where WBC technique helps in protecting the database of the
clients (Gu, Y. & et.al, 2016).
Security is most vital concern due to increased exposure of cyber attacks these days. The
company have to adopt various techniques such as WBC, firewall etc. to protect the data from
the attackers. It keeps the data secure and less dangerous (Eggleton, 2017).
CONCLUSION
Based on the above report, it can be concluded that while delivering security services it is
important to keep the data of the client safe. Further, take corrective measures that will help in
providing the customized software based on the demand of the client.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Eggleton, M. (2017). Security vital but most want convenience. The Australian Financial Review,
p 23.
Gu, Y. & et.al. (2016). White-box
cryptography: Practical protection on hostile hosts. Proceedings of the 6th Workshop on
Software Security, Protection, and Reverse Engineering. 1-8.
Liu, J. and et.al. (2012). Cyber security and privacy issues in smart grids. IEEE Communications
Surveys & Tutorials.14(4). pp.981-997.
O’Connell, M. E. (2012). Cyber security without cyber war. Journal of Conflict and Security
Law. 17(2). pp.187-209.
Pfleeger, S. L. and Caputo, D. D. (2012). Leveraging behavioral science to mitigate cyber
security risk. Computers & security. 31(4). pp.597-611.
Von Solms, R. and Van Niekerk, J. (2013). From information security to cyber
security. computers & security. 38. pp.97-102.
Yan, Y. and et.al. (2012). A survey on cyber security for smart grid communications. IEEE
Communications Surveys & Tutorials.
6
Eggleton, M. (2017). Security vital but most want convenience. The Australian Financial Review,
p 23.
Gu, Y. & et.al. (2016). White-box
cryptography: Practical protection on hostile hosts. Proceedings of the 6th Workshop on
Software Security, Protection, and Reverse Engineering. 1-8.
Liu, J. and et.al. (2012). Cyber security and privacy issues in smart grids. IEEE Communications
Surveys & Tutorials.14(4). pp.981-997.
O’Connell, M. E. (2012). Cyber security without cyber war. Journal of Conflict and Security
Law. 17(2). pp.187-209.
Pfleeger, S. L. and Caputo, D. D. (2012). Leveraging behavioral science to mitigate cyber
security risk. Computers & security. 31(4). pp.597-611.
Von Solms, R. and Van Niekerk, J. (2013). From information security to cyber
security. computers & security. 38. pp.97-102.
Yan, Y. and et.al. (2012). A survey on cyber security for smart grid communications. IEEE
Communications Surveys & Tutorials.
6
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





