Information Security Management Guidelines for A4A Organization
VerifiedAdded on 2020/04/01
|22
|4657
|37
Report
AI Summary
This report provides comprehensive information security management guidelines tailored for the A4A organization, which is in the process of transitioning to an information technology system. The report focuses on risk assessment, covering policy, legislation, and the risk management framework. It outlines steps including context establishment, risk identification, assessment, and treatment options, while also addressing cloud security considerations and potential threats like data breaches and loss. The document emphasizes the importance of Australian Privacy Law, the application of ISO 31000, and the need for continuous monitoring and review. The report concludes with recommendations to enhance the security of the information system, supporting the A4A's operational activities and safeguarding employee data.

Running head: INFORMATION SECURITY MANAGEMENT GUIDELINES
Information Security Management Guidelines
Name of the Student
Name of the University
Author Note
Information Security Management Guidelines
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INFORMATION SECURITY MANAGEMENT GUIDELINES
Executive Summary
The purpose of this report is to put emphasis on the guidelines that are suitable for the A4A
organization that is transforming its existing system into an information technology system in
order to enhance the performance. The risk assessment management of information security
includes various stages and steps that are mentioned in this report. First of all the Applicable
policy and legislations have been explained in order to specify the standard of information
security management. The whole risk assessment management process is comprised of overview
of the risk assessment management for information security has been introduced including risk
assessment framework, context establishment, risk identification, questions related to what
should be considered during risk identification, mapping risks and many more. A final comment
has also been introduced before the conclusion that states documentation and approval processes.
The whole report has been properly referenced in order to support the statements. A
recommendation has also been proposed in the conclusion part in order to enhance the security
of the information system for the A4A.
INFORMATION SECURITY MANAGEMENT GUIDELINES
Executive Summary
The purpose of this report is to put emphasis on the guidelines that are suitable for the A4A
organization that is transforming its existing system into an information technology system in
order to enhance the performance. The risk assessment management of information security
includes various stages and steps that are mentioned in this report. First of all the Applicable
policy and legislations have been explained in order to specify the standard of information
security management. The whole risk assessment management process is comprised of overview
of the risk assessment management for information security has been introduced including risk
assessment framework, context establishment, risk identification, questions related to what
should be considered during risk identification, mapping risks and many more. A final comment
has also been introduced before the conclusion that states documentation and approval processes.
The whole report has been properly referenced in order to support the statements. A
recommendation has also been proposed in the conclusion part in order to enhance the security
of the information system for the A4A.

2
INFORMATION SECURITY MANAGEMENT GUIDELINES
Table of Contents
Introduction......................................................................................................................................4
Applicable Policy and Legislation...................................................................................................4
Applicable Policy.........................................................................................................................4
Australian Privacy Law...............................................................................................................5
Privacy Legislation......................................................................................................................5
Overview of Risk Management for Information Security 624........................................................5
Risk Assessment Framework.......................................................................................................5
Applying ISO 31000....................................................................................................................6
Establish the Context...................................................................................................................7
How to Determine A4A Context.................................................................................................8
The Strategic Context of Outsourcing.........................................................................................8
Identifying Risk...........................................................................................................................8
How to Determine Agency Risk Tolerance.................................................................................9
Questions To Consider When Determining Risks within Cloud Context.................................10
Potential Threats When Outsourcing Information.....................................................................11
Mapping Risks...........................................................................................................................12
Assessing Risk...........................................................................................................................12
Guidance on Determining Potential Consequences...................................................................13
Evaluating the Risks..................................................................................................................13
INFORMATION SECURITY MANAGEMENT GUIDELINES
Table of Contents
Introduction......................................................................................................................................4
Applicable Policy and Legislation...................................................................................................4
Applicable Policy.........................................................................................................................4
Australian Privacy Law...............................................................................................................5
Privacy Legislation......................................................................................................................5
Overview of Risk Management for Information Security 624........................................................5
Risk Assessment Framework.......................................................................................................5
Applying ISO 31000....................................................................................................................6
Establish the Context...................................................................................................................7
How to Determine A4A Context.................................................................................................8
The Strategic Context of Outsourcing.........................................................................................8
Identifying Risk...........................................................................................................................8
How to Determine Agency Risk Tolerance.................................................................................9
Questions To Consider When Determining Risks within Cloud Context.................................10
Potential Threats When Outsourcing Information.....................................................................11
Mapping Risks...........................................................................................................................12
Assessing Risk...........................................................................................................................12
Guidance on Determining Potential Consequences...................................................................13
Evaluating the Risks..................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INFORMATION SECURITY MANAGEMENT GUIDELINES
How to Consider Potential Risk Treatment Options.................................................................14
Communication and Consultation.............................................................................................14
Risk Monitoring and Review.....................................................................................................15
Finalizing the Risk Assessment.....................................................................................................15
Documenting the Risk Assessment and Risk Treatment...........................................................15
Approval Process.......................................................................................................................15
Conclusion.................................................................................................................................16
References:....................................................................................................................................17
INFORMATION SECURITY MANAGEMENT GUIDELINES
How to Consider Potential Risk Treatment Options.................................................................14
Communication and Consultation.............................................................................................14
Risk Monitoring and Review.....................................................................................................15
Finalizing the Risk Assessment.....................................................................................................15
Documenting the Risk Assessment and Risk Treatment...........................................................15
Approval Process.......................................................................................................................15
Conclusion.................................................................................................................................16
References:....................................................................................................................................17
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INFORMATION SECURITY MANAGEMENT GUIDELINES
Introduction
The aim of this report is to provide guidance to the A4A organization considering the
processing and storage of data that is about to store in the information systems. The scope of this
report is to provide a security risk management approach for the organization to the integrity,
confidentiality, and availability of information that are being stored in the information systems of
the organization.
A4A is Non-Governmental Organization that is about to transform its existing system
into the information system that means various data and information are about to be uploaded
into the database. This will be vast transformation that will include outsourcing of the systems
for other organizations and for larger space, they will need cloud storage that could result in
various security issues related to the organizational operational activities and all the data related
to the employees that are looking forward to join the organization.
This report focuses on the guidelines that could help in achieving information security in
better and efficient way for the data and information related to the organization. Risk assessment
process have several step and these steps have been explained in the below report.
Applicable Policy and Legislation
Applicable Policy
The policy for security of information by the Australian Government policy has been
promulgated through the ISM and the PSPF. Several requirements those are mandatory within
the PSPF that can be helpful to relate the handling of A4A information (Sylves 2014). A4A can
only be able to achieve effective information security for the information that is about to save in
INFORMATION SECURITY MANAGEMENT GUIDELINES
Introduction
The aim of this report is to provide guidance to the A4A organization considering the
processing and storage of data that is about to store in the information systems. The scope of this
report is to provide a security risk management approach for the organization to the integrity,
confidentiality, and availability of information that are being stored in the information systems of
the organization.
A4A is Non-Governmental Organization that is about to transform its existing system
into the information system that means various data and information are about to be uploaded
into the database. This will be vast transformation that will include outsourcing of the systems
for other organizations and for larger space, they will need cloud storage that could result in
various security issues related to the organizational operational activities and all the data related
to the employees that are looking forward to join the organization.
This report focuses on the guidelines that could help in achieving information security in
better and efficient way for the data and information related to the organization. Risk assessment
process have several step and these steps have been explained in the below report.
Applicable Policy and Legislation
Applicable Policy
The policy for security of information by the Australian Government policy has been
promulgated through the ISM and the PSPF. Several requirements those are mandatory within
the PSPF that can be helpful to relate the handling of A4A information (Sylves 2014). A4A can
only be able to achieve effective information security for the information that is about to save in

5
INFORMATION SECURITY MANAGEMENT GUIDELINES
the system regarding its members and operational activities. This can only be achieved if it
becomes the part of the culture, operation and practices plans of the A4A. This implies that the
A4A should not build protective security as an afterthought rather it should build it into the
governance processes. The organization should proactively mitigate and manage the identified
security risks at its early stages that are associated with the information storage system.
Australian Privacy Law
Set of thirteen APPs (Australian Privacy Principles) has been included within the Privacy
Act 1988 (Cth) that can be helpful in regulating the handling of personal information by the A4A
(Arregui, Maynard and Ahmad 2016). The information those have been remarked as “personal”
should be determined by the A4A and handling of these information should be done according to
the principles of the APPs.
Privacy Legislation
The pieces of legislations that are applicable to this policy can be listed as: Firstly,
Freedom of Information Act 1982, secondly, Privacy Act 1988 and Archives Act 1983 (Zetler
2015).
Overview of Risk Management for Information Security
Risk Assessment Framework
This can be stated as the set of guidelines for the risk assessment process on the basis of
existing frameworks that is being defined in the Australian Standards AS/NZS ISO 31000:2009
Risk management that includes HB 167:2006 Security Risk Management, and guidelines and
principles. Risk assessment can be referred as the subjective process and A4A should ensure that
the defined process is justifiable, documented, and transparent (Saint-Germain 2015). It is the
INFORMATION SECURITY MANAGEMENT GUIDELINES
the system regarding its members and operational activities. This can only be achieved if it
becomes the part of the culture, operation and practices plans of the A4A. This implies that the
A4A should not build protective security as an afterthought rather it should build it into the
governance processes. The organization should proactively mitigate and manage the identified
security risks at its early stages that are associated with the information storage system.
Australian Privacy Law
Set of thirteen APPs (Australian Privacy Principles) has been included within the Privacy
Act 1988 (Cth) that can be helpful in regulating the handling of personal information by the A4A
(Arregui, Maynard and Ahmad 2016). The information those have been remarked as “personal”
should be determined by the A4A and handling of these information should be done according to
the principles of the APPs.
Privacy Legislation
The pieces of legislations that are applicable to this policy can be listed as: Firstly,
Freedom of Information Act 1982, secondly, Privacy Act 1988 and Archives Act 1983 (Zetler
2015).
Overview of Risk Management for Information Security
Risk Assessment Framework
This can be stated as the set of guidelines for the risk assessment process on the basis of
existing frameworks that is being defined in the Australian Standards AS/NZS ISO 31000:2009
Risk management that includes HB 167:2006 Security Risk Management, and guidelines and
principles. Risk assessment can be referred as the subjective process and A4A should ensure that
the defined process is justifiable, documented, and transparent (Saint-Germain 2015). It is the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
INFORMATION SECURITY MANAGEMENT GUIDELINES
best option for many objectives like firstly, identifying the level of risk tolerance, secondly,
identifying the specific risks to the employees, assets, and information that are being stored in
the system. Third benefit is that identifying the appropriate protection in order to mitigate the
risks that have been identified previously.
Applying ISO 31000
The process of risk assessment process should be consistent within the existing standards.
In order to successfully manage the risk assessment, the whole process can be sub-divided into
five key points that can be stated as (Draper and Ritchie 2014):
Establishment of the Context: This step states to define the external and internal influences that
can have impact on the implementation of the arrangement directly or indirectly.
Identification of the Risks: Developing a robust list of the identified risks, this might have the
capability to affect the success in implementing this arrangement.
Assessment of the identified Risks: After the first two steps it states to analysing the list of
identified risks in contrast with the organisations likelihood, impact, and the tolerances.
Selection of Proper Treatments: This step includes choosing risk assessing strategies that are
appropriate for A4A including the controls for those identified risks.
Development of overall Risk Assessment: This is the last and final step that includes
summarization of the output of identified risks in accordance with the mitigating measures or control into
all the categorized risks.
INFORMATION SECURITY MANAGEMENT GUIDELINES
best option for many objectives like firstly, identifying the level of risk tolerance, secondly,
identifying the specific risks to the employees, assets, and information that are being stored in
the system. Third benefit is that identifying the appropriate protection in order to mitigate the
risks that have been identified previously.
Applying ISO 31000
The process of risk assessment process should be consistent within the existing standards.
In order to successfully manage the risk assessment, the whole process can be sub-divided into
five key points that can be stated as (Draper and Ritchie 2014):
Establishment of the Context: This step states to define the external and internal influences that
can have impact on the implementation of the arrangement directly or indirectly.
Identification of the Risks: Developing a robust list of the identified risks, this might have the
capability to affect the success in implementing this arrangement.
Assessment of the identified Risks: After the first two steps it states to analysing the list of
identified risks in contrast with the organisations likelihood, impact, and the tolerances.
Selection of Proper Treatments: This step includes choosing risk assessing strategies that are
appropriate for A4A including the controls for those identified risks.
Development of overall Risk Assessment: This is the last and final step that includes
summarization of the output of identified risks in accordance with the mitigating measures or control into
all the categorized risks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
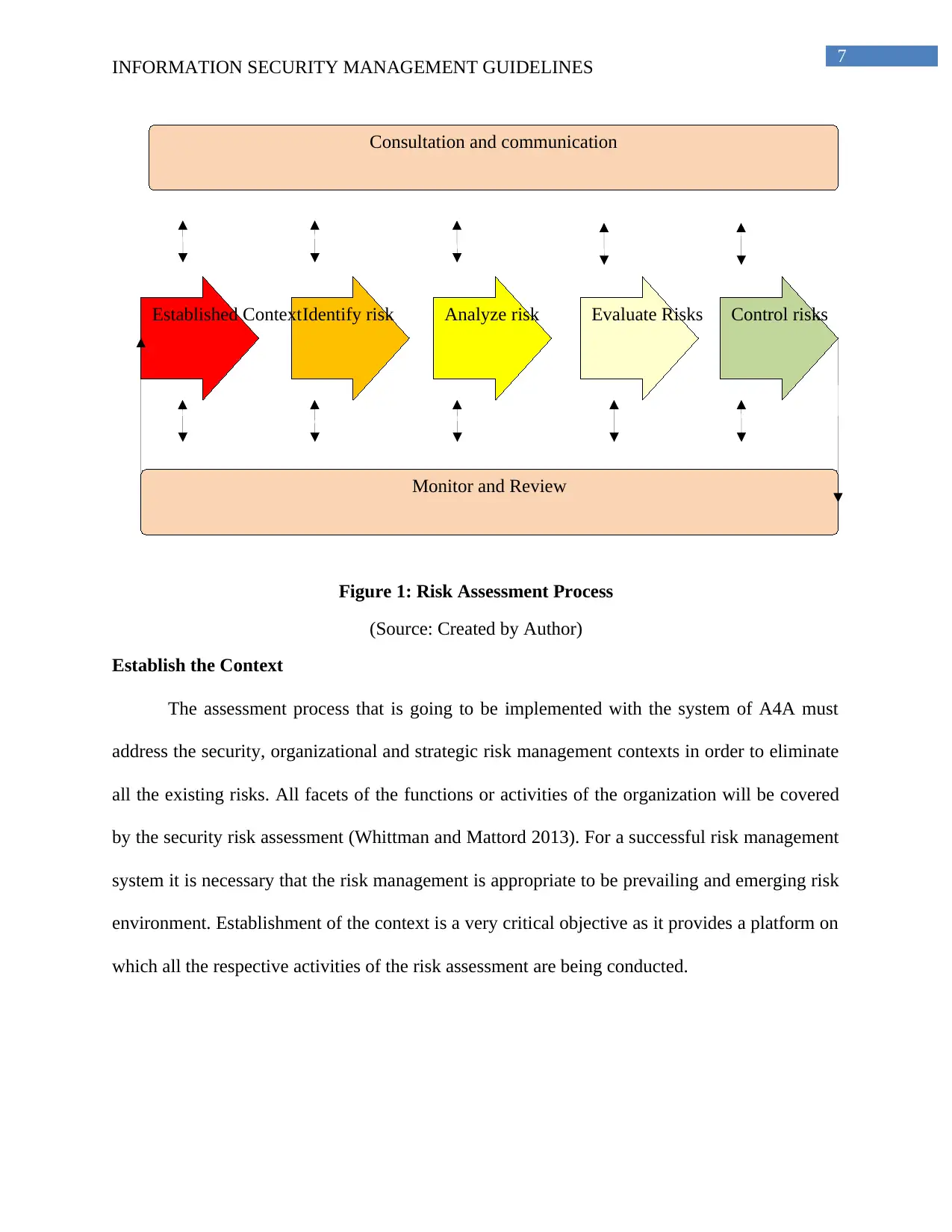
7
Control risksEvaluate RisksAnalyze riskIdentify riskEstablished Context
Consultation and communication
Monitor and Review
INFORMATION SECURITY MANAGEMENT GUIDELINES
Figure 1: Risk Assessment Process
(Source: Created by Author)
Establish the Context
The assessment process that is going to be implemented with the system of A4A must
address the security, organizational and strategic risk management contexts in order to eliminate
all the existing risks. All facets of the functions or activities of the organization will be covered
by the security risk assessment (Whittman and Mattord 2013). For a successful risk management
system it is necessary that the risk management is appropriate to be prevailing and emerging risk
environment. Establishment of the context is a very critical objective as it provides a platform on
which all the respective activities of the risk assessment are being conducted.
Control risksEvaluate RisksAnalyze riskIdentify riskEstablished Context
Consultation and communication
Monitor and Review
INFORMATION SECURITY MANAGEMENT GUIDELINES
Figure 1: Risk Assessment Process
(Source: Created by Author)
Establish the Context
The assessment process that is going to be implemented with the system of A4A must
address the security, organizational and strategic risk management contexts in order to eliminate
all the existing risks. All facets of the functions or activities of the organization will be covered
by the security risk assessment (Whittman and Mattord 2013). For a successful risk management
system it is necessary that the risk management is appropriate to be prevailing and emerging risk
environment. Establishment of the context is a very critical objective as it provides a platform on
which all the respective activities of the risk assessment are being conducted.

8
INFORMATION SECURITY MANAGEMENT GUIDELINES
How to Determine A4A Context
Internal environment in which the organization is willing in order to achieve its goals can
be stated as the context of the A4A. Following are the objectives that can be included in this
topic:
A4A Organizational structure, governance, accountabilities or responsibilities, and roles.
Extent and nature of the contractual relationships (Wensveen 2016).
Culture of the A4A including its security culture
Policies and objectives including the strategies that are being made to achieve them.
Perception, values of, and relationships with the internal stakeholders
Models, guidelines, and standards that are being adopted by the organisation
Lastly, information flows, decision making processes, and information systems
The Strategic Context of Outsourcing
A4A must consider the aspects of the strategic contexts that are relevant according to the
situation that will be the factors which will be implemented in the risk assessment management
process. These include, firstly, relevant Australian regulation, policy, and legislation considering
the facts that are responsible for safeguarding the information related to the operational activities
of the A4A (Peppard and Ward 2016). Secondly, it includes potential jurisdictional and foreign
laws access to information, and third objective that is being included in this is the potential
benefits of off shoring or outsourcing arrangements that is being arranged to manage the systems
that needs to be installed.
INFORMATION SECURITY MANAGEMENT GUIDELINES
How to Determine A4A Context
Internal environment in which the organization is willing in order to achieve its goals can
be stated as the context of the A4A. Following are the objectives that can be included in this
topic:
A4A Organizational structure, governance, accountabilities or responsibilities, and roles.
Extent and nature of the contractual relationships (Wensveen 2016).
Culture of the A4A including its security culture
Policies and objectives including the strategies that are being made to achieve them.
Perception, values of, and relationships with the internal stakeholders
Models, guidelines, and standards that are being adopted by the organisation
Lastly, information flows, decision making processes, and information systems
The Strategic Context of Outsourcing
A4A must consider the aspects of the strategic contexts that are relevant according to the
situation that will be the factors which will be implemented in the risk assessment management
process. These include, firstly, relevant Australian regulation, policy, and legislation considering
the facts that are responsible for safeguarding the information related to the operational activities
of the A4A (Peppard and Ward 2016). Secondly, it includes potential jurisdictional and foreign
laws access to information, and third objective that is being included in this is the potential
benefits of off shoring or outsourcing arrangements that is being arranged to manage the systems
that needs to be installed.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
Intolerable risk
Scope for A4A
Tolerable risk
Increasing risk
Incapacity to manage
INFORMATION SECURITY MANAGEMENT GUIDELINES
Identifying Risk
Identifying risk can be used in manner to comprehensively determine the sources of risk
that are applicable and the events that have potential to impact the business of A4A organization.
There should be full description on the issues that is being identified in manner to make the
decision makers completely understand the facts that is all about. A4A risk management team
should determine the risks that are related to the availability, integrity, and the confidentiality of
the types of data that is being saved in the information system considering the personal
information of the employees and the operational data or information (Webet al. 2014). As
mentioned in the AS/NZS 4360:2004 risks can be defined as “The chance of something
happening that will have an impact on the objectives”.
How to Determine Agency Risk Tolerance
Figure 2: Risk Tolerance
(Source: Created by author)
This determination can be made during the ‘Establishing the context’ phase during the
risk assessment processes. Risk tolerance is completely dependent on the organizational context
Intolerable risk
Scope for A4A
Tolerable risk
Increasing risk
Incapacity to manage
INFORMATION SECURITY MANAGEMENT GUIDELINES
Identifying Risk
Identifying risk can be used in manner to comprehensively determine the sources of risk
that are applicable and the events that have potential to impact the business of A4A organization.
There should be full description on the issues that is being identified in manner to make the
decision makers completely understand the facts that is all about. A4A risk management team
should determine the risks that are related to the availability, integrity, and the confidentiality of
the types of data that is being saved in the information system considering the personal
information of the employees and the operational data or information (Webet al. 2014). As
mentioned in the AS/NZS 4360:2004 risks can be defined as “The chance of something
happening that will have an impact on the objectives”.
How to Determine Agency Risk Tolerance
Figure 2: Risk Tolerance
(Source: Created by author)
This determination can be made during the ‘Establishing the context’ phase during the
risk assessment processes. Risk tolerance is completely dependent on the organizational context
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
INFORMATION SECURITY MANAGEMENT GUIDELINES
of the A4A and Heads of the A4A. Tolerance level can be stated as the sum of risk appetite of
A4A. The risk tolerance will be based on the the principle of managing risk to the reasonably
practicable low level, while it still allows the scope for the innovation and flexibility in business
practices. Boyens et al. (2014) stated that it can be affected or changed changing the evaluation
criteria, which implies that appetite risk of the head of the A4A for the risk can be variable that
can depends upon: Firstly, prevailing community and political expectations and sensitivities.
Secondly, incident security nature such as hacking terrorist attack etc., thirdly, emergence or
existence of security trends such as cyber-attacks, data breaches, trusted insider etc. Another
factors may be business or strategic priorities, ability of the government, individual or the
organization to compensate losses and lastly but not least availability of the resources for
treatment.
Questions To Consider When Determining Risks within Cloud Context
In order to establishing context in a risk management it is very necessary to understand
the nature of the vulnerabilities, criticality, and potential or relevant threat. The questionnaire
that can be included in this section in order to facilitate it can be listed as (Rebello et al. 2015):
• The aggregated value of the information holdings to the A4A
• How the integrity, availability, and confidentiality of A4A will be affected
• What would be the look of an unintended disclosure? What would be the look of an event
or incident
• How outsourcing might affect the information of the A4A including the sources of risks
and related threats
• How much impact on losing information can affect the A4A
INFORMATION SECURITY MANAGEMENT GUIDELINES
of the A4A and Heads of the A4A. Tolerance level can be stated as the sum of risk appetite of
A4A. The risk tolerance will be based on the the principle of managing risk to the reasonably
practicable low level, while it still allows the scope for the innovation and flexibility in business
practices. Boyens et al. (2014) stated that it can be affected or changed changing the evaluation
criteria, which implies that appetite risk of the head of the A4A for the risk can be variable that
can depends upon: Firstly, prevailing community and political expectations and sensitivities.
Secondly, incident security nature such as hacking terrorist attack etc., thirdly, emergence or
existence of security trends such as cyber-attacks, data breaches, trusted insider etc. Another
factors may be business or strategic priorities, ability of the government, individual or the
organization to compensate losses and lastly but not least availability of the resources for
treatment.
Questions To Consider When Determining Risks within Cloud Context
In order to establishing context in a risk management it is very necessary to understand
the nature of the vulnerabilities, criticality, and potential or relevant threat. The questionnaire
that can be included in this section in order to facilitate it can be listed as (Rebello et al. 2015):
• The aggregated value of the information holdings to the A4A
• How the integrity, availability, and confidentiality of A4A will be affected
• What would be the look of an unintended disclosure? What would be the look of an event
or incident
• How outsourcing might affect the information of the A4A including the sources of risks
and related threats
• How much impact on losing information can affect the A4A

11
INFORMATION SECURITY MANAGEMENT GUIDELINES
A4A can take into account the individual security plans while searching for the information
that are related to the risk identification process due to the existing presence of information on
security of the information.
Potential Threats When Outsourcing Information
Data Loss: There may be the permanent deletion or loss of data, which could be a result
of malicious activity or by any accident.
Data Breaches: The information those are very sensitive for the organization could be
leaked or stolen or might be manipulated by an unauthorized user (Peltier 2016).
Service traffic or Account Hijacking: this another potential threat that might lead the
external entities eavesdropping on the operational activities such as manipulating data,
transactions, through phishing, fraud, and return falsified information.
DOS (Denial of service): this threat or attack can block the user from accessing their
application or data that will affect the organization and its consumers too.
API (Application Programming Interface) and Interfaces Insecure: In manner to circumvent the
security processes, vulnerable interfaces may be exploited maliciously and accidentally both.
Malicious Insider: The insider formal stakeholders like contractor, former employee, or
any of the other business partners can be threat who had or has the access authority to the
network of the A4A organization (Dhillong, Syed and Sa-Soares 2017). This access authority
can be misused for personal gain or profit by impacting negatively to the organization.
INFORMATION SECURITY MANAGEMENT GUIDELINES
A4A can take into account the individual security plans while searching for the information
that are related to the risk identification process due to the existing presence of information on
security of the information.
Potential Threats When Outsourcing Information
Data Loss: There may be the permanent deletion or loss of data, which could be a result
of malicious activity or by any accident.
Data Breaches: The information those are very sensitive for the organization could be
leaked or stolen or might be manipulated by an unauthorized user (Peltier 2016).
Service traffic or Account Hijacking: this another potential threat that might lead the
external entities eavesdropping on the operational activities such as manipulating data,
transactions, through phishing, fraud, and return falsified information.
DOS (Denial of service): this threat or attack can block the user from accessing their
application or data that will affect the organization and its consumers too.
API (Application Programming Interface) and Interfaces Insecure: In manner to circumvent the
security processes, vulnerable interfaces may be exploited maliciously and accidentally both.
Malicious Insider: The insider formal stakeholders like contractor, former employee, or
any of the other business partners can be threat who had or has the access authority to the
network of the A4A organization (Dhillong, Syed and Sa-Soares 2017). This access authority
can be misused for personal gain or profit by impacting negatively to the organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





