Information Security Risk Assessment Report for CONVXYZ Company
VerifiedAdded on 2023/01/19
|11
|2902
|54
Report
AI Summary
This report presents a comprehensive risk assessment for CONVXYZ, a US-based real estate and conveying services company. The assessment identifies and analyzes potential threats to the company's network architecture, categorized into physical, software, and service assets. The report utilizes the HAZOP method to evaluate risks, detailing vulnerabilities such as SQL injection, misconfigurations, and lack of documentation. It assesses the likelihood and impact of various threats, including denial-of-service attacks, brute force attacks, and insider threats, culminating in a risk matrix and impact specification table. The report concludes with a summary of findings and recommendations for mitigating identified risks to ensure the company's information security and operational continuity.

INFORMATION SECURITY MANAGEMENT 1
INFORMATION SECURITY MANAGEMENT
(Student’s Name)
(Professor’s Name)
(Course Title)
(Date of Submission)
INFORMATION SECURITY MANAGEMENT
(Student’s Name)
(Professor’s Name)
(Course Title)
(Date of Submission)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SECURITY MANAGEMENT 2
Table of Contents
Executive summary.....................................................................................................................................3
Introduction.................................................................................................................................................3
Risk assessment...........................................................................................................................................4
Assets......................................................................................................................................................4
Threats.....................................................................................................................................................4
Threats to primary assets....................................................................................................................4
Server threats......................................................................................................................................5
Threats to secondary assets................................................................................................................5
Vulnerabilities......................................................................................................................................6
Vulnerability for each asset.................................................................................................................6
Likelihood level computation..............................................................................................................7
Magnitude of impact...........................................................................................................................7
Risk matrix table..................................................................................................................................8
Impact specification table....................................................................................................................9
Risk identification................................................................................................................................9
Summary and recommendation..................................................................................................................9
References.................................................................................................................................................10
Table of Contents
Executive summary.....................................................................................................................................3
Introduction.................................................................................................................................................3
Risk assessment...........................................................................................................................................4
Assets......................................................................................................................................................4
Threats.....................................................................................................................................................4
Threats to primary assets....................................................................................................................4
Server threats......................................................................................................................................5
Threats to secondary assets................................................................................................................5
Vulnerabilities......................................................................................................................................6
Vulnerability for each asset.................................................................................................................6
Likelihood level computation..............................................................................................................7
Magnitude of impact...........................................................................................................................7
Risk matrix table..................................................................................................................................8
Impact specification table....................................................................................................................9
Risk identification................................................................................................................................9
Summary and recommendation..................................................................................................................9
References.................................................................................................................................................10

INFORMATION SECURITY MANAGEMENT 3
Executive summary
CONVXYZ is a company in the US which provides real estate services for buyers and vendors. The
company also provides conveying services to lawyers. One of the major goals of the company security
team is to minimize or prevent the company from possible security incidents like information stealing,
data modification and deletion, and malfunction. An architectural diagram has been proposed as
depicted by figure one shown below. The dashed box shows the internal network of the company and all
its assets. This report is a detailed risk assessment report for figure one below. In addition, this risk
assessment report has proposed recommendations which will be based on the findings.
Introduction
Risk assessment is a process which includes three major steps which are; risk identification,
evaluation of risks, and risk impacts. The process allows IT managers to balance the economic and
operational costs of protective measures. Risk assessment methodology comprises of nine major steps
which are system characterization, threat identification, vulnerability identification, control analysis,
likelihood determination, impact analysis, risk determination, control recommendations, and results in
documentation (Vasudevan, 2017, p. 59). There are various risk assessment methods, but this paper will
utilize HAZOP method. HAZOP is an acronym for HAZard and OPerability. The method is structured for
examining the existing system components. Specifically, HAZOP method is used to identify risks to
equipment and people. One of the advantages of this method is that those conducting the risks are
expected to provide a solution for treating the risks. Other advantages are that the HAZOP process is a
systematic process and covers safety as well as operational aspects. The method also covers human
errors and the study results are recorded. Commercial software is available to assist in HAZOP analysis.
Also, the process is easily performed and learned. Lastly, HAZOP method is a technique which considers
the parts of a system systematically and separately to examine the deviation of each of the part. The
technique also considers network design representation (Gossman, 2009).
Figure 1: Proposed CONVXYZ network architecture diagram
Executive summary
CONVXYZ is a company in the US which provides real estate services for buyers and vendors. The
company also provides conveying services to lawyers. One of the major goals of the company security
team is to minimize or prevent the company from possible security incidents like information stealing,
data modification and deletion, and malfunction. An architectural diagram has been proposed as
depicted by figure one shown below. The dashed box shows the internal network of the company and all
its assets. This report is a detailed risk assessment report for figure one below. In addition, this risk
assessment report has proposed recommendations which will be based on the findings.
Introduction
Risk assessment is a process which includes three major steps which are; risk identification,
evaluation of risks, and risk impacts. The process allows IT managers to balance the economic and
operational costs of protective measures. Risk assessment methodology comprises of nine major steps
which are system characterization, threat identification, vulnerability identification, control analysis,
likelihood determination, impact analysis, risk determination, control recommendations, and results in
documentation (Vasudevan, 2017, p. 59). There are various risk assessment methods, but this paper will
utilize HAZOP method. HAZOP is an acronym for HAZard and OPerability. The method is structured for
examining the existing system components. Specifically, HAZOP method is used to identify risks to
equipment and people. One of the advantages of this method is that those conducting the risks are
expected to provide a solution for treating the risks. Other advantages are that the HAZOP process is a
systematic process and covers safety as well as operational aspects. The method also covers human
errors and the study results are recorded. Commercial software is available to assist in HAZOP analysis.
Also, the process is easily performed and learned. Lastly, HAZOP method is a technique which considers
the parts of a system systematically and separately to examine the deviation of each of the part. The
technique also considers network design representation (Gossman, 2009).
Figure 1: Proposed CONVXYZ network architecture diagram
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
INFORMATION SECURITY MANAGEMENT 4
Risk assessment
Assets
Assets for CONVXYZ are grouped into three categories which are the physical assets, software
assets, and services assets. The physical assets are the primary assets while software and service assets
are the secondary assets. As shown in figure one above, the physical assets are the communication
media equipment which in this case are the router, firewall, and switch. Other physical assets are the
estate PCs, lawyer PCs, the web-server, mail server, staff database, authentication server, and the staff
database. The secondary assets which comprise of databases stores CONVXYZ information which stored
in the organization database. This information could be finances, personnel and production information.
In addition, under secondary assets, you can also find data files which contain support and operational
procedures which have been developed by the organization over the years. Other information assets
one can get is the archived information which contains old information which is maintained by law. Also
at the database server, one can get the company continuity plans developed by the company to
maintain the continuity of the company. Another secondary assets are the software assets; this is
categorized into two which are the system software and application software. The application software
implements the business rules of the company. The system software is the various packaged software
such as the operating system, Database Management System and the office productivity. The last
secondary assets are the services; these services include communication services such as voice
communication, value-added services, the wide area network, and data communication. It also contains
computing services which a company have outsourced (Lee, 2005, p. 67)
Threats
Threat statement
This paper identified the following potential threat sources and their associated actions as
shown by table one below
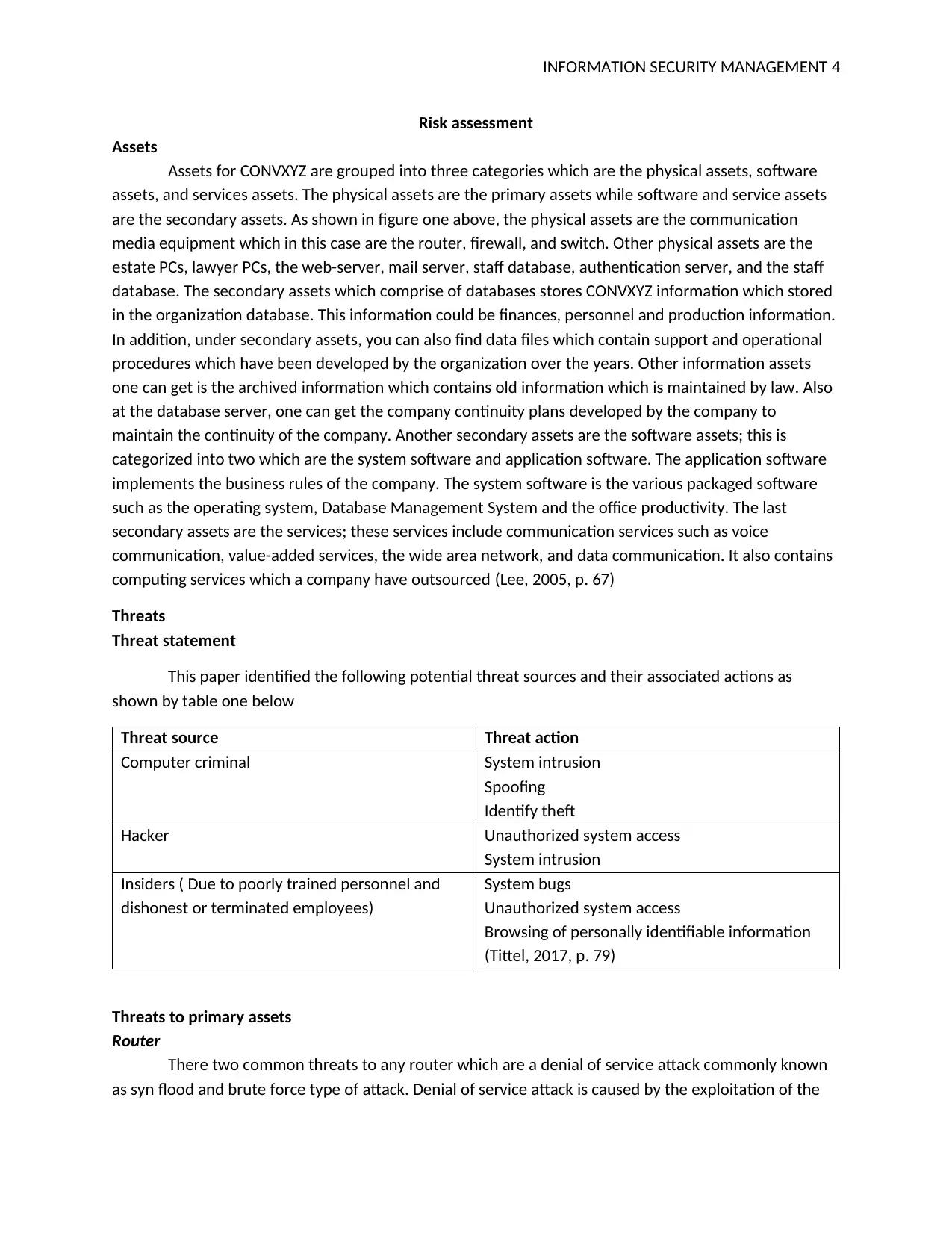
Threat source Threat action
Computer criminal System intrusion
Spoofing
Identify theft
Hacker Unauthorized system access
System intrusion
Insiders ( Due to poorly trained personnel and
dishonest or terminated employees)
System bugs
Unauthorized system access
Browsing of personally identifiable information
(Tittel, 2017, p. 79)
Threats to primary assets
Router
There two common threats to any router which are a denial of service attack commonly known
as syn flood and brute force type of attack. Denial of service attack is caused by the exploitation of the
Risk assessment
Assets
Assets for CONVXYZ are grouped into three categories which are the physical assets, software
assets, and services assets. The physical assets are the primary assets while software and service assets
are the secondary assets. As shown in figure one above, the physical assets are the communication
media equipment which in this case are the router, firewall, and switch. Other physical assets are the
estate PCs, lawyer PCs, the web-server, mail server, staff database, authentication server, and the staff
database. The secondary assets which comprise of databases stores CONVXYZ information which stored
in the organization database. This information could be finances, personnel and production information.
In addition, under secondary assets, you can also find data files which contain support and operational
procedures which have been developed by the organization over the years. Other information assets
one can get is the archived information which contains old information which is maintained by law. Also
at the database server, one can get the company continuity plans developed by the company to
maintain the continuity of the company. Another secondary assets are the software assets; this is
categorized into two which are the system software and application software. The application software
implements the business rules of the company. The system software is the various packaged software
such as the operating system, Database Management System and the office productivity. The last
secondary assets are the services; these services include communication services such as voice
communication, value-added services, the wide area network, and data communication. It also contains
computing services which a company have outsourced (Lee, 2005, p. 67)
Threats
Threat statement
This paper identified the following potential threat sources and their associated actions as
shown by table one below
Threat source Threat action
Computer criminal System intrusion
Spoofing
Identify theft
Hacker Unauthorized system access
System intrusion
Insiders ( Due to poorly trained personnel and
dishonest or terminated employees)
System bugs
Unauthorized system access
Browsing of personally identifiable information
(Tittel, 2017, p. 79)
Threats to primary assets
Router
There two common threats to any router which are a denial of service attack commonly known
as syn flood and brute force type of attack. Denial of service attack is caused by the exploitation of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SECURITY MANAGEMENT 5
TCP protocol. Here an attacker sends a number of TCP/SYN packet using forged address. The brute force
attack happens when an attacker attempts to guess the router passwords so as to gain unauthorized
access to the router. This type of threat is used in conjunction with automated guessing tools and
dictionary methods so as to crack passwords (Carnaghan, 2018).
Switch
CDP manipulation is one of threat against switches. The CDP packets are enabled by default in
all switched and transmitted in clear text which in turn allows an attacker to analyze the packets thus
gaining access of the information about the switch. Another form of attacks is MAC flooding the CAM
table with the MAC address. This type of threat leads to the switch operating as a hub thus giving the
attacker that chance to sniff all the organization traffic on the segment. Another type of attack is the
spoofing or what is widely known as DHCP or ARP attacks and STP attacks. This type of threat to the
switch enables an attacker to gain the IP address of the default gateway (Mokadem, 2018, p. 57).
Firewall
One of firewall threat is insider attacks. When a threat originates from inside or from within one
network then the firewall can’t do anything if the organization has not partitioned their assets. Another
threat is missed security patches; this arises when firewall software is not managed properly. Other
threats are lack of deep packet inspection and configuration mistakes (Byrne, 2017, p. 49).
Computer threats
Some of the computer threats which the company can experience are malware, computer
viruses like Trojan horse. In addition, the organization is prone to rogue security software, computer
worm, and malicious spyware. Also, the organization is prone to botnet type of threat. A botnet is a type
of computer threat where a computer connected to a wide area network has been compromised by a
hacker using malware. Other computer threats are rootkits, this is a collection of tools which is used to
obtain computer administrators (Comer, 2018, p. 109).
Server threats
Some of the common types of server threats are URL interpretation attack. This is a common
threat targeted to organization web servers. Another common type of threat to when servers is the
input validation attack where the web server executes a code injected by the attacker to the database
server and to the web server. Another common type of attack is the buffer overflow attack. In here the
attacker feeds executable commands in the stack (Foreman, 2017, p. 117). Another common threat is
the impersonation attack, this attack is also known as IP spoofing where an attacker pretends to have
access to the web server. Another common type of attack is a password-based attack. This is an
authentication system for an organization server. This is as a result of weak passwords. Other types of
attacks are session hijacking and source code disclosure. Session hijacking is a type of attack to a
database server (Kenny, 2009, p. 45).
Threats to secondary assets
Database store assets
One of the threats to the organization database is SQL injections. This is a type of threat, an
attacker sends unauthorized queries to the organizational database. Other threats are a denial of Service
TCP protocol. Here an attacker sends a number of TCP/SYN packet using forged address. The brute force
attack happens when an attacker attempts to guess the router passwords so as to gain unauthorized
access to the router. This type of threat is used in conjunction with automated guessing tools and
dictionary methods so as to crack passwords (Carnaghan, 2018).
Switch
CDP manipulation is one of threat against switches. The CDP packets are enabled by default in
all switched and transmitted in clear text which in turn allows an attacker to analyze the packets thus
gaining access of the information about the switch. Another form of attacks is MAC flooding the CAM
table with the MAC address. This type of threat leads to the switch operating as a hub thus giving the
attacker that chance to sniff all the organization traffic on the segment. Another type of attack is the
spoofing or what is widely known as DHCP or ARP attacks and STP attacks. This type of threat to the
switch enables an attacker to gain the IP address of the default gateway (Mokadem, 2018, p. 57).
Firewall
One of firewall threat is insider attacks. When a threat originates from inside or from within one
network then the firewall can’t do anything if the organization has not partitioned their assets. Another
threat is missed security patches; this arises when firewall software is not managed properly. Other
threats are lack of deep packet inspection and configuration mistakes (Byrne, 2017, p. 49).
Computer threats
Some of the computer threats which the company can experience are malware, computer
viruses like Trojan horse. In addition, the organization is prone to rogue security software, computer
worm, and malicious spyware. Also, the organization is prone to botnet type of threat. A botnet is a type
of computer threat where a computer connected to a wide area network has been compromised by a
hacker using malware. Other computer threats are rootkits, this is a collection of tools which is used to
obtain computer administrators (Comer, 2018, p. 109).
Server threats
Some of the common types of server threats are URL interpretation attack. This is a common
threat targeted to organization web servers. Another common type of threat to when servers is the
input validation attack where the web server executes a code injected by the attacker to the database
server and to the web server. Another common type of attack is the buffer overflow attack. In here the
attacker feeds executable commands in the stack (Foreman, 2017, p. 117). Another common threat is
the impersonation attack, this attack is also known as IP spoofing where an attacker pretends to have
access to the web server. Another common type of attack is a password-based attack. This is an
authentication system for an organization server. This is as a result of weak passwords. Other types of
attacks are session hijacking and source code disclosure. Session hijacking is a type of attack to a
database server (Kenny, 2009, p. 45).
Threats to secondary assets
Database store assets
One of the threats to the organization database is SQL injections. This is a type of threat, an
attacker sends unauthorized queries to the organizational database. Other threats are a denial of Service
INFORMATION SECURITY MANAGEMENT 6
threat some of the common types of these threats are data corruption, resource consumption, and data
corruption. Other common threats are weak authentication and exposure of backed-up data (Calder &
Watkins, 2016, p. 89).
Information assets
Data leaks are one of the information asset threat. This is done at the back end of the office.
Another security threat is abusing database features. Over the past five years, most of the database
exploits have been as a result of misuse of standard database feature. Example, an attacker can gain
access via legitimate credentials before forcing the database service to run arbitrary code. Other threats
are lack of segregation and hopscotch. Also, SQL injection is another common attack method which
remains a critical issue in organizations (Microsoft, 2011, p. 89).
Vulnerabilities
Table one below is a vulnerability statement
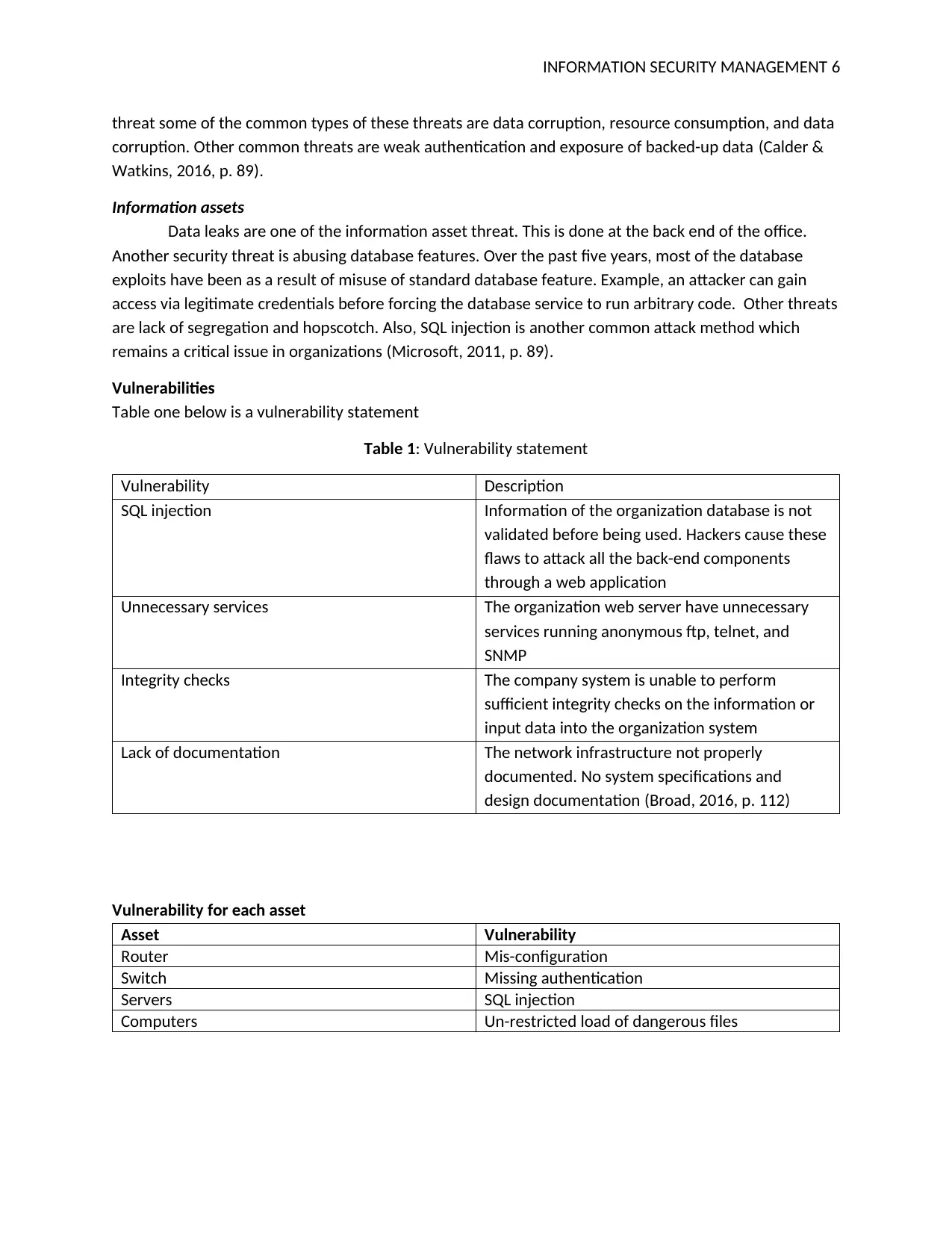
Table 1: Vulnerability statement
Vulnerability Description
SQL injection Information of the organization database is not
validated before being used. Hackers cause these
flaws to attack all the back-end components
through a web application
Unnecessary services The organization web server have unnecessary
services running anonymous ftp, telnet, and
SNMP
Integrity checks The company system is unable to perform
sufficient integrity checks on the information or
input data into the organization system
Lack of documentation The network infrastructure not properly
documented. No system specifications and
design documentation (Broad, 2016, p. 112)
Vulnerability for each asset
Asset Vulnerability
Router Mis-configuration
Switch Missing authentication
Servers SQL injection
Computers Un-restricted load of dangerous files
threat some of the common types of these threats are data corruption, resource consumption, and data
corruption. Other common threats are weak authentication and exposure of backed-up data (Calder &
Watkins, 2016, p. 89).
Information assets
Data leaks are one of the information asset threat. This is done at the back end of the office.
Another security threat is abusing database features. Over the past five years, most of the database
exploits have been as a result of misuse of standard database feature. Example, an attacker can gain
access via legitimate credentials before forcing the database service to run arbitrary code. Other threats
are lack of segregation and hopscotch. Also, SQL injection is another common attack method which
remains a critical issue in organizations (Microsoft, 2011, p. 89).
Vulnerabilities
Table one below is a vulnerability statement
Table 1: Vulnerability statement
Vulnerability Description
SQL injection Information of the organization database is not
validated before being used. Hackers cause these
flaws to attack all the back-end components
through a web application
Unnecessary services The organization web server have unnecessary
services running anonymous ftp, telnet, and
SNMP
Integrity checks The company system is unable to perform
sufficient integrity checks on the information or
input data into the organization system
Lack of documentation The network infrastructure not properly
documented. No system specifications and
design documentation (Broad, 2016, p. 112)
Vulnerability for each asset
Asset Vulnerability
Router Mis-configuration
Switch Missing authentication
Servers SQL injection
Computers Un-restricted load of dangerous files
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
INFORMATION SECURITY MANAGEMENT 7
Likelihood level computation
To identify the likelihood level of computation one has to first identify organization users. Some
of the users of the organization network are estate agents, lawyers, staff database, vendor-buyer, and IT
personnel. Some of the threat sources are as shown below
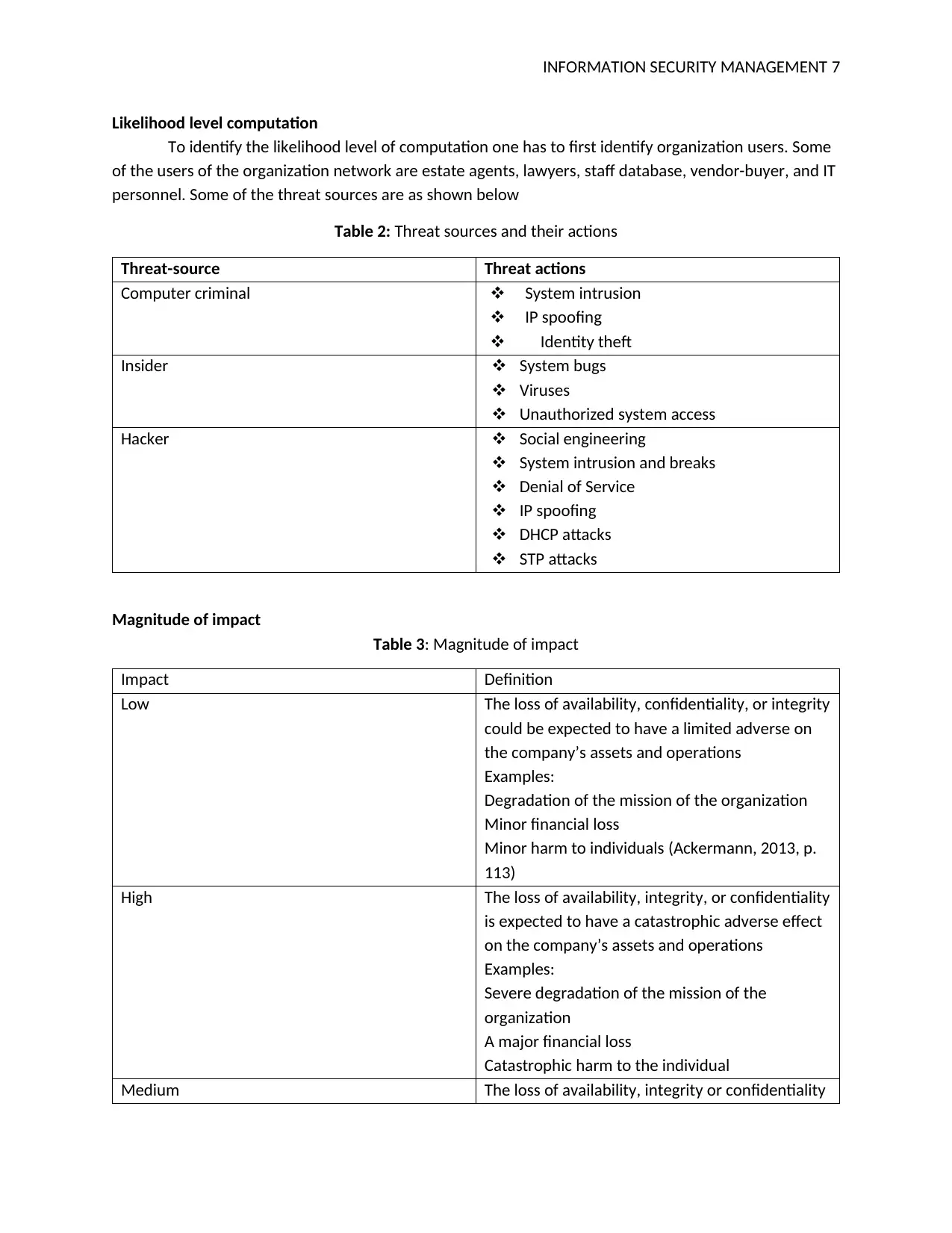
Table 2: Threat sources and their actions
Threat-source Threat actions
Computer criminal System intrusion
IP spoofing
Identity theft
Insider System bugs
Viruses
Unauthorized system access
Hacker Social engineering
System intrusion and breaks
Denial of Service
IP spoofing
DHCP attacks
STP attacks
Magnitude of impact
Table 3: Magnitude of impact
Impact Definition
Low The loss of availability, confidentiality, or integrity
could be expected to have a limited adverse on
the company’s assets and operations
Examples:
Degradation of the mission of the organization
Minor financial loss
Minor harm to individuals (Ackermann, 2013, p.
113)
High The loss of availability, integrity, or confidentiality
is expected to have a catastrophic adverse effect
on the company’s assets and operations
Examples:
Severe degradation of the mission of the
organization
A major financial loss
Catastrophic harm to the individual
Medium The loss of availability, integrity or confidentiality
Likelihood level computation
To identify the likelihood level of computation one has to first identify organization users. Some
of the users of the organization network are estate agents, lawyers, staff database, vendor-buyer, and IT
personnel. Some of the threat sources are as shown below
Table 2: Threat sources and their actions
Threat-source Threat actions
Computer criminal System intrusion
IP spoofing
Identity theft
Insider System bugs
Viruses
Unauthorized system access
Hacker Social engineering
System intrusion and breaks
Denial of Service
IP spoofing
DHCP attacks
STP attacks
Magnitude of impact
Table 3: Magnitude of impact
Impact Definition
Low The loss of availability, confidentiality, or integrity
could be expected to have a limited adverse on
the company’s assets and operations
Examples:
Degradation of the mission of the organization
Minor financial loss
Minor harm to individuals (Ackermann, 2013, p.
113)
High The loss of availability, integrity, or confidentiality
is expected to have a catastrophic adverse effect
on the company’s assets and operations
Examples:
Severe degradation of the mission of the
organization
A major financial loss
Catastrophic harm to the individual
Medium The loss of availability, integrity or confidentiality
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INFORMATION SECURITY MANAGEMENT 8
is expected to have an adverse effect on the
operations of the company, individuals and
company’s assets.
Example
Is a significant financial loss
Significant damage to the company assets
(Snedaker. & Cunningham, 2015, p. 213)
Risk matrix table
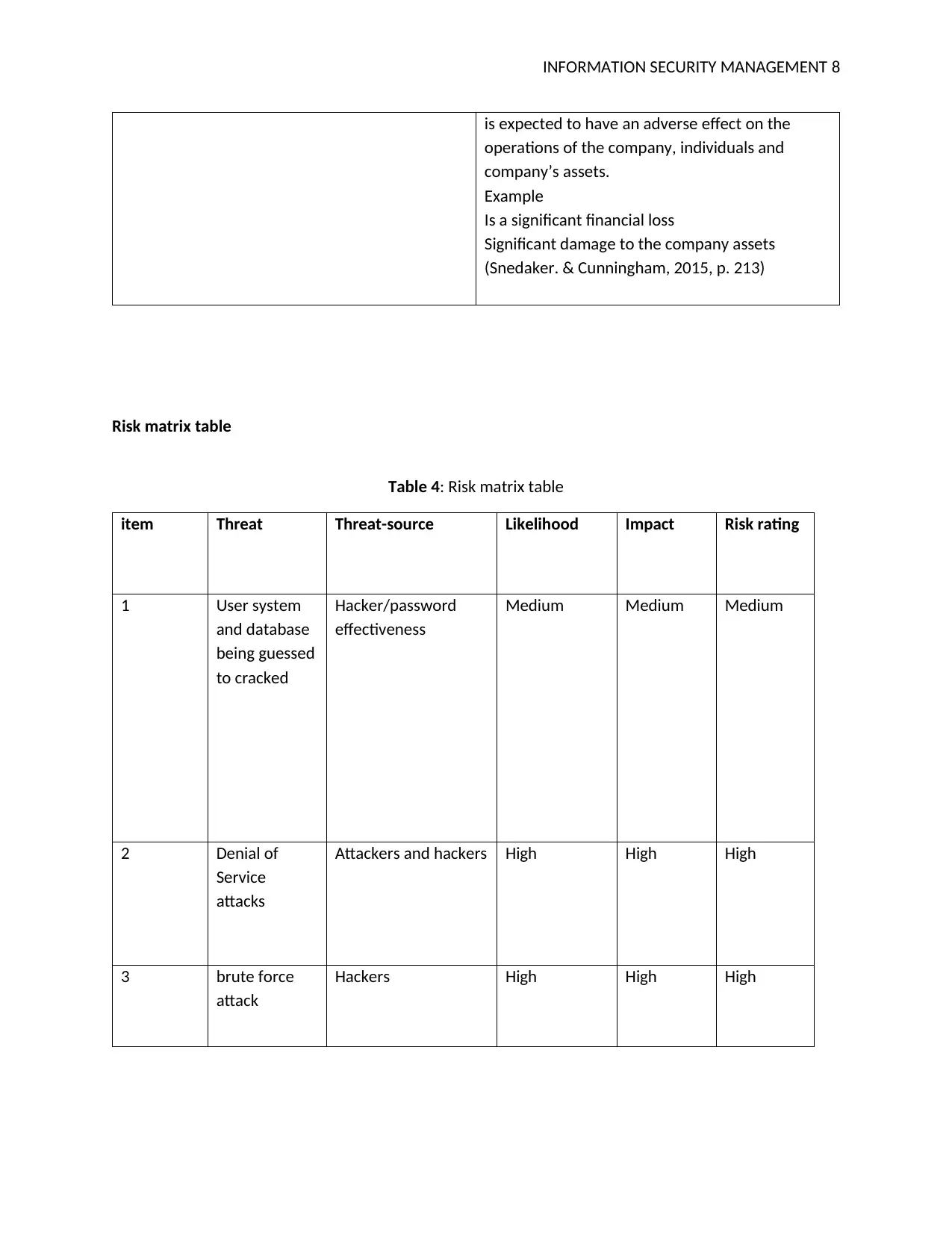
Table 4: Risk matrix table
item Threat Threat-source Likelihood Impact Risk rating
1 User system
and database
being guessed
to cracked
Hacker/password
effectiveness
Medium Medium Medium
2 Denial of
Service
attacks
Attackers and hackers High High High
3 brute force
attack
Hackers High High High
is expected to have an adverse effect on the
operations of the company, individuals and
company’s assets.
Example
Is a significant financial loss
Significant damage to the company assets
(Snedaker. & Cunningham, 2015, p. 213)
Risk matrix table
Table 4: Risk matrix table
item Threat Threat-source Likelihood Impact Risk rating
1 User system
and database
being guessed
to cracked
Hacker/password
effectiveness
Medium Medium Medium
2 Denial of
Service
attacks
Attackers and hackers High High High
3 brute force
attack
Hackers High High High
INFORMATION SECURITY MANAGEMENT 9
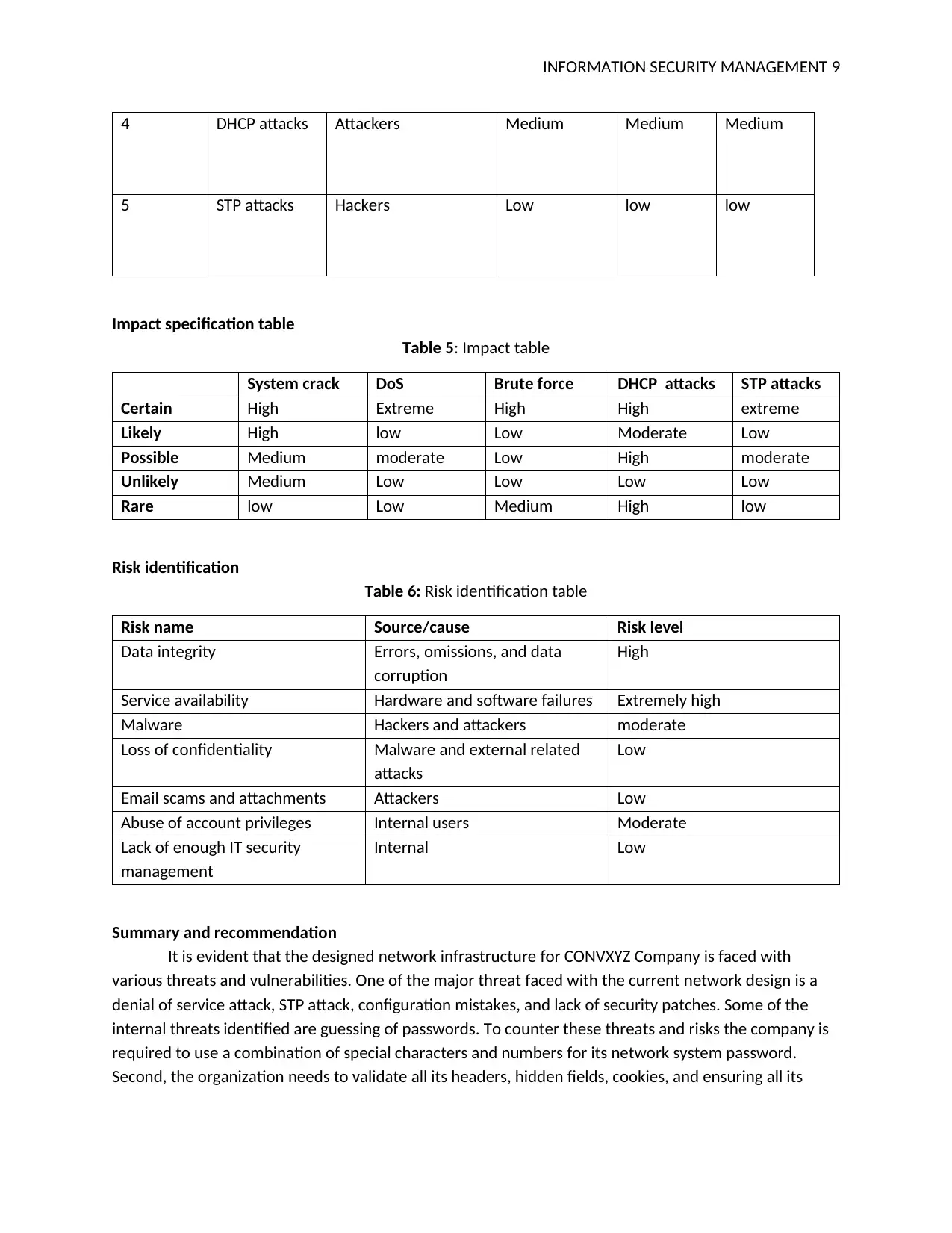
4 DHCP attacks Attackers Medium Medium Medium
5 STP attacks Hackers Low low low
Impact specification table
Table 5: Impact table
System crack DoS Brute force DHCP attacks STP attacks
Certain High Extreme High High extreme
Likely High low Low Moderate Low
Possible Medium moderate Low High moderate
Unlikely Medium Low Low Low Low
Rare low Low Medium High low
Risk identification
Table 6: Risk identification table
Risk name Source/cause Risk level
Data integrity Errors, omissions, and data
corruption
High
Service availability Hardware and software failures Extremely high
Malware Hackers and attackers moderate
Loss of confidentiality Malware and external related
attacks
Low
Email scams and attachments Attackers Low
Abuse of account privileges Internal users Moderate
Lack of enough IT security
management
Internal Low
Summary and recommendation
It is evident that the designed network infrastructure for CONVXYZ Company is faced with
various threats and vulnerabilities. One of the major threat faced with the current network design is a
denial of service attack, STP attack, configuration mistakes, and lack of security patches. Some of the
internal threats identified are guessing of passwords. To counter these threats and risks the company is
required to use a combination of special characters and numbers for its network system password.
Second, the organization needs to validate all its headers, hidden fields, cookies, and ensuring all its
4 DHCP attacks Attackers Medium Medium Medium
5 STP attacks Hackers Low low low
Impact specification table
Table 5: Impact table
System crack DoS Brute force DHCP attacks STP attacks
Certain High Extreme High High extreme
Likely High low Low Moderate Low
Possible Medium moderate Low High moderate
Unlikely Medium Low Low Low Low
Rare low Low Medium High low
Risk identification
Table 6: Risk identification table
Risk name Source/cause Risk level
Data integrity Errors, omissions, and data
corruption
High
Service availability Hardware and software failures Extremely high
Malware Hackers and attackers moderate
Loss of confidentiality Malware and external related
attacks
Low
Email scams and attachments Attackers Low
Abuse of account privileges Internal users Moderate
Lack of enough IT security
management
Internal Low
Summary and recommendation
It is evident that the designed network infrastructure for CONVXYZ Company is faced with
various threats and vulnerabilities. One of the major threat faced with the current network design is a
denial of service attack, STP attack, configuration mistakes, and lack of security patches. Some of the
internal threats identified are guessing of passwords. To counter these threats and risks the company is
required to use a combination of special characters and numbers for its network system password.
Second, the organization needs to validate all its headers, hidden fields, cookies, and ensuring all its
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION SECURITY MANAGEMENT 10
parameters are validated before they are used. To avoid data leakage, an organization needs to use TLS
or SSL encrypted communications (Rohmeyer & Bayuk, 2013, p. 118).
References
Ackermann, T., 2013. IT security risk management: perceived IT security... by Tobias Ackermann. 3rd ed.
Chicago: Springer Gabler Press.
Blanc, R. P. & Cotton, I. W., 2014. Computer networking by Robert P Blanc. 2nd ed. Amsterdam: RTU
Publishing House.
Broad, J., 2016. Risk management framework: a lab-based approach... by James Broad. 1st ed.
Amsterdam: Syngress Press.
Byrne, P., 2017. Computer networking by Paxton Byrne. 3rd ed. New York: Larsen and Keller Press.
Calder, A. & Watkins, S. G., 2016. Information security risk management for ISO27001/ISO27002 by Alan
Calder. 2nd ed. Chicago: Cambridgeshire Press.
Carnaghan, I., 2018. Two Common Router Security Threats. [Online]
Available at: https://www.carnaghan.com/two-common-router-security-threats/
[Accessed 17th April 2019].
Comer, D., 2018. The Internet book: everything you need to know about computer networking and how
the Internet works. 3rd ed. Boca Raton: CRC Press.
CSGTeam, 2018. The Advantages of Performing Cybersecurity Risk Assessments. [Online]
Available at: https://www.championsg.com/advantages-performing-cybersecurity-risk-assessments
[Accessed 5th July 2018].
Foreman, P., 2017. Vulnerability management. 4th ed. New York: CRS press.
parameters are validated before they are used. To avoid data leakage, an organization needs to use TLS
or SSL encrypted communications (Rohmeyer & Bayuk, 2013, p. 118).
References
Ackermann, T., 2013. IT security risk management: perceived IT security... by Tobias Ackermann. 3rd ed.
Chicago: Springer Gabler Press.
Blanc, R. P. & Cotton, I. W., 2014. Computer networking by Robert P Blanc. 2nd ed. Amsterdam: RTU
Publishing House.
Broad, J., 2016. Risk management framework: a lab-based approach... by James Broad. 1st ed.
Amsterdam: Syngress Press.
Byrne, P., 2017. Computer networking by Paxton Byrne. 3rd ed. New York: Larsen and Keller Press.
Calder, A. & Watkins, S. G., 2016. Information security risk management for ISO27001/ISO27002 by Alan
Calder. 2nd ed. Chicago: Cambridgeshire Press.
Carnaghan, I., 2018. Two Common Router Security Threats. [Online]
Available at: https://www.carnaghan.com/two-common-router-security-threats/
[Accessed 17th April 2019].
Comer, D., 2018. The Internet book: everything you need to know about computer networking and how
the Internet works. 3rd ed. Boca Raton: CRC Press.
CSGTeam, 2018. The Advantages of Performing Cybersecurity Risk Assessments. [Online]
Available at: https://www.championsg.com/advantages-performing-cybersecurity-risk-assessments
[Accessed 5th July 2018].
Foreman, P., 2017. Vulnerability management. 4th ed. New York: CRS press.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SECURITY MANAGEMENT 11
Gossman, D., 2009. HAZOP - Pros and Cons. [Online]
Available at: https://gcisolutions.com/gcitn0309.html
[Accessed 17th April 2019].
Kenny, L., 2009. NetworkingEssentials. 3rd ed. s.l.:Pearson Australia.
Kurose, J. F. & Ross, K. W., 2009. Computer networking: a top-down approach. 1st ed. Chicago: Boston
Pearson.
Lee, J., 2005. Networking Essentials. 2nd ed. New York: Springer.
Matthews, J., 2007. Computer Networking : Internet protocols in action. 1st edition ed. New York:
Springer.
Microsoft, 2011. Networking essentials. 4th ed. Chicago: Microsoft Press.
Mokadem, H. E., 2018. Switch Attacks andCountermeasures. Network attack, II(1), pp. 39-47.
Rohmeyer, P. & Bayuk, J. L., 2013. Financial cybersecurity risk management : leadership... by Paul
Rohmeyer. 1st ed. Chicago: Springer Press.
Snedaker., S. & Cunningham, B., 2015. The best damn IT security management book period by Susan
Snedaker.. 4th ed. Burlington city: Syngress Press.
Tittel, E., 2017. Computer networking by Ed Tittel. 3rd ed. New York: Springer.
Vasudevan, S. K., 2017. Computer networking. by Shriram K Vasudevan. 1st ed. New York: Oxford Press.
Gossman, D., 2009. HAZOP - Pros and Cons. [Online]
Available at: https://gcisolutions.com/gcitn0309.html
[Accessed 17th April 2019].
Kenny, L., 2009. NetworkingEssentials. 3rd ed. s.l.:Pearson Australia.
Kurose, J. F. & Ross, K. W., 2009. Computer networking: a top-down approach. 1st ed. Chicago: Boston
Pearson.
Lee, J., 2005. Networking Essentials. 2nd ed. New York: Springer.
Matthews, J., 2007. Computer Networking : Internet protocols in action. 1st edition ed. New York:
Springer.
Microsoft, 2011. Networking essentials. 4th ed. Chicago: Microsoft Press.
Mokadem, H. E., 2018. Switch Attacks andCountermeasures. Network attack, II(1), pp. 39-47.
Rohmeyer, P. & Bayuk, J. L., 2013. Financial cybersecurity risk management : leadership... by Paul
Rohmeyer. 1st ed. Chicago: Springer Press.
Snedaker., S. & Cunningham, B., 2015. The best damn IT security management book period by Susan
Snedaker.. 4th ed. Burlington city: Syngress Press.
Tittel, E., 2017. Computer networking by Ed Tittel. 3rd ed. New York: Springer.
Vasudevan, S. K., 2017. Computer networking. by Shriram K Vasudevan. 1st ed. New York: Oxford Press.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





