Information Security Assessment: Analysis and Solutions
VerifiedAdded on 2021/06/15
|8
|2250
|44
Homework Assignment
AI Summary
This document presents a detailed information security assessment, addressing critical aspects such as the CIA triad (Confidentiality, Integrity, and Availability) in the context of ATM systems, exploring the importance of data security, and providing examples of how each attribute is applied. It further analyzes the number of attempts a thief might make to guess a PIN, considering a scenario where some keys are broken. The assessment also delves into the working principles, advantages, and vulnerabilities of biometric authentication, including discussions on false positives and false negatives. The assignment concludes with an examination of decryption techniques for ciphertext encrypted using transposition, including letter frequency and trigram analysis, and provides a step-by-step decryption process for a given encrypted text.

Running head: INFORMATION SECURITY
Information security
Assessment No
Assessment Title
Student Name & ID
Subject Name and Code
Student Email Address
Information security
Assessment No
Assessment Title
Student Name & ID
Subject Name and Code
Student Email Address
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY
Table of Contents
Answer to Question 1.................................................................................................................2
Answer to Question 2.................................................................................................................3
Answer to Question 3.................................................................................................................3
Answer to Question 4.................................................................................................................3
Answer to Question 5.................................................................................................................4
References..................................................................................................................................7
Table of Contents
Answer to Question 1.................................................................................................................2
Answer to Question 2.................................................................................................................3
Answer to Question 3.................................................................................................................3
Answer to Question 4.................................................................................................................3
Answer to Question 5.................................................................................................................4
References..................................................................................................................................7

2INFORMATION SECURITY
Answer to Question 1
The CIA (Confidentiality, Integrity, Availability) triad is mainly important for
security of the information transmitted from different servers and user’s devices or end points
(Beng et al., 2018). For the Confidentiality it is about restricting the users who may have
access to some specific information or data.
For integrity, it is about the administration of the modification of the transmitted
information through any medium. Finally, the availability of the data is about making it sure
that authorised users can access the information at any time without any difficulties.
Following are the examples of the above triad from the perspective of the ATM
information system and how these attributes are helpful for the security of the data of such
system.
Example of confidentiality
For the ATM system, the confidentiality of the of data it is related to securing the
access of user data only to the authorized users. For the ATM information system, the
customer detail, PIN of the used ATM card to withdraw money from the ATM system should
be protected from unauthorised access to the user data. In case any unauthorised user have
access to the data, this may lead to the adverse situations for the customer (Rawat &
Bajracharya, 2015). One of such technique is Eavesdropping to get unauthorised access to
the data transmitted through the server and the ATM systems. Therefore, in order to secure
the confidentiality of the information it is suggested to use encryption technique and SSL for
data transmission mediums so that even though the data is intercepted by the hackers or
attackers they would not be able to get the decrypted data. As the lack of confidentiality of
the data an lead to severe results thus it is rated with “High” degree of importance.
Example of Integrity
The integrity of the data in the information system is another important aspect which
needs to protected. Integrity of the data ensure that the data is not modified by any
unauthorized user or hacker.
Unauthorized modification of the data can adversely impact on the users of the ATM
as well as on the financial institutions who maintains it. For the information system the data
is valuable if and only if the data is correct. As an example it can be said that, by the
unauthorized modification of data transmitted from the ATM, it can result into financial loss
of the customers (Rawat & Bajracharya, 2015). As use of the simple encryption techniques
can help in protecting the integrity of data, thus it is rated with “Moderate” degree of
importance.
Example of Availability
Availability of data is about making sure that, data from the information system is
available to the authorized users whenever they need it. This availability of data can be
interrupted through the DoS, Man in the Middle Attacks (Beng et al., 2018). Thus routine
offline backups can be very helpful in ensuring the availability of data to the users. As lack
of availability of the data will lead to the unavailability of all the services from the ATM
system, thus it can be marked with “Moderate” degree of importance.
Answer to Question 1
The CIA (Confidentiality, Integrity, Availability) triad is mainly important for
security of the information transmitted from different servers and user’s devices or end points
(Beng et al., 2018). For the Confidentiality it is about restricting the users who may have
access to some specific information or data.
For integrity, it is about the administration of the modification of the transmitted
information through any medium. Finally, the availability of the data is about making it sure
that authorised users can access the information at any time without any difficulties.
Following are the examples of the above triad from the perspective of the ATM
information system and how these attributes are helpful for the security of the data of such
system.
Example of confidentiality
For the ATM system, the confidentiality of the of data it is related to securing the
access of user data only to the authorized users. For the ATM information system, the
customer detail, PIN of the used ATM card to withdraw money from the ATM system should
be protected from unauthorised access to the user data. In case any unauthorised user have
access to the data, this may lead to the adverse situations for the customer (Rawat &
Bajracharya, 2015). One of such technique is Eavesdropping to get unauthorised access to
the data transmitted through the server and the ATM systems. Therefore, in order to secure
the confidentiality of the information it is suggested to use encryption technique and SSL for
data transmission mediums so that even though the data is intercepted by the hackers or
attackers they would not be able to get the decrypted data. As the lack of confidentiality of
the data an lead to severe results thus it is rated with “High” degree of importance.
Example of Integrity
The integrity of the data in the information system is another important aspect which
needs to protected. Integrity of the data ensure that the data is not modified by any
unauthorized user or hacker.
Unauthorized modification of the data can adversely impact on the users of the ATM
as well as on the financial institutions who maintains it. For the information system the data
is valuable if and only if the data is correct. As an example it can be said that, by the
unauthorized modification of data transmitted from the ATM, it can result into financial loss
of the customers (Rawat & Bajracharya, 2015). As use of the simple encryption techniques
can help in protecting the integrity of data, thus it is rated with “Moderate” degree of
importance.
Example of Availability
Availability of data is about making sure that, data from the information system is
available to the authorized users whenever they need it. This availability of data can be
interrupted through the DoS, Man in the Middle Attacks (Beng et al., 2018). Thus routine
offline backups can be very helpful in ensuring the availability of data to the users. As lack
of availability of the data will lead to the unavailability of all the services from the ATM
system, thus it can be marked with “Moderate” degree of importance.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY
Answer to Question 2
For the given scenario, it is given that the thief was successful in breaking five of the
total ten keys on the board of the ATM. Now, as the customer was able to enter his/her pin
using the remaining five keys thus the users PIN is combination of 4 keys out of the
remaining five keys.
Using the concept of permutation and combination we can state that the number of
efforts remains for the thief to find the customers pin is given by following formula,
5P4 = 5! / (5-4)!
=120
Thus the number of attempts that can be used by the thief is, 120 times.
Answer to Question 3
The main working principle of Biometrics can be stated as, comparison of two data
set one is previously inserted data in the device and another one inserted by the different
user’s every time they want to enter the secure premises. In order to grant access for a user
the Biometric does not requires an exactly identical for the above mentioned two data sets.
This matching technique is used as due to sweat or water in the fingertips may disrupt the
whole process of identification (Beng et al., 2018). Errors in the processing of the biometric
elements consist of a long chain of processing steps which are considered as imperfect by the
researchers. For each step the processing chain introduces a slight degree of uncertainty for
identification. Uncertainty in this process is inescapable if the first processing step too. As the
body part used for biometric can never appear exactly same as it was appeared when
registered at first. Pressure and angle of a finger on a scanner. This interruption includes
false Positive; where an invalid user is identified as a valid user and given access to the
restricted data or premises. Another issue related to this is false Negative. In case of false
negative, a valid user is rejected from the biometric authentication process.
Biometrics are hackable: On the other hand, in case of iris scanning and voice
recognition it can be said that, they can have hacked using the pictures of the Iris and voice
samples. From the example of hacking of German minister Ursula von der Leyen
finger prints, it is evident that the fingerprints and iris biometrics can be
easily hacked by using their high definition images.
Vulnerabilities in the software’s used for authentication:
security researchers also found that, most of the software’s used s for the
biometric devices contains different backdoors which can be exploited by the
hackers to extract the stored information about the users.
Lack of recovery options: even though the biometric elements are
unique for everyone but it does not make sure that these are secure
passwords (Eberz et al., 2017). Unfortunately, if any user lost their fingers, eyes
then it becomes impossible for them to access the secured data or premises
as they longer possess their passwords. In this scenario this password is also
not recoverable which leads to more complexity.
Answer to Question 2
For the given scenario, it is given that the thief was successful in breaking five of the
total ten keys on the board of the ATM. Now, as the customer was able to enter his/her pin
using the remaining five keys thus the users PIN is combination of 4 keys out of the
remaining five keys.
Using the concept of permutation and combination we can state that the number of
efforts remains for the thief to find the customers pin is given by following formula,
5P4 = 5! / (5-4)!
=120
Thus the number of attempts that can be used by the thief is, 120 times.
Answer to Question 3
The main working principle of Biometrics can be stated as, comparison of two data
set one is previously inserted data in the device and another one inserted by the different
user’s every time they want to enter the secure premises. In order to grant access for a user
the Biometric does not requires an exactly identical for the above mentioned two data sets.
This matching technique is used as due to sweat or water in the fingertips may disrupt the
whole process of identification (Beng et al., 2018). Errors in the processing of the biometric
elements consist of a long chain of processing steps which are considered as imperfect by the
researchers. For each step the processing chain introduces a slight degree of uncertainty for
identification. Uncertainty in this process is inescapable if the first processing step too. As the
body part used for biometric can never appear exactly same as it was appeared when
registered at first. Pressure and angle of a finger on a scanner. This interruption includes
false Positive; where an invalid user is identified as a valid user and given access to the
restricted data or premises. Another issue related to this is false Negative. In case of false
negative, a valid user is rejected from the biometric authentication process.
Biometrics are hackable: On the other hand, in case of iris scanning and voice
recognition it can be said that, they can have hacked using the pictures of the Iris and voice
samples. From the example of hacking of German minister Ursula von der Leyen
finger prints, it is evident that the fingerprints and iris biometrics can be
easily hacked by using their high definition images.
Vulnerabilities in the software’s used for authentication:
security researchers also found that, most of the software’s used s for the
biometric devices contains different backdoors which can be exploited by the
hackers to extract the stored information about the users.
Lack of recovery options: even though the biometric elements are
unique for everyone but it does not make sure that these are secure
passwords (Eberz et al., 2017). Unfortunately, if any user lost their fingers, eyes
then it becomes impossible for them to access the secured data or premises
as they longer possess their passwords. In this scenario this password is also
not recoverable which leads to more complexity.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY
Answer to Question 4
For biometric authentication process, there are two factors that are used to measure
the performance and efficiency of the biometric devices. These are, false positive and false
negative. False positive identification happens in case the biometric system mistakenly finds
a match for an invalid user’s fingerprint entry which is not enrolled previously in the
biometric system.
On the contrary, false negative identification happens if the biometric system finds no match
or responds with an error for a query fingerprint that is previously registered in the system.
Following are the two scenarios in which the false negatives results into severe results
compared to the results of the false positives which accept the biometric of an unregistered
user as a registered one.
Personal lockers: At present there are personal lockers are available that recognises its
owner using the biometric. In case of any emergency, it is possible that the biometric of the
locker responds with false negative. In any emergency situation there may be some critical
resources in the locker which will be unavailable for its owner due to the False negative
response.
Safety and recovery of IT infrastructure: In every organization where a significant
amount of business processes depends on the IT infrastructure, there the IT resources like
databases, servers are placed inside a restricted premise which is accessible some of the
officials of the organization (Eberz et al., 2017). In case of any failure or attack on the severs,
if the biometric system responds with false negative then the officials would not be able to
isolate the affected servers so that other servers can be used to support the business process.
Answer to Question 5
For any cipher text which is encrypted using the transposition technique then the one
of the easiest and quick way to decrypt the text is the letter frequency count and a Trigram
count. In this technique the at first the frequency of each letter in the given encrypted text.
After this the count of the frequency of triple characters in a sequence is calculated. In this
way, the encrypted text can be decrypted.
The encrypted sentence is given by,
NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
For the decryption of the given string the positional values of the letters will play a
vital role. Which are given by,
A=1,
B=2,
C=3,
D=4,
E=5,
F =6,
G=7,
Answer to Question 4
For biometric authentication process, there are two factors that are used to measure
the performance and efficiency of the biometric devices. These are, false positive and false
negative. False positive identification happens in case the biometric system mistakenly finds
a match for an invalid user’s fingerprint entry which is not enrolled previously in the
biometric system.
On the contrary, false negative identification happens if the biometric system finds no match
or responds with an error for a query fingerprint that is previously registered in the system.
Following are the two scenarios in which the false negatives results into severe results
compared to the results of the false positives which accept the biometric of an unregistered
user as a registered one.
Personal lockers: At present there are personal lockers are available that recognises its
owner using the biometric. In case of any emergency, it is possible that the biometric of the
locker responds with false negative. In any emergency situation there may be some critical
resources in the locker which will be unavailable for its owner due to the False negative
response.
Safety and recovery of IT infrastructure: In every organization where a significant
amount of business processes depends on the IT infrastructure, there the IT resources like
databases, servers are placed inside a restricted premise which is accessible some of the
officials of the organization (Eberz et al., 2017). In case of any failure or attack on the severs,
if the biometric system responds with false negative then the officials would not be able to
isolate the affected servers so that other servers can be used to support the business process.
Answer to Question 5
For any cipher text which is encrypted using the transposition technique then the one
of the easiest and quick way to decrypt the text is the letter frequency count and a Trigram
count. In this technique the at first the frequency of each letter in the given encrypted text.
After this the count of the frequency of triple characters in a sequence is calculated. In this
way, the encrypted text can be decrypted.
The encrypted sentence is given by,
NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
For the decryption of the given string the positional values of the letters will play a
vital role. Which are given by,
A=1,
B=2,
C=3,
D=4,
E=5,
F =6,
G=7,

5INFORMATION SECURITY
H=8,
I =9,
J = 10;
K = 11,
L = 12,
M = 13,
N = 14,
O = 15,
P = 16;
Q = 17,
R = 18,
S = 19,
T = 20;
U = 21,
V = 22,
W = 23,
X = 24,
Y = 25,
Z = 26.
Now for the given string of text, we get the following values for every word,
N=14, T=20, J=10, W=23, K=11, H=8, X=24 K=11;
A=1, M=13, K=11;
W=23, W=23, U=21, J=10, J=10, Y=25, Z=26 T=20, X=24;
M=13, W=23, K=11, X=24, Z=26, K=11 U=21 H=8 E=5;
Now considering the substitution key, 234, we get the transformed sequences as
follows,
N=12 T=17 J=6 W=21 K=8 H=4 X=22 K=8
A=23, M=11, K=8
W=19, W=21, U=18, J=6, J=8, Y=22, Z=22 T=18, X=21
M=9, W=21, K=8, X=20, Z=24, K=8 U=17 H=6 E=2
In this sage now we will apply the principles of decrypting Caesar cipher text, we get
the following sequences,
N T J W K H X K
H=8,
I =9,
J = 10;
K = 11,
L = 12,
M = 13,
N = 14,
O = 15,
P = 16;
Q = 17,
R = 18,
S = 19,
T = 20;
U = 21,
V = 22,
W = 23,
X = 24,
Y = 25,
Z = 26.
Now for the given string of text, we get the following values for every word,
N=14, T=20, J=10, W=23, K=11, H=8, X=24 K=11;
A=1, M=13, K=11;
W=23, W=23, U=21, J=10, J=10, Y=25, Z=26 T=20, X=24;
M=13, W=23, K=11, X=24, Z=26, K=11 U=21 H=8 E=5;
Now considering the substitution key, 234, we get the transformed sequences as
follows,
N=12 T=17 J=6 W=21 K=8 H=4 X=22 K=8
A=23, M=11, K=8
W=19, W=21, U=18, J=6, J=8, Y=22, Z=22 T=18, X=21
M=9, W=21, K=8, X=20, Z=24, K=8 U=17 H=6 E=2
In this sage now we will apply the principles of decrypting Caesar cipher text, we get
the following sequences,
N T J W K H X K
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
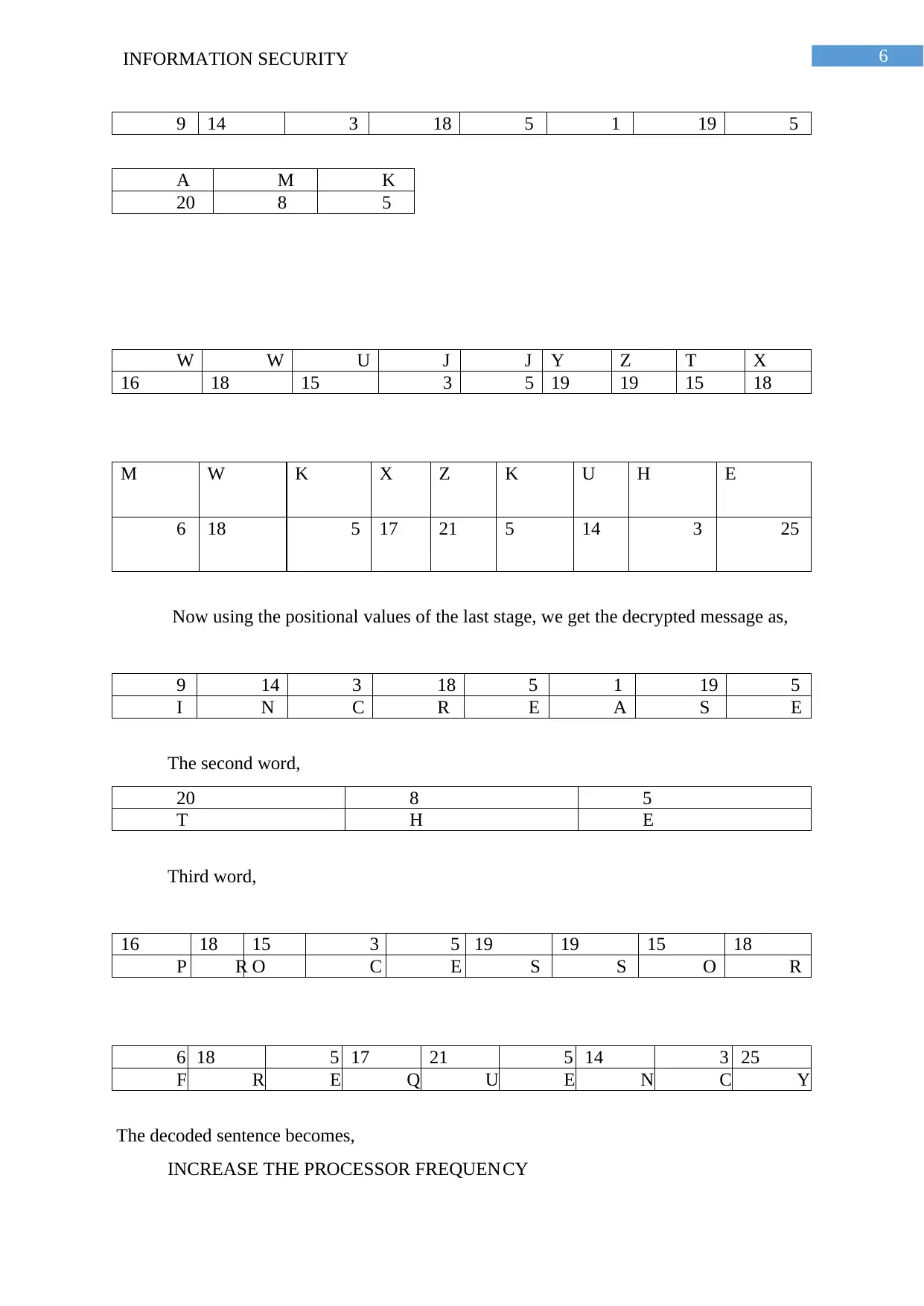
6INFORMATION SECURITY
9 14 3 18 5 1 19 5
A M K
20 8 5
W W U J J Y Z T X
16 18 15 3 5 19 19 15 18
M W K X Z K U H E
6 18 5 17 21 5 14 3 25
Now using the positional values of the last stage, we get the decrypted message as,
9 14 3 18 5 1 19 5
I N C R E A S E
The second word,
20 8 5
T H E
Third word,
16 18 15 3 5 19 19 15 18
P R O C E S S O R
6 18 5 17 21 5 14 3 25
F R E Q U E N C Y
The decoded sentence becomes,
INCREASE THE PROCESSOR FREQUEN CY
9 14 3 18 5 1 19 5
A M K
20 8 5
W W U J J Y Z T X
16 18 15 3 5 19 19 15 18
M W K X Z K U H E
6 18 5 17 21 5 14 3 25
Now using the positional values of the last stage, we get the decrypted message as,
9 14 3 18 5 1 19 5
I N C R E A S E
The second word,
20 8 5
T H E
Third word,
16 18 15 3 5 19 19 15 18
P R O C E S S O R
6 18 5 17 21 5 14 3 25
F R E Q U E N C Y
The decoded sentence becomes,
INCREASE THE PROCESSOR FREQUEN CY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY
References
Beng, T. C., Hijazi, M. H. A., Lim, Y., & Gani, A. (2018). A survey on Proof of
Retrievability for cloud data integrity and availability: Cloud storage state-of-the-art,
issues, solutions and future trends. Journal of Network and Computer Applications.
Eberz, S., Rasmussen, K. B., Lenders, V., & Martinovic, I. (2017, April). Evaluating
behavioral biometrics for continuous authentication: Challenges and metrics.
In Proceedings of the 2017 ACM on Asia Conference on Computer and
Communications Security (pp. 386-399). ACM.
Mohanty, S., Ganguly, M., & Pattnaik, P. K. (2018). CIA Triad for Achieving Accountability
in Cloud Computing Environment.
Purnama, B., & Rohayani, A. H. (2015). A New Modified Caesar Cipher Cryptography
Method with LegibleCiphertext From a Message to Be Encrypted. Procedia
Computer Science, 59, 195-204. Oktaviana, B., & Siahaan, A. P. U. (2016). Three-
Pass Protocol Implementation in Caesar Cipher Classic Cryptography. IOSR Journal
of Computer Engineering (IOSR-JCE), 18(4), 26-29.
Rawat, D. B., & Bajracharya, C. (2015, April). Cyber security for smart grid systems: Status,
challenges and perspectives. In SoutheastCon 2015 (pp. 1-6). IEEE.
References
Beng, T. C., Hijazi, M. H. A., Lim, Y., & Gani, A. (2018). A survey on Proof of
Retrievability for cloud data integrity and availability: Cloud storage state-of-the-art,
issues, solutions and future trends. Journal of Network and Computer Applications.
Eberz, S., Rasmussen, K. B., Lenders, V., & Martinovic, I. (2017, April). Evaluating
behavioral biometrics for continuous authentication: Challenges and metrics.
In Proceedings of the 2017 ACM on Asia Conference on Computer and
Communications Security (pp. 386-399). ACM.
Mohanty, S., Ganguly, M., & Pattnaik, P. K. (2018). CIA Triad for Achieving Accountability
in Cloud Computing Environment.
Purnama, B., & Rohayani, A. H. (2015). A New Modified Caesar Cipher Cryptography
Method with LegibleCiphertext From a Message to Be Encrypted. Procedia
Computer Science, 59, 195-204. Oktaviana, B., & Siahaan, A. P. U. (2016). Three-
Pass Protocol Implementation in Caesar Cipher Classic Cryptography. IOSR Journal
of Computer Engineering (IOSR-JCE), 18(4), 26-29.
Rawat, D. B., & Bajracharya, C. (2015, April). Cyber security for smart grid systems: Status,
challenges and perspectives. In SoutheastCon 2015 (pp. 1-6). IEEE.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





