Information Security Assignment: Session Hacking and Mitigation
VerifiedAdded on 2020/03/04
|17
|1220
|277
Homework Assignment
AI Summary
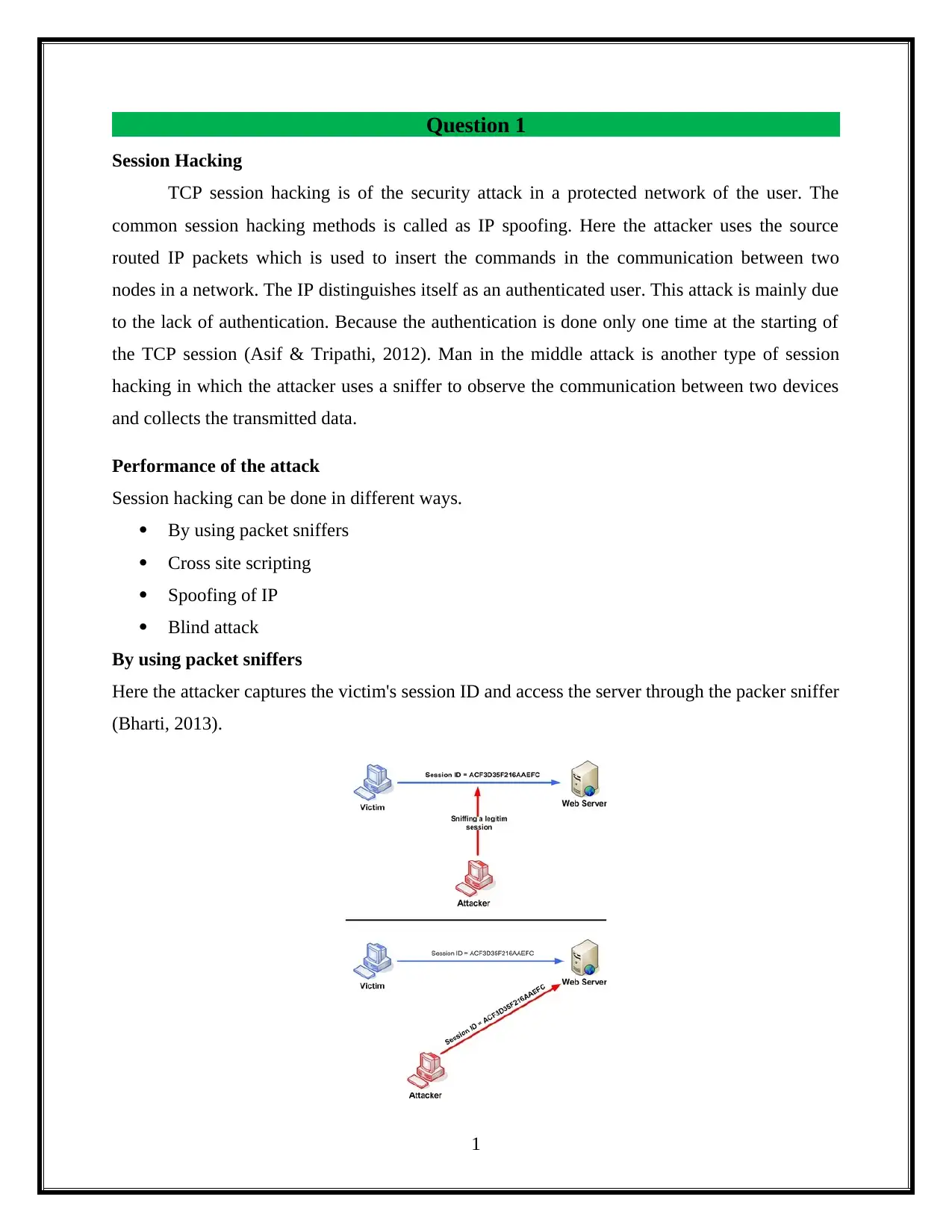
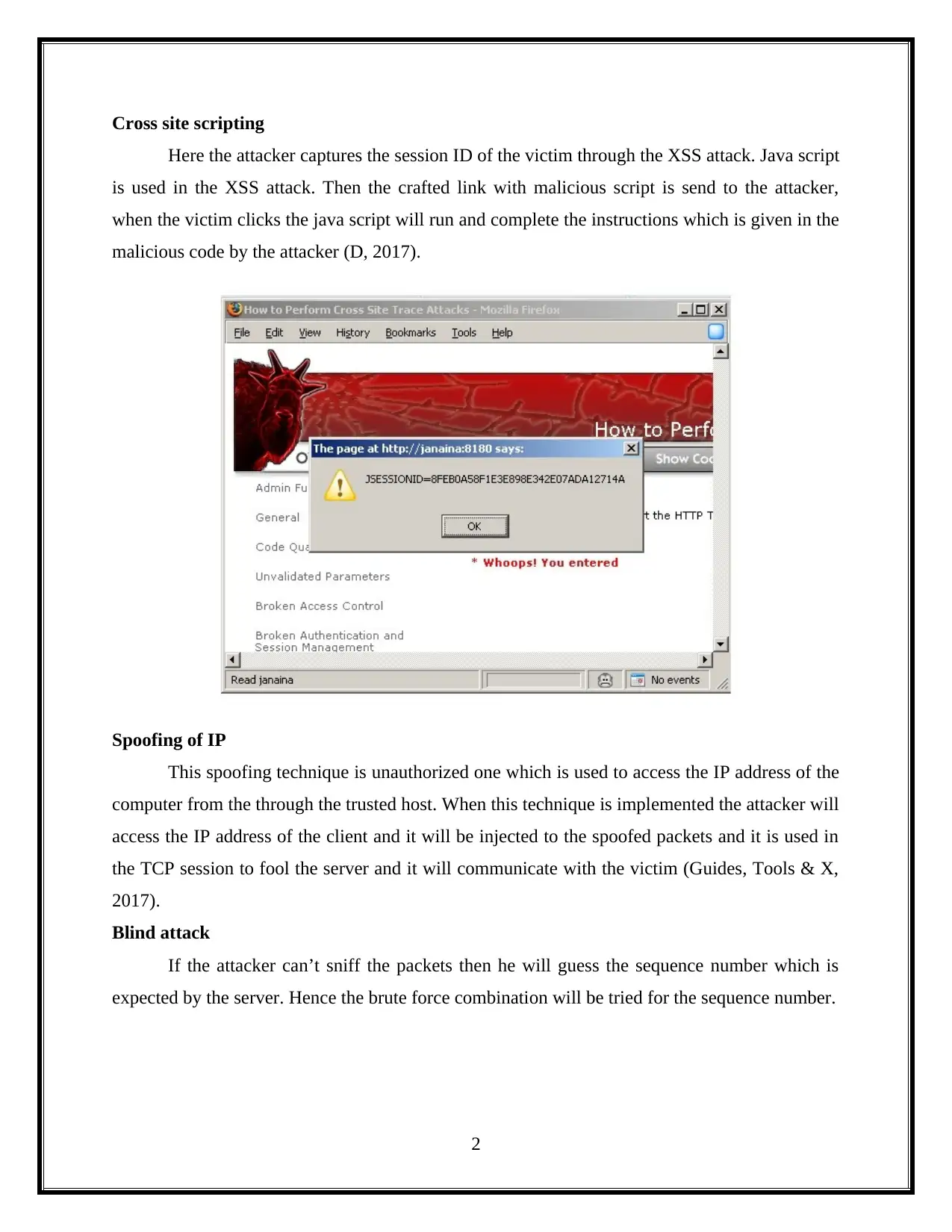
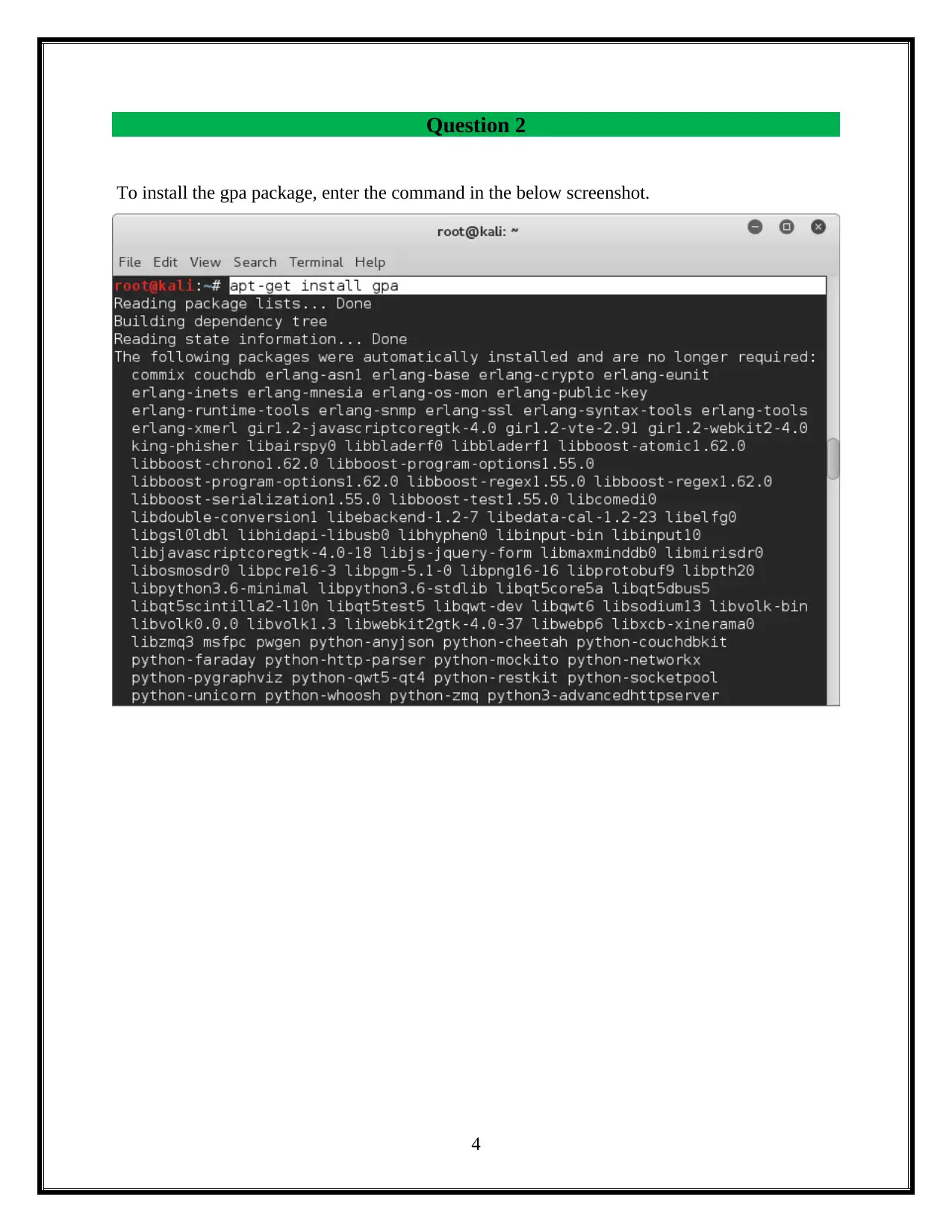
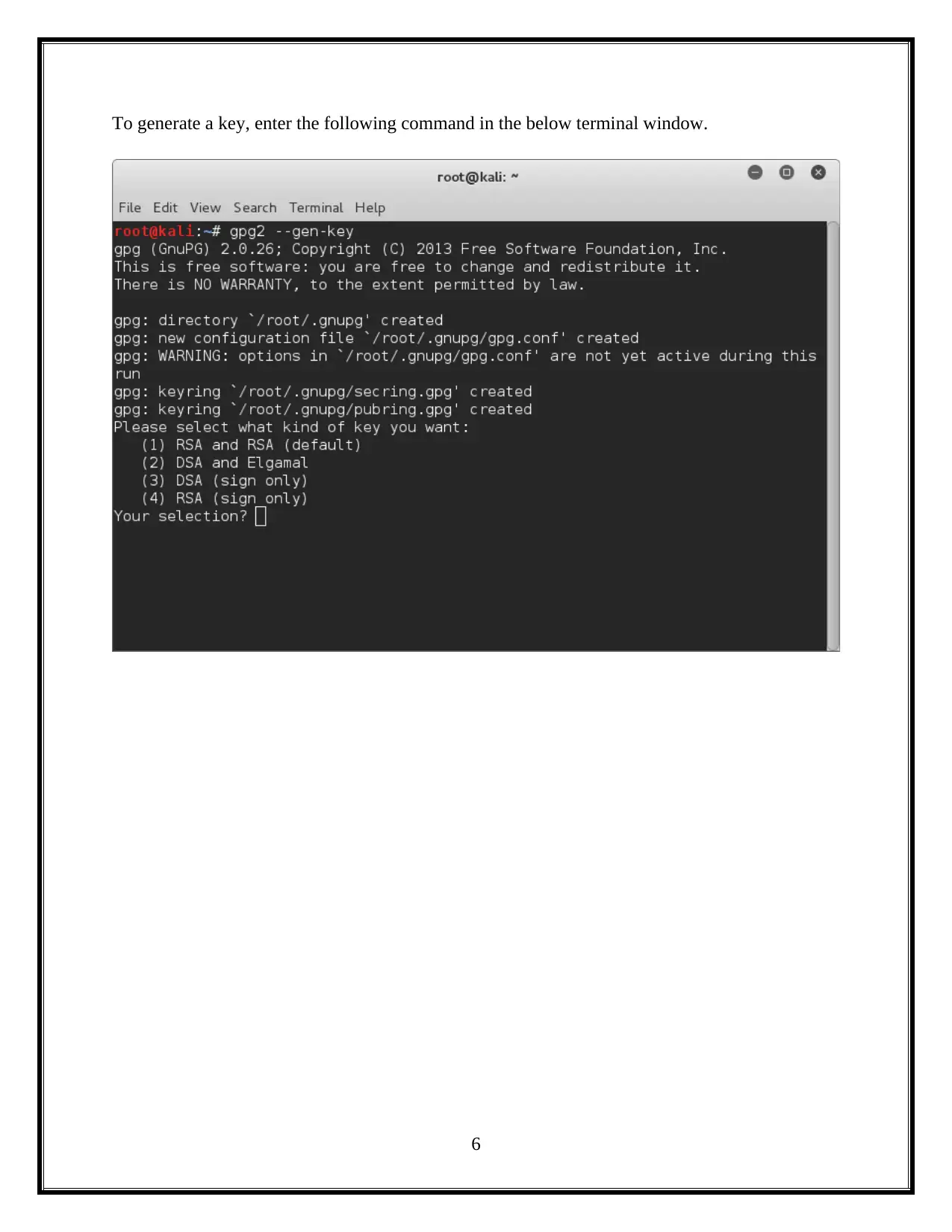
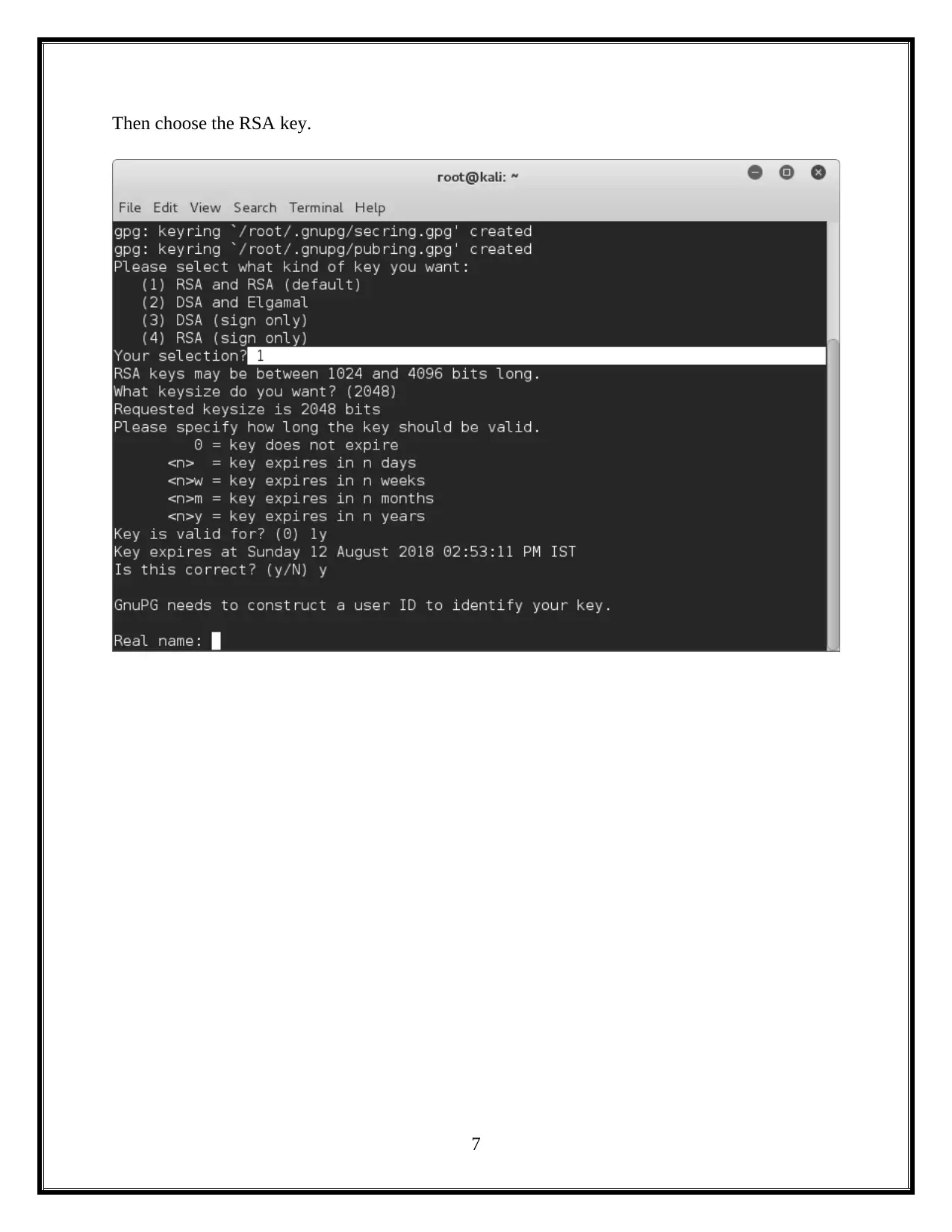
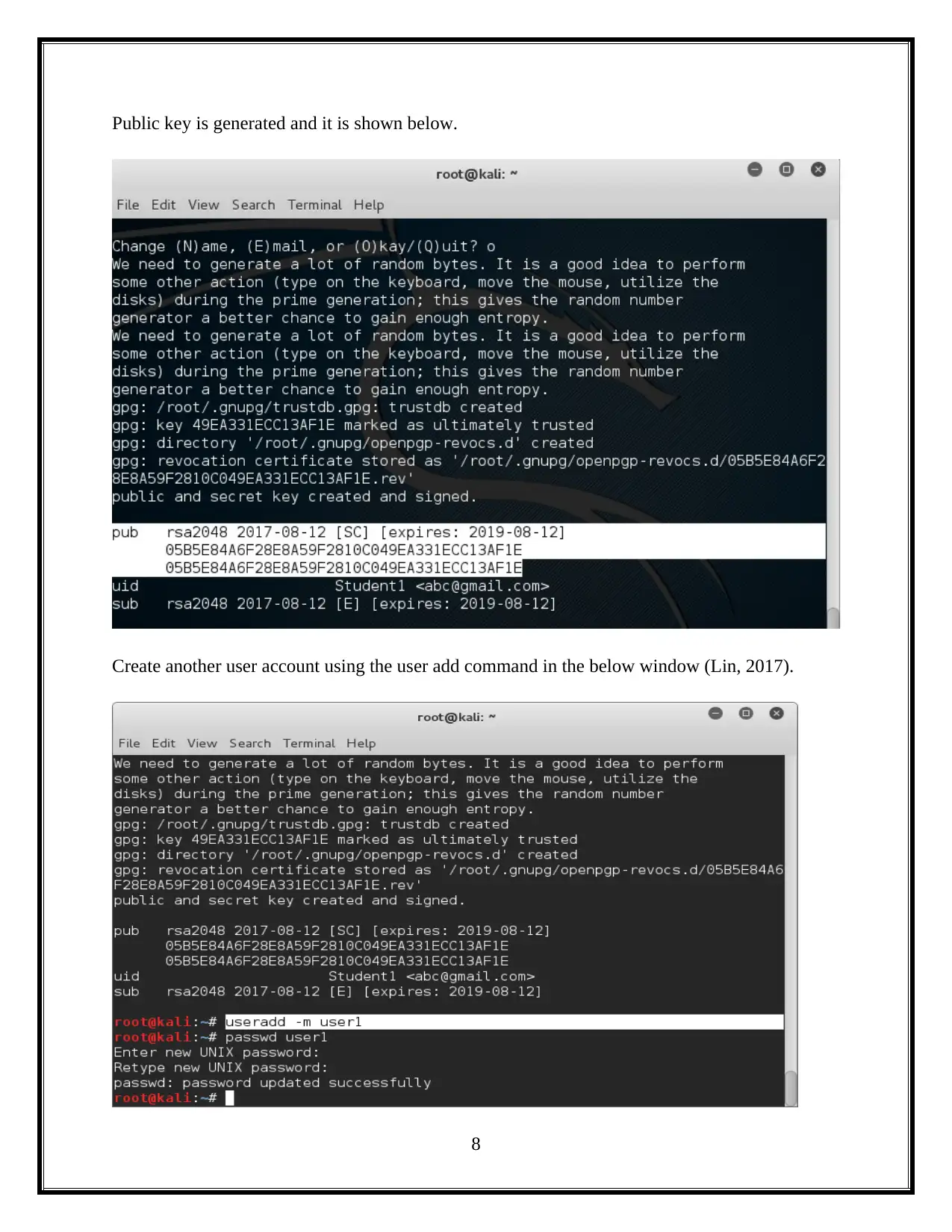
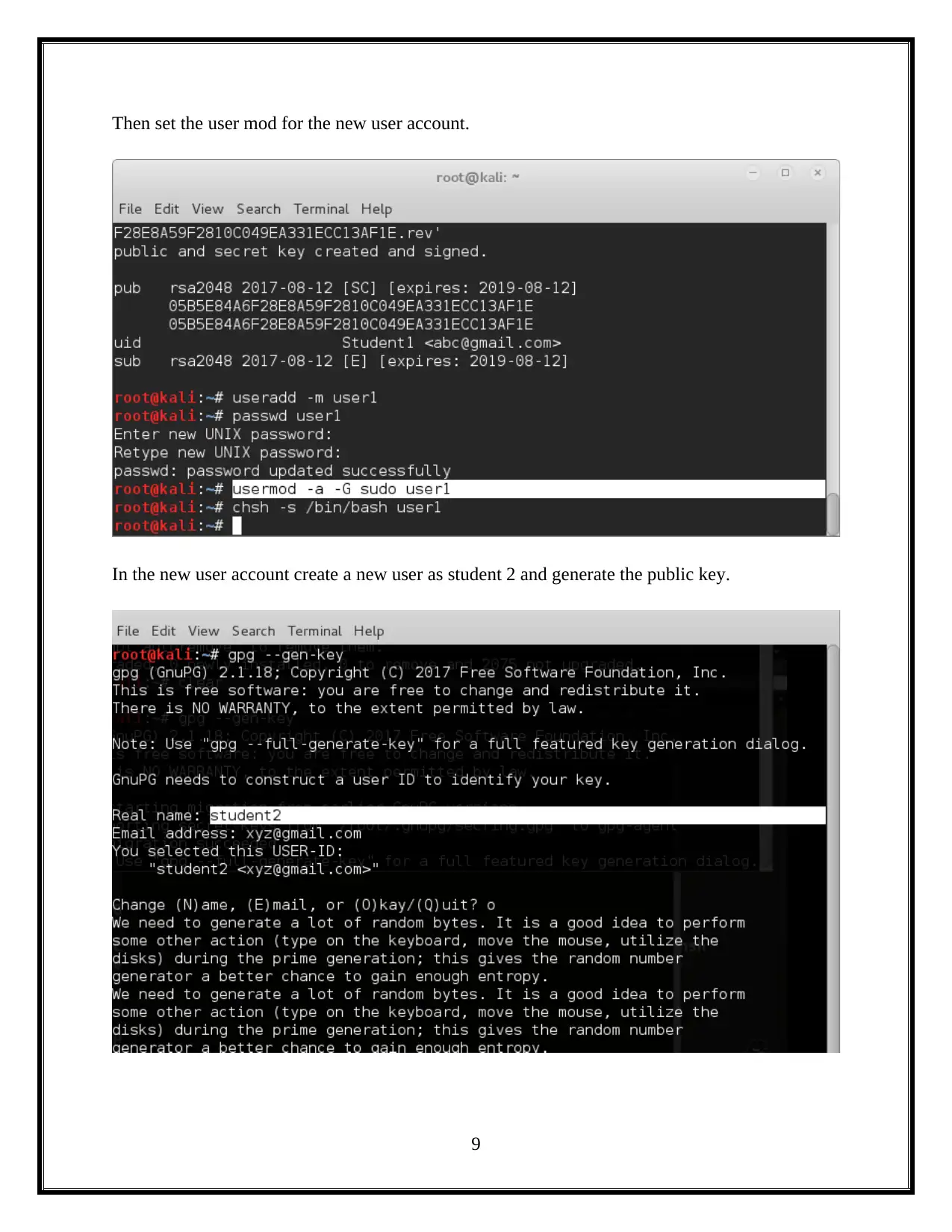
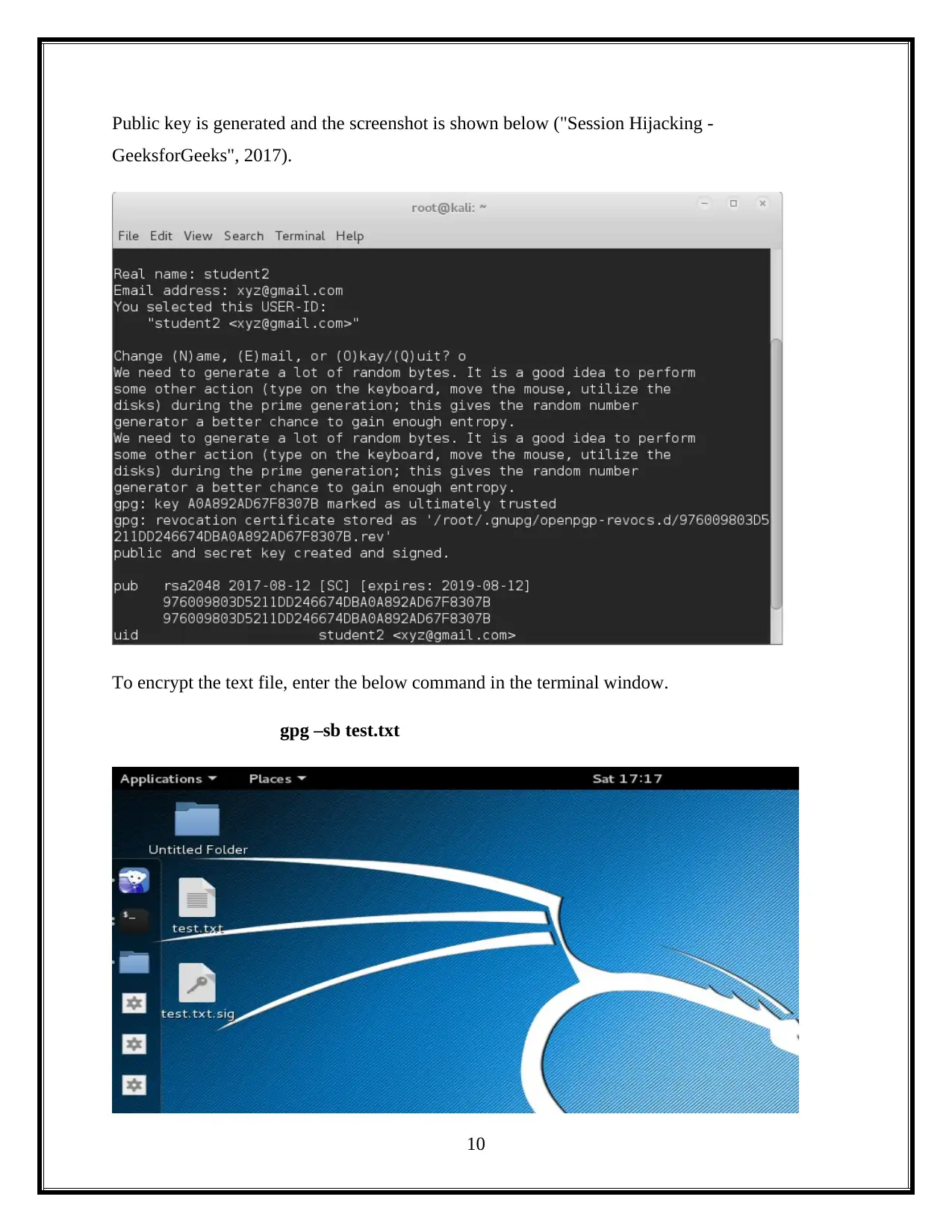
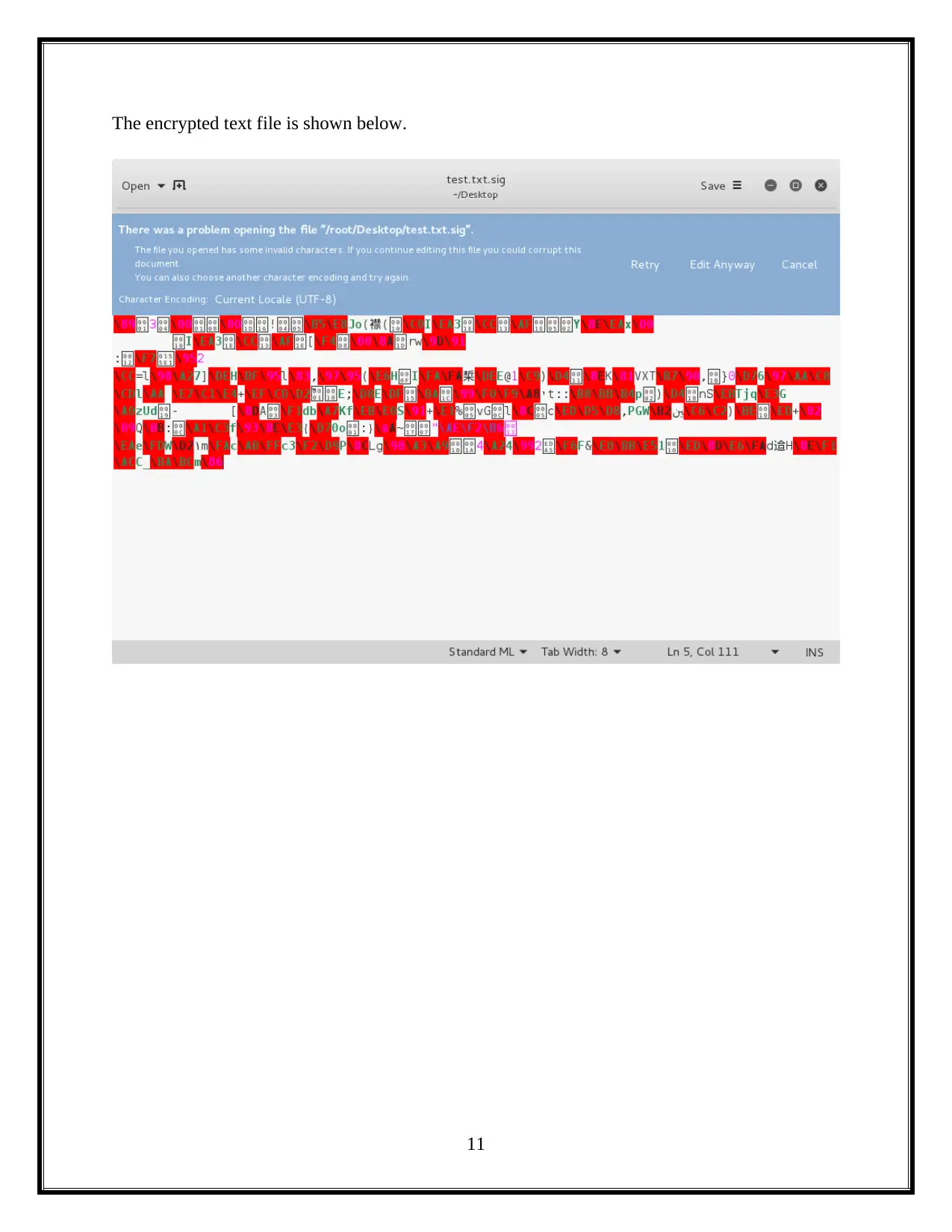
This assignment delves into the critical domain of information security, focusing on session hacking techniques and cryptographic solutions. It begins by dissecting session hacking, detailing methods such as IP spoofing, man-in-the-middle attacks, and cross-site scripting, emphasizing the vulnerabilities these attacks exploit. The assignment then pivots to mitigation strategies, highlighting the importance of network and application-level security measures, including the use of encryption protocols like IPSEC, SSH, and SSL/TLS. Furthermore, it provides a practical demonstration of cryptographic tools, specifically utilizing the gpg package to generate keys, encrypt files, and exchange keys between users to ensure secure communication and data privacy. The assignment also underscores the vital role of cryptography in safeguarding individual privacy, particularly in protecting sensitive information from unauthorized access. Overall, the assignment offers a comprehensive overview of session hacking attacks, security protocols, and cryptographic applications, offering insights into protecting information and ensuring secure communications.
1 out of 17








![[object Object]](/_next/static/media/star-bottom.7253800d.svg)