ECM1424: Information Security Assignment Report - Gordon Mediation
VerifiedAdded on 2022/08/21
|13
|2950
|11
Report
AI Summary
This report, prepared for an Information Security assignment, focuses on Gordon Mediation LTD, a consultant company requiring security analysis. The student identifies and assesses five key risks, including malicious human interference, accidental file deletion, lack of security policies, outdated hardware/software, and improper firewall configuration. A detailed risk matrix is presented, outlining impact, probability, and mitigation strategies for each identified risk. Furthermore, the report proposes a risk remediation plan addressing each vulnerability. The assignment also includes a penetration testing proposal, outlining various testing types (external, internal, website, wireless, and social engineering), the five phases of penetration testing (Reconnaissance, Scanning, Gaining Access, Maintaining Access, Covering Tracks), and the use of Wireshark for analysis. The report emphasizes the importance of confidentiality, availability, and integrity of data, along with legal considerations for penetration testing.

Running head: INFORMATION SECURITY ASSIGNMENT
INFORMATION SECURITY ASSIGNMENT
Name of the Student
Name of the University
Author Note
INFORMATION SECURITY ASSIGNMENT
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY ASSIGNMENT
Executive Summary
Gordon Mediation LTD is a consultant company that assists various companies in order to
mitigate the issues. The company needs a security analyst in order to analyse the security and
threats and the vulnerabilities of the company. The report deals with the threats and the
vulnerability analysis of the company with the help of risk matrix and the mitigation of the
risks that arise in the company. Penetration testing also needs to performed on the traffic of
the company that helps to analyse the traffic and the packets. The report focuses on the
penetration-testing proposals that are to be provided to the manager. The proposal consists of
various types of testing and the phase’s of penetration testing that are to be done.
Executive Summary
Gordon Mediation LTD is a consultant company that assists various companies in order to
mitigate the issues. The company needs a security analyst in order to analyse the security and
threats and the vulnerabilities of the company. The report deals with the threats and the
vulnerability analysis of the company with the help of risk matrix and the mitigation of the
risks that arise in the company. Penetration testing also needs to performed on the traffic of
the company that helps to analyse the traffic and the packets. The report focuses on the
penetration-testing proposals that are to be provided to the manager. The proposal consists of
various types of testing and the phase’s of penetration testing that are to be done.

2INFORMATION SECURITY ASSIGNMENT
Table of Contents
Introduction................................................................................................................................3
Risk Assessment.........................................................................................................................3
Risk Remediation Plan...............................................................................................................3
Penetration Testing Proposal......................................................................................................3
Conclusion..................................................................................................................................3
References..................................................................................................................................4
Table of Contents
Introduction................................................................................................................................3
Risk Assessment.........................................................................................................................3
Risk Remediation Plan...............................................................................................................3
Penetration Testing Proposal......................................................................................................3
Conclusion..................................................................................................................................3
References..................................................................................................................................4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3INFORMATION SECURITY ASSIGNMENT
Introduction
Information security is not only about protecting information from the access those
are unauthorized but information security is the practice of prevention of access those are
unauthorized, modification, or the destruction of information. The information can be
electrical or physical. Thus, the security of information spans over so many areas of research
like cryptography, cyber forensics and many more.
The report deals with an organization known as Gondor Mediation LTD that resolves,
mediates, and arbitrates HR and disciplinary issues for other organizations. The company
needs to assess its security of each of the procedures and areas in order to recognise and
manage the risks of cyber security. The report focuses on the risk assessment of the Gordon
Mediation LTD and discusses about the risk mediation plan. The report also has a brief
description about the penetration-testing proposal that is important for the company.
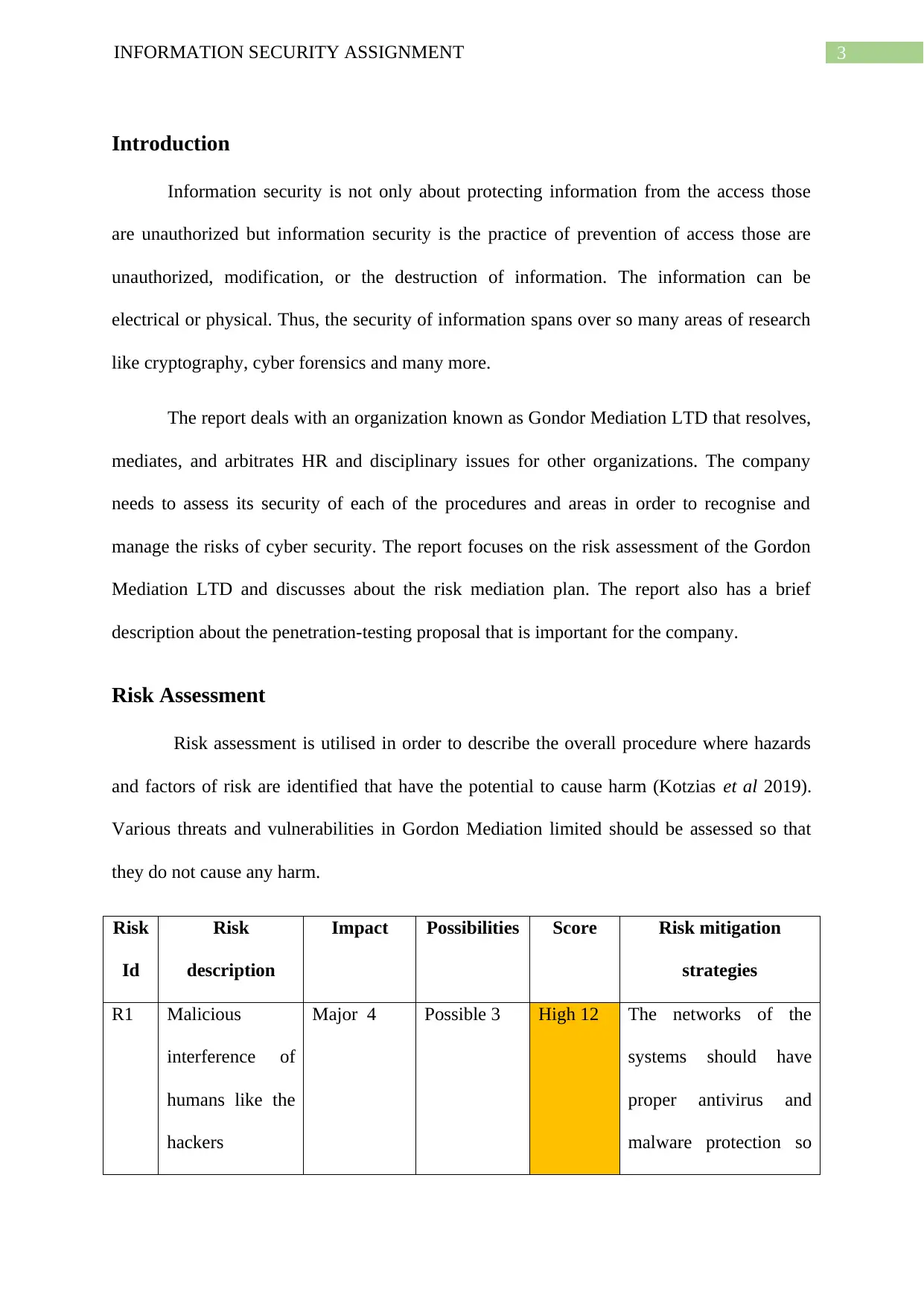
Risk Assessment
Risk assessment is utilised in order to describe the overall procedure where hazards
and factors of risk are identified that have the potential to cause harm (Kotzias et al 2019).
Various threats and vulnerabilities in Gordon Mediation limited should be assessed so that
they do not cause any harm.
Risk
Id
Risk
description
Impact Possibilities Score Risk mitigation
strategies
R1 Malicious
interference of
humans like the
hackers
Major 4 Possible 3 High 12 The networks of the
systems should have
proper antivirus and
malware protection so
Introduction
Information security is not only about protecting information from the access those
are unauthorized but information security is the practice of prevention of access those are
unauthorized, modification, or the destruction of information. The information can be
electrical or physical. Thus, the security of information spans over so many areas of research
like cryptography, cyber forensics and many more.
The report deals with an organization known as Gondor Mediation LTD that resolves,
mediates, and arbitrates HR and disciplinary issues for other organizations. The company
needs to assess its security of each of the procedures and areas in order to recognise and
manage the risks of cyber security. The report focuses on the risk assessment of the Gordon
Mediation LTD and discusses about the risk mediation plan. The report also has a brief
description about the penetration-testing proposal that is important for the company.
Risk Assessment
Risk assessment is utilised in order to describe the overall procedure where hazards
and factors of risk are identified that have the potential to cause harm (Kotzias et al 2019).
Various threats and vulnerabilities in Gordon Mediation limited should be assessed so that
they do not cause any harm.
Risk
Id
Risk
description
Impact Possibilities Score Risk mitigation
strategies
R1 Malicious
interference of
humans like the
hackers
Major 4 Possible 3 High 12 The networks of the
systems should have
proper antivirus and
malware protection so
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
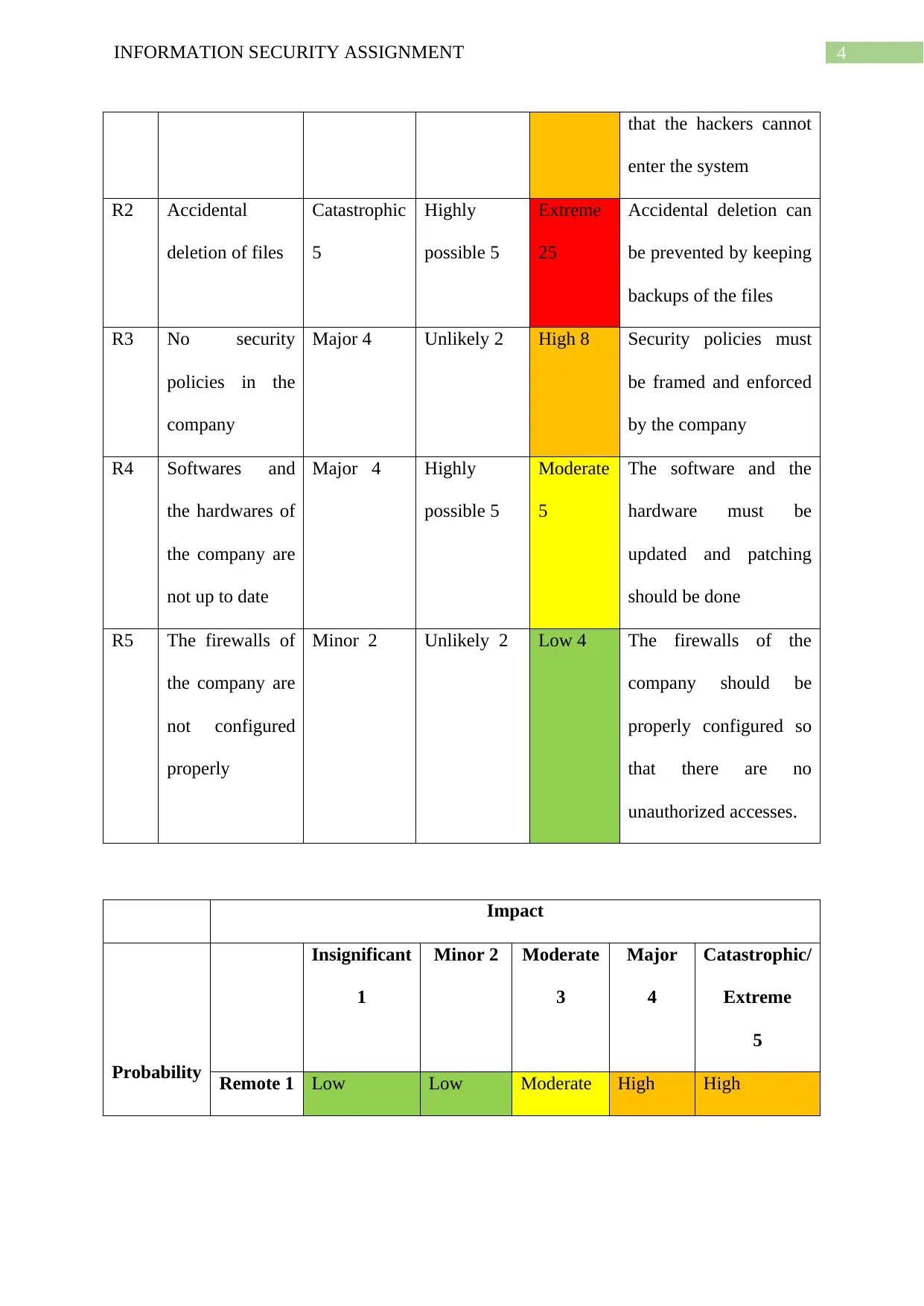
4INFORMATION SECURITY ASSIGNMENT
that the hackers cannot
enter the system
R2 Accidental
deletion of files
Catastrophic
5
Highly
possible 5
Extreme
25
Accidental deletion can
be prevented by keeping
backups of the files
R3 No security
policies in the
company
Major 4 Unlikely 2 High 8 Security policies must
be framed and enforced
by the company
R4 Softwares and
the hardwares of
the company are
not up to date
Major 4 Highly
possible 5
Moderate
5
The software and the
hardware must be
updated and patching
should be done
R5 The firewalls of
the company are
not configured
properly
Minor 2 Unlikely 2 Low 4 The firewalls of the
company should be
properly configured so
that there are no
unauthorized accesses.
Impact
Probability
Insignificant
1
Minor 2 Moderate
3
Major
4
Catastrophic/
Extreme
5
Remote 1 Low Low Moderate High High
that the hackers cannot
enter the system
R2 Accidental
deletion of files
Catastrophic
5
Highly
possible 5
Extreme
25
Accidental deletion can
be prevented by keeping
backups of the files
R3 No security
policies in the
company
Major 4 Unlikely 2 High 8 Security policies must
be framed and enforced
by the company
R4 Softwares and
the hardwares of
the company are
not up to date
Major 4 Highly
possible 5
Moderate
5
The software and the
hardware must be
updated and patching
should be done
R5 The firewalls of
the company are
not configured
properly
Minor 2 Unlikely 2 Low 4 The firewalls of the
company should be
properly configured so
that there are no
unauthorized accesses.
Impact
Probability
Insignificant
1
Minor 2 Moderate
3
Major
4
Catastrophic/
Extreme
5
Remote 1 Low Low Moderate High High
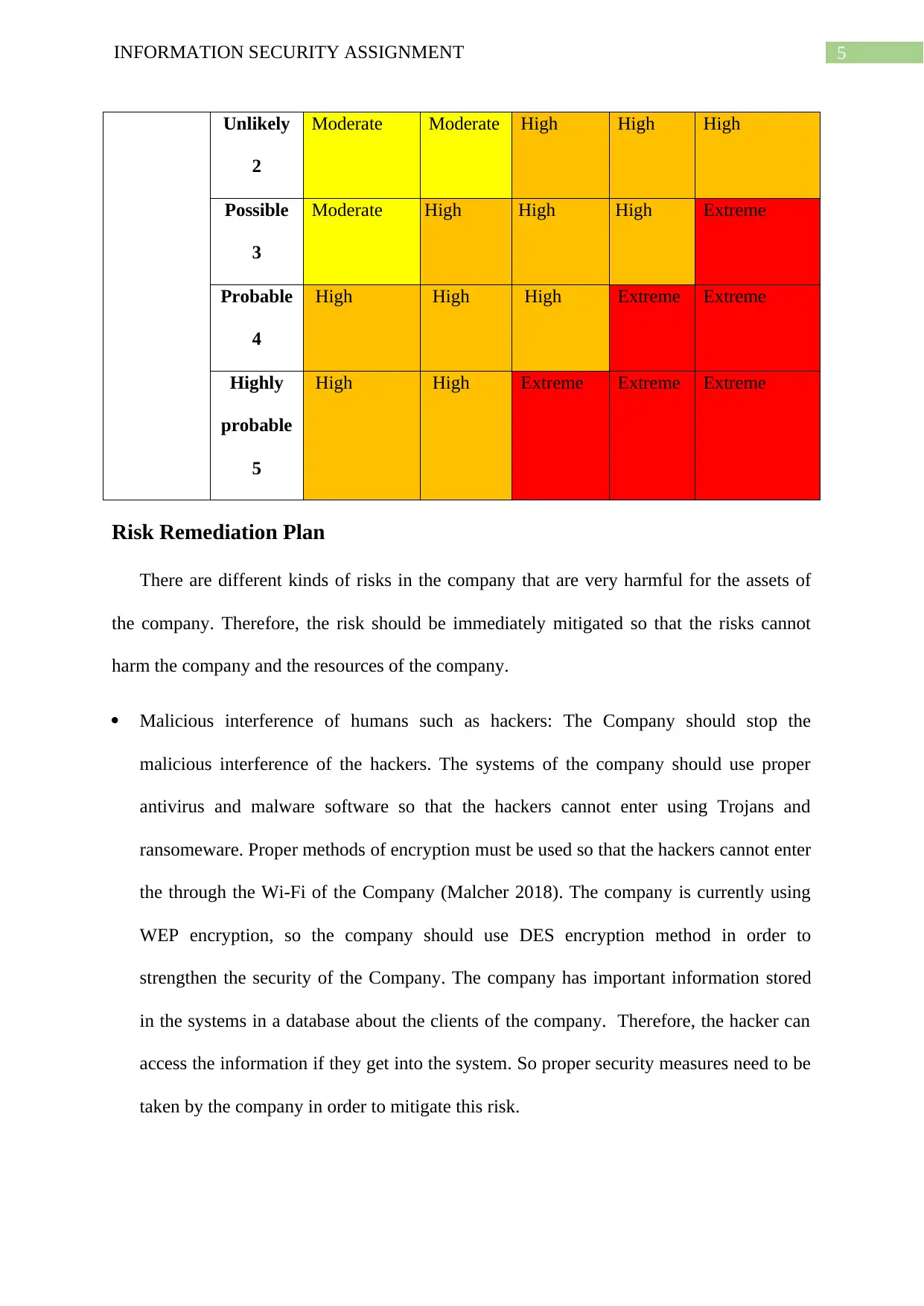
5INFORMATION SECURITY ASSIGNMENT
Unlikely
2
Moderate Moderate High High High
Possible
3
Moderate High High High Extreme
Probable
4
High High High Extreme Extreme
Highly
probable
5
High High Extreme Extreme Extreme
Risk Remediation Plan
There are different kinds of risks in the company that are very harmful for the assets of
the company. Therefore, the risk should be immediately mitigated so that the risks cannot
harm the company and the resources of the company.
Malicious interference of humans such as hackers: The Company should stop the
malicious interference of the hackers. The systems of the company should use proper
antivirus and malware software so that the hackers cannot enter using Trojans and
ransomeware. Proper methods of encryption must be used so that the hackers cannot enter
the through the Wi-Fi of the Company (Malcher 2018). The company is currently using
WEP encryption, so the company should use DES encryption method in order to
strengthen the security of the Company. The company has important information stored
in the systems in a database about the clients of the company. Therefore, the hacker can
access the information if they get into the system. So proper security measures need to be
taken by the company in order to mitigate this risk.
Unlikely
2
Moderate Moderate High High High
Possible
3
Moderate High High High Extreme
Probable
4
High High High Extreme Extreme
Highly
probable
5
High High Extreme Extreme Extreme
Risk Remediation Plan
There are different kinds of risks in the company that are very harmful for the assets of
the company. Therefore, the risk should be immediately mitigated so that the risks cannot
harm the company and the resources of the company.
Malicious interference of humans such as hackers: The Company should stop the
malicious interference of the hackers. The systems of the company should use proper
antivirus and malware software so that the hackers cannot enter using Trojans and
ransomeware. Proper methods of encryption must be used so that the hackers cannot enter
the through the Wi-Fi of the Company (Malcher 2018). The company is currently using
WEP encryption, so the company should use DES encryption method in order to
strengthen the security of the Company. The company has important information stored
in the systems in a database about the clients of the company. Therefore, the hacker can
access the information if they get into the system. So proper security measures need to be
taken by the company in order to mitigate this risk.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SECURITY ASSIGNMENT
Accidental deletion of files: Accidental deletion of risk is an important risk that needs t be
taken care by the employees of the company mainly the personnel who handle the
information of the clients and the finance of the company. If these files are deleted then
the company will be trouble because they will not have any information of the clients and
there financial details such as profits, revenue and many more. So, this risk requires to be
properly mitigated so that the company does not have any risk of the clients and their
information (Adekanye and Rahman 2018). This risk can be mitigated by properly
backing up the files and storing the information in cloud. Therefore, if the informations
and the data are deleted then back up will help them to recover the information of the
clients and the financial details of the company.
No security policies in the company: The Company does not have any security policy that
is framed. Therefore, the employees of the company do not follow any rule about the
security of the company. If there are no security policies in the company then the
employees will not follow anything as the laptops will be kept open and will not be kept
in cupboard then, their important information can be accessed (Roldán-Molina et al
2017). Training about the security of the network and data breaches must be provided to
the employees so that the know when data breaches occur in the company and they can
take safety measures hen data breaches occur in the organization.
Software and hardware of the company should be kept up to date: The hardware and the
software of the company must be kept up to date so that the systems do not lag when the
employees are working on their system. The system of the company has windows 7. So
they should be installed with latest version of Windows so that the employees do not have
any problems when they work (Lewis 2017). The softwares must be patched so that the
softwares do not have any vulnerability so that cannot be accessed or hacked by any
unauthorized person. The hardwares that are used in the company should be of latest and
Accidental deletion of files: Accidental deletion of risk is an important risk that needs t be
taken care by the employees of the company mainly the personnel who handle the
information of the clients and the finance of the company. If these files are deleted then
the company will be trouble because they will not have any information of the clients and
there financial details such as profits, revenue and many more. So, this risk requires to be
properly mitigated so that the company does not have any risk of the clients and their
information (Adekanye and Rahman 2018). This risk can be mitigated by properly
backing up the files and storing the information in cloud. Therefore, if the informations
and the data are deleted then back up will help them to recover the information of the
clients and the financial details of the company.
No security policies in the company: The Company does not have any security policy that
is framed. Therefore, the employees of the company do not follow any rule about the
security of the company. If there are no security policies in the company then the
employees will not follow anything as the laptops will be kept open and will not be kept
in cupboard then, their important information can be accessed (Roldán-Molina et al
2017). Training about the security of the network and data breaches must be provided to
the employees so that the know when data breaches occur in the company and they can
take safety measures hen data breaches occur in the organization.
Software and hardware of the company should be kept up to date: The hardware and the
software of the company must be kept up to date so that the systems do not lag when the
employees are working on their system. The system of the company has windows 7. So
they should be installed with latest version of Windows so that the employees do not have
any problems when they work (Lewis 2017). The softwares must be patched so that the
softwares do not have any vulnerability so that cannot be accessed or hacked by any
unauthorized person. The hardwares that are used in the company should be of latest and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY ASSIGNMENT
updated version like routers and the antivirus and the firewalls so that the hackers or the
attackers cannot enter the system of the company and access the important information
and data that are present in the systems of the company.
The firewalls of the systems are not properly configured: This is a huge risk for the
company, as the firewalls that are installed in the systems are not configured properly.
The IT administrators of the Company should upgrade the firewalls that are installed in
the systems of the company so that the hackers do not access the sensitive information
that is present in the system (Mukherjee 2019). The upgraded firewalls will block the
contents that will harm the system and will protect the system from unauthorized access.
The Wi-Fi of the company is protected by WEP encryption, which is not very good type
of encryption. The Wi-Fi should be encrypted with DES encryption that is very strong
and the passwords of the Gmail accounts of the company must be protected with strong
passwords and the passwords must encrypted.
Penetration Testing Proposal
Penetration testing is the practice of testing a system of computer, network or
application of web to find vulnerabilities of security that a hacker can exploit (Bueno et al
2018). Penetration testing can also be automated with the help of software applications or it
can be performed manually.
The scope of the penetration testing services is as follows:
External networking penetration testing: this assesses the defences of perimeters of the
services and the hosts that are exposed to the internet. It also assesses the firewalls that
are installed in the systems of the company (Pozzobon et al 2018).
updated version like routers and the antivirus and the firewalls so that the hackers or the
attackers cannot enter the system of the company and access the important information
and data that are present in the systems of the company.
The firewalls of the systems are not properly configured: This is a huge risk for the
company, as the firewalls that are installed in the systems are not configured properly.
The IT administrators of the Company should upgrade the firewalls that are installed in
the systems of the company so that the hackers do not access the sensitive information
that is present in the system (Mukherjee 2019). The upgraded firewalls will block the
contents that will harm the system and will protect the system from unauthorized access.
The Wi-Fi of the company is protected by WEP encryption, which is not very good type
of encryption. The Wi-Fi should be encrypted with DES encryption that is very strong
and the passwords of the Gmail accounts of the company must be protected with strong
passwords and the passwords must encrypted.
Penetration Testing Proposal
Penetration testing is the practice of testing a system of computer, network or
application of web to find vulnerabilities of security that a hacker can exploit (Bueno et al
2018). Penetration testing can also be automated with the help of software applications or it
can be performed manually.
The scope of the penetration testing services is as follows:
External networking penetration testing: this assesses the defences of perimeters of the
services and the hosts that are exposed to the internet. It also assesses the firewalls that
are installed in the systems of the company (Pozzobon et al 2018).

8INFORMATION SECURITY ASSIGNMENT
Internal Network Penetration testing: It assesses the security of the private networks those
are internal and the hosts in order to determine what an individual those are malicious
could compromise with in the different CTPF networks
CTPF websites penetration testing: It assesses the weaknesses that are present within the
websites or the software of web applications
Wireless security scanning: it assesses the requirement of the infrastructure security of
wireless networks from an unauthorized access to the wireless network of CTPF
Social engineering: it analyzes the weaknesses to different kinds of phishing attacks
It determines the requirement of protocols and security of physical access (Xin et al
2018).
Special requests: Ad-hoc requests of penetration may be required in conjunction with
particular projects of infrastructure being finished at future dates.
There are five phases in penetration testing that needs to be followed in order to conduct
penetration testing on the systems of the Company (Myasnikov 2019). The steps are as
follows:
Reconnaissance: Reconnaissance is the operation of gathering data those are preliminary
or intelligence on the assets of the system. The data is collected to better plan for the
attack on the system. Reconnaissance can be executed actively or passively
Scanning the stage of scanning needs the application of tools those are technical in order
to gather intelligence on the target, but in some of the cases, the intelligence that is being
sought is more about the computer systems that they have in place. An example would be
the utilization of vulnerability scanner on a network that is targeted (Guarda et al 2016).
Gaining access: Stage 3 is the gaining access needs taking control of multiple network
devices to extract data from the target or to utilise that device in order to launch attacks
on other devices or networks those are targeted.
Internal Network Penetration testing: It assesses the security of the private networks those
are internal and the hosts in order to determine what an individual those are malicious
could compromise with in the different CTPF networks
CTPF websites penetration testing: It assesses the weaknesses that are present within the
websites or the software of web applications
Wireless security scanning: it assesses the requirement of the infrastructure security of
wireless networks from an unauthorized access to the wireless network of CTPF
Social engineering: it analyzes the weaknesses to different kinds of phishing attacks
It determines the requirement of protocols and security of physical access (Xin et al
2018).
Special requests: Ad-hoc requests of penetration may be required in conjunction with
particular projects of infrastructure being finished at future dates.
There are five phases in penetration testing that needs to be followed in order to conduct
penetration testing on the systems of the Company (Myasnikov 2019). The steps are as
follows:
Reconnaissance: Reconnaissance is the operation of gathering data those are preliminary
or intelligence on the assets of the system. The data is collected to better plan for the
attack on the system. Reconnaissance can be executed actively or passively
Scanning the stage of scanning needs the application of tools those are technical in order
to gather intelligence on the target, but in some of the cases, the intelligence that is being
sought is more about the computer systems that they have in place. An example would be
the utilization of vulnerability scanner on a network that is targeted (Guarda et al 2016).
Gaining access: Stage 3 is the gaining access needs taking control of multiple network
devices to extract data from the target or to utilise that device in order to launch attacks
on other devices or networks those are targeted.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION SECURITY ASSIGNMENT
Maintaining access: Maintaining access needs taking the steps that are involved in being
able to be constantly within the environment of target to gather data as possible (Sina
2019). The attacker must remain quiet in this stage no to get caught while utilising the
environment of host.
Covering of tracks: The final stage of covering of track means that the attacker must take
the steps those are required to delete all the tracks of detection. Any changes that were
made and the authorizations those were escalated many more, all must be returned to the
non-recognition stage by the administrators of the host network.
The tool that is used in order to perform penetration testing on the systems of the
company is wireshark. It is utilised for troubleshooting of network and analysis of network,
development of communications and software protocols (Sandhya et al 2017). Wireshark is
used to troubleshoot the problems of network and then test the softwares since it offers the
capability to drill down and read the contents of each of the packets. The results of the
penetration testing by using Wireshark are provided in a way that is very easy to understand.
Testers can utilise wireshark to look closely at the flows of traffic and the packets those are
troublesome (Navabud and Chen 2018). It is also useful in analyzing the networks those are
wireless as wireshark can capture live traffic over-the-air.
Before allowing the tester to test the data those are sensitive, the company should take
important measures regarding the confidentiality, availability and the integrity of data
(Hatfield 2019). The legal issues that are to be considered when penetration testing should be
done are:
The tester does not know his clients- there are no grounds that he should be given
admittance of the data those are sensitive
There will be no one who will take guarantee of the data those are lost
Maintaining access: Maintaining access needs taking the steps that are involved in being
able to be constantly within the environment of target to gather data as possible (Sina
2019). The attacker must remain quiet in this stage no to get caught while utilising the
environment of host.
Covering of tracks: The final stage of covering of track means that the attacker must take
the steps those are required to delete all the tracks of detection. Any changes that were
made and the authorizations those were escalated many more, all must be returned to the
non-recognition stage by the administrators of the host network.
The tool that is used in order to perform penetration testing on the systems of the
company is wireshark. It is utilised for troubleshooting of network and analysis of network,
development of communications and software protocols (Sandhya et al 2017). Wireshark is
used to troubleshoot the problems of network and then test the softwares since it offers the
capability to drill down and read the contents of each of the packets. The results of the
penetration testing by using Wireshark are provided in a way that is very easy to understand.
Testers can utilise wireshark to look closely at the flows of traffic and the packets those are
troublesome (Navabud and Chen 2018). It is also useful in analyzing the networks those are
wireless as wireshark can capture live traffic over-the-air.
Before allowing the tester to test the data those are sensitive, the company should take
important measures regarding the confidentiality, availability and the integrity of data
(Hatfield 2019). The legal issues that are to be considered when penetration testing should be
done are:
The tester does not know his clients- there are no grounds that he should be given
admittance of the data those are sensitive
There will be no one who will take guarantee of the data those are lost
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INFORMATION SECURITY ASSIGNMENT
The company may blame for the data loss or the confidentiality
The person that is performing the penetration testing must follow few ethics before he
starts to perform penetration testing. He must not access any of the files or any sensitive
information of the company (Thomas, Burmeister and Low 2018). He should not take any
information with him about the company.
Conclusion
The report concludes with the security of the Gordon Mediation Limited. The
evaluation of the security is very important as the assets of the company can be at risk. In this
report, the threats and the vulnerabilities of the company are assessed using a risk matrix and
the mitigation of risk of the company are assessed in this report. After that a penetration
testing proposal needs to provided to the manager of the company that consist of types of
testing that are to be done and the phases of penetration testing and ethical and legal
consideration of the penetration testing. Penetration testing is important for the company as it
evaluates the traffic of the network and the packets that are coming and going out of the
network.
The company may blame for the data loss or the confidentiality
The person that is performing the penetration testing must follow few ethics before he
starts to perform penetration testing. He must not access any of the files or any sensitive
information of the company (Thomas, Burmeister and Low 2018). He should not take any
information with him about the company.
Conclusion
The report concludes with the security of the Gordon Mediation Limited. The
evaluation of the security is very important as the assets of the company can be at risk. In this
report, the threats and the vulnerabilities of the company are assessed using a risk matrix and
the mitigation of risk of the company are assessed in this report. After that a penetration
testing proposal needs to provided to the manager of the company that consist of types of
testing that are to be done and the phases of penetration testing and ethical and legal
consideration of the penetration testing. Penetration testing is important for the company as it
evaluates the traffic of the network and the packets that are coming and going out of the
network.

11INFORMATION SECURITY ASSIGNMENT
References
Adekanye, M.O. and Rahman, S.S., 2018. The Effect of Information Technology using
Enterprise Security Risk Management. International Journal of Network Security & Its
Applications (IJNSA) Vol, 10.
Bueno, P.M.S., de Franco Rosa, F., Jino, M. and Bonacin, R., 2018, October. A Security
Testing Process supported by an Ontology Environment: a conceptual proposal. In 2018
IEEE/ACS 15th International Conference on Computer Systems and Applications
(AICCSA) (pp. 1-8). IEEE.
Guarda, T., Orozco, W., Augusto, M.F., Morillo, G., Navarrete, S.A. and Pinto, F.M., 2016,
December. Penetration testing on virtual environments. In Proceedings of the 4th
International Conference on Information and Network Security (pp. 9-12).
Hatfield, J.M., 2019. Virtuous human hacking: The ethics of social engineering in
penetration-testing. computers & security, 83, pp.354-366.
Kotzias, P., Bilge, L., Vervier, P.A. and Caballero, J., 2019. Mind Your Own Business: A
Longitudinal Study of Threats and Vulnerabilities in Enterprises. In NDSS.
Lewis, K., 2017. Security Policies and Plans Development. In Computer and Information
Security Handbook (pp. 565-570). Morgan Kaufmann.
Malcher, M., 2018. Database Security. In DBA Transformations (pp. 69-82). Apress,
Berkeley, CA.
Mukherjee, S., 2019. Overview of the Importance of Corporate Security in
business. Available at SSRN 3415960.
References
Adekanye, M.O. and Rahman, S.S., 2018. The Effect of Information Technology using
Enterprise Security Risk Management. International Journal of Network Security & Its
Applications (IJNSA) Vol, 10.
Bueno, P.M.S., de Franco Rosa, F., Jino, M. and Bonacin, R., 2018, October. A Security
Testing Process supported by an Ontology Environment: a conceptual proposal. In 2018
IEEE/ACS 15th International Conference on Computer Systems and Applications
(AICCSA) (pp. 1-8). IEEE.
Guarda, T., Orozco, W., Augusto, M.F., Morillo, G., Navarrete, S.A. and Pinto, F.M., 2016,
December. Penetration testing on virtual environments. In Proceedings of the 4th
International Conference on Information and Network Security (pp. 9-12).
Hatfield, J.M., 2019. Virtuous human hacking: The ethics of social engineering in
penetration-testing. computers & security, 83, pp.354-366.
Kotzias, P., Bilge, L., Vervier, P.A. and Caballero, J., 2019. Mind Your Own Business: A
Longitudinal Study of Threats and Vulnerabilities in Enterprises. In NDSS.
Lewis, K., 2017. Security Policies and Plans Development. In Computer and Information
Security Handbook (pp. 565-570). Morgan Kaufmann.
Malcher, M., 2018. Database Security. In DBA Transformations (pp. 69-82). Apress,
Berkeley, CA.
Mukherjee, S., 2019. Overview of the Importance of Corporate Security in
business. Available at SSRN 3415960.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




