Information Security: Analyzing ATM Security, CIA Triad & Biometrics
VerifiedAdded on 2023/06/14
|9
|1640
|444
Homework Assignment
AI Summary
This assignment solution delves into key aspects of information security, beginning with an explanation of the CIA triad (Confidentiality, Integrity, Availability) and its relevance to securing data, particularly in the context of ATM PINs. It analyzes a scenario involving an ATM theft, calculating the possible PIN combinations and highlighting the limitations imposed by ATM security measures. The solution then discusses the challenges associated with biometric systems, including data breaches, false acceptance/rejection rates, and potential security implications, suggesting multi-factor authentication as a solution. Furthermore, it differentiates between false positives and false negatives in biometric systems and their organizational impacts. Finally, the assignment provides a step-by-step decryption of a cipher text, demonstrating the application of substitution and Caesar ciphers, ultimately revealing the message 'employees will increases the processor speed'. Desklib offers this solution along with numerous past papers and solved assignments to aid students in their studies.

Running head: INFORMATION SECURITY
INFORMATION SECURITY
Name of the Student
Name of the University
Authors Note:
INFORMATION SECURITY
Name of the Student
Name of the University
Authors Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY
Table of Contents
Answer to Question 1:.........................................................................................................2
Answer to Question 2:.........................................................................................................2
Answer to Question 3:.........................................................................................................3
Answer to Question 4:.........................................................................................................4
Answer to Question 5:.........................................................................................................4
References............................................................................................................................7
Table of Contents
Answer to Question 1:.........................................................................................................2
Answer to Question 2:.........................................................................................................2
Answer to Question 3:.........................................................................................................3
Answer to Question 4:.........................................................................................................4
Answer to Question 5:.........................................................................................................4
References............................................................................................................................7

2INFORMATION SECURITY
Answer to Question 1:
The CIA trait can be considered as a basic guideline, which is related to ensuring the
security of data. The concept deals with how data can be secured saved without any third party
involving into the data. In this scenario, it can be stated that the PIN can act as a security aspect
in the framework of working which is involved into the ATM. The PIN can be considered as an
identification number, which can be used for conducting transaction over the system. In order to
achieve the desired standard of security the personal who are involved into the process should
achieve adequate amount of training so that they would be helpful in the concept of mitigation of
the problem when it occurs (Prasanthi et al., 2014)
Answer to Question 2:
In this question a situation is given in which a theft broke into the ATM by means of a
screwdriver. He was able to jam the card reader and eventually break five keys of the machine.
The thief in the process had to halt due to the factor a user was approaching to use the machine.
The customer entered the card but was not able to do any type of transaction. Therefore, he went
out to get help. In the meanwhile, the theft again entered the room and started to hint the
password or the PIN. In this question, we are to undertake the maximum amount of number the
PIN can be entered by means of using the permutation technique of the mathematics. The total
number of keys, which are present in the system, is ten out of which five keys were broken.
Therefore the number of keys which would be available for guesswork is five keys so that they
four digit password can be achieved.
5P4 = 5! / (5-4)! = 5! /1! = 5*4*3*2*1/ 1 =120/1 =120.
Answer to Question 1:
The CIA trait can be considered as a basic guideline, which is related to ensuring the
security of data. The concept deals with how data can be secured saved without any third party
involving into the data. In this scenario, it can be stated that the PIN can act as a security aspect
in the framework of working which is involved into the ATM. The PIN can be considered as an
identification number, which can be used for conducting transaction over the system. In order to
achieve the desired standard of security the personal who are involved into the process should
achieve adequate amount of training so that they would be helpful in the concept of mitigation of
the problem when it occurs (Prasanthi et al., 2014)
Answer to Question 2:
In this question a situation is given in which a theft broke into the ATM by means of a
screwdriver. He was able to jam the card reader and eventually break five keys of the machine.
The thief in the process had to halt due to the factor a user was approaching to use the machine.
The customer entered the card but was not able to do any type of transaction. Therefore, he went
out to get help. In the meanwhile, the theft again entered the room and started to hint the
password or the PIN. In this question, we are to undertake the maximum amount of number the
PIN can be entered by means of using the permutation technique of the mathematics. The total
number of keys, which are present in the system, is ten out of which five keys were broken.
Therefore the number of keys which would be available for guesswork is five keys so that they
four digit password can be achieved.
5P4 = 5! / (5-4)! = 5! /1! = 5*4*3*2*1/ 1 =120/1 =120.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY
Therefore, it can be stated from the above that the outcome, which is possible, is 120. On
the other hand, according to the laws of the ATM only three tries are available. This means that
if the PIN were entered wrong three times it would result in the blocking of the card (Montefusco
et al., 2015)
Answer to Question 3:
The main issue, which can be majorly seen in the concept of biometric, are as following:
The basic working of the biometric is based on the concept of recognizing at particular
person by means of the data, which is stored in the database. The information, which is
stored in the database, may involve name, address, phone number and other crucial
information of the user. Now if the database of the system is hacked it could lead to the
leakage of the information of the customer or the user.
There can be different types of parameter, which is involved into the concept, which are
related to the false entry and false acceptance. Most of the biometric system do not have any
idea or logic related to the identification of a particular person. In the concept of the
biometric, the aspect of failure can be playing a very vital role (Haque, Nasrollahi &
Moeslund, 2015).
In the concept of biometric, the aspect of mapping can be considered as the backbone of the
technology. Mapping is done in this system by means of the information, which is saved in
the database and the fingerprint of the user or the customer. It can be majorly seen that the
system does not identify the person even though the person details exist in the database. This
can be considered as false rejection aspect.
Therefore, it can be stated from the above that the outcome, which is possible, is 120. On
the other hand, according to the laws of the ATM only three tries are available. This means that
if the PIN were entered wrong three times it would result in the blocking of the card (Montefusco
et al., 2015)
Answer to Question 3:
The main issue, which can be majorly seen in the concept of biometric, are as following:
The basic working of the biometric is based on the concept of recognizing at particular
person by means of the data, which is stored in the database. The information, which is
stored in the database, may involve name, address, phone number and other crucial
information of the user. Now if the database of the system is hacked it could lead to the
leakage of the information of the customer or the user.
There can be different types of parameter, which is involved into the concept, which are
related to the false entry and false acceptance. Most of the biometric system do not have any
idea or logic related to the identification of a particular person. In the concept of the
biometric, the aspect of failure can be playing a very vital role (Haque, Nasrollahi &
Moeslund, 2015).
In the concept of biometric, the aspect of mapping can be considered as the backbone of the
technology. Mapping is done in this system by means of the information, which is saved in
the database and the fingerprint of the user or the customer. It can be majorly seen that the
system does not identify the person even though the person details exist in the database. This
can be considered as false rejection aspect.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY
In order to make the system work proper different types of security implecations should be
implemented which would be safeguarding the overall data and the would be directly
reducing the aspect of false rejection. One of the methods, which can be implemented in the
concept, is the multi authentication process which would be safeguarding the identity of the
user.
Answer to Question 4:
False Positive: The aspect of the false negative is when the system does not identity a particular
person. In most of the cases the system rejects the identification of a particular person even
thought the database of the system contains the information of the user (Hadid et al., 2015). The
concept when implemented within the working of an organization it can create different problem
and can even result in shutting down of the entire infrastructure.
False Negative: The aspect of false negative identifies a situation where the person get the
identification of another person. This can result in a situation where a person can perform
different type of unethical activity by using the identification of another person. This can lead to
different types of problem were the actual person would not have any knowledge about the
activity which is being performed by using his /her identity.
Answer to Question 5:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
In order to make the system work proper different types of security implecations should be
implemented which would be safeguarding the overall data and the would be directly
reducing the aspect of false rejection. One of the methods, which can be implemented in the
concept, is the multi authentication process which would be safeguarding the identity of the
user.
Answer to Question 4:
False Positive: The aspect of the false negative is when the system does not identity a particular
person. In most of the cases the system rejects the identification of a particular person even
thought the database of the system contains the information of the user (Hadid et al., 2015). The
concept when implemented within the working of an organization it can create different problem
and can even result in shutting down of the entire infrastructure.
False Negative: The aspect of false negative identifies a situation where the person get the
identification of another person. This can result in a situation where a person can perform
different type of unethical activity by using the identification of another person. This can lead to
different types of problem were the actual person would not have any knowledge about the
activity which is being performed by using his /her identity.
Answer to Question 5:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
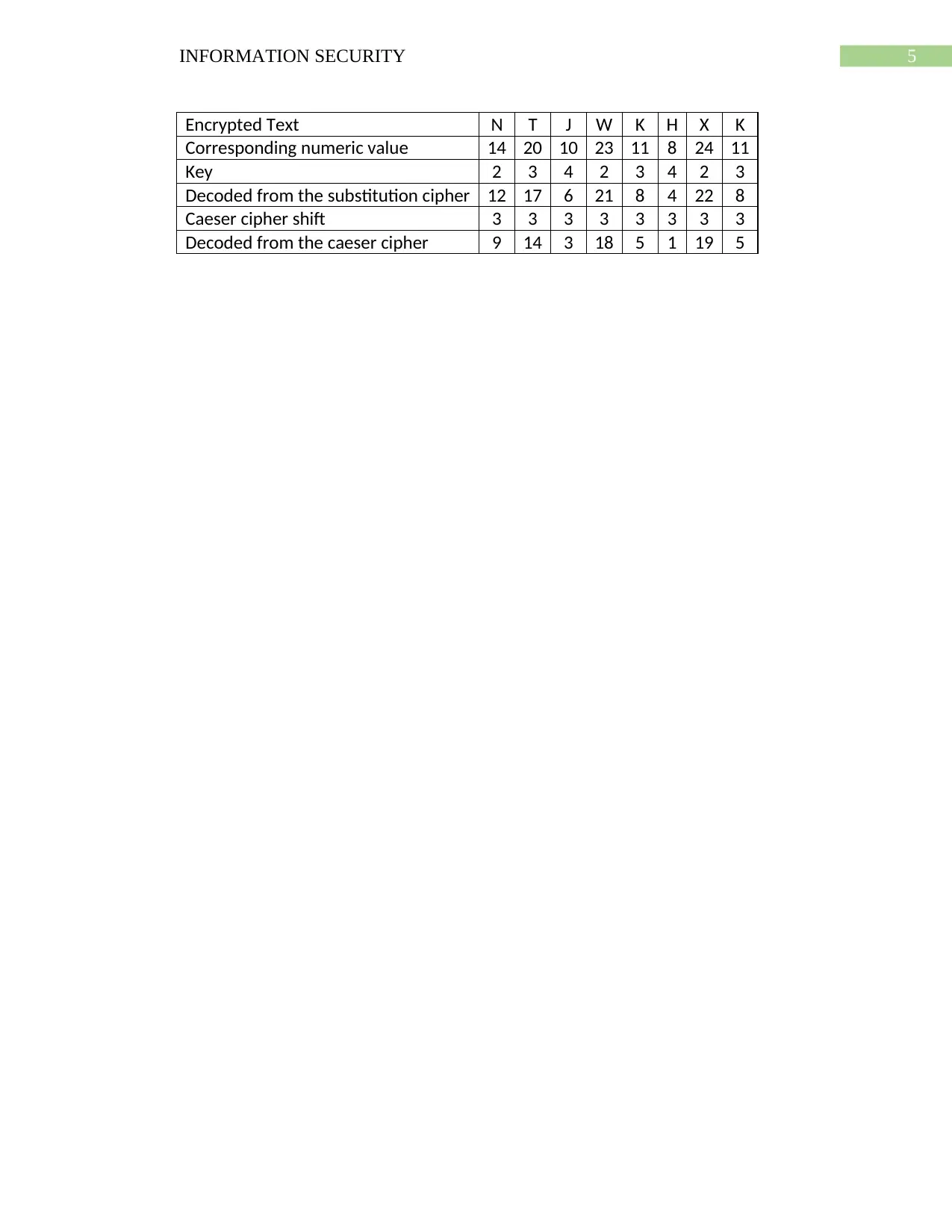
5INFORMATION SECURITY
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
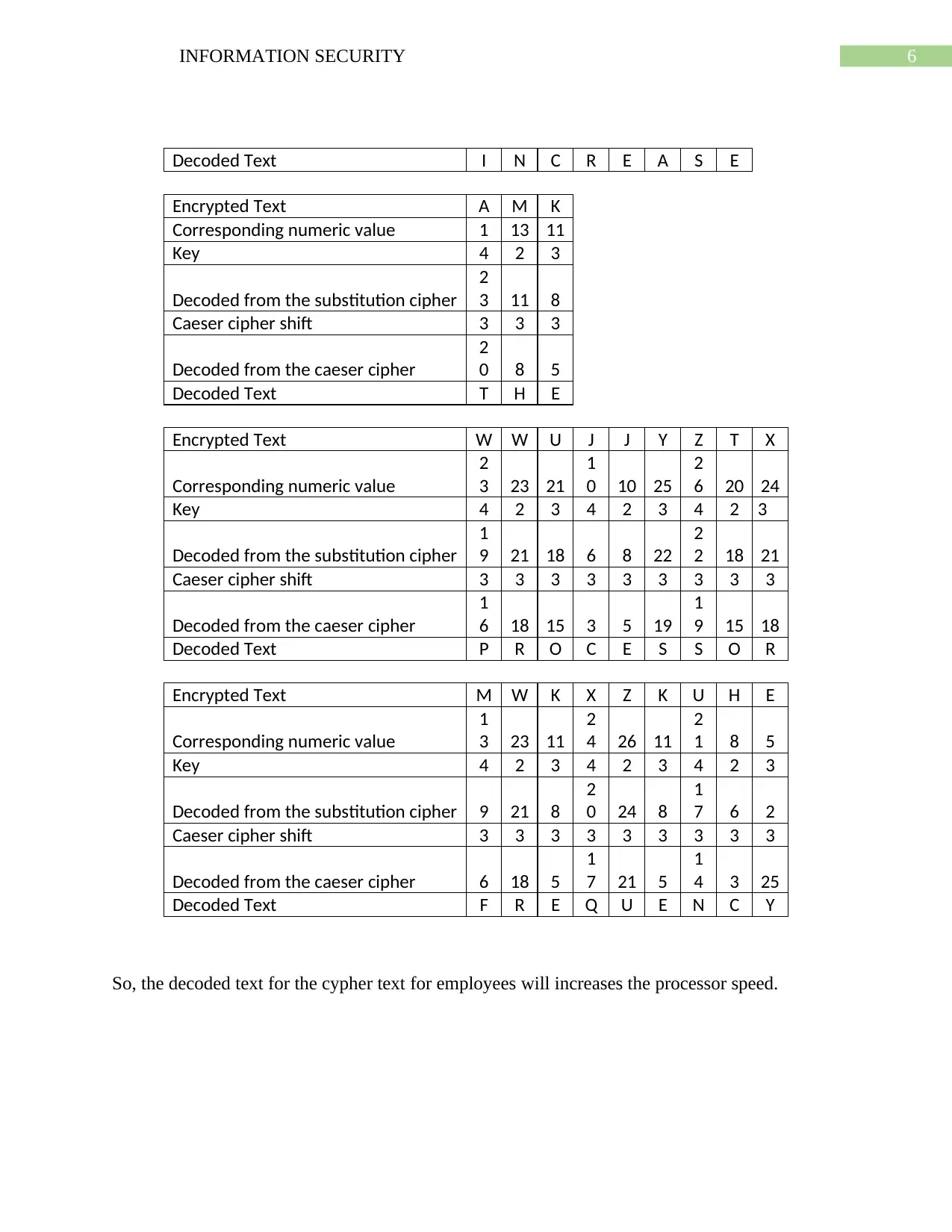
6INFORMATION SECURITY
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher
2
3 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher
2
0 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value
2
3 23 21
1
0 10 25
2
6 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher
1
9 21 18 6 8 22
2
2 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher
1
6 18 15 3 5 19
1
9 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value
1
3 23 11
2
4 26 11
2
1 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8
2
0 24 8
1
7 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5
1
7 21 5
1
4 3 25
Decoded Text F R E Q U E N C Y
So, the decoded text for the cypher text for employees will increases the processor speed.
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher
2
3 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher
2
0 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value
2
3 23 21
1
0 10 25
2
6 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher
1
9 21 18 6 8 22
2
2 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher
1
6 18 15 3 5 19
1
9 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value
1
3 23 11
2
4 26 11
2
1 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8
2
0 24 8
1
7 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5
1
7 21 5
1
4 3 25
Decoded Text F R E Q U E N C Y
So, the decoded text for the cypher text for employees will increases the processor speed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY
References
Hadid, A., Evans, N., Marcel, S., & Fierrez, J. (2015). Biometrics systems under spoofing attack:
an evaluation methodology and lessons learned. IEEE Signal Processing
Magazine, 32(5), 20-30.
Prasanthi, B. V., Jyothi, U. P., Sridevi, B., & Krishna, T. V. (2014). Security Enhancement of
ATM System with Fingerprint and DNA Data. International Journal of Advanced
Research in Computer Science and Software Engineering.
Montefusco, P., Casar, R., Stelkens-Kobsch, T. H., & Koelle, R. (2016). Addressing security in
the ATM environment.
Asgari, H., Stelkens-Kobsch, T. H., Montefusco, P., Abhaya, L., Koelle, R., Markarian, G., &
D'Auria, G. (2017). Provisioning for a distributed ATM security management: The
GAMMA approach. IEEE Aerospace and Electronic Systems Magazine, 32(11), 5-21.
Prasanthi, B. V., Jyothi, U. P., Sridevi, B., & Krishna, T. V. (2014). Security Enhancement of
ATM System with Fingerprint and DNA Data. International Journal of Advanced
Research in Computer Science and Software Engineering.
Haque, M. A., Nasrollahi, K., & Moeslund, T. B. (2015, June). Heartbeat signal from facial
video for biometric recognition. In Scandinavian Conference on Image Analysis (pp. 165-
174). Springer, Cham.
References
Hadid, A., Evans, N., Marcel, S., & Fierrez, J. (2015). Biometrics systems under spoofing attack:
an evaluation methodology and lessons learned. IEEE Signal Processing
Magazine, 32(5), 20-30.
Prasanthi, B. V., Jyothi, U. P., Sridevi, B., & Krishna, T. V. (2014). Security Enhancement of
ATM System with Fingerprint and DNA Data. International Journal of Advanced
Research in Computer Science and Software Engineering.
Montefusco, P., Casar, R., Stelkens-Kobsch, T. H., & Koelle, R. (2016). Addressing security in
the ATM environment.
Asgari, H., Stelkens-Kobsch, T. H., Montefusco, P., Abhaya, L., Koelle, R., Markarian, G., &
D'Auria, G. (2017). Provisioning for a distributed ATM security management: The
GAMMA approach. IEEE Aerospace and Electronic Systems Magazine, 32(11), 5-21.
Prasanthi, B. V., Jyothi, U. P., Sridevi, B., & Krishna, T. V. (2014). Security Enhancement of
ATM System with Fingerprint and DNA Data. International Journal of Advanced
Research in Computer Science and Software Engineering.
Haque, M. A., Nasrollahi, K., & Moeslund, T. B. (2015, June). Heartbeat signal from facial
video for biometric recognition. In Scandinavian Conference on Image Analysis (pp. 165-
174). Springer, Cham.

8INFORMATION SECURITY
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




