Information Security Assignment - Solutions and Analysis
VerifiedAdded on 2023/04/20
|8
|2208
|366
Homework Assignment
AI Summary
This document presents a comprehensive analysis of an information security assignment, providing solutions to various problems. The assignment covers topics such as ATM security, addressing confidentiality, integrity, and availability; biometric authentication, exploring public reluctance and counterarguments, and the implications of false positives and negatives. Additionally, the document delves into cryptographic methods, specifically transposition ciphers, outlining a step-by-step approach to cracking them. The solutions are well-structured, referencing relevant sources, and adhering to APA guidelines. Overall, the assignment provides a thorough understanding of key concepts in information security, offering valuable insights into practical security challenges and their mitigation strategies. This resource is ideal for students seeking to deepen their understanding of information security principles and practices. Desklib provides past papers and solved assignments to help students succeed.

Running Head: INFO SECURITY
0
IT Write Up
Information Security
(Student details :)
4/1/2019
0
IT Write Up
Information Security
(Student details :)
4/1/2019
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Info Security
1
Contents
IT Write Up: Information Security............................................................................................2
Solution 1...................................................................................................................................2
Solution 2...................................................................................................................................3
Solution 3...................................................................................................................................3
Solution 4...................................................................................................................................5
Solution 5...................................................................................................................................5
References..................................................................................................................................6
1
Contents
IT Write Up: Information Security............................................................................................2
Solution 1...................................................................................................................................2
Solution 2...................................................................................................................................3
Solution 3...................................................................................................................................3
Solution 4...................................................................................................................................5
Solution 5...................................................................................................................................5
References..................................................................................................................................6

Info Security
2
IT Write Up: Information Security
Solution 1
Within the systems like ATMs, system has to keep personal identification numbers
(PINs) confidential, in the host system as well as while doing transmission for a transaction.
In addition, system must protect the integrity of the account records along with the individual
transactions. In the context of confidentiality requirements examples, the communication
channels amid the ATMs as well as the bank must be encrypted for the confidentiality
purposes. In addition, whenever the PINs are required they must be encrypted as a major
confidentiality requirement. As we discussed, integrity of info within such systems refers to
protecting info from being changed by illegal parties. In this way, integrity requirements
suggest that the actions executed by the ATMs must be related to the bank accounts
associated with the cards. Moreover, availability of info within ATM machines refers to
assuring that all authorized parties are capable to access the info whenever needed. Hence,
availability requirements within ATMs suggest that the system has to be capable to serve at
least X concurrent consumers at a given time. Additionally, another example of availability
requirement is that the systems must be available 99.9 per cent of the time for both users as
well as administration.
On the other hand, all three requirements which are discussed above are important for
the system’s efficient working. In this context, confidentiality is important with a majorly
high degree as info has value in the form of bank account statements, debit or card numbers,
personal info, trade secrets, as well as government documents. In this way, by stealing such
info anybody can steal the life assets of an individual hence everyone wants to keep their info
a secret. In this way, protection of such info in such systems which is known as
confidentiality owns a major importance within information security systems (Tiwana &
Konsynski, 2010). In addition, info carries value only if it is correct and useful hence data
and info integrity is equally important as confidentiality while securing info in a system
(Peffers, Tuunanen, Rothenberger, & Chatterjee, 2009). Likewise, info only has some value
when the right people can retrieve it at the right time hence availability is also carrying the
same degree of importance as two of the above (Vacca, 2012).
2
IT Write Up: Information Security
Solution 1
Within the systems like ATMs, system has to keep personal identification numbers
(PINs) confidential, in the host system as well as while doing transmission for a transaction.
In addition, system must protect the integrity of the account records along with the individual
transactions. In the context of confidentiality requirements examples, the communication
channels amid the ATMs as well as the bank must be encrypted for the confidentiality
purposes. In addition, whenever the PINs are required they must be encrypted as a major
confidentiality requirement. As we discussed, integrity of info within such systems refers to
protecting info from being changed by illegal parties. In this way, integrity requirements
suggest that the actions executed by the ATMs must be related to the bank accounts
associated with the cards. Moreover, availability of info within ATM machines refers to
assuring that all authorized parties are capable to access the info whenever needed. Hence,
availability requirements within ATMs suggest that the system has to be capable to serve at
least X concurrent consumers at a given time. Additionally, another example of availability
requirement is that the systems must be available 99.9 per cent of the time for both users as
well as administration.
On the other hand, all three requirements which are discussed above are important for
the system’s efficient working. In this context, confidentiality is important with a majorly
high degree as info has value in the form of bank account statements, debit or card numbers,
personal info, trade secrets, as well as government documents. In this way, by stealing such
info anybody can steal the life assets of an individual hence everyone wants to keep their info
a secret. In this way, protection of such info in such systems which is known as
confidentiality owns a major importance within information security systems (Tiwana &
Konsynski, 2010). In addition, info carries value only if it is correct and useful hence data
and info integrity is equally important as confidentiality while securing info in a system
(Peffers, Tuunanen, Rothenberger, & Chatterjee, 2009). Likewise, info only has some value
when the right people can retrieve it at the right time hence availability is also carrying the
same degree of importance as two of the above (Vacca, 2012).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Info Security
3
Solution 2
As per the scenario, the thief broke into an ATM machine utilising a screwdriver as
well as jammed the card reader while breaking 5 keys from the ATM keypad. While he was
attempting to steal the money, he had to halt the procedure of break-in and hide because a
customer reached for using the ATM in order to withdraw money. Later then, arrived
customer successfully drew money after entering his or her ATM card as well as using the 4
digit PIN. As thief already jammed the card reader, hence the customer could not withdraw
the ATM card, and hence drove off to ask for some help. In this way, during the meantime,
thief came back as well as decided to attempt to crack the customer’s PIN for stealing money
from that customer. Here, if calculation over the maximum number of PINs which the thief
might have to enter prior correctly cracking the customer’s PIN suggests that:
As we know that total number of keys in a ATM = 10 (0,1,2,3,4,5,6,7,8,9). However,
the thief already tried out 5 keys, thus only 5 keys are left now.
Therefore, n=5. (5 keys are left to be used for cracking the customer’s ATM PIN)
Besides, we know that p=4 (as 4 digits are utilised for ATM PIN)
Provided that repetition is allowed while attempting for cracking the ATM PIN.
In this way, through applying permutation formula maximum number of the PINs to
be entered by the thief for stealing the customer’s money can be calculated as:
Thus, maximum numbers of pins to be entered by the thief are 624, as out of all 625,
one of the possible permutations is the customer or card holder’s pin itself.
Solution 3
While thinking about bio-metric authentication system, there are many reasons why
public is reluctant for using bio-metrics. On the other hand, there are also so many ways of
countering those objections of people while using bio-metric authentication (Yeh & Chang,
2007). First of all, when there will be no biometric authentication then it would be a critical
problem for the owners of the firms. People may be reluctant towards using this
authentication system because of their careless attitude towards work. For an example, many
3
Solution 2
As per the scenario, the thief broke into an ATM machine utilising a screwdriver as
well as jammed the card reader while breaking 5 keys from the ATM keypad. While he was
attempting to steal the money, he had to halt the procedure of break-in and hide because a
customer reached for using the ATM in order to withdraw money. Later then, arrived
customer successfully drew money after entering his or her ATM card as well as using the 4
digit PIN. As thief already jammed the card reader, hence the customer could not withdraw
the ATM card, and hence drove off to ask for some help. In this way, during the meantime,
thief came back as well as decided to attempt to crack the customer’s PIN for stealing money
from that customer. Here, if calculation over the maximum number of PINs which the thief
might have to enter prior correctly cracking the customer’s PIN suggests that:
As we know that total number of keys in a ATM = 10 (0,1,2,3,4,5,6,7,8,9). However,
the thief already tried out 5 keys, thus only 5 keys are left now.
Therefore, n=5. (5 keys are left to be used for cracking the customer’s ATM PIN)
Besides, we know that p=4 (as 4 digits are utilised for ATM PIN)
Provided that repetition is allowed while attempting for cracking the ATM PIN.
In this way, through applying permutation formula maximum number of the PINs to
be entered by the thief for stealing the customer’s money can be calculated as:
Thus, maximum numbers of pins to be entered by the thief are 624, as out of all 625,
one of the possible permutations is the customer or card holder’s pin itself.
Solution 3
While thinking about bio-metric authentication system, there are many reasons why
public is reluctant for using bio-metrics. On the other hand, there are also so many ways of
countering those objections of people while using bio-metric authentication (Yeh & Chang,
2007). First of all, when there will be no biometric authentication then it would be a critical
problem for the owners of the firms. People may be reluctant towards using this
authentication system because of their careless attitude towards work. For an example, many
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Info Security
4
government workers wants to work within a workplace where there is no biometric
authentication system installed (Clodfelter, 2010).
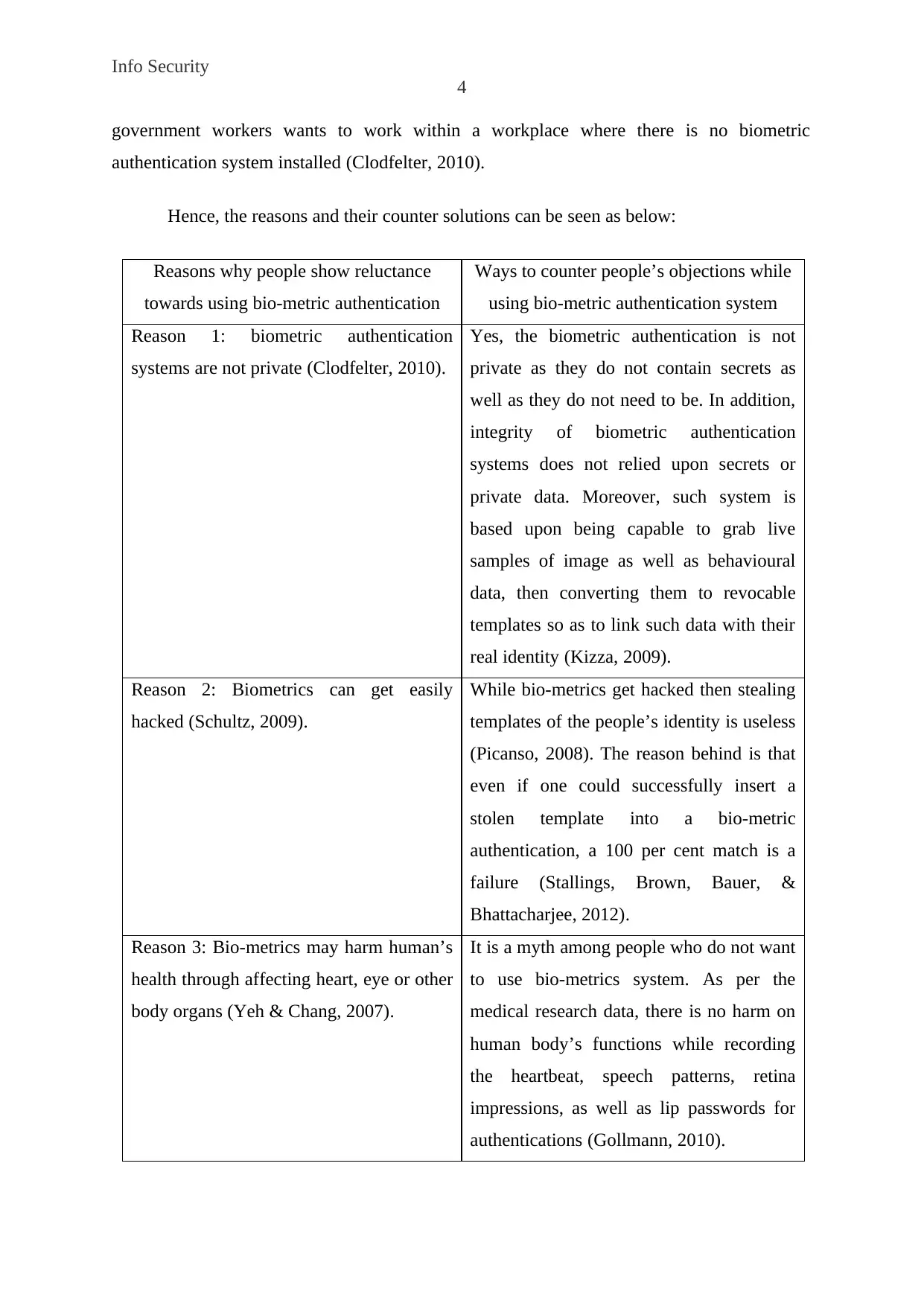
Hence, the reasons and their counter solutions can be seen as below:
Reasons why people show reluctance
towards using bio-metric authentication
Ways to counter people’s objections while
using bio-metric authentication system
Reason 1: biometric authentication
systems are not private (Clodfelter, 2010).
Yes, the biometric authentication is not
private as they do not contain secrets as
well as they do not need to be. In addition,
integrity of biometric authentication
systems does not relied upon secrets or
private data. Moreover, such system is
based upon being capable to grab live
samples of image as well as behavioural
data, then converting them to revocable
templates so as to link such data with their
real identity (Kizza, 2009).
Reason 2: Biometrics can get easily
hacked (Schultz, 2009).
While bio-metrics get hacked then stealing
templates of the people’s identity is useless
(Picanso, 2008). The reason behind is that
even if one could successfully insert a
stolen template into a bio-metric
authentication, a 100 per cent match is a
failure (Stallings, Brown, Bauer, &
Bhattacharjee, 2012).
Reason 3: Bio-metrics may harm human’s
health through affecting heart, eye or other
body organs (Yeh & Chang, 2007).
It is a myth among people who do not want
to use bio-metrics system. As per the
medical research data, there is no harm on
human body’s functions while recording
the heartbeat, speech patterns, retina
impressions, as well as lip passwords for
authentications (Gollmann, 2010).
4
government workers wants to work within a workplace where there is no biometric
authentication system installed (Clodfelter, 2010).
Hence, the reasons and their counter solutions can be seen as below:
Reasons why people show reluctance
towards using bio-metric authentication
Ways to counter people’s objections while
using bio-metric authentication system
Reason 1: biometric authentication
systems are not private (Clodfelter, 2010).
Yes, the biometric authentication is not
private as they do not contain secrets as
well as they do not need to be. In addition,
integrity of biometric authentication
systems does not relied upon secrets or
private data. Moreover, such system is
based upon being capable to grab live
samples of image as well as behavioural
data, then converting them to revocable
templates so as to link such data with their
real identity (Kizza, 2009).
Reason 2: Biometrics can get easily
hacked (Schultz, 2009).
While bio-metrics get hacked then stealing
templates of the people’s identity is useless
(Picanso, 2008). The reason behind is that
even if one could successfully insert a
stolen template into a bio-metric
authentication, a 100 per cent match is a
failure (Stallings, Brown, Bauer, &
Bhattacharjee, 2012).
Reason 3: Bio-metrics may harm human’s
health through affecting heart, eye or other
body organs (Yeh & Chang, 2007).
It is a myth among people who do not want
to use bio-metrics system. As per the
medical research data, there is no harm on
human body’s functions while recording
the heartbeat, speech patterns, retina
impressions, as well as lip passwords for
authentications (Gollmann, 2010).

Info Security
5
In this way, in this way using bio-metrics within this modern era is essential so that
people cannot cheat their organizations as well as their own career (Howell, 2017).
Solution 4
In case of bio-metric authentication, false negative as well as false positive rates are
often complementary because raising one will lower the other. However, false negatives are
significantly more serious than false positives and the same can be explained with the help of
two circumstances discussed below.
In a case, when the biometric authentication is utilised being the main authentication
way to enter a premises, then it may harm the assets of an organization. Hence, if fingerprints
of some individual are being utilized as the recognizable proof for differentiating
lawbreakers, then false antagonistic may result in right individual being charged (Datta &
Zhao, 2009). In this way, a false negative of biometrics occurred as biometric systems got
failed to recognize the wrong individual, which would have stolen or harm some asset of the
organization. In this way, two cases which can demonstrate that false negatives of bio-metrics
are more serious than false positives are as follows:
Case I: in case of a medical emergency, if a person got faint while working in the data center
and X person wants to enter in data center to take that fainted person to CPR but he could not
access the data center and the person died because of false negative of the bio-metrics. On the
other hand, X person could easily enter by logging in to authentication and saved a life of the
fainted employee then it will consider as a false positive of bio-metrics. Thus, in this
circumstance false negative is more serious than false positive (Howell, 2017).
Case II: when bio-metrics is supposed to authenticate a regular employee X and it does not,
which hindered his or her work then it is a false negative. While bio-metrics falsely
authenticated an employee who was new at the workplace then it is false positive. Thus, false
negative is much serious than false positive (Clodfelter, 2010).
Solution 5
Within the field of cryptography, transposition cipher is a kind of methods of
encryption through which the locations held from units of plaintext get shifted as per a
5
In this way, in this way using bio-metrics within this modern era is essential so that
people cannot cheat their organizations as well as their own career (Howell, 2017).
Solution 4
In case of bio-metric authentication, false negative as well as false positive rates are
often complementary because raising one will lower the other. However, false negatives are
significantly more serious than false positives and the same can be explained with the help of
two circumstances discussed below.
In a case, when the biometric authentication is utilised being the main authentication
way to enter a premises, then it may harm the assets of an organization. Hence, if fingerprints
of some individual are being utilized as the recognizable proof for differentiating
lawbreakers, then false antagonistic may result in right individual being charged (Datta &
Zhao, 2009). In this way, a false negative of biometrics occurred as biometric systems got
failed to recognize the wrong individual, which would have stolen or harm some asset of the
organization. In this way, two cases which can demonstrate that false negatives of bio-metrics
are more serious than false positives are as follows:
Case I: in case of a medical emergency, if a person got faint while working in the data center
and X person wants to enter in data center to take that fainted person to CPR but he could not
access the data center and the person died because of false negative of the bio-metrics. On the
other hand, X person could easily enter by logging in to authentication and saved a life of the
fainted employee then it will consider as a false positive of bio-metrics. Thus, in this
circumstance false negative is more serious than false positive (Howell, 2017).
Case II: when bio-metrics is supposed to authenticate a regular employee X and it does not,
which hindered his or her work then it is a false negative. While bio-metrics falsely
authenticated an employee who was new at the workplace then it is false positive. Thus, false
negative is much serious than false positive (Clodfelter, 2010).
Solution 5
Within the field of cryptography, transposition cipher is a kind of methods of
encryption through which the locations held from units of plaintext get shifted as per a
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Info Security
6
regular system in a way that the cipher text creates a permutation of the plain text. In
addition, the main thing is that the order of the texts is getting changed (Infosec, 2012).
In this way, in given problem we can crack the simple matrix transposition ciphers
with the help of following steps:
Step I: first count how many letters are there within that cipher text (for an instance,
assume the cipher text is 33 letters long)
Step II: create all possible matrices which would fit in such a length and make two
copies of the same.
Step III: for each size matrix, write down the cipher text across the rows over 1 copy.
On the other copy, write out the cipher text down the columns (Infosec, 2012).
Step IV: at every stage, check if anything legible can be found, while reading
perpendicular to how one put the cipher text-in.
References
Clodfelter, R. (2010). Biometric technology in retailing: Will consumers accept fingerprint
authentication? Journal of Retailing and Consumer Services, 17(3), 181-188.
Datta, D., & Zhao, H. (2009). Effect of false positive and false negative rates on inference of
binding target conservation across different conditions and species from ChIP-chip
data. BMC bioinformatics, 10(1), 23.
Gollmann, D. (2010). Computer Security. Wiley Interdisciplinary Reviews: Computational
Statistics, 2(5), 544-554.
Howell, K. (2017, 08 28). 3 Problems With Biometric Security, Including Fingerprint ID.
Retrieved from IP Switch: https://blog.ipswitch.com/3-reasons-biometrics-are-not-
secure
Kizza, J. (2009). Guide to computer network security. London: Springer.
Peffers, K., Tuunanen, T., Rothenberger, M., & Chatterjee, S. (2009). A design science
research methodology for information systems research. Journal of managemene
information systems, 24(3), 45-77.
6
regular system in a way that the cipher text creates a permutation of the plain text. In
addition, the main thing is that the order of the texts is getting changed (Infosec, 2012).
In this way, in given problem we can crack the simple matrix transposition ciphers
with the help of following steps:
Step I: first count how many letters are there within that cipher text (for an instance,
assume the cipher text is 33 letters long)
Step II: create all possible matrices which would fit in such a length and make two
copies of the same.
Step III: for each size matrix, write down the cipher text across the rows over 1 copy.
On the other copy, write out the cipher text down the columns (Infosec, 2012).
Step IV: at every stage, check if anything legible can be found, while reading
perpendicular to how one put the cipher text-in.
References
Clodfelter, R. (2010). Biometric technology in retailing: Will consumers accept fingerprint
authentication? Journal of Retailing and Consumer Services, 17(3), 181-188.
Datta, D., & Zhao, H. (2009). Effect of false positive and false negative rates on inference of
binding target conservation across different conditions and species from ChIP-chip
data. BMC bioinformatics, 10(1), 23.
Gollmann, D. (2010). Computer Security. Wiley Interdisciplinary Reviews: Computational
Statistics, 2(5), 544-554.
Howell, K. (2017, 08 28). 3 Problems With Biometric Security, Including Fingerprint ID.
Retrieved from IP Switch: https://blog.ipswitch.com/3-reasons-biometrics-are-not-
secure
Kizza, J. (2009). Guide to computer network security. London: Springer.
Peffers, K., Tuunanen, T., Rothenberger, M., & Chatterjee, S. (2009). A design science
research methodology for information systems research. Journal of managemene
information systems, 24(3), 45-77.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Info Security
7
Picanso, K. (2008). Protecting information security under a uniform data breach notification
law. Fordham L.(Rev.), 355.
Schultz, R. (2009). Contemporary issues in ethics and information technology (Ed. ed.).
London: IGI Global.
Stallings, W., Brown, L., Bauer, M., & Bhattacharjee, A. (2012). Computer security:
principles and practice. NJ: Pearson Education.
Tiwana, A., & Konsynski, B. (2010). Complementarities between organizational IT
architecture and governance structure. Information Systems Research, 21(2), 288-304.
Vacca, J. (2012). Computer and information security handbook. London: Newnes.
Yeh, Q., & Chang, A. (2007). Threats and countermeasures for information system security:
A cross-industry study. Information & Management, 44(5), 480-491.
7
Picanso, K. (2008). Protecting information security under a uniform data breach notification
law. Fordham L.(Rev.), 355.
Schultz, R. (2009). Contemporary issues in ethics and information technology (Ed. ed.).
London: IGI Global.
Stallings, W., Brown, L., Bauer, M., & Bhattacharjee, A. (2012). Computer security:
principles and practice. NJ: Pearson Education.
Tiwana, A., & Konsynski, B. (2010). Complementarities between organizational IT
architecture and governance structure. Information Systems Research, 21(2), 288-304.
Vacca, J. (2012). Computer and information security handbook. London: Newnes.
Yeh, Q., & Chang, A. (2007). Threats and countermeasures for information system security:
A cross-industry study. Information & Management, 44(5), 480-491.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





