AM851001: Analysis of Atlassian Information Security Report
VerifiedAdded on 2022/08/18
|23
|5947
|20
Report
AI Summary
This report provides a comprehensive analysis of Atlassian's information security landscape. It begins by examining the existing network design, highlighting its reliance on AWS and the use of multiple AWS VPCs. The report then delves into specific security threats, including identity spoofing, data tampering, and vulnerabilities related to JIRA software. A detailed risk assessment is conducted, encompassing the identification of risks, vulnerabilities, and threats, along with an evaluation of their likelihood and impact. The report also outlines a crisis management plan and a business continuity plan, emphasizing business prioritization and the redesign of network architecture. Further sections cover data storage, Infrastructure as a Service (IaaS), and data security measures. The report concludes with recommendations for enhancing Atlassian's security posture.

Atlassian Information Security Report
Student’s name
Institution Affiliation(s)
Student’s name
Institution Affiliation(s)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
The Existing Atlassian’s Network Design.................................................................................2
Spoofing Identity....................................................................................................................3
Tampering with data...............................................................................................................3
Risk assessment..........................................................................................................................4
Threat to Traditional Network Security of Atlassian.................................................................6
Crisis Management Plan.........................................................................................................6
Business continuity plan............................................................................................................7
Business Prioritization............................................................................................................7
Redesigning of network architecture.........................................................................................7
Integration of the ERP solutions.............................................................................................8
Server management................................................................................................................8
Proactive support and management........................................................................................9
Data storage..........................................................................................................................10
Iaas........................................................................................................................................10
Data Security........................................................................................................................13
Conclusion................................................................................................................................14
References................................................................................................................................16
Table of Figures
Figure 1: Network POPs........................................................................................................................2
Figure 2: Prioritization Matrix (Source: Hessami et al., 2019).............................................................7
Figure 3: Example of ERP solutions (Source: Hwang & Grant, 2016).................................................8
Figure 4: Server Management (Source: Sun et al., 2014)......................................................................9
Figure 5: Diagram of a storage array (Source: Search Storage, 2018).................................................10
Figure 6: Infrastructure as a service (IaaS) (Source: Miles Web, 2019)..............................................11
Figure 7: DevCloud (Source: Yadav, 2019)........................................................................................12
Figure 8: Data Storage Management (Source: Sun et al., 2014).........................................................14
1
The Existing Atlassian’s Network Design.................................................................................2
Spoofing Identity....................................................................................................................3
Tampering with data...............................................................................................................3
Risk assessment..........................................................................................................................4
Threat to Traditional Network Security of Atlassian.................................................................6
Crisis Management Plan.........................................................................................................6
Business continuity plan............................................................................................................7
Business Prioritization............................................................................................................7
Redesigning of network architecture.........................................................................................7
Integration of the ERP solutions.............................................................................................8
Server management................................................................................................................8
Proactive support and management........................................................................................9
Data storage..........................................................................................................................10
Iaas........................................................................................................................................10
Data Security........................................................................................................................13
Conclusion................................................................................................................................14
References................................................................................................................................16
Table of Figures
Figure 1: Network POPs........................................................................................................................2
Figure 2: Prioritization Matrix (Source: Hessami et al., 2019).............................................................7
Figure 3: Example of ERP solutions (Source: Hwang & Grant, 2016).................................................8
Figure 4: Server Management (Source: Sun et al., 2014)......................................................................9
Figure 5: Diagram of a storage array (Source: Search Storage, 2018).................................................10
Figure 6: Infrastructure as a service (IaaS) (Source: Miles Web, 2019)..............................................11
Figure 7: DevCloud (Source: Yadav, 2019)........................................................................................12
Figure 8: Data Storage Management (Source: Sun et al., 2014).........................................................14
1
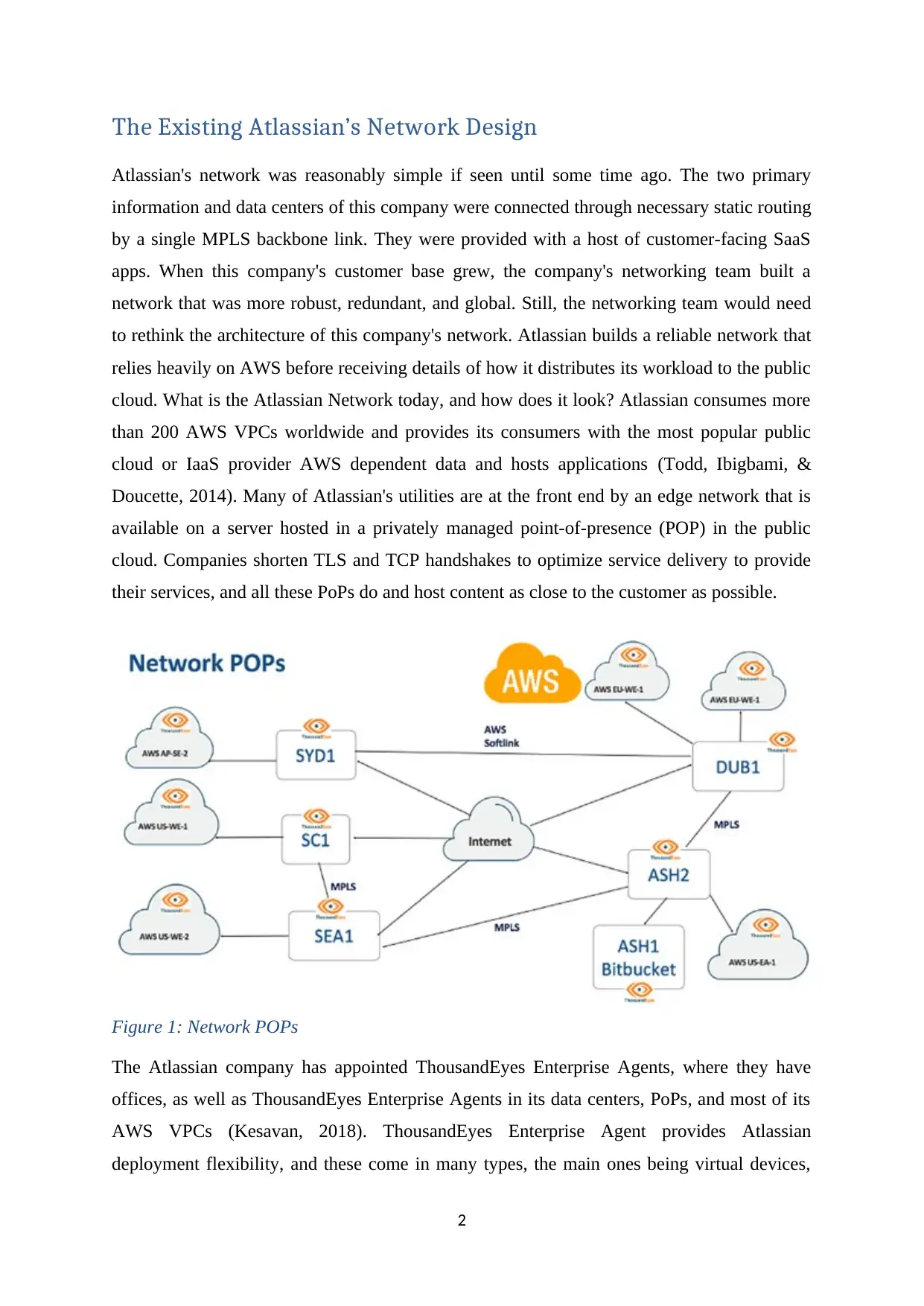
The Existing Atlassian’s Network Design
Atlassian's network was reasonably simple if seen until some time ago. The two primary
information and data centers of this company were connected through necessary static routing
by a single MPLS backbone link. They were provided with a host of customer-facing SaaS
apps. When this company's customer base grew, the company's networking team built a
network that was more robust, redundant, and global. Still, the networking team would need
to rethink the architecture of this company's network. Atlassian builds a reliable network that
relies heavily on AWS before receiving details of how it distributes its workload to the public
cloud. What is the Atlassian Network today, and how does it look? Atlassian consumes more
than 200 AWS VPCs worldwide and provides its consumers with the most popular public
cloud or IaaS provider AWS dependent data and hosts applications (Todd, Ibigbami, &
Doucette, 2014). Many of Atlassian's utilities are at the front end by an edge network that is
available on a server hosted in a privately managed point-of-presence (POP) in the public
cloud. Companies shorten TLS and TCP handshakes to optimize service delivery to provide
their services, and all these PoPs do and host content as close to the customer as possible.
Figure 1: Network POPs
The Atlassian company has appointed ThousandEyes Enterprise Agents, where they have
offices, as well as ThousandEyes Enterprise Agents in its data centers, PoPs, and most of its
AWS VPCs (Kesavan, 2018). ThousandEyes Enterprise Agent provides Atlassian
deployment flexibility, and these come in many types, the main ones being virtual devices,
2
Atlassian's network was reasonably simple if seen until some time ago. The two primary
information and data centers of this company were connected through necessary static routing
by a single MPLS backbone link. They were provided with a host of customer-facing SaaS
apps. When this company's customer base grew, the company's networking team built a
network that was more robust, redundant, and global. Still, the networking team would need
to rethink the architecture of this company's network. Atlassian builds a reliable network that
relies heavily on AWS before receiving details of how it distributes its workload to the public
cloud. What is the Atlassian Network today, and how does it look? Atlassian consumes more
than 200 AWS VPCs worldwide and provides its consumers with the most popular public
cloud or IaaS provider AWS dependent data and hosts applications (Todd, Ibigbami, &
Doucette, 2014). Many of Atlassian's utilities are at the front end by an edge network that is
available on a server hosted in a privately managed point-of-presence (POP) in the public
cloud. Companies shorten TLS and TCP handshakes to optimize service delivery to provide
their services, and all these PoPs do and host content as close to the customer as possible.
Figure 1: Network POPs
The Atlassian company has appointed ThousandEyes Enterprise Agents, where they have
offices, as well as ThousandEyes Enterprise Agents in its data centers, PoPs, and most of its
AWS VPCs (Kesavan, 2018). ThousandEyes Enterprise Agent provides Atlassian
deployment flexibility, and these come in many types, the main ones being virtual devices,
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Linux packages, or Docker containers. MPLS gives broad visibility of connectivity across
backbones, Internet links, load-balancers, and AWS VPCs and provides global coverage of
agents within Atlassian's network. Ever since the introduction of JIRA software, it has
separately increased the potential for cybersecurity threats to Atlassian Corporation's
database; however, the company has introduced strict policies against threats to the security
of the database (Kumar & Kumar, 2014).
A remote code execution (RCE) risk on an unmatched system has been discovered by
Atlassian Corporation's high-tech experts, which Atlassian Corporation has undertaken to
introduce various security criteria and programs for data security. Because the company does
not have highly experienced technical experts available, there are several versions available
for Confluence Servers and Confluent Data Center affected servers concerning cybersecurity
to address such sudden issues in various versions. For instance, versions 6.7.0 are before
6.12.3 (fixed version for 6.12.x), versions 6.13.0 are earlier than 6.13.3 (the fixed version for
6.13). x), and from version 6.14.0 before 6.14.2 (fixed version for 6.14.x) (Li, Huang, Wang,
& Li, 2019)
Spoofing Identity
CVE-2019-11581 is a system through which an attacker can hack the system. The
introduction of server-side template injection vulnerability is in version 4.4.0 of JIRA Server
and Data Center (Smyth, 2019). This fault may work if the JIRA Administrator has access to
the attack or if the Contact Administrator forms are enabled or if the SMTP server is
configured in JIRA. Attackers can exploit the JIRA server or data center version, and all of
this is possible without any authentication (Jiang, Zhao, Li, Zhao, & Du, 2020).
Tampering with data
The threat against the Atlassian domain was found, and its announcement through the
cyberspace twitter account done in December 2019 (Security Experts, 2019). Standard SSL is
resolved on any local server with a certificate, and the company's domain is bound to the
Confluence Cloud service which can redirect app traffic to malware, and this flaw enables an
experienced attacker to induce a threat (Panda, 2020).
Even though the bug abundance program has been intended to decrease the helplessness
worry in the IT business, at that point, likewise, there is nothing 100% secure. These
programs rely heavily on the quality of the researchers when they are designing and testing
3
backbones, Internet links, load-balancers, and AWS VPCs and provides global coverage of
agents within Atlassian's network. Ever since the introduction of JIRA software, it has
separately increased the potential for cybersecurity threats to Atlassian Corporation's
database; however, the company has introduced strict policies against threats to the security
of the database (Kumar & Kumar, 2014).
A remote code execution (RCE) risk on an unmatched system has been discovered by
Atlassian Corporation's high-tech experts, which Atlassian Corporation has undertaken to
introduce various security criteria and programs for data security. Because the company does
not have highly experienced technical experts available, there are several versions available
for Confluence Servers and Confluent Data Center affected servers concerning cybersecurity
to address such sudden issues in various versions. For instance, versions 6.7.0 are before
6.12.3 (fixed version for 6.12.x), versions 6.13.0 are earlier than 6.13.3 (the fixed version for
6.13). x), and from version 6.14.0 before 6.14.2 (fixed version for 6.14.x) (Li, Huang, Wang,
& Li, 2019)
Spoofing Identity
CVE-2019-11581 is a system through which an attacker can hack the system. The
introduction of server-side template injection vulnerability is in version 4.4.0 of JIRA Server
and Data Center (Smyth, 2019). This fault may work if the JIRA Administrator has access to
the attack or if the Contact Administrator forms are enabled or if the SMTP server is
configured in JIRA. Attackers can exploit the JIRA server or data center version, and all of
this is possible without any authentication (Jiang, Zhao, Li, Zhao, & Du, 2020).
Tampering with data
The threat against the Atlassian domain was found, and its announcement through the
cyberspace twitter account done in December 2019 (Security Experts, 2019). Standard SSL is
resolved on any local server with a certificate, and the company's domain is bound to the
Confluence Cloud service which can redirect app traffic to malware, and this flaw enables an
experienced attacker to induce a threat (Panda, 2020).
Even though the bug abundance program has been intended to decrease the helplessness
worry in the IT business, at that point, likewise, there is nothing 100% secure. These
programs rely heavily on the quality of the researchers when they are designing and testing
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the loops in them. Here, the primary concern comes as Atlassian has an issue with the
accessibility of the exceptionally experienced human asset that can handle the circumstance
successfully. Because of which there is always space for an event of such breaks in the
security procedure that are getting sent in the bug abundance programs because of which the
organization is at some point getting non-causing suddenly for their clients to determine their
issues while utilizing organization programming software (Hryb, 2018).
Risk assessment
The continuity planning team of business must prepare a management study of risk and
analysis report which involve a variety of possible tragedies and these disasters involve
human, technical and natural threats. Input to the Impact analysis phase of business will be
the main output of these studies. In all the initiatives related to the continuity of business, the
starting point is risk assessment because it helps to recognize the scenarios and scope which
is attempting by the company to mitigate (Chen & Cheng, 2018).
To perform the risk analysis, major steps are:
a) Identify the risks
b) Make an estimation of the likelihood of occurrence
c) Evaluate and prioritize the risks
d) Create a report of the identified risks and vulnerabilities
e) Identifying risks, vulnerabilities, and threats
When identifying those vulnerabilities that a network is susceptible to, the discovery stage is
critical as it gives the network analyst the devices or network nodes that should be included in
the risk assessment. As there is a possibility of having an unauthorized node in a network,
special network tools like the IP scanning tools, port scanners, and DNS enumeration should
be used. Using the IP scanning tool, we will be able to determine the nodes that reside within
specified subnets. Listing out those nodes, we can use a port scanning tool to determine the
OS or any running services on that node (Aven, 2016). Finally, using DNS, we can extend
our information gathering to include the DNS names of the nodes we discover as well as
determine any additional subnets that may have been missed during the IP discovery phase.
Information collected during the previous step is the latest and includes all the systems that
may be on during that day, which may mean performing multiple scans during different times
4
accessibility of the exceptionally experienced human asset that can handle the circumstance
successfully. Because of which there is always space for an event of such breaks in the
security procedure that are getting sent in the bug abundance programs because of which the
organization is at some point getting non-causing suddenly for their clients to determine their
issues while utilizing organization programming software (Hryb, 2018).
Risk assessment
The continuity planning team of business must prepare a management study of risk and
analysis report which involve a variety of possible tragedies and these disasters involve
human, technical and natural threats. Input to the Impact analysis phase of business will be
the main output of these studies. In all the initiatives related to the continuity of business, the
starting point is risk assessment because it helps to recognize the scenarios and scope which
is attempting by the company to mitigate (Chen & Cheng, 2018).
To perform the risk analysis, major steps are:
a) Identify the risks
b) Make an estimation of the likelihood of occurrence
c) Evaluate and prioritize the risks
d) Create a report of the identified risks and vulnerabilities
e) Identifying risks, vulnerabilities, and threats
When identifying those vulnerabilities that a network is susceptible to, the discovery stage is
critical as it gives the network analyst the devices or network nodes that should be included in
the risk assessment. As there is a possibility of having an unauthorized node in a network,
special network tools like the IP scanning tools, port scanners, and DNS enumeration should
be used. Using the IP scanning tool, we will be able to determine the nodes that reside within
specified subnets. Listing out those nodes, we can use a port scanning tool to determine the
OS or any running services on that node (Aven, 2016). Finally, using DNS, we can extend
our information gathering to include the DNS names of the nodes we discover as well as
determine any additional subnets that may have been missed during the IP discovery phase.
Information collected during the previous step is the latest and includes all the systems that
may be on during that day, which may mean performing multiple scans during different times
4

of the day/week. As such, it is recommended to establish a baseline of the systems within the
network (Zhang & Alipour, 2019).
Variances within this baseline may indicate abnormal network behaviour. After the
information is collected, we will continue with scanning the systems for any risks or threats
that they are vulnerable to and which can include ensuring the systems are fully patched. The
applications and services that run on them have been updated to the most secure versions.
Operating system patching is a crucial aspect to keep in mind, as OS vendors are continually
releasing updates to their OS to patch those flaws and vulnerabilities as they are discovered.
By not repairing, you are leaving your organization susceptible to flaws being exploited and
data or systems falling into the hands of an attacker.
Establishing a patching process that is followed monthly can help minimize the threat of an
attacker taking advantage of an unpatched system. While a monthly patching cycle will
apply to most patches, it is essential to understand that ad-hoc emergency patching cycles
may be required for high severity patches with the network (Joshi & Singh, 2017).
Network-based scanning of appliances should be employed to ensure that threats originating
from the Internet cannot reach the workstations or servers within the network, which is
accomplished by scanning email messages, web traffic, and level 7 traffic filtering. By
scanning email messages, we can ensure that malicious attachments are stripped at the mail
server rather than relying on the client defences to pick up on these malicious files. Web
content filtering will ensure that malicious sites are not inadvertently visited by the
employees of the organization, which means that if a system does become infected, it cannot
reasonably be able to reach any command and control systems outside of the network
(Häckel, Hänsch, Hertel, & Übelhör, 2019).
By employing multiple layers of defence within the network, it ensures that if one defence
does fail, there are other layers that a malicious application or attacker must traverse before
being able to accomplish the task at hand. Also, by scheduling vulnerability scans to be
performed a set schedule, you will be able to determine where the threats within your
organization reside and establish a plan to mitigate or reduce the risk that systems pose within
the network (Häckel et al., 2019).
5
network (Zhang & Alipour, 2019).
Variances within this baseline may indicate abnormal network behaviour. After the
information is collected, we will continue with scanning the systems for any risks or threats
that they are vulnerable to and which can include ensuring the systems are fully patched. The
applications and services that run on them have been updated to the most secure versions.
Operating system patching is a crucial aspect to keep in mind, as OS vendors are continually
releasing updates to their OS to patch those flaws and vulnerabilities as they are discovered.
By not repairing, you are leaving your organization susceptible to flaws being exploited and
data or systems falling into the hands of an attacker.
Establishing a patching process that is followed monthly can help minimize the threat of an
attacker taking advantage of an unpatched system. While a monthly patching cycle will
apply to most patches, it is essential to understand that ad-hoc emergency patching cycles
may be required for high severity patches with the network (Joshi & Singh, 2017).
Network-based scanning of appliances should be employed to ensure that threats originating
from the Internet cannot reach the workstations or servers within the network, which is
accomplished by scanning email messages, web traffic, and level 7 traffic filtering. By
scanning email messages, we can ensure that malicious attachments are stripped at the mail
server rather than relying on the client defences to pick up on these malicious files. Web
content filtering will ensure that malicious sites are not inadvertently visited by the
employees of the organization, which means that if a system does become infected, it cannot
reasonably be able to reach any command and control systems outside of the network
(Häckel, Hänsch, Hertel, & Übelhör, 2019).
By employing multiple layers of defence within the network, it ensures that if one defence
does fail, there are other layers that a malicious application or attacker must traverse before
being able to accomplish the task at hand. Also, by scheduling vulnerability scans to be
performed a set schedule, you will be able to determine where the threats within your
organization reside and establish a plan to mitigate or reduce the risk that systems pose within
the network (Häckel et al., 2019).
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network security risks and threats for Atlassian Company
a) Encryption
b) Ransomware
c) DDoS attacks
d) Insider threats
e) Cloud security
Encryption
Encryption is a double-edged sword. In recent years, corporations have appeared to protect
sensitive data by way of scrambling communications, which we recognize as encryption.
“End-to-end encryption” can create a false experience of remedy for consumers, Bloomberg
recently reported. The truth is that a hacker can manage the device in a variety of ways, along
with gaining access to the “full discussion regardless of what security precautions are built
into the app you are using.” Encryption gives hackers free rein to operate before their
eventual detection and remediation (Aven, 2016).
Ransomware
Network-based ransomware can cripple systems and data. This threat is especially alarming
as it does not be counted heavily on the human element to execute and carry and cripple a
company. A successful attack may only require an unpatched computer and an automated
software program update. Data can be compromised or misplaced altogether on a
contaminated device. And also, compounding the trouble is the truth that many small to
medium-sized organizations do now not report ransomware attacks as they occur (Aven,
2016). Preventative measures against ransomware include:
a) Using Diverse Backups
b) Keeping Antivirus Up-To-Date
c) Maintaining Patch Updates
d) Installing File and System Integrity Monitoring Software
e) Compliance Maintenance
DDoS attacks
DDoS attacks come at a real cost. The severity and frequency of DDoS assaults have many
network managers concerned. Hackers infiltrate organizations by using flooding web sites
6
a) Encryption
b) Ransomware
c) DDoS attacks
d) Insider threats
e) Cloud security
Encryption
Encryption is a double-edged sword. In recent years, corporations have appeared to protect
sensitive data by way of scrambling communications, which we recognize as encryption.
“End-to-end encryption” can create a false experience of remedy for consumers, Bloomberg
recently reported. The truth is that a hacker can manage the device in a variety of ways, along
with gaining access to the “full discussion regardless of what security precautions are built
into the app you are using.” Encryption gives hackers free rein to operate before their
eventual detection and remediation (Aven, 2016).
Ransomware
Network-based ransomware can cripple systems and data. This threat is especially alarming
as it does not be counted heavily on the human element to execute and carry and cripple a
company. A successful attack may only require an unpatched computer and an automated
software program update. Data can be compromised or misplaced altogether on a
contaminated device. And also, compounding the trouble is the truth that many small to
medium-sized organizations do now not report ransomware attacks as they occur (Aven,
2016). Preventative measures against ransomware include:
a) Using Diverse Backups
b) Keeping Antivirus Up-To-Date
c) Maintaining Patch Updates
d) Installing File and System Integrity Monitoring Software
e) Compliance Maintenance
DDoS attacks
DDoS attacks come at a real cost. The severity and frequency of DDoS assaults have many
network managers concerned. Hackers infiltrate organizations by using flooding web sites
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

and networks with questionable traffic. For instance, “DDoS for hire” offerings is one ability
through which hacking/attack capabilities are offered in trade for money. The different
channel used is the wide adoption of Internet-of-Things (IoT) technology. IoT widgets with
inadequate protection defenses are an easy target (Nohrstedt, 2018). Defending against DDoS
attacks would not have to be a challenge. Some of the methods of defending against DDoS
attacks include:
a) Identifying unusual traffic activity
b) Using the needed amount of bandwidth
c) Avoiding the wrong response to extortion attempts
d) Immediate contact with your ISP
e) Developing a Comprehensive Approach to DDoS Security
Insider threats
Insider threats proceed to infect organizations of all sizes. Experts estimate that insider threats
are in the back of roughly 50 percent of data breaches, according to McKinsey & Company.
Such incidents are usually driven by using financial gain or negligence. Though the concept
technique behind insider threats is gaining recognition inside organizations, corporations can
also not continually be proactive as the majority of community security defenses are
configured to protect from external threats. Insider abuse threats come in the forms of:
a) Remote access to sensitive data
b) Unauthorized deletion of data
c) Unauthorized access to shared folders
d) Unapproved hardware/software
Cloud security
The protection behind legitimate cloud services is being co-opted. As more organizations
gravitate towards the cloud for data storage and retrieval, hackers have observed a way into
the system. They use the same official services. However, they might also have ulterior
factors and can wreak havoc. Organizations can be left susceptible as they have come to trust
common cloud platforms and take a reactive strategy to any questionable activity, which
comes at a significant cost to them in the shape of downtime and leveraging sources to do
damage control (Nohrstedt, 2018).
7
through which hacking/attack capabilities are offered in trade for money. The different
channel used is the wide adoption of Internet-of-Things (IoT) technology. IoT widgets with
inadequate protection defenses are an easy target (Nohrstedt, 2018). Defending against DDoS
attacks would not have to be a challenge. Some of the methods of defending against DDoS
attacks include:
a) Identifying unusual traffic activity
b) Using the needed amount of bandwidth
c) Avoiding the wrong response to extortion attempts
d) Immediate contact with your ISP
e) Developing a Comprehensive Approach to DDoS Security
Insider threats
Insider threats proceed to infect organizations of all sizes. Experts estimate that insider threats
are in the back of roughly 50 percent of data breaches, according to McKinsey & Company.
Such incidents are usually driven by using financial gain or negligence. Though the concept
technique behind insider threats is gaining recognition inside organizations, corporations can
also not continually be proactive as the majority of community security defenses are
configured to protect from external threats. Insider abuse threats come in the forms of:
a) Remote access to sensitive data
b) Unauthorized deletion of data
c) Unauthorized access to shared folders
d) Unapproved hardware/software
Cloud security
The protection behind legitimate cloud services is being co-opted. As more organizations
gravitate towards the cloud for data storage and retrieval, hackers have observed a way into
the system. They use the same official services. However, they might also have ulterior
factors and can wreak havoc. Organizations can be left susceptible as they have come to trust
common cloud platforms and take a reactive strategy to any questionable activity, which
comes at a significant cost to them in the shape of downtime and leveraging sources to do
damage control (Nohrstedt, 2018).
7

Minimizing risks with file and system integrity
For many in IT, network vulnerabilities may now not be emerging risks; however, oversights.
The persistent challenge of preserving compliance and keeping the integrity of the enterprise
IT infrastructure is not consistently standardized. Utilizing file and machine integrity
monitoring software, particularly one with auditing capabilities, flexible response options,
and automatic detection approaches, may additionally minimize the risk organizations face
daily. Network-wide file and system integrity monitoring can set up complete accountability
with audit trails that cannot be altered. It should also offer unique, advanced safety towards
threats with the aid of providing admins with the ability to restore systems and documents to
a former state immediately (Chen & Cheng, 2018).
Internal network vulnerabilities for Atlassian
Some of the most common internal network vulnerabilities are:
a) USB drives
b) Laptops and netbooks
c) Wireless access points
d) Miscellaneous USB devices (digital cameras, MP3 players, etc.)
e) Employees borrowing others’ machines or devices
f) The Trojan Human (attackers who visit sites disguised as employee personnel or
contractors)
g) Optical media (CDs, DVDs, etc.)
h) Lack of employee alertness
i) Smartphones
j) E-mail
Threat to Traditional Network Security of Atlassian
During the upgrade process, Atlassian comes under the possibilities of threats for their
services and products and may risk having their business models altered. Most of the IT
companies, like Atlassian, try to protect their products and services with the traditional
security system, which is developed only in the regards of the perimeter model. Such systems
secure the data which is incorporated inside their boundaries. But the devices, users as well as
8
For many in IT, network vulnerabilities may now not be emerging risks; however, oversights.
The persistent challenge of preserving compliance and keeping the integrity of the enterprise
IT infrastructure is not consistently standardized. Utilizing file and machine integrity
monitoring software, particularly one with auditing capabilities, flexible response options,
and automatic detection approaches, may additionally minimize the risk organizations face
daily. Network-wide file and system integrity monitoring can set up complete accountability
with audit trails that cannot be altered. It should also offer unique, advanced safety towards
threats with the aid of providing admins with the ability to restore systems and documents to
a former state immediately (Chen & Cheng, 2018).
Internal network vulnerabilities for Atlassian
Some of the most common internal network vulnerabilities are:
a) USB drives
b) Laptops and netbooks
c) Wireless access points
d) Miscellaneous USB devices (digital cameras, MP3 players, etc.)
e) Employees borrowing others’ machines or devices
f) The Trojan Human (attackers who visit sites disguised as employee personnel or
contractors)
g) Optical media (CDs, DVDs, etc.)
h) Lack of employee alertness
i) Smartphones
j) E-mail
Threat to Traditional Network Security of Atlassian
During the upgrade process, Atlassian comes under the possibilities of threats for their
services and products and may risk having their business models altered. Most of the IT
companies, like Atlassian, try to protect their products and services with the traditional
security system, which is developed only in the regards of the perimeter model. Such systems
secure the data which is incorporated inside their boundaries. But the devices, users as well as
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

data which is outside of such perimeter model may not get secured by such systems. Also, the
data which is stored in the cloud remains vulnerable to threats as it may get retrieved by third
party users. Skilled hackers can also penetrate the security systems easily as no traditional
system can secure the data from all types of cyber-attacks (Akamai, 2020).
Crisis Management Plan
The crisis management team plays an essential role in the management of the organization. It
helps to confirm the control of the procedures of the organization. Top management
commitment is the primary aspect of the organization when it comes to design an effective
Business Continuity crisis and management team because senior management must involve
coordinating, developing, and ensure the active recovery of disaster within the organization.
For the development of an effective strategy, adequate resources and time must be
committed. The efforts of involved individuals and financial considerations are part of the
resources (Mikušová & Horváthová, 2019).
To supervise the implementation and development of the plan, you need to hire a planning
group that must include representatives of all the organizational function areas. The data
processing manager and operations manager must consist of the key committee members. It
is also necessary that the committee explains the scope of the plan. Due to the expensive and
sensitive nature of the subject, the committee must regularly inform the top management of
the progress of the plan. Most continuity plans of business only address the activities related
to data processing, but a comprehensive plan will also involve the operational areas of the
company outside the data processing. The plan must have an extensive range of elements that
could affect the organization, to address the scenarios of disaster effectively (Nohrstedt,
2018).
Business continuity plan
The ideal planning process of business continuity is a sealed loop that supports the
improvements and continuing iterations as the objective. Business prioritizations Integration
into IT Manage are three major sections of the planning process.
Business Prioritization
To recognize the scope of the continuity plan of business, we use the process of business
prioritization in which we understand the different types of vulnerabilities, threats, and risks,
9
data which is stored in the cloud remains vulnerable to threats as it may get retrieved by third
party users. Skilled hackers can also penetrate the security systems easily as no traditional
system can secure the data from all types of cyber-attacks (Akamai, 2020).
Crisis Management Plan
The crisis management team plays an essential role in the management of the organization. It
helps to confirm the control of the procedures of the organization. Top management
commitment is the primary aspect of the organization when it comes to design an effective
Business Continuity crisis and management team because senior management must involve
coordinating, developing, and ensure the active recovery of disaster within the organization.
For the development of an effective strategy, adequate resources and time must be
committed. The efforts of involved individuals and financial considerations are part of the
resources (Mikušová & Horváthová, 2019).
To supervise the implementation and development of the plan, you need to hire a planning
group that must include representatives of all the organizational function areas. The data
processing manager and operations manager must consist of the key committee members. It
is also necessary that the committee explains the scope of the plan. Due to the expensive and
sensitive nature of the subject, the committee must regularly inform the top management of
the progress of the plan. Most continuity plans of business only address the activities related
to data processing, but a comprehensive plan will also involve the operational areas of the
company outside the data processing. The plan must have an extensive range of elements that
could affect the organization, to address the scenarios of disaster effectively (Nohrstedt,
2018).
Business continuity plan
The ideal planning process of business continuity is a sealed loop that supports the
improvements and continuing iterations as the objective. Business prioritizations Integration
into IT Manage are three major sections of the planning process.
Business Prioritization
To recognize the scope of the continuity plan of business, we use the process of business
prioritization in which we understand the different types of vulnerabilities, threats, and risks,
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
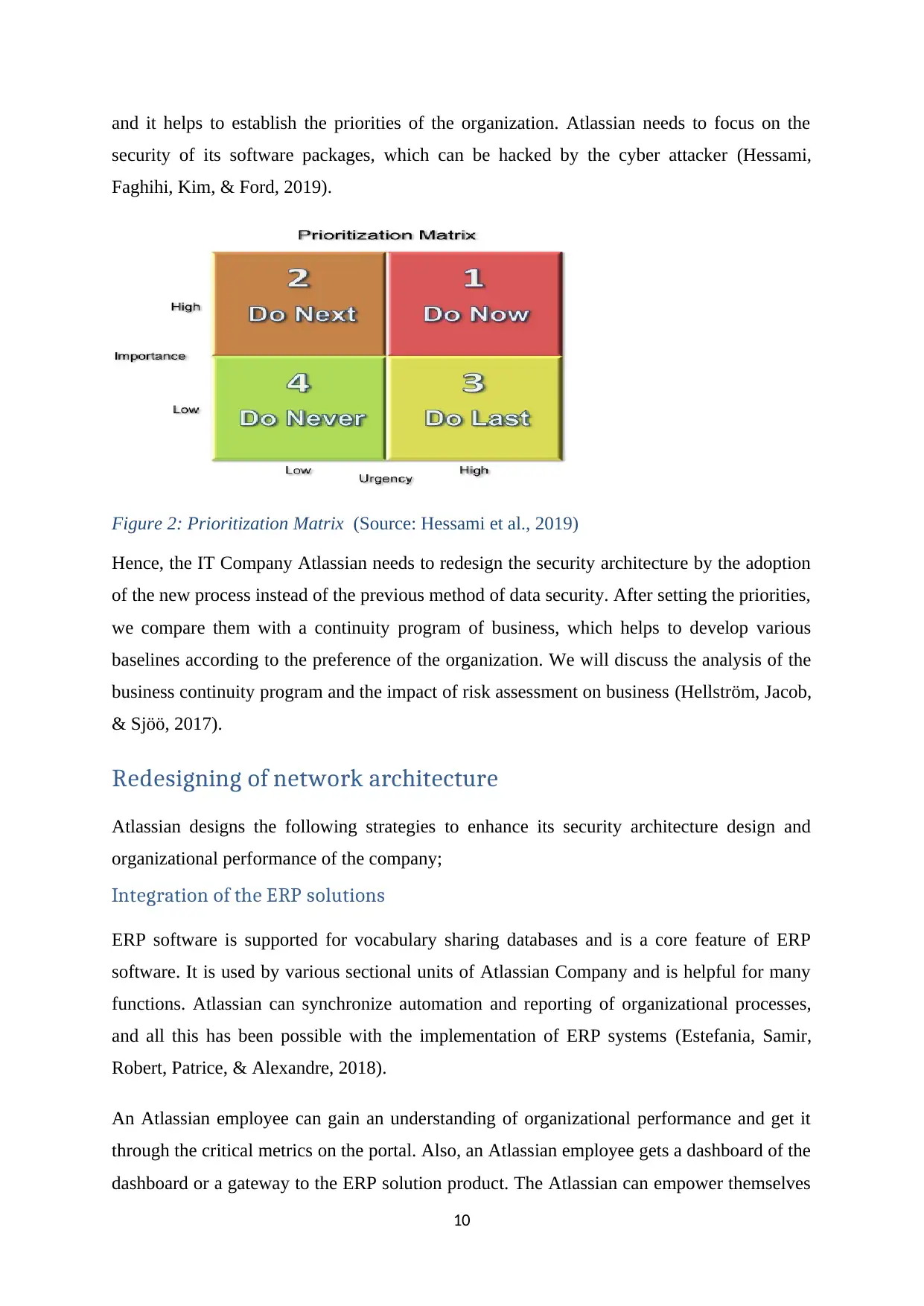
and it helps to establish the priorities of the organization. Atlassian needs to focus on the
security of its software packages, which can be hacked by the cyber attacker (Hessami,
Faghihi, Kim, & Ford, 2019).
Figure 2: Prioritization Matrix (Source: Hessami et al., 2019)
Hence, the IT Company Atlassian needs to redesign the security architecture by the adoption
of the new process instead of the previous method of data security. After setting the priorities,
we compare them with a continuity program of business, which helps to develop various
baselines according to the preference of the organization. We will discuss the analysis of the
business continuity program and the impact of risk assessment on business (Hellström, Jacob,
& Sjöö, 2017).
Redesigning of network architecture
Atlassian designs the following strategies to enhance its security architecture design and
organizational performance of the company;
Integration of the ERP solutions
ERP software is supported for vocabulary sharing databases and is a core feature of ERP
software. It is used by various sectional units of Atlassian Company and is helpful for many
functions. Atlassian can synchronize automation and reporting of organizational processes,
and all this has been possible with the implementation of ERP systems (Estefania, Samir,
Robert, Patrice, & Alexandre, 2018).
An Atlassian employee can gain an understanding of organizational performance and get it
through the critical metrics on the portal. Also, an Atlassian employee gets a dashboard of the
dashboard or a gateway to the ERP solution product. The Atlassian can empower themselves
10
security of its software packages, which can be hacked by the cyber attacker (Hessami,
Faghihi, Kim, & Ford, 2019).
Figure 2: Prioritization Matrix (Source: Hessami et al., 2019)
Hence, the IT Company Atlassian needs to redesign the security architecture by the adoption
of the new process instead of the previous method of data security. After setting the priorities,
we compare them with a continuity program of business, which helps to develop various
baselines according to the preference of the organization. We will discuss the analysis of the
business continuity program and the impact of risk assessment on business (Hellström, Jacob,
& Sjöö, 2017).
Redesigning of network architecture
Atlassian designs the following strategies to enhance its security architecture design and
organizational performance of the company;
Integration of the ERP solutions
ERP software is supported for vocabulary sharing databases and is a core feature of ERP
software. It is used by various sectional units of Atlassian Company and is helpful for many
functions. Atlassian can synchronize automation and reporting of organizational processes,
and all this has been possible with the implementation of ERP systems (Estefania, Samir,
Robert, Patrice, & Alexandre, 2018).
An Atlassian employee can gain an understanding of organizational performance and get it
through the critical metrics on the portal. Also, an Atlassian employee gets a dashboard of the
dashboard or a gateway to the ERP solution product. The Atlassian can empower themselves
10

by presenting the ERP arrangements in the authoritative acts of the organization as this
product is exceptionally steady while successfully streamlining the organization's tasks
(Hwang & Grant, 2016).
Figure 3: Example of ERP solutions (Source: Hwang & Grant, 2016)
Server management
The underlying infrastructure of an IT company is critical concerning organizational
performance in a dynamically changing business market with customer satisfaction and also
contributes to increasing organizational productivity (Sun, Zhang, Xiong, & Zhu, 2014).
11
product is exceptionally steady while successfully streamlining the organization's tasks
(Hwang & Grant, 2016).
Figure 3: Example of ERP solutions (Source: Hwang & Grant, 2016)
Server management
The underlying infrastructure of an IT company is critical concerning organizational
performance in a dynamically changing business market with customer satisfaction and also
contributes to increasing organizational productivity (Sun, Zhang, Xiong, & Zhu, 2014).
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

