Information Security: Analyzing ATM Security using CIA Model
VerifiedAdded on 2023/06/14
|10
|1839
|409
Report
AI Summary
This report provides a comprehensive analysis of information security within Automated Teller Machine (ATM) systems. It begins by explaining the CIA model (Confidentiality, Integrity, and Availability) and its relevance to ATM security, detailing how each component ensures sensitive data protection, system reliability, and authorized access. The report addresses potential vulnerabilities, such as PIN theft, by calculating the number of possible attempts given compromised keys using permutation and combination methods. It further discusses the reluctance in adopting biometric authentication due to security concerns, errors, and mapping issues, while also acknowledging its potential benefits. The report also explores the impact of false negatives in biometric systems, highlighting risks like identity theft and infrastructure shutdown. Finally, it includes a decryption exercise using substitution and Caesar ciphers, demonstrating encryption techniques to secure data transmission. This document aims to provide a thorough understanding of the security challenges and solutions associated with ATM systems.

Running head: INFORMATION SECURITY
INFORMATION SECURITY
Name of the Student
Name of the University
Authors Note
INFORMATION SECURITY
Name of the Student
Name of the University
Authors Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY
Table of Contents
Answer to Question 1:.........................................................................................................2
Answer to Question 2:.........................................................................................................3
Answer to Question 3:.........................................................................................................3
Answer to Question 4:.........................................................................................................4
Answer to Question 5:.........................................................................................................5
References............................................................................................................................7
Table of Contents
Answer to Question 1:.........................................................................................................2
Answer to Question 2:.........................................................................................................3
Answer to Question 3:.........................................................................................................3
Answer to Question 4:.........................................................................................................4
Answer to Question 5:.........................................................................................................5
References............................................................................................................................7

2INFORMATION SECURITY
Answer to Question 1:
CIA stands for confidentiality, Integrity and Availability is known to be well known
model for various kinds of security policies (Singh & Kaur, 2016). This model works well for the
various kinds of ATM machines. Confidentiality generally ensures the various sensitive
information which can be accessed by a particular kind of person. It focuses on implementation
of security mechanism like username, access control, password. It is also considered to be
common for information which is mainly recognized for the extent of damage which can easily
fall into the intended hands. Integrity mainly ensures that a particular kind of information are
provided in right quantity of format which is considered to be true and correct for original
purposes (Peltier, 2016). The receiver of this kind of information should have proper kind of
information regarding creation of intend. The information can be easily edited by an edited by
any authorized person and only remains in original state when it in rest. Integrity is generally
implemented by making use of security mechanism like data encryption and hashing.
Availability generally ensures that various kinds of information and resources are made
available for the list of person who need to implement it. It is generally implemented by making
use of various kinds of methods like software, maintenance of hardware, software for patching
and optimization of network (Pathak et al., 2015). Various kinds of process like redundancy,
RAID and availability of large of cluster is generally used for mitigation of risk when large
number of large number of hardware issues are encountered. Dedicated hardware of service is
generally used for downtime and unreachable data for various kinds of malicious action like
distribution denial of services.
Answer to Question 1:
CIA stands for confidentiality, Integrity and Availability is known to be well known
model for various kinds of security policies (Singh & Kaur, 2016). This model works well for the
various kinds of ATM machines. Confidentiality generally ensures the various sensitive
information which can be accessed by a particular kind of person. It focuses on implementation
of security mechanism like username, access control, password. It is also considered to be
common for information which is mainly recognized for the extent of damage which can easily
fall into the intended hands. Integrity mainly ensures that a particular kind of information are
provided in right quantity of format which is considered to be true and correct for original
purposes (Peltier, 2016). The receiver of this kind of information should have proper kind of
information regarding creation of intend. The information can be easily edited by an edited by
any authorized person and only remains in original state when it in rest. Integrity is generally
implemented by making use of security mechanism like data encryption and hashing.
Availability generally ensures that various kinds of information and resources are made
available for the list of person who need to implement it. It is generally implemented by making
use of various kinds of methods like software, maintenance of hardware, software for patching
and optimization of network (Pathak et al., 2015). Various kinds of process like redundancy,
RAID and availability of large of cluster is generally used for mitigation of risk when large
number of large number of hardware issues are encountered. Dedicated hardware of service is
generally used for downtime and unreachable data for various kinds of malicious action like
distribution denial of services.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY
Answer to Question 2:
The keyboard of an ATM machine contains ten numerical keys ranging from 0 to 9 and
some other kinds of keys which are assigned for some kinds of specific tasks. The case described
in the question paper is a situation in which thief has already five keys of number so more five
number of numerical keys are available (Onyesolu & Okpala, 2017). The pin number for a ATM
machine generally consist of four digits which relates us to the fact that four keys are to be
selected from five keys which are left unbroken in the keypad. For tackling this particular
situation, we are making use of permutation and combination for calculating the number of
attempts which can be easily made.
5P4 = 5! / (5-4)! =5! /1! = (5*4*3*2*1)/1=120.
The above calculation relates us to the fact that 120 number of attempts can be easily
made for tackling the situation.
Answer to Question 3:
There are generally large number of benefits can be obtained from idea of biometric on
the contrary large number of problems can be easily tackled (Koteswari & Paul, 2017). The three
important kinds of reasons behind the reluctant use of biometric are the following:
The main reason behind the use of biometric is the idea of security. In the case of
biometric the information of a particular kind of person can be easily stored in the
database (Karovaliya et al., 2015). Now if the database of a particular system is
hacked then it can easily affect an individual.
Answer to Question 2:
The keyboard of an ATM machine contains ten numerical keys ranging from 0 to 9 and
some other kinds of keys which are assigned for some kinds of specific tasks. The case described
in the question paper is a situation in which thief has already five keys of number so more five
number of numerical keys are available (Onyesolu & Okpala, 2017). The pin number for a ATM
machine generally consist of four digits which relates us to the fact that four keys are to be
selected from five keys which are left unbroken in the keypad. For tackling this particular
situation, we are making use of permutation and combination for calculating the number of
attempts which can be easily made.
5P4 = 5! / (5-4)! =5! /1! = (5*4*3*2*1)/1=120.
The above calculation relates us to the fact that 120 number of attempts can be easily
made for tackling the situation.
Answer to Question 3:
There are generally large number of benefits can be obtained from idea of biometric on
the contrary large number of problems can be easily tackled (Koteswari & Paul, 2017). The three
important kinds of reasons behind the reluctant use of biometric are the following:
The main reason behind the use of biometric is the idea of security. In the case of
biometric the information of a particular kind of person can be easily stored in the
database (Karovaliya et al., 2015). Now if the database of a particular system is
hacked then it can easily affect an individual.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY
Various kinds of errors can be easily being encountered in the technology is the
various kinds of errors. The main properties which are encountered are false
rejection and false entry.
Another important kind of parameter which is encountered is the concept or idea
of mapping (Karovaliya et al., 2015). Mapping is the system is mainly done by
making use of fingerprint. In this situation the system needs to be very much
accurate.
Gradient biometric in the domain of biometric has been considered to have experience of
more than 10 years (Karovaliya et al., 2015). This organization focus on three important aspects
of biometric are comfort, availability and lastly safety. The network and linkage between
information provides proper kinds of accesses to large number of information. Multifactor
authentication is well known thing in biometric.
Answer to Question 4:
A false kind of negative is kind of approach in which various kinds of biometric cannot
get accesses to the location of biometric. In this a situation the identity of a person can be easily
stored in the various kinds of database (Betab & Sandhu, 2014). In some of the cases it is seen
the access is not provided to a person as a result of some kinds of technical issues. Concept of
miss identity can easily arise if false person can easily get identity of a person. The first issues
which can be encountered is identity of a person is not known (Ali, 2016). Second kind of issues
which can be encountered is loss of identity of person. There are large number of illegal activity
that can be performed in recent times is the use of biometric (Jebaline & Gomathi, 2015).
Considering the level of organization, it has the power to shut down the overall infrastructure,
along with various kinds of things which is needed for storing of data (Ray, Das & Sen, 2015). It
Various kinds of errors can be easily being encountered in the technology is the
various kinds of errors. The main properties which are encountered are false
rejection and false entry.
Another important kind of parameter which is encountered is the concept or idea
of mapping (Karovaliya et al., 2015). Mapping is the system is mainly done by
making use of fingerprint. In this situation the system needs to be very much
accurate.
Gradient biometric in the domain of biometric has been considered to have experience of
more than 10 years (Karovaliya et al., 2015). This organization focus on three important aspects
of biometric are comfort, availability and lastly safety. The network and linkage between
information provides proper kinds of accesses to large number of information. Multifactor
authentication is well known thing in biometric.
Answer to Question 4:
A false kind of negative is kind of approach in which various kinds of biometric cannot
get accesses to the location of biometric. In this a situation the identity of a person can be easily
stored in the various kinds of database (Betab & Sandhu, 2014). In some of the cases it is seen
the access is not provided to a person as a result of some kinds of technical issues. Concept of
miss identity can easily arise if false person can easily get identity of a person. The first issues
which can be encountered is identity of a person is not known (Ali, 2016). Second kind of issues
which can be encountered is loss of identity of person. There are large number of illegal activity
that can be performed in recent times is the use of biometric (Jebaline & Gomathi, 2015).
Considering the level of organization, it has the power to shut down the overall infrastructure,
along with various kinds of things which is needed for storing of data (Ray, Das & Sen, 2015). It
5INFORMATION SECURITY
comes up restoring of large number of services which is needed for this particular concept or
idea.
Answer to Question 5:
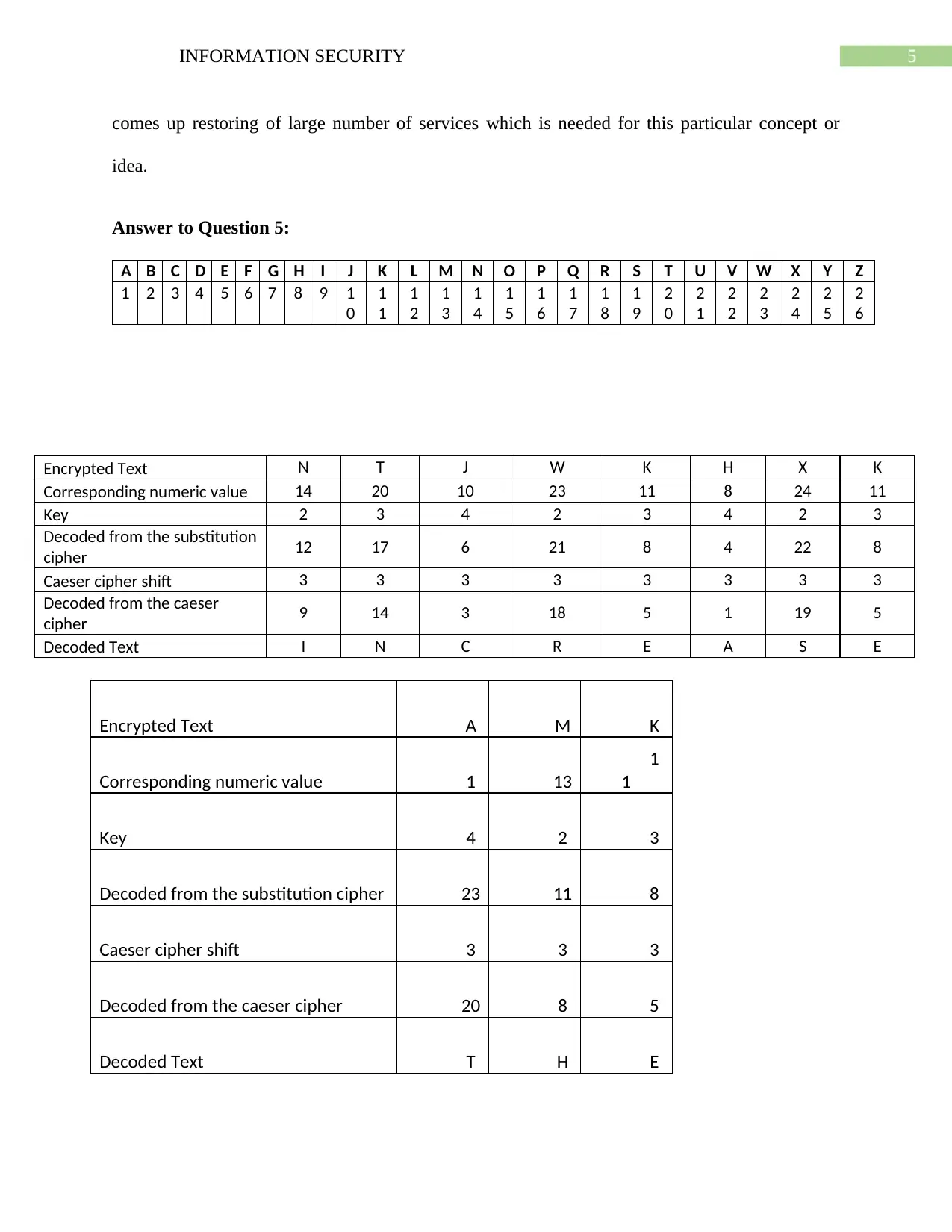
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 1
0
1
1
1
2
1
3
1
4
1
5
1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
2
6
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser
cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13
1
1
Key 4 2 3
Decoded from the substitution cipher 23 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher 20 8 5
Decoded Text T H E
comes up restoring of large number of services which is needed for this particular concept or
idea.
Answer to Question 5:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 1
0
1
1
1
2
1
3
1
4
1
5
1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
2
6
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser
cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13
1
1
Key 4 2 3
Decoded from the substitution cipher 23 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher 20 8 5
Decoded Text T H E
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6INFORMATION SECURITY
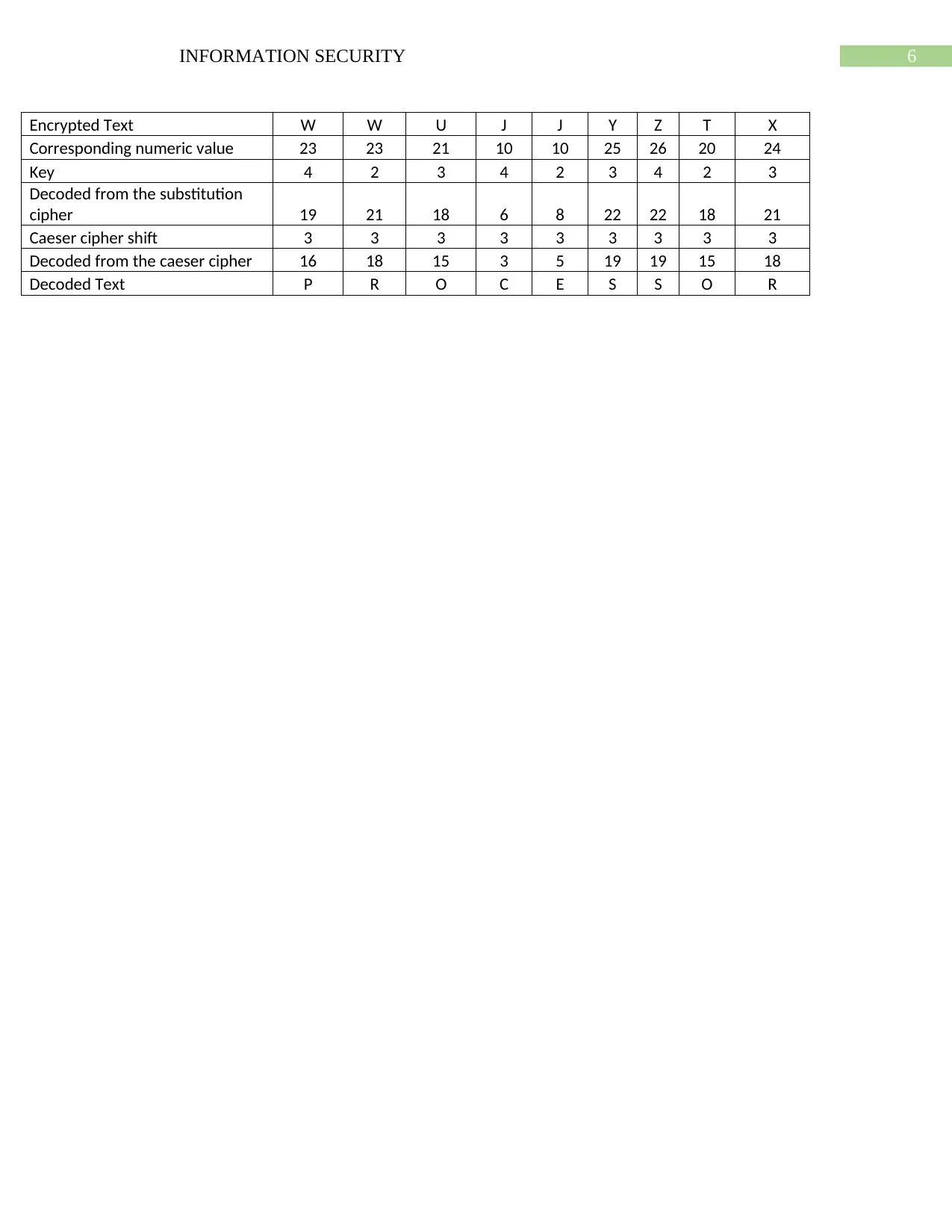
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 10 10 25 26 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 19 21 18 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 10 10 25 26 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 19 21 18 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7INFORMATION SECURITY
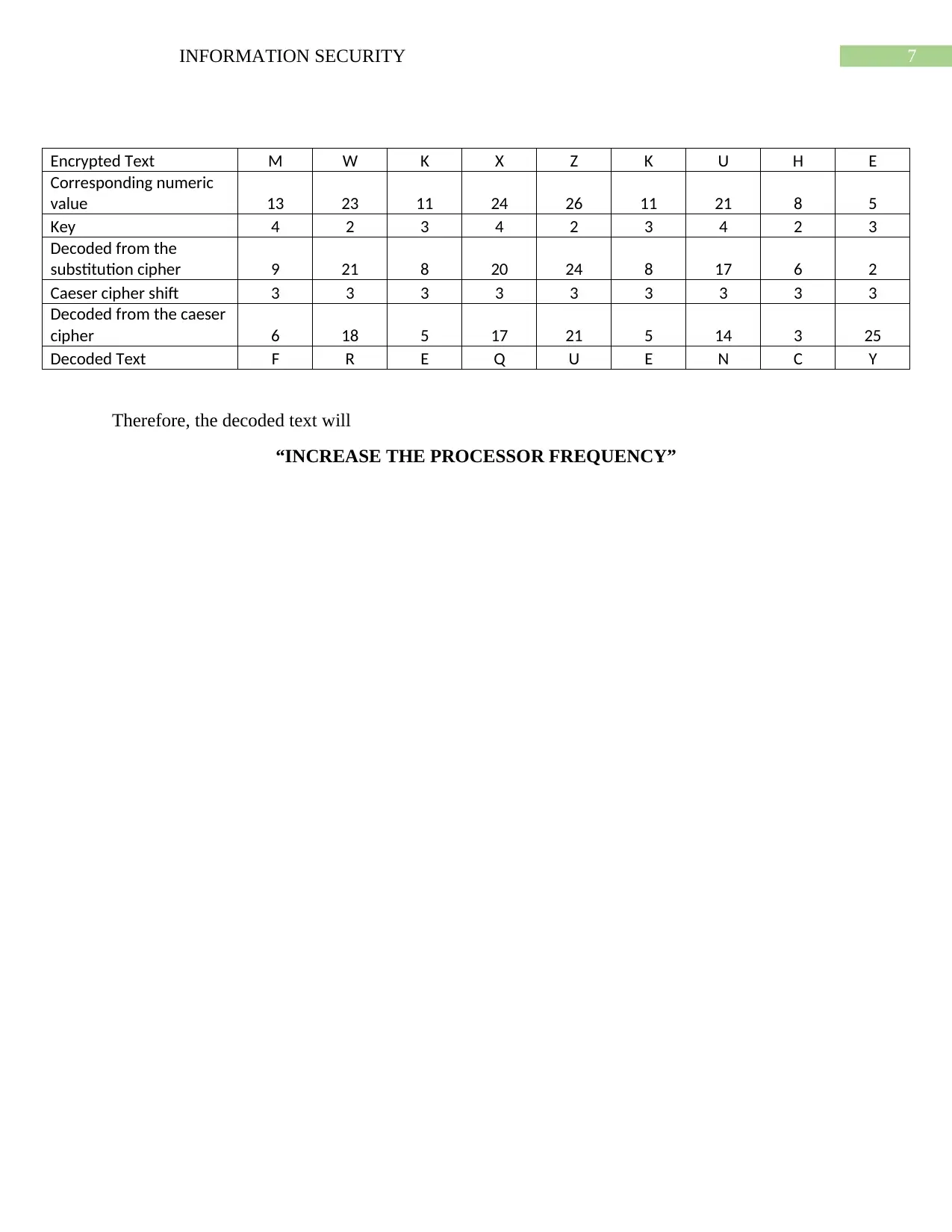
Encrypted Text M W K X Z K U H E
Corresponding numeric
value 13 23 11 24 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the
substitution cipher 9 21 8 20 24 8 17 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser
cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Therefore, the decoded text will
“INCREASE THE PROCESSOR FREQUENCY”
Encrypted Text M W K X Z K U H E
Corresponding numeric
value 13 23 11 24 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the
substitution cipher 9 21 8 20 24 8 17 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser
cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Therefore, the decoded text will
“INCREASE THE PROCESSOR FREQUENCY”

8INFORMATION SECURITY
References
Ali, P. I. (2016). Impact of automated teller machine on banking services delivery in Nigeria: a
stakeholder analysis. Brazilian Journal of Education, Technology and Society
(BRAJETS), 9(1), 64-72.
Betab, G., & Sandhu, R. K. (2014). Fingerprints in Automated Teller Machine-A
Survey. International Journal of Engineering and Advanced Technology (IJEAT) ISSN:
2249, 8958.
Jebaline, G. R., & Gomathi, S. (2015, March). A novel method to enhance the security of ATM
using biometrics. In Circuit, Power and Computing Technologies (ICCPCT), 2015
International Conference on (pp. 1-4). IEEE.
Karovaliya, M., Karedia, S., Oza, S., & Kalbande, D. R. (2015). Enhanced security for ATM
machine with OTP and Facial recognition features. Procedia Computer Science, 45, 390-
396.
Koteswari, S., & Paul, P. J. (2017). A Survey: Fusion of Fingerprint and Iris for ATM services.
Onyesolu, M. O., & Okpala, A. C. (2017). Improving Security Using a Three-Tier
Authentication for Automated Teller Machine (ATM). International Journal of
Computer Network and Information Security, 9(10), 50.
Pathak, S. K., Pathak, S. K., Mishra, M. K., Kesharwani, L., & Gupta, A. K. (2015). Automated
Teller Machine (ATM) Frauds and Security. EDITORIAL BOARD, 192.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
References
Ali, P. I. (2016). Impact of automated teller machine on banking services delivery in Nigeria: a
stakeholder analysis. Brazilian Journal of Education, Technology and Society
(BRAJETS), 9(1), 64-72.
Betab, G., & Sandhu, R. K. (2014). Fingerprints in Automated Teller Machine-A
Survey. International Journal of Engineering and Advanced Technology (IJEAT) ISSN:
2249, 8958.
Jebaline, G. R., & Gomathi, S. (2015, March). A novel method to enhance the security of ATM
using biometrics. In Circuit, Power and Computing Technologies (ICCPCT), 2015
International Conference on (pp. 1-4). IEEE.
Karovaliya, M., Karedia, S., Oza, S., & Kalbande, D. R. (2015). Enhanced security for ATM
machine with OTP and Facial recognition features. Procedia Computer Science, 45, 390-
396.
Koteswari, S., & Paul, P. J. (2017). A Survey: Fusion of Fingerprint and Iris for ATM services.
Onyesolu, M. O., & Okpala, A. C. (2017). Improving Security Using a Three-Tier
Authentication for Automated Teller Machine (ATM). International Journal of
Computer Network and Information Security, 9(10), 50.
Pathak, S. K., Pathak, S. K., Mishra, M. K., Kesharwani, L., & Gupta, A. K. (2015). Automated
Teller Machine (ATM) Frauds and Security. EDITORIAL BOARD, 192.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION SECURITY
Ray, S., Das, S., & Sen, A. (2015, December). An intelligent vision system for monitoring
security and surveillance of ATM. In India Conference (INDICON), 2015 Annual IEEE
(pp. 1-5). IEEE.
Singh, S., & Kaur, S. (2016). Enhancing ATM Security Using Fusion of Biometric
Techniques. IITM Journal of Management and IT, 7(1), 79-82.
Ray, S., Das, S., & Sen, A. (2015, December). An intelligent vision system for monitoring
security and surveillance of ATM. In India Conference (INDICON), 2015 Annual IEEE
(pp. 1-5). IEEE.
Singh, S., & Kaur, S. (2016). Enhancing ATM Security Using Fusion of Biometric
Techniques. IITM Journal of Management and IT, 7(1), 79-82.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





