Comprehensive Report on Information Security: ATMs & Biometric Systems
VerifiedAdded on 2023/06/13
|13
|3715
|129
Report
AI Summary
This report delves into the information security aspects of Automated Teller Machines (ATMs) and biometric authentication systems. It begins by examining the CIA triad—Confidentiality, Integrity, and Availability—in the context of ATM systems, providing examples of how each principle applies to ensure secure transactions. The report then analyzes a hypothetical scenario involving a thief attempting to compromise an ATM, calculating the probability of PIN detection and emphasizing the importance of ATM security features. Furthermore, the document discusses biometric authentication as a method for uniquely identifying individuals, highlighting its advantages in preventing fraud and controlling access, while also addressing common concerns such as hardware requirements, data accuracy, and password resetting challenges. Finally, the report explores the effectiveness of biometric authentication in protecting various systems, acknowledging its limitations and the potential for false negative rates, particularly in scenarios involving restricted access and patient recognition failures. The document emphasizes the need for robust security measures and continuous improvement in authentication technologies.

Running head: INFORMATION SECURITY
Information Security
Name of the Student
Name of the University
Author’s Note:
Information Security
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INFORMATION SECURITY
Table of Contents
Question 1..................................................................................................................................2
Question 2..................................................................................................................................3
Question 3..................................................................................................................................4
Question 4..................................................................................................................................5
Question 5..................................................................................................................................6
References..................................................................................................................................8
INFORMATION SECURITY
Table of Contents
Question 1..................................................................................................................................2
Question 2..................................................................................................................................3
Question 3..................................................................................................................................4
Question 4..................................................................................................................................5
Question 5..................................................................................................................................6
References..................................................................................................................................8

2
INFORMATION SECURITY
Question 1
Automated Teller Machines or simply ATMs are designed for the benefit of those
people, who do not have time to go to the bank for the purpose of withdrawing any amount of
money (Laudon & Laudon, 2015). It is a particular device for electronic telecommunications,
which significantly enables all the customers or clients of the financial institutions for
performing any kind of financial transaction. These types of systems are integrated with
information systems. CIA or confidentiality, integrity and availability are the most important
requirements that are solely related to these types of information systems. These three
requirements are extremely important for the ATM as they are responsible for the overall
security of the information system (Venkatesh, Brown & Bala, 2013). The description of
these requirements with their importance is stated below.
i) Confidentiality: This is the first and the foremost requirement of the CIA.
Confidentiality can be solely defined as the set of regulations and rules, which restricts the
access or rather, limits the access to any type of confidential or sensitive information. It is
extremely important for any type of ATM systems. The responsibility of confidentiality in
any ATM machine is completely on the bank authorities and the users. Examples of
confidentiality in any such system are as follows:
a) The details of the users should be strictly maintained and thus the confidentiality
would be maintained.
b) The data encryption of the PIN number and the ATM card number of any particular
authorized user is to be kept private and secret so that there is no chance of lack of
confidentiality (Stair & Reynolds, 2013).
ii) Integrity: The second requirement of the CIA is integrity. The data that is
categorized as per the amount or the damage incurred can be done without letting it fall in the
wrong hands. Various stringent measures could be easily implemented as per these
categories. The PIN number of the card helps to maintain this integrity. The accuracy is kept
through this. Examples of integrity in any such system are as follows:
a) The best example of integrity in ATM machine is the checksums. Even the
cryptographic checksums are utilized in this purpose.
b) The second example of the integrity maintenance is the accidental or deliberate file
deletion or even altering the contents of the confidential information.
iii) Availability: The third and another significant requirement in the CIA is the
availability (Galliers & Leidner, 2014). This particular requirement helps to determine the
available resources for any ATM transaction. The hardware that is utilized here has an
incorporation of information system within it. Under no circumstances, this data should be
changed or altered and thus, the steps for ensuring that data is not taken by the unauthorized
people should be executed with excellence. Examples of availability in any such system are
as follows:
a) The first example of availability in ATM is the availability of information, which is
solely needed for completing the transaction (Rainer et al., 2013).
INFORMATION SECURITY
Question 1
Automated Teller Machines or simply ATMs are designed for the benefit of those
people, who do not have time to go to the bank for the purpose of withdrawing any amount of
money (Laudon & Laudon, 2015). It is a particular device for electronic telecommunications,
which significantly enables all the customers or clients of the financial institutions for
performing any kind of financial transaction. These types of systems are integrated with
information systems. CIA or confidentiality, integrity and availability are the most important
requirements that are solely related to these types of information systems. These three
requirements are extremely important for the ATM as they are responsible for the overall
security of the information system (Venkatesh, Brown & Bala, 2013). The description of
these requirements with their importance is stated below.
i) Confidentiality: This is the first and the foremost requirement of the CIA.
Confidentiality can be solely defined as the set of regulations and rules, which restricts the
access or rather, limits the access to any type of confidential or sensitive information. It is
extremely important for any type of ATM systems. The responsibility of confidentiality in
any ATM machine is completely on the bank authorities and the users. Examples of
confidentiality in any such system are as follows:
a) The details of the users should be strictly maintained and thus the confidentiality
would be maintained.
b) The data encryption of the PIN number and the ATM card number of any particular
authorized user is to be kept private and secret so that there is no chance of lack of
confidentiality (Stair & Reynolds, 2013).
ii) Integrity: The second requirement of the CIA is integrity. The data that is
categorized as per the amount or the damage incurred can be done without letting it fall in the
wrong hands. Various stringent measures could be easily implemented as per these
categories. The PIN number of the card helps to maintain this integrity. The accuracy is kept
through this. Examples of integrity in any such system are as follows:
a) The best example of integrity in ATM machine is the checksums. Even the
cryptographic checksums are utilized in this purpose.
b) The second example of the integrity maintenance is the accidental or deliberate file
deletion or even altering the contents of the confidential information.
iii) Availability: The third and another significant requirement in the CIA is the
availability (Galliers & Leidner, 2014). This particular requirement helps to determine the
available resources for any ATM transaction. The hardware that is utilized here has an
incorporation of information system within it. Under no circumstances, this data should be
changed or altered and thus, the steps for ensuring that data is not taken by the unauthorized
people should be executed with excellence. Examples of availability in any such system are
as follows:
a) The first example of availability in ATM is the availability of information, which is
solely needed for completing the transaction (Rainer et al., 2013).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INFORMATION SECURITY
b) The second example of availability in ATM is the presence of systems and the
card.
INFORMATION SECURITY
b) The second example of availability in ATM is the presence of systems and the
card.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INFORMATION SECURITY
Question 2
An ATM or an Automated Teller Machine is the particular device that is utilized for
the purpose of cash withdrawal from any specific bank account. The users of this ATM are
provided with a unique card that has a number within it and a personal identification number
or PIN number (Peltier, 2013). This unique card number and the PIN number make that
particular ATM card absolutely different from the rest of the cards and thus only the
authorized user can access the bank account.
As per the given scenario, a thief wants to steal money from any typical ATM
machine and thus he has eventually broken the Automated Teller Machine with the help of a
screwdriver. He has even jammed the card reader of that ATM machine and has broken the
five specific keys of the keypad of the machine.
In the middle of all these, the thief had to stop his process of break in and had to hide
since a customer has approached to the ATM. The customer entered into the ATM, enters the
ATM card, punches his unique 4 digits PIN number and then finally withdraws some cash
from his back account. Next, he tries to take out the card. Unfortunately, since the specific
card reader of the Automated Teller Machine was jammed by the hidden thief, the customer
is unable to do so.
The customer then goes out to seek some type of help to get out his particular card
from the ATM machine. Meanwhile, the thief enters into the ATM again. This time he has
the plan to steal money from the customer’s bank account. He thus, took the decision to know
about the PIN of the customer’s ATM card.
He knew that the PIN number is of four digits and there is a fixed probability of this
detection of PIN within the ATM machine.
The total number of possibilities of the detecting of the four keys that could be
entered by the thief is as follows:
5P4 = 5!/(5 - 4)! = 5!/4! = 1205P4 = 5!/(5 - 4)! = 5!/4! = 120 times.
Thus, the thief can detect the PIN of the customer for about 120 new ways. Although,
each and every ATM system has their own security features and all of them should be
maintained substantially. The most important restriction in any ATM entry is the number of
entry into the machine. Only three times the PIN number could be given and if this number
exceeds, and more than three numbers of wrong entries are given, the card would
automatically be blocked or jammed.
INFORMATION SECURITY
Question 2
An ATM or an Automated Teller Machine is the particular device that is utilized for
the purpose of cash withdrawal from any specific bank account. The users of this ATM are
provided with a unique card that has a number within it and a personal identification number
or PIN number (Peltier, 2013). This unique card number and the PIN number make that
particular ATM card absolutely different from the rest of the cards and thus only the
authorized user can access the bank account.
As per the given scenario, a thief wants to steal money from any typical ATM
machine and thus he has eventually broken the Automated Teller Machine with the help of a
screwdriver. He has even jammed the card reader of that ATM machine and has broken the
five specific keys of the keypad of the machine.
In the middle of all these, the thief had to stop his process of break in and had to hide
since a customer has approached to the ATM. The customer entered into the ATM, enters the
ATM card, punches his unique 4 digits PIN number and then finally withdraws some cash
from his back account. Next, he tries to take out the card. Unfortunately, since the specific
card reader of the Automated Teller Machine was jammed by the hidden thief, the customer
is unable to do so.
The customer then goes out to seek some type of help to get out his particular card
from the ATM machine. Meanwhile, the thief enters into the ATM again. This time he has
the plan to steal money from the customer’s bank account. He thus, took the decision to know
about the PIN of the customer’s ATM card.
He knew that the PIN number is of four digits and there is a fixed probability of this
detection of PIN within the ATM machine.
The total number of possibilities of the detecting of the four keys that could be
entered by the thief is as follows:
5P4 = 5!/(5 - 4)! = 5!/4! = 1205P4 = 5!/(5 - 4)! = 5!/4! = 120 times.
Thus, the thief can detect the PIN of the customer for about 120 new ways. Although,
each and every ATM system has their own security features and all of them should be
maintained substantially. The most important restriction in any ATM entry is the number of
entry into the machine. Only three times the PIN number could be given and if this number
exceeds, and more than three numbers of wrong entries are given, the card would
automatically be blocked or jammed.

5
INFORMATION SECURITY
Question 3
The typical process of security for uniquely identifying any particular individual is
known as biometric authentication procedure. The unique characteristics or features of
biological attribute of any person are utilized in this type of system to recognize him without
any type of problem (Von Solms & Van Niekerk, 2013). This type of verification is done in
almost all offices, schools or colleges. Fraud cases or forged identification is avoided in the
biometric authentication. The biometric authentication system is the unique combination of
biological features and information system.
Databases are present within these types of biometric authentication systems. The
databases are responsible for collecting as well as storing all types of authenticated data that
are being extracted from the previously existing data (Baskerville, Spagnoletti & Kim, 2014).
The data that is entered in the real time are matched with the data present within the database.
This helps to know about the fact whether the person who is entering into the system or the
building is actually the authenticated person or not. If the data is not matched, the
authentication fails and the system stops the person from entering into the building or getting
access of that system. This type of authentication system is also utilized in the control of the
access to the physical devices or any type of digital resources. Sufficient communication
bandwidth is provided and thus preventing of the bottleneck occurrence is extremely
significant (Jouini, Rabai & Aissa, 2014). Disaster recovery and redundancy are also checked
by this. Thus, data redundancy is avoided by the system of biometric authentication. Various
people; even utilize this type of authentication system for locking their phones, tablets or
laptops. It is very difficult to crack any computing device that is already being locked with
bio-metric authentication.
Although, few disadvantages are also present in this type of systems. For these
disadvantages, people are reluctant to utilize this system. Three such important reasons are
depicted below with their solutions.
i) Requirement of Extra Hardware: This is the most important reason that people
wish to avoid biometric machines for their use (Soomro, Shah & Ahmed, 2016). When any
office installs the biometric system, they would also have to install the biometric machine or
system in their building. Without the system, it is nearly impossible to implement the
biometric within the office.
For solving the problem of extra or additional requirement of hardware, the office can
opt for cost effective and cheap hardware. This would be helpful for the office or school as
their budget would be maintained.
ii) Lack of Data Accuracy: The second reason of people being reluctant with the
biometric authentication system is the lack of data accuracy. The accuracy of the information
or data that is being entered within the biometric system is not perfect and often it loses
integrity (Tamjidyamcholo etal., 2013).
To help in type of situation, various metrics like False Rejection Rate or FRR and
False Acceptance Rate or Far are being utilized.
iii) Problem in Password Resetting: The final reason of various people being
absolutely reluctant with biometric system is that the password could not reset easily.
INFORMATION SECURITY
Question 3
The typical process of security for uniquely identifying any particular individual is
known as biometric authentication procedure. The unique characteristics or features of
biological attribute of any person are utilized in this type of system to recognize him without
any type of problem (Von Solms & Van Niekerk, 2013). This type of verification is done in
almost all offices, schools or colleges. Fraud cases or forged identification is avoided in the
biometric authentication. The biometric authentication system is the unique combination of
biological features and information system.
Databases are present within these types of biometric authentication systems. The
databases are responsible for collecting as well as storing all types of authenticated data that
are being extracted from the previously existing data (Baskerville, Spagnoletti & Kim, 2014).
The data that is entered in the real time are matched with the data present within the database.
This helps to know about the fact whether the person who is entering into the system or the
building is actually the authenticated person or not. If the data is not matched, the
authentication fails and the system stops the person from entering into the building or getting
access of that system. This type of authentication system is also utilized in the control of the
access to the physical devices or any type of digital resources. Sufficient communication
bandwidth is provided and thus preventing of the bottleneck occurrence is extremely
significant (Jouini, Rabai & Aissa, 2014). Disaster recovery and redundancy are also checked
by this. Thus, data redundancy is avoided by the system of biometric authentication. Various
people; even utilize this type of authentication system for locking their phones, tablets or
laptops. It is very difficult to crack any computing device that is already being locked with
bio-metric authentication.
Although, few disadvantages are also present in this type of systems. For these
disadvantages, people are reluctant to utilize this system. Three such important reasons are
depicted below with their solutions.
i) Requirement of Extra Hardware: This is the most important reason that people
wish to avoid biometric machines for their use (Soomro, Shah & Ahmed, 2016). When any
office installs the biometric system, they would also have to install the biometric machine or
system in their building. Without the system, it is nearly impossible to implement the
biometric within the office.
For solving the problem of extra or additional requirement of hardware, the office can
opt for cost effective and cheap hardware. This would be helpful for the office or school as
their budget would be maintained.
ii) Lack of Data Accuracy: The second reason of people being reluctant with the
biometric authentication system is the lack of data accuracy. The accuracy of the information
or data that is being entered within the biometric system is not perfect and often it loses
integrity (Tamjidyamcholo etal., 2013).
To help in type of situation, various metrics like False Rejection Rate or FRR and
False Acceptance Rate or Far are being utilized.
iii) Problem in Password Resetting: The final reason of various people being
absolutely reluctant with biometric system is that the password could not reset easily.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
INFORMATION SECURITY
The passwords could be easily reset with regulations like HIPAA, Sarbanes-Oxley
and PCI-DDS. These do not incur any type of complexity.
INFORMATION SECURITY
The passwords could be easily reset with regulations like HIPAA, Sarbanes-Oxley
and PCI-DDS. These do not incur any type of complexity.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
INFORMATION SECURITY
Question 4
Biometric authentication system can be solely defined as the verification process of
any user’s identity, which eventually involves the any type of biological input, scanning or
even analysis of the body parts. The methods of biometric authentication are utilized for the
successful protection of several types of systems, such as the logical systems that are being
facilitated through the access points of hardware or even to the physical systems that are
eventually protected with the help of physical barriers (Chaudhry et al., 2015). The physical
barriers mainly refer to the secured facilities as well as the protected research site. The
biometric authentication system is very much different from the other authentication systems
like passwords or unique usernames and it is extremely effective.
Biometric authentication system is the most effective authentication system as it is
impossible to transfer any biological feature or characteristic to any other person. Thus, the
chances of fraud cases are almost nil in this type of authentication system. For the schools,
colleges, and offices any kind of forged attendance is reduced or removed and thus the
confidentiality or integrity of the attendance is maintained properly.
The traditional expenses of the biometric system sometimes make it difficult to
implement or utilize (Schroff, Kalenichenko & Philbin, 2015). However, the most important
advantages of this system mainly include improvised security and privacy, improvised
customer experience and satisfaction, reduction in the operational costs and also avoidance of
password remembrance or lost.
The popular examples of the biometric authentication system are the iris recognition,
face recognition, fingerprint recognition, identification of DNA, voice recognition, scanning
of retina, scanning of palm, scanning of hand geometry and many others.
Biometric authentication provides perfect results and thus helps to maintain the
integrity and confidentiality (Frank et al., 2013). However, they are certain situations, where
this particular system fails to provide perfect or accurate outputs. It falsifies the data and the
system is not trusted again. This type of situation mainly arrives when the authorized person
is stopped from getting access of his or her own things. The false negative rates are then
considered as more serious than the false rates that are positive. Two circumstances are
depicted below, which helps to understand this type of situation.
i) Restriction in Accessing Possessions: This type of circumstance occurs while any
authorized user is being restricted to access his or her things. It is his right to access his own
things. However, due to few issues or problems in the information security system of the
biometric authentication system, the authorized user is stopped from accessing (Sayed et al.,
2013). Thus he can face various tough situations due to this.
ii) Failure in Recognition of Patients: The next significant circumstance of false
negative rates in biometric system is while detecting the biometric feature of any individual.
Suppose that individual is a patient and he is unable to reach out to the doctors. His doctors
might not be able to reach to him as the doors or the entry points are locked with the
biometric authentication of the patient. This can cause serious problem and the patient might
be in danger.
INFORMATION SECURITY
Question 4
Biometric authentication system can be solely defined as the verification process of
any user’s identity, which eventually involves the any type of biological input, scanning or
even analysis of the body parts. The methods of biometric authentication are utilized for the
successful protection of several types of systems, such as the logical systems that are being
facilitated through the access points of hardware or even to the physical systems that are
eventually protected with the help of physical barriers (Chaudhry et al., 2015). The physical
barriers mainly refer to the secured facilities as well as the protected research site. The
biometric authentication system is very much different from the other authentication systems
like passwords or unique usernames and it is extremely effective.
Biometric authentication system is the most effective authentication system as it is
impossible to transfer any biological feature or characteristic to any other person. Thus, the
chances of fraud cases are almost nil in this type of authentication system. For the schools,
colleges, and offices any kind of forged attendance is reduced or removed and thus the
confidentiality or integrity of the attendance is maintained properly.
The traditional expenses of the biometric system sometimes make it difficult to
implement or utilize (Schroff, Kalenichenko & Philbin, 2015). However, the most important
advantages of this system mainly include improvised security and privacy, improvised
customer experience and satisfaction, reduction in the operational costs and also avoidance of
password remembrance or lost.
The popular examples of the biometric authentication system are the iris recognition,
face recognition, fingerprint recognition, identification of DNA, voice recognition, scanning
of retina, scanning of palm, scanning of hand geometry and many others.
Biometric authentication provides perfect results and thus helps to maintain the
integrity and confidentiality (Frank et al., 2013). However, they are certain situations, where
this particular system fails to provide perfect or accurate outputs. It falsifies the data and the
system is not trusted again. This type of situation mainly arrives when the authorized person
is stopped from getting access of his or her own things. The false negative rates are then
considered as more serious than the false rates that are positive. Two circumstances are
depicted below, which helps to understand this type of situation.
i) Restriction in Accessing Possessions: This type of circumstance occurs while any
authorized user is being restricted to access his or her things. It is his right to access his own
things. However, due to few issues or problems in the information security system of the
biometric authentication system, the authorized user is stopped from accessing (Sayed et al.,
2013). Thus he can face various tough situations due to this.
ii) Failure in Recognition of Patients: The next significant circumstance of false
negative rates in biometric system is while detecting the biometric feature of any individual.
Suppose that individual is a patient and he is unable to reach out to the doctors. His doctors
might not be able to reach to him as the doors or the entry points are locked with the
biometric authentication of the patient. This can cause serious problem and the patient might
be in danger.
8
INFORMATION SECURITY
Question 5
1st part
Encryption can be defined as the safest mode for hiding any confidential information
from the unauthorized access. Thus, this confidentiality should be maintained with utmost
safety and security (Singh, 2013). Columnar transposition is the specific type or method of
encryption that helps to encrypt or decrypt any sensitive information or data. It is the process
by which plain text is being encrypted to a cipher text so that all the unauthorized users are
unable to hack or crack it. The plain text could be written in any language, however, the
cipher text is written in a decrypted format. The order of all the units in a cipher text is altered
and thus the plaintext is solely recorded (Tamjidyamcholo etal., 2013). Mathematically, any
particular bijective function is being utilized on the positions of the characters for the purpose
of encrypting and a particular inverse function for decryption that typical cipher text. The
transposition cipher could be easily decrypted with the help of a columnar transposition of the
method of decrypting. It is done by permutation procedure. The best methodology of
transposition cipher is the rail fence cipher method. The plain text within the rail fence cipher
is usually written downwards as specific rails of any imaginary fence and thus shifting up
when it is pushed to bottom. The first keyword could be utilized for both times or even some
other key could be utilized for the application of this algorithm during the next time (Sayed et
al., 2013). The process of rail fence consists of two steps.
i) Looking at column length through sub division of the length with length of the key.
ii) Message that is written in the columns repeatedly and thus the key is retransforms
all columns.
2nd part
George has a company that is responsible for producing mobile phones. He is facing
competition in the market and he has decided to change few things in the existing phones. To
prevent the information from getting leaked, he has encrypted the information. This is done
with Caesar cipher.
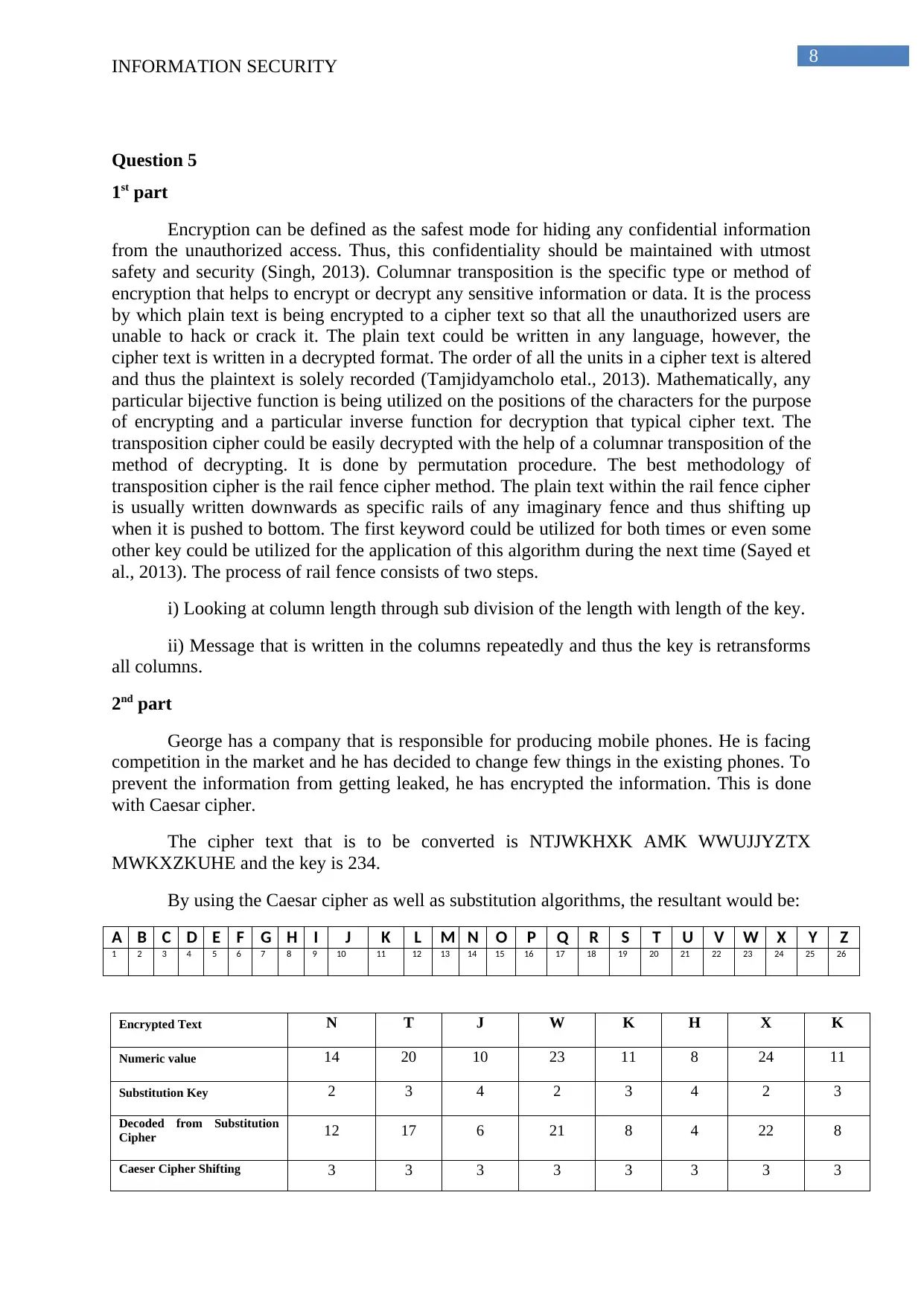
The cipher text that is to be converted is NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE and the key is 234.
By using the Caesar cipher as well as substitution algorithms, the resultant would be:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
Encrypted Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Substitution Key 2 3 4 2 3 4 2 3
Decoded from Substitution
Cipher 12 17 6 21 8 4 22 8
Caeser Cipher Shifting 3 3 3 3 3 3 3 3
INFORMATION SECURITY
Question 5
1st part
Encryption can be defined as the safest mode for hiding any confidential information
from the unauthorized access. Thus, this confidentiality should be maintained with utmost
safety and security (Singh, 2013). Columnar transposition is the specific type or method of
encryption that helps to encrypt or decrypt any sensitive information or data. It is the process
by which plain text is being encrypted to a cipher text so that all the unauthorized users are
unable to hack or crack it. The plain text could be written in any language, however, the
cipher text is written in a decrypted format. The order of all the units in a cipher text is altered
and thus the plaintext is solely recorded (Tamjidyamcholo etal., 2013). Mathematically, any
particular bijective function is being utilized on the positions of the characters for the purpose
of encrypting and a particular inverse function for decryption that typical cipher text. The
transposition cipher could be easily decrypted with the help of a columnar transposition of the
method of decrypting. It is done by permutation procedure. The best methodology of
transposition cipher is the rail fence cipher method. The plain text within the rail fence cipher
is usually written downwards as specific rails of any imaginary fence and thus shifting up
when it is pushed to bottom. The first keyword could be utilized for both times or even some
other key could be utilized for the application of this algorithm during the next time (Sayed et
al., 2013). The process of rail fence consists of two steps.
i) Looking at column length through sub division of the length with length of the key.
ii) Message that is written in the columns repeatedly and thus the key is retransforms
all columns.
2nd part
George has a company that is responsible for producing mobile phones. He is facing
competition in the market and he has decided to change few things in the existing phones. To
prevent the information from getting leaked, he has encrypted the information. This is done
with Caesar cipher.
The cipher text that is to be converted is NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE and the key is 234.
By using the Caesar cipher as well as substitution algorithms, the resultant would be:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
Encrypted Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Substitution Key 2 3 4 2 3 4 2 3
Decoded from Substitution
Cipher 12 17 6 21 8 4 22 8
Caeser Cipher Shifting 3 3 3 3 3 3 3 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
INFORMATION SECURITY
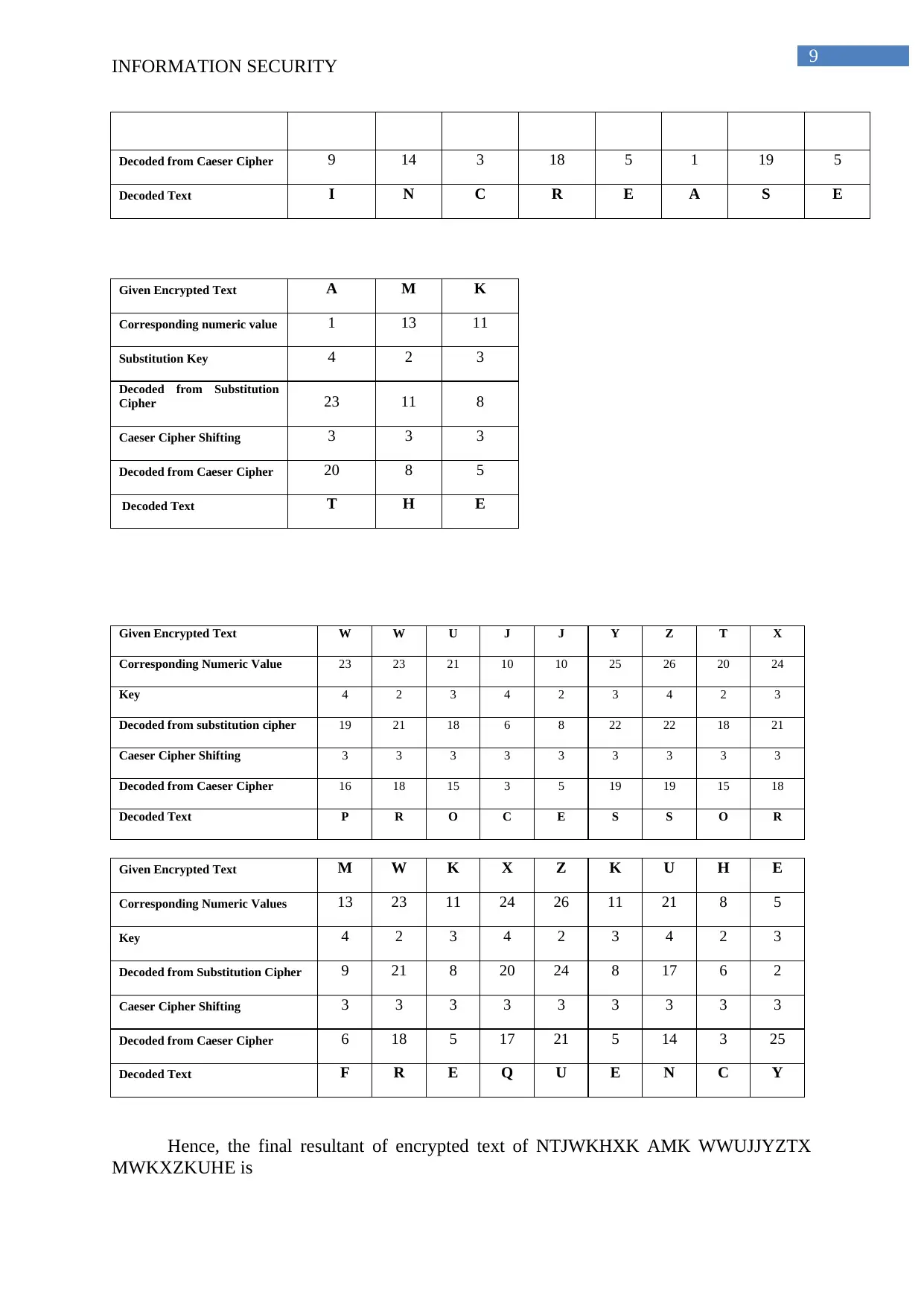
Decoded from Caeser Cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Given Encrypted Text A M K
Corresponding numeric value 1 13 11
Substitution Key 4 2 3
Decoded from Substitution
Cipher 23 11 8
Caeser Cipher Shifting 3 3 3
Decoded from Caeser Cipher 20 8 5
Decoded Text T H E
Given Encrypted Text W W U J J Y Z T X
Corresponding Numeric Value 23 23 21 10 10 25 26 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 19 21 18 6 8 22 22 18 21
Caeser Cipher Shifting 3 3 3 3 3 3 3 3 3
Decoded from Caeser Cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Given Encrypted Text M W K X Z K U H E
Corresponding Numeric Values 13 23 11 24 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from Substitution Cipher 9 21 8 20 24 8 17 6 2
Caeser Cipher Shifting 3 3 3 3 3 3 3 3 3
Decoded from Caeser Cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Hence, the final resultant of encrypted text of NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE is
INFORMATION SECURITY
Decoded from Caeser Cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Given Encrypted Text A M K
Corresponding numeric value 1 13 11
Substitution Key 4 2 3
Decoded from Substitution
Cipher 23 11 8
Caeser Cipher Shifting 3 3 3
Decoded from Caeser Cipher 20 8 5
Decoded Text T H E
Given Encrypted Text W W U J J Y Z T X
Corresponding Numeric Value 23 23 21 10 10 25 26 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 19 21 18 6 8 22 22 18 21
Caeser Cipher Shifting 3 3 3 3 3 3 3 3 3
Decoded from Caeser Cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Given Encrypted Text M W K X Z K U H E
Corresponding Numeric Values 13 23 11 24 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from Substitution Cipher 9 21 8 20 24 8 17 6 2
Caeser Cipher Shifting 3 3 3 3 3 3 3 3 3
Decoded from Caeser Cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Hence, the final resultant of encrypted text of NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
INFORMATION SECURITY
INCREASE THE PROCESSOR FREQUENCY.
INFORMATION SECURITY
INCREASE THE PROCESSOR FREQUENCY.

11
INFORMATION SECURITY
References
Baskerville, R., Spagnoletti, P., & Kim, J. (2014). Incident-centered information security:
Managing a strategic balance between prevention and response. Information &
Management, 51(1), 138-151.
Chaudhry, S. A., Mahmood, K., Naqvi, H., & Khan, M. K. (2015). An improved and secure
biometric authentication scheme for telecare medicine information systems based on
elliptic curve cryptography. Journal of Medical Systems, 39(11), 175.
Frank, M., Biedert, R., Ma, E., Martinovic, I., & Song, D. (2013). Touchalytics: On the
applicability of touchscreen input as a behavioral biometric for continuous
authentication. IEEE transactions on information forensics and security, 8(1), 136-
148.
Galliers, R. D., & Leidner, D. E. (Eds.). (2014). Strategic information management:
challenges and strategies in managing information systems. Routledge.
Jouini, M., Rabai, L. B. A., & Aissa, A. B. (2014). Classification of security threats in
information systems. Procedia Computer Science, 32, 489-496.
Laudon, K. C., & Laudon, J. P. (2015). Management Information Systems: Managing the
Digital Firm Plus MyMISLab with Pearson eText--Access Card Package. Prentice
Hall Press.
Peltier, T. R. (2013). Information security fundamentals. CRC Press.
Rainer, R. K., Cegielski, C. G., Splettstoesser-Hogeterp, I., & Sanchez-Rodriguez, C.
(2013). Introduction to information systems. John Wiley & Sons.
Sayed, B., Traoré, I., Woungang, I., & Obaidat, M. S. (2013). Biometric authentication using
mouse gesture dynamics. IEEE Systems Journal, 7(2), 262-274.
Schroff, F., Kalenichenko, D., & Philbin, J. (2015). Facenet: A unified embedding for face
recognition and clustering. In Proceedings of the IEEE conference on computer vision
and pattern recognition (pp. 815-823).
Singh, G. (2013). A study of encryption algorithms (RSA, DES, 3DES and AES) for
information security. International Journal of Computer Applications, 67(19).
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), 215-225.
Stair, R., & Reynolds, G. (2013). Principles of information systems. Cengage Learning.
Tamjidyamcholo, A., Baba, M. S. B., Tamjid, H., & Gholipour, R. (2013). Information
security–Professional perceptions of knowledge-sharing intention under self-efficacy,
trust, reciprocity, and shared-language. Computers & Education, 68, 223-232.
Venkatesh, V., Brown, S. A., & Bala, H. (2013). Bridging the qualitative-quantitative divide:
Guidelines for conducting mixed methods research in information systems. MIS
quarterly, 37(1).
INFORMATION SECURITY
References
Baskerville, R., Spagnoletti, P., & Kim, J. (2014). Incident-centered information security:
Managing a strategic balance between prevention and response. Information &
Management, 51(1), 138-151.
Chaudhry, S. A., Mahmood, K., Naqvi, H., & Khan, M. K. (2015). An improved and secure
biometric authentication scheme for telecare medicine information systems based on
elliptic curve cryptography. Journal of Medical Systems, 39(11), 175.
Frank, M., Biedert, R., Ma, E., Martinovic, I., & Song, D. (2013). Touchalytics: On the
applicability of touchscreen input as a behavioral biometric for continuous
authentication. IEEE transactions on information forensics and security, 8(1), 136-
148.
Galliers, R. D., & Leidner, D. E. (Eds.). (2014). Strategic information management:
challenges and strategies in managing information systems. Routledge.
Jouini, M., Rabai, L. B. A., & Aissa, A. B. (2014). Classification of security threats in
information systems. Procedia Computer Science, 32, 489-496.
Laudon, K. C., & Laudon, J. P. (2015). Management Information Systems: Managing the
Digital Firm Plus MyMISLab with Pearson eText--Access Card Package. Prentice
Hall Press.
Peltier, T. R. (2013). Information security fundamentals. CRC Press.
Rainer, R. K., Cegielski, C. G., Splettstoesser-Hogeterp, I., & Sanchez-Rodriguez, C.
(2013). Introduction to information systems. John Wiley & Sons.
Sayed, B., Traoré, I., Woungang, I., & Obaidat, M. S. (2013). Biometric authentication using
mouse gesture dynamics. IEEE Systems Journal, 7(2), 262-274.
Schroff, F., Kalenichenko, D., & Philbin, J. (2015). Facenet: A unified embedding for face
recognition and clustering. In Proceedings of the IEEE conference on computer vision
and pattern recognition (pp. 815-823).
Singh, G. (2013). A study of encryption algorithms (RSA, DES, 3DES and AES) for
information security. International Journal of Computer Applications, 67(19).
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), 215-225.
Stair, R., & Reynolds, G. (2013). Principles of information systems. Cengage Learning.
Tamjidyamcholo, A., Baba, M. S. B., Tamjid, H., & Gholipour, R. (2013). Information
security–Professional perceptions of knowledge-sharing intention under self-efficacy,
trust, reciprocity, and shared-language. Computers & Education, 68, 223-232.
Venkatesh, V., Brown, S. A., & Bala, H. (2013). Bridging the qualitative-quantitative divide:
Guidelines for conducting mixed methods research in information systems. MIS
quarterly, 37(1).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



