A Comprehensive Report on Information Security at Banks of America
VerifiedAdded on 2021/01/02
|14
|3858
|413
Report
AI Summary
This report provides a detailed analysis of information security practices within Banks of America, focusing on the development and implementation of a robust security program. It addresses the importance of information security in the context of a multinational financial service provider, emphasizing the need to protect sensitive financial data from cyberattacks and unauthorized access. The report outlines key components of a security program, including risk assessment, management, system testing, and incident response, along with the roles and responsibilities of security management staff. It also provides a plan for incorporating changes, including training requirements, and explores the application of ISO security standards, specifically recommending a suitable standard for Banks of America. The report further examines the sustainability of certifications, threats, and risk assessment strategies to ensure the ongoing protection of confidential information. Finally, the report offers practical recommendations for enhancing security measures and mitigating potential risks within the organization.

Information security
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................3
Developing a security program in Banks of America ................................................................3
Roles and responsibilities of security management staff members in preventing the secured
information..................................................................................................................................6
Provide a plan to make these changes incorporating training requirements...............................7
ISO Security standards and determine the suitable standard for Banks of America..................8
Sustainability of certification, threats and risk assessment.......................................................10
CONCLUSION..............................................................................................................................12
REFERENCES..............................................................................................................................13
2
INTRODUCTION...........................................................................................................................3
Developing a security program in Banks of America ................................................................3
Roles and responsibilities of security management staff members in preventing the secured
information..................................................................................................................................6
Provide a plan to make these changes incorporating training requirements...............................7
ISO Security standards and determine the suitable standard for Banks of America..................8
Sustainability of certification, threats and risk assessment.......................................................10
CONCLUSION..............................................................................................................................12
REFERENCES..............................................................................................................................13
2

INTRODUCTION
Information security is referred as state of protecting the confidential information of
organization in order to prevent data from unauthorised users. Info-sec is considered as practice
which is performed to prevent use of highly secured data from unauthorised people. This protects
the data from hacking and other malpractices which destroy potential capabilities of information
security. The present report is based on the information security of Banks of America which
deals in wealth management and bank investment corporation. The study will provide some
aspects of developing security program in an organisation. This report will also cover the
planning strategies to provide the security to confidential information and it also focuses on
training requirements of such incorporated changes in enterprise. Also, roles of current security
personnel with appropriate suggestions in order to implement new planning to prevent security
of information. It will also provide the ISO/ IEC 27000 series of information security
management and furthermore and risk assessment strategies and threats.
Developing a security program in Banks of America
Banks of America is the multinational financial service provider which provides support
to those who need funding and investment for different purpose it is dealing with highly secured
data on a regular basis as basic operation of the company is to deal with large financial sources
of data. Information security programs describe structure and efforts of the security management
staff members to minimise the risk in order to provide quality based and integrated data services
to customers (Ahmad, Maynard and Park, 2014). These type of institutions require high
information security in order to facilitate the large funding to other companies or to individual.
Huge amount of financial data in banks of America need to be protected against the
criminal practices such as cyber-attacks and protection of information from unauthorised user.
Following functions are needed to implement info-sec programs such as Risk assessment,
management, system testing, policy legal assessment, incident response, planning, measurement
compliance etc. description of these security programs is enumerated below:
1. Risk assessment: this can be termed as analysing and identifying the risk elements of the
Banks of America. It is helpful in determining correct implementation of new strategies
for securing the data and information.
3
Information security is referred as state of protecting the confidential information of
organization in order to prevent data from unauthorised users. Info-sec is considered as practice
which is performed to prevent use of highly secured data from unauthorised people. This protects
the data from hacking and other malpractices which destroy potential capabilities of information
security. The present report is based on the information security of Banks of America which
deals in wealth management and bank investment corporation. The study will provide some
aspects of developing security program in an organisation. This report will also cover the
planning strategies to provide the security to confidential information and it also focuses on
training requirements of such incorporated changes in enterprise. Also, roles of current security
personnel with appropriate suggestions in order to implement new planning to prevent security
of information. It will also provide the ISO/ IEC 27000 series of information security
management and furthermore and risk assessment strategies and threats.
Developing a security program in Banks of America
Banks of America is the multinational financial service provider which provides support
to those who need funding and investment for different purpose it is dealing with highly secured
data on a regular basis as basic operation of the company is to deal with large financial sources
of data. Information security programs describe structure and efforts of the security management
staff members to minimise the risk in order to provide quality based and integrated data services
to customers (Ahmad, Maynard and Park, 2014). These type of institutions require high
information security in order to facilitate the large funding to other companies or to individual.
Huge amount of financial data in banks of America need to be protected against the
criminal practices such as cyber-attacks and protection of information from unauthorised user.
Following functions are needed to implement info-sec programs such as Risk assessment,
management, system testing, policy legal assessment, incident response, planning, measurement
compliance etc. description of these security programs is enumerated below:
1. Risk assessment: this can be termed as analysing and identifying the risk elements of the
Banks of America. It is helpful in determining correct implementation of new strategies
for securing the data and information.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2. Risk management: This can be considered as finding alternative solution of those risk
factors which are assessed. Security management are able to identify course of action for
preventing threats and risks in maintaining the confidentiality.
3. System testing: the purpose of this program is to implement new concepts and analyse
working impacts of this new methodologies which is applied in order to eliminate risk
factor from banks.
4. Policy: These are considered as plans and procedures which are adopted to overcome the
drawbacks of previously used security policy. This helps in an effective management of
information security in Banks of America.
5. Legal assessment: It can be referred as the government rules and regulations which are
used to formulate the operational functions with legal standards and process of
government.
6. Incident response: This is determined as measures which are taken to overcome the
challenges of information security management (Baskerville, Spagnolett and Kim, 2014).
Application of appropriate course of action according to risk assessment are termed as
incident response to risk.
7. Planning: Banks of America apply various strategies and planning procedures to provide
high security to the financial information of banks. Security management is applying
functional risk assessment function to overcome threats of company.
8. Measurement: These can be considered as the actions which are taken to avoid
information security risk of Banks of America.
9. Compliance: The purpose of this function is to provide quality service to customers. This
is generally adopted to verify system and network administrator to provide required
treatment to security risk of bank.
10. Centralised authentication: This program is often used by security management
administrator to control the activities of risk management as a whole.
11. System security administration: The task is generally performed by manager of Banks of
America to develop security program in Banks of America.
4
factors which are assessed. Security management are able to identify course of action for
preventing threats and risks in maintaining the confidentiality.
3. System testing: the purpose of this program is to implement new concepts and analyse
working impacts of this new methodologies which is applied in order to eliminate risk
factor from banks.
4. Policy: These are considered as plans and procedures which are adopted to overcome the
drawbacks of previously used security policy. This helps in an effective management of
information security in Banks of America.
5. Legal assessment: It can be referred as the government rules and regulations which are
used to formulate the operational functions with legal standards and process of
government.
6. Incident response: This is determined as measures which are taken to overcome the
challenges of information security management (Baskerville, Spagnolett and Kim, 2014).
Application of appropriate course of action according to risk assessment are termed as
incident response to risk.
7. Planning: Banks of America apply various strategies and planning procedures to provide
high security to the financial information of banks. Security management is applying
functional risk assessment function to overcome threats of company.
8. Measurement: These can be considered as the actions which are taken to avoid
information security risk of Banks of America.
9. Compliance: The purpose of this function is to provide quality service to customers. This
is generally adopted to verify system and network administrator to provide required
treatment to security risk of bank.
10. Centralised authentication: This program is often used by security management
administrator to control the activities of risk management as a whole.
11. System security administration: The task is generally performed by manager of Banks of
America to develop security program in Banks of America.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

12. Training: It is generally provided to it staff members to understand the use and
implementation of technology changes which helps in sustaining the authorised access of
data in banks of America.
13. Vulnerability assessment: This practice is done to predict or forecast different measured
in order to minimise the risk of information security in company (Dworkin, 2016). It is
helpful in identifying the vulnerable possibilities to secure data and information of banks.
Bank generally maintains large wealth to lend those financial resources to those small
medium enterprises who is in a great need to obtain investment for performing business
operations. Strong security programs need to be introduced in Banks of America to prevent the
use of confidential data from unauthorised users. Features which need to be applied to get the
effective security management of data are as follows:
Confidentiality: This is refers to the protection of data and information from an
unauthorised user. It is considered as a state in which the information is kept private from
those who are authorised to use it. This principle allows the access to data to people who
are authorised to it. Banks of America have established the concept of data hiding in
which customers are allowed to see only abstracted data. The customers are assigned with
their unique bank number and passwords to access bank account with specific
information (Ifinedo, 2014). All the other information is not provided to users as if
availability of detailed information to customers may cause cyberattacks and other
malware practices.
Integrity: Application of this policy in Banks of America ensure the accuracy and
consistency of data. It allows flow of accurate and proper information of customers in
order to keep records of transactions which are actually occurred by authorised user. It
contains the non-manipulative source of information. Banking institutions has adopted
many soft wares to prevent interruptions of hackers and in order to maintain integration
of trustworthy information. This principle also ensures that authorised user have
manipulated or edit the original information.
Availability: It can be considered as accessibility of available data at the time when it is
in need. If highly secured information is available at all the time, then it might be
5
implementation of technology changes which helps in sustaining the authorised access of
data in banks of America.
13. Vulnerability assessment: This practice is done to predict or forecast different measured
in order to minimise the risk of information security in company (Dworkin, 2016). It is
helpful in identifying the vulnerable possibilities to secure data and information of banks.
Bank generally maintains large wealth to lend those financial resources to those small
medium enterprises who is in a great need to obtain investment for performing business
operations. Strong security programs need to be introduced in Banks of America to prevent the
use of confidential data from unauthorised users. Features which need to be applied to get the
effective security management of data are as follows:
Confidentiality: This is refers to the protection of data and information from an
unauthorised user. It is considered as a state in which the information is kept private from
those who are authorised to use it. This principle allows the access to data to people who
are authorised to it. Banks of America have established the concept of data hiding in
which customers are allowed to see only abstracted data. The customers are assigned with
their unique bank number and passwords to access bank account with specific
information (Ifinedo, 2014). All the other information is not provided to users as if
availability of detailed information to customers may cause cyberattacks and other
malware practices.
Integrity: Application of this policy in Banks of America ensure the accuracy and
consistency of data. It allows flow of accurate and proper information of customers in
order to keep records of transactions which are actually occurred by authorised user. It
contains the non-manipulative source of information. Banking institutions has adopted
many soft wares to prevent interruptions of hackers and in order to maintain integration
of trustworthy information. This principle also ensures that authorised user have
manipulated or edit the original information.
Availability: It can be considered as accessibility of available data at the time when it is
in need. If highly secured information is available at all the time, then it might be
5

responsible for loss of information security in banks which prove to be a great threat for
the bank.
Roles and responsibilities of security management staff members in preventing the secured
information
Managers of Banks of America are responsible for correct implementation of policies to
secure data and confidential information of the banks. Banks of America have hired highly
experienced professionals to strategies and planning the security aspects to maintain data security
and integrity. Management of Banks of America has to perform strong security practices such as
Authorize processing (C&A), contingency planning, data integrity, continues monitoring,
network and personal security etc. Security management is considered as one of the major task of
managers as they have to prevent confidential data from unauthorised access (Jouini, Rabai and
Aissa, 2014). Various roles and responsibilities are performed by management security staff
members. Such duties are as follows:
Role and responsibilities of Banks of America includes various duties as they have to
establish the appropriate security policies and are also answerable to those who are
maintaining the confidential and secured information within company.
Physical and environmental protection is also referred as one of the greatest concern for
security management staff members. Management have to provide security to system and
building because this infrastructure issues may be responsible for destruction of data and
info-sec (information security).
Security management are responsible for formulation of policies and procedures in Banks
of America, so formulation of these standards need to be strongly developed in order to
achieve successful banking functions to support the confidential data.
Managers are also accountable for loss of data and security as they are the one who have
formulated security policies in Banks of America.
Suggestions
Security management professionals should be highly skilled and they must know main
drawbacks of security policies because risk assessment allows security managers to
overcome threats and this would help them to develop strong security plans.
6
the bank.
Roles and responsibilities of security management staff members in preventing the secured
information
Managers of Banks of America are responsible for correct implementation of policies to
secure data and confidential information of the banks. Banks of America have hired highly
experienced professionals to strategies and planning the security aspects to maintain data security
and integrity. Management of Banks of America has to perform strong security practices such as
Authorize processing (C&A), contingency planning, data integrity, continues monitoring,
network and personal security etc. Security management is considered as one of the major task of
managers as they have to prevent confidential data from unauthorised access (Jouini, Rabai and
Aissa, 2014). Various roles and responsibilities are performed by management security staff
members. Such duties are as follows:
Role and responsibilities of Banks of America includes various duties as they have to
establish the appropriate security policies and are also answerable to those who are
maintaining the confidential and secured information within company.
Physical and environmental protection is also referred as one of the greatest concern for
security management staff members. Management have to provide security to system and
building because this infrastructure issues may be responsible for destruction of data and
info-sec (information security).
Security management are responsible for formulation of policies and procedures in Banks
of America, so formulation of these standards need to be strongly developed in order to
achieve successful banking functions to support the confidential data.
Managers are also accountable for loss of data and security as they are the one who have
formulated security policies in Banks of America.
Suggestions
Security management professionals should be highly skilled and they must know main
drawbacks of security policies because risk assessment allows security managers to
overcome threats and this would help them to develop strong security plans.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

One should be certified with professional certifications as it ensures the accessibility of
information with a certified authority. The government have also regulated laws
regarding protection of data.
Proper Application of laws and ethics in organisation would be helpful in providing ease
to access the authorised data.
Provide a plan to make these changes incorporating training requirements.
As the managers apply new security concepts in banking institutions then it need to be
conveyed to all the staff members of security management. This would provide them a better
guidance to use newly designed software in company (Lee and et.al., 2017). These practices need
to be applied in Banks of America using appropriate knowledge and skills regarding the use and
its purpose in order to maintain highly secured data. Bank of America deals with financial data
which is to be kept private from other unauthorised users. Information security possess a big
threat to the banking institution. They have to formulate strong security policies in company this
will be resulted in effective implementation of strategies. Advancement in information
technology bring changes in working policies of company and hence, this require proper
trainings and skills related to the use of those implemented policies in organisation. Various
strategies and plans are required to incorporate changes in training requirements. These plans are
as follows:
Security manager of Banks of America need support from technical team to implement
this security planning and strategies within bank. The administrator and technician are
required to work under the supervision of manager. Info-sec department mainly belongs
to IT management staff members (Information security, 2018).
They analyse current implementation of strategies and they are also responsible for
determining the drawbacks of these plans and then security manager changes plan
accordingly.
Main responsibility of security manager is to provide long term secured ways to protect
the huge amount of information from hackers and different malware practices.
Another popular security option includes the flow of information from security manager
to IT department which renders different administrative services (Peltier, 2016).
7
information with a certified authority. The government have also regulated laws
regarding protection of data.
Proper Application of laws and ethics in organisation would be helpful in providing ease
to access the authorised data.
Provide a plan to make these changes incorporating training requirements.
As the managers apply new security concepts in banking institutions then it need to be
conveyed to all the staff members of security management. This would provide them a better
guidance to use newly designed software in company (Lee and et.al., 2017). These practices need
to be applied in Banks of America using appropriate knowledge and skills regarding the use and
its purpose in order to maintain highly secured data. Bank of America deals with financial data
which is to be kept private from other unauthorised users. Information security possess a big
threat to the banking institution. They have to formulate strong security policies in company this
will be resulted in effective implementation of strategies. Advancement in information
technology bring changes in working policies of company and hence, this require proper
trainings and skills related to the use of those implemented policies in organisation. Various
strategies and plans are required to incorporate changes in training requirements. These plans are
as follows:
Security manager of Banks of America need support from technical team to implement
this security planning and strategies within bank. The administrator and technician are
required to work under the supervision of manager. Info-sec department mainly belongs
to IT management staff members (Information security, 2018).
They analyse current implementation of strategies and they are also responsible for
determining the drawbacks of these plans and then security manager changes plan
accordingly.
Main responsibility of security manager is to provide long term secured ways to protect
the huge amount of information from hackers and different malware practices.
Another popular security option includes the flow of information from security manager
to IT department which renders different administrative services (Peltier, 2016).
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
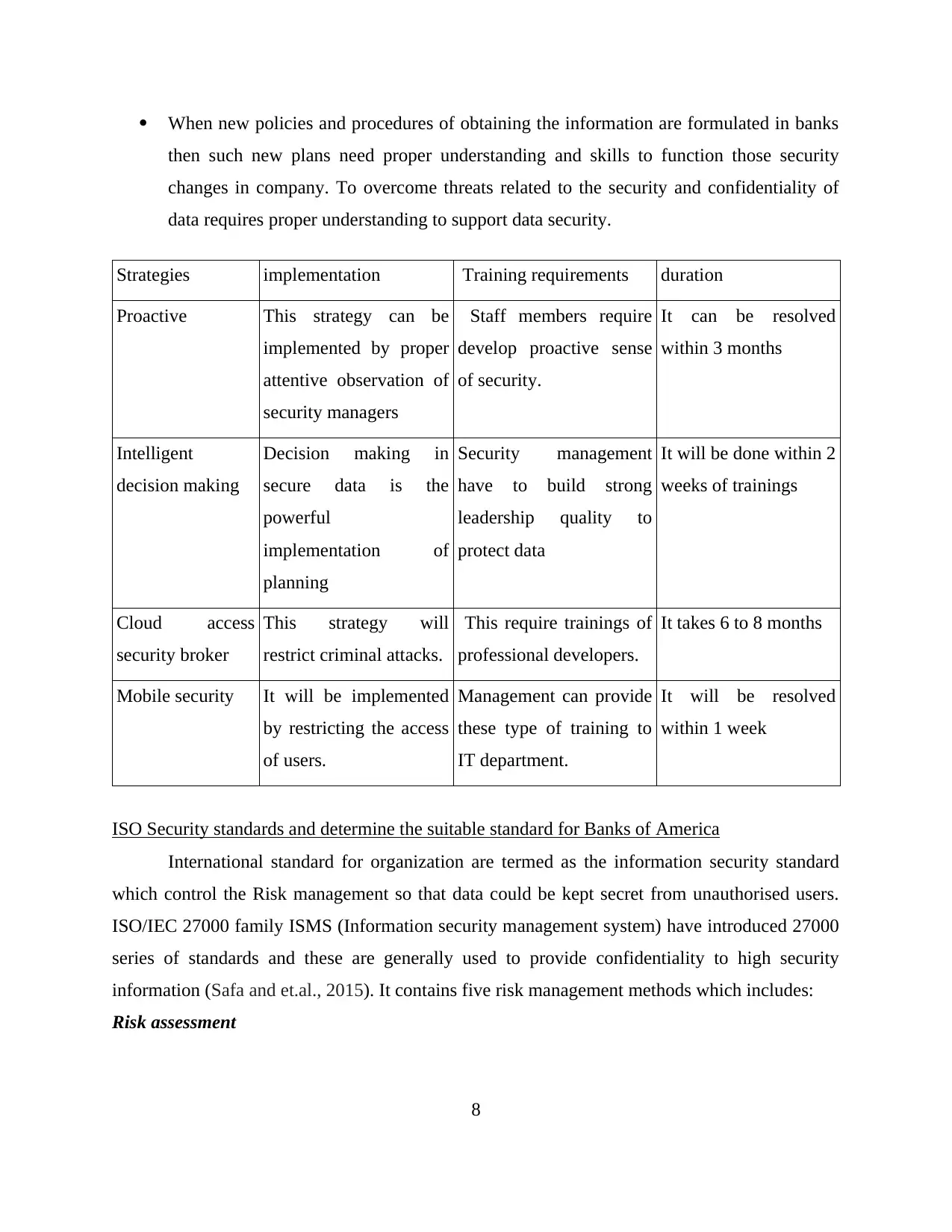
When new policies and procedures of obtaining the information are formulated in banks
then such new plans need proper understanding and skills to function those security
changes in company. To overcome threats related to the security and confidentiality of
data requires proper understanding to support data security.
Strategies implementation Training requirements duration
Proactive This strategy can be
implemented by proper
attentive observation of
security managers
Staff members require
develop proactive sense
of security.
It can be resolved
within 3 months
Intelligent
decision making
Decision making in
secure data is the
powerful
implementation of
planning
Security management
have to build strong
leadership quality to
protect data
It will be done within 2
weeks of trainings
Cloud access
security broker
This strategy will
restrict criminal attacks.
This require trainings of
professional developers.
It takes 6 to 8 months
Mobile security It will be implemented
by restricting the access
of users.
Management can provide
these type of training to
IT department.
It will be resolved
within 1 week
ISO Security standards and determine the suitable standard for Banks of America
International standard for organization are termed as the information security standard
which control the Risk management so that data could be kept secret from unauthorised users.
ISO/IEC 27000 family ISMS (Information security management system) have introduced 27000
series of standards and these are generally used to provide confidentiality to high security
information (Safa and et.al., 2015). It contains five risk management methods which includes:
Risk assessment
8
then such new plans need proper understanding and skills to function those security
changes in company. To overcome threats related to the security and confidentiality of
data requires proper understanding to support data security.
Strategies implementation Training requirements duration
Proactive This strategy can be
implemented by proper
attentive observation of
security managers
Staff members require
develop proactive sense
of security.
It can be resolved
within 3 months
Intelligent
decision making
Decision making in
secure data is the
powerful
implementation of
planning
Security management
have to build strong
leadership quality to
protect data
It will be done within 2
weeks of trainings
Cloud access
security broker
This strategy will
restrict criminal attacks.
This require trainings of
professional developers.
It takes 6 to 8 months
Mobile security It will be implemented
by restricting the access
of users.
Management can provide
these type of training to
IT department.
It will be resolved
within 1 week
ISO Security standards and determine the suitable standard for Banks of America
International standard for organization are termed as the information security standard
which control the Risk management so that data could be kept secret from unauthorised users.
ISO/IEC 27000 family ISMS (Information security management system) have introduced 27000
series of standards and these are generally used to provide confidentiality to high security
information (Safa and et.al., 2015). It contains five risk management methods which includes:
Risk assessment
8

It is the considered as the methodology in which management of Banks of America
predicts and forecasts threats to security. Risk assessment is also useful for ISMS to control data
and information and this restricts the possibilities of fraudulent practices in an organization. Risk
can be assessed by evaluating the following survey. for this the following factors which includes
identifying risk components, analysing those factors, and then evaluating risks by applying
appropriate method to control Risk management system.
Risk treatment
This methodology consists of various ways to prevent the loss of secured information. It
can be considered as the method in which strategies related to risk assessment is practically
implemented. Risk treatment includes strategic goals, functions to overcome these threats,
business process, system architecture and implementation of System development life-cycle
(SDLC) phases (Safa, Von Solms and Furnell, 2016). It is practiced by applying tools and
techniques to assess the risk to info-sec in Banks of America.
Risk Acceptance
It can be addressed by the proper guidance of information security management. Risk
assessment can be assessed by applying the appropriate course of action. This can be treated as
responding risks by the alternative course of action. There can be various risk response
components which includes acceptance, avoidance, migration, sharing and transfer of Risk.
Risk communication
This risk management component can be addressed by proper analysing and monitoring
risk factors of information security in Banks of America. It is used to verify that planned
strategies are effectively responding to risk management requirements. Also, it identifies the
impact of risk assessment strategies which supports banks in protecting financial security
information. Risk communication is also changes the work ethics in order to implement secure
ways to protect confidential data.
Risk monitoring and Review
It is a final stage which briefly describe the effectiveness of implemented tools and
techniques. This approach is used to monitor the ongoing effectiveness and efficiency of NIST
risk management model.
9
predicts and forecasts threats to security. Risk assessment is also useful for ISMS to control data
and information and this restricts the possibilities of fraudulent practices in an organization. Risk
can be assessed by evaluating the following survey. for this the following factors which includes
identifying risk components, analysing those factors, and then evaluating risks by applying
appropriate method to control Risk management system.
Risk treatment
This methodology consists of various ways to prevent the loss of secured information. It
can be considered as the method in which strategies related to risk assessment is practically
implemented. Risk treatment includes strategic goals, functions to overcome these threats,
business process, system architecture and implementation of System development life-cycle
(SDLC) phases (Safa, Von Solms and Furnell, 2016). It is practiced by applying tools and
techniques to assess the risk to info-sec in Banks of America.
Risk Acceptance
It can be addressed by the proper guidance of information security management. Risk
assessment can be assessed by applying the appropriate course of action. This can be treated as
responding risks by the alternative course of action. There can be various risk response
components which includes acceptance, avoidance, migration, sharing and transfer of Risk.
Risk communication
This risk management component can be addressed by proper analysing and monitoring
risk factors of information security in Banks of America. It is used to verify that planned
strategies are effectively responding to risk management requirements. Also, it identifies the
impact of risk assessment strategies which supports banks in protecting financial security
information. Risk communication is also changes the work ethics in order to implement secure
ways to protect confidential data.
Risk monitoring and Review
It is a final stage which briefly describe the effectiveness of implemented tools and
techniques. This approach is used to monitor the ongoing effectiveness and efficiency of NIST
risk management model.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

One more risk management standard was introduced that is ISO 31000. This basically
helps in providing the structure to these methods (Shropshire, Warkentin and Sharma, 2015). It
also helps in evaluating the threats of economic performances in Banks of America. NIST
(National institutes of standard and technology) has established its fundamental approach in
order to achieve the effective standards for risk management.
Management of risks in order to prevent threats of info-sec can be considered as a
comprehensive process in which various activities are forecasted and predicted so that
management get an idea whenever an unauthorised user try to hack information security of
Banks of America. These risk management components are practiced to overcome the threats
and challenges of security management in banks.
Most suitable security standard for Banks of America: This organization have adopted
functional risk management model. It is mainly used to identify sustainable development of
strategies and links between the process of risk management and their required resources for
proper functioning of risk management models. Banks have identified threats of Banks of
America in order to secure details from hackers as they might misuse bank information which
may result in cybercrimes. So functional risk management can be identified as an appropriate
risk management model to control and protect the data.
Sustainability of certification, threats and risk assessment
Information security need to be protected as it can affect the organisations in a long term.
IS security standards are imposed for providing sustainability of certification to protect the data
from criminals. Security credentials are created to secure data by providing the authorised
certificate to access Private information of company (Siponen, Mahmood and Pahnila, 2014).
Various security methods have contributed towards protecting the information of customers.
These standards had not only provided actual security breaches but it had also lowered the
possibilities of risk occurrence in organization. SDLC phases are designed to protect the
confidentiality of information at Banks of America. Large threats are identified by security
management system. There are lot of threats and challenges faced by security management.
Threat identification:
10
helps in providing the structure to these methods (Shropshire, Warkentin and Sharma, 2015). It
also helps in evaluating the threats of economic performances in Banks of America. NIST
(National institutes of standard and technology) has established its fundamental approach in
order to achieve the effective standards for risk management.
Management of risks in order to prevent threats of info-sec can be considered as a
comprehensive process in which various activities are forecasted and predicted so that
management get an idea whenever an unauthorised user try to hack information security of
Banks of America. These risk management components are practiced to overcome the threats
and challenges of security management in banks.
Most suitable security standard for Banks of America: This organization have adopted
functional risk management model. It is mainly used to identify sustainable development of
strategies and links between the process of risk management and their required resources for
proper functioning of risk management models. Banks have identified threats of Banks of
America in order to secure details from hackers as they might misuse bank information which
may result in cybercrimes. So functional risk management can be identified as an appropriate
risk management model to control and protect the data.
Sustainability of certification, threats and risk assessment
Information security need to be protected as it can affect the organisations in a long term.
IS security standards are imposed for providing sustainability of certification to protect the data
from criminals. Security credentials are created to secure data by providing the authorised
certificate to access Private information of company (Siponen, Mahmood and Pahnila, 2014).
Various security methods have contributed towards protecting the information of customers.
These standards had not only provided actual security breaches but it had also lowered the
possibilities of risk occurrence in organization. SDLC phases are designed to protect the
confidentiality of information at Banks of America. Large threats are identified by security
management system. There are lot of threats and challenges faced by security management.
Threat identification:
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Social media attacks: These threats are major threats to industry as attackers identify and
interact with cluster of websites in order to hack the secured data. Lack of encryption:These threats can be resolved by application of appropriate project
management strategies to secure the information of Banks of America. Application of
project management includes System development life-cycle to test the system before
new technologies are ready to implement in the business. SDLC contains various phases
which helps in testing the function and formulations of those policies.
Technology with weak security:Threats of security management may include problems
regarding resistance to new technology. When pros and cons of implemented technology
is clearly communicated to staff members then it could be helpful in adopting the changes
and this will resulted in effective security management methodologies (Soomro, Shah and
Ahmed, 2017). So this would be helpful for security management staff members to resist
the new strategies in banks in order to apply powerful security controls to restrict the
users in accessing the high security data it provides user authentication of certified users.
Risk assessment
Threats might be in the form of cyber-attacks, software attacks, human error or failure,
thefts, technical errors, information extortion. Vulnerability assessment of these types of
threats may include traffic disturbance when router is transmitting the values.
It may be responsible for destruction if this is compromised. Human errors might be
responsible for the loss of information and security so this need to be verified before
processing or transactions are occurred.
To protect the information security of banks lot of laws and regulations are implemented
which have enhanced the quality of securing information (Tuna and et.al., 2017).
Potential implementation of risk assessment techniques helps in identifying the elements
which impact on the organization negatively.
Project Risk management includes the following processes such as risk identification,
Risk quantification, Risk response development and risk response control.
11
interact with cluster of websites in order to hack the secured data. Lack of encryption:These threats can be resolved by application of appropriate project
management strategies to secure the information of Banks of America. Application of
project management includes System development life-cycle to test the system before
new technologies are ready to implement in the business. SDLC contains various phases
which helps in testing the function and formulations of those policies.
Technology with weak security:Threats of security management may include problems
regarding resistance to new technology. When pros and cons of implemented technology
is clearly communicated to staff members then it could be helpful in adopting the changes
and this will resulted in effective security management methodologies (Soomro, Shah and
Ahmed, 2017). So this would be helpful for security management staff members to resist
the new strategies in banks in order to apply powerful security controls to restrict the
users in accessing the high security data it provides user authentication of certified users.
Risk assessment
Threats might be in the form of cyber-attacks, software attacks, human error or failure,
thefts, technical errors, information extortion. Vulnerability assessment of these types of
threats may include traffic disturbance when router is transmitting the values.
It may be responsible for destruction if this is compromised. Human errors might be
responsible for the loss of information and security so this need to be verified before
processing or transactions are occurred.
To protect the information security of banks lot of laws and regulations are implemented
which have enhanced the quality of securing information (Tuna and et.al., 2017).
Potential implementation of risk assessment techniques helps in identifying the elements
which impact on the organization negatively.
Project Risk management includes the following processes such as risk identification,
Risk quantification, Risk response development and risk response control.
11

CONCLUSION
The study had concluded that banking institutions and other financial organisations need
to implement great security planning to prevent the confidential data from cyberattacks. report
had covered few points which are related to roles and responsibilities of managers who impose
the security policies in organisation. This Study had also mentioned ISO security standards and
NIST risk management model to identify the risk factors. Furthermore, it had also explained 5
info-sec components to prevent high security data from unauthorised user. It has also provided
suitable security model in Banks of America. This report had also discussed risks and security
certification in maintaining the secured data.
12
The study had concluded that banking institutions and other financial organisations need
to implement great security planning to prevent the confidential data from cyberattacks. report
had covered few points which are related to roles and responsibilities of managers who impose
the security policies in organisation. This Study had also mentioned ISO security standards and
NIST risk management model to identify the risk factors. Furthermore, it had also explained 5
info-sec components to prevent high security data from unauthorised user. It has also provided
suitable security model in Banks of America. This report had also discussed risks and security
certification in maintaining the secured data.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




