Information Security and Risk Management: A Case Study on E-bay
VerifiedAdded on 2020/03/02
|11
|3102
|443
Report
AI Summary
This report provides a comprehensive analysis of IS security and risk management, with a specific focus on the e-commerce giant, E-bay. The introduction highlights the importance of information security in organizations, particularly concerning data management and client information protection, addressing the challenges of unauthorized data access. The report then delves into the necessity of a robust IT security policy, outlining its main components such as security definitions, enforcement mechanisms, user access protocols, security profiles, password policies, and email usage guidelines. The report also includes an overview of E-bay's organizational structure, illustrating how information systems contribute to its competitive advantage. The discussion covers security standards like ISO 17799 and ISO 27001, and security controls, including authentication and audit trails. The risk analysis section explores E-bay's approach to identifying and evaluating risks, with a focus on network protocols like SSL. Finally, the report examines contingency planning, including vendor readiness, to mitigate potential business disruptions and security concerns. This report offers a detailed examination of E-bay's security infrastructure.

Running head: IS SECURITY AND RISK MANAGEMENT 1
IS Security and Risk Management
Name:
Institution Affiliation:
IS Security and Risk Management
Name:
Institution Affiliation:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IS SECURITY AND RISK MANAGEMENT 2
Introduction
The information security is significant in organization in the areas such as the record keeping, as
well as on the financial uses. The IT security could help organization in solving the requirements
of the clients particularly in the management of their personal information, the data as well as the
security information (Ali, 2014). These are the challenges which are encountered by the
organization particularly in the management of the data so that it does not fall in the hands of the
unauthorized individuals or perhaps the hackers. An effective IT security management system
help in the reduction of the risk when there are crisis in the organization. The organization
should understand the IT security to enable them overcome the challenges (Ali, 2014).
Additionally, organization should have policies when it comes to securing of their data so that it
could be safe (Ross, 2013). In this research it intends to answer the question on how the
information technology security could be enforced in the organization. Additionally, the essay
will look at the main content of the IT security policy, and how it is determined (Bergström &
Åhlfeldt, 2014). The essay will be focused on the E-Bay organization. Other components that
will be looked are the IT model for the organization, the security standards and the control, risk
analysis and contingency planning. Lastly, it will focus on the analysis of the IT threats,
vulnerabilities and tools.
Key Terms Identification
Protocols: These are often described in an industry or perhaps the international standard such as
the TCP/IP protocols that uses the set rules to exchange the message with the other internet
points at the data packet levels.
Introduction
The information security is significant in organization in the areas such as the record keeping, as
well as on the financial uses. The IT security could help organization in solving the requirements
of the clients particularly in the management of their personal information, the data as well as the
security information (Ali, 2014). These are the challenges which are encountered by the
organization particularly in the management of the data so that it does not fall in the hands of the
unauthorized individuals or perhaps the hackers. An effective IT security management system
help in the reduction of the risk when there are crisis in the organization. The organization
should understand the IT security to enable them overcome the challenges (Ali, 2014).
Additionally, organization should have policies when it comes to securing of their data so that it
could be safe (Ross, 2013). In this research it intends to answer the question on how the
information technology security could be enforced in the organization. Additionally, the essay
will look at the main content of the IT security policy, and how it is determined (Bergström &
Åhlfeldt, 2014). The essay will be focused on the E-Bay organization. Other components that
will be looked are the IT model for the organization, the security standards and the control, risk
analysis and contingency planning. Lastly, it will focus on the analysis of the IT threats,
vulnerabilities and tools.
Key Terms Identification
Protocols: These are often described in an industry or perhaps the international standard such as
the TCP/IP protocols that uses the set rules to exchange the message with the other internet
points at the data packet levels.

IS SECURITY AND RISK MANAGEMENT 3
Contingency: This is a plan which is set in place to prevent any shortcoming which may occur
in the future.
Standards: These are definite rules, principles or perhaps the measures which have been
established to guide the organization against the risk that could occur.
Overview of E-bay organization
This is a multinational e-commerce corporation, which help the online consumer to consumer as
well as the business to consumer sales (Chen, 2009). The organization manages eBay.com which
is an online shopping portal that helps the people and the businesses to buy and sell goods and
services globally (Bergström & Åhlfeldt, 2014). In addition to its auction style sales, the website
has expanded to “Buy It Now” shopping. Over the years the company has become one of the best
online retail business organization.
Discussion of Policy and Auditing features for E-bay
The organizations requires protection against the cyber-attack which entails to document the
information technology security policy (Ross, 2013). Each and every employee need to
understand their obligation in order to protect the organization data (Anton, Anderson & Mesic,
2004). The workers should have a clear expectation about their behavior when it comes to
interaction with the information of the organization sales (Chen, 2009). There is need to have an
IT security policy that should be published, understandable as well as enforceable. The
following are the main components of an information technology security policy for E-bay
organization;
Contingency: This is a plan which is set in place to prevent any shortcoming which may occur
in the future.
Standards: These are definite rules, principles or perhaps the measures which have been
established to guide the organization against the risk that could occur.
Overview of E-bay organization
This is a multinational e-commerce corporation, which help the online consumer to consumer as
well as the business to consumer sales (Chen, 2009). The organization manages eBay.com which
is an online shopping portal that helps the people and the businesses to buy and sell goods and
services globally (Bergström & Åhlfeldt, 2014). In addition to its auction style sales, the website
has expanded to “Buy It Now” shopping. Over the years the company has become one of the best
online retail business organization.
Discussion of Policy and Auditing features for E-bay
The organizations requires protection against the cyber-attack which entails to document the
information technology security policy (Ross, 2013). Each and every employee need to
understand their obligation in order to protect the organization data (Anton, Anderson & Mesic,
2004). The workers should have a clear expectation about their behavior when it comes to
interaction with the information of the organization sales (Chen, 2009). There is need to have an
IT security policy that should be published, understandable as well as enforceable. The
following are the main components of an information technology security policy for E-bay
organization;
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IS SECURITY AND RISK MANAGEMENT 4
Security definition: the E-bay IT security policy have a well-defined security vision for the
organization which is to safeguard on the safety of the clients and that of the business which they
operate with (Axelrod, Bayuk & Schutzer, 2009). This security definition is meant to make
certain there is confidentiality, integrity in addition to the accessibility to the data and the
resources through the use of the effective and established information technology security
methods and the process.
Enforcement: on this part it evidently outlines precisely how the policy could be enforced and
also precisely how the security breaches might be handled sales (Chen, 2009). Additionally, the
chief data officer in addition to the information system security have the responsibility of
implementing on these policy and ensuringtheir compliance (Bergström & Åhlfeldt, 2014). In
this section it includes the procedures to request short term exception to the policy. Additionally,
all the exceptions to the policy needs to be reviewed and also approved or perhaps denied by the
security officers concerned.
The user access to the computer resources: on their policy it outlines the functions along with
the responsibilities of the customers accessing the resources of the business especially to their
website (Peltier, 2013). It could include things like the passwords, guidelines for the termination
of the accounts, procedure for the threat notification and the security awareness training to the
clients.
Security profiles: E-bay has an excellent security policy including the data which recognizes
precisely how the security profiles might be utilized uniformly throughout the common devices,
such as the firewalls, proxy servers and the servers (Peltier, 2013).
Security definition: the E-bay IT security policy have a well-defined security vision for the
organization which is to safeguard on the safety of the clients and that of the business which they
operate with (Axelrod, Bayuk & Schutzer, 2009). This security definition is meant to make
certain there is confidentiality, integrity in addition to the accessibility to the data and the
resources through the use of the effective and established information technology security
methods and the process.
Enforcement: on this part it evidently outlines precisely how the policy could be enforced and
also precisely how the security breaches might be handled sales (Chen, 2009). Additionally, the
chief data officer in addition to the information system security have the responsibility of
implementing on these policy and ensuringtheir compliance (Bergström & Åhlfeldt, 2014). In
this section it includes the procedures to request short term exception to the policy. Additionally,
all the exceptions to the policy needs to be reviewed and also approved or perhaps denied by the
security officers concerned.
The user access to the computer resources: on their policy it outlines the functions along with
the responsibilities of the customers accessing the resources of the business especially to their
website (Peltier, 2013). It could include things like the passwords, guidelines for the termination
of the accounts, procedure for the threat notification and the security awareness training to the
clients.
Security profiles: E-bay has an excellent security policy including the data which recognizes
precisely how the security profiles might be utilized uniformly throughout the common devices,
such as the firewalls, proxy servers and the servers (Peltier, 2013).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IS SECURITY AND RISK MANAGEMENT 5
Passwords: The passwords are very critical aspects especially in protecting the infrastructure of
the organization. They have higher passwords so that they do not compromise the organization
especially the website to the external threats, and also the insiders (Duncan & Whittington,
2014). The passwords such as the user log in details need to be strong not to be compromised
through social engineering or the password cracking procedures.
Email: in the security policy of the E-bay organization there is an email usage policy which is
very important. There are several viruses, malware and the Trojans which could use the email as
the vehicle in order to propagate themselves through the internet (Duncan & Whittington, 2014).
To prevent this there are content filtering email messages. These help to filter out attachments
with the extensions of exe, .scr or perhaps .inf, which would help enhance on the prevention
efforts.
Backup and recovery: E-bay does a comprehensive back-up as well as a recovery plan in order
to mitigate any incidents. The backup acts as the key for the past. E-bay has an effective backup
as well as recovery plans which are established through the comprehensive risk assessments of
all their systems on the networks.
Logical map of organisational structure
Passwords: The passwords are very critical aspects especially in protecting the infrastructure of
the organization. They have higher passwords so that they do not compromise the organization
especially the website to the external threats, and also the insiders (Duncan & Whittington,
2014). The passwords such as the user log in details need to be strong not to be compromised
through social engineering or the password cracking procedures.
Email: in the security policy of the E-bay organization there is an email usage policy which is
very important. There are several viruses, malware and the Trojans which could use the email as
the vehicle in order to propagate themselves through the internet (Duncan & Whittington, 2014).
To prevent this there are content filtering email messages. These help to filter out attachments
with the extensions of exe, .scr or perhaps .inf, which would help enhance on the prevention
efforts.
Backup and recovery: E-bay does a comprehensive back-up as well as a recovery plan in order
to mitigate any incidents. The backup acts as the key for the past. E-bay has an effective backup
as well as recovery plans which are established through the comprehensive risk assessments of
all their systems on the networks.
Logical map of organisational structure
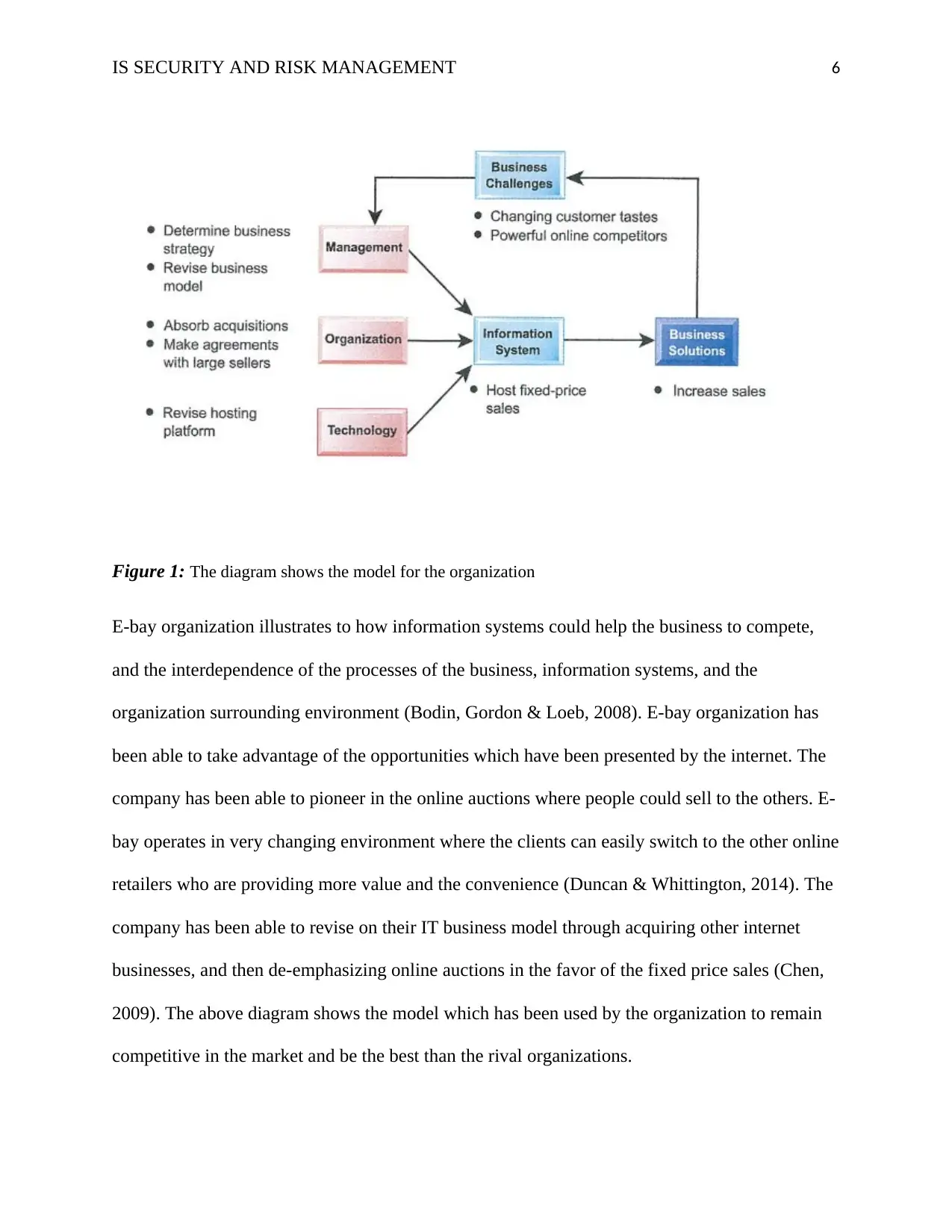
IS SECURITY AND RISK MANAGEMENT 6
Figure 1: The diagram shows the model for the organization
E-bay organization illustrates to how information systems could help the business to compete,
and the interdependence of the processes of the business, information systems, and the
organization surrounding environment (Bodin, Gordon & Loeb, 2008). E-bay organization has
been able to take advantage of the opportunities which have been presented by the internet. The
company has been able to pioneer in the online auctions where people could sell to the others. E-
bay operates in very changing environment where the clients can easily switch to the other online
retailers who are providing more value and the convenience (Duncan & Whittington, 2014). The
company has been able to revise on their IT business model through acquiring other internet
businesses, and then de-emphasizing online auctions in the favor of the fixed price sales (Chen,
2009). The above diagram shows the model which has been used by the organization to remain
competitive in the market and be the best than the rival organizations.
Figure 1: The diagram shows the model for the organization
E-bay organization illustrates to how information systems could help the business to compete,
and the interdependence of the processes of the business, information systems, and the
organization surrounding environment (Bodin, Gordon & Loeb, 2008). E-bay organization has
been able to take advantage of the opportunities which have been presented by the internet. The
company has been able to pioneer in the online auctions where people could sell to the others. E-
bay operates in very changing environment where the clients can easily switch to the other online
retailers who are providing more value and the convenience (Duncan & Whittington, 2014). The
company has been able to revise on their IT business model through acquiring other internet
businesses, and then de-emphasizing online auctions in the favor of the fixed price sales (Chen,
2009). The above diagram shows the model which has been used by the organization to remain
competitive in the market and be the best than the rival organizations.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IS SECURITY AND RISK MANAGEMENT 7
Discussion of Models and standards
There are various security standards and controls which are observed by E-bay organization
(Bodin, Gordon & Loeb, 2008). One of the security standards which is implemented in the
organization is ISO 17799 which defines the information as an assets which could exist in many
forms and has a value to the organization. The goal for the information security would be
suitably protect the assets of the organization to ensure that the continuity of the business,
minimize on the damage of the business, and maximize on the return of the investments (Bodin,
Gordon & Loeb, 2008). As defined by the ISO 17799 the information security has been
characterized as the preservation of the confidentiality which ensures that the information is
accessible only to the individuals who have been authorized to have access. Additionally, to
ensure integrity which ensure that safeguarding the accuracy and the completeness of the
information and the methods of processing (Lam, 2014). Lastly, it focus on the availability,
which ensures that the users who are authorized have the access to the data and associated assets
when they are required. The ISO 17799 has offered E-bay organization a benchmark against
which to build on the organizational information security. Moreover, it provides a mechanism to
manage of the processes of the information security. Another security standards that is utilized
by the organization is the ISO 27001 which is a security management specification (Bergström &
Åhlfeldt, 2014). It is a framework which is more often procedures as well as policies that entails
the physical, legal as well as the controls in the organization information risk management
process (PITAS, Němec & Soušek, 2014). This ISO has provided the organization the benefit of
proof for the security especially the third parties for the partners, customers and the legal aspects.
Moreover, there is a reduced cost through the optimization of the structures and transparency.
Discussion of Models and standards
There are various security standards and controls which are observed by E-bay organization
(Bodin, Gordon & Loeb, 2008). One of the security standards which is implemented in the
organization is ISO 17799 which defines the information as an assets which could exist in many
forms and has a value to the organization. The goal for the information security would be
suitably protect the assets of the organization to ensure that the continuity of the business,
minimize on the damage of the business, and maximize on the return of the investments (Bodin,
Gordon & Loeb, 2008). As defined by the ISO 17799 the information security has been
characterized as the preservation of the confidentiality which ensures that the information is
accessible only to the individuals who have been authorized to have access. Additionally, to
ensure integrity which ensure that safeguarding the accuracy and the completeness of the
information and the methods of processing (Lam, 2014). Lastly, it focus on the availability,
which ensures that the users who are authorized have the access to the data and associated assets
when they are required. The ISO 17799 has offered E-bay organization a benchmark against
which to build on the organizational information security. Moreover, it provides a mechanism to
manage of the processes of the information security. Another security standards that is utilized
by the organization is the ISO 27001 which is a security management specification (Bergström &
Åhlfeldt, 2014). It is a framework which is more often procedures as well as policies that entails
the physical, legal as well as the controls in the organization information risk management
process (PITAS, Němec & Soušek, 2014). This ISO has provided the organization the benefit of
proof for the security especially the third parties for the partners, customers and the legal aspects.
Moreover, there is a reduced cost through the optimization of the structures and transparency.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IS SECURITY AND RISK MANAGEMENT 8
Some of the security control which have been implemented by the organization is authentication.
The staff of the organization are required to pass the multi factor authentication before they gain
access to the system (Sadgrove, 2016). This helps keep the data of the organization safe from
exploit of any vulnerabilities from internal access or external access (Bergström & Åhlfeldt,
2014). Another control is the audit trail. The organization have a server which records the IP
addresses as well as the URLs for each of the access and they are able to retain such data for a
given period of time as an audit trail (Kranakis, Haroutunian & Shahbazian, 2008). There is also
the application of cryptography where the data is stored in encrypted on all the devices.
Discussion of Risk Analysis for E-bay
E-bay organization has a given protocol on how to carry the risk analysis. One thing they
highlight is to identify on the hazards. This is achieved through understanding of the various
difference between the hazard and the risk. The second thing is to decide on what could have
caused it and how (Bodin, Gordon & Loeb, 2008). When the organization identifies the risk that
have affected them they evaluate them and decide on the control measures. Some of the risk
analysis aspect to evaluate on the risks the focus is on security and the networks protocols, which
E-bay organization has implemented. One of the network protocol is the secure sockets layer
(Bodin, Gordon & Loeb, 2008). This is a cryptographic protocol which has been designed in
order to secure the communications over the TCP/IP networks. The SSL protocol became the
Transport Layer Security which is intended to provide a secure connections between the client
and the server through encrypting of the data which is passed between them. The E-bay network
has been encrypted so that any individual who do not have an accessibility to the network would
not sniff the packets, reading the user names, passwords, or maybe the credit card information as
Some of the security control which have been implemented by the organization is authentication.
The staff of the organization are required to pass the multi factor authentication before they gain
access to the system (Sadgrove, 2016). This helps keep the data of the organization safe from
exploit of any vulnerabilities from internal access or external access (Bergström & Åhlfeldt,
2014). Another control is the audit trail. The organization have a server which records the IP
addresses as well as the URLs for each of the access and they are able to retain such data for a
given period of time as an audit trail (Kranakis, Haroutunian & Shahbazian, 2008). There is also
the application of cryptography where the data is stored in encrypted on all the devices.
Discussion of Risk Analysis for E-bay
E-bay organization has a given protocol on how to carry the risk analysis. One thing they
highlight is to identify on the hazards. This is achieved through understanding of the various
difference between the hazard and the risk. The second thing is to decide on what could have
caused it and how (Bodin, Gordon & Loeb, 2008). When the organization identifies the risk that
have affected them they evaluate them and decide on the control measures. Some of the risk
analysis aspect to evaluate on the risks the focus is on security and the networks protocols, which
E-bay organization has implemented. One of the network protocol is the secure sockets layer
(Bodin, Gordon & Loeb, 2008). This is a cryptographic protocol which has been designed in
order to secure the communications over the TCP/IP networks. The SSL protocol became the
Transport Layer Security which is intended to provide a secure connections between the client
and the server through encrypting of the data which is passed between them. The E-bay network
has been encrypted so that any individual who do not have an accessibility to the network would
not sniff the packets, reading the user names, passwords, or maybe the credit card information as

IS SECURITY AND RISK MANAGEMENT 9
well as other confidential data which is sent across the network. The company also observes the
document protocol that is accountable for the compression, the encryption in addition to the
verification of the data. The data which the business transmit is split into the data. Each of the
record consist of the header byte, which is accompanied by protocol version, the length to which
the information is to be sent, in addition to the payload itself.
Analysis of business processes
The contingency plan can be done on the worst case risks which could affect the organization.
An example could be on the case when the business is not in a position of supporting itself
particularly on their ongoing basis. There could be issues of the security concern for the business
(Lam, 2014). On the contingency plan it contains various things such as the vendor readiness
plan. Each and every organization relies on the vendors in providing them with equipment,
supplies, goods as well as the services.
Discussion of Vendors
Some of the vendors could be regarded very critical than the others. To minimize on the
potential exposure to the disruption by the vendors, there are various steps which the company
takes in advance (Lam, 2014). One of the step would be to avoid a single source. The
organization has many vendors which provide each of our critical goods as well as the services
required to support the business. Example of the vendors for E-bay are WC and the Flipkart.
These groups helps the sellers to sell their goods to the shoppers all across the globe.
Depth of analysis of threat, vulnerabilities and tools
well as other confidential data which is sent across the network. The company also observes the
document protocol that is accountable for the compression, the encryption in addition to the
verification of the data. The data which the business transmit is split into the data. Each of the
record consist of the header byte, which is accompanied by protocol version, the length to which
the information is to be sent, in addition to the payload itself.
Analysis of business processes
The contingency plan can be done on the worst case risks which could affect the organization.
An example could be on the case when the business is not in a position of supporting itself
particularly on their ongoing basis. There could be issues of the security concern for the business
(Lam, 2014). On the contingency plan it contains various things such as the vendor readiness
plan. Each and every organization relies on the vendors in providing them with equipment,
supplies, goods as well as the services.
Discussion of Vendors
Some of the vendors could be regarded very critical than the others. To minimize on the
potential exposure to the disruption by the vendors, there are various steps which the company
takes in advance (Lam, 2014). One of the step would be to avoid a single source. The
organization has many vendors which provide each of our critical goods as well as the services
required to support the business. Example of the vendors for E-bay are WC and the Flipkart.
These groups helps the sellers to sell their goods to the shoppers all across the globe.
Depth of analysis of threat, vulnerabilities and tools
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IS SECURITY AND RISK MANAGEMENT 10
The vulnerabilities in the E-bay organization network security could be summed as the soft spots
which are present to every information technology network. The networks could be plugged into
three categories; the technology, configuration or the security policy weaknesses. The
technology have intrinsic security weaknesses. Some of the vulnerabilities which have affected
E-bay organization are TCP/IP protocol weaknesses, the operating and the network equipment.
When you look at the TCP protocol the HTTP, ICMP could be insecure. On the operating system
the OS could have security issues which needs to be addressed (Lam, 2014). The network
equipment weaknesses highlights that the various kind of the networks equipment’s such as the
routers, the firewalls have the security concerns and should be recognized in order to protect
against.
Some of the threats which the organization has encountered is the social engineering. This has
occurred where the attackers have been able to obtain the data from the individual’s accounts or
the organization to use it for the malicious purpose (Lam, 2014). One kind of the social
engineering that has been used by the attacker is phishing. The attackers use the email in an
attempt to trick individuals into providing their sensitive data, for example the credit card
numbers or perhaps the passwords.
One of the tool that has been used for attack to obtain the customer information is the keylogger.
This tool enables one to know everything which the user writes through the keyboard, and it can
capture on the screens. The organization usually uses the integrated sales as well as the purchases
system therefore the staff inputs data into the system which could pose a risk to occur.
The vulnerabilities in the E-bay organization network security could be summed as the soft spots
which are present to every information technology network. The networks could be plugged into
three categories; the technology, configuration or the security policy weaknesses. The
technology have intrinsic security weaknesses. Some of the vulnerabilities which have affected
E-bay organization are TCP/IP protocol weaknesses, the operating and the network equipment.
When you look at the TCP protocol the HTTP, ICMP could be insecure. On the operating system
the OS could have security issues which needs to be addressed (Lam, 2014). The network
equipment weaknesses highlights that the various kind of the networks equipment’s such as the
routers, the firewalls have the security concerns and should be recognized in order to protect
against.
Some of the threats which the organization has encountered is the social engineering. This has
occurred where the attackers have been able to obtain the data from the individual’s accounts or
the organization to use it for the malicious purpose (Lam, 2014). One kind of the social
engineering that has been used by the attacker is phishing. The attackers use the email in an
attempt to trick individuals into providing their sensitive data, for example the credit card
numbers or perhaps the passwords.
One of the tool that has been used for attack to obtain the customer information is the keylogger.
This tool enables one to know everything which the user writes through the keyboard, and it can
capture on the screens. The organization usually uses the integrated sales as well as the purchases
system therefore the staff inputs data into the system which could pose a risk to occur.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IS SECURITY AND RISK MANAGEMENT 11
References
Ali, S. M. (2014). Integration of information security essential controls into information
technology infrastructure library-A proposed framework. International Journal of
Applied, 4(1).
Anton, P., Anderson, R., & Mesic, R. (2004). Finding and Fixing Vulnerabilities in Information
Systems. Santa Monica: RAND Corporation.
Axelrod, C., Bayuk, J., & Schutzer, D. (2009). Enterprise information security and privacy.
Boston: Artech House.
Bergström, E., & Åhlfeldt, R. M. (2014, October). Information classification issues. In Nordic
Conference on Secure IT Systems (pp. 27-41). Springer, Cham.
Bodin, L. D., Gordon, L. A., & Loeb, M. P. (2008). Information security and risk management.
Communications of the ACM, 51(4), 64-68.
Chen, T. M. (2009). Information security and risk management. In Encyclopedia of Multimedia
Technology and Networking, Second Edition (pp. 668-674). IGI Global.
Duncan, B., & Whittington, M. (2014, September). Compliance with standards, assurance and
audit: Does this equal security?. In Proceedings of the 7th International Conference on
Security of Information and Networks (p. 77). ACM.
Kranakis, E., Haroutunian, E., & Shahbazian, E. (2008). Aspects of Network and Information
Security. Amsterdam: IOS Press.
Lam, J. (2014). Enterprise risk management: from incentives to controls. John Wiley & Sons.
Peltier, T. R. (2013). Information security fundamentals. CRC Press.
PITAS, J., Němec, V., & Soušek, R. (2014). Mutual Influence of Management Processes of
Stakeholders and Risk Management in Cyber Security Environment. In The 18th World
Multi-Conference on Systemics, Cybernetics and Informatics. Orlando, Florida:
International Institute of Informatics and Systemics (Vol. 2, pp. 94-97).
References
Ali, S. M. (2014). Integration of information security essential controls into information
technology infrastructure library-A proposed framework. International Journal of
Applied, 4(1).
Anton, P., Anderson, R., & Mesic, R. (2004). Finding and Fixing Vulnerabilities in Information
Systems. Santa Monica: RAND Corporation.
Axelrod, C., Bayuk, J., & Schutzer, D. (2009). Enterprise information security and privacy.
Boston: Artech House.
Bergström, E., & Åhlfeldt, R. M. (2014, October). Information classification issues. In Nordic
Conference on Secure IT Systems (pp. 27-41). Springer, Cham.
Bodin, L. D., Gordon, L. A., & Loeb, M. P. (2008). Information security and risk management.
Communications of the ACM, 51(4), 64-68.
Chen, T. M. (2009). Information security and risk management. In Encyclopedia of Multimedia
Technology and Networking, Second Edition (pp. 668-674). IGI Global.
Duncan, B., & Whittington, M. (2014, September). Compliance with standards, assurance and
audit: Does this equal security?. In Proceedings of the 7th International Conference on
Security of Information and Networks (p. 77). ACM.
Kranakis, E., Haroutunian, E., & Shahbazian, E. (2008). Aspects of Network and Information
Security. Amsterdam: IOS Press.
Lam, J. (2014). Enterprise risk management: from incentives to controls. John Wiley & Sons.
Peltier, T. R. (2013). Information security fundamentals. CRC Press.
PITAS, J., Němec, V., & Soušek, R. (2014). Mutual Influence of Management Processes of
Stakeholders and Risk Management in Cyber Security Environment. In The 18th World
Multi-Conference on Systemics, Cybernetics and Informatics. Orlando, Florida:
International Institute of Informatics and Systemics (Vol. 2, pp. 94-97).
1 out of 11
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

