CSI5133 - Information Security: Risk Management of Facial Recognition
VerifiedAdded on 2023/06/07
|22
|5582
|350
Report
AI Summary
This report provides a comprehensive analysis of facial recognition systems, focusing on the legal and ethical considerations surrounding their implementation, particularly in the context of the City of Perth's proposal. It explores the ethical principles and legal responsibilities relevant to information security professionals, including privacy, data protection, and compliance with regulations. The report also delves into risk management, covering risk identification, assessment, and mitigation strategies for facial recognition systems. Furthermore, it discusses various technologies for addressing security issues and highlights the advantages and disadvantages of facial recognition technology. The analysis includes considerations for system design, data storage, and potential impacts on individuals' rights to privacy and security. It also includes the role of risk management, risk identification, risk analysis and contingency planning in information security. The report concludes by summarizing the key findings and providing recommendations for responsible and ethical implementation of facial recognition systems.

Running Head: INFORMATION SECURITY 0
Information Security
Individual Assignment
Student Name
10/6/2018
Information Security
Individual Assignment
Student Name
10/6/2018
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Information security 1
Contents
Executive Summary.....................................................................................................................................1
Introduction.................................................................................................................................................3
Legal issues for security system...................................................................................................................3
Principles underlying the code of ethics..................................................................................................5
Responsibilities to clients........................................................................................................................6
For the community worker:.................................................................................................................6
Responsibility to Organizations...........................................................................................................6
Responsibility to colleagues....................................................................................................................6
The community worker is expected to:...............................................................................................6
The community worker will:................................................................................................................6
Risk management:.......................................................................................................................................7
Risk identification................................................................................................................................8
Identifying application software, hardware devices, and networking devices....................................9
Identification people, procedures, and information assets:..............................................................10
Risk Assessment:...............................................................................................................................11
Likelihood:.........................................................................................................................................12
Assessing potential loss:....................................................................................................................12
Percentage of risk mitigated by current controls:.............................................................................12
Uncertainty:.......................................................................................................................................12
Risk determination:...........................................................................................................................12
Identify possible controls:..................................................................................................................13
Technologies for solving security issues....................................................................................................13
Facial recognition system:.........................................................................................................................16
Conclusion.................................................................................................................................................16
References.................................................................................................................................................18
Contents
Executive Summary.....................................................................................................................................1
Introduction.................................................................................................................................................3
Legal issues for security system...................................................................................................................3
Principles underlying the code of ethics..................................................................................................5
Responsibilities to clients........................................................................................................................6
For the community worker:.................................................................................................................6
Responsibility to Organizations...........................................................................................................6
Responsibility to colleagues....................................................................................................................6
The community worker is expected to:...............................................................................................6
The community worker will:................................................................................................................6
Risk management:.......................................................................................................................................7
Risk identification................................................................................................................................8
Identifying application software, hardware devices, and networking devices....................................9
Identification people, procedures, and information assets:..............................................................10
Risk Assessment:...............................................................................................................................11
Likelihood:.........................................................................................................................................12
Assessing potential loss:....................................................................................................................12
Percentage of risk mitigated by current controls:.............................................................................12
Uncertainty:.......................................................................................................................................12
Risk determination:...........................................................................................................................12
Identify possible controls:..................................................................................................................13
Technologies for solving security issues....................................................................................................13
Facial recognition system:.........................................................................................................................16
Conclusion.................................................................................................................................................16
References.................................................................................................................................................18

Information security 2
Executive Summary
In this report, facial recognition system will discussed, and various types of security
systems will be discussed in respect of information system for security. This report has
explaining ethical and legal issues, which are associated with facial recognition system, and it
also analyses their implications. There are so many risk in that time of systems, it was also
included in this report for identification of risk and analysis on that risk and manage that risk. In
this report, different types of investigation data are included for better understanding of
information system. According to this report, there are so many reviews for security systems
with their classification. There are also some implementation data of a facial recognition system.
This report shows many key points about a security system. Different types of system
requirements included in this report. It was based on the security system, which was related to
finding issues for security in different aspects, such as legal and ethical.
In the end of the report, it discussed about advantages of facial recognition system and
other systems for security systems.
.
Executive Summary
In this report, facial recognition system will discussed, and various types of security
systems will be discussed in respect of information system for security. This report has
explaining ethical and legal issues, which are associated with facial recognition system, and it
also analyses their implications. There are so many risk in that time of systems, it was also
included in this report for identification of risk and analysis on that risk and manage that risk. In
this report, different types of investigation data are included for better understanding of
information system. According to this report, there are so many reviews for security systems
with their classification. There are also some implementation data of a facial recognition system.
This report shows many key points about a security system. Different types of system
requirements included in this report. It was based on the security system, which was related to
finding issues for security in different aspects, such as legal and ethical.
In the end of the report, it discussed about advantages of facial recognition system and
other systems for security systems.
.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Information security 3
Introduction
Security system is based on the analysis for problem and providing solution of that
problem. There are different legal and ethical issues for security reasons, which are discussed in
the next part of this report. In this report, City of Perth’s facial recognition system proposal and
implementation research was discussed. There are lot of things for consider to development of
facial recognition system in a city. So many issues occurred in that types of system related to
confidentiality, legality, and privacy of people (Reynolds, 2011). Therefore, there are so many
variations in the results of facial recognition system. It have some limitation in which it fails, still
it have many advantages for the security purpose. This report is explaining about issues of facial
recognition system implementation in the City of Perth (aap, 2017). Basic outcomes of this
report are identifying the legal and ethical issues related to facial recognition information
security system and about their implementation issues ( Parker, 2018). A main issue is risk
analysis for the facial recognition system. It was start from identification of risks for that system
and solution of that risk. There are different types of planning for implementation of a security
system ( Burt, 2018).
Legal issues for security system
For the information security expert, it is must to understand about the responsibilities of
organization for ethics and legal laws. Security system is responsible for the privacy and security
risks at the organization (WARREN, 2011). It I must to know about current laws and ethical
issues for implementation of the security system, so in future no more changes will require for
those issues in the security system ( Epps, 2018). To reduce liability always considers all legal
action for information security system. It should be informed to all employees and operator for
proper use of their right, according to legal and ethical obligation (Quinn, 2010). Therefore,
organization focuses on the main objectives and properly uses of information technology in the
information system (Gupta & Hammond, 2005). In the first part of this report, it is describe
about the legislation and regulations for information management system of an organization.
In the next part, it is describe about the ethical issues in implementing security system in
the organization. Policies are required because of acceptable and unacceptable behaviors of
Introduction
Security system is based on the analysis for problem and providing solution of that
problem. There are different legal and ethical issues for security reasons, which are discussed in
the next part of this report. In this report, City of Perth’s facial recognition system proposal and
implementation research was discussed. There are lot of things for consider to development of
facial recognition system in a city. So many issues occurred in that types of system related to
confidentiality, legality, and privacy of people (Reynolds, 2011). Therefore, there are so many
variations in the results of facial recognition system. It have some limitation in which it fails, still
it have many advantages for the security purpose. This report is explaining about issues of facial
recognition system implementation in the City of Perth (aap, 2017). Basic outcomes of this
report are identifying the legal and ethical issues related to facial recognition information
security system and about their implementation issues ( Parker, 2018). A main issue is risk
analysis for the facial recognition system. It was start from identification of risks for that system
and solution of that risk. There are different types of planning for implementation of a security
system ( Burt, 2018).
Legal issues for security system
For the information security expert, it is must to understand about the responsibilities of
organization for ethics and legal laws. Security system is responsible for the privacy and security
risks at the organization (WARREN, 2011). It I must to know about current laws and ethical
issues for implementation of the security system, so in future no more changes will require for
those issues in the security system ( Epps, 2018). To reduce liability always considers all legal
action for information security system. It should be informed to all employees and operator for
proper use of their right, according to legal and ethical obligation (Quinn, 2010). Therefore,
organization focuses on the main objectives and properly uses of information technology in the
information system (Gupta & Hammond, 2005). In the first part of this report, it is describe
about the legislation and regulations for information management system of an organization.
In the next part, it is describe about the ethical issues in implementing security system in
the organization. Policies are required because of acceptable and unacceptable behaviors of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Information security 4
workers in the company, and manage all those issues raised by the behavior of an employee in
the company (Heiser & Nicolett, 2008). Therefore, policies and laws are used for solving those
issues with penalties, and require compliance of real issue. Basic five criteria for making policies
for an organization working process are as:
Distribution- it means all polices is must aware by the employee in hard copy or
electronic distribution.
Review- All policies and rules are converting in audio mode also so everyone
learn about all of the policies.
Understanding- the company must be able to explain that the worker understood
the content of policy and the requirements. They also used different types of ways
for understanding the policy, such as quizzes, and assessments.
Agreement- it should be assured from the employee side that he or she has read,
understood, and agreed to the treated according to the policy.
Uniform enforcement- it was must that; policy is not for a single person. It is
common for the all employees of organization.
All of these are helpful for creating policies for solving raised issues in the company by
the employees. All these are also provide authorization to organization for penalize the employee
who violate the terms and condition of the organization, which are mentioned in the policy of
organization (Tavani, 2003). Laws are dividing in two parts, which are civil and criminal laws
for different activities, but laws also divide two parts, such as private, and public laws. Private
laws handle family, commercial, labor, and regulate the bonding between personal and
companies. Public laws regulate the citizens, workers, and different government relationship
with the structure and administration of government agencies (Jin, Drozdenko, & Bassett, 2007).
Privacy has become one of the huge points in information security system. Many
organizations are having data about the employees and customers in their databases (Smith,
Dinev, & Xu, 2011). Many companies are selling personal information of their employees and
customers for different uses by third party companies. As an example we can take, Cambridge
Analytica and Facebook scandal for US election 2016 (Whitman & Mattord, 2011).
workers in the company, and manage all those issues raised by the behavior of an employee in
the company (Heiser & Nicolett, 2008). Therefore, policies and laws are used for solving those
issues with penalties, and require compliance of real issue. Basic five criteria for making policies
for an organization working process are as:
Distribution- it means all polices is must aware by the employee in hard copy or
electronic distribution.
Review- All policies and rules are converting in audio mode also so everyone
learn about all of the policies.
Understanding- the company must be able to explain that the worker understood
the content of policy and the requirements. They also used different types of ways
for understanding the policy, such as quizzes, and assessments.
Agreement- it should be assured from the employee side that he or she has read,
understood, and agreed to the treated according to the policy.
Uniform enforcement- it was must that; policy is not for a single person. It is
common for the all employees of organization.
All of these are helpful for creating policies for solving raised issues in the company by
the employees. All these are also provide authorization to organization for penalize the employee
who violate the terms and condition of the organization, which are mentioned in the policy of
organization (Tavani, 2003). Laws are dividing in two parts, which are civil and criminal laws
for different activities, but laws also divide two parts, such as private, and public laws. Private
laws handle family, commercial, labor, and regulate the bonding between personal and
companies. Public laws regulate the citizens, workers, and different government relationship
with the structure and administration of government agencies (Jin, Drozdenko, & Bassett, 2007).
Privacy has become one of the huge points in information security system. Many
organizations are having data about the employees and customers in their databases (Smith,
Dinev, & Xu, 2011). Many companies are selling personal information of their employees and
customers for different uses by third party companies. As an example we can take, Cambridge
Analytica and Facebook scandal for US election 2016 (Whitman & Mattord, 2011).

Information security 5
Different professional groups have provided rules for governing ethical behavior of
employees in the organization. There are some ethics for uses of computer system are:
Do not use a computer system to harm other person
Do not interfere in other person personal computer system work.
Do not access files from other person computer system.
Do not steal files form other person computer system
Do not use pirated software without paid for that software
Do not access and use other person’s computer system without proper permission.
Do not steal other person’s intellectual properties.
Always think about your program that is beneficial for social purpose.
Always use a computer system for respect for your fellow humans.
Most of the professional always follow ethics of their organization. All profession
expects from their employees to meet a standard of ethical behavior and this thing is based on the
code of ethics. In term of community work, ethics matter a lot because it is involved the group of
people (Kizza, 2007). The Australian Community Workers Association code of ethics sets a
space for community work for all practitioners. The community worker should respect the worth
of all individuals regardless of their religion, age, gender diversity, race, sexual, and other
individual differences (Kshetri, 2013).
Principles underlying the code of ethics
Every professional person, regardless of sexual, religious, race, age, and gender diversity,
or other individual differences.
Codes of ethics are helpful for maintaining equity, equality, social justice, and freedom.
Every society should balance equity in their society members. Therefore, no one can take
advantages of their position (Doctor, 1991).
Every person is legally protected from different types of discrimination based on
disability, gender, religious, age, sex, and their universal human rights are inviolable.
Responsibilities to clients
For the community worker:
They shall determine relationship between Client and them.
Different professional groups have provided rules for governing ethical behavior of
employees in the organization. There are some ethics for uses of computer system are:
Do not use a computer system to harm other person
Do not interfere in other person personal computer system work.
Do not access files from other person computer system.
Do not steal files form other person computer system
Do not use pirated software without paid for that software
Do not access and use other person’s computer system without proper permission.
Do not steal other person’s intellectual properties.
Always think about your program that is beneficial for social purpose.
Always use a computer system for respect for your fellow humans.
Most of the professional always follow ethics of their organization. All profession
expects from their employees to meet a standard of ethical behavior and this thing is based on the
code of ethics. In term of community work, ethics matter a lot because it is involved the group of
people (Kizza, 2007). The Australian Community Workers Association code of ethics sets a
space for community work for all practitioners. The community worker should respect the worth
of all individuals regardless of their religion, age, gender diversity, race, sexual, and other
individual differences (Kshetri, 2013).
Principles underlying the code of ethics
Every professional person, regardless of sexual, religious, race, age, and gender diversity,
or other individual differences.
Codes of ethics are helpful for maintaining equity, equality, social justice, and freedom.
Every society should balance equity in their society members. Therefore, no one can take
advantages of their position (Doctor, 1991).
Every person is legally protected from different types of discrimination based on
disability, gender, religious, age, sex, and their universal human rights are inviolable.
Responsibilities to clients
For the community worker:
They shall determine relationship between Client and them.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Information security 6
When they faced any failure then it should be informed to the client
Worker has an obligation to treat clients with dignity.
Worker always inform if he or she can access information about himself or herself.
Responsibility to Organizations
The community workers expected as an employee are:
Follow all rules and responsibilities to fulfill their terms and conditions.
Always achieved the targets provided by clients.
Always maintain a professional relationship with clients using social media also.
Act as a responsible persona in the spending of public monies.
Responsibility to colleagues
The community worker is expected to:
Always share their knowledge with their colleagues for enhancing their skills.
Always respect the knowledge, experience, and different skills of colleagues.
Always discuss about unethical behavior of colleague with the higher post person.
Should acknowledge the legal rights for protecting our health and safety at the workplace
The community worker will:
Should keep and upgrade education and training for the betterment of the organization
Should engage meeting with the colleagues through an appropriate channel.
Employee should always respect the other people protection rights (UWA, 2018).
Disclose about any improper relationship in the organization between a worker and
client.
Risk management:
Risk management is a factor in every project in whole lifetime of that project. Therefore,
every professional of project management, have to analysis deeply to all modules of that project.
There are different phase of risk analysis in case of information security, such as risk profile
selection, identification of risk on the bases of critical assets, control selection, and
When they faced any failure then it should be informed to the client
Worker has an obligation to treat clients with dignity.
Worker always inform if he or she can access information about himself or herself.
Responsibility to Organizations
The community workers expected as an employee are:
Follow all rules and responsibilities to fulfill their terms and conditions.
Always achieved the targets provided by clients.
Always maintain a professional relationship with clients using social media also.
Act as a responsible persona in the spending of public monies.
Responsibility to colleagues
The community worker is expected to:
Always share their knowledge with their colleagues for enhancing their skills.
Always respect the knowledge, experience, and different skills of colleagues.
Always discuss about unethical behavior of colleague with the higher post person.
Should acknowledge the legal rights for protecting our health and safety at the workplace
The community worker will:
Should keep and upgrade education and training for the betterment of the organization
Should engage meeting with the colleagues through an appropriate channel.
Employee should always respect the other people protection rights (UWA, 2018).
Disclose about any improper relationship in the organization between a worker and
client.
Risk management:
Risk management is a factor in every project in whole lifetime of that project. Therefore,
every professional of project management, have to analysis deeply to all modules of that project.
There are different phase of risk analysis in case of information security, such as risk profile
selection, identification of risk on the bases of critical assets, control selection, and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Information security 7
implementation and proper management of the system. In risk analysis, different types of risk
occur before implication and during running project (Gray, 2003).
Many organizations are use Risk Evolution matrix to find out different areas of risk, such
as legal, marketing, stability, productivity, and regulatory. In a system, some assets are so
important for proper functioning of the complete system, in case of information security system,
systems, network, people, and applications are important assets (Roberts, 2007). Risk
management is based on data storage also now a day’s data stored in the cloud storage, which is
a third party service (Zhang, Wuwong, Li, & Zhang, 2010). There are some questions for
implementation of the complete system to avoid risk and manage that risk at any time. The
questions are:
Who controls the system?
Who are the users?
How people use it?
Why it is important for any mission?
Security is a risk management strategy in which minimizes uncertain events in the
systems on the bases of a procedure. First identifies the issues in the system, then control that
issue and finally eliminate that issue form the system. Those issues may be affects information
assents of the system and resources also. There are number of concerns related to
implementation of facial recognition system. System should be designed to protect right to
privacy of every person (Reason, 2016). In an organization, information security departments are
managing information technology risks. It is a key responsibility of every manager in an
organization. There are two procedures for developing a risk management program. First, is risk
identification in the system, and second is risk control (Ericson, 2006).
First step of security knows about us, means level of security at your end. Risk
management is a process by which you maintain and control different devices of a system. It is
also must for every manager that flow of information in the system. Second thing knows about
the enemy, which means analyze threats facing by the system’s information assets (Bulgurcu,
Cavusoglu, & Benbasat, 2010).it is like identification, examining, and understanding about the
threat in the system. Manager must be preparing for handling that type of threat that creates risks
implementation and proper management of the system. In risk analysis, different types of risk
occur before implication and during running project (Gray, 2003).
Many organizations are use Risk Evolution matrix to find out different areas of risk, such
as legal, marketing, stability, productivity, and regulatory. In a system, some assets are so
important for proper functioning of the complete system, in case of information security system,
systems, network, people, and applications are important assets (Roberts, 2007). Risk
management is based on data storage also now a day’s data stored in the cloud storage, which is
a third party service (Zhang, Wuwong, Li, & Zhang, 2010). There are some questions for
implementation of the complete system to avoid risk and manage that risk at any time. The
questions are:
Who controls the system?
Who are the users?
How people use it?
Why it is important for any mission?
Security is a risk management strategy in which minimizes uncertain events in the
systems on the bases of a procedure. First identifies the issues in the system, then control that
issue and finally eliminate that issue form the system. Those issues may be affects information
assents of the system and resources also. There are number of concerns related to
implementation of facial recognition system. System should be designed to protect right to
privacy of every person (Reason, 2016). In an organization, information security departments are
managing information technology risks. It is a key responsibility of every manager in an
organization. There are two procedures for developing a risk management program. First, is risk
identification in the system, and second is risk control (Ericson, 2006).
First step of security knows about us, means level of security at your end. Risk
management is a process by which you maintain and control different devices of a system. It is
also must for every manager that flow of information in the system. Second thing knows about
the enemy, which means analyze threats facing by the system’s information assets (Bulgurcu,
Cavusoglu, & Benbasat, 2010).it is like identification, examining, and understanding about the
threat in the system. Manager must be preparing for handling that type of threat that creates risks

Information security 8
to the system. Using the risk management can be controlled or mitigated the threats in the system
(Zhou, Vasconcelos, & Nunes, 2008).
Next step for risk management is accountability. All systems working on these points for
managing risks are:
Evaluating the risk controls
Identifying threats
Identifying about cost effective control option
Installing the suitable control for managing risk
Overseeing processes
Identifying risks
Organizing assets
Allocating values to information assets
Assessing risks
Calculating the risks
Information assets
Reviewing controls for identification of vulnerabilities
Documentation of the all process of risk management
Risk identification
Risk identification is just like self-examination. In this, manager must identify the
information assets of the system, and provides priorities to all assets according to their
importance for the system. In the information assets of a system manager includes different
things, such as people, systems, data, software, hardware, procedures, network, and devices used
in the system.
to the system. Using the risk management can be controlled or mitigated the threats in the system
(Zhou, Vasconcelos, & Nunes, 2008).
Next step for risk management is accountability. All systems working on these points for
managing risks are:
Evaluating the risk controls
Identifying threats
Identifying about cost effective control option
Installing the suitable control for managing risk
Overseeing processes
Identifying risks
Organizing assets
Allocating values to information assets
Assessing risks
Calculating the risks
Information assets
Reviewing controls for identification of vulnerabilities
Documentation of the all process of risk management
Risk identification
Risk identification is just like self-examination. In this, manager must identify the
information assets of the system, and provides priorities to all assets according to their
importance for the system. In the information assets of a system manager includes different
things, such as people, systems, data, software, hardware, procedures, network, and devices used
in the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Information security 9
Risk Identification Process
Assets of an Organization, which used in systems, are:
Identifying application software, hardware devices, and networking devices
Identification is based on the importance of the asset for the system’s risk management.
Some preferences also provide to assets according to information technology communities. It is
also depend of the attributes of the information asset. Some potential attributes of information
asset are:
IP address
Risk Identification Process
Assets of an Organization, which used in systems, are:
Identifying application software, hardware devices, and networking devices
Identification is based on the importance of the asset for the system’s risk management.
Some preferences also provide to assets according to information technology communities. It is
also depend of the attributes of the information asset. Some potential attributes of information
asset are:
IP address
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Information security 10
Logical location
MAC address
Name of System
Asset type
Machine Serial number
Model number
Version of software
Controlling entity
Physical location of the system
Port number
Vendor name
Identification people, procedures, and information assets:
It is depend on the managers, they will decide about this thing according to information,
skill, and judgment. When these assets identified, they should be recorded via a trustworthy
information management process, such as the one used for software program and hardware
devices of a system.
Some things are bind with assets are:
People
Procedures
Position number ID
Description
Supervisor name
Intendant purpose
Security clearance level
Software and hardware elements to which it is used
Location of data storage
Classification
Online or offline
Owner
Data structure used
Logical location
MAC address
Name of System
Asset type
Machine Serial number
Model number
Version of software
Controlling entity
Physical location of the system
Port number
Vendor name
Identification people, procedures, and information assets:
It is depend on the managers, they will decide about this thing according to information,
skill, and judgment. When these assets identified, they should be recorded via a trustworthy
information management process, such as the one used for software program and hardware
devices of a system.
Some things are bind with assets are:
People
Procedures
Position number ID
Description
Supervisor name
Intendant purpose
Security clearance level
Software and hardware elements to which it is used
Location of data storage
Classification
Online or offline
Owner
Data structure used
Information security 11
Backup procedures
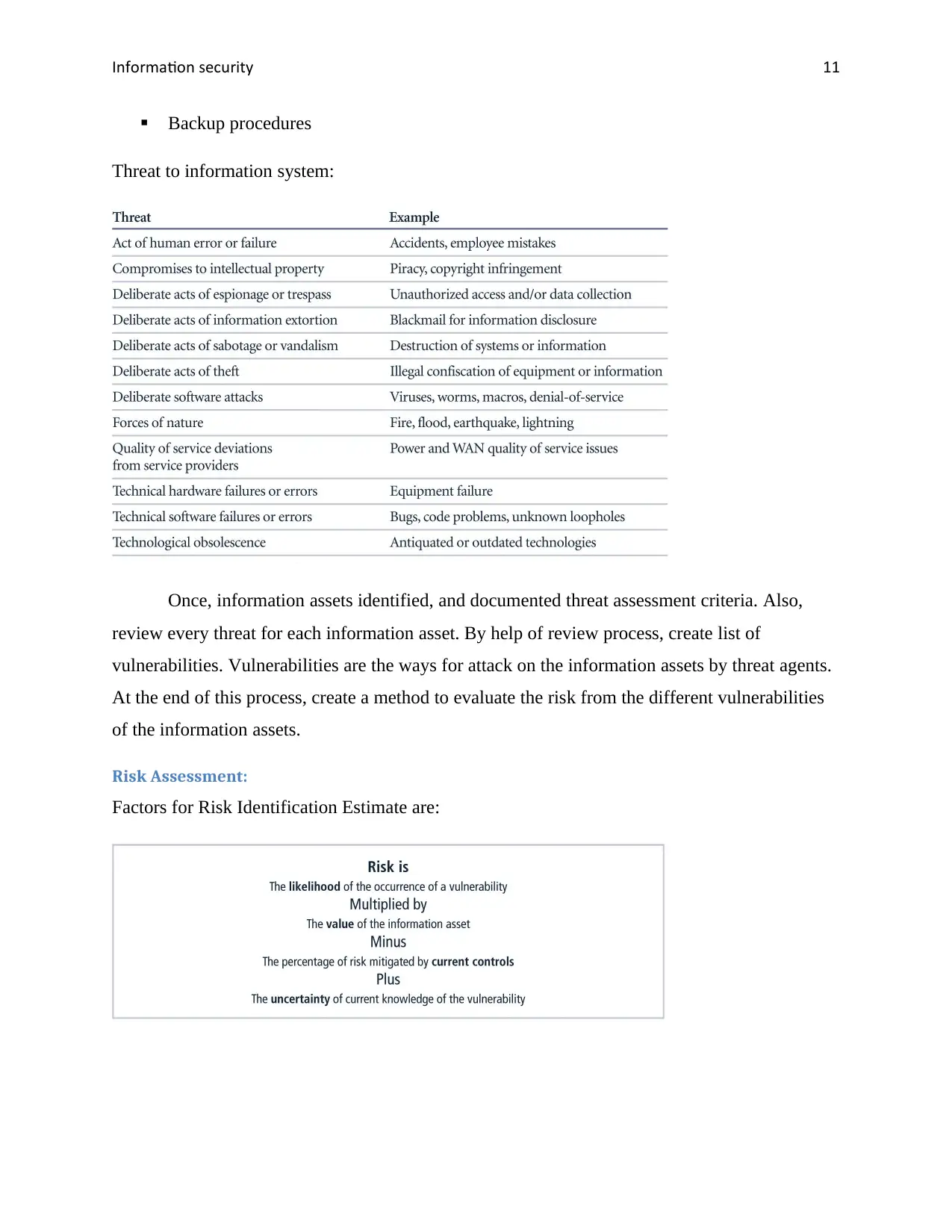
Threat to information system:
Once, information assets identified, and documented threat assessment criteria. Also,
review every threat for each information asset. By help of review process, create list of
vulnerabilities. Vulnerabilities are the ways for attack on the information assets by threat agents.
At the end of this process, create a method to evaluate the risk from the different vulnerabilities
of the information assets.
Risk Assessment:
Factors for Risk Identification Estimate are:
Backup procedures
Threat to information system:
Once, information assets identified, and documented threat assessment criteria. Also,
review every threat for each information asset. By help of review process, create list of
vulnerabilities. Vulnerabilities are the ways for attack on the information assets by threat agents.
At the end of this process, create a method to evaluate the risk from the different vulnerabilities
of the information assets.
Risk Assessment:
Factors for Risk Identification Estimate are:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





