Report on Information Systems Security Architecture for IBM Company
VerifiedAdded on 2023/05/26
|5
|791
|494
Report
AI Summary
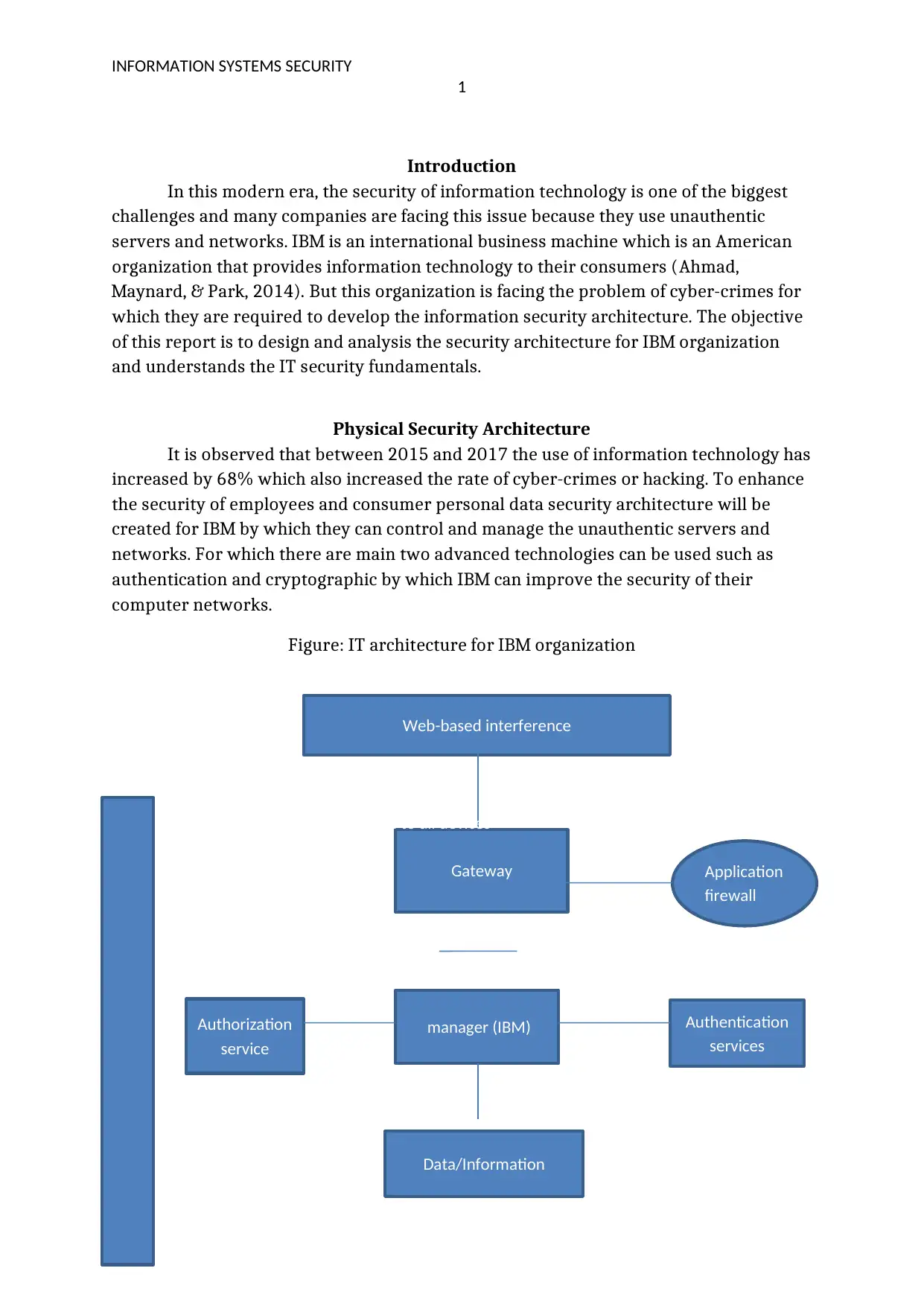
This report focuses on designing and analyzing a security architecture for IBM to address the challenges of cyber-crimes and enhance data protection. The report begins with an introduction highlighting the increasing reliance on information technology and the associated rise in cyber-attacks. It then proposes a security architecture for IBM, emphasizing the use of authentication and cryptographic technologies to manage unauthentic servers and networks. The architecture is divided into four key components: application firewall, authentication services, authorization services, and cryptographic techniques. The report explains the function of each component in detail, illustrating how these technologies can be employed to identify and block unwanted signals, control login attempts, grant data access, and detect malware. The conclusion emphasizes the importance of using authentic networks and updated software to ensure data security. References to relevant literature are included to support the analysis.
1 out of 5










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)