SheeNoar Technological University's IT Standards & Security Plan
VerifiedAdded on 2023/06/11
|9
|1766
|380
Report
AI Summary
This document presents an information security plan (ISP) for SheeNoar Technological University, outlining IT standards and practices. The plan details policies and procedures for controlling, managing, and evaluating IT activities, ensuring the protection of confidential data from unauthorized access while meeting ethical and legal responsibilities. Key components include algorithm requirements, admittance supervision, authentication, authorization, and policy statements. The ISP emphasizes risk assessment, confidentiality, integrity, and compliance with university policies, providing guidelines for all members of the university community. The plan is subject to annual review and updates to adapt to environmental changes and maintain effective information security.

Running head: INFORMATION SECURITY PLAN 1
SheeNoar Technological University’s It Standards and Practices
Name
Affiliation
SheeNoar Technological University’s It Standards and Practices
Name
Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SECURITY PLAN 2
Table of Contents
1. Overview......................................................................................................................................2
2. Purpose........................................................................................................................................3
3. Scope............................................................................................................................................4
4. Policy...........................................................................................................................................5
4.1. Algorithm requirements........................................................................................................5
4.3. Admittance supervision and identity.....................................................................................5
4.4 Authentication........................................................................................................................5
4.5. Authorization........................................................................................................................6
4.6. Policy statement....................................................................................................................6
5. Definitions and terms...................................................................................................................6
6. Policy Compliance.......................................................................................................................7
7. ISP Revision History..................................................................................................................8
8.0 References..................................................................................................................................9
Table of Contents
1. Overview......................................................................................................................................2
2. Purpose........................................................................................................................................3
3. Scope............................................................................................................................................4
4. Policy...........................................................................................................................................5
4.1. Algorithm requirements........................................................................................................5
4.3. Admittance supervision and identity.....................................................................................5
4.4 Authentication........................................................................................................................5
4.5. Authorization........................................................................................................................6
4.6. Policy statement....................................................................................................................6
5. Definitions and terms...................................................................................................................6
6. Policy Compliance.......................................................................................................................7
7. ISP Revision History..................................................................................................................8
8.0 References..................................................................................................................................9

INFORMATION SECURITY PLAN 3
SHEENOAR TECHNOLOGICAL UNIVERSITY’S IT STANDARDS AND PRACTICES
1. Overview
The information security plan is a document of guidelines that state the policies and
procedures governing SheeNoar Technological university’s IT standards and practices. The
policies formulated explains the objectives of the institution for controlling, managing and
evaluation of activities. The systems are also responsible for the maintenance of internal control
since the systems present the protocols and plans of the university. The program governs and
protects confidential data of the institution from access by unauthorized individuals. The
program also allows the university to meet ethical and legal considerations and responsibilities
concerning IT resources.
The policies and techniques represent the information security plan (ISP) of the
university which serves as guidelines for the management and implementation of security on
information across the institution. IT security is created to enhance protection of information
resources and maintain the privacy and confidentiality of the community members of SheeNoar
University. The members of the community in the university are the president, directors, vice
president, dean, students, and head of departments, staff, contractors, faculty, alumni, guests, and
trustees who have access to the university resources. All users of SheeNoar Tech's Information
properties ought to adhere to the policies and all the regulations as well as set standards in the
university to all community members (Rhodes-Ousley, 2013).
2. Purpose
The purpose of this security plan is to make sure the availability of data, confidentiality,
develop, integrity, define and document the info strategies and techniques that are in support to
SHEENOAR TECHNOLOGICAL UNIVERSITY’S IT STANDARDS AND PRACTICES
1. Overview
The information security plan is a document of guidelines that state the policies and
procedures governing SheeNoar Technological university’s IT standards and practices. The
policies formulated explains the objectives of the institution for controlling, managing and
evaluation of activities. The systems are also responsible for the maintenance of internal control
since the systems present the protocols and plans of the university. The program governs and
protects confidential data of the institution from access by unauthorized individuals. The
program also allows the university to meet ethical and legal considerations and responsibilities
concerning IT resources.
The policies and techniques represent the information security plan (ISP) of the
university which serves as guidelines for the management and implementation of security on
information across the institution. IT security is created to enhance protection of information
resources and maintain the privacy and confidentiality of the community members of SheeNoar
University. The members of the community in the university are the president, directors, vice
president, dean, students, and head of departments, staff, contractors, faculty, alumni, guests, and
trustees who have access to the university resources. All users of SheeNoar Tech's Information
properties ought to adhere to the policies and all the regulations as well as set standards in the
university to all community members (Rhodes-Ousley, 2013).
2. Purpose
The purpose of this security plan is to make sure the availability of data, confidentiality,
develop, integrity, define and document the info strategies and techniques that are in support to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION SECURITY PLAN 4
the goals of the university as well as its objectives. The plan also allows the university to meet
ethical and legal considerations and responsibilities concerning IT resources. The policies and
techniques represent the information security plan (ISP) of the university which serves as
guidelines for the management and implementation of security on information across the
institution. There exists internal control which assists in checks and balances which are aimed at
identifying fraud and irregularities as well as preventing waste in the institution (Zhang,
Wuwong & Zhang, 2010).
Also, the controls assist in solving conflicts and discrepancies which are introduced into
the business accidentally. When these policies and procedures are incorporated in the institution,
technology resources of information are protected from many threats to guarantee the continuity
of the company and involve in deep investments for the interests of the business. The ISP reflects
SheeNoar Tech's obligation to stewardship to critical information on the company as well as
personal information based on the threats towards information security and the need to protect
the privacy of the institution elements. This plan will be reviewed as well as being updated based
on the environmental changes and at least annually.
3. Scope
This plan applies to the whole community of SheeNoar who are: the president, directors,
vice president, dean, students, and head of departments, staff, contractors, faculty, alumni,
guests, and trustees who have access to the university resources (Puhakainen & Siponen, 2010).
The assets in the institutions are like data, texts, images stored in either software, hardware,
paper or any other storage media. 4
the goals of the university as well as its objectives. The plan also allows the university to meet
ethical and legal considerations and responsibilities concerning IT resources. The policies and
techniques represent the information security plan (ISP) of the university which serves as
guidelines for the management and implementation of security on information across the
institution. There exists internal control which assists in checks and balances which are aimed at
identifying fraud and irregularities as well as preventing waste in the institution (Zhang,
Wuwong & Zhang, 2010).
Also, the controls assist in solving conflicts and discrepancies which are introduced into
the business accidentally. When these policies and procedures are incorporated in the institution,
technology resources of information are protected from many threats to guarantee the continuity
of the company and involve in deep investments for the interests of the business. The ISP reflects
SheeNoar Tech's obligation to stewardship to critical information on the company as well as
personal information based on the threats towards information security and the need to protect
the privacy of the institution elements. This plan will be reviewed as well as being updated based
on the environmental changes and at least annually.
3. Scope
This plan applies to the whole community of SheeNoar who are: the president, directors,
vice president, dean, students, and head of departments, staff, contractors, faculty, alumni,
guests, and trustees who have access to the university resources (Puhakainen & Siponen, 2010).
The assets in the institutions are like data, texts, images stored in either software, hardware,
paper or any other storage media. 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SECURITY PLAN 5
4. Policy
4.1. Algorithm requirements
Information security board of evaluations (ISBE) responsibility is to give the direction of
the information security and assurance of privacy in the institution.
Chief technology general (CTG) is responsible for budgeting, planning and also the
management of performance. The officer is responsible in making of decisions which should
focus mainly on the management of perils that may arise.
Information and Security Adherence Officer (ISO) has the role of security programs most
especially threat management. The officers help in evaluating and identify risks towards the IT
resources which in turn supports the institution mission and the set goals.
4.3. Admittance supervision and identity
Access management as well as identity creates a secure authenticated chance to access to
network services usage and ensures accurate identification of permitted university community.
4.4 Authentication
Authentication is a process which determines the identity of someone or a thing. The
method uses passwords or token in identifying individuals through IT. Passwords are used as for
security and protection of accounts. Passwords in SheeNoar University are choose wisely to
protect their network. The university community has the role in protecting the passwords and
also a wide selection of the passwords.
4. Policy
4.1. Algorithm requirements
Information security board of evaluations (ISBE) responsibility is to give the direction of
the information security and assurance of privacy in the institution.
Chief technology general (CTG) is responsible for budgeting, planning and also the
management of performance. The officer is responsible in making of decisions which should
focus mainly on the management of perils that may arise.
Information and Security Adherence Officer (ISO) has the role of security programs most
especially threat management. The officers help in evaluating and identify risks towards the IT
resources which in turn supports the institution mission and the set goals.
4.3. Admittance supervision and identity
Access management as well as identity creates a secure authenticated chance to access to
network services usage and ensures accurate identification of permitted university community.
4.4 Authentication
Authentication is a process which determines the identity of someone or a thing. The
method uses passwords or token in identifying individuals through IT. Passwords are used as for
security and protection of accounts. Passwords in SheeNoar University are choose wisely to
protect their network. The university community has the role in protecting the passwords and
also a wide selection of the passwords.

INFORMATION SECURITY PLAN 6
4.5. Authorization
Authorization is a criterion of permitting the authenticated users whereby they are given
the right to access to information whose access is managed by the institution on what to and not
to obtain. Level of control is determined by data classification and the sensitivity of the level at
risks which put information under threat.
4.6. Policy statement
It is a duty to all departments to protect the institution properties by implementing
security standards and techniques that are developed and approved by Information security board
of evaluations in the ISP. All the various departments ought to meet the set standards for the
overall success of the institution based on teamwork among the departments in the university
(Peltier, 2016). Departments are also required to protect the organization resources which are
entirely within those specific departments. The rest of the members of the university must adhere
to the department's policies and comply to achieve the laid down objectives.
5. Definitions and terms
Risk assessment is a procedure that seeks to identify the IT resources in risk and ways of
protecting the information from establishing threat. The process also determines the security
failures that may lead to loss of essential information (Kissel, 2011).
Confidentiality is the preservation of private information through restriction from
unauthorized access or information disclosure of personal privacy.
Control activities are the mechanism or techniques that aid in assuring the management
response in eradication associated risks identified in the risk assessment process.
4.5. Authorization
Authorization is a criterion of permitting the authenticated users whereby they are given
the right to access to information whose access is managed by the institution on what to and not
to obtain. Level of control is determined by data classification and the sensitivity of the level at
risks which put information under threat.
4.6. Policy statement
It is a duty to all departments to protect the institution properties by implementing
security standards and techniques that are developed and approved by Information security board
of evaluations in the ISP. All the various departments ought to meet the set standards for the
overall success of the institution based on teamwork among the departments in the university
(Peltier, 2016). Departments are also required to protect the organization resources which are
entirely within those specific departments. The rest of the members of the university must adhere
to the department's policies and comply to achieve the laid down objectives.
5. Definitions and terms
Risk assessment is a procedure that seeks to identify the IT resources in risk and ways of
protecting the information from establishing threat. The process also determines the security
failures that may lead to loss of essential information (Kissel, 2011).
Confidentiality is the preservation of private information through restriction from
unauthorized access or information disclosure of personal privacy.
Control activities are the mechanism or techniques that aid in assuring the management
response in eradication associated risks identified in the risk assessment process.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION SECURITY PLAN 7
Integrity is a process identified with guarding against inappropriate information
destruction which ensures there is no authenticity and repudiation of inf0ormation.
Information assets are the various pieces of information in any manner that is stored in
any form of media and is known to be valuable in the institution.
A virtual private network is a form of the system which uses public telecommunication as
the internet to provide personal users with secure access to the university network. The data on
the internet cannot be intercepted, and there is a strict authorization of who access to these
networks of the organization.
6. Policy Compliance
The IT resources at SheeNoar Tech sustenance research, educational and administrative
activities of the institution and the university community using the resources is an extended
privilege from the university. Any person involved in the university information technology
should follow strict set guidelines and standards. The resources are to be used in consideration of
other people in the university.
On a personal basis, individuals are required to be responsible for protecting own
information resources either shared or stand alone. It is unacceptable and against the laws of the
University for an Individual to use information resources in violation of the institution policies,
laws or unethical performance in academic and institutional acts (Bulgurcu, Cavusoglu &
Benbasat, 2010).
SheeNoar Tech's Adequate Use of Information Technology Resources is an act that
entails the governing philosophy for practical usage of the university's calculating
communications and the information properties by the members of the community in the
Integrity is a process identified with guarding against inappropriate information
destruction which ensures there is no authenticity and repudiation of inf0ormation.
Information assets are the various pieces of information in any manner that is stored in
any form of media and is known to be valuable in the institution.
A virtual private network is a form of the system which uses public telecommunication as
the internet to provide personal users with secure access to the university network. The data on
the internet cannot be intercepted, and there is a strict authorization of who access to these
networks of the organization.
6. Policy Compliance
The IT resources at SheeNoar Tech sustenance research, educational and administrative
activities of the institution and the university community using the resources is an extended
privilege from the university. Any person involved in the university information technology
should follow strict set guidelines and standards. The resources are to be used in consideration of
other people in the university.
On a personal basis, individuals are required to be responsible for protecting own
information resources either shared or stand alone. It is unacceptable and against the laws of the
University for an Individual to use information resources in violation of the institution policies,
laws or unethical performance in academic and institutional acts (Bulgurcu, Cavusoglu &
Benbasat, 2010).
SheeNoar Tech's Adequate Use of Information Technology Resources is an act that
entails the governing philosophy for practical usage of the university's calculating
communications and the information properties by the members of the community in the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INFORMATION SECURITY PLAN 8
university. The directors are responsible for ensuring acquiescence with information security
practices. IT in collaboration with other departments will come up with an annual security
consciousness and training to enhance technical expertise and correct use for the workers who
can access the information technology properties.
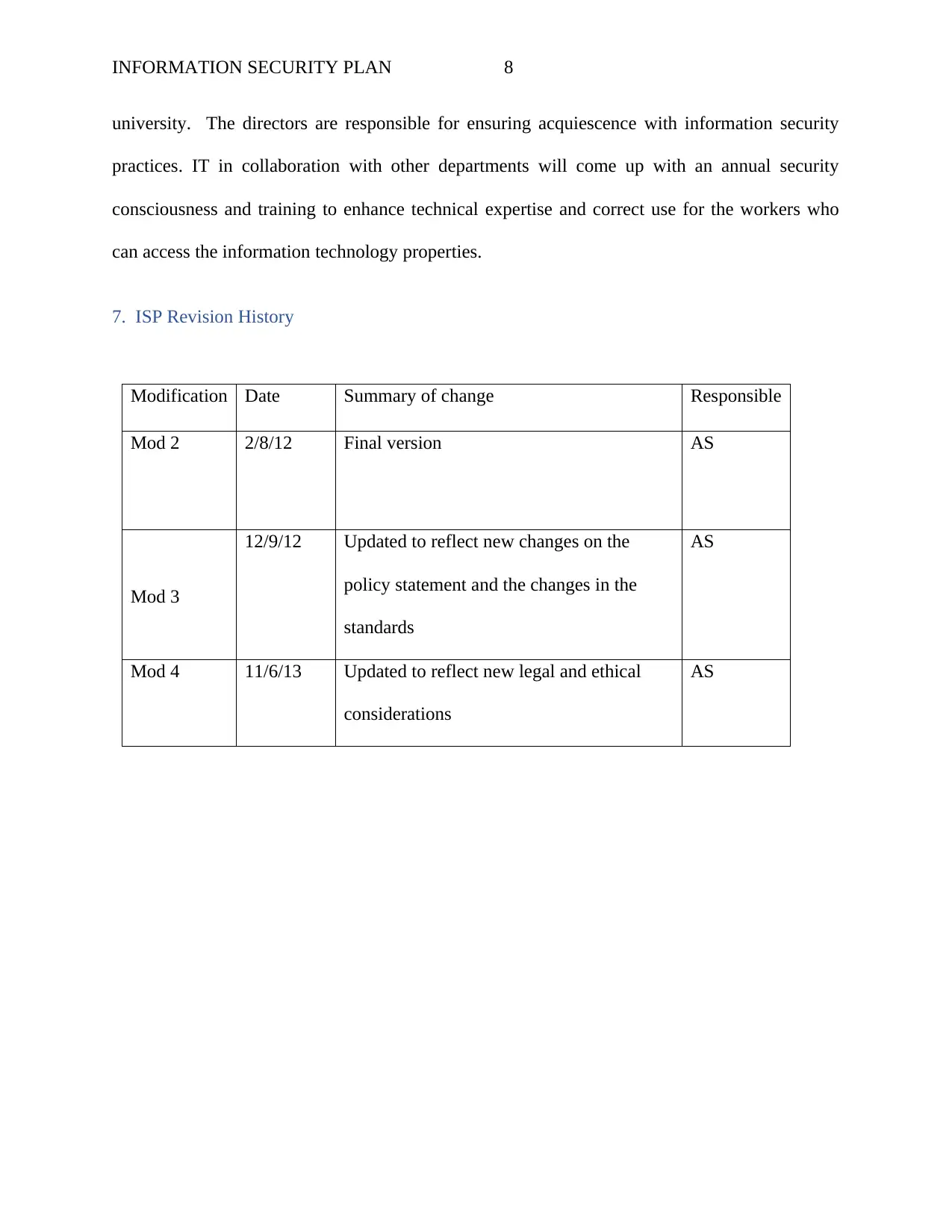
7. ISP Revision History
Modification Date Summary of change Responsible
Mod 2 2/8/12 Final version AS
Mod 3
12/9/12 Updated to reflect new changes on the
policy statement and the changes in the
standards
AS
Mod 4 11/6/13 Updated to reflect new legal and ethical
considerations
AS
university. The directors are responsible for ensuring acquiescence with information security
practices. IT in collaboration with other departments will come up with an annual security
consciousness and training to enhance technical expertise and correct use for the workers who
can access the information technology properties.
7. ISP Revision History
Modification Date Summary of change Responsible
Mod 2 2/8/12 Final version AS
Mod 3
12/9/12 Updated to reflect new changes on the
policy statement and the changes in the
standards
AS
Mod 4 11/6/13 Updated to reflect new legal and ethical
considerations
AS

INFORMATION SECURITY PLAN 9
8.0 References
Bulgurcu, B., Cavusoglu, H., & Benbasat, I. (2010). Information security policy compliance: an
empirical study of rationality-based beliefs and information security awareness. MIS
Quarterly, 34(3), 523-548.
Kissel, R. (Ed.). (2011). Glossary of key information security terms. Diane Publishing.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Puhakainen, P., & Siponen, M. (2010). Improving employees' compliance through information
systems security training: an action research study. Mis Quarterly, 757-778.
Rhodes-Ousley, M. (2013). Information security: the complete reference. McGraw Hill
Education.
Zhang, X., Wuwong, N., Li, H., & Zhang, X. (2010, June). Information security risk
management framework for the cloud computing environments. In Computer and
Information Technology (CIT), 2010 IEEE 10th International Conference on (pp. 1328-
1334). IEEE.
8.0 References
Bulgurcu, B., Cavusoglu, H., & Benbasat, I. (2010). Information security policy compliance: an
empirical study of rationality-based beliefs and information security awareness. MIS
Quarterly, 34(3), 523-548.
Kissel, R. (Ed.). (2011). Glossary of key information security terms. Diane Publishing.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Puhakainen, P., & Siponen, M. (2010). Improving employees' compliance through information
systems security training: an action research study. Mis Quarterly, 757-778.
Rhodes-Ousley, M. (2013). Information security: the complete reference. McGraw Hill
Education.
Zhang, X., Wuwong, N., Li, H., & Zhang, X. (2010, June). Information security risk
management framework for the cloud computing environments. In Computer and
Information Technology (CIT), 2010 IEEE 10th International Conference on (pp. 1328-
1334). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





