ITC595 Information Security Assessment: Security Fundamentals ITC595
VerifiedAdded on 2024/05/21
|9
|1704
|56
Homework Assignment
AI Summary
This ITC595 Information Security assignment solution provides a detailed analysis of security fundamentals, focusing on confidentiality, integrity, and availability within the context of an ATM system. It explores potential vulnerabilities, such as PIN cracking, and discusses the reluctance of users towards biometric authentication, addressing concerns like data loss, cost, and system faults. The assignment also examines the implications of false negatives in biometric systems and includes a decryption exercise using a substitution key to reveal a hidden message related to processor frequency. The document concludes with references to support the analysis and solutions presented. Desklib offers this and many other solved assignments for students.

ITC595: Information security
Assessment 2
Security Fundamental
Student Name: Nayankumar Kantilal Thakkar
Student ID: 11609358
Assessment 2
Security Fundamental
Student Name: Nayankumar Kantilal Thakkar
Student ID: 11609358
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Nayankumar Kantilal Thakkar 11609358
Contents
Part 1:.........................................................................................................................................2
Confidentiality:.......................................................................................................................2
Integrity..................................................................................................................................2
Availability:.............................................................................................................................2
Part 2..........................................................................................................................................3
Part 3..........................................................................................................................................4
Part 4..........................................................................................................................................5
Part 5:.........................................................................................................................................6
References..................................................................................................................................8
1
Contents
Part 1:.........................................................................................................................................2
Confidentiality:.......................................................................................................................2
Integrity..................................................................................................................................2
Availability:.............................................................................................................................2
Part 2..........................................................................................................................................3
Part 3..........................................................................................................................................4
Part 4..........................................................................................................................................5
Part 5:.........................................................................................................................................6
References..................................................................................................................................8
1

Nayankumar Kantilal Thakkar 11609358
Part 1:
Confidentiality:
Refers to the Confidentiality of the ATM system, then this is the most important part. Refers
to the word Confidentiality, then this means to hide the data or the information, with the
help of this the other user will not able to see and use the information. Refers to the case of
the ATM, then the ATM PIN is needed to be Confidentiality, by the help of the PIN the user
can able to performs the banking transactions, hence the ATM PIN has to be Confidential to
the user. Therefore only single user can access the ATM for the same ATM card and this will
maintain the security of the system for both user and for banks.
Refers to the degree of functionality, it has high confidentiality. This is because if there is
any failure occurs then it leads to the major loss to the user and to the banks. so, there is
need to apply some sort of the security to this to protect the system from the unwanted
access of the user and the hackers. Some of the techniques are encryption, biometric
authentication, encryption etc. all the technique that helps to maintains the Confidentiality
of the system (Chia, 2012).
Integrity:
Refers to the Integrity, then this is defining to protect the loss of the data. Now refers to the
ATM system, then there are also chances of loss of the data and the information. This can
be done by the various failures. Sometimes the user is failure and sometimes the system
failure. There is need to secure all the transactions from the unwanted access.
The degree of the functionality is also high, there is need to protect the data at the time of
the deposit and the withdrawal money in the banks. Consider the current scenario then
there are ATM is developed that are multifunction use for both cash deposit and cash
withdrawal. There is need to use the system carefully (Enterprise, 2018).
Availability:
This is one of the systems, which define the availability of the functions to the user. Refers
to the ATM system, then there is the availability of the money should be there and the
maintenance of the system properly.
The degree of the functionality is medium of this case, as there are some chances of the
system failure and sometimes the system goes for the maintenance, at that time the
availability of the ATM system is reduced.
2
Part 1:
Confidentiality:
Refers to the Confidentiality of the ATM system, then this is the most important part. Refers
to the word Confidentiality, then this means to hide the data or the information, with the
help of this the other user will not able to see and use the information. Refers to the case of
the ATM, then the ATM PIN is needed to be Confidentiality, by the help of the PIN the user
can able to performs the banking transactions, hence the ATM PIN has to be Confidential to
the user. Therefore only single user can access the ATM for the same ATM card and this will
maintain the security of the system for both user and for banks.
Refers to the degree of functionality, it has high confidentiality. This is because if there is
any failure occurs then it leads to the major loss to the user and to the banks. so, there is
need to apply some sort of the security to this to protect the system from the unwanted
access of the user and the hackers. Some of the techniques are encryption, biometric
authentication, encryption etc. all the technique that helps to maintains the Confidentiality
of the system (Chia, 2012).
Integrity:
Refers to the Integrity, then this is defining to protect the loss of the data. Now refers to the
ATM system, then there are also chances of loss of the data and the information. This can
be done by the various failures. Sometimes the user is failure and sometimes the system
failure. There is need to secure all the transactions from the unwanted access.
The degree of the functionality is also high, there is need to protect the data at the time of
the deposit and the withdrawal money in the banks. Consider the current scenario then
there are ATM is developed that are multifunction use for both cash deposit and cash
withdrawal. There is need to use the system carefully (Enterprise, 2018).
Availability:
This is one of the systems, which define the availability of the functions to the user. Refers
to the ATM system, then there is the availability of the money should be there and the
maintenance of the system properly.
The degree of the functionality is medium of this case, as there are some chances of the
system failure and sometimes the system goes for the maintenance, at that time the
availability of the ATM system is reduced.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Nayankumar Kantilal Thakkar 11609358
Part 2
Refers to the ATM pin then, it would be of the four digits. Below, it shows some case to get
the correct pin by the hacker.
Refers to the case 1: In this user breaks the 0 from the ATM keyboard
That time the user will not able to press the zero key from the keyboard. All four zero will
not allow being a pin of the ATM. For this case, it will be removed from the cases.
There are total four digits of the Pin and have total five numbers are remaining as to fill the
places. So the total numbers of possible combinations of the pin are given as:
For the first-place, possible numbers are: 5
Second place: 5
Third place:5
Fourth place:5
Total= 5*5*5*5= 625.
Refers to the case 2
If the zero is not broken by the user
Then the number of possible chances is reducing by one. That means all the four zero is not
a valid password or pin. So, the total numbers of possible cases are:
5*5*5*5 -1 = 624.
All the calculation is done above are theoretical, refers to the original scenario of the banks
and the ATM then there are only three-time chances to enters the wrong pin. More than
that the ATM of the user will block and the hacker will not able to use the card.
3
Part 2
Refers to the ATM pin then, it would be of the four digits. Below, it shows some case to get
the correct pin by the hacker.
Refers to the case 1: In this user breaks the 0 from the ATM keyboard
That time the user will not able to press the zero key from the keyboard. All four zero will
not allow being a pin of the ATM. For this case, it will be removed from the cases.
There are total four digits of the Pin and have total five numbers are remaining as to fill the
places. So the total numbers of possible combinations of the pin are given as:
For the first-place, possible numbers are: 5
Second place: 5
Third place:5
Fourth place:5
Total= 5*5*5*5= 625.
Refers to the case 2
If the zero is not broken by the user
Then the number of possible chances is reducing by one. That means all the four zero is not
a valid password or pin. So, the total numbers of possible cases are:
5*5*5*5 -1 = 624.
All the calculation is done above are theoretical, refers to the original scenario of the banks
and the ATM then there are only three-time chances to enters the wrong pin. More than
that the ATM of the user will block and the hacker will not able to use the card.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Nayankumar Kantilal Thakkar 11609358
Part 3
Below show the three reasons, why the reasons are user will reluctance the biometrics as
for the authentication process.
1. Loss of the data: Major of the customer thinks that with the use of the biometrics so,
the major user does not want to share the personal information with the machine.
Refers to the peoples then they do not want to share the information with the
machines.
For this case, there are need to trust on the machines, the machine takes the data and
saves to the government database. The machine needs apply the two-way
authentication to gains the trust of persons.
2. Costing: Refers to the biometric than the setup cost for the authentication is higher and
this is not economically stable.
Refers to the solution as the costing for the biometric, then this is a one-time
investment. The government also provides the help to the user by providing the loans or
offers various schemes. The government reduces the costing and help to upgrade the
system.
3. Faults and issue with the system: Refer to the biometric system that has some sort of
faults and error. Errors are occurred due to the server or the device. Many times the
machine will not accept the fingerprint of the user. If there is some part burn or cut
market on the finger, then the system does not accept and it leads to the authentication
failure.
There is need to apply a different type of the authentication techniques for the
authentication (Dascalescu, 2018).
4
Part 3
Below show the three reasons, why the reasons are user will reluctance the biometrics as
for the authentication process.
1. Loss of the data: Major of the customer thinks that with the use of the biometrics so,
the major user does not want to share the personal information with the machine.
Refers to the peoples then they do not want to share the information with the
machines.
For this case, there are need to trust on the machines, the machine takes the data and
saves to the government database. The machine needs apply the two-way
authentication to gains the trust of persons.
2. Costing: Refers to the biometric than the setup cost for the authentication is higher and
this is not economically stable.
Refers to the solution as the costing for the biometric, then this is a one-time
investment. The government also provides the help to the user by providing the loans or
offers various schemes. The government reduces the costing and help to upgrade the
system.
3. Faults and issue with the system: Refer to the biometric system that has some sort of
faults and error. Errors are occurred due to the server or the device. Many times the
machine will not accept the fingerprint of the user. If there is some part burn or cut
market on the finger, then the system does not accept and it leads to the authentication
failure.
There is need to apply a different type of the authentication techniques for the
authentication (Dascalescu, 2018).
4

Nayankumar Kantilal Thakkar 11609358
Part 4
Below show the two cases when the negative pose is more serious threats.
1. Case 1, when the system does not recognize the correct person for the biometric
authentication. If the system fails to detect the correct person in that situation
important data of the system loss, in this case, the false negative leads to a serious
problem.
2. Case 2 as all the data is stored over the database and the database also has the
biometric authentication, if the system fails to recognize the user or manager, then a
large amount of the data is a loss of the different users. And this leads to the serious
consequences.
5
Part 4
Below show the two cases when the negative pose is more serious threats.
1. Case 1, when the system does not recognize the correct person for the biometric
authentication. If the system fails to detect the correct person in that situation
important data of the system loss, in this case, the false negative leads to a serious
problem.
2. Case 2 as all the data is stored over the database and the database also has the
biometric authentication, if the system fails to recognize the user or manager, then a
large amount of the data is a loss of the different users. And this leads to the serious
consequences.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
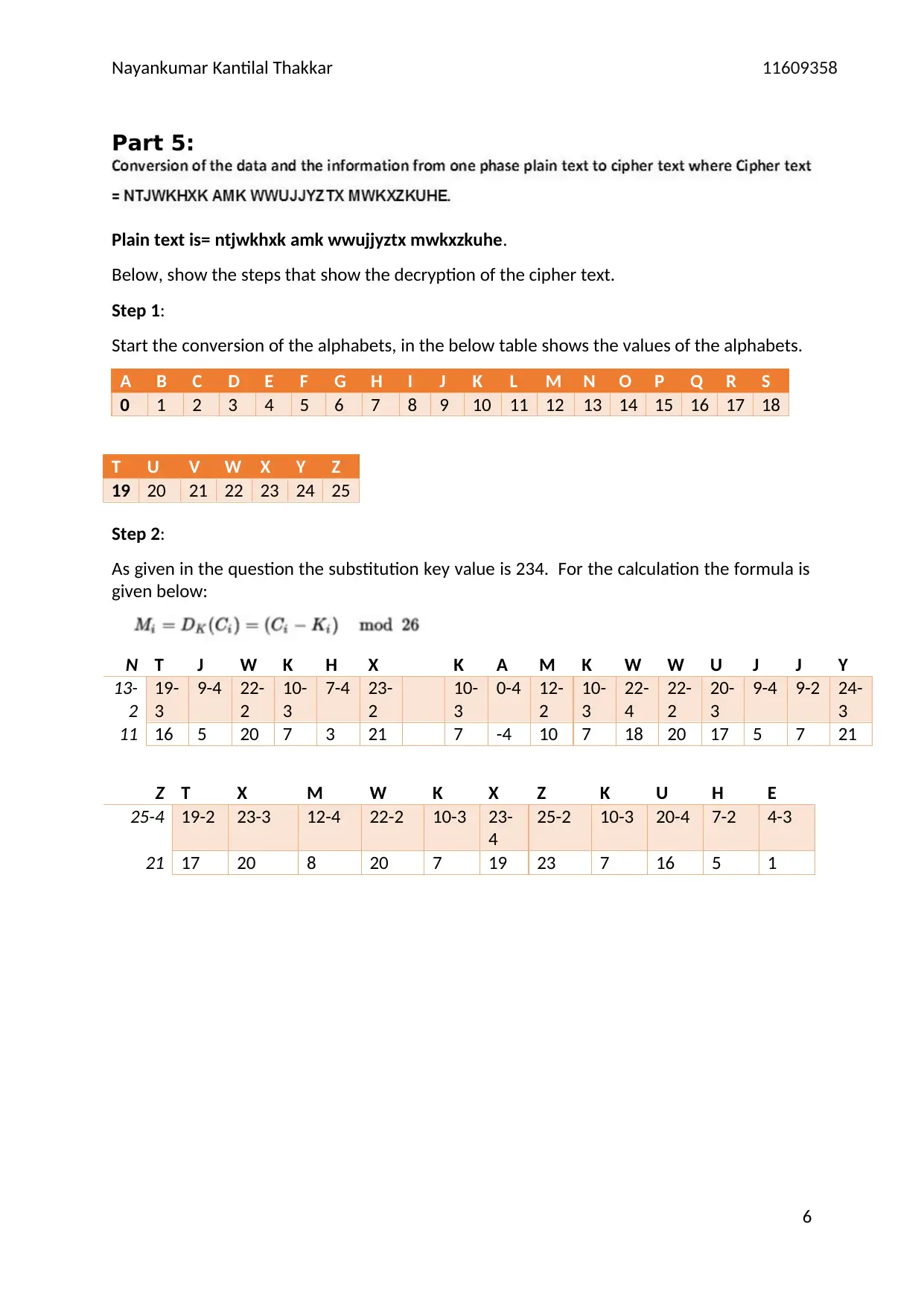
Nayankumar Kantilal Thakkar 11609358
Part 5:
Plain text is= ntjwkhxk amk wwujjyztx mwkxzkuhe.
Below, show the steps that show the decryption of the cipher text.
Step 1:
Start the conversion of the alphabets, in the below table shows the values of the alphabets.
A B C D E F G H I J K L M N O P Q R S
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18
Step 2:
As given in the question the substitution key value is 234. For the calculation the formula is
given below:
N T J W K H X K A M K W W U J J Y
13-
2
19-
3
9-4 22-
2
10-
3
7-4 23-
2
10-
3
0-4 12-
2
10-
3
22-
4
22-
2
20-
3
9-4 9-2 24-
3
11 16 5 20 7 3 21 7 -4 10 7 18 20 17 5 7 21
Z T X M W K X Z K U H E
25-4 19-2 23-3 12-4 22-2 10-3 23-
4
25-2 10-3 20-4 7-2 4-3
21 17 20 8 20 7 19 23 7 16 5 1
6
T U V W X Y Z
19 20 21 22 23 24 25
Part 5:
Plain text is= ntjwkhxk amk wwujjyztx mwkxzkuhe.
Below, show the steps that show the decryption of the cipher text.
Step 1:
Start the conversion of the alphabets, in the below table shows the values of the alphabets.
A B C D E F G H I J K L M N O P Q R S
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18
Step 2:
As given in the question the substitution key value is 234. For the calculation the formula is
given below:
N T J W K H X K A M K W W U J J Y
13-
2
19-
3
9-4 22-
2
10-
3
7-4 23-
2
10-
3
0-4 12-
2
10-
3
22-
4
22-
2
20-
3
9-4 9-2 24-
3
11 16 5 20 7 3 21 7 -4 10 7 18 20 17 5 7 21
Z T X M W K X Z K U H E
25-4 19-2 23-3 12-4 22-2 10-3 23-
4
25-2 10-3 20-4 7-2 4-3
21 17 20 8 20 7 19 23 7 16 5 1
6
T U V W X Y Z
19 20 21 22 23 24 25
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
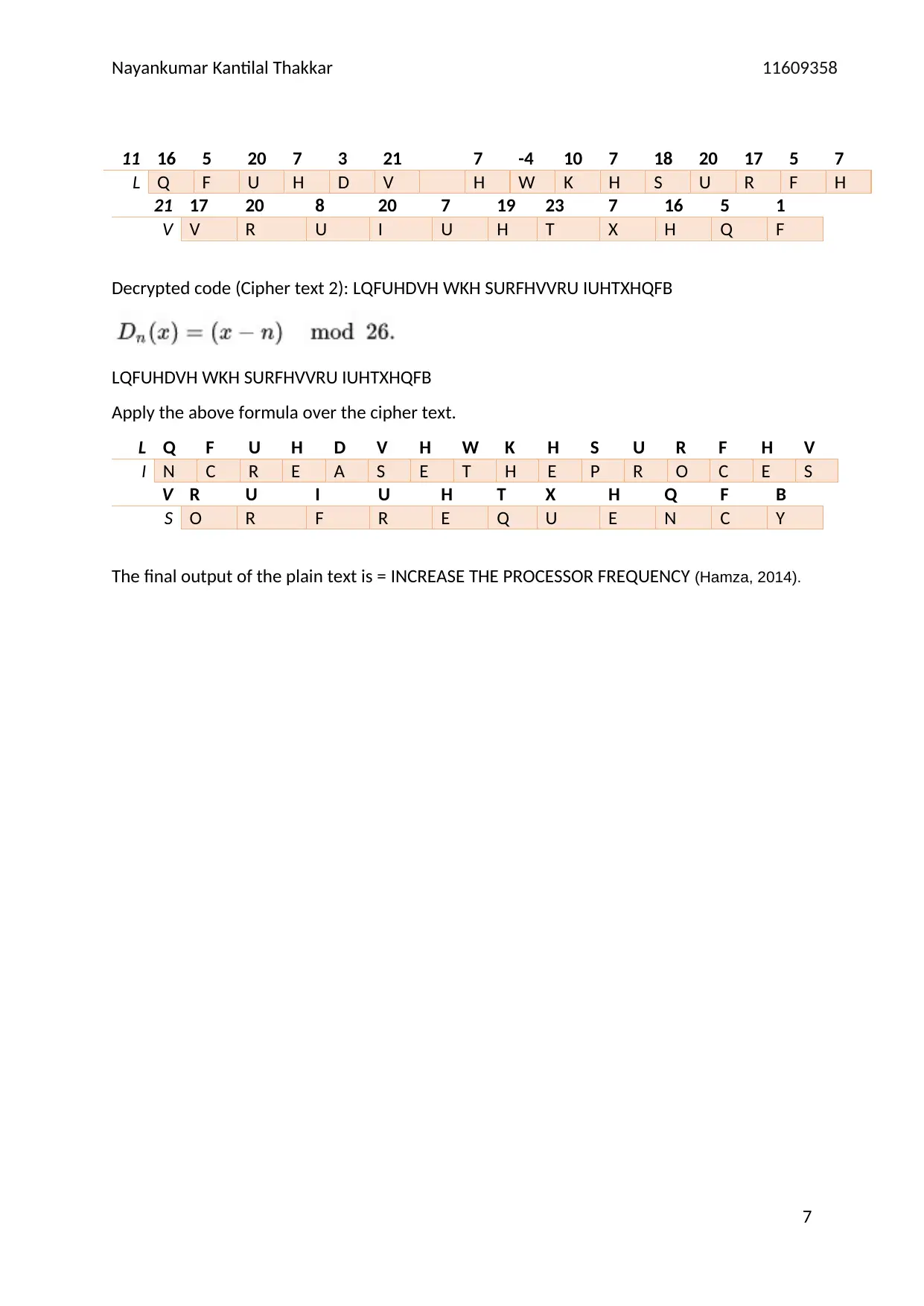
Nayankumar Kantilal Thakkar 11609358
11 16 5 20 7 3 21 7 -4 10 7 18 20 17 5 7
L Q F U H D V H W K H S U R F H
21 17 20 8 20 7 19 23 7 16 5 1
V V R U I U H T X H Q F
Decrypted code (Cipher text 2): LQFUHDVH WKH SURFHVVRU IUHTXHQFB
LQFUHDVH WKH SURFHVVRU IUHTXHQFB
Apply the above formula over the cipher text.
L Q F U H D V H W K H S U R F H V
I N C R E A S E T H E P R O C E S
V R U I U H T X H Q F B
S O R F R E Q U E N C Y
The final output of the plain text is = INCREASE THE PROCESSOR FREQUENCY (Hamza, 2014).
7
11 16 5 20 7 3 21 7 -4 10 7 18 20 17 5 7
L Q F U H D V H W K H S U R F H
21 17 20 8 20 7 19 23 7 16 5 1
V V R U I U H T X H Q F
Decrypted code (Cipher text 2): LQFUHDVH WKH SURFHVVRU IUHTXHQFB
LQFUHDVH WKH SURFHVVRU IUHTXHQFB
Apply the above formula over the cipher text.
L Q F U H D V H W K H S U R F H V
I N C R E A S E T H E P R O C E S
V R U I U H T X H Q F B
S O R F R E Q U E N C Y
The final output of the plain text is = INCREASE THE PROCESSOR FREQUENCY (Hamza, 2014).
7

Nayankumar Kantilal Thakkar 11609358
References
Chia, T. (2012). Confidentiality, Integrity, Availability: The three components of the
CIA Triad « Stack Exchange Security Blog. Security.blogoverflow.com. Retrieved from
https://security.blogoverflow.com/2012/08/confidentiality-integrity-availability-the-
three-components-of-the-cia-triad/
DASCALESCU, A. (2018). Biometric Authentication Overview, Advantages &
Disadvantages. Heimdal Security Blog. Retrieved from
https://heimdalsecurity.com/blog/biometric-authentication/
Enterprise, M. (2018). Five Ways to Improve ATM Security Using McAfee Integrity
Control McAfee Blogs. McAfee Blogs. Retrieved from
https://securingtomorrow.mcafee.com/business/five-ways-improve-atm-security-
using-mcafee-integrity-control/
Hamza, M. (2014). Converting plain text to cipher text. Issue. Retrieved from
https://issuu.com/hamzamac/docs/is102-assignment2
8
References
Chia, T. (2012). Confidentiality, Integrity, Availability: The three components of the
CIA Triad « Stack Exchange Security Blog. Security.blogoverflow.com. Retrieved from
https://security.blogoverflow.com/2012/08/confidentiality-integrity-availability-the-
three-components-of-the-cia-triad/
DASCALESCU, A. (2018). Biometric Authentication Overview, Advantages &
Disadvantages. Heimdal Security Blog. Retrieved from
https://heimdalsecurity.com/blog/biometric-authentication/
Enterprise, M. (2018). Five Ways to Improve ATM Security Using McAfee Integrity
Control McAfee Blogs. McAfee Blogs. Retrieved from
https://securingtomorrow.mcafee.com/business/five-ways-improve-atm-security-
using-mcafee-integrity-control/
Hamza, M. (2014). Converting plain text to cipher text. Issue. Retrieved from
https://issuu.com/hamzamac/docs/is102-assignment2
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





