Cybersecurity Use Cases: Mitre ATT&CK Framework Report and Analysis
VerifiedAdded on 2022/09/05
|14
|2484
|33
Report
AI Summary
This report provides a comprehensive analysis of 40 IT security monitoring use cases, developed based on the Mitre ATT&CK framework. The use cases are designed to address various cyber threats, including those from Advanced Persistent Threat (APT) groups, and are aligned with NIST 800-53 and CIS CSC standards. Each use case includes a description, Mitre ATT&CK ID, tactic, technique, data sources, suggested mitigations, and detection methods. The report emphasizes the importance of understanding and applying the MITRE ATT&CK framework for effective cybersecurity. The assignment aims to provide a practical guide for identifying and mitigating potential security risks within organizations, covering a wide range of attack techniques and offering actionable strategies for enhancing security posture. The report also includes an Excel file with all the use cases.

Running head:Information Security Management 1
Information Security Management
Name
Institution
Information Security Management
Name
Institution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Information Security Management 2
Summary
Every day, some attacks have been designed to steal confidential data. The main targets of
these attacks are the organizations that harbor large databases, according to the Verizon Data
Breach Investigation Report of 2015. The databases are being attacked because they form the heart
of an organization, and the main targets include business data, personal information, and other
confidential own records (Wirtz & Heisel, 2019, July). Many organizations are not protecting these
data well enough. The hacking happens when malicious people have access to personal information
that may inflict damage to business operations, and besides, there may be a financial loss to an
organization (Maurer, 2004). Organizations have also suffered reputation, loss, and breaches that
may result in regulatory violations, legal fees, and fines.
The top threats to data include excessive privileges, including when workers are granted
rights that surpass their activity necessities. The benefits can be manhandled, for instance if a bank
bookkeeper may have too much privilege access and increase the bookkeeper balance for an offered
record, to take fitting measures to secure the data, and get to benefits, most organizations still
neglect to refresh the entrance benefits for workers who change jobs inside the association (Elmasri
& Navathe, 2011).
Another database attack include database injection attacks, the two types of attacks include
the DQL injection, and database systems (Stech, Heckman & Strom, 2016). Although big data is
not susceptible to SLQ injection attacks, they have their vulnerabilities that make it possible to have
a successful attack. Malware attack is another type of attack that may be carried out on a database
(Wirtz & Heisel, 2018, October). Lack of patch of databases is another problem that may lead to a
successful attack. Most companies still take time to do patching that leads to high workloads,
complex, and time-consuming procedures for testing and implementing the database patches.
Summary
Every day, some attacks have been designed to steal confidential data. The main targets of
these attacks are the organizations that harbor large databases, according to the Verizon Data
Breach Investigation Report of 2015. The databases are being attacked because they form the heart
of an organization, and the main targets include business data, personal information, and other
confidential own records (Wirtz & Heisel, 2019, July). Many organizations are not protecting these
data well enough. The hacking happens when malicious people have access to personal information
that may inflict damage to business operations, and besides, there may be a financial loss to an
organization (Maurer, 2004). Organizations have also suffered reputation, loss, and breaches that
may result in regulatory violations, legal fees, and fines.
The top threats to data include excessive privileges, including when workers are granted
rights that surpass their activity necessities. The benefits can be manhandled, for instance if a bank
bookkeeper may have too much privilege access and increase the bookkeeper balance for an offered
record, to take fitting measures to secure the data, and get to benefits, most organizations still
neglect to refresh the entrance benefits for workers who change jobs inside the association (Elmasri
& Navathe, 2011).
Another database attack include database injection attacks, the two types of attacks include
the DQL injection, and database systems (Stech, Heckman & Strom, 2016). Although big data is
not susceptible to SLQ injection attacks, they have their vulnerabilities that make it possible to have
a successful attack. Malware attack is another type of attack that may be carried out on a database
(Wirtz & Heisel, 2018, October). Lack of patch of databases is another problem that may lead to a
successful attack. Most companies still take time to do patching that leads to high workloads,
complex, and time-consuming procedures for testing and implementing the database patches.

Information Security Management 3
Contents
Summary..................................................................................................................................2
Contents....................................................................................................................................3
Information Security Use Cases...............................................................................................5
No.........................................................................................................................................5
Use Case Description..........................................................................................................5
Mitre ID...............................................................................................................................5
Mitre Tactic........................................................................................................................5
Mitre Technique.................................................................................................................5
Data Sources.......................................................................................................................5
Mitigations..........................................................................................................................5
Detections............................................................................................................................5
NIST REF#..........................................................................................................................5
CSC REF#...........................................................................................................................5
Conclusions............................................................................................................................11
References..............................................................................................................................11
Contents
Summary..................................................................................................................................2
Contents....................................................................................................................................3
Information Security Use Cases...............................................................................................5
No.........................................................................................................................................5
Use Case Description..........................................................................................................5
Mitre ID...............................................................................................................................5
Mitre Tactic........................................................................................................................5
Mitre Technique.................................................................................................................5
Data Sources.......................................................................................................................5
Mitigations..........................................................................................................................5
Detections............................................................................................................................5
NIST REF#..........................................................................................................................5
CSC REF#...........................................................................................................................5
Conclusions............................................................................................................................11
References..............................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Information Security Management 4
Introduction
MITRE ATT&Ck is a set of tools that help to logically assess the security controls against
the risks that a company may face. The MITRE Framework is useful in in understanding the gaps
that are existing in the current system, there are many usecases that make MITRE attacks
compelling and need a closer look by companies. The use cases are used to describe application
threat intelligence. The threat intelligence data is important in most security operations and most
security officers do not know what to do with the security operations. Most individuals will step
back and view what they need to do more strategically (Wirtz & Heisel, 2018, October). MITRE
ATT&CK gives the cyber security professionals a way to relate the probability of the threats, a
prospective attacker tactics and the techniques used in the attacks are documented. The response are
also well outlined. The MITRE ATTACK helps document a good view of the system gaps that
may face these threats, then using the security framework build from the MITRE ATT&CK, a
security plan can be built (Munaiah & Meneely, 2016, November). The MITRe ATT&CK maix has
been shown in appendix A in the appendices section.
Introduction
MITRE ATT&Ck is a set of tools that help to logically assess the security controls against
the risks that a company may face. The MITRE Framework is useful in in understanding the gaps
that are existing in the current system, there are many usecases that make MITRE attacks
compelling and need a closer look by companies. The use cases are used to describe application
threat intelligence. The threat intelligence data is important in most security operations and most
security officers do not know what to do with the security operations. Most individuals will step
back and view what they need to do more strategically (Wirtz & Heisel, 2018, October). MITRE
ATT&CK gives the cyber security professionals a way to relate the probability of the threats, a
prospective attacker tactics and the techniques used in the attacks are documented. The response are
also well outlined. The MITRE ATTACK helps document a good view of the system gaps that
may face these threats, then using the security framework build from the MITRE ATT&CK, a
security plan can be built (Munaiah & Meneely, 2016, November). The MITRe ATT&CK maix has
been shown in appendix A in the appendices section.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
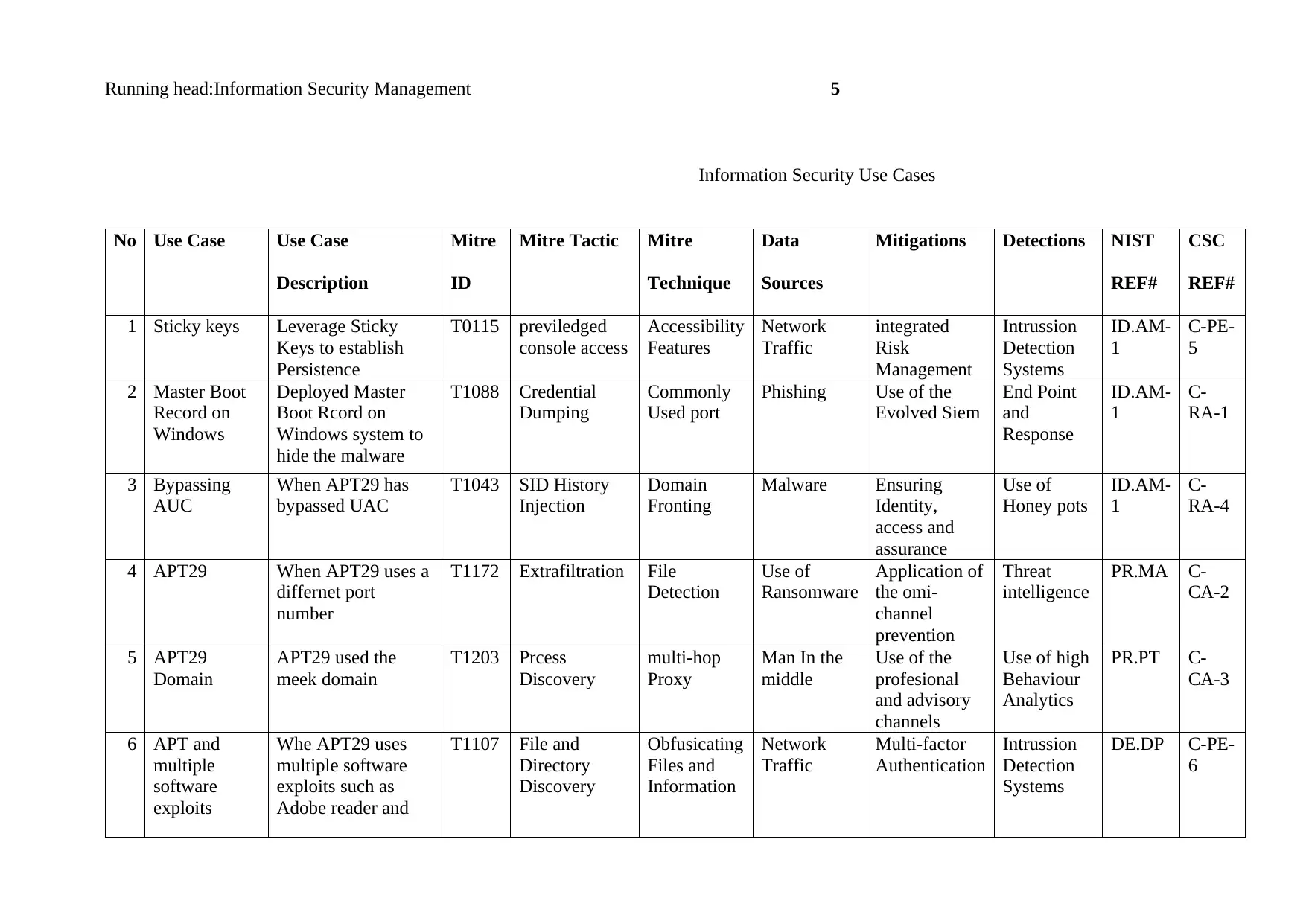
Running head:Information Security Management 5
Information Security Use Cases
No Use Case Use Case
Description
Mitre
ID
Mitre Tactic Mitre
Technique
Data
Sources
Mitigations Detections NIST
REF#
CSC
REF#
1 Sticky keys Leverage Sticky
Keys to establish
Persistence
T0115 previledged
console access
Accessibility
Features
Network
Traffic
integrated
Risk
Management
Intrussion
Detection
Systems
ID.AM-
1
C-PE-
5
2 Master Boot
Record on
Windows
Deployed Master
Boot Rcord on
Windows system to
hide the malware
T1088 Credential
Dumping
Commonly
Used port
Phishing Use of the
Evolved Siem
End Point
and
Response
ID.AM-
1
C-
RA-1
3 Bypassing
AUC
When APT29 has
bypassed UAC
T1043 SID History
Injection
Domain
Fronting
Malware Ensuring
Identity,
access and
assurance
Use of
Honey pots
ID.AM-
1
C-
RA-4
4 APT29 When APT29 uses a
differnet port
number
T1172 Extrafiltration File
Detection
Use of
Ransomware
Application of
the omi-
channel
prevention
Threat
intelligence
PR.MA C-
CA-2
5 APT29
Domain
APT29 used the
meek domain
T1203 Prcess
Discovery
multi-hop
Proxy
Man In the
middle
Use of the
profesional
and advisory
channels
Use of high
Behaviour
Analytics
PR.PT C-
CA-3
6 APT and
multiple
software
exploits
Whe APT29 uses
multiple software
exploits such as
Adobe reader and
T1107 File and
Directory
Discovery
Obfusicating
Files and
Information
Network
Traffic
Multi-factor
Authentication
Intrussion
Detection
Systems
DE.DP C-PE-
6
Information Security Use Cases
No Use Case Use Case
Description
Mitre
ID
Mitre Tactic Mitre
Technique
Data
Sources
Mitigations Detections NIST
REF#
CSC
REF#
1 Sticky keys Leverage Sticky
Keys to establish
Persistence
T0115 previledged
console access
Accessibility
Features
Network
Traffic
integrated
Risk
Management
Intrussion
Detection
Systems
ID.AM-
1
C-PE-
5
2 Master Boot
Record on
Windows
Deployed Master
Boot Rcord on
Windows system to
hide the malware
T1088 Credential
Dumping
Commonly
Used port
Phishing Use of the
Evolved Siem
End Point
and
Response
ID.AM-
1
C-
RA-1
3 Bypassing
AUC
When APT29 has
bypassed UAC
T1043 SID History
Injection
Domain
Fronting
Malware Ensuring
Identity,
access and
assurance
Use of
Honey pots
ID.AM-
1
C-
RA-4
4 APT29 When APT29 uses a
differnet port
number
T1172 Extrafiltration File
Detection
Use of
Ransomware
Application of
the omi-
channel
prevention
Threat
intelligence
PR.MA C-
CA-2
5 APT29
Domain
APT29 used the
meek domain
T1203 Prcess
Discovery
multi-hop
Proxy
Man In the
middle
Use of the
profesional
and advisory
channels
Use of high
Behaviour
Analytics
PR.PT C-
CA-3
6 APT and
multiple
software
exploits
Whe APT29 uses
multiple software
exploits such as
Adobe reader and
T1107 File and
Directory
Discovery
Obfusicating
Files and
Information
Network
Traffic
Multi-factor
Authentication
Intrussion
Detection
Systems
DE.DP C-PE-
6
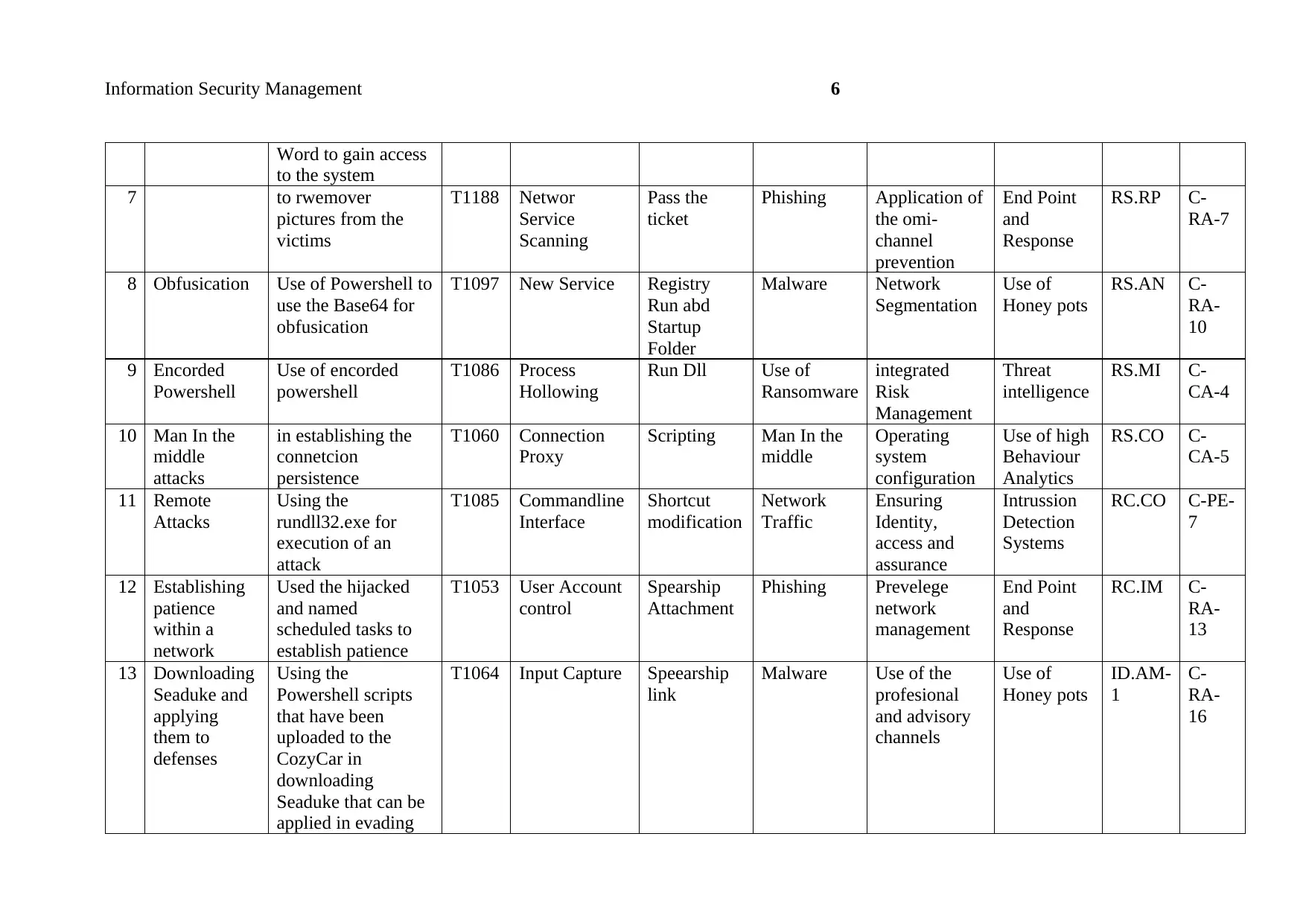
Information Security Management 6
Word to gain access
to the system
7 to rwemover
pictures from the
victims
T1188 Networ
Service
Scanning
Pass the
ticket
Phishing Application of
the omi-
channel
prevention
End Point
and
Response
RS.RP C-
RA-7
8 Obfusication Use of Powershell to
use the Base64 for
obfusication
T1097 New Service Registry
Run abd
Startup
Folder
Malware Network
Segmentation
Use of
Honey pots
RS.AN C-
RA-
10
9 Encorded
Powershell
Use of encorded
powershell
T1086 Process
Hollowing
Run Dll Use of
Ransomware
integrated
Risk
Management
Threat
intelligence
RS.MI C-
CA-4
10 Man In the
middle
attacks
in establishing the
connetcion
persistence
T1060 Connection
Proxy
Scripting Man In the
middle
Operating
system
configuration
Use of high
Behaviour
Analytics
RS.CO C-
CA-5
11 Remote
Attacks
Using the
rundll32.exe for
execution of an
attack
T1085 Commandline
Interface
Shortcut
modification
Network
Traffic
Ensuring
Identity,
access and
assurance
Intrussion
Detection
Systems
RC.CO C-PE-
7
12 Establishing
patience
within a
network
Used the hijacked
and named
scheduled tasks to
establish patience
T1053 User Account
control
Spearship
Attachment
Phishing Prevelege
network
management
End Point
and
Response
RC.IM C-
RA-
13
13 Downloading
Seaduke and
applying
them to
defenses
Using the
Powershell scripts
that have been
uploaded to the
CozyCar in
downloading
Seaduke that can be
applied in evading
T1064 Input Capture Speearship
link
Malware Use of the
profesional
and advisory
channels
Use of
Honey pots
ID.AM-
1
C-
RA-
16
Word to gain access
to the system
7 to rwemover
pictures from the
victims
T1188 Networ
Service
Scanning
Pass the
ticket
Phishing Application of
the omi-
channel
prevention
End Point
and
Response
RS.RP C-
RA-7
8 Obfusication Use of Powershell to
use the Base64 for
obfusication
T1097 New Service Registry
Run abd
Startup
Folder
Malware Network
Segmentation
Use of
Honey pots
RS.AN C-
RA-
10
9 Encorded
Powershell
Use of encorded
powershell
T1086 Process
Hollowing
Run Dll Use of
Ransomware
integrated
Risk
Management
Threat
intelligence
RS.MI C-
CA-4
10 Man In the
middle
attacks
in establishing the
connetcion
persistence
T1060 Connection
Proxy
Scripting Man In the
middle
Operating
system
configuration
Use of high
Behaviour
Analytics
RS.CO C-
CA-5
11 Remote
Attacks
Using the
rundll32.exe for
execution of an
attack
T1085 Commandline
Interface
Shortcut
modification
Network
Traffic
Ensuring
Identity,
access and
assurance
Intrussion
Detection
Systems
RC.CO C-PE-
7
12 Establishing
patience
within a
network
Used the hijacked
and named
scheduled tasks to
establish patience
T1053 User Account
control
Spearship
Attachment
Phishing Prevelege
network
management
End Point
and
Response
RC.IM C-
RA-
13
13 Downloading
Seaduke and
applying
them to
defenses
Using the
Powershell scripts
that have been
uploaded to the
CozyCar in
downloading
Seaduke that can be
applied in evading
T1064 Input Capture Speearship
link
Malware Use of the
profesional
and advisory
channels
Use of
Honey pots
ID.AM-
1
C-
RA-
16
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
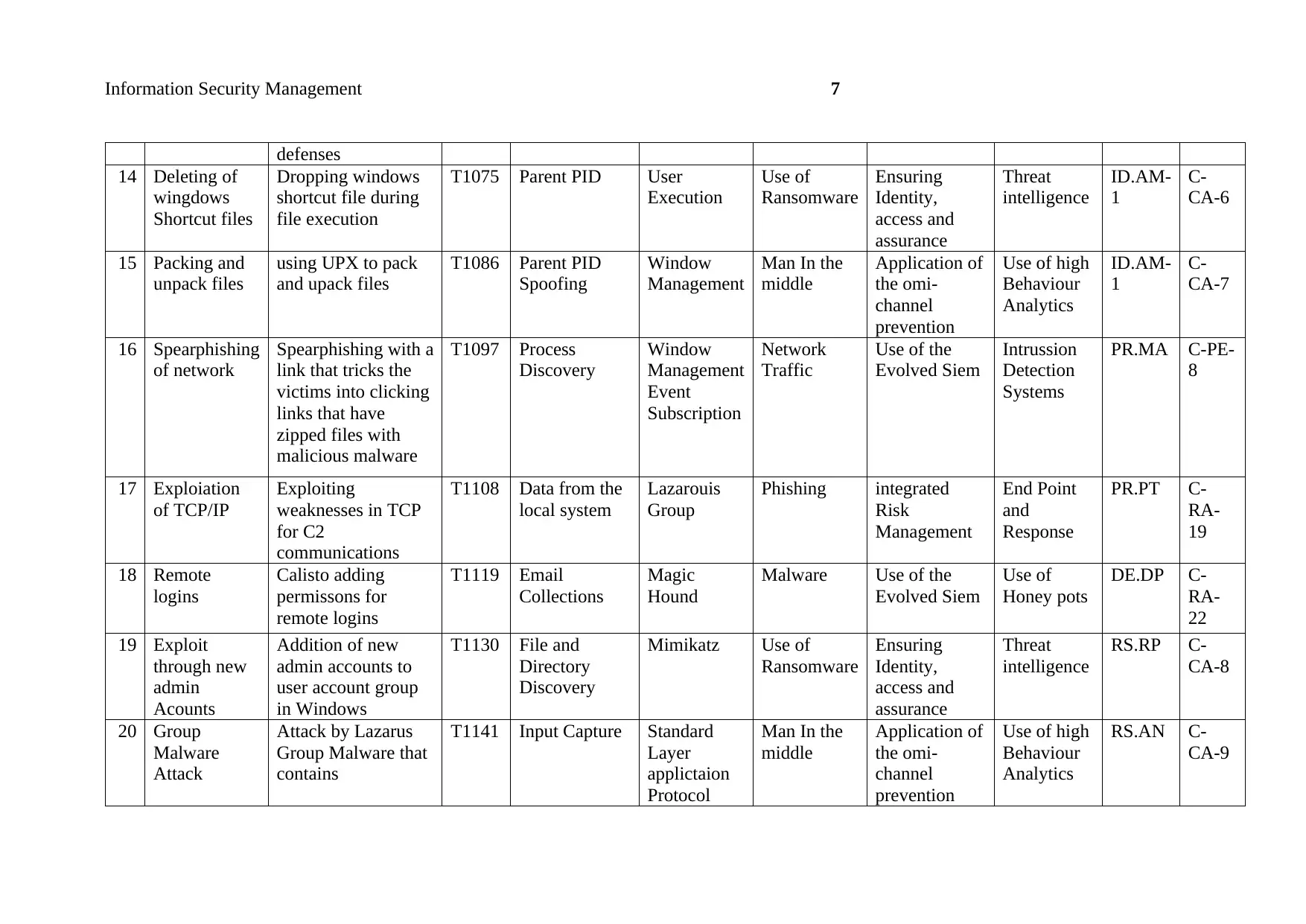
Information Security Management 7
defenses
14 Deleting of
wingdows
Shortcut files
Dropping windows
shortcut file during
file execution
T1075 Parent PID User
Execution
Use of
Ransomware
Ensuring
Identity,
access and
assurance
Threat
intelligence
ID.AM-
1
C-
CA-6
15 Packing and
unpack files
using UPX to pack
and upack files
T1086 Parent PID
Spoofing
Window
Management
Man In the
middle
Application of
the omi-
channel
prevention
Use of high
Behaviour
Analytics
ID.AM-
1
C-
CA-7
16 Spearphishing
of network
Spearphishing with a
link that tricks the
victims into clicking
links that have
zipped files with
malicious malware
T1097 Process
Discovery
Window
Management
Event
Subscription
Network
Traffic
Use of the
Evolved Siem
Intrussion
Detection
Systems
PR.MA C-PE-
8
17 Exploiation
of TCP/IP
Exploiting
weaknesses in TCP
for C2
communications
T1108 Data from the
local system
Lazarouis
Group
Phishing integrated
Risk
Management
End Point
and
Response
PR.PT C-
RA-
19
18 Remote
logins
Calisto adding
permissons for
remote logins
T1119 Email
Collections
Magic
Hound
Malware Use of the
Evolved Siem
Use of
Honey pots
DE.DP C-
RA-
22
19 Exploit
through new
admin
Acounts
Addition of new
admin accounts to
user account group
in Windows
T1130 File and
Directory
Discovery
Mimikatz Use of
Ransomware
Ensuring
Identity,
access and
assurance
Threat
intelligence
RS.RP C-
CA-8
20 Group
Malware
Attack
Attack by Lazarus
Group Malware that
contains
T1141 Input Capture Standard
Layer
applictaion
Protocol
Man In the
middle
Application of
the omi-
channel
prevention
Use of high
Behaviour
Analytics
RS.AN C-
CA-9
defenses
14 Deleting of
wingdows
Shortcut files
Dropping windows
shortcut file during
file execution
T1075 Parent PID User
Execution
Use of
Ransomware
Ensuring
Identity,
access and
assurance
Threat
intelligence
ID.AM-
1
C-
CA-6
15 Packing and
unpack files
using UPX to pack
and upack files
T1086 Parent PID
Spoofing
Window
Management
Man In the
middle
Application of
the omi-
channel
prevention
Use of high
Behaviour
Analytics
ID.AM-
1
C-
CA-7
16 Spearphishing
of network
Spearphishing with a
link that tricks the
victims into clicking
links that have
zipped files with
malicious malware
T1097 Process
Discovery
Window
Management
Event
Subscription
Network
Traffic
Use of the
Evolved Siem
Intrussion
Detection
Systems
PR.MA C-PE-
8
17 Exploiation
of TCP/IP
Exploiting
weaknesses in TCP
for C2
communications
T1108 Data from the
local system
Lazarouis
Group
Phishing integrated
Risk
Management
End Point
and
Response
PR.PT C-
RA-
19
18 Remote
logins
Calisto adding
permissons for
remote logins
T1119 Email
Collections
Magic
Hound
Malware Use of the
Evolved Siem
Use of
Honey pots
DE.DP C-
RA-
22
19 Exploit
through new
admin
Acounts
Addition of new
admin accounts to
user account group
in Windows
T1130 File and
Directory
Discovery
Mimikatz Use of
Ransomware
Ensuring
Identity,
access and
assurance
Threat
intelligence
RS.RP C-
CA-8
20 Group
Malware
Attack
Attack by Lazarus
Group Malware that
contains
T1141 Input Capture Standard
Layer
applictaion
Protocol
Man In the
middle
Application of
the omi-
channel
prevention
Use of high
Behaviour
Analytics
RS.AN C-
CA-9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
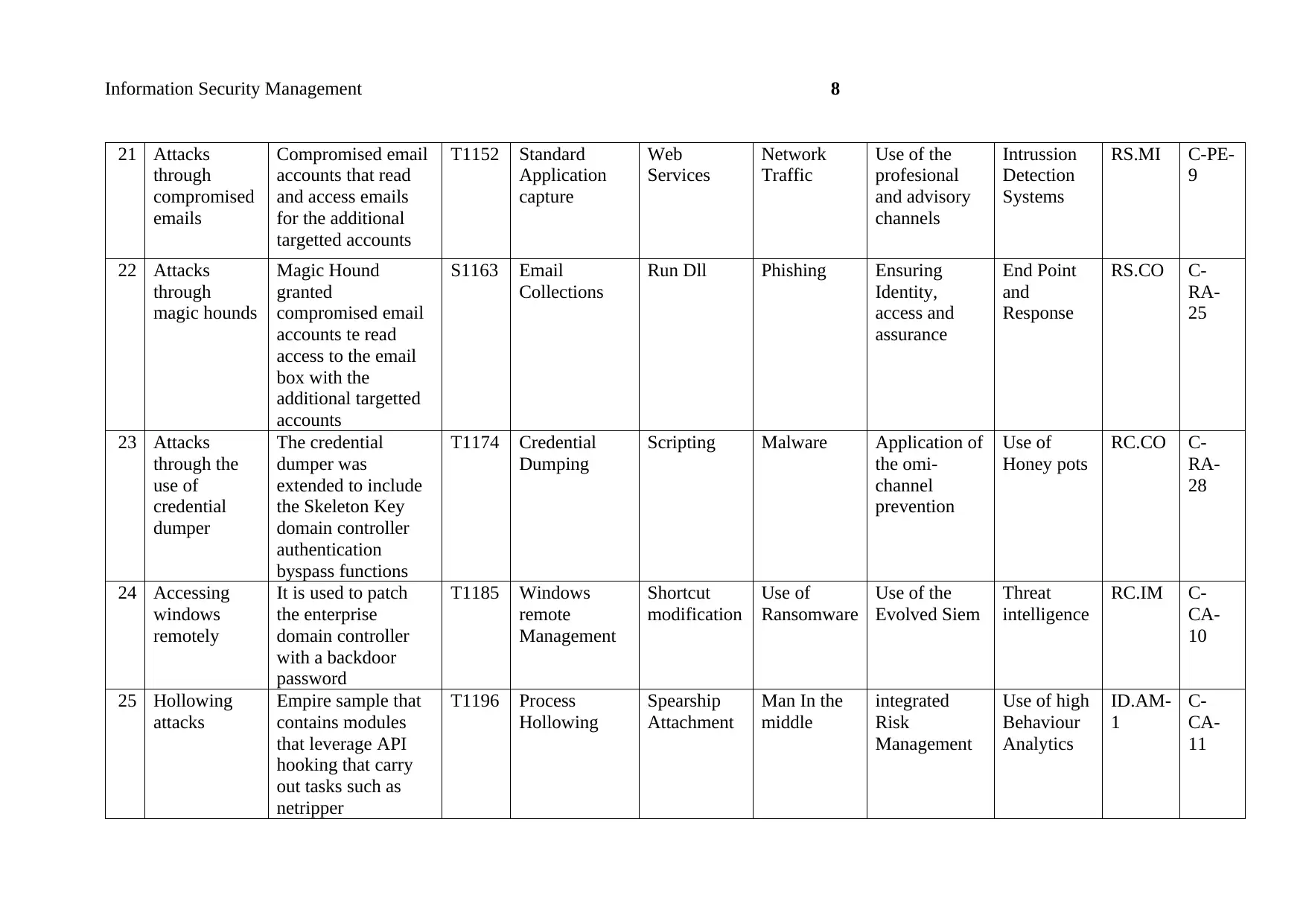
Information Security Management 8
21 Attacks
through
compromised
emails
Compromised email
accounts that read
and access emails
for the additional
targetted accounts
T1152 Standard
Application
capture
Web
Services
Network
Traffic
Use of the
profesional
and advisory
channels
Intrussion
Detection
Systems
RS.MI C-PE-
9
22 Attacks
through
magic hounds
Magic Hound
granted
compromised email
accounts te read
access to the email
box with the
additional targetted
accounts
S1163 Email
Collections
Run Dll Phishing Ensuring
Identity,
access and
assurance
End Point
and
Response
RS.CO C-
RA-
25
23 Attacks
through the
use of
credential
dumper
The credential
dumper was
extended to include
the Skeleton Key
domain controller
authentication
byspass functions
T1174 Credential
Dumping
Scripting Malware Application of
the omi-
channel
prevention
Use of
Honey pots
RC.CO C-
RA-
28
24 Accessing
windows
remotely
It is used to patch
the enterprise
domain controller
with a backdoor
password
T1185 Windows
remote
Management
Shortcut
modification
Use of
Ransomware
Use of the
Evolved Siem
Threat
intelligence
RC.IM C-
CA-
10
25 Hollowing
attacks
Empire sample that
contains modules
that leverage API
hooking that carry
out tasks such as
netripper
T1196 Process
Hollowing
Spearship
Attachment
Man In the
middle
integrated
Risk
Management
Use of high
Behaviour
Analytics
ID.AM-
1
C-
CA-
11
21 Attacks
through
compromised
emails
Compromised email
accounts that read
and access emails
for the additional
targetted accounts
T1152 Standard
Application
capture
Web
Services
Network
Traffic
Use of the
profesional
and advisory
channels
Intrussion
Detection
Systems
RS.MI C-PE-
9
22 Attacks
through
magic hounds
Magic Hound
granted
compromised email
accounts te read
access to the email
box with the
additional targetted
accounts
S1163 Email
Collections
Run Dll Phishing Ensuring
Identity,
access and
assurance
End Point
and
Response
RS.CO C-
RA-
25
23 Attacks
through the
use of
credential
dumper
The credential
dumper was
extended to include
the Skeleton Key
domain controller
authentication
byspass functions
T1174 Credential
Dumping
Scripting Malware Application of
the omi-
channel
prevention
Use of
Honey pots
RC.CO C-
RA-
28
24 Accessing
windows
remotely
It is used to patch
the enterprise
domain controller
with a backdoor
password
T1185 Windows
remote
Management
Shortcut
modification
Use of
Ransomware
Use of the
Evolved Siem
Threat
intelligence
RC.IM C-
CA-
10
25 Hollowing
attacks
Empire sample that
contains modules
that leverage API
hooking that carry
out tasks such as
netripper
T1196 Process
Hollowing
Spearship
Attachment
Man In the
middle
integrated
Risk
Management
Use of high
Behaviour
Analytics
ID.AM-
1
C-
CA-
11
Information Security Management 9
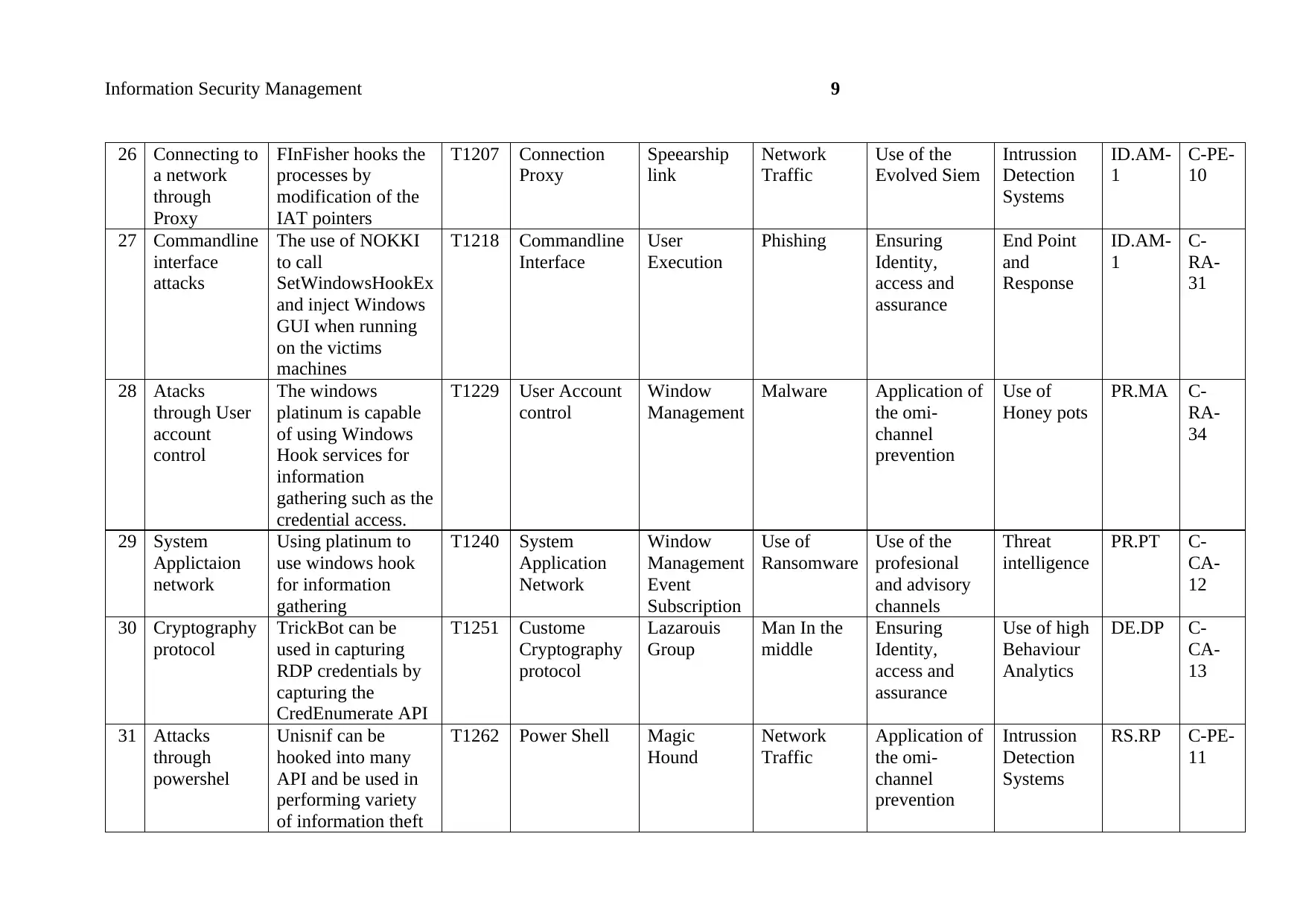
26 Connecting to
a network
through
Proxy
FInFisher hooks the
processes by
modification of the
IAT pointers
T1207 Connection
Proxy
Speearship
link
Network
Traffic
Use of the
Evolved Siem
Intrussion
Detection
Systems
ID.AM-
1
C-PE-
10
27 Commandline
interface
attacks
The use of NOKKI
to call
SetWindowsHookEx
and inject Windows
GUI when running
on the victims
machines
T1218 Commandline
Interface
User
Execution
Phishing Ensuring
Identity,
access and
assurance
End Point
and
Response
ID.AM-
1
C-
RA-
31
28 Atacks
through User
account
control
The windows
platinum is capable
of using Windows
Hook services for
information
gathering such as the
credential access.
T1229 User Account
control
Window
Management
Malware Application of
the omi-
channel
prevention
Use of
Honey pots
PR.MA C-
RA-
34
29 System
Applictaion
network
Using platinum to
use windows hook
for information
gathering
T1240 System
Application
Network
Window
Management
Event
Subscription
Use of
Ransomware
Use of the
profesional
and advisory
channels
Threat
intelligence
PR.PT C-
CA-
12
30 Cryptography
protocol
TrickBot can be
used in capturing
RDP credentials by
capturing the
CredEnumerate API
T1251 Custome
Cryptography
protocol
Lazarouis
Group
Man In the
middle
Ensuring
Identity,
access and
assurance
Use of high
Behaviour
Analytics
DE.DP C-
CA-
13
31 Attacks
through
powershel
Unisnif can be
hooked into many
API and be used in
performing variety
of information theft
T1262 Power Shell Magic
Hound
Network
Traffic
Application of
the omi-
channel
prevention
Intrussion
Detection
Systems
RS.RP C-PE-
11
26 Connecting to
a network
through
Proxy
FInFisher hooks the
processes by
modification of the
IAT pointers
T1207 Connection
Proxy
Speearship
link
Network
Traffic
Use of the
Evolved Siem
Intrussion
Detection
Systems
ID.AM-
1
C-PE-
10
27 Commandline
interface
attacks
The use of NOKKI
to call
SetWindowsHookEx
and inject Windows
GUI when running
on the victims
machines
T1218 Commandline
Interface
User
Execution
Phishing Ensuring
Identity,
access and
assurance
End Point
and
Response
ID.AM-
1
C-
RA-
31
28 Atacks
through User
account
control
The windows
platinum is capable
of using Windows
Hook services for
information
gathering such as the
credential access.
T1229 User Account
control
Window
Management
Malware Application of
the omi-
channel
prevention
Use of
Honey pots
PR.MA C-
RA-
34
29 System
Applictaion
network
Using platinum to
use windows hook
for information
gathering
T1240 System
Application
Network
Window
Management
Event
Subscription
Use of
Ransomware
Use of the
profesional
and advisory
channels
Threat
intelligence
PR.PT C-
CA-
12
30 Cryptography
protocol
TrickBot can be
used in capturing
RDP credentials by
capturing the
CredEnumerate API
T1251 Custome
Cryptography
protocol
Lazarouis
Group
Man In the
middle
Ensuring
Identity,
access and
assurance
Use of high
Behaviour
Analytics
DE.DP C-
CA-
13
31 Attacks
through
powershel
Unisnif can be
hooked into many
API and be used in
performing variety
of information theft
T1262 Power Shell Magic
Hound
Network
Traffic
Application of
the omi-
channel
prevention
Intrussion
Detection
Systems
RS.RP C-PE-
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Information Security Management 10
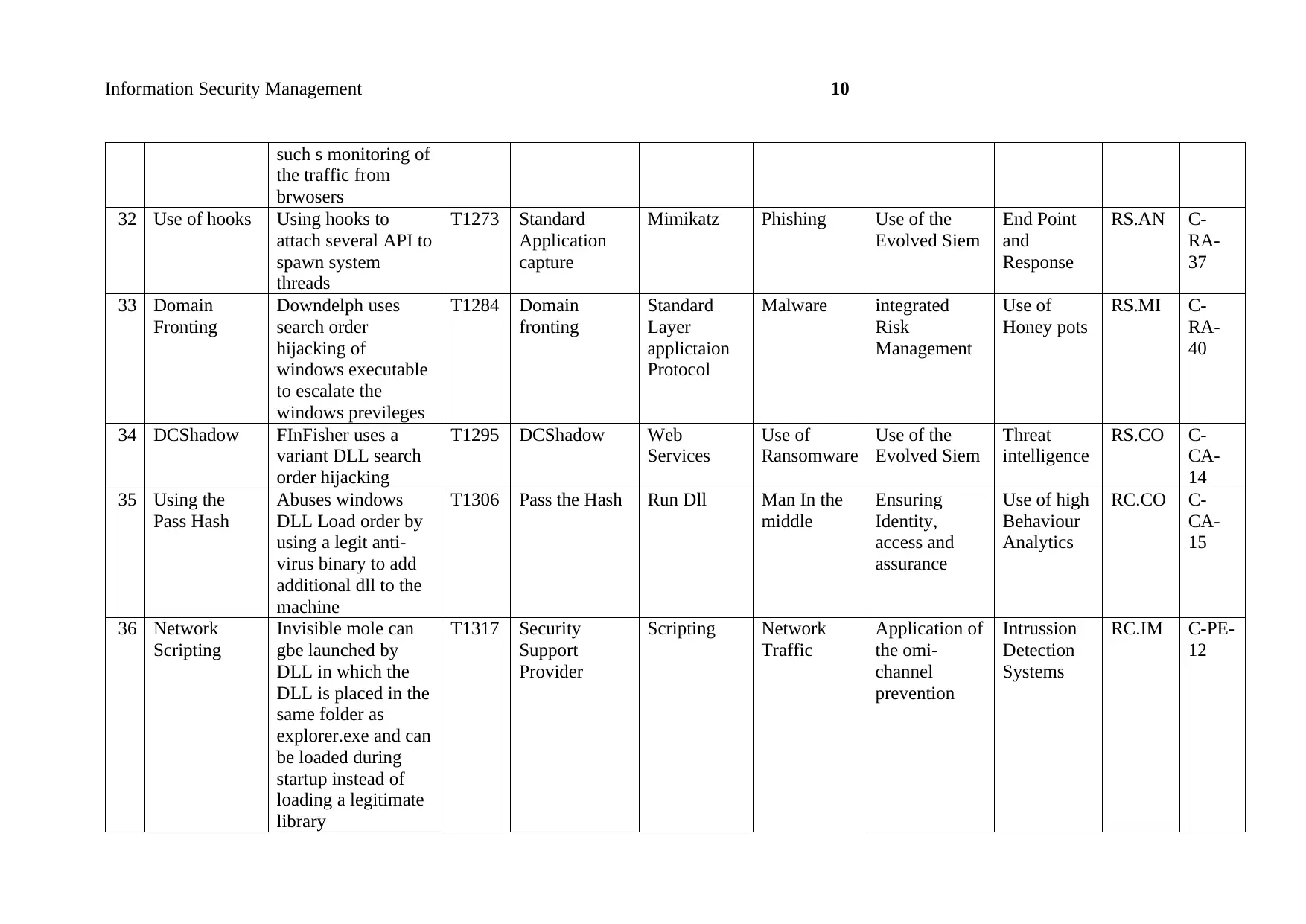
such s monitoring of
the traffic from
brwosers
32 Use of hooks Using hooks to
attach several API to
spawn system
threads
T1273 Standard
Application
capture
Mimikatz Phishing Use of the
Evolved Siem
End Point
and
Response
RS.AN C-
RA-
37
33 Domain
Fronting
Downdelph uses
search order
hijacking of
windows executable
to escalate the
windows previleges
T1284 Domain
fronting
Standard
Layer
applictaion
Protocol
Malware integrated
Risk
Management
Use of
Honey pots
RS.MI C-
RA-
40
34 DCShadow FInFisher uses a
variant DLL search
order hijacking
T1295 DCShadow Web
Services
Use of
Ransomware
Use of the
Evolved Siem
Threat
intelligence
RS.CO C-
CA-
14
35 Using the
Pass Hash
Abuses windows
DLL Load order by
using a legit anti-
virus binary to add
additional dll to the
machine
T1306 Pass the Hash Run Dll Man In the
middle
Ensuring
Identity,
access and
assurance
Use of high
Behaviour
Analytics
RC.CO C-
CA-
15
36 Network
Scripting
Invisible mole can
gbe launched by
DLL in which the
DLL is placed in the
same folder as
explorer.exe and can
be loaded during
startup instead of
loading a legitimate
library
T1317 Security
Support
Provider
Scripting Network
Traffic
Application of
the omi-
channel
prevention
Intrussion
Detection
Systems
RC.IM C-PE-
12
such s monitoring of
the traffic from
brwosers
32 Use of hooks Using hooks to
attach several API to
spawn system
threads
T1273 Standard
Application
capture
Mimikatz Phishing Use of the
Evolved Siem
End Point
and
Response
RS.AN C-
RA-
37
33 Domain
Fronting
Downdelph uses
search order
hijacking of
windows executable
to escalate the
windows previleges
T1284 Domain
fronting
Standard
Layer
applictaion
Protocol
Malware integrated
Risk
Management
Use of
Honey pots
RS.MI C-
RA-
40
34 DCShadow FInFisher uses a
variant DLL search
order hijacking
T1295 DCShadow Web
Services
Use of
Ransomware
Use of the
Evolved Siem
Threat
intelligence
RS.CO C-
CA-
14
35 Using the
Pass Hash
Abuses windows
DLL Load order by
using a legit anti-
virus binary to add
additional dll to the
machine
T1306 Pass the Hash Run Dll Man In the
middle
Ensuring
Identity,
access and
assurance
Use of high
Behaviour
Analytics
RC.CO C-
CA-
15
36 Network
Scripting
Invisible mole can
gbe launched by
DLL in which the
DLL is placed in the
same folder as
explorer.exe and can
be loaded during
startup instead of
loading a legitimate
library
T1317 Security
Support
Provider
Scripting Network
Traffic
Application of
the omi-
channel
prevention
Intrussion
Detection
Systems
RC.IM C-PE-
12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Information Security Management 11
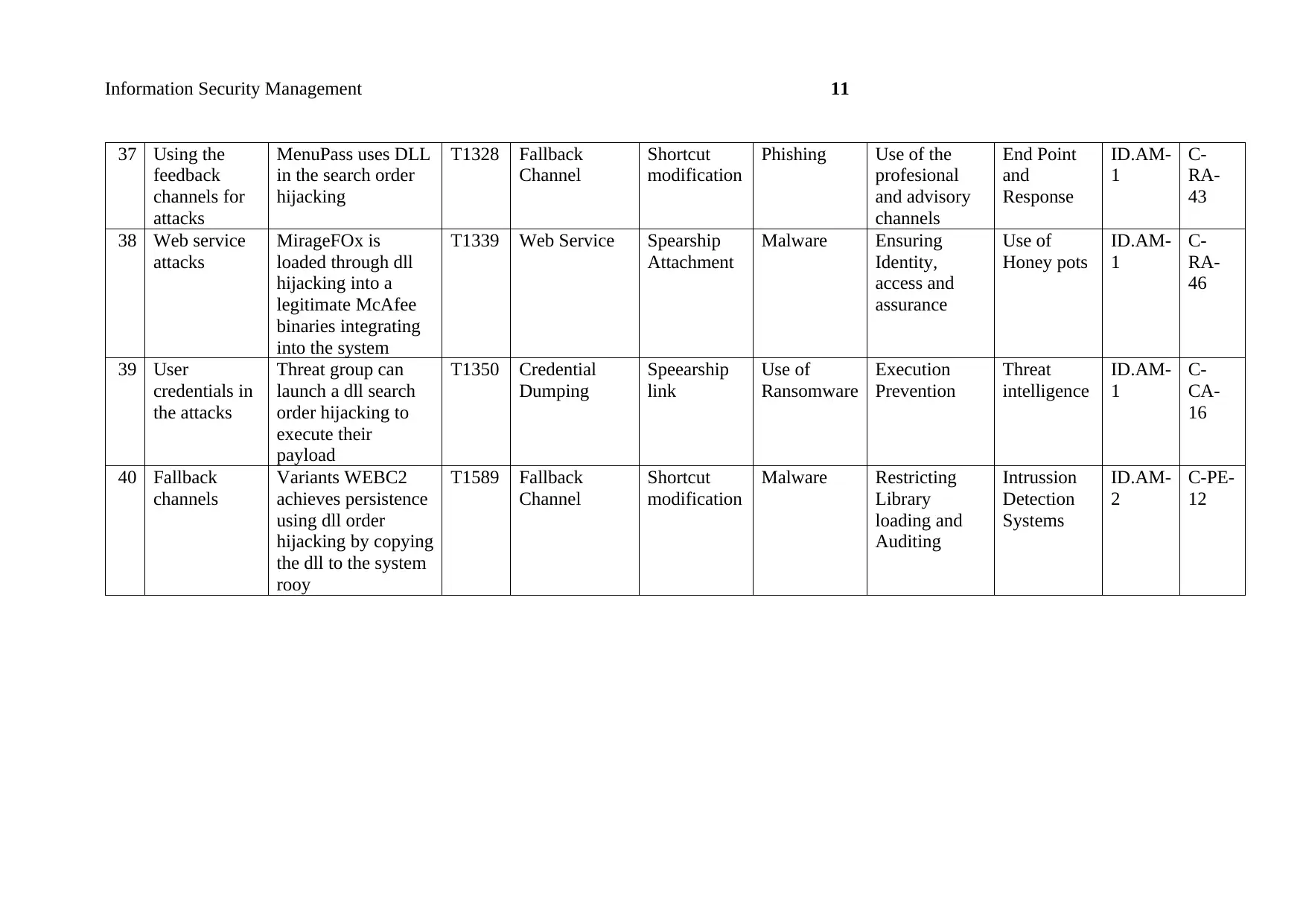
37 Using the
feedback
channels for
attacks
MenuPass uses DLL
in the search order
hijacking
T1328 Fallback
Channel
Shortcut
modification
Phishing Use of the
profesional
and advisory
channels
End Point
and
Response
ID.AM-
1
C-
RA-
43
38 Web service
attacks
MirageFOx is
loaded through dll
hijacking into a
legitimate McAfee
binaries integrating
into the system
T1339 Web Service Spearship
Attachment
Malware Ensuring
Identity,
access and
assurance
Use of
Honey pots
ID.AM-
1
C-
RA-
46
39 User
credentials in
the attacks
Threat group can
launch a dll search
order hijacking to
execute their
payload
T1350 Credential
Dumping
Speearship
link
Use of
Ransomware
Execution
Prevention
Threat
intelligence
ID.AM-
1
C-
CA-
16
40 Fallback
channels
Variants WEBC2
achieves persistence
using dll order
hijacking by copying
the dll to the system
rooy
T1589 Fallback
Channel
Shortcut
modification
Malware Restricting
Library
loading and
Auditing
Intrussion
Detection
Systems
ID.AM-
2
C-PE-
12
37 Using the
feedback
channels for
attacks
MenuPass uses DLL
in the search order
hijacking
T1328 Fallback
Channel
Shortcut
modification
Phishing Use of the
profesional
and advisory
channels
End Point
and
Response
ID.AM-
1
C-
RA-
43
38 Web service
attacks
MirageFOx is
loaded through dll
hijacking into a
legitimate McAfee
binaries integrating
into the system
T1339 Web Service Spearship
Attachment
Malware Ensuring
Identity,
access and
assurance
Use of
Honey pots
ID.AM-
1
C-
RA-
46
39 User
credentials in
the attacks
Threat group can
launch a dll search
order hijacking to
execute their
payload
T1350 Credential
Dumping
Speearship
link
Use of
Ransomware
Execution
Prevention
Threat
intelligence
ID.AM-
1
C-
CA-
16
40 Fallback
channels
Variants WEBC2
achieves persistence
using dll order
hijacking by copying
the dll to the system
rooy
T1589 Fallback
Channel
Shortcut
modification
Malware Restricting
Library
loading and
Auditing
Intrussion
Detection
Systems
ID.AM-
2
C-PE-
12

Running head:Information Security Management 12
Conclusions
Cyber attacks have had several challenges in the digital era as shown by the 40 possible
Cyber threat challenges. It has become more difficult for the security operations to detect and
prioritize and even respond to threats that may affect a computer. The treats listed have far much
extended threats and have introduced the third parties into cloud. Mitigating these threats have also
faced a lack of coordinated resposnse, there are many operational silos that prevent the business
stakeholders from coordinating attacks in their effots to reduce the imopacts of attacks. Therefore
security teams must have advanced threat detection techniques as listed in the Security use case
above, the threat reduction effrts can include Silos and SIEM capabilities that increase system
visibility. The security teams msut also reduce the silos that prevent coordinated response to a
security threat through enabling of the thorough threat assessment and integrating workflows across
the security and risks management teams. The system must also incorporate a risk management
strategy for the cyber risk mitigation with a broad risk identificastions and response.
Conclusions
Cyber attacks have had several challenges in the digital era as shown by the 40 possible
Cyber threat challenges. It has become more difficult for the security operations to detect and
prioritize and even respond to threats that may affect a computer. The treats listed have far much
extended threats and have introduced the third parties into cloud. Mitigating these threats have also
faced a lack of coordinated resposnse, there are many operational silos that prevent the business
stakeholders from coordinating attacks in their effots to reduce the imopacts of attacks. Therefore
security teams must have advanced threat detection techniques as listed in the Security use case
above, the threat reduction effrts can include Silos and SIEM capabilities that increase system
visibility. The security teams msut also reduce the silos that prevent coordinated response to a
security threat through enabling of the thorough threat assessment and integrating workflows across
the security and risks management teams. The system must also incorporate a risk management
strategy for the cyber risk mitigation with a broad risk identificastions and response.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





