Quantum Cryptography: Security Issues and Implementation Report 2017
VerifiedAdded on 2020/04/07
|10
|2078
|41
Report
AI Summary
This report delves into the realm of quantum cryptography, exploring its principles, particularly the uncertainty principle and photon polarization, and its application in securing information through quantum key distribution (QKD). It outlines the working of QKD, including photon transmission and base state selection, highlighting its attributes such as keys confidentiality, authentication, rapid key delivery, and robustness against attacks. The report also examines the implementation of quantum cryptography, including the use of virtual private networks and protocol stacks, while also addressing the issues associated with this technology, such as high implementation costs and signal strength limitations. A key issue discussed is the impact of channel length on the transfer rate. Furthermore, the report analyzes the real-world impact of quantum cryptography, including its ability to enhance security, the speed of encryption, and its role in detecting and mitigating various security threats, such as eavesdropping and denial-of-service attacks. The report concludes by reflecting on the effectiveness of quantum cryptography and its potential to overcome the flaws of traditional security systems, referencing the Bennet brassard protocol.

[Assignment on Information security]
2017
2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Abstract:................................................................................................................................................2
Introduction:..........................................................................................................................................2
Description of quantum cryptography:..................................................................................................2
Working of the Quantum key distribution:............................................................................................3
Attributes of Quantum key distribution:................................................................................................4
1. Keys Confidentiality:..................................................................................................................4
2. Authentication:..........................................................................................................................4
3. Delivery of the rapid key:...........................................................................................................4
4. Robust:......................................................................................................................................5
5. Analysis of the traffic:................................................................................................................5
Implementation of the quantum cryptography:......................................................................................5
Issues associated with the Quantum cryptography:...............................................................................6
Identification of the issue......................................................................................................................7
Impact of Quantum cryptography on Real world:.................................................................................7
Reflection:.............................................................................................................................................8
Conclusion:............................................................................................................................................8
References:............................................................................................................................................8
Abstract:................................................................................................................................................2
Introduction:..........................................................................................................................................2
Description of quantum cryptography:..................................................................................................2
Working of the Quantum key distribution:............................................................................................3
Attributes of Quantum key distribution:................................................................................................4
1. Keys Confidentiality:..................................................................................................................4
2. Authentication:..........................................................................................................................4
3. Delivery of the rapid key:...........................................................................................................4
4. Robust:......................................................................................................................................5
5. Analysis of the traffic:................................................................................................................5
Implementation of the quantum cryptography:......................................................................................5
Issues associated with the Quantum cryptography:...............................................................................6
Identification of the issue......................................................................................................................7
Impact of Quantum cryptography on Real world:.................................................................................7
Reflection:.............................................................................................................................................8
Conclusion:............................................................................................................................................8
References:............................................................................................................................................8

Abstract:
In this paper we are going to reflect the security issues associated with the working of the
quantum cryptography. The quantum cryptographic procedures are used for establishing
quantum communication between the participating units with the use of shared keys. The
issue which is not taken in the consideration is the increase in the length of the channel will
result into decrement in the rate of transfer. The focus should be given on analysing the
effective working of the quantum cryptography.
Introduction:
Quantum cryptography is the methodology which is used for performing cryptographic
procedures used for changing the mechanical properties of the quantum. The quantum key
distribution procedures are used for providing security to the problems associated with the
scenario of key exchange. The most popular approaches used quantum cryptography for
securing information are public key encryption techniques and the use of digital signature
methodology. The cryptographic procedures can be easily completed with the use quantum
cryptography (Clavis, 2009). The quantum cryptographic procedures are used for establishing
quantum communication between the participating units with the use of shared keys. The
quantum key distribution is the common approach which is used for managing quantum key
cryptographic procedure for handling communication between the sender and the receiver.
These cryptographic procedures are used for resolving the issues like eavesdropping, man in
the middle attack, denial of service attack, and others (Dhammeratchi, 2013). This
cryptographic method makes use of physics and mathematics fundamentals for the
development of secured cryptosystem for the distribution of information.
Description of quantum cryptography:
The two principles are followed for the construction of quantum cryptography procedures
which are categorised as principle of uncertainty and polarization of the photon. The principle
of uncertainty is used for identifying the quantum state of the data used for encryptions. The
polarisation of the photon is used for identifying the accumulation of the unknown q-bits
which are used for creating the unknown quantum states (Wijisikera, 2007). The following
diagram is used identifying the mechanics used for deploying the quantum cryptography.
In this paper we are going to reflect the security issues associated with the working of the
quantum cryptography. The quantum cryptographic procedures are used for establishing
quantum communication between the participating units with the use of shared keys. The
issue which is not taken in the consideration is the increase in the length of the channel will
result into decrement in the rate of transfer. The focus should be given on analysing the
effective working of the quantum cryptography.
Introduction:
Quantum cryptography is the methodology which is used for performing cryptographic
procedures used for changing the mechanical properties of the quantum. The quantum key
distribution procedures are used for providing security to the problems associated with the
scenario of key exchange. The most popular approaches used quantum cryptography for
securing information are public key encryption techniques and the use of digital signature
methodology. The cryptographic procedures can be easily completed with the use quantum
cryptography (Clavis, 2009). The quantum cryptographic procedures are used for establishing
quantum communication between the participating units with the use of shared keys. The
quantum key distribution is the common approach which is used for managing quantum key
cryptographic procedure for handling communication between the sender and the receiver.
These cryptographic procedures are used for resolving the issues like eavesdropping, man in
the middle attack, denial of service attack, and others (Dhammeratchi, 2013). This
cryptographic method makes use of physics and mathematics fundamentals for the
development of secured cryptosystem for the distribution of information.
Description of quantum cryptography:
The two principles are followed for the construction of quantum cryptography procedures
which are categorised as principle of uncertainty and polarization of the photon. The principle
of uncertainty is used for identifying the quantum state of the data used for encryptions. The
polarisation of the photon is used for identifying the accumulation of the unknown q-bits
which are used for creating the unknown quantum states (Wijisikera, 2007). The following
diagram is used identifying the mechanics used for deploying the quantum cryptography.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The 0 and 1 bits are used for developing the encryption for the digital signal which is
composed of photons. The quantum cryptography procedures are used for overcoming the
flaws of traditional security system. Bennet brassard protocol is the commonly used protocol
for deploying the quantum key distribution.
Working of the Quantum key distribution:
The photon series is send by the sender to initiate the communication with the
participating units. The selection of the base state is arbitrarily done for the associated
photon. The polarization of the base state is performed at an angle of 45 in any of the
direction i.e. up or down and left or right (Rubya, 2010). The arbitrarily selection of
the actual polarization can be performed in any direction. The incoming photons are
used for detecting the occurrence of polarization at the receiver end. The base state is
used for analysing the state of the photon right or wrong.
The direction of the polarisation does not matter in carrying out public
communication by preserving the base state of the sender and the receiver. The
rejection of photons helps in managing bit sequence for identifying the transmission
of flow of photons with the use of information channel.
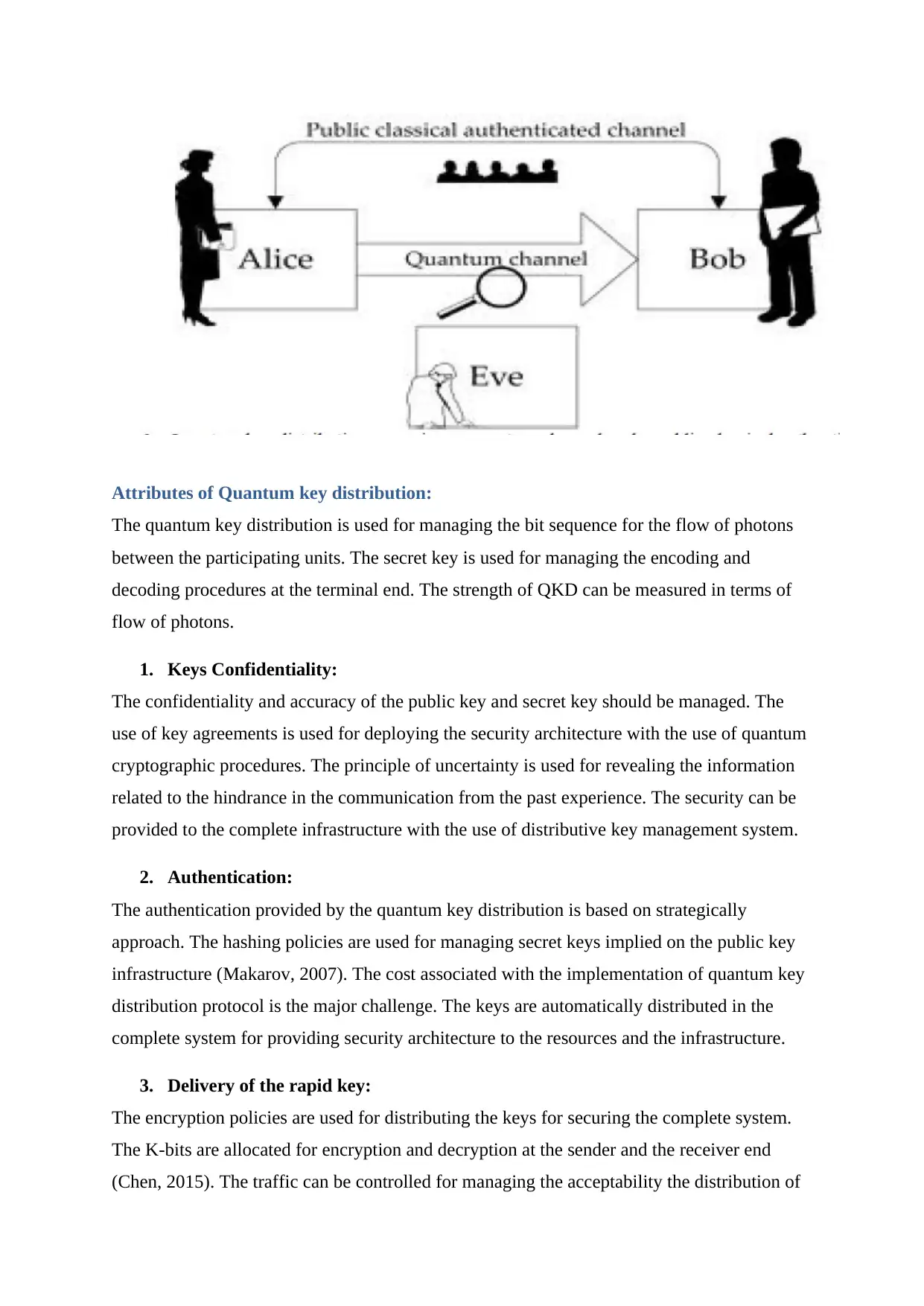
The following diagram shows the sequence of quantum channel between sender and
receiver.
composed of photons. The quantum cryptography procedures are used for overcoming the
flaws of traditional security system. Bennet brassard protocol is the commonly used protocol
for deploying the quantum key distribution.
Working of the Quantum key distribution:
The photon series is send by the sender to initiate the communication with the
participating units. The selection of the base state is arbitrarily done for the associated
photon. The polarization of the base state is performed at an angle of 45 in any of the
direction i.e. up or down and left or right (Rubya, 2010). The arbitrarily selection of
the actual polarization can be performed in any direction. The incoming photons are
used for detecting the occurrence of polarization at the receiver end. The base state is
used for analysing the state of the photon right or wrong.
The direction of the polarisation does not matter in carrying out public
communication by preserving the base state of the sender and the receiver. The
rejection of photons helps in managing bit sequence for identifying the transmission
of flow of photons with the use of information channel.
The following diagram shows the sequence of quantum channel between sender and
receiver.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Attributes of Quantum key distribution:
The quantum key distribution is used for managing the bit sequence for the flow of photons
between the participating units. The secret key is used for managing the encoding and
decoding procedures at the terminal end. The strength of QKD can be measured in terms of
flow of photons.
1. Keys Confidentiality:
The confidentiality and accuracy of the public key and secret key should be managed. The
use of key agreements is used for deploying the security architecture with the use of quantum
cryptographic procedures. The principle of uncertainty is used for revealing the information
related to the hindrance in the communication from the past experience. The security can be
provided to the complete infrastructure with the use of distributive key management system.
2. Authentication:
The authentication provided by the quantum key distribution is based on strategically
approach. The hashing policies are used for managing secret keys implied on the public key
infrastructure (Makarov, 2007). The cost associated with the implementation of quantum key
distribution protocol is the major challenge. The keys are automatically distributed in the
complete system for providing security architecture to the resources and the infrastructure.
3. Delivery of the rapid key:
The encryption policies are used for distributing the keys for securing the complete system.
The K-bits are allocated for encryption and decryption at the sender and the receiver end
(Chen, 2015). The traffic can be controlled for managing the acceptability the distribution of
The quantum key distribution is used for managing the bit sequence for the flow of photons
between the participating units. The secret key is used for managing the encoding and
decoding procedures at the terminal end. The strength of QKD can be measured in terms of
flow of photons.
1. Keys Confidentiality:
The confidentiality and accuracy of the public key and secret key should be managed. The
use of key agreements is used for deploying the security architecture with the use of quantum
cryptographic procedures. The principle of uncertainty is used for revealing the information
related to the hindrance in the communication from the past experience. The security can be
provided to the complete infrastructure with the use of distributive key management system.
2. Authentication:
The authentication provided by the quantum key distribution is based on strategically
approach. The hashing policies are used for managing secret keys implied on the public key
infrastructure (Makarov, 2007). The cost associated with the implementation of quantum key
distribution protocol is the major challenge. The keys are automatically distributed in the
complete system for providing security architecture to the resources and the infrastructure.
3. Delivery of the rapid key:
The encryption policies are used for distributing the keys for securing the complete system.
The K-bits are allocated for encryption and decryption at the sender and the receiver end
(Chen, 2015). The traffic can be controlled for managing the acceptability the distribution of
the quantum key. The advanced encryption procedures are used for developing the secret key
and the supreme key for providing security to the complete infrastructure.
4. Robust:
The implementation of the secured communication with the use of secret key helps in
managing the distribution of the quantum key all over the system (Paterson, 2004). The point
to point technology are used for providing encryption techniques to resolve the issues related
with the eavesdropping attack. The meshed topology is being implemented for the
development of secured infrastructure. The multiple paths are created with the use of mesh
topology for managing the peer to peer link between the terminologies.
5. Analysis of the traffic:
The quantum key distribution protocol is efficient in analysing the flow of traffic between the
participating units. The confidentiality of the data can be maintained by analysing the weak
points of the security architecture.
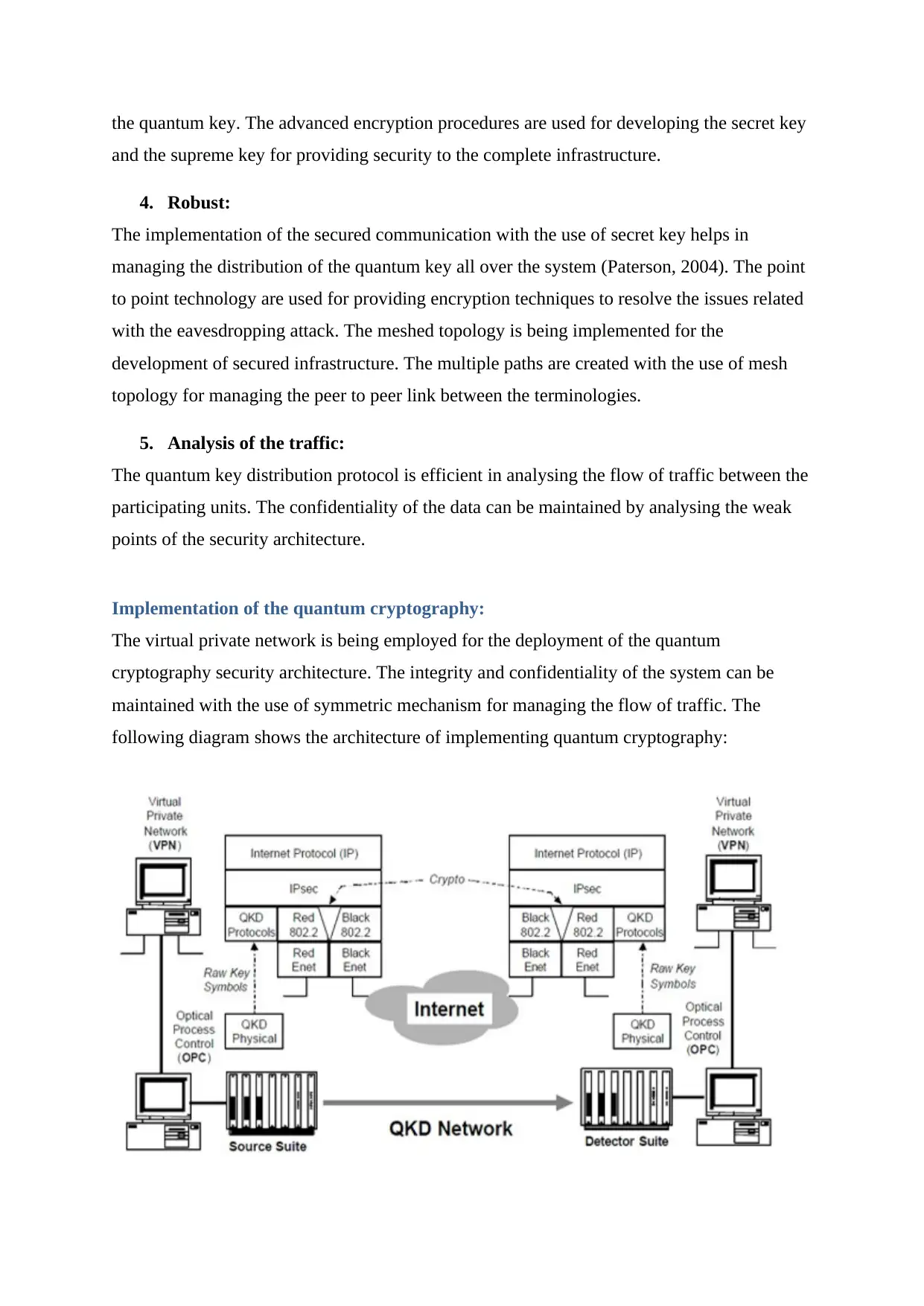
Implementation of the quantum cryptography:
The virtual private network is being employed for the deployment of the quantum
cryptography security architecture. The integrity and confidentiality of the system can be
maintained with the use of symmetric mechanism for managing the flow of traffic. The
following diagram shows the architecture of implementing quantum cryptography:
and the supreme key for providing security to the complete infrastructure.
4. Robust:
The implementation of the secured communication with the use of secret key helps in
managing the distribution of the quantum key all over the system (Paterson, 2004). The point
to point technology are used for providing encryption techniques to resolve the issues related
with the eavesdropping attack. The meshed topology is being implemented for the
development of secured infrastructure. The multiple paths are created with the use of mesh
topology for managing the peer to peer link between the terminologies.
5. Analysis of the traffic:
The quantum key distribution protocol is efficient in analysing the flow of traffic between the
participating units. The confidentiality of the data can be maintained by analysing the weak
points of the security architecture.
Implementation of the quantum cryptography:
The virtual private network is being employed for the deployment of the quantum
cryptography security architecture. The integrity and confidentiality of the system can be
maintained with the use of symmetric mechanism for managing the flow of traffic. The
following diagram shows the architecture of implementing quantum cryptography:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
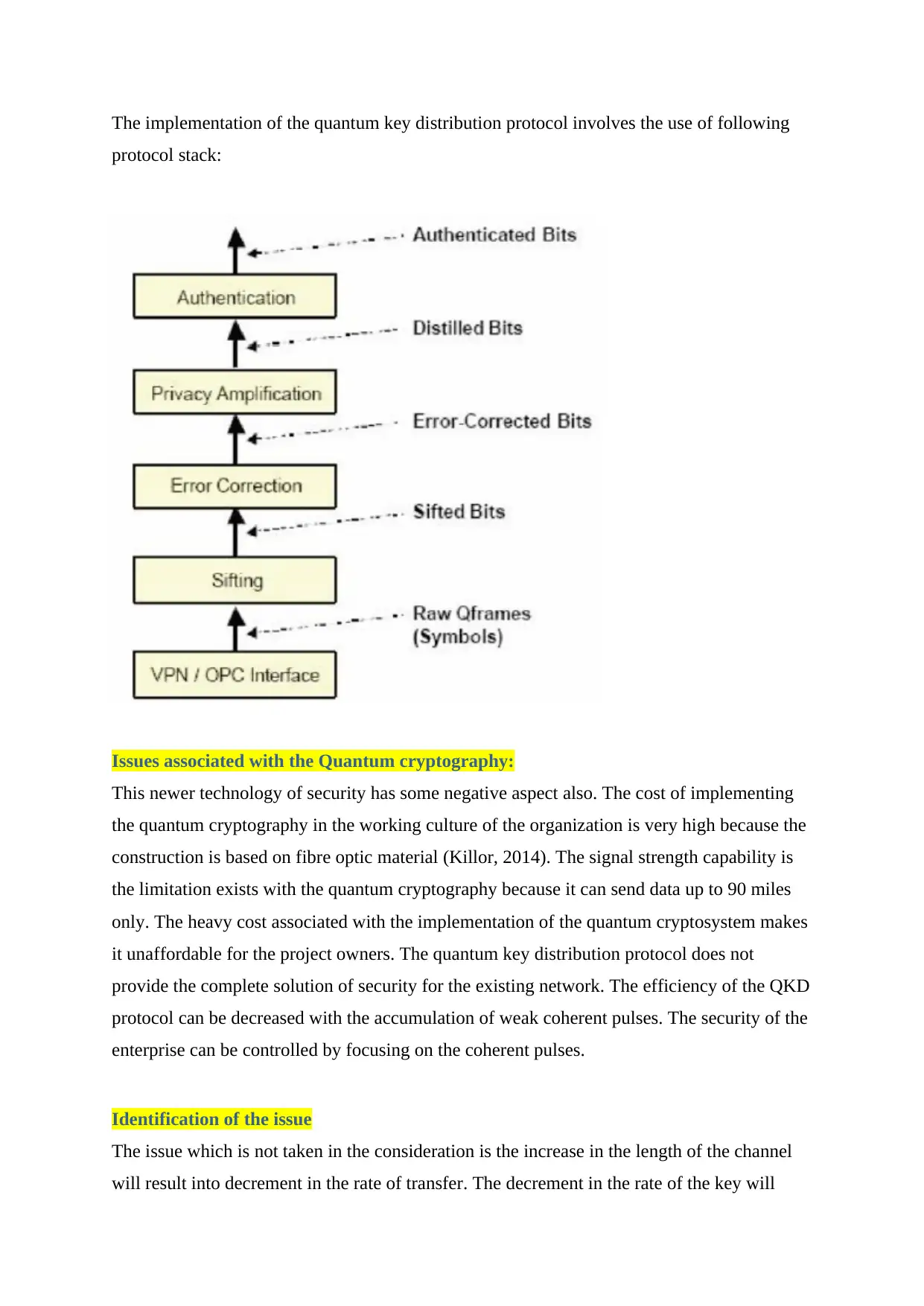
The implementation of the quantum key distribution protocol involves the use of following
protocol stack:
Issues associated with the Quantum cryptography:
This newer technology of security has some negative aspect also. The cost of implementing
the quantum cryptography in the working culture of the organization is very high because the
construction is based on fibre optic material (Killor, 2014). The signal strength capability is
the limitation exists with the quantum cryptography because it can send data up to 90 miles
only. The heavy cost associated with the implementation of the quantum cryptosystem makes
it unaffordable for the project owners. The quantum key distribution protocol does not
provide the complete solution of security for the existing network. The efficiency of the QKD
protocol can be decreased with the accumulation of weak coherent pulses. The security of the
enterprise can be controlled by focusing on the coherent pulses.
Identification of the issue
The issue which is not taken in the consideration is the increase in the length of the channel
will result into decrement in the rate of transfer. The decrement in the rate of the key will
protocol stack:
Issues associated with the Quantum cryptography:
This newer technology of security has some negative aspect also. The cost of implementing
the quantum cryptography in the working culture of the organization is very high because the
construction is based on fibre optic material (Killor, 2014). The signal strength capability is
the limitation exists with the quantum cryptography because it can send data up to 90 miles
only. The heavy cost associated with the implementation of the quantum cryptosystem makes
it unaffordable for the project owners. The quantum key distribution protocol does not
provide the complete solution of security for the existing network. The efficiency of the QKD
protocol can be decreased with the accumulation of weak coherent pulses. The security of the
enterprise can be controlled by focusing on the coherent pulses.
Identification of the issue
The issue which is not taken in the consideration is the increase in the length of the channel
will result into decrement in the rate of transfer. The decrement in the rate of the key will
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

directly affect the registration of the photon. The rate of data transmission can result into the
occurrence of error because the depolarization will takes place in the quantum channel. The
use of QKD protocol is not easy for implementation for the practical situation (Rao, 2013).
The complexity of the security system can be increased with the deployment of quantum
cryptography technique in the working culture of the organization because the employees are
well-versed in using the traditional public key infrastructure for the security purpose.
Impact of Quantum cryptography on Real world:
The high level security is provided to the resources of the enterprise with the implementation
of the quantum cryptography tactics. It is difficult for the hacker to break the quantum
cryptosystem and hack the files of the user. The speed of developing encrypted data is very
high. The photons can be transmitted to the longer distance. It is capable of removing
uncertainty associated with the system to make the system functional without any
complexity. It is easy to implement in the working system of the enterprise for providing
security to the infrastructure and the resources associated with it. The maintainability of the
resources can be easily handled. The eavesdropping, denial of service attack, and Spoofing
attack can be easily detected with the use of this technology. The level of error occurred due
to eavesdropper is detected by comparing it with the quantum error level. The laws of
quantum mechanics are used for setting standards of error for quantum cryptography. The
sifting process is used for analysing the failure occurred in the distribution of K-bits
(Kulkarni, 2012). The interception of dependency of data helps in analysing the facts
associated with the error occurred in the traditional working system. The supreme key is used
for transforming the simple text with the cipher text. The supreme key is developed for
providing encryption to the text for increasing the level of security. The quantum key
distribution protocol is used for providing security to the resources and the infrastructure of
the enterprise. The amplification of the security and privacy procedure can be easily done
with the use of quantum cryptography technique.
Reflection:
From the research, we analysed that the quantum cryptography is the efficient technology in
providing security to the resources and the infrastructure of the enterprise. The mesh topology
and virtual private network are used for the implementation of the quantum cryptosystem.
occurrence of error because the depolarization will takes place in the quantum channel. The
use of QKD protocol is not easy for implementation for the practical situation (Rao, 2013).
The complexity of the security system can be increased with the deployment of quantum
cryptography technique in the working culture of the organization because the employees are
well-versed in using the traditional public key infrastructure for the security purpose.
Impact of Quantum cryptography on Real world:
The high level security is provided to the resources of the enterprise with the implementation
of the quantum cryptography tactics. It is difficult for the hacker to break the quantum
cryptosystem and hack the files of the user. The speed of developing encrypted data is very
high. The photons can be transmitted to the longer distance. It is capable of removing
uncertainty associated with the system to make the system functional without any
complexity. It is easy to implement in the working system of the enterprise for providing
security to the infrastructure and the resources associated with it. The maintainability of the
resources can be easily handled. The eavesdropping, denial of service attack, and Spoofing
attack can be easily detected with the use of this technology. The level of error occurred due
to eavesdropper is detected by comparing it with the quantum error level. The laws of
quantum mechanics are used for setting standards of error for quantum cryptography. The
sifting process is used for analysing the failure occurred in the distribution of K-bits
(Kulkarni, 2012). The interception of dependency of data helps in analysing the facts
associated with the error occurred in the traditional working system. The supreme key is used
for transforming the simple text with the cipher text. The supreme key is developed for
providing encryption to the text for increasing the level of security. The quantum key
distribution protocol is used for providing security to the resources and the infrastructure of
the enterprise. The amplification of the security and privacy procedure can be easily done
with the use of quantum cryptography technique.
Reflection:
From the research, we analysed that the quantum cryptography is the efficient technology in
providing security to the resources and the infrastructure of the enterprise. The mesh topology
and virtual private network are used for the implementation of the quantum cryptosystem.

Conclusion:
The quantum cryptography procedures are used for overcoming the flaws of traditional
security system. Bennet brassard protocol is the commonly used protocol for deploying the
quantum key distribution. It is capable of removing uncertainty associated with the system to
make the system functional without any complexity. he traffic can be controlled for managing
the acceptability the distribution of the quantum key.
References:
Chen, L. (2015). Quantum safe cryptography and security. Retrieved from
http://www.etsi.org/images/files/ETSIWhitePapers/QuantumSafeWhitepaper.pdf
Clavis, J. (2009). Understanding Quantum crpytography. Retrieved from
http://www.idquantique.com/wordpress/wp-content/uploads/clavis2-whitepaper.pdf
Dhammeratchi, D. (2013). Need for quantum cryptography. Retrieved from
http://aircconline.com/ijaia/V6N5/6515ijaia07.pdf
Killor, P. (2014). Quantum cryptography: Realizing next generation information security.
Retrieved from http://ijaiem.org/volume3issue2/IJAIEM-2014-02-28-090.pdf
Kulkarni, D. (2012). Research direction in quantum cryptography and quntum key
distribution. Retrieved from http://www.ijsrp.org/research_paper_jun2012/ijsrp-June-
2012-105.pdf
Makarov, V. (2007). Quantum cryptography and quantum crpytanalysis. Retrieved from
http://www.vad1.com/publications/phd-thesis-makarov-200703-photos300dpi.pdf
Paterson, K. (2004). A quantum cryptography: A practical information security perspective.
Retrieved from https://eprint.iacr.org/2004/156.pdf
Rao, S. (2013). Quantum cryptography. Retrieved from
http://cs.stanford.edu/people/adityaj/QuantumCryptography.pdf
Rubya, T. (2010). A survey on recent security trends using quantum cryptography. Retrieved
from http://citeseerx.ist.psu.edu/viewdoc/download?
doi=10.1.1.301.7040&rep=rep1&type=pdf
The quantum cryptography procedures are used for overcoming the flaws of traditional
security system. Bennet brassard protocol is the commonly used protocol for deploying the
quantum key distribution. It is capable of removing uncertainty associated with the system to
make the system functional without any complexity. he traffic can be controlled for managing
the acceptability the distribution of the quantum key.
References:
Chen, L. (2015). Quantum safe cryptography and security. Retrieved from
http://www.etsi.org/images/files/ETSIWhitePapers/QuantumSafeWhitepaper.pdf
Clavis, J. (2009). Understanding Quantum crpytography. Retrieved from
http://www.idquantique.com/wordpress/wp-content/uploads/clavis2-whitepaper.pdf
Dhammeratchi, D. (2013). Need for quantum cryptography. Retrieved from
http://aircconline.com/ijaia/V6N5/6515ijaia07.pdf
Killor, P. (2014). Quantum cryptography: Realizing next generation information security.
Retrieved from http://ijaiem.org/volume3issue2/IJAIEM-2014-02-28-090.pdf
Kulkarni, D. (2012). Research direction in quantum cryptography and quntum key
distribution. Retrieved from http://www.ijsrp.org/research_paper_jun2012/ijsrp-June-
2012-105.pdf
Makarov, V. (2007). Quantum cryptography and quantum crpytanalysis. Retrieved from
http://www.vad1.com/publications/phd-thesis-makarov-200703-photos300dpi.pdf
Paterson, K. (2004). A quantum cryptography: A practical information security perspective.
Retrieved from https://eprint.iacr.org/2004/156.pdf
Rao, S. (2013). Quantum cryptography. Retrieved from
http://cs.stanford.edu/people/adityaj/QuantumCryptography.pdf
Rubya, T. (2010). A survey on recent security trends using quantum cryptography. Retrieved
from http://citeseerx.ist.psu.edu/viewdoc/download?
doi=10.1.1.301.7040&rep=rep1&type=pdf
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Wijisikera, S. (2007). Quantum cryptography for secure communication. Retrieved from
http://ws680.nist.gov/publication/get_pdf.cfm?pub_id=906716
http://ws680.nist.gov/publication/get_pdf.cfm?pub_id=906716
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





