CP3404 SP1 Report: BYOD, Zero-Day, Diffie-Hellman Analysis
VerifiedAdded on 2022/11/28
|37
|6568
|166
Report
AI Summary
This report addresses key aspects of information security, beginning with an analysis of Bring Your Own Device (BYOD) policies, comparing those of Sydney and Victoria Universities and proposing a model policy. The report then investigates zero-day attacks, their discovery methods, and mitigation strategies, referencing real-world examples like the Stuxnet worm and attacks on the Swift banking network. Finally, the report examines the Diffie-Hellman algorithm, explaining its role in establishing a shared secret key for secure communication over public networks, including its use of elliptic curve cryptography. The report is structured as a scientific paper, including references and addressing critical thinking and problem-solving skills as required by the CP3404 assignment.

Running head: INFORMATION SECURITY
INFORMATION SECURITY
Name of the Student
Name of the University
Author Note
INFORMATION SECURITY
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SECURITY 1
Question 1:
Bring Your Own Device (BYOD) Policy:
The Bring Your Own Device policy is important for organizations and corporation as
it help the corporation control the usage of this mobile device which when left uncontrolled
can be used by attacker to launch malwares and serious data breaches at the corporation if no
formal policy is established (Wilkins, 2014) . It is therefore vital for organization to have
some formal Bring Your Own Device policy in place. This report discuss the Bring Your
Own Device policy of Sydney University and Victoria university focusing on the components
of their individual policy which shall inform the report to formulate a bring your own device
policy for the organisation. The Sydney University deals with a large number of students and
stand who have access to the university network using their own devices. It is therefore vital
for the university to have clear formal policy on the BYOD policy. The policy has the
following components:
Security of the university data on this device was a key component of the policy. In
this component, the university has defined what is considers as sensitive data through their
data classification schemes and use the scheme to define what each entity in the university
domain can access what regardless of their device they using.
The second component to the policy defines what the IT department is mandated to
do. It is clear the university has not completely abandon control of the employees and
students devices. The policy has defined the minimum software recommended for the mobile
devices to have in order to access some of the university critical systems and data. The role of
IT in event of a cyber-security incident is again outlined in the policy document. This
includes active incident response plans and disaster recovery mechanism in case of a cyber-
Question 1:
Bring Your Own Device (BYOD) Policy:
The Bring Your Own Device policy is important for organizations and corporation as
it help the corporation control the usage of this mobile device which when left uncontrolled
can be used by attacker to launch malwares and serious data breaches at the corporation if no
formal policy is established (Wilkins, 2014) . It is therefore vital for organization to have
some formal Bring Your Own Device policy in place. This report discuss the Bring Your
Own Device policy of Sydney University and Victoria university focusing on the components
of their individual policy which shall inform the report to formulate a bring your own device
policy for the organisation. The Sydney University deals with a large number of students and
stand who have access to the university network using their own devices. It is therefore vital
for the university to have clear formal policy on the BYOD policy. The policy has the
following components:
Security of the university data on this device was a key component of the policy. In
this component, the university has defined what is considers as sensitive data through their
data classification schemes and use the scheme to define what each entity in the university
domain can access what regardless of their device they using.
The second component to the policy defines what the IT department is mandated to
do. It is clear the university has not completely abandon control of the employees and
students devices. The policy has defined the minimum software recommended for the mobile
devices to have in order to access some of the university critical systems and data. The role of
IT in event of a cyber-security incident is again outlined in the policy document. This
includes active incident response plans and disaster recovery mechanism in case of a cyber-

2INFORMATION SECURITY
attack on the university’s network that can emancipate from a breach through the mobile
devices usage on the university network.
The third most critical component of the policy outlines the acceptable usage of the
university’s network using the mobile device. This includes the acceptable usage of the
university’s network infrastructure, data and systems. This has been strategically been put in
place to avoid the university being liable in case its resources is used by rogue student’s to
commit a cyber-attack or data breaches on other system which is not uncommon in most of
the universities.
The fourth part of the policy outlines the university due diligence in terms of
providing education and creation of awareness to ensure the students are aware of the dangers
the devices which are not properly controlled can wreak havoc not only to the student’s own
data but also to the university as a whole. The same applies to the staff of the university.
Victoria University, which was the second case study of the report, had more less the
same outline in terms of the key components of the BYOD policy. The university has
included a policy clause on monitoring of the user devices in terms of traffic exchanges
between the user devices and the university systems and application.
The personal cloud used by students and staff is again added to the policy where the
policy has outline to take no liability for the user data in their own personal clouds
From the above case study, the following policy can be adopted by the university to
properly managed the user devices
Policy audience and purpose: This policy addresses all the staff and the students’ personal
devices which includes but not limited to smartphones, tablets and laptops hereinafter
referred to as BYOD
attack on the university’s network that can emancipate from a breach through the mobile
devices usage on the university network.
The third most critical component of the policy outlines the acceptable usage of the
university’s network using the mobile device. This includes the acceptable usage of the
university’s network infrastructure, data and systems. This has been strategically been put in
place to avoid the university being liable in case its resources is used by rogue student’s to
commit a cyber-attack or data breaches on other system which is not uncommon in most of
the universities.
The fourth part of the policy outlines the university due diligence in terms of
providing education and creation of awareness to ensure the students are aware of the dangers
the devices which are not properly controlled can wreak havoc not only to the student’s own
data but also to the university as a whole. The same applies to the staff of the university.
Victoria University, which was the second case study of the report, had more less the
same outline in terms of the key components of the BYOD policy. The university has
included a policy clause on monitoring of the user devices in terms of traffic exchanges
between the user devices and the university systems and application.
The personal cloud used by students and staff is again added to the policy where the
policy has outline to take no liability for the user data in their own personal clouds
From the above case study, the following policy can be adopted by the university to
properly managed the user devices
Policy audience and purpose: This policy addresses all the staff and the students’ personal
devices which includes but not limited to smartphones, tablets and laptops hereinafter
referred to as BYOD
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY
General principle: Ensure the device your own is properly protected to safeguard its data
Policy statements:
Users must set up passwords or passphrases for devices used in the university network
Users must ensure their devices’ software’s are up to date
Users must ensure the university data are backup in some way to ensure recovery in
case of theft
Users must securely delete user and university data when no longer using the devices
Users must configure their devices to be able to remote wipe in case of theft
Users must ensure their devices have up to date antivirus on their devices
Users must always disable wireless and the Bluetooth survives when not in use
Compliance:
Failure to follow the policy can be used against the user when such devices is used to
cause data breached, which has legal implication. This can attract a fine of not less than
$500,000. The user may be subjected to disciplinary hearings, which may lead to dismal from
the university
Question 2
Zero-Day Attacks:
Zero data attacks according to security experts are deemed as the most dangerous
security attacks in the cyber security domain (Zhou & Pezaros, 2019). A survey by (Vishal
Sharma et al., 2017) indicates that nearly a third of corporations have been compromised by
the zero day attacks in the past one year. These attacks are extremely costly as on average $7
million is spent on mitigating such attacks. This reports focused on some highly reported zero
General principle: Ensure the device your own is properly protected to safeguard its data
Policy statements:
Users must set up passwords or passphrases for devices used in the university network
Users must ensure their devices’ software’s are up to date
Users must ensure the university data are backup in some way to ensure recovery in
case of theft
Users must securely delete user and university data when no longer using the devices
Users must configure their devices to be able to remote wipe in case of theft
Users must ensure their devices have up to date antivirus on their devices
Users must always disable wireless and the Bluetooth survives when not in use
Compliance:
Failure to follow the policy can be used against the user when such devices is used to
cause data breached, which has legal implication. This can attract a fine of not less than
$500,000. The user may be subjected to disciplinary hearings, which may lead to dismal from
the university
Question 2
Zero-Day Attacks:
Zero data attacks according to security experts are deemed as the most dangerous
security attacks in the cyber security domain (Zhou & Pezaros, 2019). A survey by (Vishal
Sharma et al., 2017) indicates that nearly a third of corporations have been compromised by
the zero day attacks in the past one year. These attacks are extremely costly as on average $7
million is spent on mitigating such attacks. This reports focused on some highly reported zero
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY
day attacks, how the zero day vulnerabilities are discovered and some mitigation strategies
recommended by the report (Shaer, 2014).
A zero day vulnerability is a security flaw in software that may be known to the
vendor of the but currently has no patch to it hence is risky since cyber criminals can exploit
that vulnerability by writing zero day attack exploits. The terms zero day is used to refer to
the newly learnt vulnerability in software. Since the developers has just learnt about the flaw,
no proper patches or fixes has been developed, making it easily exploited by the attackers
(Pierre et al, 2018).
The zero day vulnerabilities can be discovered by several means. First, security
researcher can use their systems and application to discover the vulnerabilities. The
researchers always try to seal the information on such vulnerability to avoid the bad people
from knowing about it hence giving the developers time to write patches on the vulnerability.
They may even go ahead and inform the developers of such discovered vulnerabilities
(Nakao et al., 2009). Secondly, the developers themselves when doing the rotational patches
onto their systems and applications can discovered a vulnerability, which currently they have
not figured a fix for. This again is less threat to the users as the developers will try to keep the
information a secret and try out some patches to fix the vulnerability. However, if the hackers
use their tools to discover the vulnerability, they normally make such vulnerable public
causing the rush between the developers and hackers (Huang, Siegel, & Madnick, 2018). The
hackers will rush to exploit the vulnerability before it is fixed while the developers are trying
to write patches and fixes for the same security flaws before a potential zero day exploits is
exposed to the users. Such kind of zero day attacks have been reported widely onto the
internet. The mostly publicly exposed was the stunt worm attack. The attackers behind the
stunt worm used up to four zero day’s vulnerabilities in the windows operating system. The
worm was targeted at Siemen’s PLC used by the Iran nuclear program (Radziwill, 2018). The
day attacks, how the zero day vulnerabilities are discovered and some mitigation strategies
recommended by the report (Shaer, 2014).
A zero day vulnerability is a security flaw in software that may be known to the
vendor of the but currently has no patch to it hence is risky since cyber criminals can exploit
that vulnerability by writing zero day attack exploits. The terms zero day is used to refer to
the newly learnt vulnerability in software. Since the developers has just learnt about the flaw,
no proper patches or fixes has been developed, making it easily exploited by the attackers
(Pierre et al, 2018).
The zero day vulnerabilities can be discovered by several means. First, security
researcher can use their systems and application to discover the vulnerabilities. The
researchers always try to seal the information on such vulnerability to avoid the bad people
from knowing about it hence giving the developers time to write patches on the vulnerability.
They may even go ahead and inform the developers of such discovered vulnerabilities
(Nakao et al., 2009). Secondly, the developers themselves when doing the rotational patches
onto their systems and applications can discovered a vulnerability, which currently they have
not figured a fix for. This again is less threat to the users as the developers will try to keep the
information a secret and try out some patches to fix the vulnerability. However, if the hackers
use their tools to discover the vulnerability, they normally make such vulnerable public
causing the rush between the developers and hackers (Huang, Siegel, & Madnick, 2018). The
hackers will rush to exploit the vulnerability before it is fixed while the developers are trying
to write patches and fixes for the same security flaws before a potential zero day exploits is
exposed to the users. Such kind of zero day attacks have been reported widely onto the
internet. The mostly publicly exposed was the stunt worm attack. The attackers behind the
stunt worm used up to four zero day’s vulnerabilities in the windows operating system. The
worm was targeted at Siemen’s PLC used by the Iran nuclear program (Radziwill, 2018). The

5INFORMATION SECURITY
worm exploited the four zero day vulnerabilities in Microsoft to breach the PLC of Siemens
and make them function abnormally thereby not able to enrich Uranium for the Nuclear
program of Iran. This zero day attack spread across the Internet and was discovered by the
Kaspersky antivirus group who made their research public. It took Microsoft up to four years
to fix the zero days making numerous computer system using the Microsoft OS susceptible to
the stunt worm (Kerner, 2015).
The second zero day was attack on the Swift banking network where reportedly
millions of dollar was stolen. This was first reported by central bank of Bangladesh where
attackers taken advantage of zero day in Microsoft windows OS to launch attack from
unpatched end points in the Bangladesh central bank systems as easily got into the swift
network (Wojcik, 2014). This caused loss of millions of dollars due to the failure of the
patching of the systems at the Bangladesh central bank system.
From the literature, it is critical for organization to organized mitigation strategies for
zero day attacks, the report recommends the following strategies. First, the company should
put limits on the type of email attachments that can be sent or received in the network.
Second, install firewall to carefully scan the inbound and outbound traffic through the
organization for any abnormally. Third, that should be well-established disaster recovery
procedure in place in case a zero day exploit materialize.
Question 3:
Diffie-Helman Research:
The diffie helman algorithm is utilized for establishing one secret key which can be
used for the communication that remain secret at the time of exchanging data over the public
network by utilizing the elliptic curve for generating the points as well as for getting the
private key by utilizing the parameters. The diffie-helman key exchange algorithm can solve
worm exploited the four zero day vulnerabilities in Microsoft to breach the PLC of Siemens
and make them function abnormally thereby not able to enrich Uranium for the Nuclear
program of Iran. This zero day attack spread across the Internet and was discovered by the
Kaspersky antivirus group who made their research public. It took Microsoft up to four years
to fix the zero days making numerous computer system using the Microsoft OS susceptible to
the stunt worm (Kerner, 2015).
The second zero day was attack on the Swift banking network where reportedly
millions of dollar was stolen. This was first reported by central bank of Bangladesh where
attackers taken advantage of zero day in Microsoft windows OS to launch attack from
unpatched end points in the Bangladesh central bank systems as easily got into the swift
network (Wojcik, 2014). This caused loss of millions of dollars due to the failure of the
patching of the systems at the Bangladesh central bank system.
From the literature, it is critical for organization to organized mitigation strategies for
zero day attacks, the report recommends the following strategies. First, the company should
put limits on the type of email attachments that can be sent or received in the network.
Second, install firewall to carefully scan the inbound and outbound traffic through the
organization for any abnormally. Third, that should be well-established disaster recovery
procedure in place in case a zero day exploit materialize.
Question 3:
Diffie-Helman Research:
The diffie helman algorithm is utilized for establishing one secret key which can be
used for the communication that remain secret at the time of exchanging data over the public
network by utilizing the elliptic curve for generating the points as well as for getting the
private key by utilizing the parameters. The diffie-helman key exchange algorithm can solve
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SECURITY
the following dilemma. Bob and Alice agree for sharing a secret key to utilize in a symmetric
cipher. However, the only means of their communication is not so secure. Each of the pieces
of the information that are exchanged within them has been countered by their adversary
EVE. How this is possible for Bob and Alice to share the key without informing EVE. For
the first time this appears that, Bob and Alice this is appearing that the issues that are
associated with the discrete logarithm problem for Fp gives a possible solution for the
problem. The protocol is not in any used in exchanging the data in public key encryption but
it is however used in exchanging the cryptographic keys which shall be later be used in
securing the data being exchanges by the parties involved in the communication via the
unsecure channel. This mechanism is particularly useful in case the two parties are using non
secure channel like the Internet to exchange information hence needs a way to ensure even if
the attacker gains access to the traffic, which they can easily sniff, the protocol shall ensure
the attacker will have difficult time figuring out the keys used in the data encryption hence
will not be able to breach the data on transit.
In this protocol, the two parties creates private and public key pairs where the private key is
only known to the party while the public key is published and communicated to the other
parties involved in the communication. The protocol uses the concept of elliptic curves to
ensure the keys i.e. private and public keys are different but mathematically related to each
other in a sense that that the same unique private key can be calculated on both sides of the
communication using the ones private key and the other side’s public key. The complexity of
the algorithm relies on exponential modulo of the prime numbers sets.
The primary step for both Bob and Alice is to agree on huge prime p as well as one non-zero
integer g modulo p. Bob and Alice create the values that are associated with g and p public
knowledge; as example Bob and Alice may post the values on the web sites of them.
the following dilemma. Bob and Alice agree for sharing a secret key to utilize in a symmetric
cipher. However, the only means of their communication is not so secure. Each of the pieces
of the information that are exchanged within them has been countered by their adversary
EVE. How this is possible for Bob and Alice to share the key without informing EVE. For
the first time this appears that, Bob and Alice this is appearing that the issues that are
associated with the discrete logarithm problem for Fp gives a possible solution for the
problem. The protocol is not in any used in exchanging the data in public key encryption but
it is however used in exchanging the cryptographic keys which shall be later be used in
securing the data being exchanges by the parties involved in the communication via the
unsecure channel. This mechanism is particularly useful in case the two parties are using non
secure channel like the Internet to exchange information hence needs a way to ensure even if
the attacker gains access to the traffic, which they can easily sniff, the protocol shall ensure
the attacker will have difficult time figuring out the keys used in the data encryption hence
will not be able to breach the data on transit.
In this protocol, the two parties creates private and public key pairs where the private key is
only known to the party while the public key is published and communicated to the other
parties involved in the communication. The protocol uses the concept of elliptic curves to
ensure the keys i.e. private and public keys are different but mathematically related to each
other in a sense that that the same unique private key can be calculated on both sides of the
communication using the ones private key and the other side’s public key. The complexity of
the algorithm relies on exponential modulo of the prime numbers sets.
The primary step for both Bob and Alice is to agree on huge prime p as well as one non-zero
integer g modulo p. Bob and Alice create the values that are associated with g and p public
knowledge; as example Bob and Alice may post the values on the web sites of them.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
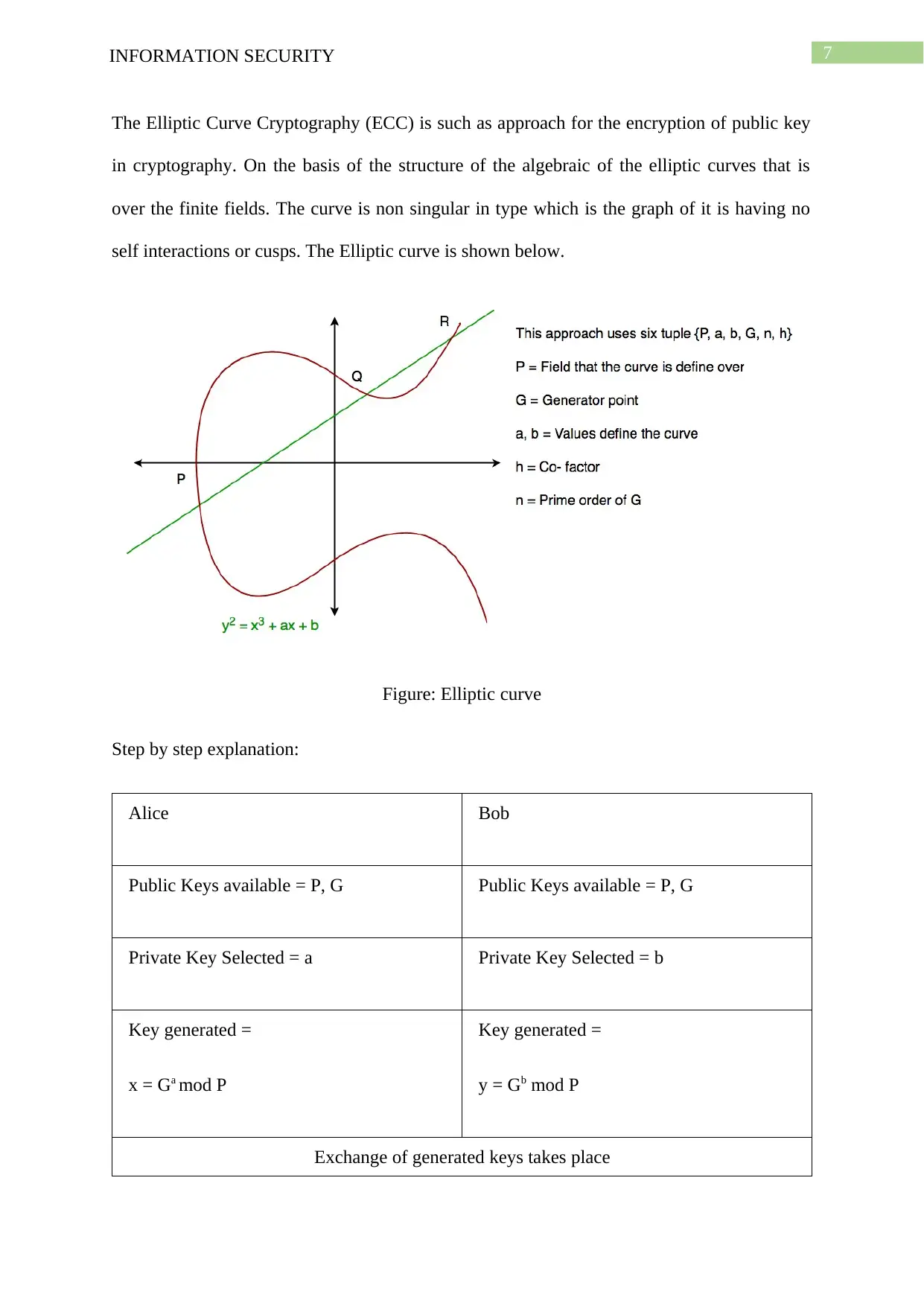
7INFORMATION SECURITY
The Elliptic Curve Cryptography (ECC) is such as approach for the encryption of public key
in cryptography. On the basis of the structure of the algebraic of the elliptic curves that is
over the finite fields. The curve is non singular in type which is the graph of it is having no
self interactions or cusps. The Elliptic curve is shown below.
Figure: Elliptic curve
Step by step explanation:
Alice Bob
Public Keys available = P, G Public Keys available = P, G
Private Key Selected = a Private Key Selected = b
Key generated =
x = Ga mod P
Key generated =
y = Gb mod P
Exchange of generated keys takes place
The Elliptic Curve Cryptography (ECC) is such as approach for the encryption of public key
in cryptography. On the basis of the structure of the algebraic of the elliptic curves that is
over the finite fields. The curve is non singular in type which is the graph of it is having no
self interactions or cusps. The Elliptic curve is shown below.
Figure: Elliptic curve
Step by step explanation:
Alice Bob
Public Keys available = P, G Public Keys available = P, G
Private Key Selected = a Private Key Selected = b
Key generated =
x = Ga mod P
Key generated =
y = Gb mod P
Exchange of generated keys takes place

8INFORMATION SECURITY
Key received = y key received = x
Generated Secret Key =
ka = ya mod P
Generated Secret Key =
kb = xb mod P
Algebraically it can be shown that ka = kb
Users now have a symmetric secret key to encrypt
Example:
Step 1:
Alice and Bob get the public numbers P = 23, G = 9
Step 2: Alice selected a private key a = 4 and
Bob selected a private key b = 3
Step 3: Alice & Bob compute public values
Alice: x =(9^4 mod 23) = (6561 mod 23) = 6
Bob: y = (9^3 mod 23) = (729 mod 23) = 16
Step 4: Alice & Bob exchange public numbers
Step 5: Alice receives public key y =16 and
Bob receives public key x = 6
Key received = y key received = x
Generated Secret Key =
ka = ya mod P
Generated Secret Key =
kb = xb mod P
Algebraically it can be shown that ka = kb
Users now have a symmetric secret key to encrypt
Example:
Step 1:
Alice and Bob get the public numbers P = 23, G = 9
Step 2: Alice selected a private key a = 4 and
Bob selected a private key b = 3
Step 3: Alice & Bob compute public values
Alice: x =(9^4 mod 23) = (6561 mod 23) = 6
Bob: y = (9^3 mod 23) = (729 mod 23) = 16
Step 4: Alice & Bob exchange public numbers
Step 5: Alice receives public key y =16 and
Bob receives public key x = 6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION SECURITY
Step 6: The symmetric keys are computed by Bob and Alice
Alice: ka = y^a mod p = 65536 mod 23 = 9
Bob: kb = x^b mod p = 216 mod 23 = 9
Step 7: The secret key is 9
Question 4:
The term HTTPS is an abbreviation for hypertext exchange convention secure. The
abbreviation goes before the URL in a site address. Barely any individuals know about its
importance. The HTTPS is just about a precise of the ordinary hypertext exchange
convention, this variant of this is distinctive in light of the fact that the "S" toward the end
recognizes this as it is having a protected HTTP association. A HTTPS association is utilized
every now and again in organizations where touchy data, for example, government disability
numbers and Mastercard numbers that have been passed with the purpose of procurement
destinations or the payment of bills locales. The hypertext exchange convention secure gives
confirmation that programmers are not ready to block the message that contain touchy
information as it heads towards the server. To comprehend the HTTPS convention,
comprehend that HTTPS is certainly not a different convention from HTTP. It is just a safe
variety. Sending messages by means of a scrambled Secure Sockets Layer (SSL) or Transport
Layer Security (TLS) association gives clients a sensible measure of assurance from meddlers
and go-between assaults that have the ability to siphon significant data or access specific
servers that are private.
It is a down to earth path for individuals who are new to the risks of programmers and
different issues to know which are utilizing a protected informing framework. It is likewise
every now and again suggested, even on site pages, that individuals who don't see HTTPS
toward the start of the URL in the location bar ought not to enter any delicate data, not
Step 6: The symmetric keys are computed by Bob and Alice
Alice: ka = y^a mod p = 65536 mod 23 = 9
Bob: kb = x^b mod p = 216 mod 23 = 9
Step 7: The secret key is 9
Question 4:
The term HTTPS is an abbreviation for hypertext exchange convention secure. The
abbreviation goes before the URL in a site address. Barely any individuals know about its
importance. The HTTPS is just about a precise of the ordinary hypertext exchange
convention, this variant of this is distinctive in light of the fact that the "S" toward the end
recognizes this as it is having a protected HTTP association. A HTTPS association is utilized
every now and again in organizations where touchy data, for example, government disability
numbers and Mastercard numbers that have been passed with the purpose of procurement
destinations or the payment of bills locales. The hypertext exchange convention secure gives
confirmation that programmers are not ready to block the message that contain touchy
information as it heads towards the server. To comprehend the HTTPS convention,
comprehend that HTTPS is certainly not a different convention from HTTP. It is just a safe
variety. Sending messages by means of a scrambled Secure Sockets Layer (SSL) or Transport
Layer Security (TLS) association gives clients a sensible measure of assurance from meddlers
and go-between assaults that have the ability to siphon significant data or access specific
servers that are private.
It is a down to earth path for individuals who are new to the risks of programmers and
different issues to know which are utilizing a protected informing framework. It is likewise
every now and again suggested, even on site pages, that individuals who don't see HTTPS
toward the start of the URL in the location bar ought not to enter any delicate data, not
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INFORMATION SECURITY
exclusively to ensure the guest to the site, however to secure the site's notoriety for being
admirably.
HTTP: No Data Encryption Implemented
Each URL interface that starts with HTTP utilizes a fundamental sort of "hypertext exchange
convention". Made by Tim Berners-Lee back in the mid 1990's, the point at which the web
was still in the early stages, this system convention standard is the thing that permits internet
servers and the browsers to impart through the trading of information.
HTTPS: Encrypted Connections
HTTPS is not something contrary to HTTP; however, it is more youthful cousin. The two are
the equivalent, in that the two allude to the equivalent "hypertext exchange convention" that
empowers mentioned web information to be exhibited on the screen. However, HTTPS is still
marginally unique, further developed, and significantly more secure. It is a down to earth
path for individuals who are new to the risks of programmers and different issues to know
which are utilizing a protected informing framework. It is likewise every now and again
suggested, even on site pages, that individuals who don't see HTTPS toward the start of the
URL in the location bar ought not to enter any delicate data, not exclusively to ensure the
guest to the site, however to secure the site's notoriety for being admirably. HTTPS
convention is an augmentation of HTTP. That "S" in the shortened form originates from the
word Secure and it is controlled by Transport Layer Security (TLS) [the successor to Secure
Sockets Layer (SSL)], the security that is standard innovation that builds up an encoded
association between a program and web server.
The Advantages and Disadvantages of HTTPS
As talked about above, HTTPS guarantees digital wellbeing. It is, undoubtedly, a superior
system convention arrangement than its more established cousin, HTTP.
exclusively to ensure the guest to the site, however to secure the site's notoriety for being
admirably.
HTTP: No Data Encryption Implemented
Each URL interface that starts with HTTP utilizes a fundamental sort of "hypertext exchange
convention". Made by Tim Berners-Lee back in the mid 1990's, the point at which the web
was still in the early stages, this system convention standard is the thing that permits internet
servers and the browsers to impart through the trading of information.
HTTPS: Encrypted Connections
HTTPS is not something contrary to HTTP; however, it is more youthful cousin. The two are
the equivalent, in that the two allude to the equivalent "hypertext exchange convention" that
empowers mentioned web information to be exhibited on the screen. However, HTTPS is still
marginally unique, further developed, and significantly more secure. It is a down to earth
path for individuals who are new to the risks of programmers and different issues to know
which are utilizing a protected informing framework. It is likewise every now and again
suggested, even on site pages, that individuals who don't see HTTPS toward the start of the
URL in the location bar ought not to enter any delicate data, not exclusively to ensure the
guest to the site, however to secure the site's notoriety for being admirably. HTTPS
convention is an augmentation of HTTP. That "S" in the shortened form originates from the
word Secure and it is controlled by Transport Layer Security (TLS) [the successor to Secure
Sockets Layer (SSL)], the security that is standard innovation that builds up an encoded
association between a program and web server.
The Advantages and Disadvantages of HTTPS
As talked about above, HTTPS guarantees digital wellbeing. It is, undoubtedly, a superior
system convention arrangement than its more established cousin, HTTP.

11INFORMATION SECURITY
Nevertheless, is HTTPS about the focal points? Maybe there is a disadvantage to everything?
We should discover.
The Advantages of Using HTTPS
The security related benefits referenced above - validating the server, encoding information
transmission, and shielding the trades from altering - are the undeniable fundamental
favourable circumstances to utilizing HTTPS. Site administrators need and need to ensure
their guests information (HTTPS is really a prerequisite for any destinations gathering
instalment data as per the PCI Data Security Standard) and site guests need to realize that
their information is being transmitted safely.
The developing interest for information protection as well as the security that is from the
overall population is another bit of leeway to utilizing HTTPS. Truth be told, agreeing to
Make the Websites, 13% of entire truck surrender is because of instalment concerns of the
security. Site guests need to realize that they are able to confide in your site, particularly in
the event that they have been entering budgetary subtleties, and utilizing HTTPS is one of the
approaches to do that (for example it's single direction to demonstrate your guests that any
data that is entered by them will be scrambled).
Question 5:
Task 1:
Cipher text:
ij ticvs ij rat zgzra fthrxcs e.f. rat jwicrihj tjrievgjatm rat zgcjr jsjrtb qz bgvgrics
fcswrqnciwas. fcswrqnciwas gh grj ticvs sticj ctjtbevtm ltcs bxfa jtfctr dcgrghn. rat dtvv
uhqdh fitjic fgwatc, dagfa dij xjtm rq thfcswr bgvgrics qcmtcj, gj ih tkibwvt qz ragj
nthtcirgqh. gh ragj jsjrtb faicifrtcj dtct rcihjzqcbtm xjghn i ltcs jgbwvt jxejrgrxrgqh.
Nevertheless, is HTTPS about the focal points? Maybe there is a disadvantage to everything?
We should discover.
The Advantages of Using HTTPS
The security related benefits referenced above - validating the server, encoding information
transmission, and shielding the trades from altering - are the undeniable fundamental
favourable circumstances to utilizing HTTPS. Site administrators need and need to ensure
their guests information (HTTPS is really a prerequisite for any destinations gathering
instalment data as per the PCI Data Security Standard) and site guests need to realize that
their information is being transmitted safely.
The developing interest for information protection as well as the security that is from the
overall population is another bit of leeway to utilizing HTTPS. Truth be told, agreeing to
Make the Websites, 13% of entire truck surrender is because of instalment concerns of the
security. Site guests need to realize that they are able to confide in your site, particularly in
the event that they have been entering budgetary subtleties, and utilizing HTTPS is one of the
approaches to do that (for example it's single direction to demonstrate your guests that any
data that is entered by them will be scrambled).
Question 5:
Task 1:
Cipher text:
ij ticvs ij rat zgzra fthrxcs e.f. rat jwicrihj tjrievgjatm rat zgcjr jsjrtb qz bgvgrics
fcswrqnciwas. fcswrqnciwas gh grj ticvs sticj ctjtbevtm ltcs bxfa jtfctr dcgrghn. rat dtvv
uhqdh fitjic fgwatc, dagfa dij xjtm rq thfcswr bgvgrics qcmtcj, gj ih tkibwvt qz ragj
nthtcirgqh. gh ragj jsjrtb faicifrtcj dtct rcihjzqcbtm xjghn i ltcs jgbwvt jxejrgrxrgqh.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 37
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





