Analysis of Information Systems and Security at Lambton College
VerifiedAdded on 2020/04/13
|5
|320
|58
Report
AI Summary
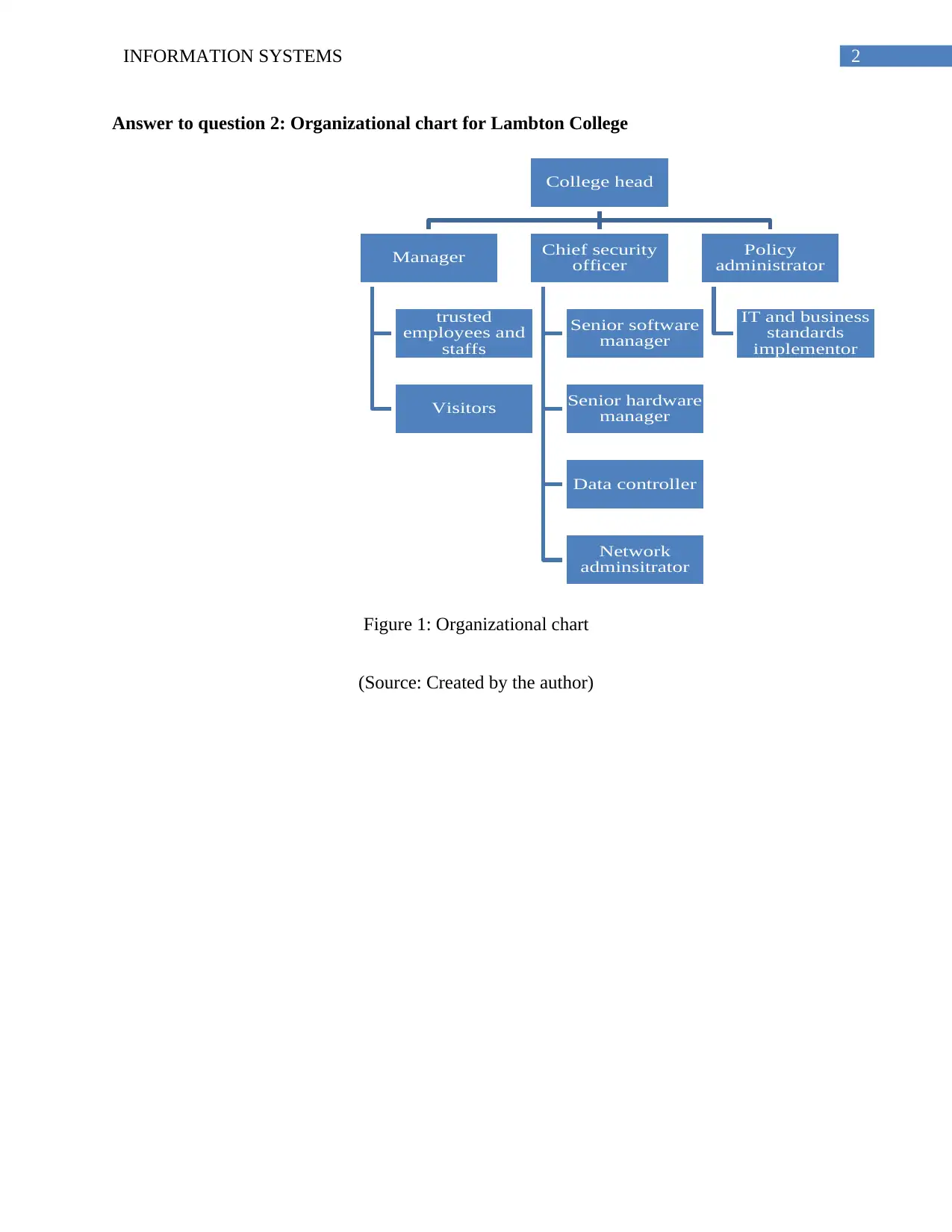
This report examines the information systems at Lambton College, focusing on its organizational structure and security measures. The report begins by identifying the college's flat organizational structure and explains its components, including employees, procedures, data, software, and hardware. It also includes an organizational chart illustrating the college's structure. Furthermore, the report discusses the importance of information security and includes references to relevant academic sources such as Ashkenas et al. (2015), Laudon & Laudon (2015), and Peppard & Ward (2016). The report also includes a section on designing an information security awareness poster.
1 out of 5










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)