CO4512 Information Security: Cloud Architecture Risk Assessment Report
VerifiedAdded on 2023/06/12
|15
|3032
|114
Report
AI Summary
This report presents a comprehensive risk assessment of a cloud architecture, adhering to ISO 27001 standards for information security management. It identifies primary and secondary assets within the architecture, such as cloud storage, virtual servers, firewalls, and intranet, and analyzes potential threats and vulnerabilities associated with each. The assessment utilizes the Boston grid method to compute risk levels and includes specific CVE numbers for identified vulnerabilities. The report highlights the importance of robust security measures, regular updates, and adherence to international security standards to protect customer data and maintain system integrity. Addressing legal constraints and ensuring customer confidence through certified security practices are also emphasized. The analysis provides a structured approach to understanding and mitigating risks in cloud environments, contributing to enhanced security and operational resilience.

Running head: CLOUD ARCHITECTURE RISK ASSESSMENT
CLOUD ARCHITECTURE RISK ASSESSMENT
Name of the student:
Name of the university:
Author note:
CLOUD ARCHITECTURE RISK ASSESSMENT
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CLOUD ARCHITECTURE RISK ASSESSMENT
Executive summary:
The cloud architecture constitutes of several primary as well secondary assets which are used to
create the overall architecture. The asset brings security related threats for the network as well for the
cloud system. The security concerns are related to security of the network, security of data and overall
security of the system.
In order to conduct the security assessment of the ISO 27001 model is recommended. There
are a variety of benefits that makes the ISO 27001 standards appropriate for the risk assessment for the
proposed architectural model. The advantages include more improvement in security measures,
standardized security report, identifications of the flaws regarding the cloud system. The security
assessment provided by the ISO standard ensures that the report is independent and at the same time
unbiased and it increases the dependability of the evaluation.
The act of dealing with customers’ data not only challenging but also brings different legal
constraints. These type of legal constrains has the ability to affect the business course at various levels.
In order To ensure that the legal issues are avoided while working with customer data, certified security
hallmark is preferred to be associated with the security system. The major benefit of having the
international standard for the security system is that it directly contributes to the confidence of the
customer as it make them assured that the data they are providing to the organizations is completely
secured as it ensures global security best practices and hence the chance of data thefts and illegal data
access. . Moreover there is no need for the organizations to conduct lengthy and costly onsite security
audits
Executive summary:
The cloud architecture constitutes of several primary as well secondary assets which are used to
create the overall architecture. The asset brings security related threats for the network as well for the
cloud system. The security concerns are related to security of the network, security of data and overall
security of the system.
In order to conduct the security assessment of the ISO 27001 model is recommended. There
are a variety of benefits that makes the ISO 27001 standards appropriate for the risk assessment for the
proposed architectural model. The advantages include more improvement in security measures,
standardized security report, identifications of the flaws regarding the cloud system. The security
assessment provided by the ISO standard ensures that the report is independent and at the same time
unbiased and it increases the dependability of the evaluation.
The act of dealing with customers’ data not only challenging but also brings different legal
constraints. These type of legal constrains has the ability to affect the business course at various levels.
In order To ensure that the legal issues are avoided while working with customer data, certified security
hallmark is preferred to be associated with the security system. The major benefit of having the
international standard for the security system is that it directly contributes to the confidence of the
customer as it make them assured that the data they are providing to the organizations is completely
secured as it ensures global security best practices and hence the chance of data thefts and illegal data
access. . Moreover there is no need for the organizations to conduct lengthy and costly onsite security
audits

2CLOUD ARCHITECTURE RISK ASSESSMENT
Table of Contents
Executive summary:....................................................................................................................................1
Introduction:...............................................................................................................................................3
Risk Assessment:.........................................................................................................................................4
Owner specification:...............................................................................................................................4
Type of assets:.........................................................................................................................................5
Threats for each asset:............................................................................................................................6
Threats with cloud storage:................................................................................................................6
Threats with virtual servers:...............................................................................................................6
Threats with firewall:..........................................................................................................................6
Threats with the intranet:...................................................................................................................6
Threats with web and mail servers:....................................................................................................7
Threats with the firmware and the admin and user pc:......................................................................7
Vulnerabilities for each asset:.................................................................................................................8
Level computation, using Boston gird:..................................................................................................10
Impact table specification:....................................................................................................................11
Risk identification with the risk level, using Boston grid:......................................................................12
Reference:.................................................................................................................................................13
Table of Contents
Executive summary:....................................................................................................................................1
Introduction:...............................................................................................................................................3
Risk Assessment:.........................................................................................................................................4
Owner specification:...............................................................................................................................4
Type of assets:.........................................................................................................................................5
Threats for each asset:............................................................................................................................6
Threats with cloud storage:................................................................................................................6
Threats with virtual servers:...............................................................................................................6
Threats with firewall:..........................................................................................................................6
Threats with the intranet:...................................................................................................................6
Threats with web and mail servers:....................................................................................................7
Threats with the firmware and the admin and user pc:......................................................................7
Vulnerabilities for each asset:.................................................................................................................8
Level computation, using Boston gird:..................................................................................................10
Impact table specification:....................................................................................................................11
Risk identification with the risk level, using Boston grid:......................................................................12
Reference:.................................................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CLOUD ARCHITECTURE RISK ASSESSMENT
Introduction:
Risk evaluation for cloud architecture proposed in this context will be prepared with ISO 27001
standards. It provides a standard methodology that is useful for analyzing the factors that are security
related. There are various advantages associated with the ISO 27001 like improvement in security
procedures, security report, identifications of flaws in the cloud system and standard safety measure for
the architecture (Alebrahim et al. 2015).
The standard enables approach in a systematic way that helps examining the information security
system risk and it is also effective to find out the associated threats with the system. Vulnerabilities and
impact that threat poses on the system is unique depending on the organizational context. However the
assessment helps in finding out the (Kurnianto, Isnanto and Widodo 2018).
The analysis provides solution that is most appropriate for addressing the security needs that the
organization requires to increase the strength of the security. It also provides the security assessment on a
continuous basis to keep the organization updated about security measures with a thorough review of thee
strength and weakness of the security of the existing architecture (Hoy and Foley 2015).
The report of assessment first provides information about the specifications of owner which
includes the software and hardware specifications that had been used to design the cloud system. The
threats that are related to every asset have been discussed in the report. The Vulnerabilities that are to the
assets are described along with the official CVE number. The Boston grid-method, which is useful for
computing the risk level associated with each asset has been included in the report. A specification table
which contains the risk level associated with each of the assets has also been provided
Introduction:
Risk evaluation for cloud architecture proposed in this context will be prepared with ISO 27001
standards. It provides a standard methodology that is useful for analyzing the factors that are security
related. There are various advantages associated with the ISO 27001 like improvement in security
procedures, security report, identifications of flaws in the cloud system and standard safety measure for
the architecture (Alebrahim et al. 2015).
The standard enables approach in a systematic way that helps examining the information security
system risk and it is also effective to find out the associated threats with the system. Vulnerabilities and
impact that threat poses on the system is unique depending on the organizational context. However the
assessment helps in finding out the (Kurnianto, Isnanto and Widodo 2018).
The analysis provides solution that is most appropriate for addressing the security needs that the
organization requires to increase the strength of the security. It also provides the security assessment on a
continuous basis to keep the organization updated about security measures with a thorough review of thee
strength and weakness of the security of the existing architecture (Hoy and Foley 2015).
The report of assessment first provides information about the specifications of owner which
includes the software and hardware specifications that had been used to design the cloud system. The
threats that are related to every asset have been discussed in the report. The Vulnerabilities that are to the
assets are described along with the official CVE number. The Boston grid-method, which is useful for
computing the risk level associated with each asset has been included in the report. A specification table
which contains the risk level associated with each of the assets has also been provided
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4CLOUD ARCHITECTURE RISK ASSESSMENT
Risk Assessment:
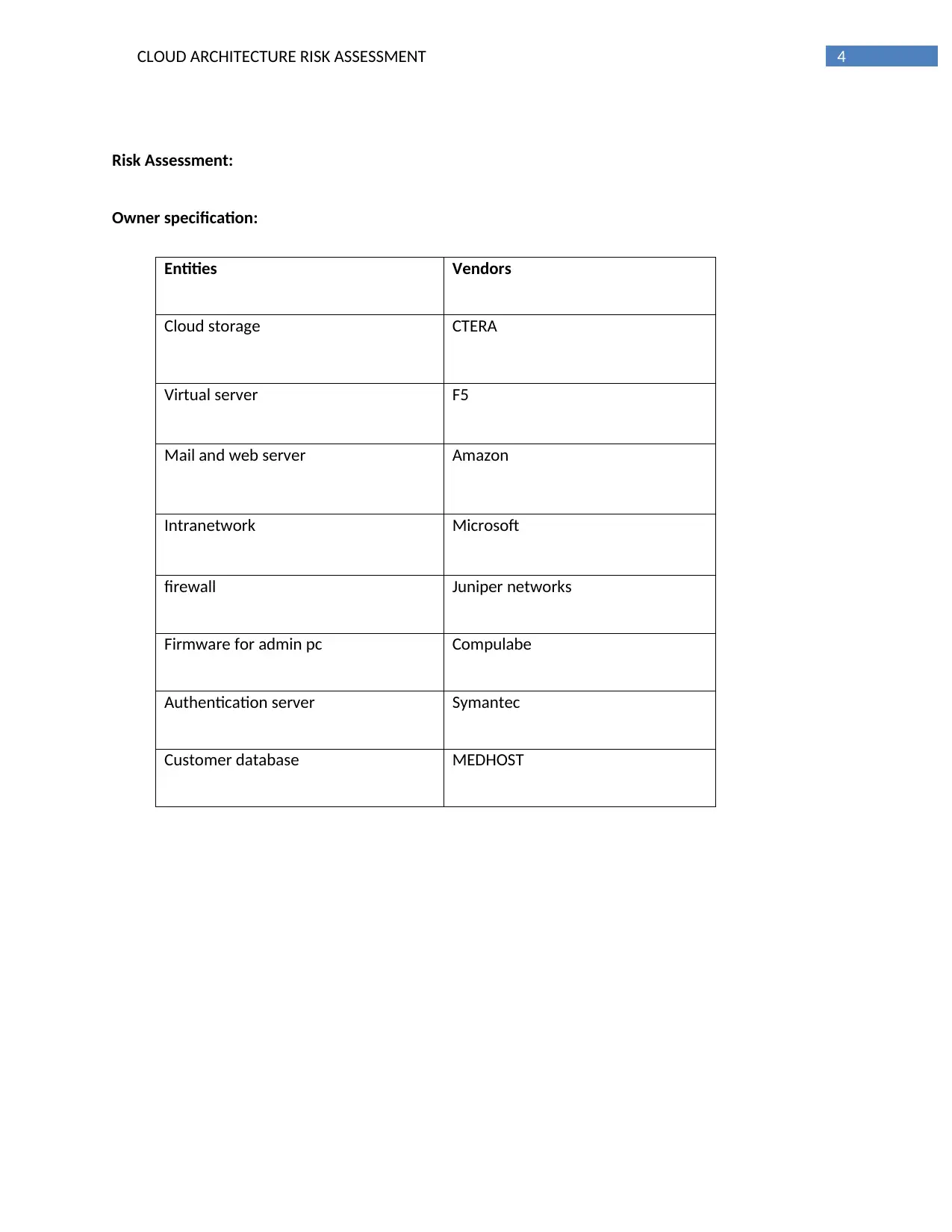
Owner specification:
Entities Vendors
Cloud storage CTERA
Virtual server F5
Mail and web server Amazon
Intranetwork Microsoft
firewall Juniper networks
Firmware for admin pc Compulabe
Authentication server Symantec
Customer database MEDHOST
Risk Assessment:
Owner specification:
Entities Vendors
Cloud storage CTERA
Virtual server F5
Mail and web server Amazon
Intranetwork Microsoft
firewall Juniper networks
Firmware for admin pc Compulabe
Authentication server Symantec
Customer database MEDHOST

5CLOUD ARCHITECTURE RISK ASSESSMENT
Type of assets:
The assets that are primary, belong to the assets that form the basis for incorporating all other
assets to the system architecture. The assets which depend on the primary assets for implementation
are the secondary assets (Puiler, Martinez and Hill 2015).
In order to enable the implementation of the cloud architecture there is requirement for both
hardware and software . However it is the software that has to be brought into action before the
hardware can be implemented for supporting the cloud architecture. Hence software should be
considered as the primary assets and associated hardware should be regarded as secondary asset.
Primary assets are as described as the following:
Cloud storage system
Virtual servers
Firewall
Firmware
Intranet
Internet
Web and email server
The secondary assets are described as the following:
Admin pc
Human resource pc
User pc
Threats for each asset:
Type of assets:
The assets that are primary, belong to the assets that form the basis for incorporating all other
assets to the system architecture. The assets which depend on the primary assets for implementation
are the secondary assets (Puiler, Martinez and Hill 2015).
In order to enable the implementation of the cloud architecture there is requirement for both
hardware and software . However it is the software that has to be brought into action before the
hardware can be implemented for supporting the cloud architecture. Hence software should be
considered as the primary assets and associated hardware should be regarded as secondary asset.
Primary assets are as described as the following:
Cloud storage system
Virtual servers
Firewall
Firmware
Intranet
Internet
Web and email server
The secondary assets are described as the following:
Admin pc
Human resource pc
User pc
Threats for each asset:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CLOUD ARCHITECTURE RISK ASSESSMENT
Threats with cloud storage:
Third party service provider provides the cloud storage and the storage is accessed remotely by
the users. .hence, it is impossible for the users to be in charge of the storage (Almorsy, Grundy and
Muller 2016).
The options that are used by the users are not totally foolproof and the flaws in the login
techniques are identifiable by the experts. Although the security strength depends on the quality of the
service provider, but the majority of the service providers out there accepts that the systems are not
fully secured (Almorsy, Grundy and Muller 2016).
Threats with virtual servers:
Virtual server requires strong knowledge regarding administrations process. In case
administrator does not have high level of understanding about the servers, the server has to deal with
security issues due to server access by the unauthorized access.
Virtual servers need to updating with security patches in regular basis, in another case there is a
chance that the server becomes less secure and it becomes easily hackable for lack of security (Jokar,
Arianpoo and Leung 2016).
Threats with firewall:
Firewall protects the internal network from the external threats like malicious attacks which are
carried out with the help of the external internet. However, it is not appropriate for defending the
network from the threats that is due to the flaws in the internal security.
In case external communication like receiving emails from the outside sources is allowed by the
system, it is not possible for the firewall to prevent the communication by analyzing the flaws and
nature of the communication (Singh, Jeong and Park 2016).
Threats with the intranet:
Intranet is deployed to enable internal communication that is in the institute. Due to this,
employees have a felling that the communication is highly secured and it is not possible to access the
network from outside. Hence the employees often end up creating weak password for their profiles
hosted on the internal network. This is one of the major reasons making the network a bit less
secured(Wang, Wei and Vangury 2014).
The access to the network is given to peoples associated with the organizations get access to
network easily. However if the network is not accessed and managed properly, there might be security
threats.
Threats with web and mail servers:
In order to secure the web and mail servers that belong to the network, firewall is used.
However it is not one stop solution to protect the web and mail servers from as it too has limitations.
Threats with cloud storage:
Third party service provider provides the cloud storage and the storage is accessed remotely by
the users. .hence, it is impossible for the users to be in charge of the storage (Almorsy, Grundy and
Muller 2016).
The options that are used by the users are not totally foolproof and the flaws in the login
techniques are identifiable by the experts. Although the security strength depends on the quality of the
service provider, but the majority of the service providers out there accepts that the systems are not
fully secured (Almorsy, Grundy and Muller 2016).
Threats with virtual servers:
Virtual server requires strong knowledge regarding administrations process. In case
administrator does not have high level of understanding about the servers, the server has to deal with
security issues due to server access by the unauthorized access.
Virtual servers need to updating with security patches in regular basis, in another case there is a
chance that the server becomes less secure and it becomes easily hackable for lack of security (Jokar,
Arianpoo and Leung 2016).
Threats with firewall:
Firewall protects the internal network from the external threats like malicious attacks which are
carried out with the help of the external internet. However, it is not appropriate for defending the
network from the threats that is due to the flaws in the internal security.
In case external communication like receiving emails from the outside sources is allowed by the
system, it is not possible for the firewall to prevent the communication by analyzing the flaws and
nature of the communication (Singh, Jeong and Park 2016).
Threats with the intranet:
Intranet is deployed to enable internal communication that is in the institute. Due to this,
employees have a felling that the communication is highly secured and it is not possible to access the
network from outside. Hence the employees often end up creating weak password for their profiles
hosted on the internal network. This is one of the major reasons making the network a bit less
secured(Wang, Wei and Vangury 2014).
The access to the network is given to peoples associated with the organizations get access to
network easily. However if the network is not accessed and managed properly, there might be security
threats.
Threats with web and mail servers:
In order to secure the web and mail servers that belong to the network, firewall is used.
However it is not one stop solution to protect the web and mail servers from as it too has limitations.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CLOUD ARCHITECTURE RISK ASSESSMENT
Hackers are always looking for these flaws and once identified it is too easy to break the network
security and get unauthorized access and important data being stolen (Wang, Wei and Vangury 2014).
Threats with the firmware and the admin and user pc:
Firmware does not include the signed cryptography. Without the encryption, the firmware is
easily hackable. It is possible for the hackers to gain access to the internal hardware by breaking the
security of the firmware as it contains information about the hardware as well as the data that the
hardware contains (Singh, Jeong and Park 2016) .
The admin pc and the user pc contains the firmware, thus it is responsible for the security
threats to the overall network.
Hackers are always looking for these flaws and once identified it is too easy to break the network
security and get unauthorized access and important data being stolen (Wang, Wei and Vangury 2014).
Threats with the firmware and the admin and user pc:
Firmware does not include the signed cryptography. Without the encryption, the firmware is
easily hackable. It is possible for the hackers to gain access to the internal hardware by breaking the
security of the firmware as it contains information about the hardware as well as the data that the
hardware contains (Singh, Jeong and Park 2016) .
The admin pc and the user pc contains the firmware, thus it is responsible for the security
threats to the overall network.

8CLOUD ARCHITECTURE RISK ASSESSMENT
Vulnerabilities for each asset:
CVE-2013-2639
Vulnerability was discovered in the CTERA cloud storage. The vulnerability is associated with the
Cross-site scripting (XSS). The scripting enables remote attackers in injecting arbitrary web script. The
script hackers inject HTML through the description that is stored in the project folder (Cvedetails.com
2018).
CVE-2016-9245
The vulnerability is associated with the F5 BIG-IP systems, the platform that is used for Virtual
servers. The attackers make malicious request through some HTTP profile that restarts the TMM. This
Vulnerability relates to all the BIG-IP APM profiles. The issue also extends to the BIG-IP LTM policies.
This Vulnerability makes it possible to disrupt the traffic for making disruption in the BIG-IP system
(Cve.mitre.org 2018).
CVE-2008-6096
This vulnerability is associated with the Juniper NetScreen ScreenOS which helps to design the
DMZ network that is used for cloud architecture. With cross-site scripting, remote attackers successfully
inject web script that is completely arbitrary. The script also includes features like injecting HTML via
user name parameters which is basically used for web interface associated with user login page
(Cve.mitre.org 2018).
CVE-2017-6062
The "OpenID Connect Relying Party and OAuth 2.0 Resource Server" is used for the HTTP
authentication server uphold by Apache software foundation. This makes the attackers in bypassing the
authentication request made through the HTTP traffic (Cve.mitre.org 2018).
CVE-2017-11693
The vulnerability is identified with MEDHOST; a system that manages documents helps to create
the customer database deployed in cloud infrastructure. The system makes use of the hard-coded
credentials that enables access request to the database. It is possible for the unauthorized users to
access the database. With the knowledge of the credentials it is possible for the hackers to make direct
communication with the database which helps to access and modify the data without the user concerns.
The Account name is dms and the password is hard-coded which is same throughout the applications.
The customer does not have the flexibility to change the password either. The dms account is connected
with the PostgreSQL enables access to the database DMS (Cve.mitre.org 2018).
Vulnerabilities for each asset:
CVE-2013-2639
Vulnerability was discovered in the CTERA cloud storage. The vulnerability is associated with the
Cross-site scripting (XSS). The scripting enables remote attackers in injecting arbitrary web script. The
script hackers inject HTML through the description that is stored in the project folder (Cvedetails.com
2018).
CVE-2016-9245
The vulnerability is associated with the F5 BIG-IP systems, the platform that is used for Virtual
servers. The attackers make malicious request through some HTTP profile that restarts the TMM. This
Vulnerability relates to all the BIG-IP APM profiles. The issue also extends to the BIG-IP LTM policies.
This Vulnerability makes it possible to disrupt the traffic for making disruption in the BIG-IP system
(Cve.mitre.org 2018).
CVE-2008-6096
This vulnerability is associated with the Juniper NetScreen ScreenOS which helps to design the
DMZ network that is used for cloud architecture. With cross-site scripting, remote attackers successfully
inject web script that is completely arbitrary. The script also includes features like injecting HTML via
user name parameters which is basically used for web interface associated with user login page
(Cve.mitre.org 2018).
CVE-2017-6062
The "OpenID Connect Relying Party and OAuth 2.0 Resource Server" is used for the HTTP
authentication server uphold by Apache software foundation. This makes the attackers in bypassing the
authentication request made through the HTTP traffic (Cve.mitre.org 2018).
CVE-2017-11693
The vulnerability is identified with MEDHOST; a system that manages documents helps to create
the customer database deployed in cloud infrastructure. The system makes use of the hard-coded
credentials that enables access request to the database. It is possible for the unauthorized users to
access the database. With the knowledge of the credentials it is possible for the hackers to make direct
communication with the database which helps to access and modify the data without the user concerns.
The Account name is dms and the password is hard-coded which is same throughout the applications.
The customer does not have the flexibility to change the password either. The dms account is connected
with the PostgreSQL enables access to the database DMS (Cve.mitre.org 2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CLOUD ARCHITECTURE RISK ASSESSMENT
CVE-2017-9457
The vulnerability deals with the admin pc. The firmware is from Compulabe. The primary issue
that is associated with the firmware and is the absence signature checking for providing updates to the
firmware. anyone who has access to the computer during the system flash , can easily make
modification in the firmware setting and for doing the modification user needs the Phoenix “UEFI
update program”. It is not need any dedicated effort for obtaining the Phoenix utility program. The
Windows or the DOS version of the program provides free download and it is easily available online.
The utility program helps to install the rootkit at the firmware level, which might corrupt the entire
computer system which leads to the denial of the service and the service is not accessible even with the
admin profile (Cve.mitre.org 2018).
CVE-2017-8514
The vulnerability is associated with intranetwork used for the connections within the network
with internal devices. The intra network considered for the architecture is Microsoft SharePoint. The
issue associated with SharePoint is that security is not strong enough for protecting the network. Hence
the privacy of the data is compromised and due to this the data may be accessible to the users who are
not authorized to access the data Once the hackers are successful in gaining entrance to the network, it
is possible for them to use the identity of the victims for performing action on behalf of the user. The
actions range from changing security setting, deleting content to theft of important information like
browser cookies and it is also possible for the hackers to inject malevolent codes in the browser of the
user (Cve.mitre.org 2018).
CVE-2017-9450
The susceptibility is relevant to the Amazon Web Services that provide mail and web service.
Amazon Web Services or AWS, the bootstrap tools package called CloudFormation, enables users to
execute codes in arbitrary fashion with root access. It permits the hacker to create local files in the
directory that are not system specific (Cve.mitre.org 2018).
CVE-2017-9457
The vulnerability deals with the admin pc. The firmware is from Compulabe. The primary issue
that is associated with the firmware and is the absence signature checking for providing updates to the
firmware. anyone who has access to the computer during the system flash , can easily make
modification in the firmware setting and for doing the modification user needs the Phoenix “UEFI
update program”. It is not need any dedicated effort for obtaining the Phoenix utility program. The
Windows or the DOS version of the program provides free download and it is easily available online.
The utility program helps to install the rootkit at the firmware level, which might corrupt the entire
computer system which leads to the denial of the service and the service is not accessible even with the
admin profile (Cve.mitre.org 2018).
CVE-2017-8514
The vulnerability is associated with intranetwork used for the connections within the network
with internal devices. The intra network considered for the architecture is Microsoft SharePoint. The
issue associated with SharePoint is that security is not strong enough for protecting the network. Hence
the privacy of the data is compromised and due to this the data may be accessible to the users who are
not authorized to access the data Once the hackers are successful in gaining entrance to the network, it
is possible for them to use the identity of the victims for performing action on behalf of the user. The
actions range from changing security setting, deleting content to theft of important information like
browser cookies and it is also possible for the hackers to inject malevolent codes in the browser of the
user (Cve.mitre.org 2018).
CVE-2017-9450
The susceptibility is relevant to the Amazon Web Services that provide mail and web service.
Amazon Web Services or AWS, the bootstrap tools package called CloudFormation, enables users to
execute codes in arbitrary fashion with root access. It permits the hacker to create local files in the
directory that are not system specific (Cve.mitre.org 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10CLOUD ARCHITECTURE RISK ASSESSMENT
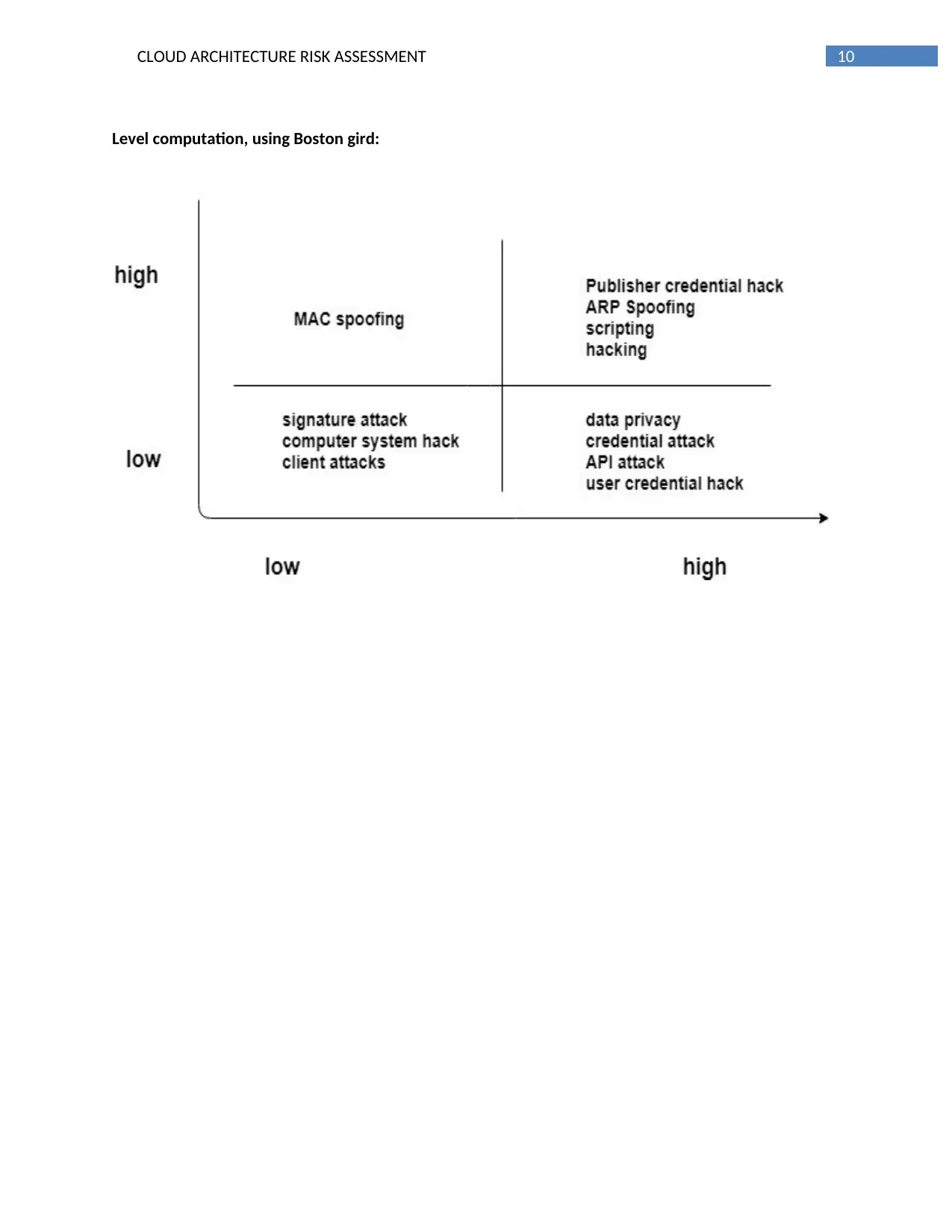
Level computation, using Boston gird:
Level computation, using Boston gird:
11CLOUD ARCHITECTURE RISK ASSESSMENT
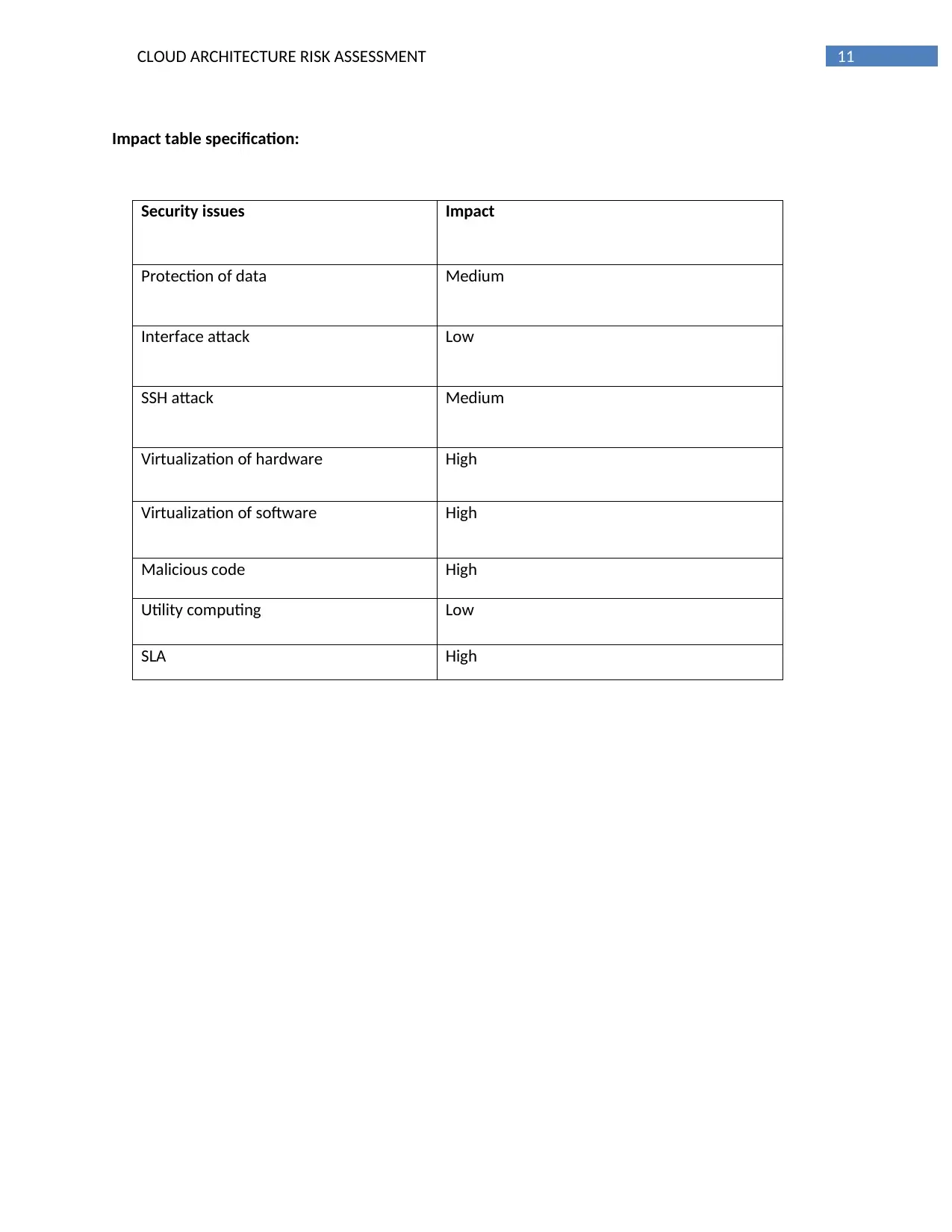
Impact table specification:
Security issues Impact
Protection of data Medium
Interface attack Low
SSH attack Medium
Virtualization of hardware High
Virtualization of software High
Malicious code High
Utility computing Low
SLA High
Impact table specification:
Security issues Impact
Protection of data Medium
Interface attack Low
SSH attack Medium
Virtualization of hardware High
Virtualization of software High
Malicious code High
Utility computing Low
SLA High
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




