Information Security Risk Management Case Study: Vic. Gov.
VerifiedAdded on 2020/03/07
|14
|3276
|39
Case Study
AI Summary
This case study examines information security risk management within the Victorian State Government. It begins with a diagram illustrating security risks, concerns, and the Protective Security Policy Framework. The study then delves into the identification of internal and external risks, categorizing threats as deliberate or accidental. A comparative analysis of these threat types is provided, followed by a ranking of threats based on their severity (high, medium, medium-low, and low). The study justifies these rankings and explores the challenges faced by the Victorian government in deciding on risk management strategies, including data insecurity, the current state of government systems, and information respectability. The case study also differentiates between risk and uncertainty, and discusses various approaches for risk control and mitigation. The document references the Privacy and Data Protection Act 2014, the Victorian Protective Data Security Framework, and related concepts like public sector data and protective data security, culminating in a discussion of the Information Privacy Principle.

Running head: INFORMATION SECURITY RISK MANAGEMENT
Information Security Risk Management: A Case Study of
Victorian State Government
Student Name:
University Name:
Information Security Risk Management: A Case Study of
Victorian State Government
Student Name:
University Name:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY RISK MANAGEMENT
Table of Contents
1. Diagram for illustrating Victorian State Government security risks and concerns and
the Protective security policy framework........................................................................................2
2. Detailed explanation of the diagram................................................................................2
2.1 Identification of risks according to area of exposure.................................................3
3. Comparative analysis of the Deliberate and Accidental Threats.....................................4
3.1 Ranking of threats in order of importance.................................................................5
3.2 Justification of the rankings.......................................................................................6
4. Challenges faced by Victorian state government in deciding Risk management............7
5. Difference between Risk and Uncertainty.......................................................................8
6. Different approaches for risk control and mitigation in Victorian State Government....9
Privacy and data Protection Act 2014...........................................................................10
Victorian Protective Data Security Framework.............................................................10
Public Sector Data.........................................................................................................10
Protective Data Security................................................................................................10
Information Privacy Principle........................................................................................11
References..........................................................................................................................12
Table of Contents
1. Diagram for illustrating Victorian State Government security risks and concerns and
the Protective security policy framework........................................................................................2
2. Detailed explanation of the diagram................................................................................2
2.1 Identification of risks according to area of exposure.................................................3
3. Comparative analysis of the Deliberate and Accidental Threats.....................................4
3.1 Ranking of threats in order of importance.................................................................5
3.2 Justification of the rankings.......................................................................................6
4. Challenges faced by Victorian state government in deciding Risk management............7
5. Difference between Risk and Uncertainty.......................................................................8
6. Different approaches for risk control and mitigation in Victorian State Government....9
Privacy and data Protection Act 2014...........................................................................10
Victorian Protective Data Security Framework.............................................................10
Public Sector Data.........................................................................................................10
Protective Data Security................................................................................................10
Information Privacy Principle........................................................................................11
References..........................................................................................................................12

2INFORMATION SECURITY RISK MANAGEMENT
1. Diagram for illustrating Victorian State Government security risks and
concerns and the Protective security policy framework
Figure 1: Victorian State Government security risks and concerns and the Protective
security policy framework
Source: (created by Author)
2. Detailed explanation of the diagram
The diagram provides the details about the details about the security and the risk that are
involved with the Information Security Risk Management System that is adopted by the
Victorian government. The diagram explains the different type of risks and also categories the
risk according the effect of the risk and their outcomes on the organization. The diagram also
provides the information about the Victorian Protective data Security Framework. This
framework comes under the Protective Security Policy Framework. Additionally the diagram
1. Diagram for illustrating Victorian State Government security risks and
concerns and the Protective security policy framework
Figure 1: Victorian State Government security risks and concerns and the Protective
security policy framework
Source: (created by Author)
2. Detailed explanation of the diagram
The diagram provides the details about the details about the security and the risk that are
involved with the Information Security Risk Management System that is adopted by the
Victorian government. The diagram explains the different type of risks and also categories the
risk according the effect of the risk and their outcomes on the organization. The diagram also
provides the information about the Victorian Protective data Security Framework. This
framework comes under the Protective Security Policy Framework. Additionally the diagram
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY RISK MANAGEMENT
also provides the information about the internal and the external risks. In addition to this the
threats that were identified can also be categorized into deliberate threats and accidental threats.
The report is concerned with the analysis of the threats that were faced by the government and
also the different type of threat analysis and the risk mitigation techniques that can be
implemented by the Victorian government for their safety. The entire procedure has been
displayed efficiently in the diagram that is provided in this report. Additionally, there has been
some information about the information security risk and the different parts of the information
security risks. They can occur by various types of sources. Theft is one of the main reasons that
give rise to the Information security risks. In addition to this, the Malware Infection and
Eavesdropping also affects the security of the information system and hampers them. The
Victorian government has adopted the Victorian Protective data Security Framework, that would
help them to mitigate the risk obtain optimum resolution for the risks. The frame is the
Information Security Risk Management system for the government. This framework follows the
ISO/IEC 27002:2013 (Code of practice for information security controls). The framework is
based upon the risk assessment technique. The risk assessment technique involves the processes
of risk identification, risk evaluation, risk analysis and Documentation of the risk assessment
techniques.
2.1 Identification of risks according to area of exposure
Area of Exposure Internal Risks External Risks
Deliberate Accidental Deliberate Accidental
High Fire
Sabotage
Failure of
the
outsourced
operations
Malicious
destruction
of the data
and the files.
Masquerade
Unauthorize
d Dial-In
Access
Programmin
g or coding
errors
also provides the information about the internal and the external risks. In addition to this the
threats that were identified can also be categorized into deliberate threats and accidental threats.
The report is concerned with the analysis of the threats that were faced by the government and
also the different type of threat analysis and the risk mitigation techniques that can be
implemented by the Victorian government for their safety. The entire procedure has been
displayed efficiently in the diagram that is provided in this report. Additionally, there has been
some information about the information security risk and the different parts of the information
security risks. They can occur by various types of sources. Theft is one of the main reasons that
give rise to the Information security risks. In addition to this, the Malware Infection and
Eavesdropping also affects the security of the information system and hampers them. The
Victorian government has adopted the Victorian Protective data Security Framework, that would
help them to mitigate the risk obtain optimum resolution for the risks. The frame is the
Information Security Risk Management system for the government. This framework follows the
ISO/IEC 27002:2013 (Code of practice for information security controls). The framework is
based upon the risk assessment technique. The risk assessment technique involves the processes
of risk identification, risk evaluation, risk analysis and Documentation of the risk assessment
techniques.
2.1 Identification of risks according to area of exposure
Area of Exposure Internal Risks External Risks
Deliberate Accidental Deliberate Accidental
High Fire
Sabotage
Failure of
the
outsourced
operations
Malicious
destruction
of the data
and the files.
Masquerade
Unauthorize
d Dial-In
Access
Programmin
g or coding
errors
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
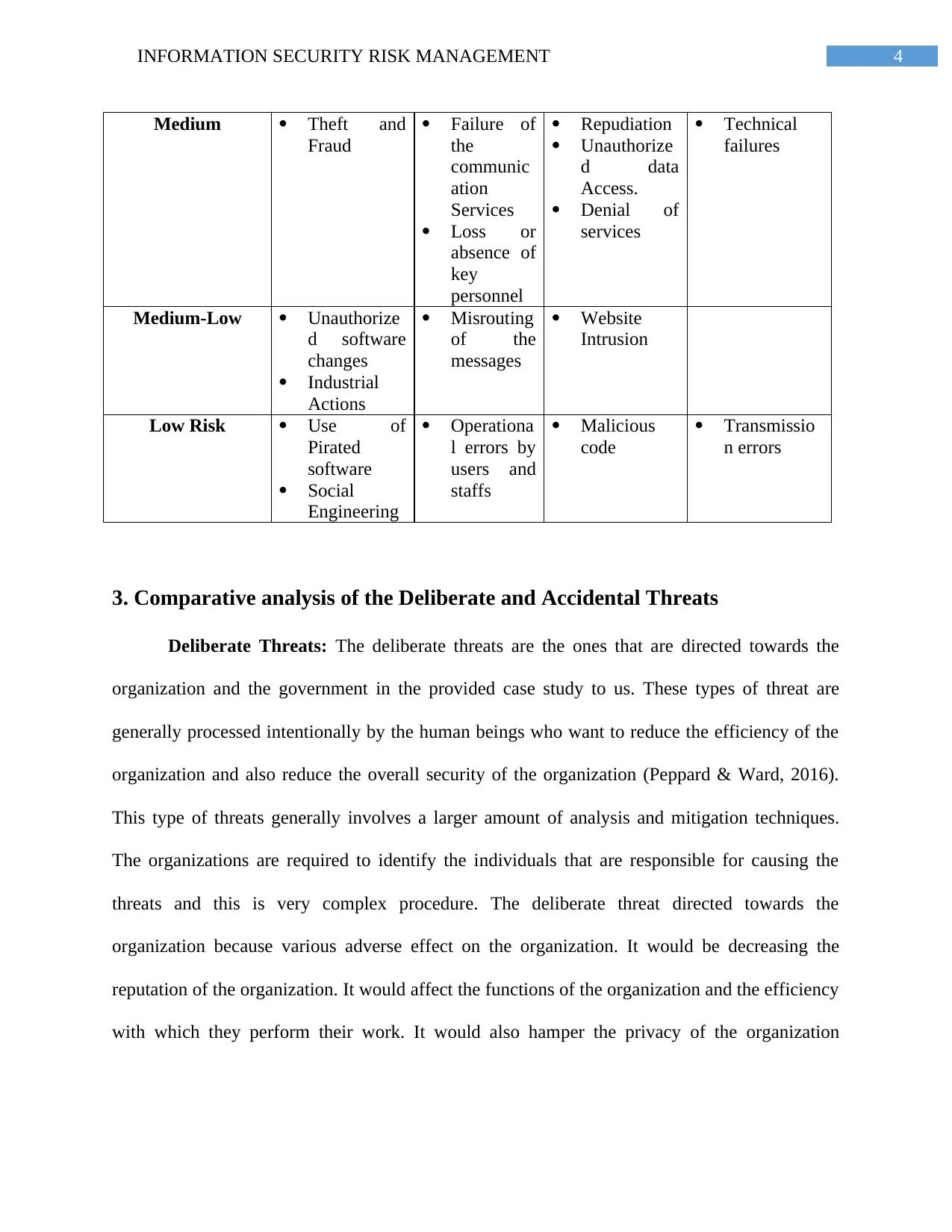
4INFORMATION SECURITY RISK MANAGEMENT
Medium Theft and
Fraud
Failure of
the
communic
ation
Services
Loss or
absence of
key
personnel
Repudiation
Unauthorize
d data
Access.
Denial of
services
Technical
failures
Medium-Low Unauthorize
d software
changes
Industrial
Actions
Misrouting
of the
messages
Website
Intrusion
Low Risk Use of
Pirated
software
Social
Engineering
Operationa
l errors by
users and
staffs
Malicious
code
Transmissio
n errors
3. Comparative analysis of the Deliberate and Accidental Threats
Deliberate Threats: The deliberate threats are the ones that are directed towards the
organization and the government in the provided case study to us. These types of threat are
generally processed intentionally by the human beings who want to reduce the efficiency of the
organization and also reduce the overall security of the organization (Peppard & Ward, 2016).
This type of threats generally involves a larger amount of analysis and mitigation techniques.
The organizations are required to identify the individuals that are responsible for causing the
threats and this is very complex procedure. The deliberate threat directed towards the
organization because various adverse effect on the organization. It would be decreasing the
reputation of the organization. It would affect the functions of the organization and the efficiency
with which they perform their work. It would also hamper the privacy of the organization
Medium Theft and
Fraud
Failure of
the
communic
ation
Services
Loss or
absence of
key
personnel
Repudiation
Unauthorize
d data
Access.
Denial of
services
Technical
failures
Medium-Low Unauthorize
d software
changes
Industrial
Actions
Misrouting
of the
messages
Website
Intrusion
Low Risk Use of
Pirated
software
Social
Engineering
Operationa
l errors by
users and
staffs
Malicious
code
Transmissio
n errors
3. Comparative analysis of the Deliberate and Accidental Threats
Deliberate Threats: The deliberate threats are the ones that are directed towards the
organization and the government in the provided case study to us. These types of threat are
generally processed intentionally by the human beings who want to reduce the efficiency of the
organization and also reduce the overall security of the organization (Peppard & Ward, 2016).
This type of threats generally involves a larger amount of analysis and mitigation techniques.
The organizations are required to identify the individuals that are responsible for causing the
threats and this is very complex procedure. The deliberate threat directed towards the
organization because various adverse effect on the organization. It would be decreasing the
reputation of the organization. It would affect the functions of the organization and the efficiency
with which they perform their work. It would also hamper the privacy of the organization

5INFORMATION SECURITY RISK MANAGEMENT
(Dinev, McConnell & Smith, 2015). In addition to this, the data efficiency of the organization
would also be hampered.
Accidental Threats: The accidental threats are the threats that are not directed towards
the organization but the threats are the general result of the accidents that might take place both
inside the organization or outside it (Pieters et al., 2014). This type of threats can generally be
anticipated and hence the mitigation of this type of threats are less complex and the mitigation
procedures involved for this type of threats are generally easier to implement. This type of
threats results in the data displacement or the data corruption for the system of the organization.
In addition to this, the technical issues and the non-functional issues for the organization can also
arise as a result of these threats,
3.1 Ranking of threats in order of importance
The threats that were analyzed for the organization can very easily categories into four
different ranks (Vasenev et al., 2017). They can be ranked into high, medium, medium low and
low rankings. The ranking provides the information about the severity of the threats and effects
that they can create on the organization.
High: The high is the highest ranking for the threats. The threats with the high ranking
are the most severe for the organization. The threats are generally very difficult to detect and also
these threats are very difficult to mitigate and also the threat analysis are also very difficult. The
threats that have very high risk are Fire, Sabotage, and Failure of the operations that are
outsourced. In addition to this there are some external threats that are of high risk for the State
government of Victoria. They are malicious destruction of the data and the files, Masquerade,
Unauthorized Dial-In Access and Programming or coding errors.
(Dinev, McConnell & Smith, 2015). In addition to this, the data efficiency of the organization
would also be hampered.
Accidental Threats: The accidental threats are the threats that are not directed towards
the organization but the threats are the general result of the accidents that might take place both
inside the organization or outside it (Pieters et al., 2014). This type of threats can generally be
anticipated and hence the mitigation of this type of threats are less complex and the mitigation
procedures involved for this type of threats are generally easier to implement. This type of
threats results in the data displacement or the data corruption for the system of the organization.
In addition to this, the technical issues and the non-functional issues for the organization can also
arise as a result of these threats,
3.1 Ranking of threats in order of importance
The threats that were analyzed for the organization can very easily categories into four
different ranks (Vasenev et al., 2017). They can be ranked into high, medium, medium low and
low rankings. The ranking provides the information about the severity of the threats and effects
that they can create on the organization.
High: The high is the highest ranking for the threats. The threats with the high ranking
are the most severe for the organization. The threats are generally very difficult to detect and also
these threats are very difficult to mitigate and also the threat analysis are also very difficult. The
threats that have very high risk are Fire, Sabotage, and Failure of the operations that are
outsourced. In addition to this there are some external threats that are of high risk for the State
government of Victoria. They are malicious destruction of the data and the files, Masquerade,
Unauthorized Dial-In Access and Programming or coding errors.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SECURITY RISK MANAGEMENT
Medium: The medium risks have priority lesser than the high risk threats, although they
cause a serious amount of problems for the organizations. The identification of these threats is
easier than the high risk threats although the mitigation of these threats are very difficult and also
the treats are very severe on the systems of the organization. For the State government of
Victoria the identified threats that are of medium risk are Theft and Fraud, Failure of the
communication Services, Loss or absence of key personnel, Repudiation, Unauthorized data
Access, Denial of services and Technical failures.
Medium Low: The medium low risk threats are ranked below the medium level treats
but are equally important for the threat analysis techniques. The medium low threats cannot be
ignored and also they should be mitigated with equal importance. Ignoring these risks can result
in severe consequences for the organization. The threats that have been identified as the medium
low level risks are unauthorized software changes, Industrial Actions, Misrouting of the
messages and Website Intrusion.
Low: The low level risks are the ones that are not of major concern for the Victorian
State Government. The low level risks can be very easily mitigated and additionally they can be
easily avoided with some security methods that can be adopted by the organizations. Although
these risks are very minor they can result into serious situation if they are not addressed properly.
3.2 Justification of the rankings
The ranking of the threats on the information system maintained by the State government
of Victoria are set according to the severity of the threats on the system and the effect of the
threat on the system of the Victorian State Government. The threats that are ranked high are
generally severe for the government and the government has to implement various type off
mitigation procedures that would be providing security to the Information system of the
Medium: The medium risks have priority lesser than the high risk threats, although they
cause a serious amount of problems for the organizations. The identification of these threats is
easier than the high risk threats although the mitigation of these threats are very difficult and also
the treats are very severe on the systems of the organization. For the State government of
Victoria the identified threats that are of medium risk are Theft and Fraud, Failure of the
communication Services, Loss or absence of key personnel, Repudiation, Unauthorized data
Access, Denial of services and Technical failures.
Medium Low: The medium low risk threats are ranked below the medium level treats
but are equally important for the threat analysis techniques. The medium low threats cannot be
ignored and also they should be mitigated with equal importance. Ignoring these risks can result
in severe consequences for the organization. The threats that have been identified as the medium
low level risks are unauthorized software changes, Industrial Actions, Misrouting of the
messages and Website Intrusion.
Low: The low level risks are the ones that are not of major concern for the Victorian
State Government. The low level risks can be very easily mitigated and additionally they can be
easily avoided with some security methods that can be adopted by the organizations. Although
these risks are very minor they can result into serious situation if they are not addressed properly.
3.2 Justification of the rankings
The ranking of the threats on the information system maintained by the State government
of Victoria are set according to the severity of the threats on the system and the effect of the
threat on the system of the Victorian State Government. The threats that are ranked high are
generally severe for the government and the government has to implement various type off
mitigation procedures that would be providing security to the Information system of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY RISK MANAGEMENT
government (Darst & Murphy, 2013). For instance the Fire and Sabotage threats are very severe
for the information system of the government as this would affect both the hardware and the
software system of the information system of the state government. The medium level threats are
not so severe as the high level risk but the medium level risks should not be ignored. They can
also cause very severs effect on the systems. For instance the Denial of Services attacks on the
information system of the government of Victoria. This would interrupt the procedures of the
organization. This also affects the various types of activities of the government. The next is the
medium-low level of risk detected in the risk analysis of the information system of the
government. These risks are not very severe but can cause various types of adversities for the
government. In addition to this, the unauthorized software changes that would make it difficult
for the staffs to get accustomed to the system and this would result in the inefficiency of the
process that are conducted by the government (Aziz et al., 2013). The low level risks are the ones
that are easily identified and can be mitigated easily. The government can adopt various policies
that can help in avoiding the threats that result from the risks for the organization. For instance
the social engineering is one of the threats that not much of a concern for the government as they
already have plans for avoiding this type of threats and their only responsibility is to make sure
the policies are in place to prevent themselves from any kind of threat.
4. Challenges faced by Victorian state government in deciding Risk
management
The Victorian State government faced various type of challenges while implementing
their Protective Security Policy Frameworks for the protection of their information system and
also for mitigating the risks related to the Information system of the government (Schmied et al.,
2015). The external threats and the internal threats related to the Information system might make
government (Darst & Murphy, 2013). For instance the Fire and Sabotage threats are very severe
for the information system of the government as this would affect both the hardware and the
software system of the information system of the state government. The medium level threats are
not so severe as the high level risk but the medium level risks should not be ignored. They can
also cause very severs effect on the systems. For instance the Denial of Services attacks on the
information system of the government of Victoria. This would interrupt the procedures of the
organization. This also affects the various types of activities of the government. The next is the
medium-low level of risk detected in the risk analysis of the information system of the
government. These risks are not very severe but can cause various types of adversities for the
government. In addition to this, the unauthorized software changes that would make it difficult
for the staffs to get accustomed to the system and this would result in the inefficiency of the
process that are conducted by the government (Aziz et al., 2013). The low level risks are the ones
that are easily identified and can be mitigated easily. The government can adopt various policies
that can help in avoiding the threats that result from the risks for the organization. For instance
the social engineering is one of the threats that not much of a concern for the government as they
already have plans for avoiding this type of threats and their only responsibility is to make sure
the policies are in place to prevent themselves from any kind of threat.
4. Challenges faced by Victorian state government in deciding Risk
management
The Victorian State government faced various type of challenges while implementing
their Protective Security Policy Frameworks for the protection of their information system and
also for mitigating the risks related to the Information system of the government (Schmied et al.,
2015). The external threats and the internal threats related to the Information system might make

8INFORMATION SECURITY RISK MANAGEMENT
it difficult for the government to implement the system. The filtration of the system helps the
organization to reduce the vulnerabilities that are related to the information system. The
challenges that the organization faces are listed below with some brief descriptions;
Data insecurity: The protective data security faces one of the biggest challenges for the
information system of the government. The data of the organization needs to be efficiently
secured and also the data security is one of the main vulnerabilities against the threats such as
Masquerade and Denial of Service attacks.
Foundation of Victoria State Government: The foundation of the Victoria State
government is also of the min challenges that the system face in their aim of implementing the
Information system risk management system. The present systems of the government are not up
to date and hence, this a major challenge against the implementation of the system.
Information respectability: Information respectability is one of the major challenges that
the organization would face as they look to implement the information system security
framework for the organization. In addition to this the framework for the organization would also
require complaint with the standards and hence, the organization would face the challenge in this
area.
5. Difference between Risk and Uncertainty
Risk and uncertainty are two theories that are related to the economic theories. However,
the risk and the uncertainties have different definition for the threats that are related to the
information system of the organization (Bekaert, Hoerova & Duca, 2013). Risk and
Uncertainties have distinct meaning for them in each and every context. The main differences in
between Risk and Uncertainty are:
it difficult for the government to implement the system. The filtration of the system helps the
organization to reduce the vulnerabilities that are related to the information system. The
challenges that the organization faces are listed below with some brief descriptions;
Data insecurity: The protective data security faces one of the biggest challenges for the
information system of the government. The data of the organization needs to be efficiently
secured and also the data security is one of the main vulnerabilities against the threats such as
Masquerade and Denial of Service attacks.
Foundation of Victoria State Government: The foundation of the Victoria State
government is also of the min challenges that the system face in their aim of implementing the
Information system risk management system. The present systems of the government are not up
to date and hence, this a major challenge against the implementation of the system.
Information respectability: Information respectability is one of the major challenges that
the organization would face as they look to implement the information system security
framework for the organization. In addition to this the framework for the organization would also
require complaint with the standards and hence, the organization would face the challenge in this
area.
5. Difference between Risk and Uncertainty
Risk and uncertainty are two theories that are related to the economic theories. However,
the risk and the uncertainties have different definition for the threats that are related to the
information system of the organization (Bekaert, Hoerova & Duca, 2013). Risk and
Uncertainties have distinct meaning for them in each and every context. The main differences in
between Risk and Uncertainty are:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION SECURITY RISK MANAGEMENT
Risk is a probabilistic estimate of the likely event, while uncertainty is generally a huge
range of possible outcomes for any particular outcomes and complexities that make it
very difficult to define a particular set of probability (Pastor & Veronesi, 2013).
If the risk and the potential damage that can occur form any exposure is identified, then
the amount of effort required to be spent for the mitigation of the risk can be very easily
calculated. The scenarios can be created and used for defining the different outcomes that
are available and can take place in the future, but the actual outcome can never be
predicted in estimation.
Risk is the condition of person on verge of losing something, but uncertainty is the
condition where the person is unaware about the information of the future events.
Risk is measurable by various means and can be evaluated on the basis of their effect on
the system but uncertainty can neither be predicted nor be measured.
The potential outcomes for the risks are already known but there are no effective
outcomes for the uncertain events.
Risk can be controlled, if authentic measures are taken to control it. But, uncertainty is
outside the capacity to control of the individual or attempt, as what needs to come is
indeterminate.
Minimization of risk is ought to be conceivable, by staying away from potential hazard.
But Uncertainty can't be limited.
Probabilities are dispensed to a game plan of risks that is farfetched if there ought to
emerge an event of insecurity.
Risk is a probabilistic estimate of the likely event, while uncertainty is generally a huge
range of possible outcomes for any particular outcomes and complexities that make it
very difficult to define a particular set of probability (Pastor & Veronesi, 2013).
If the risk and the potential damage that can occur form any exposure is identified, then
the amount of effort required to be spent for the mitigation of the risk can be very easily
calculated. The scenarios can be created and used for defining the different outcomes that
are available and can take place in the future, but the actual outcome can never be
predicted in estimation.
Risk is the condition of person on verge of losing something, but uncertainty is the
condition where the person is unaware about the information of the future events.
Risk is measurable by various means and can be evaluated on the basis of their effect on
the system but uncertainty can neither be predicted nor be measured.
The potential outcomes for the risks are already known but there are no effective
outcomes for the uncertain events.
Risk can be controlled, if authentic measures are taken to control it. But, uncertainty is
outside the capacity to control of the individual or attempt, as what needs to come is
indeterminate.
Minimization of risk is ought to be conceivable, by staying away from potential hazard.
But Uncertainty can't be limited.
Probabilities are dispensed to a game plan of risks that is farfetched if there ought to
emerge an event of insecurity.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INFORMATION SECURITY RISK MANAGEMENT
6. Different approaches for risk control and mitigation in Victorian State
Government
Risk management techniques that are applied by the Victorian state Government is to
identify the major risks of the systems and also apply proper analysis of the risk mitigation
techniques and apply proper risk mitigation techniques. The risk management includes various
types of methods for the implementation of the risk control techniques and also the mitigation of
the risks. There are various methods that can be applied for the mitigation of the risks that are
being raised in the scenario. These methods are:
Privacy and data Protection Act 2014
The Privacy and the Data Protection Act of 2014 would change the point of view of the
data protection policies in the Victorian State Government (Jay, 2014). It involves the following
g steps:
Develop the Victorian Protective Data Security Framework
Issue the Victorian Protective Data Security Standards
Establishment of the monitoring and assuring of the public sector data security
Victorian Protective Data Security Framework
The framework provides the guidelines for the data security obligation and the standard
followed by the agencies in Victoria (Schlosberg, 2016). They are in compliance with the PDPA
and provided the capabilities of risk management and security management for the government.
6. Different approaches for risk control and mitigation in Victorian State
Government
Risk management techniques that are applied by the Victorian state Government is to
identify the major risks of the systems and also apply proper analysis of the risk mitigation
techniques and apply proper risk mitigation techniques. The risk management includes various
types of methods for the implementation of the risk control techniques and also the mitigation of
the risks. There are various methods that can be applied for the mitigation of the risks that are
being raised in the scenario. These methods are:
Privacy and data Protection Act 2014
The Privacy and the Data Protection Act of 2014 would change the point of view of the
data protection policies in the Victorian State Government (Jay, 2014). It involves the following
g steps:
Develop the Victorian Protective Data Security Framework
Issue the Victorian Protective Data Security Standards
Establishment of the monitoring and assuring of the public sector data security
Victorian Protective Data Security Framework
The framework provides the guidelines for the data security obligation and the standard
followed by the agencies in Victoria (Schlosberg, 2016). They are in compliance with the PDPA
and provided the capabilities of risk management and security management for the government.

11INFORMATION SECURITY RISK MANAGEMENT
Public Sector Data
Under this section it is clearly stated that any kind of data that is obtained or stored by
any kind of agency is to be discreet and the information held by the agency should be without the
object of anyone and is a use for the agency.
Protective Data Security
This method is very important for the Victorian government to protect tier own data. The
Public sector organization can also come under this policy and protect their data against probable
threat and risk of being damaged.
Information Privacy Principle
Under PPI 4.1 the organization must take some essential actions so that the personal data
of the individuals that are present within the organization and should take full responsibility of
their data.
Public Sector Data
Under this section it is clearly stated that any kind of data that is obtained or stored by
any kind of agency is to be discreet and the information held by the agency should be without the
object of anyone and is a use for the agency.
Protective Data Security
This method is very important for the Victorian government to protect tier own data. The
Public sector organization can also come under this policy and protect their data against probable
threat and risk of being damaged.
Information Privacy Principle
Under PPI 4.1 the organization must take some essential actions so that the personal data
of the individuals that are present within the organization and should take full responsibility of
their data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





