Information Security: Threat Profile, Mitigation & Cryptography
VerifiedAdded on 2023/06/14
|10
|1587
|170
Report
AI Summary
This report provides an overview of information security, focusing on threat profiles and cryptography. It begins by profiling the Heartbleed vulnerability, detailing the systems it attacks, how the attack is performed, and effective mitigation strategies. The report also discusses the scope of the threat and reflects on the adequacy of the mitigation strategies. Furthermore, the report explores the use of GPG/PGP for securing email messages and documents, including practical exercises in a Linux Kali environment. It covers key size considerations, encryption/decryption timing, and the importance of ASCII format for exported keys. Finally, it includes a reflection on the role of cryptography in ensuring individual privacy, emphasizing the importance of key management and the overall effectiveness of cryptography in securing communications.

Running head: INFORMATION SECURITY 1
Information Security
Student Name
Student ID
Course
Instructor
Institutional Affiliation
Information Security
Student Name
Student ID
Course
Instructor
Institutional Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INFORMATION SECURITY
2
Threat Profile
Threat Profile
Name of the
threat
Heart bleed
Target
System
Twitter, Instagram, Facebook, open SSL, Gmail, Google, yahoo
How heart
bleed attacks
The heart bleed bug executes by checking for missing limit in the TSL treatment
to enable remote bugs to access the 64KB memory of the affected server. This
gives aggressors to retrieve private keys and convert the server or duplicate its
normal activities (Osman, 2017). The Heart drain bug accesses the nginx and
apache like the normal programs using Open SSL. Regardless, whether the
servers are running a HTTPS advantage, or running uncovered sorts of Open SSL
with heartbeats empowered the bug could still penetrate. Latest SSL research have
found that the beat development was empowered on 17.5% of SSL objectives,
addressing around a broad piece of a million insistences issued by trusted check
powers (Norton, 2016). These introductions are hence feeble against being
scrutinized (through private key divulgence), enabling an aggressor to imitate the
influenced districts without rising any program observes.
Mitigation
strategy
Since this enterprise misuses frailty in encoded trades, any diminishing game
plan must obstruct that correspondence. That is ensured. In that way are three
concentrations where this attempt can be lightened
They can check the customer working structure and gadget sort and match
that against known usage of the affected OpenSSL outlines. Once perceived
the customer can be rejected - keeping the blameworthy demand from
reliably being sent in any case (Poulin, 2014). Removal of customers in
context of the likelihood they may be an attacker can accomplish irritated
good 'old fashioned purchasers, experts or partners, notwithstanding.
Secondly, investigate customer demands interminable supply of a Heartbeat
Message, dismiss it. This shields the demand from being sending to exposed
frameworks and servers. Finally, examine responses and subsequent to
watching a Heartbleed Message reaction, check its length. On the off chance
2
2
Threat Profile
Threat Profile
Name of the
threat
Heart bleed
Target
System
Twitter, Instagram, Facebook, open SSL, Gmail, Google, yahoo
How heart
bleed attacks
The heart bleed bug executes by checking for missing limit in the TSL treatment
to enable remote bugs to access the 64KB memory of the affected server. This
gives aggressors to retrieve private keys and convert the server or duplicate its
normal activities (Osman, 2017). The Heart drain bug accesses the nginx and
apache like the normal programs using Open SSL. Regardless, whether the
servers are running a HTTPS advantage, or running uncovered sorts of Open SSL
with heartbeats empowered the bug could still penetrate. Latest SSL research have
found that the beat development was empowered on 17.5% of SSL objectives,
addressing around a broad piece of a million insistences issued by trusted check
powers (Norton, 2016). These introductions are hence feeble against being
scrutinized (through private key divulgence), enabling an aggressor to imitate the
influenced districts without rising any program observes.
Mitigation
strategy
Since this enterprise misuses frailty in encoded trades, any diminishing game
plan must obstruct that correspondence. That is ensured. In that way are three
concentrations where this attempt can be lightened
They can check the customer working structure and gadget sort and match
that against known usage of the affected OpenSSL outlines. Once perceived
the customer can be rejected - keeping the blameworthy demand from
reliably being sent in any case (Poulin, 2014). Removal of customers in
context of the likelihood they may be an attacker can accomplish irritated
good 'old fashioned purchasers, experts or partners, notwithstanding.
Secondly, investigate customer demands interminable supply of a Heartbeat
Message, dismiss it. This shields the demand from being sending to exposed
frameworks and servers. Finally, examine responses and subsequent to
watching a Heartbleed Message reaction, check its length. On the off chance
2
INFORMATION SECURITY
3
that it's more unmistakable than a length you feel uncommon with, dispose of
it (Davis, 2017). This framework will shield aggressors from enduring
delicate information, yet it ought to be seen that at the inspiration driving
disclosure, the server - and information - has beginning at now been traded
off.
Scope of the
Heart bleed
On April 15, 2014, all clients of WIPO administrations which rely upon
WIPO Accounts ought to have gotten an email asking for them to reset their
passwords because some of WIPO's frameworks utilized an OpenSSL
rendition which is defenceless to the Heartbleed bug (Oltmann, 2017). When
they got the notice, they quickly fixed their frameworks and supplanted the
server endorsements to keep the bug from being utilized. Besides they don't
have any proof that any client data has been traded off, yet the likelihood
remains that usernames and passwords were taken before the servers were
fixed. Although they settled the issue with change login passwords and
refresh their frameworks with new security programming.
Conclusion
and
Reflection
The Heartbleed bug’s severity is medium. It discloses only considerable
information’s access to some system file is very easy, but the attacker does
not have control over what is obtained.
For those expert associations that are affected this is a not too bad
opportunity to refresh security quality. An extensive measure of
programming gets revives which for the most part would have not been
sincere. Although this is troublesome for the security gathering, we can rest
ensured that establishment of the computerized guilty parties and their
favoured bits of knowledge have been revealed also. As per a study it is
unmistakably observed that 317 million new malware assignments were
made in 2014, around 1 million reliably. Email remains a fundamental vector
of assault for cybercriminals, yet they keep attempting diverse things with
new frameworks for strike on PDAs and easy-going gatherings to contact
more individuals with less exertion. The security gathering, we included,
must make sense of how to find these inevitable human stumbles sooner.
3
3
that it's more unmistakable than a length you feel uncommon with, dispose of
it (Davis, 2017). This framework will shield aggressors from enduring
delicate information, yet it ought to be seen that at the inspiration driving
disclosure, the server - and information - has beginning at now been traded
off.
Scope of the
Heart bleed
On April 15, 2014, all clients of WIPO administrations which rely upon
WIPO Accounts ought to have gotten an email asking for them to reset their
passwords because some of WIPO's frameworks utilized an OpenSSL
rendition which is defenceless to the Heartbleed bug (Oltmann, 2017). When
they got the notice, they quickly fixed their frameworks and supplanted the
server endorsements to keep the bug from being utilized. Besides they don't
have any proof that any client data has been traded off, yet the likelihood
remains that usernames and passwords were taken before the servers were
fixed. Although they settled the issue with change login passwords and
refresh their frameworks with new security programming.
Conclusion
and
Reflection
The Heartbleed bug’s severity is medium. It discloses only considerable
information’s access to some system file is very easy, but the attacker does
not have control over what is obtained.
For those expert associations that are affected this is a not too bad
opportunity to refresh security quality. An extensive measure of
programming gets revives which for the most part would have not been
sincere. Although this is troublesome for the security gathering, we can rest
ensured that establishment of the computerized guilty parties and their
favoured bits of knowledge have been revealed also. As per a study it is
unmistakably observed that 317 million new malware assignments were
made in 2014, around 1 million reliably. Email remains a fundamental vector
of assault for cybercriminals, yet they keep attempting diverse things with
new frameworks for strike on PDAs and easy-going gatherings to contact
more individuals with less exertion. The security gathering, we included,
must make sense of how to find these inevitable human stumbles sooner.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
INFORMATION SECURITY
4
Risk Assessment
Rating Definitions
Critical
A helplessness, which, if misused would permit malignant code to execute,
possibly without a client staying alert
High
A helplessness, which, if misused could affect the secretly, respectability, or
accessibility of information, or of the honesty or accessibility of assets.
Medium
A helplessness that is restricted to a noteworthy degree by elements, for
example, default setup, examining, or is hard to misuse
Low
A powerlessness that has negligible effect to the framework and is to a great
degree hard to misuse
Risk = Impact x likelihood
Impact: - 2.9
Likelihood: -10.0
= 2.9 x 10.0
Risk = 29
4
4
Risk Assessment
Rating Definitions
Critical
A helplessness, which, if misused would permit malignant code to execute,
possibly without a client staying alert
High
A helplessness, which, if misused could affect the secretly, respectability, or
accessibility of information, or of the honesty or accessibility of assets.
Medium
A helplessness that is restricted to a noteworthy degree by elements, for
example, default setup, examining, or is hard to misuse
Low
A powerlessness that has negligible effect to the framework and is to a great
degree hard to misuse
Risk = Impact x likelihood
Impact: - 2.9
Likelihood: -10.0
= 2.9 x 10.0
Risk = 29
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INFORMATION SECURITY
5
Question 2:
Question 2: You are required to learn the GPG/PGP package using Linux Kali environment
(learning the applications of private and public key cryptography to secure email messages
and documents) to be able to answer the following questions. You should pair up with one of
your class fellow to do this lab and record results and gives commentary on the results.
If you do not have a class fellow then create two user accounts and you can encrypt using one
account and descript using other account.
Answer: - key size 1024
(Source: Garg, 2016)
c) Create a file of close to 1 GB and encrypt and decrypt it and note the time taken.
Comment on the reason why this much time has taken. Calculate how long it would
take to do the encryption/decryption of a 10 GBs of data.
5
5
Question 2:
Question 2: You are required to learn the GPG/PGP package using Linux Kali environment
(learning the applications of private and public key cryptography to secure email messages
and documents) to be able to answer the following questions. You should pair up with one of
your class fellow to do this lab and record results and gives commentary on the results.
If you do not have a class fellow then create two user accounts and you can encrypt using one
account and descript using other account.
Answer: - key size 1024
(Source: Garg, 2016)
c) Create a file of close to 1 GB and encrypt and decrypt it and note the time taken.
Comment on the reason why this much time has taken. Calculate how long it would
take to do the encryption/decryption of a 10 GBs of data.
5
INFORMATION SECURITY
6
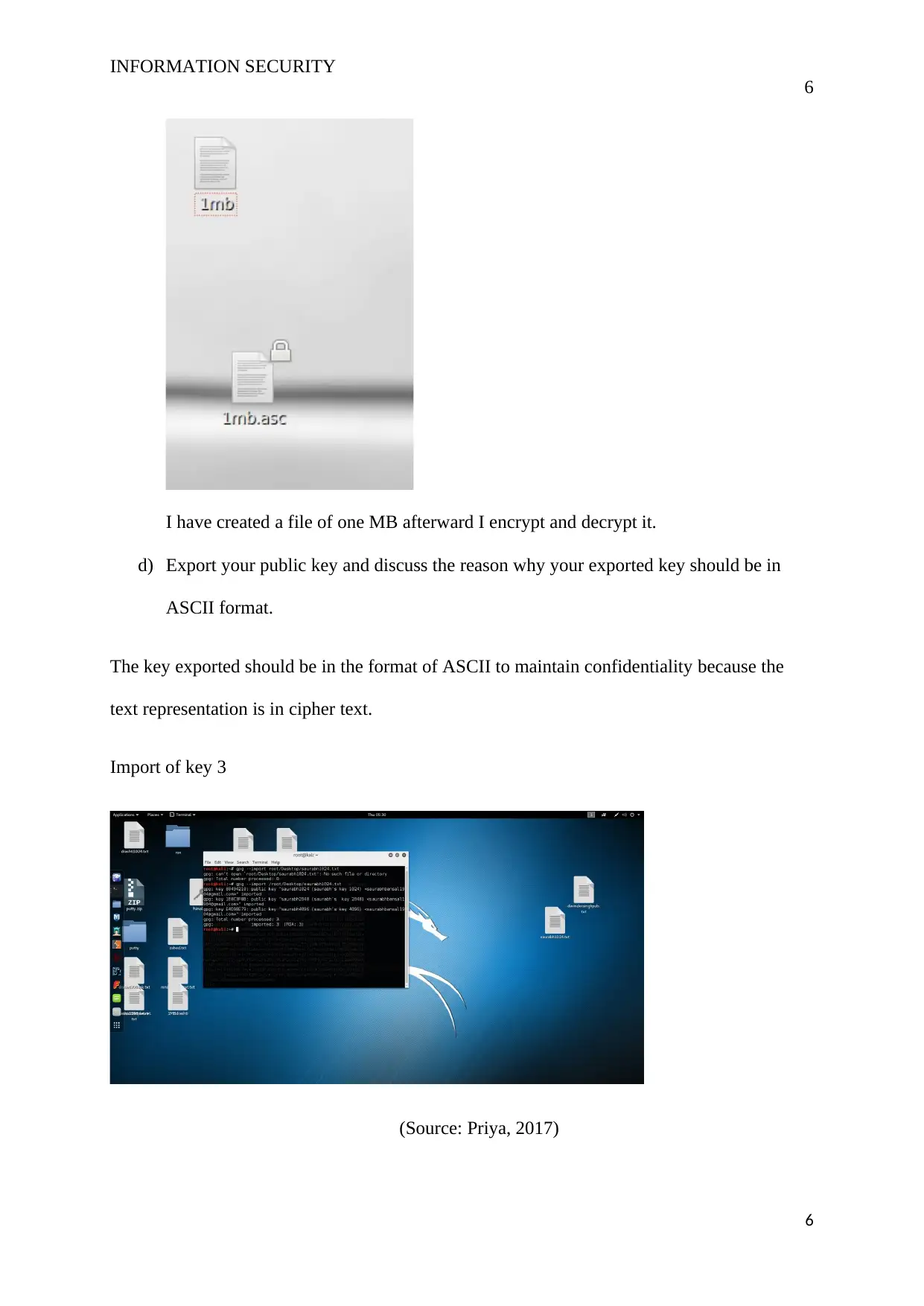
I have created a file of one MB afterward I encrypt and decrypt it.
d) Export your public key and discuss the reason why your exported key should be in
ASCII format.
The key exported should be in the format of ASCII to maintain confidentiality because the
text representation is in cipher text.
Import of key 3
(Source: Priya, 2017)
6
6
I have created a file of one MB afterward I encrypt and decrypt it.
d) Export your public key and discuss the reason why your exported key should be in
ASCII format.
The key exported should be in the format of ASCII to maintain confidentiality because the
text representation is in cipher text.
Import of key 3
(Source: Priya, 2017)
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
INFORMATION SECURITY
7
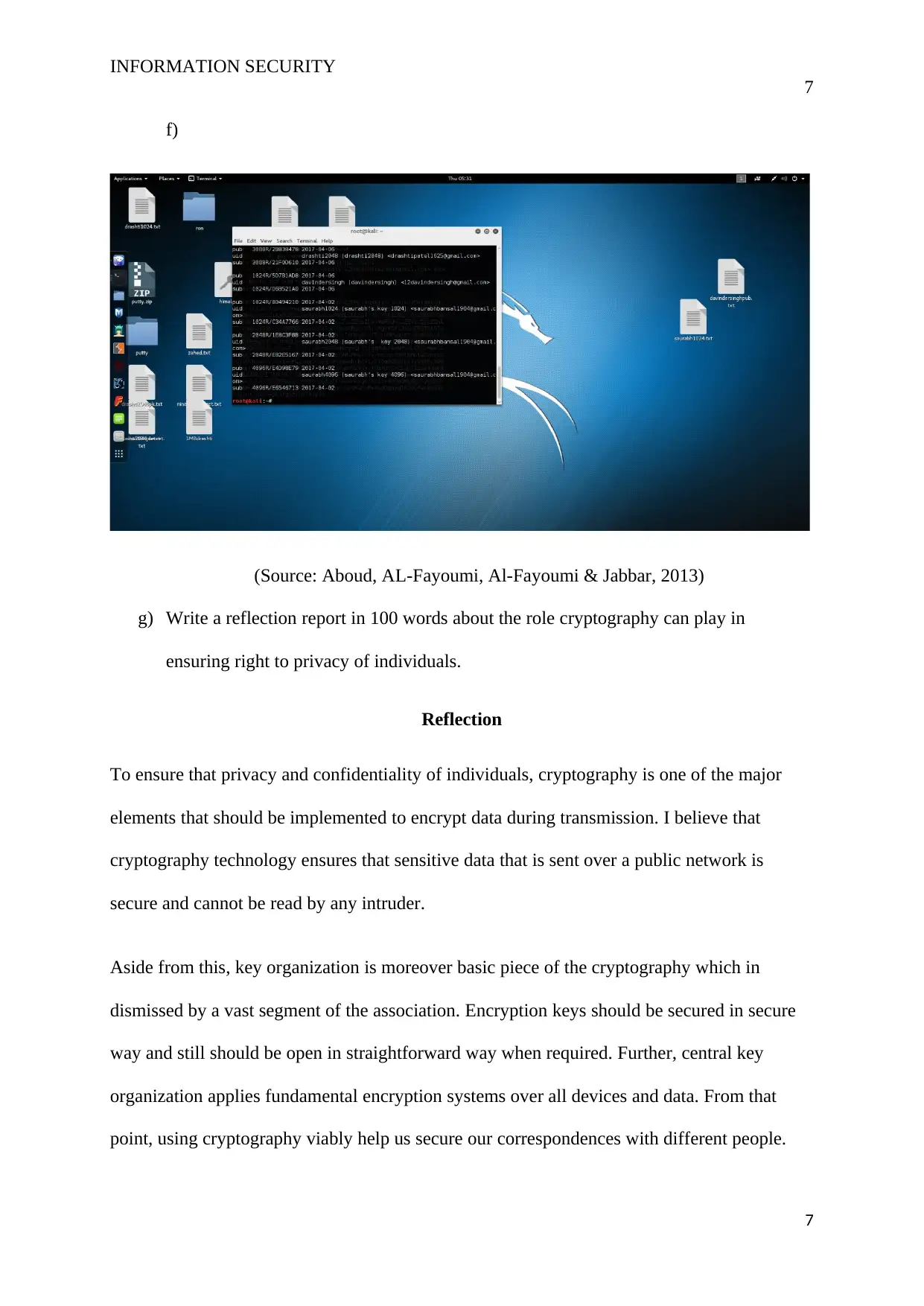
f)
(Source: Aboud, AL-Fayoumi, Al-Fayoumi & Jabbar, 2013)
g) Write a reflection report in 100 words about the role cryptography can play in
ensuring right to privacy of individuals.
Reflection
To ensure that privacy and confidentiality of individuals, cryptography is one of the major
elements that should be implemented to encrypt data during transmission. I believe that
cryptography technology ensures that sensitive data that is sent over a public network is
secure and cannot be read by any intruder.
Aside from this, key organization is moreover basic piece of the cryptography which in
dismissed by a vast segment of the association. Encryption keys should be secured in secure
way and still should be open in straightforward way when required. Further, central key
organization applies fundamental encryption systems over all devices and data. From that
point, using cryptography viably help us secure our correspondences with different people.
7
7
f)
(Source: Aboud, AL-Fayoumi, Al-Fayoumi & Jabbar, 2013)
g) Write a reflection report in 100 words about the role cryptography can play in
ensuring right to privacy of individuals.
Reflection
To ensure that privacy and confidentiality of individuals, cryptography is one of the major
elements that should be implemented to encrypt data during transmission. I believe that
cryptography technology ensures that sensitive data that is sent over a public network is
secure and cannot be read by any intruder.
Aside from this, key organization is moreover basic piece of the cryptography which in
dismissed by a vast segment of the association. Encryption keys should be secured in secure
way and still should be open in straightforward way when required. Further, central key
organization applies fundamental encryption systems over all devices and data. From that
point, using cryptography viably help us secure our correspondences with different people.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SECURITY
8
This is to an awesome degree relentless, especially while overseeing subtle information, also
while overseeing typical, well ordered educating.
8
8
This is to an awesome degree relentless, especially while overseeing subtle information, also
while overseeing typical, well ordered educating.
8

INFORMATION SECURITY
9
References
Aboud, S., AL-Fayoumi, M., Al-Fayoumi, M., & Jabbar, H. (2013). An Efficient RSA Public Key
Encryption Scheme. Fifth International Conference On Information Technology: New
Generations (Itng 2008). http://dx.doi.org/10.1109/itng.2013.199
Davis, G. (2017). The Heartbleed Vulnerability: What It Is and How It Affects You | McAfee
Blogs. McAfee Blogs. Retrieved 2 April 2018, from
https://securingtomorrow.mcafee.com/consumer/consumer-threat-notices/what-is-
heartbleed/
Garg, S. (2016). A Review on RSA Encryption Algorithm. International Journal Of Engineering
And Computer Science. http://dx.doi.org/10.18535/ijecs/v5i7.07
Heartbleed Impact: Community Health Systems Breach. (2017). Bankinfosecurity.com.
Retrieved 2 April 2018, from http://www.bankinfosecurity.com/interviews/threat-
intelligence-heartbleed-impact-i-2378
Norton, N. (2016). Heartbleed Bug and Norton's protection against the
vulnerability. Support.norton.com. Retrieved 3 April 2018, from
https://support.norton.com/sp/en/us/home/current/solutions/v98431836_EndUserProfile_en
_us
Oltmann, V. (2017). The Heartbleed Bug – a security threat you need to act on. The Fraud
Chronicles. Retrieved 4 April 2017, from http://fraudchronicles.com/the-heartbleed-
bug-a-security-threat-you-need-to-act-on/
Osman, N. (2017). Heartbleed: What is it and what are options to mitigate it?. Serverfault.com.
Retrieved 2 April 2018, from https://serverfault.com/questions/587329/heartbleed-what-is-
it-and-what-are-options-to-mitigate-it
9
9
References
Aboud, S., AL-Fayoumi, M., Al-Fayoumi, M., & Jabbar, H. (2013). An Efficient RSA Public Key
Encryption Scheme. Fifth International Conference On Information Technology: New
Generations (Itng 2008). http://dx.doi.org/10.1109/itng.2013.199
Davis, G. (2017). The Heartbleed Vulnerability: What It Is and How It Affects You | McAfee
Blogs. McAfee Blogs. Retrieved 2 April 2018, from
https://securingtomorrow.mcafee.com/consumer/consumer-threat-notices/what-is-
heartbleed/
Garg, S. (2016). A Review on RSA Encryption Algorithm. International Journal Of Engineering
And Computer Science. http://dx.doi.org/10.18535/ijecs/v5i7.07
Heartbleed Impact: Community Health Systems Breach. (2017). Bankinfosecurity.com.
Retrieved 2 April 2018, from http://www.bankinfosecurity.com/interviews/threat-
intelligence-heartbleed-impact-i-2378
Norton, N. (2016). Heartbleed Bug and Norton's protection against the
vulnerability. Support.norton.com. Retrieved 3 April 2018, from
https://support.norton.com/sp/en/us/home/current/solutions/v98431836_EndUserProfile_en
_us
Oltmann, V. (2017). The Heartbleed Bug – a security threat you need to act on. The Fraud
Chronicles. Retrieved 4 April 2017, from http://fraudchronicles.com/the-heartbleed-
bug-a-security-threat-you-need-to-act-on/
Osman, N. (2017). Heartbleed: What is it and what are options to mitigate it?. Serverfault.com.
Retrieved 2 April 2018, from https://serverfault.com/questions/587329/heartbleed-what-is-
it-and-what-are-options-to-mitigate-it
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION SECURITY
10
Poulin, C. (2014). Heartbleed OpenSSL Vulnerability: Everything You Need to Know. Security
Intelligence. Retrieved 3 April 2018, from https://securityintelligence.com/heartbleed-
openssl-vulnerability-what-to-do-protect/
Priya, N. (2017). Comparative Study of RSA and Probabilistic Encryption/Decryption
Algorithms. International Journal Of Engineering And Computer Science.
http://dx.doi.org/10.18535/ijecs/v6i1.04
10
10
Poulin, C. (2014). Heartbleed OpenSSL Vulnerability: Everything You Need to Know. Security
Intelligence. Retrieved 3 April 2018, from https://securityintelligence.com/heartbleed-
openssl-vulnerability-what-to-do-protect/
Priya, N. (2017). Comparative Study of RSA and Probabilistic Encryption/Decryption
Algorithms. International Journal Of Engineering And Computer Science.
http://dx.doi.org/10.18535/ijecs/v6i1.04
10
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.