SBM4304 Information Security Report: Analysis of Threats and Solutions
VerifiedAdded on 2023/06/04
|13
|3335
|174
Report
AI Summary
This report provides a comprehensive analysis of information security threats and solutions, focusing on the Vend organization. It begins by exploring the working mechanisms of ransomware and suggests three tools to combat such attacks. The report then delves into the vulnerabilities of network routers and switches, discussing three types of threats that can compromise these devices. It emphasizes the importance of web service reliability and employee data confidentiality. The report also addresses operational, hardware, software, project, data, and compliance risks. Furthermore, it covers email server security using DKIM and reverse DNS. The impact of human factors on security is also discussed, along with the significance of log records and various network security measures such as VPNs, firewalls, SSL encryption, MDM, and behavioral analytics. This report provides a detailed overview of the key aspects of information security and offers recommendations for maintaining a robust security posture.

Running head: INFORMATION SECURITY
Information Security
Name of the Student
Name of the University
Author Note
Information Security
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2INFORMATION SECURITY
Table of Contents
Introduction....................................................................................................................3
Common Malwares and Ransomwares..........................................................................3
Conclusion......................................................................................................................8
Recommendation............................................................................................................9
Table of Contents
Introduction....................................................................................................................3
Common Malwares and Ransomwares..........................................................................3
Conclusion......................................................................................................................8
Recommendation............................................................................................................9

3INFORMATION SECURITY
Introduction
The Vend is one of the major organisation is the Australia which deals with many of
the modern technological marvels like the cloud based point of services, ecommerce business
help, POS software management, investment management and others. Thus it can be said the
Vend is one of the leading organisation which helps many of the customers in the process
ensuring proper technological supports (Feizollah et al., 2015). One of the most important
thing that is to be done by the organization is to keep the data of customer safe and hence
there is a need to maintain proper security features and essentials. This paper introduces us to
major technical faults that can hamper the normal working of the organisation and how these
can affect the clients and the customers. The paper discusses about the major malwares that
can affect the organisation and how these can be overcome. Further, the paper explains the
major threats to the switches and the routers that are used in the organisation and how this
can be easily overcome. Further, ways of server maintenance and maintaining the integrity
and confidentiality of the employees are also a important part of the paper. Lastly the paper
proposed some of the long terms network security terms are also explained in the paper.
Common Malwares and Ransomwares.
The malwares and the ransomewares are the computer programs that are designed for
the purpose of harming the system and servers of the victim in order to disrupt or damage or
to gain personal information from the systems (Sharma & Sahay, 2014). While the
Ransomewares are designed in such a way that it enter the host computer access private
information and in exchange of the information ask for ransomed. The ransomewares uses the
technology of encryptions for the process of affecting the computers. These are some of the
most dangerous forms of the malwares that effect the normal working of the organisation and
can lead to disastrous effects.
Introduction
The Vend is one of the major organisation is the Australia which deals with many of
the modern technological marvels like the cloud based point of services, ecommerce business
help, POS software management, investment management and others. Thus it can be said the
Vend is one of the leading organisation which helps many of the customers in the process
ensuring proper technological supports (Feizollah et al., 2015). One of the most important
thing that is to be done by the organization is to keep the data of customer safe and hence
there is a need to maintain proper security features and essentials. This paper introduces us to
major technical faults that can hamper the normal working of the organisation and how these
can affect the clients and the customers. The paper discusses about the major malwares that
can affect the organisation and how these can be overcome. Further, the paper explains the
major threats to the switches and the routers that are used in the organisation and how this
can be easily overcome. Further, ways of server maintenance and maintaining the integrity
and confidentiality of the employees are also a important part of the paper. Lastly the paper
proposed some of the long terms network security terms are also explained in the paper.
Common Malwares and Ransomwares.
The malwares and the ransomewares are the computer programs that are designed for
the purpose of harming the system and servers of the victim in order to disrupt or damage or
to gain personal information from the systems (Sharma & Sahay, 2014). While the
Ransomewares are designed in such a way that it enter the host computer access private
information and in exchange of the information ask for ransomed. The ransomewares uses the
technology of encryptions for the process of affecting the computers. These are some of the
most dangerous forms of the malwares that effect the normal working of the organisation and
can lead to disastrous effects.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4INFORMATION SECURITY
The working mechanism of the ransomewares are very much simple yet it affects a
user very much. The step starts when the hacker sends some ransomewares code to the victim
computer using emails, or any other methods and the source in injected to the victim’s
computer (Mercaldo & Visaggio, 2015). The ransomewares then searchers for points from
where the attack can be started. Once the point of attack is sourced, the ransomewares
exploits the vulnerability and starts the process of encryption. Once the system is encrypted,
the decryption is send to the attacker and the attacker asks for money or other information in
order to unlock the system. This is one of the most dangerous form of virus attack that can
hamper a organisations normal flow of work.
Some of the major processes and tools that can decrease the chances of these kind of attacks
are:
Using proper Antivirus software: Using an antivirus ensures that no harmful file can
enter the system and hence reduce the chances of any attack.
Using of Firewalls: Using the firewalls systems can help Vend to regulate the
incoming and the outgoing traffics (Aydogan & Sen, 2015). Hence this can reduce the
chances of any kind incoming malware effect the servers of the organisation.
Using authenticated Operating systems: The organisation must ensure that all the
machines it is having must be running in the original operating software, as pirated
versions of the OS can lead to low security features.
Threats against network
The routers and the switches are the primary components of the organisation. These
ensures that internet works well within the orgasaition without any error (Sharma &
Purohit, 2018). However there are many of the attacks that can be made in the routers that
The working mechanism of the ransomewares are very much simple yet it affects a
user very much. The step starts when the hacker sends some ransomewares code to the victim
computer using emails, or any other methods and the source in injected to the victim’s
computer (Mercaldo & Visaggio, 2015). The ransomewares then searchers for points from
where the attack can be started. Once the point of attack is sourced, the ransomewares
exploits the vulnerability and starts the process of encryption. Once the system is encrypted,
the decryption is send to the attacker and the attacker asks for money or other information in
order to unlock the system. This is one of the most dangerous form of virus attack that can
hamper a organisations normal flow of work.
Some of the major processes and tools that can decrease the chances of these kind of attacks
are:
Using proper Antivirus software: Using an antivirus ensures that no harmful file can
enter the system and hence reduce the chances of any attack.
Using of Firewalls: Using the firewalls systems can help Vend to regulate the
incoming and the outgoing traffics (Aydogan & Sen, 2015). Hence this can reduce the
chances of any kind incoming malware effect the servers of the organisation.
Using authenticated Operating systems: The organisation must ensure that all the
machines it is having must be running in the original operating software, as pirated
versions of the OS can lead to low security features.
Threats against network
The routers and the switches are the primary components of the organisation. These
ensures that internet works well within the orgasaition without any error (Sharma &
Purohit, 2018). However there are many of the attacks that can be made in the routers that
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5INFORMATION SECURITY
can affect the normal working of the organisation some of the major things that can affect
the normal working of the switches and the routers are:
Session hijacking: The sessional hacking can happen when a hacker falsely
inserts a falsified IP address in the router in order to access information.
Masquerading: Masquerade outbreaks arise when an attacker deploys IP
packets to falsify IP addresses (Takeuchi, Sakai & Fukumoto, 2018 ).
Masquerades are used to gain illicit access or to inject counterfeit data into a
network.
Routing protocol attacks: The Routing protocol attacks or the RIP attacks
where a hacker forges RIP routing updates to a router instead of the original
router and misuse the data.
IP fragmentation attacks: The attacks are done to bypass the router traffic data
instead of filtering (Lee et al., 2017). Usually, packet filters are only applied to
the non-fragments and the initial fragment of an IP packet because they
contain both Layer 3 and Layer 4 information that the packet filters can match
to a "permit" or "deny" action.
The web services are one of the major thing that must be ensured in order to smooth
flow of the working of the organization. The web services can be explained as a generic and
open model that helps in ensuring a proper and sacred web delivery service over the web. It
helps in the process to guarantee a message delivery system that guarantees a proper message
delivery system (Hsieh et al., 2015). The Quality of the services is one of the most important
thing that has to be enabled. The properties that are enabled in the process of ensuring better
customer support, the following defines the QOS
Message persistence
can affect the normal working of the organisation some of the major things that can affect
the normal working of the switches and the routers are:
Session hijacking: The sessional hacking can happen when a hacker falsely
inserts a falsified IP address in the router in order to access information.
Masquerading: Masquerade outbreaks arise when an attacker deploys IP
packets to falsify IP addresses (Takeuchi, Sakai & Fukumoto, 2018 ).
Masquerades are used to gain illicit access or to inject counterfeit data into a
network.
Routing protocol attacks: The Routing protocol attacks or the RIP attacks
where a hacker forges RIP routing updates to a router instead of the original
router and misuse the data.
IP fragmentation attacks: The attacks are done to bypass the router traffic data
instead of filtering (Lee et al., 2017). Usually, packet filters are only applied to
the non-fragments and the initial fragment of an IP packet because they
contain both Layer 3 and Layer 4 information that the packet filters can match
to a "permit" or "deny" action.
The web services are one of the major thing that must be ensured in order to smooth
flow of the working of the organization. The web services can be explained as a generic and
open model that helps in ensuring a proper and sacred web delivery service over the web. It
helps in the process to guarantee a message delivery system that guarantees a proper message
delivery system (Hsieh et al., 2015). The Quality of the services is one of the most important
thing that has to be enabled. The properties that are enabled in the process of ensuring better
customer support, the following defines the QOS
Message persistence

6INFORMATION SECURITY
Message acknowledgement
Elimination of the Messages
Delivery of messages
Delivery assistance
The organisation needs to maintain a proper integrity and the confidentiality of the
employees of the organisation (Perlman et al., 2016). Confidentiality can be explained as the
process of keeping the personal data of the employees safe and secured. While integrity
means using the data only when it is required and only by the authorised personals. Thus it
has to be ensured that all the data of the employees are safe enough and are used only when
required. This is one of the major thing that has to be properly ensured in order to enhance
the companies’ name. Proper security measures must be taken to protect the data of the
customers also. The staff malign systems must be properly ensured with the help of the
services and to provide the best results to the organisations.
The organisation must be able to cope up with the upcoming threats from the
malwares that are present and are increasing with days. There is always a need to prioritise
the threats that are related to the systems and the security (Beberlein et al., 2017). There
needs to be some of major threats issue that are related to computer security. The first thing
that is to be ensured is to ensure that all the, the security threats are:
1. Operations risks: This is one of the most important thing that is to be ensured that
there are zero operational risk.
2. Hardware risks: The organisational must ensure that all the hardware are secured
enough for the process of smooth flowing of the work.
Message acknowledgement
Elimination of the Messages
Delivery of messages
Delivery assistance
The organisation needs to maintain a proper integrity and the confidentiality of the
employees of the organisation (Perlman et al., 2016). Confidentiality can be explained as the
process of keeping the personal data of the employees safe and secured. While integrity
means using the data only when it is required and only by the authorised personals. Thus it
has to be ensured that all the data of the employees are safe enough and are used only when
required. This is one of the major thing that has to be properly ensured in order to enhance
the companies’ name. Proper security measures must be taken to protect the data of the
customers also. The staff malign systems must be properly ensured with the help of the
services and to provide the best results to the organisations.
The organisation must be able to cope up with the upcoming threats from the
malwares that are present and are increasing with days. There is always a need to prioritise
the threats that are related to the systems and the security (Beberlein et al., 2017). There
needs to be some of major threats issue that are related to computer security. The first thing
that is to be ensured is to ensure that all the, the security threats are:
1. Operations risks: This is one of the most important thing that is to be ensured that
there are zero operational risk.
2. Hardware risks: The organisational must ensure that all the hardware are secured
enough for the process of smooth flowing of the work.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7INFORMATION SECURITY
3. Software risks: Authenticated software must be used in order to get the best security
from the outside world.
4. Project risks: In specific project, risks must be analysed in a proper manner.
5. Data risks: The data must be ensured in a secured manner and chances of data loss
must be reduced.
6. Compliance & security risks: This is one of the other major thing that has be properly
analysed in order to ensure all the data must be ensured and must be kept in a secured
manner.
Availability of email servers:
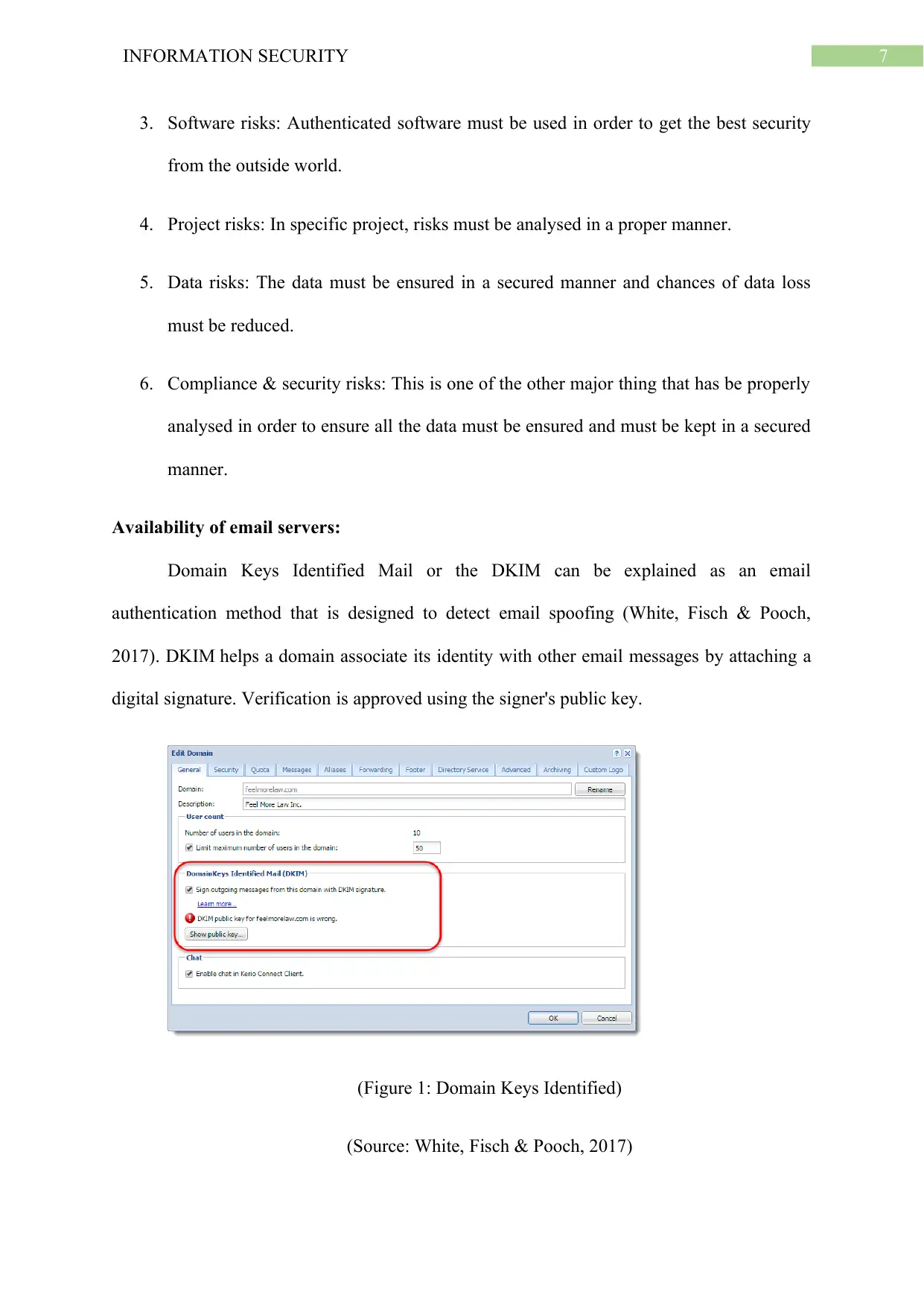
Domain Keys Identified Mail or the DKIM can be explained as an email
authentication method that is designed to detect email spoofing (White, Fisch & Pooch,
2017). DKIM helps a domain associate its identity with other email messages by attaching a
digital signature. Verification is approved using the signer's public key.
(Figure 1: Domain Keys Identified)
(Source: White, Fisch & Pooch, 2017)
3. Software risks: Authenticated software must be used in order to get the best security
from the outside world.
4. Project risks: In specific project, risks must be analysed in a proper manner.
5. Data risks: The data must be ensured in a secured manner and chances of data loss
must be reduced.
6. Compliance & security risks: This is one of the other major thing that has be properly
analysed in order to ensure all the data must be ensured and must be kept in a secured
manner.
Availability of email servers:
Domain Keys Identified Mail or the DKIM can be explained as an email
authentication method that is designed to detect email spoofing (White, Fisch & Pooch,
2017). DKIM helps a domain associate its identity with other email messages by attaching a
digital signature. Verification is approved using the signer's public key.
(Figure 1: Domain Keys Identified)
(Source: White, Fisch & Pooch, 2017)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8INFORMATION SECURITY
The other method that can be used is the reverse DNS (Acemoglu, Malekian &
Ozdaglar, 2016). The Reverse DNS is an method of resolving an IP address into a domain
name, that can help the organisation with enhancing the email servers.
(Figure 2: Reverse DNS)
(Source: White, Fisch & Pooch, 2017)
Impact of human factors
The human beings is one the main reason behind the idea of the machines, but this
humans are also one of the major reasons sometimes for incrsing the lags in the security of
the computer machines. The humans plays a major role in decreasing some of the major.
Some of the major things are direct factors and the non-direct factors. The direct factors that
are responsible Error, skill, empathy, ignorance and stress. There are some of the major
factors the decreases the security of the directly (Lévesque et al.,2018). While there are also
some of non-direct actions also which are not done intentionally but hampers the security of
the machines are the budget, culture and communication. The organisation must ensure that
these kind of problems does not happen with the employees of the organisation. The
The other method that can be used is the reverse DNS (Acemoglu, Malekian &
Ozdaglar, 2016). The Reverse DNS is an method of resolving an IP address into a domain
name, that can help the organisation with enhancing the email servers.
(Figure 2: Reverse DNS)
(Source: White, Fisch & Pooch, 2017)
Impact of human factors
The human beings is one the main reason behind the idea of the machines, but this
humans are also one of the major reasons sometimes for incrsing the lags in the security of
the computer machines. The humans plays a major role in decreasing some of the major.
Some of the major things are direct factors and the non-direct factors. The direct factors that
are responsible Error, skill, empathy, ignorance and stress. There are some of the major
factors the decreases the security of the directly (Lévesque et al.,2018). While there are also
some of non-direct actions also which are not done intentionally but hampers the security of
the machines are the budget, culture and communication. The organisation must ensure that
these kind of problems does not happen with the employees of the organisation. The

9INFORMATION SECURITY
employees must ensure that the employees works in a proper manner and is satisfied with the
work.
Logs records
The logs reports ensures all the works that are done in the organisation are stored in a
place. The log reports helps in the process of maintaining a proper and detailed information
about everything (Devendran, Shahriar & Clincy, 2015). The major purpose it can be used is
for ensuring all the works that are done in the organisation is done in proper manner and there
is no fault related to these. This also ensures that when there is any case of emergency the log
report can be audited so that there where the fault have happened can be understood
(McClain et al., 2018). The log report contains details of everything related to security
features.
Network security
Some of the major security measures that can be taken up that can help the
organisation for the process of ensuring proper security feature in future are:
1: Using of the virtual private networks: The use of the virtual private networks is one
of the major thing that can be used up for the process of ensuring security. The VPN
functions helps in keeping the organisational data private (Harmening, 2017). Also these
helps in the process of ensuring the location of the organisational private and helps in
accessing the data that are present in the network.
2. The use of the firewalls is one of the other major thing that must be implemented in
order to ensure that the incoming and the outgoing data. This can not only help in reducing
the chances of attack from the outside world but can also help in the process of ensuring that
the employees does not falsely use the data of the orgasaition.
employees must ensure that the employees works in a proper manner and is satisfied with the
work.
Logs records
The logs reports ensures all the works that are done in the organisation are stored in a
place. The log reports helps in the process of maintaining a proper and detailed information
about everything (Devendran, Shahriar & Clincy, 2015). The major purpose it can be used is
for ensuring all the works that are done in the organisation is done in proper manner and there
is no fault related to these. This also ensures that when there is any case of emergency the log
report can be audited so that there where the fault have happened can be understood
(McClain et al., 2018). The log report contains details of everything related to security
features.
Network security
Some of the major security measures that can be taken up that can help the
organisation for the process of ensuring proper security feature in future are:
1: Using of the virtual private networks: The use of the virtual private networks is one
of the major thing that can be used up for the process of ensuring security. The VPN
functions helps in keeping the organisational data private (Harmening, 2017). Also these
helps in the process of ensuring the location of the organisational private and helps in
accessing the data that are present in the network.
2. The use of the firewalls is one of the other major thing that must be implemented in
order to ensure that the incoming and the outgoing data. This can not only help in reducing
the chances of attack from the outside world but can also help in the process of ensuring that
the employees does not falsely use the data of the orgasaition.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10INFORMATION SECURITY
3. Using the SSL encryption process is one of the other major thing that can be used
for the process of proper encryption of the websites of the organisations (Husák et al., 2016).
The secured socket layers can be explained as the standard security protocol that helps in
creating secured links in between the web servers and the browsers.
4: Mobile Device management: The mobile technology is the most growing
technology in the world. It can help the organisation with the proper management of the
devices though the use of the MDM software (Konidis et al., 2016). These systems can be
remotely control of the devices and enabling the process in a very swift manner.
5. Use of the Behavioural Analytics: This is a new concept that have come up with
time. This helps in studying the behaviour of a person (Henze, Sanford & Hohlfeld, 2017).
This can help the organisation is studying and properly analysing the employees of the
organisation. This can help to learn how the organizational helps in the process of ensuring
the process of acceding proper behavioural issues related to the customers.
Conclusion:
Thus concluding the topic it must be said the Vend must be ensuring proper security
details in order to enhance the customer base. As the organisation works for the purpose of
enhancing the customer supports. The orgasaition needs to ensure that all the networks has
the most advanced features for the purpose of enhancing the security in the servers. The
organisational data is one of the most important data and in order to ensure smooth flow of
the work there needs to be a secured experience for the customers. The organisation needs to
ensure that necessary steps are taken in order to reduce the chances of any malware attack or
any ransomewares attack. Proper security features are to be ensured.
Recommendation:
3. Using the SSL encryption process is one of the other major thing that can be used
for the process of proper encryption of the websites of the organisations (Husák et al., 2016).
The secured socket layers can be explained as the standard security protocol that helps in
creating secured links in between the web servers and the browsers.
4: Mobile Device management: The mobile technology is the most growing
technology in the world. It can help the organisation with the proper management of the
devices though the use of the MDM software (Konidis et al., 2016). These systems can be
remotely control of the devices and enabling the process in a very swift manner.
5. Use of the Behavioural Analytics: This is a new concept that have come up with
time. This helps in studying the behaviour of a person (Henze, Sanford & Hohlfeld, 2017).
This can help the organisation is studying and properly analysing the employees of the
organisation. This can help to learn how the organizational helps in the process of ensuring
the process of acceding proper behavioural issues related to the customers.
Conclusion:
Thus concluding the topic it must be said the Vend must be ensuring proper security
details in order to enhance the customer base. As the organisation works for the purpose of
enhancing the customer supports. The orgasaition needs to ensure that all the networks has
the most advanced features for the purpose of enhancing the security in the servers. The
organisational data is one of the most important data and in order to ensure smooth flow of
the work there needs to be a secured experience for the customers. The organisation needs to
ensure that necessary steps are taken in order to reduce the chances of any malware attack or
any ransomewares attack. Proper security features are to be ensured.
Recommendation:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11INFORMATION SECURITY
Some of the major recommendations to be ensure that all the works must be done in a
secured manner. The organisation must ensure that all the security features are present in
order to ensure proper support to the customers. The organisation must monitor all the data
that are present in the organisation, Proper use of the modern technology is one of the other
major thing that is to be ensured. Using proper Antivirus software, Using of Firewalls, Using
authenticated Operating systems must be ensured in order to obtain maximum security. The
use of the technologies like the Artificial Intelligence, Big data can help the organization in
gaining more customers and increasing customer supports.
References
Acemoglu, D., Malekian, A., & Ozdaglar, A. (2016). Network security and
contagion. Journal of Economic Theory, 166, 536-585.
Aydogan, E., & Sen, S. (2015, April). Automatic generation of mobile malwares using
genetic programming. In European conference on the applications of evolutionary
computation(pp. 745-756). Springer, Cham.
Beberlein, L. T., Dias, G., Levitt, K. N., Mukherjee, B., & Wood, J. (2017). Network attacks
and an Ethernet-based network security monitor.
Devendran, V. K., Shahriar, H., & Clincy, V. (2015). A comparative study of email forensic
tools. Journal of Information Security, 6(2), 111.
Feizollah, A., Anuar, N. B., Salleh, R., & Amalina, F. (2015). Comparative Evaluation of
Ensemble Learning and Supervised Learning in Android Malwares Using Network-
Some of the major recommendations to be ensure that all the works must be done in a
secured manner. The organisation must ensure that all the security features are present in
order to ensure proper support to the customers. The organisation must monitor all the data
that are present in the organisation, Proper use of the modern technology is one of the other
major thing that is to be ensured. Using proper Antivirus software, Using of Firewalls, Using
authenticated Operating systems must be ensured in order to obtain maximum security. The
use of the technologies like the Artificial Intelligence, Big data can help the organization in
gaining more customers and increasing customer supports.
References
Acemoglu, D., Malekian, A., & Ozdaglar, A. (2016). Network security and
contagion. Journal of Economic Theory, 166, 536-585.
Aydogan, E., & Sen, S. (2015, April). Automatic generation of mobile malwares using
genetic programming. In European conference on the applications of evolutionary
computation(pp. 745-756). Springer, Cham.
Beberlein, L. T., Dias, G., Levitt, K. N., Mukherjee, B., & Wood, J. (2017). Network attacks
and an Ethernet-based network security monitor.
Devendran, V. K., Shahriar, H., & Clincy, V. (2015). A comparative study of email forensic
tools. Journal of Information Security, 6(2), 111.
Feizollah, A., Anuar, N. B., Salleh, R., & Amalina, F. (2015). Comparative Evaluation of
Ensemble Learning and Supervised Learning in Android Malwares Using Network-

12INFORMATION SECURITY
Based Analysis. In Advanced Computer and Communication Engineering
Technology (pp. 1025-1035). Springer, Cham.
Harmening, J. T. (2017). Virtual private networks. In Computer and Information Security
Handbook (Third Edition) (pp. 843-856).
Henze, M., Sanford, M. P., & Hohlfeld, O. (2017, June). Veiled in clouds? Assessing the
prevalence of cloud computing in the email landscape. In Network Traffic
Measurement and Analysis Conference (TMA), 2017 (pp. 1-9). IEEE.
Hsieh, W. C., Wu, C. C., & Kao, Y. W. (2015, September). A study of android malware
detection technology evolution. In Security Technology (ICCST), 2015 International
Carnahan Conference on (pp. 135-140). IEEE.
Husák, M., Čermák, M., Jirsík, T., & Čeleda, P. (2016). HTTPS traffic analysis and client
identification using passive SSL/TLS fingerprinting. EURASIP Journal on
Information Security, 2016(1), 6.
Konidis, E., Kokkinos, P., & Varvarigos, E. (2016, December). Evaluating Traffic
Redirection Mechanisms for High Availability Servers. In Globecom Workshops (GC
Wkshps), 2016 IEEE (pp. 1-5). IEEE.
Lee, Y., & Spring, N. (2017, November). Identifying and Analyzing Broadband Internet
Reverse DNS Names. In Proceedings of the 13th International Conference on
emerging Networking EXperiments and Technologies (pp. 35-40). ACM.
Lee, Y., & Spring, N. (2017, November). Identifying and Analyzing Broadband Internet
Reverse DNS Names. In Proceedings of the 13th International Conference on
emerging Networking EXperiments and Technologies (pp. 35-40). ACM.
Based Analysis. In Advanced Computer and Communication Engineering
Technology (pp. 1025-1035). Springer, Cham.
Harmening, J. T. (2017). Virtual private networks. In Computer and Information Security
Handbook (Third Edition) (pp. 843-856).
Henze, M., Sanford, M. P., & Hohlfeld, O. (2017, June). Veiled in clouds? Assessing the
prevalence of cloud computing in the email landscape. In Network Traffic
Measurement and Analysis Conference (TMA), 2017 (pp. 1-9). IEEE.
Hsieh, W. C., Wu, C. C., & Kao, Y. W. (2015, September). A study of android malware
detection technology evolution. In Security Technology (ICCST), 2015 International
Carnahan Conference on (pp. 135-140). IEEE.
Husák, M., Čermák, M., Jirsík, T., & Čeleda, P. (2016). HTTPS traffic analysis and client
identification using passive SSL/TLS fingerprinting. EURASIP Journal on
Information Security, 2016(1), 6.
Konidis, E., Kokkinos, P., & Varvarigos, E. (2016, December). Evaluating Traffic
Redirection Mechanisms for High Availability Servers. In Globecom Workshops (GC
Wkshps), 2016 IEEE (pp. 1-5). IEEE.
Lee, Y., & Spring, N. (2017, November). Identifying and Analyzing Broadband Internet
Reverse DNS Names. In Proceedings of the 13th International Conference on
emerging Networking EXperiments and Technologies (pp. 35-40). ACM.
Lee, Y., & Spring, N. (2017, November). Identifying and Analyzing Broadband Internet
Reverse DNS Names. In Proceedings of the 13th International Conference on
emerging Networking EXperiments and Technologies (pp. 35-40). ACM.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





