Charles Sturt University: Security of Information in Workplace Ethics
VerifiedAdded on 2023/06/09
|9
|2709
|268
Essay
AI Summary
This essay from Charles Sturt University analyzes the ethical dimensions of workplace information security, focusing on a company, ABC. It explores ethical dilemmas from professional, philosophical, and sociological perspectives. The professional perspective examines manual data handling, employee loyalty, and brand image concerns. The philosophical viewpoint addresses customer dissatisfaction, data leakage, client loyalty, the impact of social media, and customer anger. The sociological perspective covers data breaches, access control, social influence, and the use of big data. The essay uses various references to support its arguments and includes a marking sheet outlining the criteria for evaluation.

SC C M A D MA S Charles Sturt niversityHOOL OF O PUTING N TH , U
Security of information in a workplace
Assignment hree Distinct erspectives of Applied thics1: T P E
our ameY N
Student Number
Word Count: 1500
Security of information in a workplace
Assignment hree Distinct erspectives of Applied thics1: T P E
our ameY N
Student Number
Word Count: 1500
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security of information in a workplace
1. Introduction
thics can be described as a set of principles that are to be followed by anE
organization society or an individual he law of the nation does not bind these principles, . T .
Some principles might be legal according to the law of nation but it might not be ethical for
an organization organizations face various ethical dilemmas such as dilemma in decision. IT -
making security issues and many more, (Ifinedo, 2014) he dilemma that would be. T
discussed in this essay is security of information in a workplace of company A C owadaysB . N
employers are able to monitor the use of technologies like social media emails and many,
more by their workers Monitoring their activities lead to several ethical problems faced by the.
employers hese problems might be from the perspective of the profession philosophical or. T ,
sociological hese issues are mentioned in details in the discussion part of the essay. T .
2. Professional Ethics Perspectives
Manual handling of data the handling of some information is done manually in:
the A C organization he data that are manually handled in the organizationB . T
are registers that are maintained for various purposes like noting down the
number of workers in the employees collecting the resumes of new joiners,
and many more Manual handling of data may cause many ethical issues such.
as misplacing of information which leads in a mishap occurred in the,
organization (Ortmeier, 2017) his process consumes a lot of ti me which might. T ,
create a negative impact on the operations of the organization he issue faced. T
by the organization is that the data that are handled manually could be done,
through a machine but it would involve a huge amount if investment and the
manual handling crates problem for the organization.
oyalty of employees in some of the organizations employees are required toL : ,
sign a nondisclosure agreement paper his maintains a security of information. T
regarding the organizations According to the principles of this paper the. ,
employees are not allowed to share any information about the organization or
its operations to anyone (Chu, Chau & So, 2015) n some organizations they. I ,
do not have any such agreement such as the company A C he employeesB . T
might share the important information with people who do not belong to the
organization his might harm the organization in various ways and the data. T
obtained can be used for illegal purposes.
our ameY N
1. Introduction
thics can be described as a set of principles that are to be followed by anE
organization society or an individual he law of the nation does not bind these principles, . T .
Some principles might be legal according to the law of nation but it might not be ethical for
an organization organizations face various ethical dilemmas such as dilemma in decision. IT -
making security issues and many more, (Ifinedo, 2014) he dilemma that would be. T
discussed in this essay is security of information in a workplace of company A C owadaysB . N
employers are able to monitor the use of technologies like social media emails and many,
more by their workers Monitoring their activities lead to several ethical problems faced by the.
employers hese problems might be from the perspective of the profession philosophical or. T ,
sociological hese issues are mentioned in details in the discussion part of the essay. T .
2. Professional Ethics Perspectives
Manual handling of data the handling of some information is done manually in:
the A C organization he data that are manually handled in the organizationB . T
are registers that are maintained for various purposes like noting down the
number of workers in the employees collecting the resumes of new joiners,
and many more Manual handling of data may cause many ethical issues such.
as misplacing of information which leads in a mishap occurred in the,
organization (Ortmeier, 2017) his process consumes a lot of ti me which might. T ,
create a negative impact on the operations of the organization he issue faced. T
by the organization is that the data that are handled manually could be done,
through a machine but it would involve a huge amount if investment and the
manual handling crates problem for the organization.
oyalty of employees in some of the organizations employees are required toL : ,
sign a nondisclosure agreement paper his maintains a security of information. T
regarding the organizations According to the principles of this paper the. ,
employees are not allowed to share any information about the organization or
its operations to anyone (Chu, Chau & So, 2015) n some organizations they. I ,
do not have any such agreement such as the company A C he employeesB . T
might share the important information with people who do not belong to the
organization his might harm the organization in various ways and the data. T
obtained can be used for illegal purposes.
our ameY N

Security of information in a workplace
rand image the leakage of information from any source of the organizationB :
might lead in affecting the brand image of the company he customers would. T
not feel safe to purchase services or products from the organization Any.
purchase done from the organization would include fi nancial transaction (Hsu,
Shih & Hung, 2015) he customers would not agree to provide their bank. T
details for any kind of transaction because the leakage of bank details of a
customer would not only affect the organization but also the customer A.
company spends a lot of ti me in creating a good brand image and it takes hardly
fi
ve minutes to destroy it irrespective of the reason.
3. Philosophical Ethics Perspectives
Customer dissatisfaction one of the most effective ethical issues faced due to:
improper security of the organization is customer satisfaction f the personal. I
information regarding a customer were leaked by the organization through any
means would lead in customer dissatisfaction (Blythe, 2015) Dissatisfaction.
among customers would result in loosing loyal customers.
Mishaps due to leakage of information leakage of information causes mishap in:
the organization as well as among the customers his creates an ethical issue. T
in the organization (Grunwald, 2015) he leakage of data regarding customers. T
and employees might cause a problem to both of them.
Clients loyalty the loyalty of the client is affected if data regarding personal’ :
information of customers is revealed by any means Sometimes customers go.
through fi nancial transactions through their atm cards that are carried out by
the organization After transaction is over customers are given an opportunity to. ,
save their details for further use (Arnold, 2014) Most of the ti mes customers.
agree with the terms because saving the details allow them to pay directly for
the products or services enjoyed by them Access of bank details of the.
customers to an outsider would have a negative impact on the loyalty of the
clients.
se of social media use of social media in organization has become anU :
emerging trend to gain information for various purposes he use of social. T
media itself results in creating ethical dilemmas in the organization eakage of. L
information through social media creates worse ethical issues that affect the
our ameY N
rand image the leakage of information from any source of the organizationB :
might lead in affecting the brand image of the company he customers would. T
not feel safe to purchase services or products from the organization Any.
purchase done from the organization would include fi nancial transaction (Hsu,
Shih & Hung, 2015) he customers would not agree to provide their bank. T
details for any kind of transaction because the leakage of bank details of a
customer would not only affect the organization but also the customer A.
company spends a lot of ti me in creating a good brand image and it takes hardly
fi
ve minutes to destroy it irrespective of the reason.
3. Philosophical Ethics Perspectives
Customer dissatisfaction one of the most effective ethical issues faced due to:
improper security of the organization is customer satisfaction f the personal. I
information regarding a customer were leaked by the organization through any
means would lead in customer dissatisfaction (Blythe, 2015) Dissatisfaction.
among customers would result in loosing loyal customers.
Mishaps due to leakage of information leakage of information causes mishap in:
the organization as well as among the customers his creates an ethical issue. T
in the organization (Grunwald, 2015) he leakage of data regarding customers. T
and employees might cause a problem to both of them.
Clients loyalty the loyalty of the client is affected if data regarding personal’ :
information of customers is revealed by any means Sometimes customers go.
through fi nancial transactions through their atm cards that are carried out by
the organization After transaction is over customers are given an opportunity to. ,
save their details for further use (Arnold, 2014) Most of the ti mes customers.
agree with the terms because saving the details allow them to pay directly for
the products or services enjoyed by them Access of bank details of the.
customers to an outsider would have a negative impact on the loyalty of the
clients.
se of social media use of social media in organization has become anU :
emerging trend to gain information for various purposes he use of social. T
media itself results in creating ethical dilemmas in the organization eakage of. L
information through social media creates worse ethical issues that affect the
our ameY N
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Security of information in a workplace
organization and the customers as well (Gritzalis, Kandias & Stavrou, 2014).
Many customers share important information regarding the organization
through social media such as sharing about their working schedule or the
project that they are working on presently and many more his information is. T
accessible by everyone because these posts are kept public nformation. I
gathered from social media might be used for ill purpose which might harm,
the organization.
Angry customers an organization holds various categories of customers A: .
particular category of customer might be satisfied with a product or service
provided by an organization but the same product or service might not satisfy a
different category of customers Sometimes customers might get furious due to.
some problems occurred in services provided by organization (Kosinski, Matz
& Gosling, 2015) his might lead the customer in damaging the image of. T
organization by posting the problems on their site or on the official site of the
organization utsiders might take advantage of this and damage the image as. O
well as the customer base of the organization.
4. Sociological/Descriptive Ethics Perspectives
Data breaches official site of the organizations often ask various security questions:
to the users while logging in to their site hese questions are used when the. T
user losses or forgets his password his is done in order to recognize. T
weather the user is the one who he claims to be rganizations follow these. O
steps for protecting the personal details of their customers (Chang, Liu & Lin,
2015) he ethical issue here is that the security questions are asked by. T
website of the organization in order to maintain privacy of their account and
the website saves this information to authenticate the user later f data breach. I
takes place this information might be stolen and the account of the customer,
might be used for ill purposes.
Access control most of the ti me organizations have various departments that:
perform their individual tasks Department that is responsible for tasks such.
as handling the personal information of the customers looking after whether,
the organization is operating well or deals with fi nancial transactions done by the
our ameY N
organization and the customers as well (Gritzalis, Kandias & Stavrou, 2014).
Many customers share important information regarding the organization
through social media such as sharing about their working schedule or the
project that they are working on presently and many more his information is. T
accessible by everyone because these posts are kept public nformation. I
gathered from social media might be used for ill purpose which might harm,
the organization.
Angry customers an organization holds various categories of customers A: .
particular category of customer might be satisfied with a product or service
provided by an organization but the same product or service might not satisfy a
different category of customers Sometimes customers might get furious due to.
some problems occurred in services provided by organization (Kosinski, Matz
& Gosling, 2015) his might lead the customer in damaging the image of. T
organization by posting the problems on their site or on the official site of the
organization utsiders might take advantage of this and damage the image as. O
well as the customer base of the organization.
4. Sociological/Descriptive Ethics Perspectives
Data breaches official site of the organizations often ask various security questions:
to the users while logging in to their site hese questions are used when the. T
user losses or forgets his password his is done in order to recognize. T
weather the user is the one who he claims to be rganizations follow these. O
steps for protecting the personal details of their customers (Chang, Liu & Lin,
2015) he ethical issue here is that the security questions are asked by. T
website of the organization in order to maintain privacy of their account and
the website saves this information to authenticate the user later f data breach. I
takes place this information might be stolen and the account of the customer,
might be used for ill purposes.
Access control most of the ti me organizations have various departments that:
perform their individual tasks Department that is responsible for tasks such.
as handling the personal information of the customers looking after whether,
the organization is operating well or deals with fi nancial transactions done by the
our ameY N
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security of information in a workplace
customers have access to the detailed information regarding the customers.
he members of that particular department have access to this informationT
(Gritzalis, Stavrou & Kandias, 2014) his multiple access of the information. T
regarding the customers might result in leakage of data he data leakage. T
would cause great damage to the customers as well as the organization n. I
order to maintain privacy the organization should provide access of personal
information about the customers to limited number of employees ere occurs. H
an ethical issue that the limited number of employees might not be able to
handle the information of all the customers An organization holds a customer.
base of around lacks (Gritzalis, Stavrou & Kandias, 2014) A big team is.
required to handle the detailed information of customers ust couple of. J
people would not be able to do it.
Social influence the influence of social media has affected social medial: ,
stakeholders as well as the customers rganizations have been integrating. O
social media into their business for growing their customers and revenue.
his has resulted in social engagement of the employees mployees postT . E
regarding every activity in their job (Hajli & Lin, 2016) his allows the outside. T
world to get access of the whereabouts of organization he revealing of. T
internal information about operations of organization might cause harm to the
organization as well as customers ack of privacy in the social usage of. L
employees may lead to disastrous changes in the organization.
se of big data there has been huge number of privacy concerns related toU :
big data he use of big data allows organizations the right to track every. T
online activity of the customer his helps the customer to fulfill his needs by. T
not wasting much ti me (Kosinski, Matz & Gosling, 2015) nline habits reflect. O
various details regarding the personality of the user such as the type of
products preferred by the user the sites preferred by him and many more, .
Some breaches occurred in the organization s system might cause stealing of’
information related to the customers.
our ameY N
customers have access to the detailed information regarding the customers.
he members of that particular department have access to this informationT
(Gritzalis, Stavrou & Kandias, 2014) his multiple access of the information. T
regarding the customers might result in leakage of data he data leakage. T
would cause great damage to the customers as well as the organization n. I
order to maintain privacy the organization should provide access of personal
information about the customers to limited number of employees ere occurs. H
an ethical issue that the limited number of employees might not be able to
handle the information of all the customers An organization holds a customer.
base of around lacks (Gritzalis, Stavrou & Kandias, 2014) A big team is.
required to handle the detailed information of customers ust couple of. J
people would not be able to do it.
Social influence the influence of social media has affected social medial: ,
stakeholders as well as the customers rganizations have been integrating. O
social media into their business for growing their customers and revenue.
his has resulted in social engagement of the employees mployees postT . E
regarding every activity in their job (Hajli & Lin, 2016) his allows the outside. T
world to get access of the whereabouts of organization he revealing of. T
internal information about operations of organization might cause harm to the
organization as well as customers ack of privacy in the social usage of. L
employees may lead to disastrous changes in the organization.
se of big data there has been huge number of privacy concerns related toU :
big data he use of big data allows organizations the right to track every. T
online activity of the customer his helps the customer to fulfill his needs by. T
not wasting much ti me (Kosinski, Matz & Gosling, 2015) nline habits reflect. O
various details regarding the personality of the user such as the type of
products preferred by the user the sites preferred by him and many more, .
Some breaches occurred in the organization s system might cause stealing of’
information related to the customers.
our ameY N

Security of information in a workplace
5. References
Gritzalis, D., Kandias, M., Stavrou, V., & Mitrou, L. (2014). History of information: the case
of privacy and security in social media. In Proc. of the History of Information
Conference (pp. 283-310).
Arnold, D. G. (2014). Ethical theory and business. T. L. Beauchamp, & N. E. Bowie (Eds.).
Pearson.
Blythe, J. (2015). Information security in the workplace: A mixed-methods approach to
understanding and improving security behaviours (Doctoral dissertation, Northumbria
University).
Chang, S. E., Liu, A. Y., & Lin, S. (2015). Exploring privacy and trust for employee
monitoring. Industrial Management & Data Systems, 115(1), 88-106.
Chu, A. M., Chau, P. Y., & So, M. K. (2015). Explaining the misuse of information systems
resources in the workplace: A dual-process approach. Journal of business ethics,
131(1), 209-225.
Gritzalis, D., Stavrou, V., Kandias, M., & Stergiopoulos, G. (2014, March). Insider Threat:
Enhancing BPM through Social Media. In NTMS (pp. 1-6).
Grunwald, A. (2015). Technology assessment. In Encyclopedia of Information Science and
Technology, Third Edition (pp. 3998-4006). IGI Global.
Hajli, N., & Lin, X. (2016). Exploring the security of information sharing on social
networking sites: The role of perceived control of information. Journal of Business
Ethics, 133(1), 111-123.
Hsu, J. S. C., Shih, S. P., Hung, Y. W., & Lowry, P. B. (2015). The role of extra-role
behaviors and social controls in information security policy effectiveness. Information
Systems Research, 26(2), 282-300.
Ifinedo, P. (2014). Information systems security policy compliance: An empirical study of the
effects of socialisation, influence, and cognition. Information & Management, 51(1),
69-79.
our ameY N
5. References
Gritzalis, D., Kandias, M., Stavrou, V., & Mitrou, L. (2014). History of information: the case
of privacy and security in social media. In Proc. of the History of Information
Conference (pp. 283-310).
Arnold, D. G. (2014). Ethical theory and business. T. L. Beauchamp, & N. E. Bowie (Eds.).
Pearson.
Blythe, J. (2015). Information security in the workplace: A mixed-methods approach to
understanding and improving security behaviours (Doctoral dissertation, Northumbria
University).
Chang, S. E., Liu, A. Y., & Lin, S. (2015). Exploring privacy and trust for employee
monitoring. Industrial Management & Data Systems, 115(1), 88-106.
Chu, A. M., Chau, P. Y., & So, M. K. (2015). Explaining the misuse of information systems
resources in the workplace: A dual-process approach. Journal of business ethics,
131(1), 209-225.
Gritzalis, D., Stavrou, V., Kandias, M., & Stergiopoulos, G. (2014, March). Insider Threat:
Enhancing BPM through Social Media. In NTMS (pp. 1-6).
Grunwald, A. (2015). Technology assessment. In Encyclopedia of Information Science and
Technology, Third Edition (pp. 3998-4006). IGI Global.
Hajli, N., & Lin, X. (2016). Exploring the security of information sharing on social
networking sites: The role of perceived control of information. Journal of Business
Ethics, 133(1), 111-123.
Hsu, J. S. C., Shih, S. P., Hung, Y. W., & Lowry, P. B. (2015). The role of extra-role
behaviors and social controls in information security policy effectiveness. Information
Systems Research, 26(2), 282-300.
Ifinedo, P. (2014). Information systems security policy compliance: An empirical study of the
effects of socialisation, influence, and cognition. Information & Management, 51(1),
69-79.
our ameY N
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Security of information in a workplace
Kosinski, M., Matz, S. C., Gosling, S. D., Popov, V., & Stillwell, D. (2015). Facebook as a
research tool for the social sciences: Opportunities, challenges, ethical considerations,
and practical guidelines. American Psychologist, 70(6), 543.
Ortmeier, P. J. (2017). Introduction to security. Pearson.
our ameY N
Kosinski, M., Matz, S. C., Gosling, S. D., Popov, V., & Stillwell, D. (2015). Facebook as a
research tool for the social sciences: Opportunities, challenges, ethical considerations,
and practical guidelines. American Psychologist, 70(6), 543.
Ortmeier, P. J. (2017). Introduction to security. Pearson.
our ameY N
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Security of information in a workplace
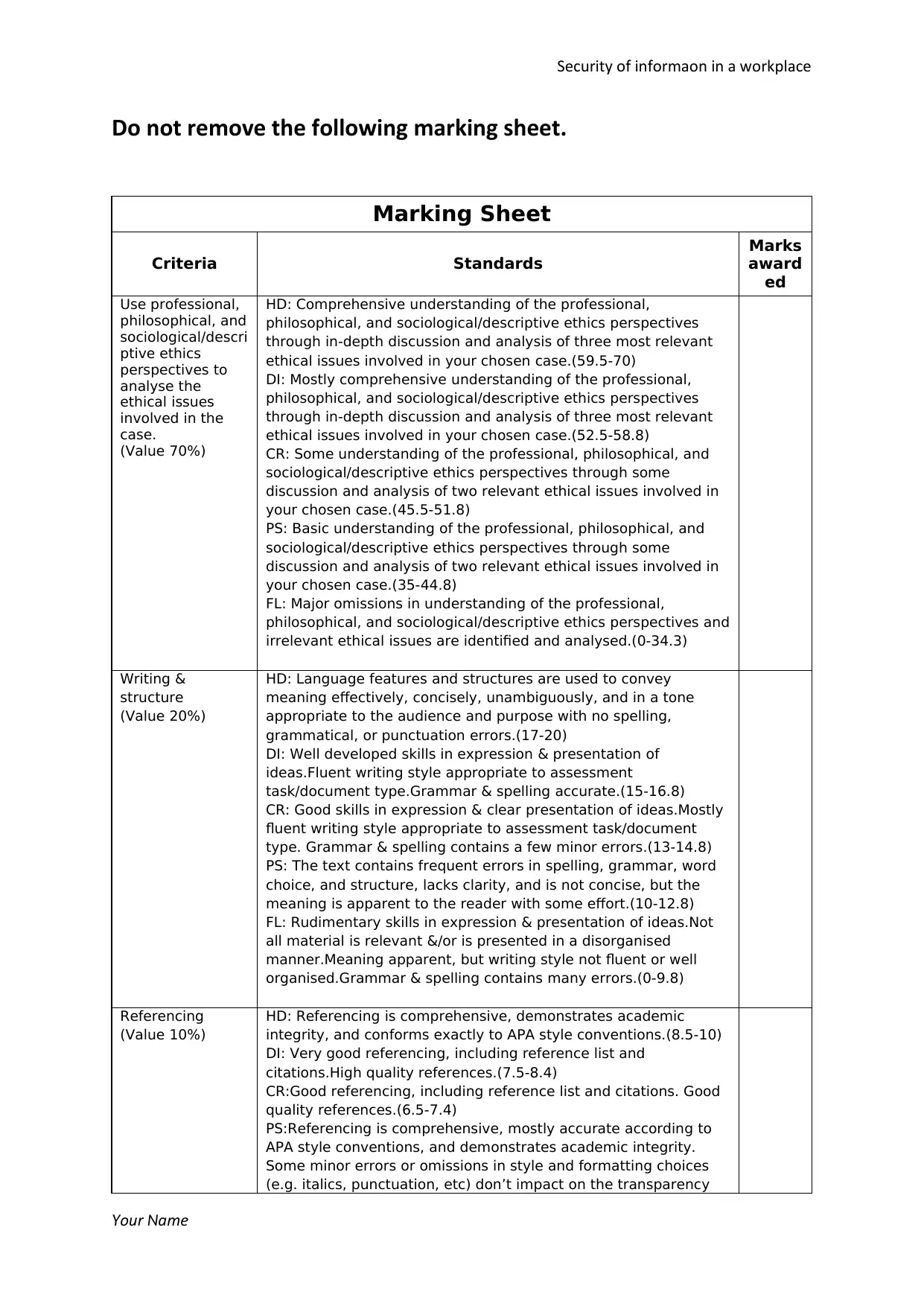
Do not remove the following marking sheet.
Marking Sheet
Criteria Standards
Marks
award
ed
Use professional,
philosophical, and
sociological/descri
ptive ethics
perspectives to
analyse the
ethical issues
involved in the
case.
(Value 70%)
HD: Comprehensive understanding of the professional,
philosophical, and sociological/descriptive ethics perspectives
through in-depth discussion and analysis of three most relevant
ethical issues involved in your chosen case.(59.5-70)
DI: Mostly comprehensive understanding of the professional,
philosophical, and sociological/descriptive ethics perspectives
through in-depth discussion and analysis of three most relevant
ethical issues involved in your chosen case.(52.5-58.8)
CR: Some understanding of the professional, philosophical, and
sociological/descriptive ethics perspectives through some
discussion and analysis of two relevant ethical issues involved in
your chosen case.(45.5-51.8)
PS: Basic understanding of the professional, philosophical, and
sociological/descriptive ethics perspectives through some
discussion and analysis of two relevant ethical issues involved in
your chosen case.(35-44.8)
FL: Major omissions in understanding of the professional,
philosophical, and sociological/descriptive ethics perspectives and
irrelevant ethical issues are identified and analysed.(0-34.3)
Writing &
structure
(Value 20%)
HD: Language features and structures are used to convey
meaning effectively, concisely, unambiguously, and in a tone
appropriate to the audience and purpose with no spelling,
grammatical, or punctuation errors.(17-20)
DI: Well developed skills in expression & presentation of
ideas.Fluent writing style appropriate to assessment
task/document type.Grammar & spelling accurate.(15-16.8)
CR: Good skills in expression & clear presentation of ideas.Mostly
fluent writing style appropriate to assessment task/document
type. Grammar & spelling contains a few minor errors.(13-14.8)
PS: The text contains frequent errors in spelling, grammar, word
choice, and structure, lacks clarity, and is not concise, but the
meaning is apparent to the reader with some effort.(10-12.8)
FL: Rudimentary skills in expression & presentation of ideas.Not
all material is relevant &/or is presented in a disorganised
manner.Meaning apparent, but writing style not fluent or well
organised.Grammar & spelling contains many errors.(0-9.8)
Referencing
(Value 10%)
HD: Referencing is comprehensive, demonstrates academic
integrity, and conforms exactly to APA style conventions.(8.5-10)
DI: Very good referencing, including reference list and
citations.High quality references.(7.5-8.4)
CR:Good referencing, including reference list and citations. Good
quality references.(6.5-7.4)
PS:Referencing is comprehensive, mostly accurate according to
APA style conventions, and demonstrates academic integrity.
Some minor errors or omissions in style and formatting choices
(e.g. italics, punctuation, etc) don’t impact on the transparency
our ameY N
Do not remove the following marking sheet.
Marking Sheet
Criteria Standards
Marks
award
ed
Use professional,
philosophical, and
sociological/descri
ptive ethics
perspectives to
analyse the
ethical issues
involved in the
case.
(Value 70%)
HD: Comprehensive understanding of the professional,
philosophical, and sociological/descriptive ethics perspectives
through in-depth discussion and analysis of three most relevant
ethical issues involved in your chosen case.(59.5-70)
DI: Mostly comprehensive understanding of the professional,
philosophical, and sociological/descriptive ethics perspectives
through in-depth discussion and analysis of three most relevant
ethical issues involved in your chosen case.(52.5-58.8)
CR: Some understanding of the professional, philosophical, and
sociological/descriptive ethics perspectives through some
discussion and analysis of two relevant ethical issues involved in
your chosen case.(45.5-51.8)
PS: Basic understanding of the professional, philosophical, and
sociological/descriptive ethics perspectives through some
discussion and analysis of two relevant ethical issues involved in
your chosen case.(35-44.8)
FL: Major omissions in understanding of the professional,
philosophical, and sociological/descriptive ethics perspectives and
irrelevant ethical issues are identified and analysed.(0-34.3)
Writing &
structure
(Value 20%)
HD: Language features and structures are used to convey
meaning effectively, concisely, unambiguously, and in a tone
appropriate to the audience and purpose with no spelling,
grammatical, or punctuation errors.(17-20)
DI: Well developed skills in expression & presentation of
ideas.Fluent writing style appropriate to assessment
task/document type.Grammar & spelling accurate.(15-16.8)
CR: Good skills in expression & clear presentation of ideas.Mostly
fluent writing style appropriate to assessment task/document
type. Grammar & spelling contains a few minor errors.(13-14.8)
PS: The text contains frequent errors in spelling, grammar, word
choice, and structure, lacks clarity, and is not concise, but the
meaning is apparent to the reader with some effort.(10-12.8)
FL: Rudimentary skills in expression & presentation of ideas.Not
all material is relevant &/or is presented in a disorganised
manner.Meaning apparent, but writing style not fluent or well
organised.Grammar & spelling contains many errors.(0-9.8)
Referencing
(Value 10%)
HD: Referencing is comprehensive, demonstrates academic
integrity, and conforms exactly to APA style conventions.(8.5-10)
DI: Very good referencing, including reference list and
citations.High quality references.(7.5-8.4)
CR:Good referencing, including reference list and citations. Good
quality references.(6.5-7.4)
PS:Referencing is comprehensive, mostly accurate according to
APA style conventions, and demonstrates academic integrity.
Some minor errors or omissions in style and formatting choices
(e.g. italics, punctuation, etc) don’t impact on the transparency
our ameY N

Security of information in a workplace
and traceability of the source, or demonstration of academic
integrity.(5-6.4)
FL: Sub-standard (or no) referencing. Poor quality (or no)
references.(0-4.9)
Total Marks
our ameY N
and traceability of the source, or demonstration of academic
integrity.(5-6.4)
FL: Sub-standard (or no) referencing. Poor quality (or no)
references.(0-4.9)
Total Marks
our ameY N
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





