Comprehensive Analysis of Information System and Risk Management
VerifiedAdded on 2020/03/16
|12
|3862
|148
Report
AI Summary
This report provides a comprehensive analysis of information system security and risk management. It begins by exploring the importance of security audits, detailing how they help identify vulnerabilities and ensure system integrity. The report then delves into various security controls, including physical, technical, and administrative measures, and their roles in protecting sensitive information. Disaster recovery planning is discussed, outlining essential steps such as devising a plan, monitoring implementation, testing, and off-site data storage. The report also covers business continuity planning, emphasizing the need for a BCP to maintain operations during unplanned events. Risk management strategies, including the use of a risk analysis matrix, are examined to determine the adequacy of IT controls. The report concludes by highlighting the significance of proactive risk assessment and mitigation in safeguarding an organization's information systems and ensuring business resilience.

Running head: Information System and Risk Management 1
Information System and Risk Management
Name
Affiliate Institutions
Information System and Risk Management
Name
Affiliate Institutions
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: Information System and Risk Management 2
Table of Contents
Introduction......................................................................................................................................3
Security audits.................................................................................................................................3
Security Controls.............................................................................................................................3
Disaster Recovery Planning.............................................................................................................4
Business Continuity Plan.................................................................................................................6
Risk Management............................................................................................................................7
Risk Analysis Matrix...................................................................................................................7
Risk Considerations in Determining the Adequacy of IT Controls.............................................7
The Information System Environment.........................................................................................8
Information System Risks Faced by the Organization.................................................................8
Risk Appetite and Tolerance........................................................................................................8
Performing a Risk Analysis.........................................................................................................8
Strategies to Mitigate Risks.........................................................................................................9
Conclusion.......................................................................................................................................9
References......................................................................................................................................10
Table of Contents
Introduction......................................................................................................................................3
Security audits.................................................................................................................................3
Security Controls.............................................................................................................................3
Disaster Recovery Planning.............................................................................................................4
Business Continuity Plan.................................................................................................................6
Risk Management............................................................................................................................7
Risk Analysis Matrix...................................................................................................................7
Risk Considerations in Determining the Adequacy of IT Controls.............................................7
The Information System Environment.........................................................................................8
Information System Risks Faced by the Organization.................................................................8
Risk Appetite and Tolerance........................................................................................................8
Performing a Risk Analysis.........................................................................................................8
Strategies to Mitigate Risks.........................................................................................................9
Conclusion.......................................................................................................................................9
References......................................................................................................................................10

Running head: Information System and Risk Management 3
Introduction
The objective of this report is to critically analyze on the system security audit, risk analysis and
management, implementation of control, disaster recovery and business continuity plans. Risk
management in any business is a very important aspect because it helps in identifying
vulnerabilities within the system and thus the organization can be able to handle them in good
time to avoid massive negative impacts. System security audit helps in making sure that there is
no abnormal transaction within the system and that its operations are consistent. Also disaster
recovery and business continuity plans are very important to any organization.
Security audits
Businesses receives benefits from the advancement of technology and information system.
However, due to existence of cybercrimes, malware, hackers, and viruses, it causes more
challenges in the business. As such strong and regular follow up is needed through frequent
security audits of information system. The main challenges to success is lack of enough
professionals and existence of frameworks that are wrongly suited. (Roebuck, 2012).
Security audits of information systems) is an examination and an independent review of system
activities, records, activities and related files. The purpose of these audits is to increase
information security level, avoid inappropriate information security structure, and optimize
security processes and safeguard effectiveness. Security is a process that is never-ending, it is
still in its early stage and needs a continuous follow-up. In addition, security audits also needs a
framework that is simple for process guidance. (Moeller, 2010).
In order to manage a successful audit, the organization should; outline objectives, select auditors
with security experiences, enhance establishment of a security baseline via annual audits, ensure
managers are involved early, ensure auditors depend on experience, and make sure that the
reports of auditors reflect the company’s risks.
Security Controls
The following are some types of security controls;
Physical Security Controls- physical security controls are machines that manage physical access
to information that is sensitive and safeguard information availability. These elements of security
required to protect assets and physical assets from being accessed by unauthorized individuals
represents potential risks. All kind of computers, computing components, and associated
facilities of communication should be viewed as spaces and assets that are sensitive and be
safeguarded accordingly. Some of the examples of physical security controls are system of
physical access, receptionist, physical protection systems, guards, physical intrusion detection
systems, door access controls, human traps, restricted areas, automatic door controls, and CCTV.
Proper management of physical security controls enhance technical and administrative controls.
(Jacobs, 2011).
Introduction
The objective of this report is to critically analyze on the system security audit, risk analysis and
management, implementation of control, disaster recovery and business continuity plans. Risk
management in any business is a very important aspect because it helps in identifying
vulnerabilities within the system and thus the organization can be able to handle them in good
time to avoid massive negative impacts. System security audit helps in making sure that there is
no abnormal transaction within the system and that its operations are consistent. Also disaster
recovery and business continuity plans are very important to any organization.
Security audits
Businesses receives benefits from the advancement of technology and information system.
However, due to existence of cybercrimes, malware, hackers, and viruses, it causes more
challenges in the business. As such strong and regular follow up is needed through frequent
security audits of information system. The main challenges to success is lack of enough
professionals and existence of frameworks that are wrongly suited. (Roebuck, 2012).
Security audits of information systems) is an examination and an independent review of system
activities, records, activities and related files. The purpose of these audits is to increase
information security level, avoid inappropriate information security structure, and optimize
security processes and safeguard effectiveness. Security is a process that is never-ending, it is
still in its early stage and needs a continuous follow-up. In addition, security audits also needs a
framework that is simple for process guidance. (Moeller, 2010).
In order to manage a successful audit, the organization should; outline objectives, select auditors
with security experiences, enhance establishment of a security baseline via annual audits, ensure
managers are involved early, ensure auditors depend on experience, and make sure that the
reports of auditors reflect the company’s risks.
Security Controls
The following are some types of security controls;
Physical Security Controls- physical security controls are machines that manage physical access
to information that is sensitive and safeguard information availability. These elements of security
required to protect assets and physical assets from being accessed by unauthorized individuals
represents potential risks. All kind of computers, computing components, and associated
facilities of communication should be viewed as spaces and assets that are sensitive and be
safeguarded accordingly. Some of the examples of physical security controls are system of
physical access, receptionist, physical protection systems, guards, physical intrusion detection
systems, door access controls, human traps, restricted areas, automatic door controls, and CCTV.
Proper management of physical security controls enhance technical and administrative controls.
(Jacobs, 2011).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: Information System and Risk Management 4
Technical Security Controls- technical security control is also referred to as logical controls and
they enhance restriction of system access. These controls involve features of software and
hardware offered in a system and enhances the security and integrity of information, operating
systems and programs.
Software components offer management capabilities access. These are the major elements of
security in a program to safeguard electronic data. An efficient logical security system offers
ways to authorize, identify, authenticate or restrict the authorized users to specific stipulated
action, for every application called on by the computer to facilitate processing of the documents
value factors that are established. (Qadir, 2016).
Administrative Security Controls- Administrative security controls is also referred to as
procedural controls. These controls are primarily policies and procedures which are structured to
guide and define action of employees in handling sensitive information of the organization. They
create awareness to people on ways of running the business and means of conducting daily
operations. Other types of administrative controls that enlighten people are the law and
regulations developed by bodies of the government.
Physical or technical security controls can enforce administrative security controls which are in
the structure of a policy. For example, security policy may suggest that computer lacking
antivirus programs cannot facilitate connection to the network, but technical control like control
software of network access looks for antivirus software when an attempt to attach to the network
by a computer is carried out. (Satzinger, Jackson & Burd, 2008).
Disaster Recovery Planning
The following are some ways to carry out disaster recovery planning;
Devising a disaster recovery plan- disaster recovery planning involves evaluation of several
scenarios and pursuing of options. As such, its undertaking may be discouraging and so it is
essential for the organization to begin with the basics and progress with other plan over time.
First, the organization should define important aspects that will enhance the running of the
business such as access of applications and email, backing up of the database, computer devices
and recovery time goals. Other components for major plan is determining the individual in the
company who announces the disaster, ways of informing the employees on the occurrence of the
disaster and communication methods to the client to restore confidence to them that the
organization can still offer services to their needs. (Broad, 2013).
Monitor implementation- after the establishment of disaster recovery plan, it is essential to
control the plan to enhance effective implementation of the components. Disaster recovery plan
should be considered as living document and requires frequent updates. In addition, progressive
monitoring that is proactive and processes remediation like backing up replication data and data
storage can lead to minimal issues of information system and less downtime in a crisis
occurrence. (Nahari & Krutz, 2011).
Technical Security Controls- technical security control is also referred to as logical controls and
they enhance restriction of system access. These controls involve features of software and
hardware offered in a system and enhances the security and integrity of information, operating
systems and programs.
Software components offer management capabilities access. These are the major elements of
security in a program to safeguard electronic data. An efficient logical security system offers
ways to authorize, identify, authenticate or restrict the authorized users to specific stipulated
action, for every application called on by the computer to facilitate processing of the documents
value factors that are established. (Qadir, 2016).
Administrative Security Controls- Administrative security controls is also referred to as
procedural controls. These controls are primarily policies and procedures which are structured to
guide and define action of employees in handling sensitive information of the organization. They
create awareness to people on ways of running the business and means of conducting daily
operations. Other types of administrative controls that enlighten people are the law and
regulations developed by bodies of the government.
Physical or technical security controls can enforce administrative security controls which are in
the structure of a policy. For example, security policy may suggest that computer lacking
antivirus programs cannot facilitate connection to the network, but technical control like control
software of network access looks for antivirus software when an attempt to attach to the network
by a computer is carried out. (Satzinger, Jackson & Burd, 2008).
Disaster Recovery Planning
The following are some ways to carry out disaster recovery planning;
Devising a disaster recovery plan- disaster recovery planning involves evaluation of several
scenarios and pursuing of options. As such, its undertaking may be discouraging and so it is
essential for the organization to begin with the basics and progress with other plan over time.
First, the organization should define important aspects that will enhance the running of the
business such as access of applications and email, backing up of the database, computer devices
and recovery time goals. Other components for major plan is determining the individual in the
company who announces the disaster, ways of informing the employees on the occurrence of the
disaster and communication methods to the client to restore confidence to them that the
organization can still offer services to their needs. (Broad, 2013).
Monitor implementation- after the establishment of disaster recovery plan, it is essential to
control the plan to enhance effective implementation of the components. Disaster recovery plan
should be considered as living document and requires frequent updates. In addition, progressive
monitoring that is proactive and processes remediation like backing up replication data and data
storage can lead to minimal issues of information system and less downtime in a crisis
occurrence. (Nahari & Krutz, 2011).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: Information System and Risk Management 5
Test disaster recovery plan- statistics shows that most organizations perform testing of their
disaster recovery system once in a year and so causing vulnerabilities to their technology and
failures in business in case a disaster occurs. A plan that is under-tested can cause more
hindrances than lack of a plan at all. Evaluation on the efficiency of disaster recovery plan in
circumstances of emergencies is achieved if frequent testing is performed more than one time
annually in conditions that are realistic by simulating situations that are applicable in real
emergency. The testing stage of the plan should contain essential verification operations to
enable the plan to persevere to events that are most disruptive.
Off-site data storage and back-up - Any disaster that attempts closing down a business makes it
hard to access data backup to the on-site. The major concern for backing up data is the safety
during and accessibility following a critical situation. If information is not moved through a safe
method and kept in data storage center that is offsite which is fully protected, then there is no
need of developing a back-up document of data that is valuable. As part of back-up solution
establishment, every organization should determine its RPO (recovery point objective). RPO is
the time between last backup availability and the occurrence of a disruption. It is based on
perseverance for data loss or data reentering. Every organization should ensure data is backed up
at least one time a day, usually overnight but the company should consider regular back-up.
(Gantz & Philpott, 2013).
Data restoration tests- use of tape back-up for several years for storage of data has been essential
to activities of IT. However, this method of back-up is not dependable. The common method that
is gaining popularity is the disk to disk systems. Back-up software and the hardware that holds
the software should be verified daily to check that completion of back-up is successful and that
there are no hanging hardware problems. With tape back-up, organizations should keep the tapes
in an accessible and secure offsite location. With disk systems, the company should perform an
offsite replication if back-up is not carried out in the offsite initially.in addition, organization
should carry out monthly restoration test to verify accomplishment of a restoration during a
disaster. (In Vacca, 2013).
Back-up desktops and laptops-organizations should ensure that the policy of storing data on the
organization’s network is followed by all employees. Users normally keep vital documents on a
local system for various reasons such as the need to work on documents while on a journey and
the need to safeguard data that is sensitive from other people. Backing up desktops and laptops
safeguard this sensitive data in situations of stolen, damaged or lost workstation. An ideal
solution is the use of automatic data protection in the laptop and desktop.
Be redundant- important elements of a company’s disaster recovery planning is enhancing
establishment of services that are redundant for all sensitive data and offering an alternate
method to access data. Disaster recovery time can be minimized to minutes instead of days if
redundant services are kept in place at an offsite location that is secure. (Stewart, Chapple &
Gibson, 2012).
Invest in data delete solutions and theft recovery for laptops- desktop computers are being
replaced by laptops. However, laptops are easily stolen or misplaced and so the need arises for
Test disaster recovery plan- statistics shows that most organizations perform testing of their
disaster recovery system once in a year and so causing vulnerabilities to their technology and
failures in business in case a disaster occurs. A plan that is under-tested can cause more
hindrances than lack of a plan at all. Evaluation on the efficiency of disaster recovery plan in
circumstances of emergencies is achieved if frequent testing is performed more than one time
annually in conditions that are realistic by simulating situations that are applicable in real
emergency. The testing stage of the plan should contain essential verification operations to
enable the plan to persevere to events that are most disruptive.
Off-site data storage and back-up - Any disaster that attempts closing down a business makes it
hard to access data backup to the on-site. The major concern for backing up data is the safety
during and accessibility following a critical situation. If information is not moved through a safe
method and kept in data storage center that is offsite which is fully protected, then there is no
need of developing a back-up document of data that is valuable. As part of back-up solution
establishment, every organization should determine its RPO (recovery point objective). RPO is
the time between last backup availability and the occurrence of a disruption. It is based on
perseverance for data loss or data reentering. Every organization should ensure data is backed up
at least one time a day, usually overnight but the company should consider regular back-up.
(Gantz & Philpott, 2013).
Data restoration tests- use of tape back-up for several years for storage of data has been essential
to activities of IT. However, this method of back-up is not dependable. The common method that
is gaining popularity is the disk to disk systems. Back-up software and the hardware that holds
the software should be verified daily to check that completion of back-up is successful and that
there are no hanging hardware problems. With tape back-up, organizations should keep the tapes
in an accessible and secure offsite location. With disk systems, the company should perform an
offsite replication if back-up is not carried out in the offsite initially.in addition, organization
should carry out monthly restoration test to verify accomplishment of a restoration during a
disaster. (In Vacca, 2013).
Back-up desktops and laptops-organizations should ensure that the policy of storing data on the
organization’s network is followed by all employees. Users normally keep vital documents on a
local system for various reasons such as the need to work on documents while on a journey and
the need to safeguard data that is sensitive from other people. Backing up desktops and laptops
safeguard this sensitive data in situations of stolen, damaged or lost workstation. An ideal
solution is the use of automatic data protection in the laptop and desktop.
Be redundant- important elements of a company’s disaster recovery planning is enhancing
establishment of services that are redundant for all sensitive data and offering an alternate
method to access data. Disaster recovery time can be minimized to minutes instead of days if
redundant services are kept in place at an offsite location that is secure. (Stewart, Chapple &
Gibson, 2012).
Invest in data delete solutions and theft recovery for laptops- desktop computers are being
replaced by laptops. However, laptops are easily stolen or misplaced and so the need arises for

Running head: Information System and Risk Management 6
the companies to safeguard data deletion and provide options of theft recovery for the laptop
users. Solutions for theft can enable organizations to remotely erase data from stolen or lost
laptops therefore avoiding release of information that is sensitive.
Business Continuity Plan
A BCP (business continuity plan) is a file that involves important information required by an
organization to continue operating during an event that is unplanned. The BCP should outline
important operations of the business, identify processes and systems to be sustained, and
describe ways of maintaining them. In addition, a BCP should account and disruption of the
business that is likely to occur. (Swanson, Bowen, Phillips, Gallup, & Lynes, 2010).
It is important for a company to have a BCP to maintain its reputation and health from risks such
as cyberattacks, natural disaster and human error. An appropriate business continuity plan
minimizes chances of cost outage. A business continuity plan needs the following; initial data
like essential contact information situated at start of the plan, process of revision management
that defines procedures of change management, scope and purpose, ways of using the plan and
instructions on the date of plan initiation, policy data, emergency management and response, step
by step processes, flow diagrams and checklists, and timeline for plan reviewing, testing and
updating.
Some of the steps of Business continuity planning include; project initiation, information of
gathering stage, featuring business impact assessment and management of risk, development of
the plan, and testing, updating and maintenance of the plan.
the companies to safeguard data deletion and provide options of theft recovery for the laptop
users. Solutions for theft can enable organizations to remotely erase data from stolen or lost
laptops therefore avoiding release of information that is sensitive.
Business Continuity Plan
A BCP (business continuity plan) is a file that involves important information required by an
organization to continue operating during an event that is unplanned. The BCP should outline
important operations of the business, identify processes and systems to be sustained, and
describe ways of maintaining them. In addition, a BCP should account and disruption of the
business that is likely to occur. (Swanson, Bowen, Phillips, Gallup, & Lynes, 2010).
It is important for a company to have a BCP to maintain its reputation and health from risks such
as cyberattacks, natural disaster and human error. An appropriate business continuity plan
minimizes chances of cost outage. A business continuity plan needs the following; initial data
like essential contact information situated at start of the plan, process of revision management
that defines procedures of change management, scope and purpose, ways of using the plan and
instructions on the date of plan initiation, policy data, emergency management and response, step
by step processes, flow diagrams and checklists, and timeline for plan reviewing, testing and
updating.
Some of the steps of Business continuity planning include; project initiation, information of
gathering stage, featuring business impact assessment and management of risk, development of
the plan, and testing, updating and maintenance of the plan.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: Information System and Risk Management 7
Figure 1: Business Continuity and Disaster recovery Planning
Risk Management
Information system controls are chosen depending on the risks they mitigate. Upon identification
of these risks it is important to develop countermeasures to respond to them. This part seeks to
outline the ideas of when and how to apply information system controls. Creating a list of
suitable controls is such a straightforward concept but nevertheless it is important to note that
each control as a specific task and not all the controls are universal in all the organizations. Each
organization has different controls depending on their needs to address risks. Strong judgement
must be used when identifying the appropriate controls as much as there are numerous advices
on the controls that are suitable. The chief audit executive (CAE) should advice the audit
committee appropriately on the internal control framework reliability and appropriateness.
Sterling, S. (2012).
It is the responsibility of the CAE to consider if there is consistency in the information system
environment of the organization, there is adequate internal control framework to allow the
organization to operate within acceptable limits of tolerance of risks.
Risk Analysis Matrix
This is a chart that shows the certainty of a risk happening and the possibility of it happening on
another. A risk matrix can be formatted in several forms including as a table where the likelihood of a
threat and its impacts are in columns. By analyzing the already existing potential threats and risks, one
can evaluate their effects and prioritize them depending on their impact. (Liu, 2012).
Figure 1: Business Continuity and Disaster recovery Planning
Risk Management
Information system controls are chosen depending on the risks they mitigate. Upon identification
of these risks it is important to develop countermeasures to respond to them. This part seeks to
outline the ideas of when and how to apply information system controls. Creating a list of
suitable controls is such a straightforward concept but nevertheless it is important to note that
each control as a specific task and not all the controls are universal in all the organizations. Each
organization has different controls depending on their needs to address risks. Strong judgement
must be used when identifying the appropriate controls as much as there are numerous advices
on the controls that are suitable. The chief audit executive (CAE) should advice the audit
committee appropriately on the internal control framework reliability and appropriateness.
Sterling, S. (2012).
It is the responsibility of the CAE to consider if there is consistency in the information system
environment of the organization, there is adequate internal control framework to allow the
organization to operate within acceptable limits of tolerance of risks.
Risk Analysis Matrix
This is a chart that shows the certainty of a risk happening and the possibility of it happening on
another. A risk matrix can be formatted in several forms including as a table where the likelihood of a
threat and its impacts are in columns. By analyzing the already existing potential threats and risks, one
can evaluate their effects and prioritize them depending on their impact. (Liu, 2012).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
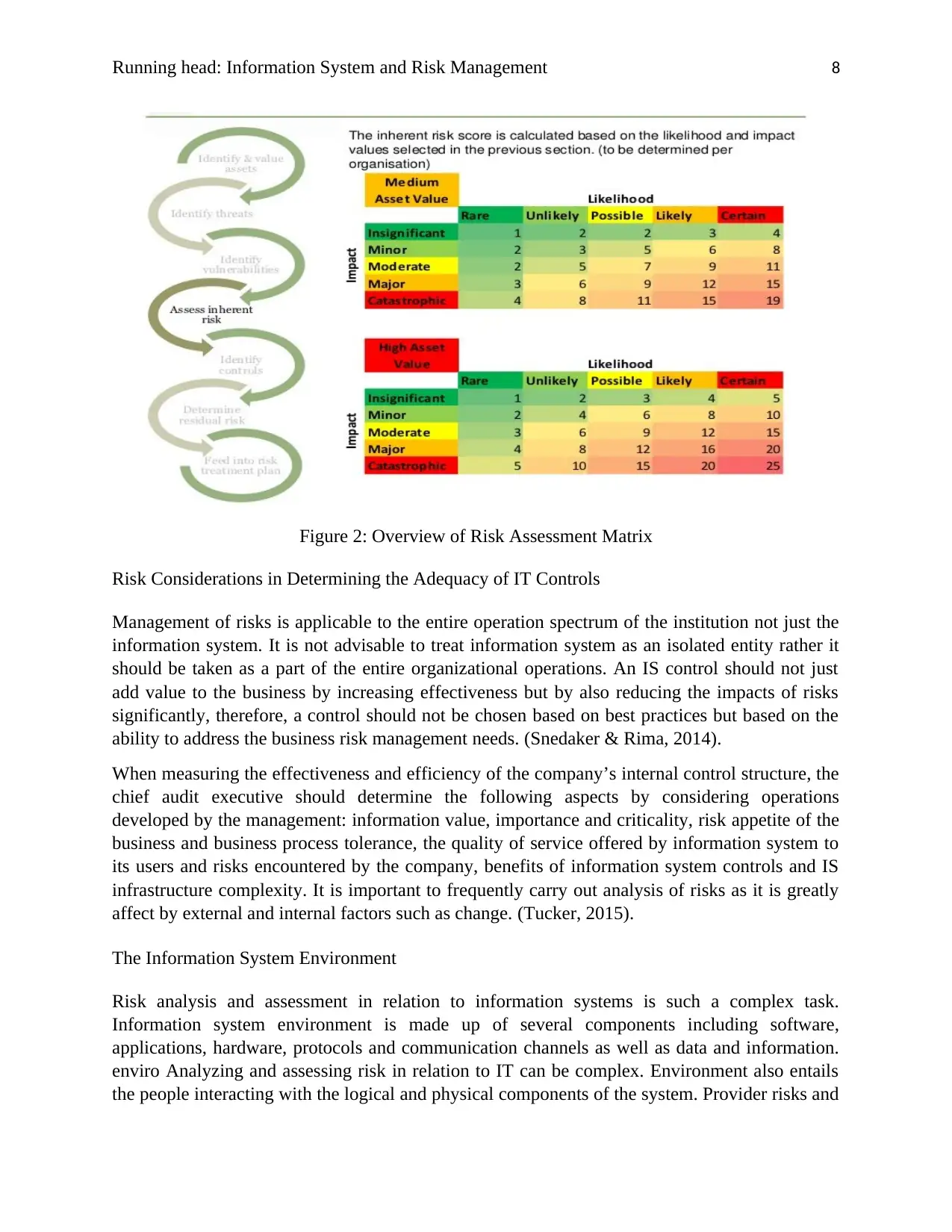
Running head: Information System and Risk Management 8
Figure 2: Overview of Risk Assessment Matrix
Risk Considerations in Determining the Adequacy of IT Controls
Management of risks is applicable to the entire operation spectrum of the institution not just the
information system. It is not advisable to treat information system as an isolated entity rather it
should be taken as a part of the entire organizational operations. An IS control should not just
add value to the business by increasing effectiveness but by also reducing the impacts of risks
significantly, therefore, a control should not be chosen based on best practices but based on the
ability to address the business risk management needs. (Snedaker & Rima, 2014).
When measuring the effectiveness and efficiency of the company’s internal control structure, the
chief audit executive should determine the following aspects by considering operations
developed by the management: information value, importance and criticality, risk appetite of the
business and business process tolerance, the quality of service offered by information system to
its users and risks encountered by the company, benefits of information system controls and IS
infrastructure complexity. It is important to frequently carry out analysis of risks as it is greatly
affect by external and internal factors such as change. (Tucker, 2015).
The Information System Environment
Risk analysis and assessment in relation to information systems is such a complex task.
Information system environment is made up of several components including software,
applications, hardware, protocols and communication channels as well as data and information.
enviro Analyzing and assessing risk in relation to IT can be complex. Environment also entails
the people interacting with the logical and physical components of the system. Provider risks and
Figure 2: Overview of Risk Assessment Matrix
Risk Considerations in Determining the Adequacy of IT Controls
Management of risks is applicable to the entire operation spectrum of the institution not just the
information system. It is not advisable to treat information system as an isolated entity rather it
should be taken as a part of the entire organizational operations. An IS control should not just
add value to the business by increasing effectiveness but by also reducing the impacts of risks
significantly, therefore, a control should not be chosen based on best practices but based on the
ability to address the business risk management needs. (Snedaker & Rima, 2014).
When measuring the effectiveness and efficiency of the company’s internal control structure, the
chief audit executive should determine the following aspects by considering operations
developed by the management: information value, importance and criticality, risk appetite of the
business and business process tolerance, the quality of service offered by information system to
its users and risks encountered by the company, benefits of information system controls and IS
infrastructure complexity. It is important to frequently carry out analysis of risks as it is greatly
affect by external and internal factors such as change. (Tucker, 2015).
The Information System Environment
Risk analysis and assessment in relation to information systems is such a complex task.
Information system environment is made up of several components including software,
applications, hardware, protocols and communication channels as well as data and information.
enviro Analyzing and assessing risk in relation to IT can be complex. Environment also entails
the people interacting with the logical and physical components of the system. Provider risks and

Running head: Information System and Risk Management 9
project related weaknesses are other areas that must be considered. Risks related to project
includes insufficient resources, technical skills, budget among others. In the case of a third party
provider, the auditor should analyze matters to do with controls, stability, audit rights, reliability,
financial strength among others. (Mouatassim & Ibenrissoul, 2015)
Information System Risks Faced by the Organization
The chief auditor should discuss IS risks with the management to make sure that there’s is vast
understanding on the technical risks that the company face and the roles of audit committee in
implementing effective and appropriate controls.
Risk Appetite and Tolerance
Having been equipped with the necessary knowledge the auditor can carry out validation of the
presence of appropriate controls and their tolerance to risks in IS. Assessment by the auditor will
engage all the company stakeholders. The assessment activities should include risk management
processes and techniques. Basically this process should begin by first identifying potential risks,
evaluating them in terms of impact they will cause to the business, identifying the appropriate
controls and finally implementation and monitoring of the efficiency of the controls. (Liu, 2012).
Performing a Risk Analysis
When carrying out a risk analysis, the team should include chief audit executive, chief risk
officer, and business representative. Some basic aspect on the table during the risk analysis
include: the information system components likely to be at risk, vulnerability evaluation, impact
to the business if the risk/ threat occurs, frequency of risk occurrence, what should be done to
minimize risks, the cost implications to this effect and efficiency of response strategies.
(Karmakar, Simonovic, Peck & Black, 2010).
Strategies to Mitigate Risks
Sometimes it may not be necessary to implement controls upon identification and evaluation of
risks because their impact is so minute and implementing controls to them may be costly. Below
are some of the ways to counter risks:
First accept the existence of risks. Some threats have very minimal impact on the information
systems and thus sometimes accepting the risk will help save on some costs but it is
recommended to consistently evaluate them to check that the impact does increase to a
catastrophe. (Yin, Guo & Lai, 2010).
Secondly, conduct risk elimination. If a risk is related to the vendor technology, then it would be
appropriate to replace this technology with a more enhanced one capable of eliminating such
risks.
project related weaknesses are other areas that must be considered. Risks related to project
includes insufficient resources, technical skills, budget among others. In the case of a third party
provider, the auditor should analyze matters to do with controls, stability, audit rights, reliability,
financial strength among others. (Mouatassim & Ibenrissoul, 2015)
Information System Risks Faced by the Organization
The chief auditor should discuss IS risks with the management to make sure that there’s is vast
understanding on the technical risks that the company face and the roles of audit committee in
implementing effective and appropriate controls.
Risk Appetite and Tolerance
Having been equipped with the necessary knowledge the auditor can carry out validation of the
presence of appropriate controls and their tolerance to risks in IS. Assessment by the auditor will
engage all the company stakeholders. The assessment activities should include risk management
processes and techniques. Basically this process should begin by first identifying potential risks,
evaluating them in terms of impact they will cause to the business, identifying the appropriate
controls and finally implementation and monitoring of the efficiency of the controls. (Liu, 2012).
Performing a Risk Analysis
When carrying out a risk analysis, the team should include chief audit executive, chief risk
officer, and business representative. Some basic aspect on the table during the risk analysis
include: the information system components likely to be at risk, vulnerability evaluation, impact
to the business if the risk/ threat occurs, frequency of risk occurrence, what should be done to
minimize risks, the cost implications to this effect and efficiency of response strategies.
(Karmakar, Simonovic, Peck & Black, 2010).
Strategies to Mitigate Risks
Sometimes it may not be necessary to implement controls upon identification and evaluation of
risks because their impact is so minute and implementing controls to them may be costly. Below
are some of the ways to counter risks:
First accept the existence of risks. Some threats have very minimal impact on the information
systems and thus sometimes accepting the risk will help save on some costs but it is
recommended to consistently evaluate them to check that the impact does increase to a
catastrophe. (Yin, Guo & Lai, 2010).
Secondly, conduct risk elimination. If a risk is related to the vendor technology, then it would be
appropriate to replace this technology with a more enhanced one capable of eliminating such
risks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: Information System and Risk Management 10
Thirdly, risk sharing with vendors and partners can be an effective mitigation strategy because it
will bring about collaboration to eliminate this and because it is a collaboration then it would be
cheaper. The supplier of the information system can also perform his/ her assessment and
implement controls to these risks and updating it on the clients IS.
Finally, it is important to always manage and control risks that have been identified even after
implementing controls to counter them. Sometimes risks may outdo the controls and therefore,
monitoring the will help measure on the effectiveness of the controls in place. (Wang, Wang &
Wang, 2017).
Conclusion
By frequently carrying out system audits, risk assessment, control implementation, businesses
and organizations put themselves in a better position to safeguard its systems and creating value
for stakeholders. Thus, risk management should always be taken as a critical function in a
business to ensure business continuity. However, sometimes carrying out risk assessment will
encourage employees will ill intentions to know the weaknesses of a system and thus may use
these vulnerabilities to bring down the business or compromise its operations.
Thirdly, risk sharing with vendors and partners can be an effective mitigation strategy because it
will bring about collaboration to eliminate this and because it is a collaboration then it would be
cheaper. The supplier of the information system can also perform his/ her assessment and
implement controls to these risks and updating it on the clients IS.
Finally, it is important to always manage and control risks that have been identified even after
implementing controls to counter them. Sometimes risks may outdo the controls and therefore,
monitoring the will help measure on the effectiveness of the controls in place. (Wang, Wang &
Wang, 2017).
Conclusion
By frequently carrying out system audits, risk assessment, control implementation, businesses
and organizations put themselves in a better position to safeguard its systems and creating value
for stakeholders. Thus, risk management should always be taken as a critical function in a
business to ensure business continuity. However, sometimes carrying out risk assessment will
encourage employees will ill intentions to know the weaknesses of a system and thus may use
these vulnerabilities to bring down the business or compromise its operations.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: Information System and Risk Management 11
References
Broad, J. (2013). Risk management framework: A lab-based approach to securing information
systems. Amsterdam: Syngress, an imprint of Elsevier.
Gantz, S. D., & Philpott, D. R. (2013). FISMA and the risk management framework [recurso
electrónico]: The new practice of federal cyber security. Estados Unidos: Syngress.
In Vacca, J. R. (2013). Network and system security. Rockland, Massachusetts : Syngress.
isaster recovery. (2010). Clifton Park, NY: Cengage Learning.
Jacobs, S. (2011). Engineering information security: The application of systems engineering
concepts to achieve information assurance. Hoboken, N.J: Wiley.
Karmakar, S., Simonovic, S., Peck, A., & Black, J., (2010). "An Information System for Risk-
Vulnerability Assessment to Flood," Journal of Geographic Information System, Vol. 2
No. 3, pp. 129-146. doi: 10.4236/jgis.2010.23020.
Liu, J. (2012). Microfinance Risk Management with Work Breakdown Structure. Journal of
Financial Risk Management, 1, 38-41. doi: 10.4236/jfrm.2012.13007.
Moeller, R. R. (2010). IT audit, control, and security. Hoboken, N.J: Wiley.
Mouatassim, H., & Ibenrissoul, A. (2015) Proposal for an Implementation Methodology of Key
Risk Indicators System: Case of Investment Management Process in Moroccan Asset
Management Company. Journal of Financial Risk Management, 4, 187-205.
doi: 10.4236/jfrm.2015.43015.
Nahari, H., & Krutz, R. L. (2011). Web commerce security: Design and development.
Indianapolis, IN: Wiley.
Qadir, S. and Quadri, S. (2016) Information Availability: An Insight into the Most Important
Attribute of Information Security. Journal of Information Security, 7, 185-194.
doi: 10.4236/jis.2016.73014.
Roebuck, K. (2012). Information security audit: High-impact Strategies - What You Need to
Know: Definitions, Adoptions, Impact, Benefits, Maturity, Vendors. Dayboro: Emereo
Pub.
Satzinger, J. W., Jackson, R. B., & Burd, S. D. (2008). Systems analysis and design in a
changing world. Cambridge Mass: Course Technology.
Snedaker, S., & Rima, C. (2014). Business continuity and disaster recovery planning for IT
professionals. Waltham, MA: Syngress.
Sterling, S. (2012). Business continuity for dummies. Chichester, West Sussex: John Wiley &
Sons, Ltd.
References
Broad, J. (2013). Risk management framework: A lab-based approach to securing information
systems. Amsterdam: Syngress, an imprint of Elsevier.
Gantz, S. D., & Philpott, D. R. (2013). FISMA and the risk management framework [recurso
electrónico]: The new practice of federal cyber security. Estados Unidos: Syngress.
In Vacca, J. R. (2013). Network and system security. Rockland, Massachusetts : Syngress.
isaster recovery. (2010). Clifton Park, NY: Cengage Learning.
Jacobs, S. (2011). Engineering information security: The application of systems engineering
concepts to achieve information assurance. Hoboken, N.J: Wiley.
Karmakar, S., Simonovic, S., Peck, A., & Black, J., (2010). "An Information System for Risk-
Vulnerability Assessment to Flood," Journal of Geographic Information System, Vol. 2
No. 3, pp. 129-146. doi: 10.4236/jgis.2010.23020.
Liu, J. (2012). Microfinance Risk Management with Work Breakdown Structure. Journal of
Financial Risk Management, 1, 38-41. doi: 10.4236/jfrm.2012.13007.
Moeller, R. R. (2010). IT audit, control, and security. Hoboken, N.J: Wiley.
Mouatassim, H., & Ibenrissoul, A. (2015) Proposal for an Implementation Methodology of Key
Risk Indicators System: Case of Investment Management Process in Moroccan Asset
Management Company. Journal of Financial Risk Management, 4, 187-205.
doi: 10.4236/jfrm.2015.43015.
Nahari, H., & Krutz, R. L. (2011). Web commerce security: Design and development.
Indianapolis, IN: Wiley.
Qadir, S. and Quadri, S. (2016) Information Availability: An Insight into the Most Important
Attribute of Information Security. Journal of Information Security, 7, 185-194.
doi: 10.4236/jis.2016.73014.
Roebuck, K. (2012). Information security audit: High-impact Strategies - What You Need to
Know: Definitions, Adoptions, Impact, Benefits, Maturity, Vendors. Dayboro: Emereo
Pub.
Satzinger, J. W., Jackson, R. B., & Burd, S. D. (2008). Systems analysis and design in a
changing world. Cambridge Mass: Course Technology.
Snedaker, S., & Rima, C. (2014). Business continuity and disaster recovery planning for IT
professionals. Waltham, MA: Syngress.
Sterling, S. (2012). Business continuity for dummies. Chichester, West Sussex: John Wiley &
Sons, Ltd.

Running head: Information System and Risk Management 12
Stewart, J. M., Chapple, M., & Gibson, D. (2012). CISSP. Hoboken: John Wiley & Sons.
Swanson, M., Bowen, P., Phillips, A. W., Gallup, D., & Lynes, D., (2010). Contingency
planning guide for federal information systems.
Tucker, E. (2015). Business continuity from preparedness to recovery: A standards-based
approach. Oxford ; Waltham, MA : Buttersworth-Heinemann
Wang, Y., Wang, W., & Wang, J. (2017). Credit Risk Management Framework for Rural
Commercial Banks in China. Journal of Financial Risk Management, 6, 48-65.
doi: 10.4236/jfrm.2017.61005.
Yin, Z., Guo, Y., & Lai, M., (2010). "The Research of Risk Management in Two Non-
Independent IT System," Journal of Service Science and Management, Vol. 3 No. 2,
2010, pp. 181-185. doi: 10.4236/jssm.2010.32023.
Stewart, J. M., Chapple, M., & Gibson, D. (2012). CISSP. Hoboken: John Wiley & Sons.
Swanson, M., Bowen, P., Phillips, A. W., Gallup, D., & Lynes, D., (2010). Contingency
planning guide for federal information systems.
Tucker, E. (2015). Business continuity from preparedness to recovery: A standards-based
approach. Oxford ; Waltham, MA : Buttersworth-Heinemann
Wang, Y., Wang, W., & Wang, J. (2017). Credit Risk Management Framework for Rural
Commercial Banks in China. Journal of Financial Risk Management, 6, 48-65.
doi: 10.4236/jfrm.2017.61005.
Yin, Z., Guo, Y., & Lai, M., (2010). "The Research of Risk Management in Two Non-
Independent IT System," Journal of Service Science and Management, Vol. 3 No. 2,
2010, pp. 181-185. doi: 10.4236/jssm.2010.32023.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





