Information Systems Audit Report: Findings on WA Government Systems
VerifiedAdded on 2023/01/11
|11
|2785
|34
Report
AI Summary
This report presents the findings of IT audits conducted on several key systems within the Western Australian government, including the Recruitment Advertisement Management System (RAMS), Horizon Power's advanced metering infrastructure, the Pensioner Rebate Scheme & Exchange (PRS & PRX), and the New Land Register-Tiles (NRL-T). The audits focused on assessing the effectiveness of IT controls in ensuring data security, integrity, and availability. Key findings reveal vulnerabilities in areas such as vendor controls, risk assessment, access control, HR security, network configuration, and user access management. The report highlights specific weaknesses, including unsupported software, inadequate encryption, insufficient user account management, and weak password configurations. Additionally, the report outlines the responsibilities of an IT auditor, encompassing ethical, professional, and legal obligations, and references the COBIT framework for IT governance. The identified issues underscore the need for improved security measures, risk management practices, and adherence to best practices to safeguard sensitive information and maintain the operational integrity of these critical government systems.

Report
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction......................................................................................................................................3
Determine audit focus as well as scope of audit report..........................................................3
Illustrate audit findings in the RAMS....................................................................................3
Show audit findings in Horizon Power..................................................................................5
Demonstrate audit findings in PRS & PRX...........................................................................5
Illustrate audit findings in NRL-T..........................................................................................6
Responsibilities of an IT Auditor...........................................................................................7
Conclusion.......................................................................................................................................9
Reefrences......................................................................................................................................10
Introduction......................................................................................................................................3
Determine audit focus as well as scope of audit report..........................................................3
Illustrate audit findings in the RAMS....................................................................................3
Show audit findings in Horizon Power..................................................................................5
Demonstrate audit findings in PRS & PRX...........................................................................5
Illustrate audit findings in NRL-T..........................................................................................6
Responsibilities of an IT Auditor...........................................................................................7
Conclusion.......................................................................................................................................9
Reefrences......................................................................................................................................10
Introduction
The examination as well as assessment of firm’s information technology policies, operations
and infrastructure is referred to as IT audit. It is liable for identification of IT controls which
protects assets as well as makes sure data integrity along with aligning their operations with their
goals (Bentley, Lambert and Wang, 2020). This report is based on different firms, audit is being
carried out via a two important steps, they are collection of knowledge and analyse current
system for internal regulations. This report comprises of audit finding of RAMS, Horizon Power,
PRS along with PRX and NRL-T. Furthermore, it will also furnish adequate knowledge related
with legal, ethical and professional liabilities of IT auditor.
Determine audit focus as well as scope of audit report.
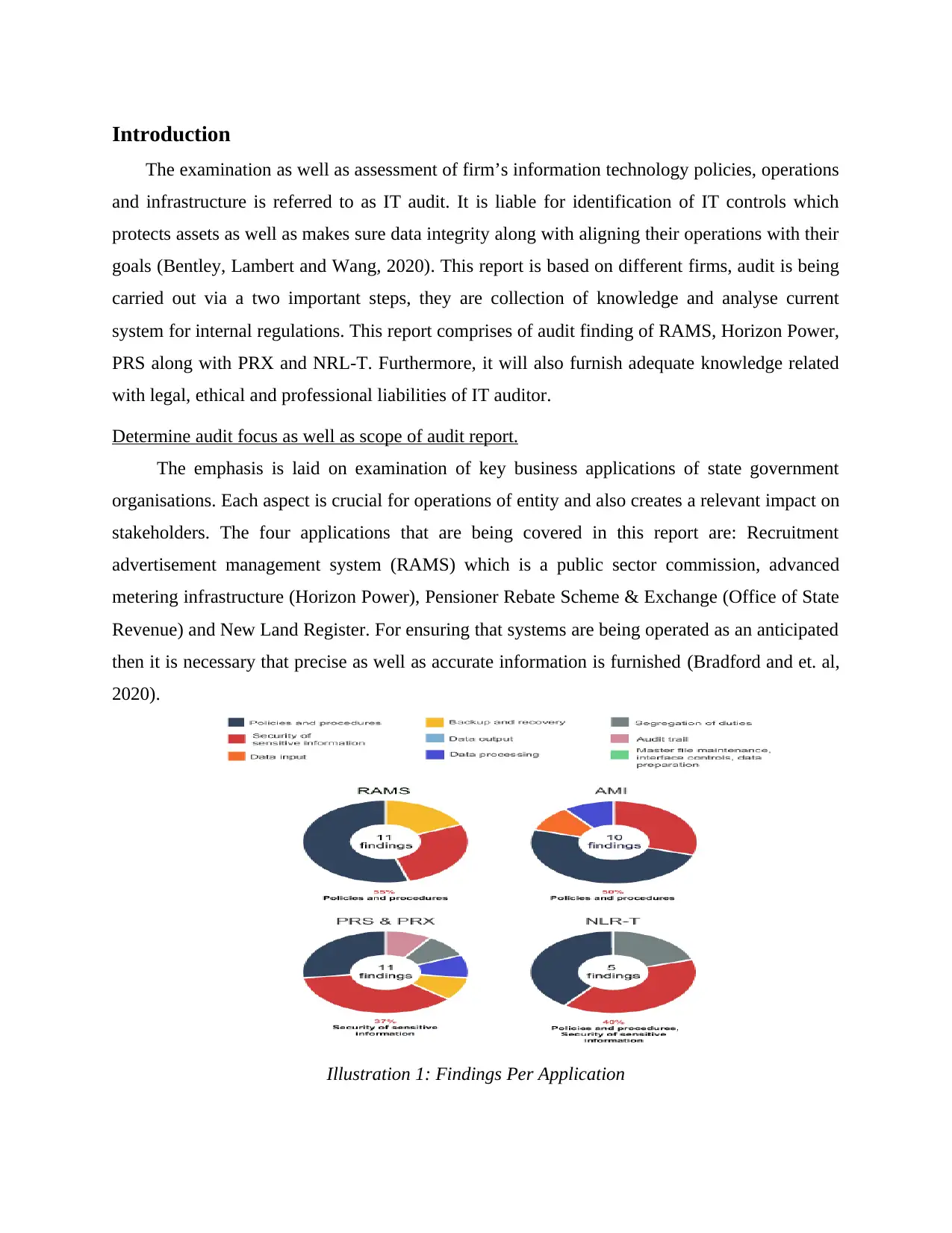
The emphasis is laid on examination of key business applications of state government
organisations. Each aspect is crucial for operations of entity and also creates a relevant impact on
stakeholders. The four applications that are being covered in this report are: Recruitment
advertisement management system (RAMS) which is a public sector commission, advanced
metering infrastructure (Horizon Power), Pensioner Rebate Scheme & Exchange (Office of State
Revenue) and New Land Register. For ensuring that systems are being operated as an anticipated
then it is necessary that precise as well as accurate information is furnished (Bradford and et. al,
2020).
Illustration 1: Findings Per Application
The examination as well as assessment of firm’s information technology policies, operations
and infrastructure is referred to as IT audit. It is liable for identification of IT controls which
protects assets as well as makes sure data integrity along with aligning their operations with their
goals (Bentley, Lambert and Wang, 2020). This report is based on different firms, audit is being
carried out via a two important steps, they are collection of knowledge and analyse current
system for internal regulations. This report comprises of audit finding of RAMS, Horizon Power,
PRS along with PRX and NRL-T. Furthermore, it will also furnish adequate knowledge related
with legal, ethical and professional liabilities of IT auditor.
Determine audit focus as well as scope of audit report.
The emphasis is laid on examination of key business applications of state government
organisations. Each aspect is crucial for operations of entity and also creates a relevant impact on
stakeholders. The four applications that are being covered in this report are: Recruitment
advertisement management system (RAMS) which is a public sector commission, advanced
metering infrastructure (Horizon Power), Pensioner Rebate Scheme & Exchange (Office of State
Revenue) and New Land Register. For ensuring that systems are being operated as an anticipated
then it is necessary that precise as well as accurate information is furnished (Bradford and et. al,
2020).
Illustration 1: Findings Per Application
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The application reviews focus on systematic processing as well as handling of data with
respect to different control categories, they are: policies & procedures, security of sensitive data,
data input, backup & recovery, data output, data processing, segregation of duties, audit trail,
masterfile maintenance, interface controls and data preparation.
For this, sample of key controls along with processes for attaining reasonable assurance
with respect to that whether applications are working as per desired standards and information
contained id secured, reliable and accessible. Testing is being carried out to identify the
weaknesses that exist within control design or the ways in which they are implemented that
enhances risk for compromise.
Illustrate audit findings in the RAMS.
WA makes use of Recruitment Advertisement Management System for managing their
employee recruitment as well as redevelopment and recording severance details (Western
Australian Auditor General’s Report, 2019). The Commission has not received or undertaken
any independent assurance in context of managed data security protocols along with this, there is
no surety with respect to availability, confidentiality and integrity. Certain findings have been
illustrated below:
Commission do not have relevant assurance on vendor controls: There is no
declaration that data in RAMS is secured and certain deficiencies have been identified in them:
Unsupported software: Some components which are used in applications do not have
support from vendors. Furthermore, 1 component did not has software updates which is
being applied for fixing security vulnerabilities.
Outdated technical specification: The documentation did not describe current application
environment. This does not ascertain that all the relevant controls are in place for
protecting applications (Bratten, Causholli and Sulcaj, 2020).
Lack of risk assessment leads to insufficient IS needs: The information security risks
were not accessed by Commission towards application and information of RAMS when contract
was made. Key conditions as well as terms were not adequately specified and their weaknesses
were:
respect to different control categories, they are: policies & procedures, security of sensitive data,
data input, backup & recovery, data output, data processing, segregation of duties, audit trail,
masterfile maintenance, interface controls and data preparation.
For this, sample of key controls along with processes for attaining reasonable assurance
with respect to that whether applications are working as per desired standards and information
contained id secured, reliable and accessible. Testing is being carried out to identify the
weaknesses that exist within control design or the ways in which they are implemented that
enhances risk for compromise.
Illustrate audit findings in the RAMS.
WA makes use of Recruitment Advertisement Management System for managing their
employee recruitment as well as redevelopment and recording severance details (Western
Australian Auditor General’s Report, 2019). The Commission has not received or undertaken
any independent assurance in context of managed data security protocols along with this, there is
no surety with respect to availability, confidentiality and integrity. Certain findings have been
illustrated below:
Commission do not have relevant assurance on vendor controls: There is no
declaration that data in RAMS is secured and certain deficiencies have been identified in them:
Unsupported software: Some components which are used in applications do not have
support from vendors. Furthermore, 1 component did not has software updates which is
being applied for fixing security vulnerabilities.
Outdated technical specification: The documentation did not describe current application
environment. This does not ascertain that all the relevant controls are in place for
protecting applications (Bratten, Causholli and Sulcaj, 2020).
Lack of risk assessment leads to insufficient IS needs: The information security risks
were not accessed by Commission towards application and information of RAMS when contract
was made. Key conditions as well as terms were not adequately specified and their weaknesses
were:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security audits: There is no peculiar right for Commission to carry out security audit
this lead them to have restricted abilities for verifying security controls. Encryption not specified: Data encryption is required for protecting sensitive
information within transit and is stored on backups but it was not specified (Che, Hope
and Langli, 2020).
Inadequate access control: Some restrictions have been identified within access controls
for minimising unauthorised access:
Inefficient user account management: Commission do not possess any procedures for
managing accounts of users even if they are highly privileged. Furthermore, user
activities are also not reviewed which may lead to misuse or unauthorised access to
information within the application.
Weak password configuration: The admin portal does not have adequate requirements for
password complexities along with this their re-use is also not restrictions. It will leads to
guessing attacks (Chen and et. al, 2020).
Furthermore, there are many aspects which have not been addressed effectively like
inadequate business continuity arrangements, vendor compliance is not being monitored for
ensuring RAMS address needs of entities, risk related with unplanned downtime and many
others.
Show audit findings in Horizon Power.
Horizon has effectual systems for detection as well as remedy errors within data with
respect to consumption readings. The velocity system is liable for generating relevant billing
variances in context of early corrective actions when they are carried out (Cohen and et. al,
2020). Along with this bills are being reviewed before they are issued to their commercial
customers. Around $1.43 billion valued errors were being corrected by Horizon in 2017-18.
These errors were due to incorrect data, rates, manual readings and system changes. Some
aspects related with this have been specified beneath:
Insufficient HR security & contractor access management: It has been identified the
new employees employed by them do not have any criminal history and have privileged access
for critical systems. But continuous background check of employees is not taken up.
Furthermore, third party contractors are not effectual as they have inadequate HR records.
this lead them to have restricted abilities for verifying security controls. Encryption not specified: Data encryption is required for protecting sensitive
information within transit and is stored on backups but it was not specified (Che, Hope
and Langli, 2020).
Inadequate access control: Some restrictions have been identified within access controls
for minimising unauthorised access:
Inefficient user account management: Commission do not possess any procedures for
managing accounts of users even if they are highly privileged. Furthermore, user
activities are also not reviewed which may lead to misuse or unauthorised access to
information within the application.
Weak password configuration: The admin portal does not have adequate requirements for
password complexities along with this their re-use is also not restrictions. It will leads to
guessing attacks (Chen and et. al, 2020).
Furthermore, there are many aspects which have not been addressed effectively like
inadequate business continuity arrangements, vendor compliance is not being monitored for
ensuring RAMS address needs of entities, risk related with unplanned downtime and many
others.
Show audit findings in Horizon Power.
Horizon has effectual systems for detection as well as remedy errors within data with
respect to consumption readings. The velocity system is liable for generating relevant billing
variances in context of early corrective actions when they are carried out (Cohen and et. al,
2020). Along with this bills are being reviewed before they are issued to their commercial
customers. Around $1.43 billion valued errors were being corrected by Horizon in 2017-18.
These errors were due to incorrect data, rates, manual readings and system changes. Some
aspects related with this have been specified beneath:
Insufficient HR security & contractor access management: It has been identified the
new employees employed by them do not have any criminal history and have privileged access
for critical systems. But continuous background check of employees is not taken up.
Furthermore, third party contractors are not effectual as they have inadequate HR records.

Horizon have outsourced near about 300 contractors and ICT functions (Western Australian
Auditor General’s Report, 2019). They have provided access to key systems for carrying out
their responsibilities which brings in high risk as they can be utilised for attacking IT systems
and networks.
System information is at risk due to errors & unintentional disclosure: Horizon
depends on manual forms for recording crucial meter installation data before information is
being entered within application (Ernstberger and et. al, 2020). When work is done manually, it
enhances risks of invalid information. Data errors will be unnoticed which will hamper integrity
of information in case validation process is not currently followed.
Inadequate network firewall configuration: The firewall is liable for separating AMI
network from corporate network of Horizon was not configured appropriately. Along with this,
software was not up to date and software updates for addressing vulnerabilities as well as
performance were not installed which leads network to be vulnerable for exploitation.
Demonstrate audit findings in PRS & PRX
They support LGs and State Revenue for processing reimbursement claims. From 2005,
State Revenue has not carried out land ownership as well as occupancy which lead to enhanced
risks of concessions that are paid for ineligible individuals. As per audit findings, some major
aspects are specified:
Irrelevant controls leads towards unauthorised usage of information: State revenue do
not have adequate security controls or user access irrespective of storing personal as well as
confidential data in PRX and PRS. The weaknesses are shown below: Inadequate access controls & reviews: Administrator privileges assist higher level of
access and are being mostly targeted by attackers. It has been found that PRX user
accounts which have high privileges are not being accessed from 12 months. These can
be utilised for carrying out malicious activities (Kang, Piercey and Trotman, 2020). Ample of users have access to sensitive data: Around 60 users are there who have
complete access to modify, delete and read pensioner eligibility reports as well as
payment files. This amplifies risks for altering data, unauthorised access and fraudulent
payments.
Auditor General’s Report, 2019). They have provided access to key systems for carrying out
their responsibilities which brings in high risk as they can be utilised for attacking IT systems
and networks.
System information is at risk due to errors & unintentional disclosure: Horizon
depends on manual forms for recording crucial meter installation data before information is
being entered within application (Ernstberger and et. al, 2020). When work is done manually, it
enhances risks of invalid information. Data errors will be unnoticed which will hamper integrity
of information in case validation process is not currently followed.
Inadequate network firewall configuration: The firewall is liable for separating AMI
network from corporate network of Horizon was not configured appropriately. Along with this,
software was not up to date and software updates for addressing vulnerabilities as well as
performance were not installed which leads network to be vulnerable for exploitation.
Demonstrate audit findings in PRS & PRX
They support LGs and State Revenue for processing reimbursement claims. From 2005,
State Revenue has not carried out land ownership as well as occupancy which lead to enhanced
risks of concessions that are paid for ineligible individuals. As per audit findings, some major
aspects are specified:
Irrelevant controls leads towards unauthorised usage of information: State revenue do
not have adequate security controls or user access irrespective of storing personal as well as
confidential data in PRX and PRS. The weaknesses are shown below: Inadequate access controls & reviews: Administrator privileges assist higher level of
access and are being mostly targeted by attackers. It has been found that PRX user
accounts which have high privileges are not being accessed from 12 months. These can
be utilised for carrying out malicious activities (Kang, Piercey and Trotman, 2020). Ample of users have access to sensitive data: Around 60 users are there who have
complete access to modify, delete and read pensioner eligibility reports as well as
payment files. This amplifies risks for altering data, unauthorised access and fraudulent
payments.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Database passwords can be easily guessed: Near about 10 database accounts have easy
passwords and around 70 accounts whose passwords are not changed for more than 10
months. Weak passwords enhanced risks for unauthorised system access.
Security vulnerabilities leaves PRS & PRX exposed: There is inadequate management of
vulnerability. It has been identified that more than 600 vulnerabilities are due to unsupported
applications furnished by third party. Furthermore, state government do not have anti-malware
software within their production servers of PRS and they do not have any processes for
identification of vulnerabilities (Bentley, Lambert and Wang, 2020).
Illustrate audit findings in NRL-T.
New Land Registry-Tiles is being utilised by Western Australian Land Information
Authority which is trading like Landgate for managing property ownership along with location
information records. For preserving security as well as dignity of data, Landgate amplifies user
access as well as knowledge protection. Furthermore, data management and framework will
intensify data analysis as well as network security (Bradford and et. al, 2020).
Alterations within land information, not reviewed: Landgate do not review transactions
for accuracy in NLR-T. In 2018, 2 land titles have been altered which are being carried out
without any relevant delegation. It leads to enhancement within inappropriate alterations or
erroneous risk to change NLR-T information.
Inadequate user access controls: There are weak access controls for user which increases
risk for unauthorised access as well as misuse of data that is being given. Some weaknesses are
specified beneath:
Inadequate isolation of duties: 2 staff members are being given excessive privileges
which assist them within carrying out end-to end land transactions. But as duties are
inadequately segregated it leads to enhancement within errors that are not being detected
and may lead to deceptive activities (Bratten, Causholli and Sulcaj, 2020). Asymmetrical access reviews of user: The rights as well as permissions of user are not
accessed regularly for confirming that they are appropriate and needed. This aids users to
have an excessive privilege that leads to inappropriate access for data.
passwords and around 70 accounts whose passwords are not changed for more than 10
months. Weak passwords enhanced risks for unauthorised system access.
Security vulnerabilities leaves PRS & PRX exposed: There is inadequate management of
vulnerability. It has been identified that more than 600 vulnerabilities are due to unsupported
applications furnished by third party. Furthermore, state government do not have anti-malware
software within their production servers of PRS and they do not have any processes for
identification of vulnerabilities (Bentley, Lambert and Wang, 2020).
Illustrate audit findings in NRL-T.
New Land Registry-Tiles is being utilised by Western Australian Land Information
Authority which is trading like Landgate for managing property ownership along with location
information records. For preserving security as well as dignity of data, Landgate amplifies user
access as well as knowledge protection. Furthermore, data management and framework will
intensify data analysis as well as network security (Bradford and et. al, 2020).
Alterations within land information, not reviewed: Landgate do not review transactions
for accuracy in NLR-T. In 2018, 2 land titles have been altered which are being carried out
without any relevant delegation. It leads to enhancement within inappropriate alterations or
erroneous risk to change NLR-T information.
Inadequate user access controls: There are weak access controls for user which increases
risk for unauthorised access as well as misuse of data that is being given. Some weaknesses are
specified beneath:
Inadequate isolation of duties: 2 staff members are being given excessive privileges
which assist them within carrying out end-to end land transactions. But as duties are
inadequately segregated it leads to enhancement within errors that are not being detected
and may lead to deceptive activities (Bratten, Causholli and Sulcaj, 2020). Asymmetrical access reviews of user: The rights as well as permissions of user are not
accessed regularly for confirming that they are appropriate and needed. This aids users to
have an excessive privilege that leads to inappropriate access for data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Lack of peripheral network penetration testing: Landgate carry out scans internal
vulnerabilities of source code as well as infrastructure. This do not test adequacy and efficiency
of controls for detecting & preventing NLR-T from external attacks as it went live. Failure of
these controls will create an impact on integrity, availability and confidentiality of land data.
Tests are essential as applications are being accessed publicly as well as they reside within
shared cloud environment which means that there are enhanced cyber threats (Che, Hope and
Langli, 2020). Thus, test must be carried out regularly for keeping in pace with those.
Responsibilities of an IT Auditor
IT auditor is liable for carrying out analysis as well as assessment of technological
infrastructure of organisation for ensuring that processes and systems executes efficiently along
as well as accurately while addressing security regulations.
Ethical responsibilities: Ethics illustrates moral principles that guide industry practices as
well as person’s behaviour (Chen and et. al, 2020). With respect to IT auditor, the code of ethics
formulates four rules they are: integrity (firms or clients anticipate that auditors uphold principles
of industry and adequate guidelines), confidentiality (information must be shared only with
authorised stakeholders), competency (continual professional development make sure that
auditors have relevant current knowledge) and objectivity (services must be carried out without
any biasness, self-servicing and impartially).
Professional responsibilities: IT auditor is liable for examination of internal IT controls,
evaluation of designs, and operational effectiveness along with identification of exposure
towards risk as well as development of adequate remediation strategies. Along with this, they are
answerable to all network or system security breaches or problems that are being faced by others
while rendering their services (Cohen and et. al, 2020).
Legal responsibilities: IT auditors need to ensure that they carry out professional services
with appropriate care by furnishing adequate knowledge levels. Furthermore, they must also
establish contractual relationship among clients. In case, IT auditor is not able carry out their
duties as per contractual agreement then it is breach of client’s contract (privity). When facts are
misrepresented in terms of financial statement for misleading another entity is denoted by harm
to third party. If IT auditor makes negligence within preparation of financial statements then it
will lead to financial loss and it is referred to as fraud.
vulnerabilities of source code as well as infrastructure. This do not test adequacy and efficiency
of controls for detecting & preventing NLR-T from external attacks as it went live. Failure of
these controls will create an impact on integrity, availability and confidentiality of land data.
Tests are essential as applications are being accessed publicly as well as they reside within
shared cloud environment which means that there are enhanced cyber threats (Che, Hope and
Langli, 2020). Thus, test must be carried out regularly for keeping in pace with those.
Responsibilities of an IT Auditor
IT auditor is liable for carrying out analysis as well as assessment of technological
infrastructure of organisation for ensuring that processes and systems executes efficiently along
as well as accurately while addressing security regulations.
Ethical responsibilities: Ethics illustrates moral principles that guide industry practices as
well as person’s behaviour (Chen and et. al, 2020). With respect to IT auditor, the code of ethics
formulates four rules they are: integrity (firms or clients anticipate that auditors uphold principles
of industry and adequate guidelines), confidentiality (information must be shared only with
authorised stakeholders), competency (continual professional development make sure that
auditors have relevant current knowledge) and objectivity (services must be carried out without
any biasness, self-servicing and impartially).
Professional responsibilities: IT auditor is liable for examination of internal IT controls,
evaluation of designs, and operational effectiveness along with identification of exposure
towards risk as well as development of adequate remediation strategies. Along with this, they are
answerable to all network or system security breaches or problems that are being faced by others
while rendering their services (Cohen and et. al, 2020).
Legal responsibilities: IT auditors need to ensure that they carry out professional services
with appropriate care by furnishing adequate knowledge levels. Furthermore, they must also
establish contractual relationship among clients. In case, IT auditor is not able carry out their
duties as per contractual agreement then it is breach of client’s contract (privity). When facts are
misrepresented in terms of financial statement for misleading another entity is denoted by harm
to third party. If IT auditor makes negligence within preparation of financial statements then it
will lead to financial loss and it is referred to as fraud.
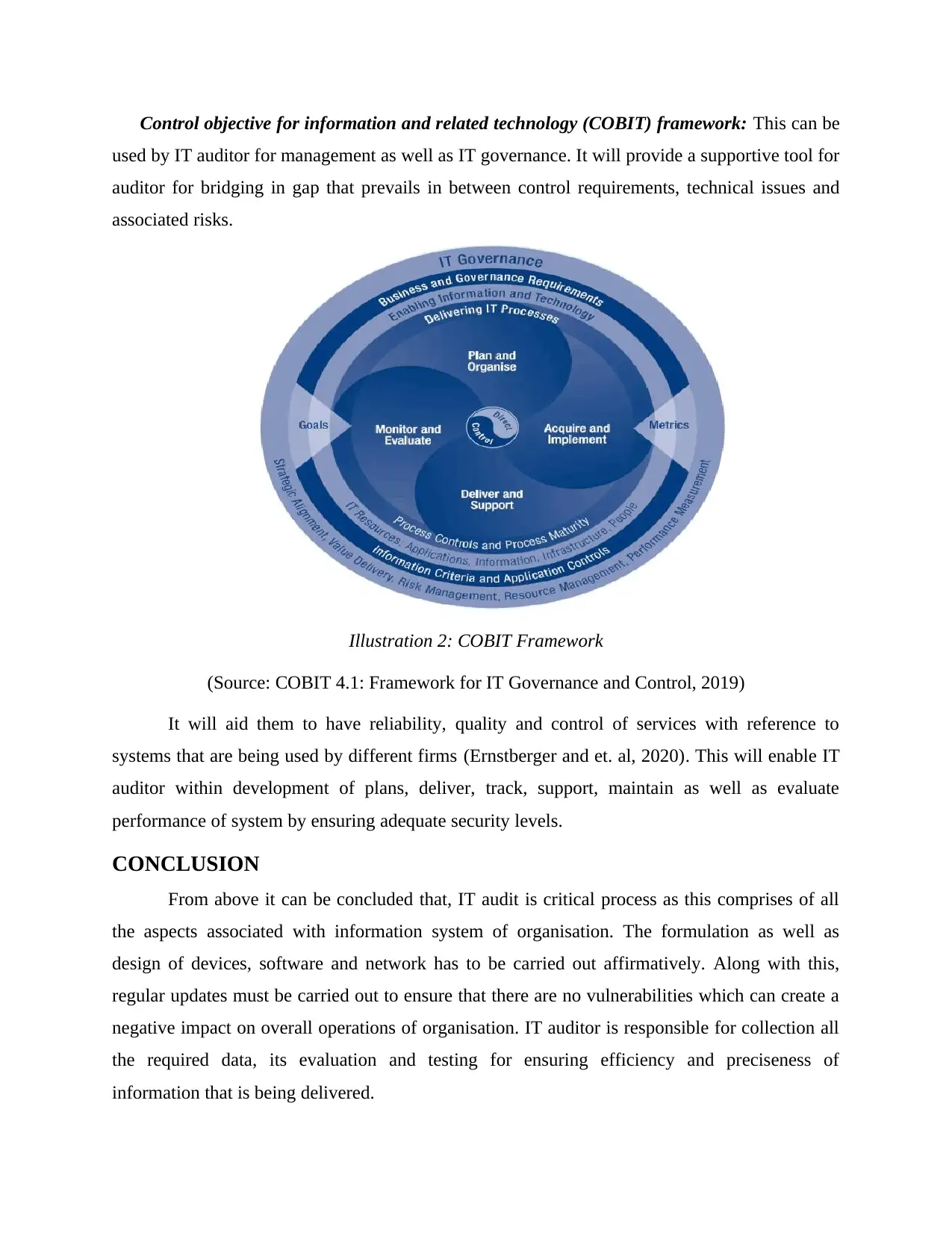
Control objective for information and related technology (COBIT) framework: This can be
used by IT auditor for management as well as IT governance. It will provide a supportive tool for
auditor for bridging in gap that prevails in between control requirements, technical issues and
associated risks.
Illustration 2: COBIT Framework
(Source: COBIT 4.1: Framework for IT Governance and Control, 2019)
It will aid them to have reliability, quality and control of services with reference to
systems that are being used by different firms (Ernstberger and et. al, 2020). This will enable IT
auditor within development of plans, deliver, track, support, maintain as well as evaluate
performance of system by ensuring adequate security levels.
CONCLUSION
From above it can be concluded that, IT audit is critical process as this comprises of all
the aspects associated with information system of organisation. The formulation as well as
design of devices, software and network has to be carried out affirmatively. Along with this,
regular updates must be carried out to ensure that there are no vulnerabilities which can create a
negative impact on overall operations of organisation. IT auditor is responsible for collection all
the required data, its evaluation and testing for ensuring efficiency and preciseness of
information that is being delivered.
used by IT auditor for management as well as IT governance. It will provide a supportive tool for
auditor for bridging in gap that prevails in between control requirements, technical issues and
associated risks.
Illustration 2: COBIT Framework
(Source: COBIT 4.1: Framework for IT Governance and Control, 2019)
It will aid them to have reliability, quality and control of services with reference to
systems that are being used by different firms (Ernstberger and et. al, 2020). This will enable IT
auditor within development of plans, deliver, track, support, maintain as well as evaluate
performance of system by ensuring adequate security levels.
CONCLUSION
From above it can be concluded that, IT audit is critical process as this comprises of all
the aspects associated with information system of organisation. The formulation as well as
design of devices, software and network has to be carried out affirmatively. Along with this,
regular updates must be carried out to ensure that there are no vulnerabilities which can create a
negative impact on overall operations of organisation. IT auditor is responsible for collection all
the required data, its evaluation and testing for ensuring efficiency and preciseness of
information that is being delivered.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REEFRENCES
Books and Journals
Bentley, J.W., Lambert, T.A. and Wang, E.Y., 2020. The Effect of Increased Audit Disclosure
on Managers' Real Operating Decisions: Evidence from Disclosing Critical Audit
Matters. The Accounting Review.
Bradford, M. and et. al, 2020. Using generalized audit software to detect material misstatements,
control deficiencies and fraud. Managerial Auditing Journal.
Bratten, B., Causholli, M. and Sulcaj, V., 2020. Overseeing the external audit function: Evidence
from audit committees’ reported activities. Available at SSRN 3314334.
Che, L., Hope, O.K. and Langli, J.C., 2020. How Big-4 firms improve audit
quality. Management Science.
Chen, J. and et. al, 2020. Does Audit Partner Workload Compression Affect Audit
Quality?. European Accounting Review, pp.1-33.
Cohen, J.R. and et. al, 2020. Audit Partners’ Judgments and Challenges in the Audit of Internal
Control over Financial Reporting. Available at SSRN 3551763.
Ernstberger, J. and et. al, 2020. Are Audit Firms' Compensation Policies Associated with Audit
Quality?. Contemporary Accounting Research, 37(1), pp.218-244.
Kang, Y.J., Piercey, M.D. and Trotman, A., 2020. Does an audit judgment rule increase or
decrease auditors' use of innovative audit procedures?. Contemporary Accounting
Research, 37(1), pp.297-321.
Online
Western Australian Auditor General’s Report. 2019. [Onlone]. Available through:
<https://audit.wa.gov.au/wp-content/uploads/2019/05/IS-Report-2019.pdf>.
Books and Journals
Bentley, J.W., Lambert, T.A. and Wang, E.Y., 2020. The Effect of Increased Audit Disclosure
on Managers' Real Operating Decisions: Evidence from Disclosing Critical Audit
Matters. The Accounting Review.
Bradford, M. and et. al, 2020. Using generalized audit software to detect material misstatements,
control deficiencies and fraud. Managerial Auditing Journal.
Bratten, B., Causholli, M. and Sulcaj, V., 2020. Overseeing the external audit function: Evidence
from audit committees’ reported activities. Available at SSRN 3314334.
Che, L., Hope, O.K. and Langli, J.C., 2020. How Big-4 firms improve audit
quality. Management Science.
Chen, J. and et. al, 2020. Does Audit Partner Workload Compression Affect Audit
Quality?. European Accounting Review, pp.1-33.
Cohen, J.R. and et. al, 2020. Audit Partners’ Judgments and Challenges in the Audit of Internal
Control over Financial Reporting. Available at SSRN 3551763.
Ernstberger, J. and et. al, 2020. Are Audit Firms' Compensation Policies Associated with Audit
Quality?. Contemporary Accounting Research, 37(1), pp.218-244.
Kang, Y.J., Piercey, M.D. and Trotman, A., 2020. Does an audit judgment rule increase or
decrease auditors' use of innovative audit procedures?. Contemporary Accounting
Research, 37(1), pp.297-321.
Online
Western Australian Auditor General’s Report. 2019. [Onlone]. Available through:
<https://audit.wa.gov.au/wp-content/uploads/2019/05/IS-Report-2019.pdf>.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





