Information Systems: Analysis of Project Failures and Big Data Impacts
VerifiedAdded on 2020/04/21
|17
|3191
|101
Report
AI Summary
This report provides a comprehensive analysis of information systems, covering project failure causes, integrated business information systems (IBIS), and the impact of big data. It examines the reasons behind IT project failures, including lack of user involvement, lengthy project timelines, inadequate requirements, scope creep, lack of change control, and insufficient testing. The report also defines IBIS, its components, advantages, and disadvantages, with a focus on flexibility, simplicity, interoperability, and modifiability, while addressing security challenges such as accidents, sabotages, disasters, theft, and hacking. Furthermore, the report explores the effects of big data on organizational performance, including changes in decision-making, risk management, and customer relationship management. The report is a valuable resource for students studying information systems and data science.

Running head: INFORMATION SYSTEMS
Information systems
Name of the student
Name of the University
Author Note
Information systems
Name of the student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SYSTEMS
Answer to question 1:
The information and communication technology is associated to an essential part of each
organization or business companies. This is also associated to the way the communication occurs
among the various entities related to each other. In addition, the use of information systems is
also associated in providing quality and value in our lives (Kerzner, 2013). For all the developed
and the developing countries, are accepting the innovations in technologies which are causing
rapid changes in every emerging fields. The use of information systems is the core operations in
any kinds of businesses. The spending amount for adopting this process is considered to be
billion dollars which have led to the adoption of information and communication processes in
companies and business organizations. However, in spite of the adopted practices in the
information sector for development and efficient advancements, their applications are
experiencing failures which is the cause for concern among various developing countries as well.
The need for adopting these innovations are increasing in a day a by day interval and the
failure rate of their implementation process is also increasing at the same rate (Burke, 2013). The
main reason for the failure of IT projects is mainly due to being unable to comply with the three
rules for project development. These are the timely delivery, meeting of budget criteria and
efficient working of them. These criteria are important and every project must meet them in
order to get an industrially approved solutions. There are various reasons for which a project
becomes unable to meet these criteria.
The first reason for a project failure is the lack of users getting involved. This reason has
been the cause for failure from a long time. Without the involvement of a user, people engaged
in a project do not feel committed to the system and thus a project gets failed (Larson & Gray,
Answer to question 1:
The information and communication technology is associated to an essential part of each
organization or business companies. This is also associated to the way the communication occurs
among the various entities related to each other. In addition, the use of information systems is
also associated in providing quality and value in our lives (Kerzner, 2013). For all the developed
and the developing countries, are accepting the innovations in technologies which are causing
rapid changes in every emerging fields. The use of information systems is the core operations in
any kinds of businesses. The spending amount for adopting this process is considered to be
billion dollars which have led to the adoption of information and communication processes in
companies and business organizations. However, in spite of the adopted practices in the
information sector for development and efficient advancements, their applications are
experiencing failures which is the cause for concern among various developing countries as well.
The need for adopting these innovations are increasing in a day a by day interval and the
failure rate of their implementation process is also increasing at the same rate (Burke, 2013). The
main reason for the failure of IT projects is mainly due to being unable to comply with the three
rules for project development. These are the timely delivery, meeting of budget criteria and
efficient working of them. These criteria are important and every project must meet them in
order to get an industrially approved solutions. There are various reasons for which a project
becomes unable to meet these criteria.
The first reason for a project failure is the lack of users getting involved. This reason has
been the cause for failure from a long time. Without the involvement of a user, people engaged
in a project do not feel committed to the system and thus a project gets failed (Larson & Gray,

2INFORMATION SYSTEMS
2013). For addressing this requirement, the senior management personnel and end-users of a
system should show more engagement on the project. This increases the time and the effort
required for handling pressures which in turn increases the priorities on these projects thereby
increasing the efficiency. Thus, the senior management must support the whole process of
project development to make it a clear priority among the personnel responsible for it.
Another reason which accounts for the failures in systematic project development is the
long time scale for a project. This causes a long scheduled time table for achieving short asks and
thus the availability and efficiency often reduces due to this. The main objective for a project
must include shorter time scale which can be used cover the whole aspect of the project in a short
time usually by dividing the key components into many (Schwalbe, 2015). Although, this
process of agile methodology is a much acceptable solution for project development, they are
said to have much disadvantages as well. However, a time scale is always made by the project
manager considering a general review of the project and not by careful evaluation. As a result the
project that is being delivered usually has short deliverables or do not meet the efficient criteria.
In extreme cases, they are also delivered late due to this problem. For addressing such problems,
the project manager or the senior management team must watch and review the requirements of a
project and allot a time scale effectively so that all the project criteria are met.
The third reason for project failures is the lack of requirements or limited access. Due to
this problem, many times it is seen that the project developers get no access for the requirements
and usually deliver a project which is way off the charts. Additionally, it have also been reported
that the project is developed without meeting any set criteria or any definitions (Fleming &
Koppelman, 2016). These are a great cause for project failures which greatly affects a system. In
extreme cases, a business loses their relationship with their clients and leads to loss of revenue
2013). For addressing this requirement, the senior management personnel and end-users of a
system should show more engagement on the project. This increases the time and the effort
required for handling pressures which in turn increases the priorities on these projects thereby
increasing the efficiency. Thus, the senior management must support the whole process of
project development to make it a clear priority among the personnel responsible for it.
Another reason which accounts for the failures in systematic project development is the
long time scale for a project. This causes a long scheduled time table for achieving short asks and
thus the availability and efficiency often reduces due to this. The main objective for a project
must include shorter time scale which can be used cover the whole aspect of the project in a short
time usually by dividing the key components into many (Schwalbe, 2015). Although, this
process of agile methodology is a much acceptable solution for project development, they are
said to have much disadvantages as well. However, a time scale is always made by the project
manager considering a general review of the project and not by careful evaluation. As a result the
project that is being delivered usually has short deliverables or do not meet the efficient criteria.
In extreme cases, they are also delivered late due to this problem. For addressing such problems,
the project manager or the senior management team must watch and review the requirements of a
project and allot a time scale effectively so that all the project criteria are met.
The third reason for project failures is the lack of requirements or limited access. Due to
this problem, many times it is seen that the project developers get no access for the requirements
and usually deliver a project which is way off the charts. Additionally, it have also been reported
that the project is developed without meeting any set criteria or any definitions (Fleming &
Koppelman, 2016). These are a great cause for project failures which greatly affects a system. In
extreme cases, a business loses their relationship with their clients and leads to loss of revenue
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SYSTEMS
made. To address these requirements, user responsible for the project must specify the clear
objectives and the developers must also clear the criteria before proceeding with their task.
The fourth reason responsible for project failures are the scope creep. A scope of a
project defines the deliverable of a project which must be present in the outcome of the project.
This is the most required deliverable and must be addressed by managers as well. However, due
to changes in the scope, project outcomes become very difficult to achieve (Walker, 2015). This
is termed as scope creep. For example, in case a company wants to build an information system
which will be able to add customer records or view them, the next scope gets changed to the
project being able to access customer data and send the data via online communications to the
customers themselves, causes changes in the scope and it becomes unable to achieve. This is an
example of scope creeps. To address these solutions, the management of the project must be
done effectively and the personnel responsible for this must identify clear objectives and set clear
timescales to achieve the required changes in criteria.
Another reason for the occurrence of failures in projects is the lack of control for changes
in the system. Although, business is changing at a rapid rate, the need for managing the changes
is a necessity. Lack of such management leads to grave amount of threats within the system
which is another cause for failures in project development. This causes a need for a short
duration of time scales and an approach that is phased to meet the necessary requirements
(Leach, 2014). The various businesses must identify and analyze the parameters of changes in
terms of effects, cost and mitigations which can be referenced in the project management
lifecycles.
made. To address these requirements, user responsible for the project must specify the clear
objectives and the developers must also clear the criteria before proceeding with their task.
The fourth reason responsible for project failures are the scope creep. A scope of a
project defines the deliverable of a project which must be present in the outcome of the project.
This is the most required deliverable and must be addressed by managers as well. However, due
to changes in the scope, project outcomes become very difficult to achieve (Walker, 2015). This
is termed as scope creep. For example, in case a company wants to build an information system
which will be able to add customer records or view them, the next scope gets changed to the
project being able to access customer data and send the data via online communications to the
customers themselves, causes changes in the scope and it becomes unable to achieve. This is an
example of scope creeps. To address these solutions, the management of the project must be
done effectively and the personnel responsible for this must identify clear objectives and set clear
timescales to achieve the required changes in criteria.
Another reason for the occurrence of failures in projects is the lack of control for changes
in the system. Although, business is changing at a rapid rate, the need for managing the changes
is a necessity. Lack of such management leads to grave amount of threats within the system
which is another cause for failures in project development. This causes a need for a short
duration of time scales and an approach that is phased to meet the necessary requirements
(Leach, 2014). The various businesses must identify and analyze the parameters of changes in
terms of effects, cost and mitigations which can be referenced in the project management
lifecycles.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SYSTEMS
The last reason for failures in project management is lack of effective testing during the
development phase of software processes. The main reason for a project to fail is due to the
presence of peer requirements which cannot be met, poor planning of the tests, lack of users with
adequate trainings and less amount of time to complete (Mir & Pinnington, 2014). To address
such requirements, the personnel responsible for the project must test the system based on actual
user reviews and update accordingly. This captures the feedbacks of the system and in turn helps
to address them in the process.
Answer to question 2:
An information system which is integrated in business operations is termed as the
Integrated Business Information System (IBIS). A business information system is defined by a
group of components which are interconnected among each other to serve the processes of any
businesses. These processes are basically the input, processing, output, storage and processing
operations which is mainly used for the conversion of data into information related products
which can then be used for planning, analysis, implementation and outcome addressing (Peppard
& Ward, 2016). The major components of this system are the people associated, hardware,
software, communications among them and the data. The people are those personnel who are the
clients and the developers of the system. Similarly, the hardware and the software are the major
devices like computers, printers or other necessary devices as well as the computer programs
which help in normal operations. The communication among these components is usually done
by utilizing networks or other wireless devices while the data is the information that is to be
stored in the systems.
The last reason for failures in project management is lack of effective testing during the
development phase of software processes. The main reason for a project to fail is due to the
presence of peer requirements which cannot be met, poor planning of the tests, lack of users with
adequate trainings and less amount of time to complete (Mir & Pinnington, 2014). To address
such requirements, the personnel responsible for the project must test the system based on actual
user reviews and update accordingly. This captures the feedbacks of the system and in turn helps
to address them in the process.
Answer to question 2:
An information system which is integrated in business operations is termed as the
Integrated Business Information System (IBIS). A business information system is defined by a
group of components which are interconnected among each other to serve the processes of any
businesses. These processes are basically the input, processing, output, storage and processing
operations which is mainly used for the conversion of data into information related products
which can then be used for planning, analysis, implementation and outcome addressing (Peppard
& Ward, 2016). The major components of this system are the people associated, hardware,
software, communications among them and the data. The people are those personnel who are the
clients and the developers of the system. Similarly, the hardware and the software are the major
devices like computers, printers or other necessary devices as well as the computer programs
which help in normal operations. The communication among these components is usually done
by utilizing networks or other wireless devices while the data is the information that is to be
stored in the systems.

5INFORMATION SYSTEMS
The integrated business information systems have been the most effective method for
business operations due to their adoptions of personal computers. This has led to the increased
efficiency of business operations along with the increase in speed and accuracy. However, there
are various disadvantages to this system mainly due to the lack of decision making process and
lack of further innovations to be applied in existing systems.
The main purpose for the acceptance of the IBIS standard is the addressing of four
factors. They are the flexibility, simplicity, interoperatibility and modifiability (Pearlson,
Saunders & Galletta, 2016). The term flexibility denotes the allotment of free access to change
from a wide range of applications for database related purposes. The various applications that
support the integrated process are the MySQL, SQL Server, Access or ORACLE. Simplicity is
another feature of the IBIS which generally implies that the use of this method does not require
much implementation. In addition, an organization or company do not need to hire employees for
tending to the applications and can be accessed immediately after purchasing. The next purpose
of the integrated business information system is the ability for interoperations. This involves the
ability to be able to use for other operations. For this purpose, the system can be imported in
other formats so that this can be used in other files or programs as well. Lastly, the options for
modifications can be easily adopted by the use of IBIS systems.
The major challenges of an integrated system are the security issues in their operations.
These present a need for the system to protect the data against loss or breach (Valacich &
Schneider, 2015). In addition, the cost is another factor which accounts for challenges to the
system. The most common threats are the accidents, sabotages, disasters, theft and hacking.
Accidents involve the damages that exist inside information systems. This involves inaccuracy in
data entries, lack of efficiency in operations, failure to comply with company standards or failure
The integrated business information systems have been the most effective method for
business operations due to their adoptions of personal computers. This has led to the increased
efficiency of business operations along with the increase in speed and accuracy. However, there
are various disadvantages to this system mainly due to the lack of decision making process and
lack of further innovations to be applied in existing systems.
The main purpose for the acceptance of the IBIS standard is the addressing of four
factors. They are the flexibility, simplicity, interoperatibility and modifiability (Pearlson,
Saunders & Galletta, 2016). The term flexibility denotes the allotment of free access to change
from a wide range of applications for database related purposes. The various applications that
support the integrated process are the MySQL, SQL Server, Access or ORACLE. Simplicity is
another feature of the IBIS which generally implies that the use of this method does not require
much implementation. In addition, an organization or company do not need to hire employees for
tending to the applications and can be accessed immediately after purchasing. The next purpose
of the integrated business information system is the ability for interoperations. This involves the
ability to be able to use for other operations. For this purpose, the system can be imported in
other formats so that this can be used in other files or programs as well. Lastly, the options for
modifications can be easily adopted by the use of IBIS systems.
The major challenges of an integrated system are the security issues in their operations.
These present a need for the system to protect the data against loss or breach (Valacich &
Schneider, 2015). In addition, the cost is another factor which accounts for challenges to the
system. The most common threats are the accidents, sabotages, disasters, theft and hacking.
Accidents involve the damages that exist inside information systems. This involves inaccuracy in
data entries, lack of efficiency in operations, failure to comply with company standards or failure
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SYSTEMS
to regularly backup the data. These problems can lead to major damages to the system leading to
loss in business. Failure to address such issues can also damage the relations among the
businesses and their clients.
Sabotages are the next challenges that are faced by business processes in operations.
These are the deliberate attempts for sabotaging and the accidental attacks. The deliberate
attempts are done usually by someone with a grudge against the system (Galliers & Leidner,
2014). One attempt of such attacks includes the disruption of services by using back door
attacks. Another type of sabotaging attacks is the logic bombs which can be done to affect a
system. The accidental attacks are mainly due to lack of efficiency in operations or the lack of
training.
Disasters are a threat to the information systems which can prove to be fatal. These are
the natural ones and the artificial ones. Natural disasters can be done by natural phenomena
whereas the man-made attacks are mainly due to activities like power-cut. Similarly, theft is
another challenge to the system that affects the system infrastructure. This method can be
divided into different categories namely the physical theft and the data theft. Data theft implies
the stealing of information by copying from the original files while the physical theft involves
stealing of company materials (Venkatesh, Brown & Bala, 2013). Moreover, the breaches are the
last point of concern for a security issue. This involves hacking in the system and stealing the
information from the company or organization concerned. This is mainly done by attacking the
system with viruses or malicious tools which can be used to harm the components and get
access.
to regularly backup the data. These problems can lead to major damages to the system leading to
loss in business. Failure to address such issues can also damage the relations among the
businesses and their clients.
Sabotages are the next challenges that are faced by business processes in operations.
These are the deliberate attempts for sabotaging and the accidental attacks. The deliberate
attempts are done usually by someone with a grudge against the system (Galliers & Leidner,
2014). One attempt of such attacks includes the disruption of services by using back door
attacks. Another type of sabotaging attacks is the logic bombs which can be done to affect a
system. The accidental attacks are mainly due to lack of efficiency in operations or the lack of
training.
Disasters are a threat to the information systems which can prove to be fatal. These are
the natural ones and the artificial ones. Natural disasters can be done by natural phenomena
whereas the man-made attacks are mainly due to activities like power-cut. Similarly, theft is
another challenge to the system that affects the system infrastructure. This method can be
divided into different categories namely the physical theft and the data theft. Data theft implies
the stealing of information by copying from the original files while the physical theft involves
stealing of company materials (Venkatesh, Brown & Bala, 2013). Moreover, the breaches are the
last point of concern for a security issue. This involves hacking in the system and stealing the
information from the company or organization concerned. This is mainly done by attacking the
system with viruses or malicious tools which can be used to harm the components and get
access.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SYSTEMS
Lastly, the requirements for cost are the last challenge that is faced by the implementation
of the IBIS processes (Jones, 2014). This involves upgrading the current infrastructure to support
the other necessary integrations which definitely costs more to the organizations or companies
implementing them.
Answer to question 3:
The use of big data has been a widely accepted term in terms of organizational
performance. It is mainly used to use the ability of prediction algorithms in business processes
thereby gaining more insights in the operations. This section discusses about the major impacts
the use of big data have led to in the organizations or companies accepting them (John Walker,
2014). The first major impact of big data is the changes of the various industries. Their use has
been extensively adopted for addressing in the business objectives. This has led the various
industries get a view of the analytical data from the vast amount of data sets and applies
accordingly in their businesses.
Another great impact in terms of businesses is the opening of a new revenue stream in the
industry. Organizations with great big data information are associated with selling their data in
the form of advertisement which in turn increases the revenue made from these aspects (Provost
& Fawcett, 2013). In turn, the advertising industries also gain various upgrades due to efficiency
in advertisements as the clients will now be able to target a greater audience set and can also
target globally.
Answer to question 4:
Lastly, the requirements for cost are the last challenge that is faced by the implementation
of the IBIS processes (Jones, 2014). This involves upgrading the current infrastructure to support
the other necessary integrations which definitely costs more to the organizations or companies
implementing them.
Answer to question 3:
The use of big data has been a widely accepted term in terms of organizational
performance. It is mainly used to use the ability of prediction algorithms in business processes
thereby gaining more insights in the operations. This section discusses about the major impacts
the use of big data have led to in the organizations or companies accepting them (John Walker,
2014). The first major impact of big data is the changes of the various industries. Their use has
been extensively adopted for addressing in the business objectives. This has led the various
industries get a view of the analytical data from the vast amount of data sets and applies
accordingly in their businesses.
Another great impact in terms of businesses is the opening of a new revenue stream in the
industry. Organizations with great big data information are associated with selling their data in
the form of advertisement which in turn increases the revenue made from these aspects (Provost
& Fawcett, 2013). In turn, the advertising industries also gain various upgrades due to efficiency
in advertisements as the clients will now be able to target a greater audience set and can also
target globally.
Answer to question 4:
8INFORMATION SYSTEMS
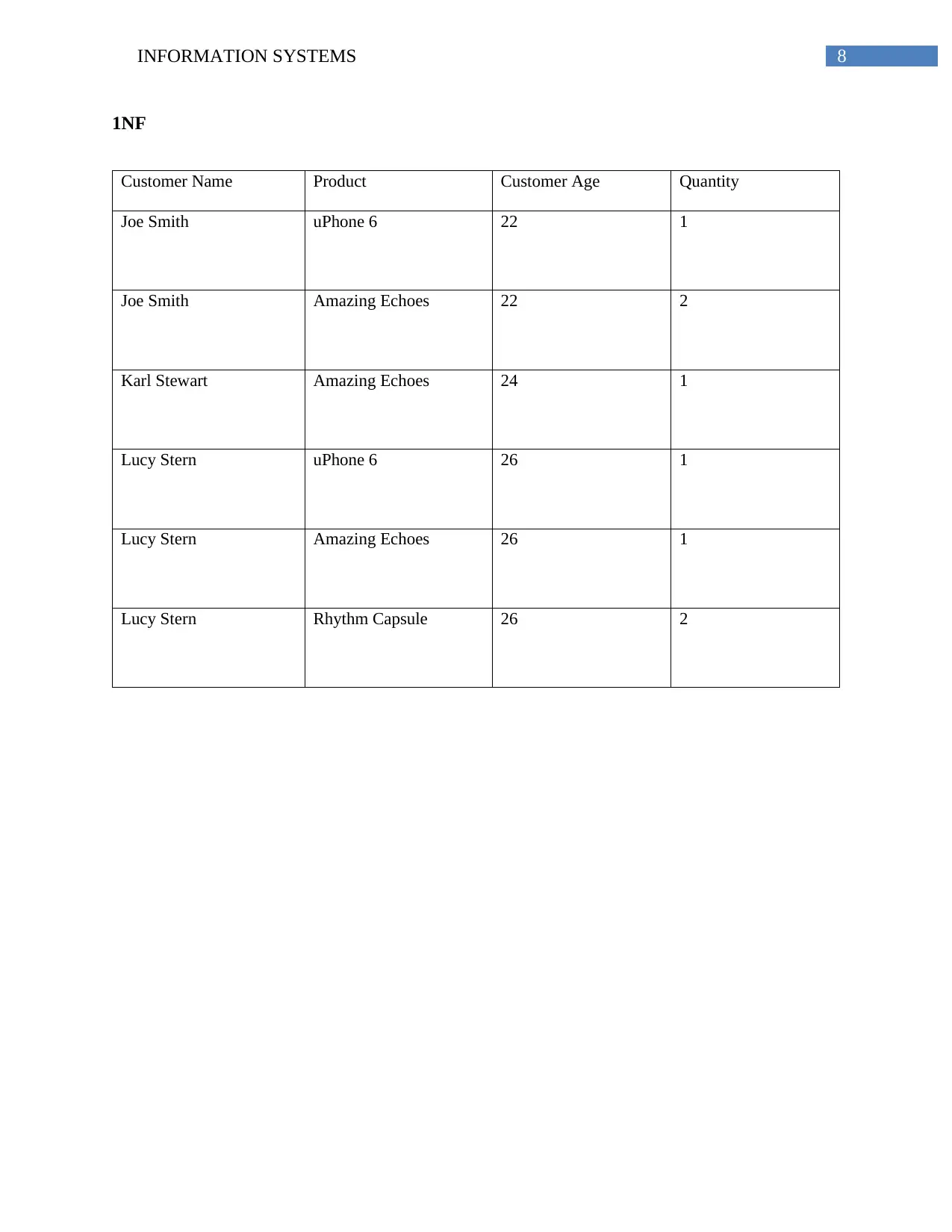
1NF
Customer Name Product Customer Age Quantity
Joe Smith uPhone 6 22 1
Joe Smith Amazing Echoes 22 2
Karl Stewart Amazing Echoes 24 1
Lucy Stern uPhone 6 26 1
Lucy Stern Amazing Echoes 26 1
Lucy Stern Rhythm Capsule 26 2
1NF
Customer Name Product Customer Age Quantity
Joe Smith uPhone 6 22 1
Joe Smith Amazing Echoes 22 2
Karl Stewart Amazing Echoes 24 1
Lucy Stern uPhone 6 26 1
Lucy Stern Amazing Echoes 26 1
Lucy Stern Rhythm Capsule 26 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9INFORMATION SYSTEMS
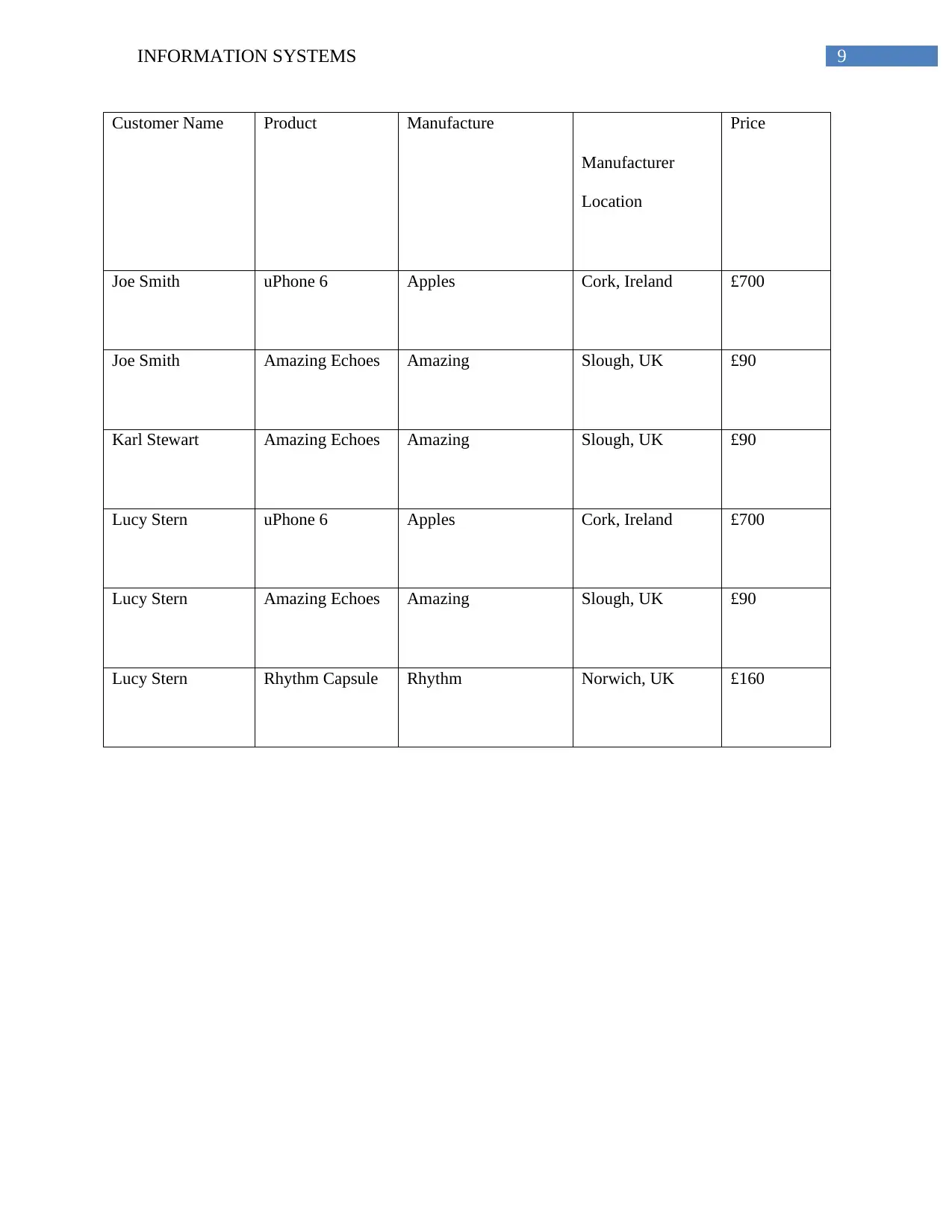
Customer Name Product Manufacture
Manufacturer
Location
Price
Joe Smith uPhone 6 Apples Cork, Ireland £700
Joe Smith Amazing Echoes Amazing Slough, UK £90
Karl Stewart Amazing Echoes Amazing Slough, UK £90
Lucy Stern uPhone 6 Apples Cork, Ireland £700
Lucy Stern Amazing Echoes Amazing Slough, UK £90
Lucy Stern Rhythm Capsule Rhythm Norwich, UK £160
Customer Name Product Manufacture
Manufacturer
Location
Price
Joe Smith uPhone 6 Apples Cork, Ireland £700
Joe Smith Amazing Echoes Amazing Slough, UK £90
Karl Stewart Amazing Echoes Amazing Slough, UK £90
Lucy Stern uPhone 6 Apples Cork, Ireland £700
Lucy Stern Amazing Echoes Amazing Slough, UK £90
Lucy Stern Rhythm Capsule Rhythm Norwich, UK £160
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10INFORMATION SYSTEMS
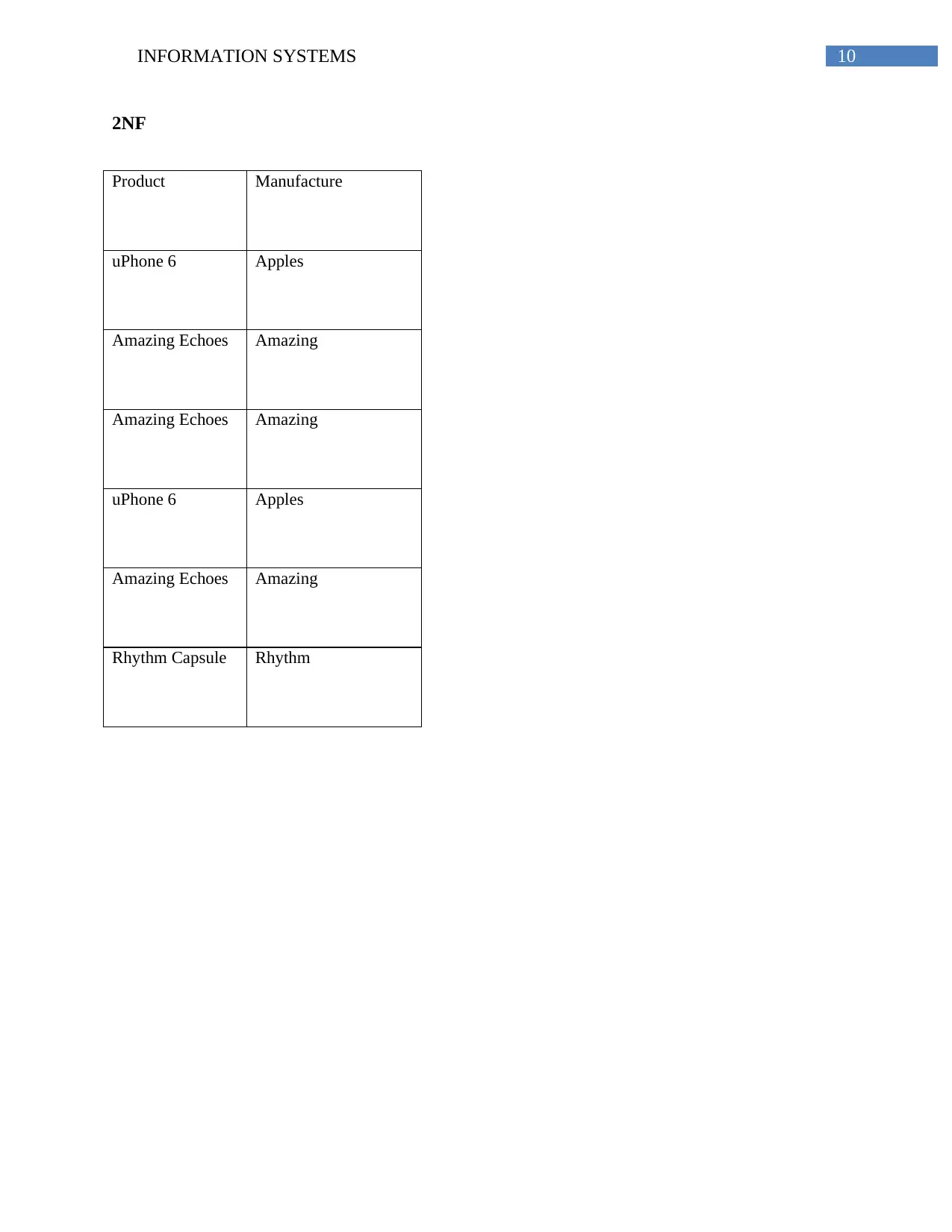
2NF
Product Manufacture
uPhone 6 Apples
Amazing Echoes Amazing
Amazing Echoes Amazing
uPhone 6 Apples
Amazing Echoes Amazing
Rhythm Capsule Rhythm
2NF
Product Manufacture
uPhone 6 Apples
Amazing Echoes Amazing
Amazing Echoes Amazing
uPhone 6 Apples
Amazing Echoes Amazing
Rhythm Capsule Rhythm
11INFORMATION SYSTEMS
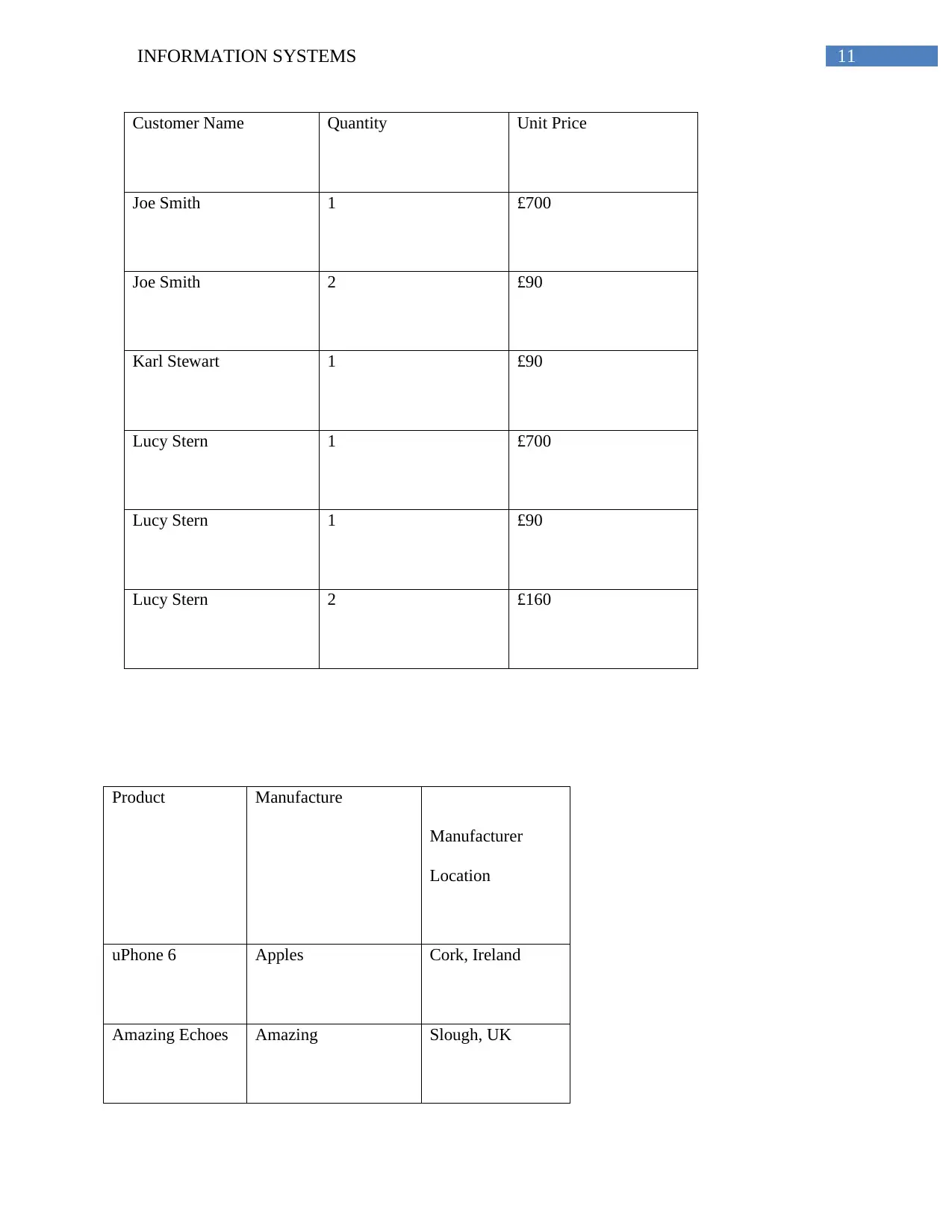
Customer Name Quantity Unit Price
Joe Smith 1 £700
Joe Smith 2 £90
Karl Stewart 1 £90
Lucy Stern 1 £700
Lucy Stern 1 £90
Lucy Stern 2 £160
Product Manufacture
Manufacturer
Location
uPhone 6 Apples Cork, Ireland
Amazing Echoes Amazing Slough, UK
Customer Name Quantity Unit Price
Joe Smith 1 £700
Joe Smith 2 £90
Karl Stewart 1 £90
Lucy Stern 1 £700
Lucy Stern 1 £90
Lucy Stern 2 £160
Product Manufacture
Manufacturer
Location
uPhone 6 Apples Cork, Ireland
Amazing Echoes Amazing Slough, UK
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





